Risky Bulletin Newsletter
April 21, 2025
Risky Bulletin: Zoom has a remote control feature and crypto thieves are abusing it
Written by

News Editor
This newsletter is brought to you by Devicie. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
Hackers are abusing a little known Zoom feature to take control of their victims' computers to install malware and steal cryptocurrency.
The feature is named "Remote Control" and is part of Zoom's accessibility suite, where it was included for users with various disabilities to allow other users in the same meeting to control their PC.
Since at least this year, a cybercrime group named ELUSIVE COMET has incorporated this secret Zoom feature into their social engineering attacks and has successfully stolen millions of US dollars worth of crypto assets from their victims.
According to the Security Alliance, a cybersecurity team with members from across the cryptocurrency community, the group operates by reaching out to prominent figures in the cryptocurrency community via Twitter DMs.
Elusive Comet poses as venture capital firms, podcast hosts, and reporters to invite targets to Zoom video conferences.
The trick is that one member of the group also joins the meeting but with the generic name of "Zoom," which they use to request remote control to a victim's system. The trick here is that because that video conference participant is named Zoom, the popup asking the victim to grant remote control looks like a native Zoom permission request, which can trick inattentive victims.
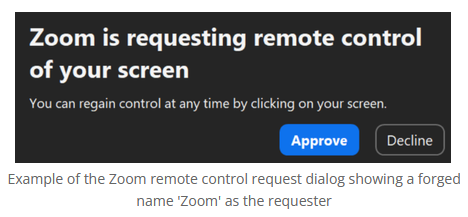
One of these gang's targets was Trail of Bits CEO Dan Guido, who wrote up his encounter with the gang in a blog post last week.
Both Trail of Bits and the Security Alliance recommend disabling the Remote Control feature and possibly the entire Zoom accessibility suite altogether—if it is not needed. Instructions on how to do this are included in this Zoom help page and in the Trail of Bits blog post.
Risky Business Podcasts
Risky Business is now on YouTube with video versions of our main podcasts. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
Japanese brokerage firms hacked big: Hackers have hijacked over $700 million worth of assets from Japanese brokerage firms. The hackers gained access to brokerage accounts through phishing attacks, sold the victim's stocks, and bought shares in Chinese companies with the proceeds. Japan's financial regulator says most of the hacks took place between February and April this year. [Additional coverage in Nippon]
GJC Corp leak: Brazilian media giant GJC left an AWS S3 bucket exposed that could have allowed attackers to hijack JS code from their authentication flows.
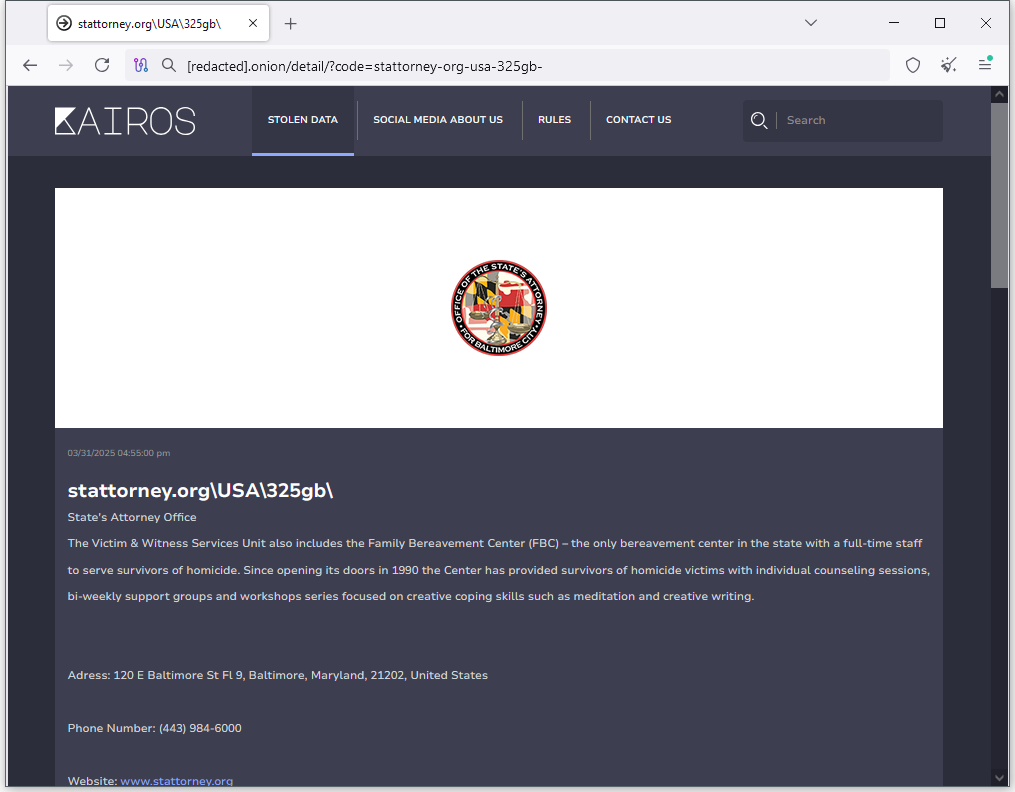
Baltimore Attorney's Office breach: The Kairos data extortion group has leaked a small collection of files from the Baltimore State's Attorney's Office. The small leak is likely part of an ongoing extortion attempt after the group listed the office on its leak portal at the end of March. The Kairos group emerged in November and claimed hacks at over 30 organizations. [Additional coverage in DataBreaches.net]
