Risky Bulletin Newsletter
May 30, 2025