General tech and privacy
Discord tests face scans: Discord is testing a new age verification system that requires users to scan their faces before accessing sensitive content. If users don't want to scan their faces, they'll be asked to verify their age the old way by submitting a scan or photo of their ID or driver's license. The feature is currently under testing in Australia and the UK, where stricter child protection laws have recently passed. [Additional coverage in Video Games Chronicle]
Ubuntu EOL: Ubuntu 20.04, Focal Fossa, is set to reach EOL in May.
GrapheneOS looking for new devs: GrapheneOS, a super-secure version of Android, is looking for new developers after one of its two senior developers was conscripted into the military in their home country.
One of our two senior developers has been forcibly detained and conscripted to participate in a war. When they first went missing, we revoked their repository access as a precaution. We soon learned their disappearance was completely unrelated to GrapheneOS. Our priority has been keeping them safe.
— GrapheneOS (@grapheneos.org) 2025-04-18T15:25:58.300Z
Python's verified cryptography: After 2.5 years of work, Python now runs on over 15,000 lines of verified cryptographic code.
Private Proof API: Google is working on a new Web API to help websites detect bots and online fraud. The new Private Proof API is meant to replace existing and intrusive bot and fraud detection systems that rely on cookies and device fingerprinting. The API uses Zero-Knowledge Proofs (ZKPs) and allows websites to ask browsers about a user's profile age.
EU delays Apple, Meta fines: According to the WSJ, the EU delayed fining Apple and Meta in years-long anti-trust investigations at the pressure of US authorities.
Entra lockouts: Microsoft Entra customers are reporting a sudden spike in security alerts and account lockouts. According to reports on Reddit, the issue appears to be caused by a new Entra feature named MACE Credential Revocation. The feature warns companies when employees are using an insecure password that leaked online in a past breach. Customers said that investigations showed the affected accounts to be perfectly safe. [Additional coverage in BleepingComputer]
Government, politics, and policy
EU offers anti-spy pouches to MPs: The EU offered Faraday bags to protect phones to five MPs who visited Hungary last week on an official investigation. The EU took steps to protect MPs after a previous delegation was spied on and secretly followed by Hungarian intelligence in previous years. EU officials told Politico Europe that the use of Faraday pouches to protect phones is not a common EU practice. A previous report claimed the EU started advising top officials to use burner phones when traveling abroad, including to former ally the US. Both Hungary and the US have slid into autocratic rule.
CISA discontinues VT, Censys access: The US Cybersecurity and Infrastructure Security Agency has discontinued its Censys and VirusTotal contracts. According to a NextGov report, the agency notified threat-hunting teams last week and promised to find alternative tools. Both tools are used to find and investigate signs of compromise and threat actor activity. According to Axios, CISA also fired 75 Nightwing and Peraton contractors who worked with its threat-hunting teams.
Dutch government wants more AI, fewer employees: The Dutch Minister of the Interior wants to hire fewer ICT (information, communication, and technology) workers and look at using more "labor-saving AI." This also comes as the Dutch government wants to establish itself as an AI hub in the EU. [Additional coverage in Tweakers]
The Netherlands to recruit cyber reservists: The Dutch government is seeking to recruit new cyber reservists in its armed forces. A new recruitment campaign is scheduled for later this year. According to Dutch public broadcaster NOS, the Dutch Defense Cyber Command operated six platoons of 110 cyber reservists last year.
Zambia introduces new cybersecurity law: The Zambian government passed a new cybersecurity law that requires telecommunication companies to provide lawful interception capabilities for all types of electronic communications. The new law has spooked some countries, with the US issuing a travel advisory for Americans visiting the country. Zambian officials say the law mimics similar laws elsewhere and will be used only under judicial oversight. They say the law is needed to fight fraud, disinformation, and CSAM content.
Zambia's new cybersecurity law requires interception of *all* electronic comms? Guess privacy is now a luxury, not a right. What could possibly go wrong? #Cybersecurity #Privacy #Zambia #SurveillanceState
— Hella Sheppard (@hellasheppard.bsky.social) 2025-04-17T18:55:51.298111+00:00
Sponsor section
In this Risky Bulletin sponsor interview Shane Harding, CEO of Devicie, talks to Tom Uren about trends in the enterprise software and security market that he thinks will have huge impacts. Software is becoming smarter and aims to solve problems rather than simply provide capabilities and Microsoft has embarked on a big push into the SME security market.
Arrests, cybercrime, and threat intel
Scrublord charged: US authorities have indicted a man on cybercrime charges for stealing the personal data of over 65,000 people. Nicholas Moses used the hacker name Scrublord and was an alleged customer of the SmokeLoader botnet. He is accused of renting access to the botnet and deploying infostealers on victims' computers. Authorities discovered Moses' actions after they took down the SmokeLoader botnet last May. [h/t CourtWatchNews]
US charges Nemesis market admin: The US Justice Department has charged an Iranian man for running the Nemesis dark web marketplace. Behrouz Parsarad launched the website in March 2021 and ran it for three years until it was seized by German authorities last year. It was mainly known for selling drugs and cyber services. Parsarad was also sanctioned by the US Treasury last month.
Scam group sentenced: A Dutch judge has sentenced four suspects to three years in prison for running a scam call center out of a vacation home in the country's north.
Scammers impersonate IC3 agents: The FBI says scammers are impersonating its Internet Crime Complaint Center (IC3) staff as part of a new campaign taking place via social media and internet forums. Scammers pose as attractive females and redirect victims of fraud to an account posing as an IC3 agent. Victims are told the fake IC3 agent can help recover their funds, but victims are scammed again for new payments.
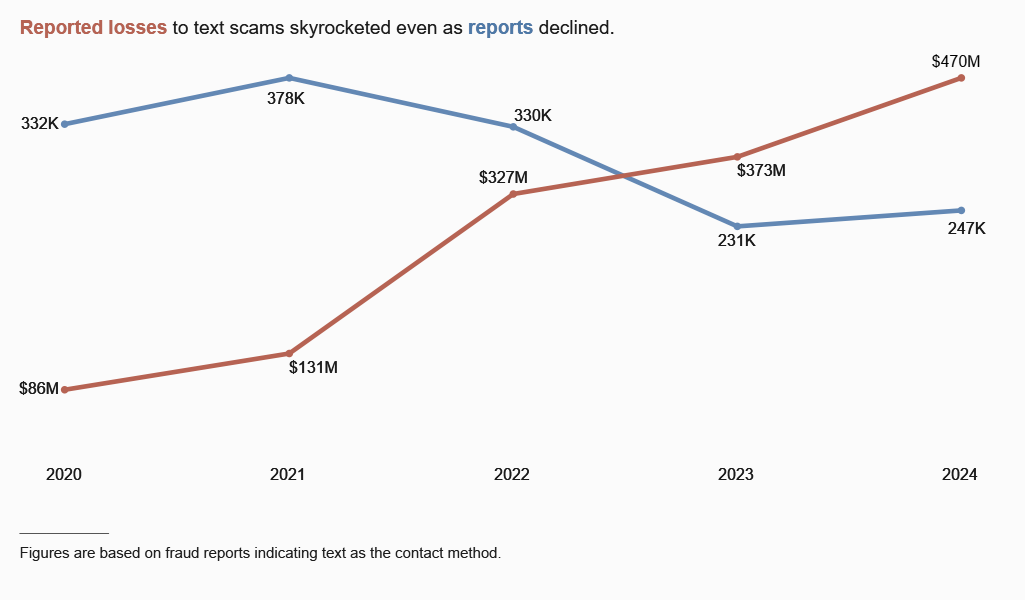
Americans lost $470mil to phone scams: The US Federal Trade Commission says Americans lost $470 million to phone scams last year. The agency says the real figure is likely many times higher since most users report only a fraction of the incidents. The most common phone hoaxes involve package delivery scams, phony job opportunities, and fake fraud alerts. Scams involving unpaid toll fees saw the biggest growth last year.
New npm malware: Sixty-nine malicious npm packages were discovered and taken down last week. Check out the GitHub security advisory portal for more details. This also includes reports of typosquatted Telegram bot libraries delivering SSH backdoors and data exfiltration routines.
Malware on the Chrome Web Store: The Browser Boost Chrome extension was modified to include malware shortly after its developer sold it off to an unnamed third party. The extension has now been removed from the official Web Store. [h/t John Tuckner]
Cyber threats caused by rise in global tensions: France's cybersecurity agency and security firm Resecurity warn that the rise in global tensions might lead to an increase in cyber threats. ANSSI warns about cyber-enabled disruptions to urban transport networks, while Resecurity warns of the same thing to the energy and nuclear sectors.
CPJ issues advisory for journalists traveling to the US: The Committee to Protect Journalists has issued a safety advisory for journalists traveling to the US. Reporters were urged to travel with burner phones, new SIM cards, and spare laptops.
Meduza Stealer admin disappears: The administrator of the Meduza Stealer infostealer has been MIA for over a month and removed his Telegram account. I smell a rug pull!
SilverFox TTP updates: SilverFox, a China-based cybercrime group, is now using WDAC to block antivirus software.
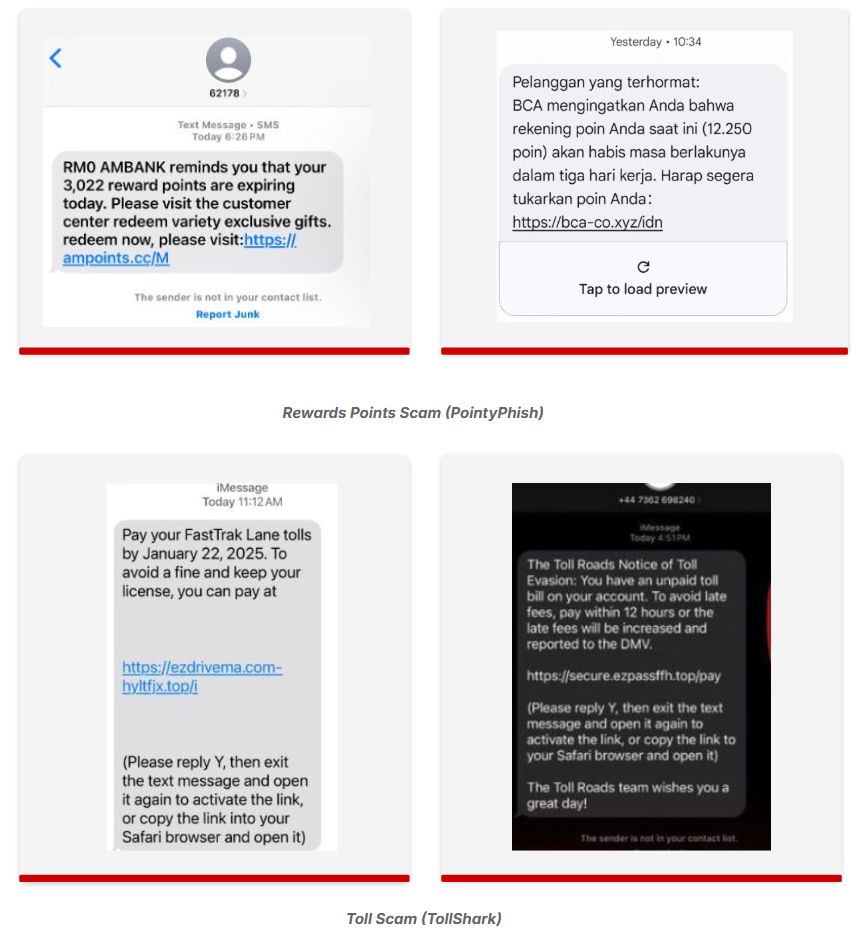
PointyPhish and TollShark: CTM360 researchers look at PointyPhish and TollShark, two smishing waves targeting reward points programs and toll services, respectively. CTM360 says both campaigns originate from the Darcula PhaaS.
Malware technical reports
SpyMax malware: ThreatMon has found the SpyMax malware disguised as the official application of the Chinese Prosecutor's Office. The campaign targeted Chinese-speaking users across mainland China and Hong Kong.
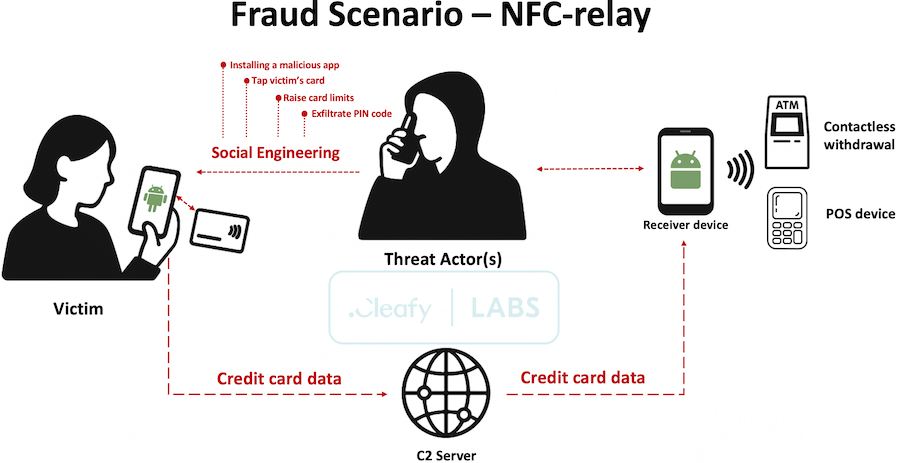
SuperCard X automates NFC relay attacks: A Chinese cybercrime group has developed and is renting access to Android malware capable of automating NFC relay attacks. The new SuperCard X malware can be deployed on victim devices, from where it can capture NFC data and relay it to an attacker. The NFC operation details are then used to withdraw the victim's funds at an ATM or pay for expensive products via POS. SuperCard X is offered through a Malware-as-a-Service (MaaS) model and is part of a rising trend of NFC-capable malware first spotted in Russia last year.
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Devicie Technical Product Manager Tom Plant on the upcoming Windows 10 end-of-support and the looming Great Windows 11 Migration.
APTs, cyber-espionage, and info-ops
New Billbug attacks: Broadcom's Symantec has spotted Chinese espionage group Billbug (Lotus Blossom, Lotus Panda, Bronze Elgin) compromise multiple organizations in a Southeast Asian country between August 2024 and February 2025.
"Targets included a government ministry, an air traffic control organization, a telecoms operator, and a construction company. In addition to this, the group staged an intrusion against a news agency located in another country in Southeast Asia and an air freight organization located in another neighboring country."
Chinese APT leaks exploits: A Chinese cyber-espionage group briefly misconfigured one of its servers and exposed some of its attack tooling. The leak allegedly contained exploit scripts for Fortinet firewalls and VPNs, PHP web shells, and network reconnaissance scripts customized for a major Japanese company. Security firm Hunt Intelligence says the server was likely operated by an APT tracked as RedGolf.
Team46 linked to TaxOff: Russian security firm Positive Technologies has linked hacking group Team46 (spotted last year attacking a Russian rail freight operator) to TaxOff (a group typically posing as the Russian tax office).
Vulnerabilities, security research, and bug bounty
ViPNeT exploitation in Russia: A hacking group is planting backdoors inside Russian companies using the ViPNet enterprise VPN software. According to Kaspersky, the attackers exploit the software's update mechanism to install the backdoor. ViPNet owner Infotecs has confirmed the attacks but said the exploit was taking place after hackers already had access to a victim's VPN nodes. The attacks took place this month, and Kaspersky described the backdoor as "complex."
SSL.com bug issues fake certificates: Certificate authority SSL.com is investigating a bug in its domain control validation (DCV) system that can be abused to issue fake certificates for domains a person doesn't control.
SonicWall exploitation: ArcticWolf believes it spotted the campaign exploiting a 2021 vulnerability used to recently hack SonicWall SMA devices. CISA warned about these attacks last week.
ASUS AiCloud auth bypass: ASUS has fixed an authentication bypass vulnerability that could allow attackers to run malicious code on ASUS routers where the AiCloud service is installed. The company says that if users can't install the firmware updates, they should disable the AiCloud. The service allows ASUS users to connect to their home networks through a mobile app or a custom URL.
LLMs suck at CTI: An academic paper argues that large language models are inefficient for cyber threat intelligence operations, where they produce longer reports with worse, lacking, and untrustworthy output.
"Few-shot learning and fine-tuning only partially improve the results, thus posing doubts about the possibility of using LLMs for CTI scenarios, where labeled datasets are lacking and where confidence is a fundamental factor."
"Regarding the CVE codes we could see how the maximum recall is 0.90 (gemini and mistral) and the minimum is 0.87 (gpt4o), meaning that LLMs overlook at least the 10% of the vulnerabilities contained in the threat report and exploited during threat campaigns. The same phenomena concern attack vector, in which the maximum recall is 0.83 and the minimum is 0.74, meaning that 26% of the techniques used to exploit CVEs are overlooked."
Hilarious!
Infosec industry
Acquisition news: Indian IT company Infosys has acquired Australian cybersecurity company The Missing Link.
New tool—BBRadar: Security researcher Kle0z has built BBRadar, a tool to find the latest and active bug bounty programs.
New tool—Audit GitHub Actions: GitHub has released Audit GitHub Actions, an unofficial tool to audit GitHub Actions.
New tool—DockerKnocker: TrustedSec researcher n00py has released DockerKnocker, a tool to access unsecured Docker APIs.
Threat/trend reports: The Australian Cyber Network, Ernst & Young, IBM X-Force, Microsoft MSTIC, and SafeDep have recently published reports and summaries covering various infosec trends and industry threats.
Risky Business podcasts
Tom Uren and Patrick Gray discuss Trump's order singling out Chris Krebs, former head of CISA, which requires investigations into Krebs and also punishes his employer. It is a move deliberately designed to chill dissent, and they look at what the cybersecurity industry will likely do in response, which is probably not much.
In this edition of Between Two Nerds, Tom Uren and The Grugq look at the idea of global critical infrastructure. One common example is submarine cables, which are globally important but are vulnerable because they are hard to defend. But what about services from tech giants? Are they global critical infrastructure?
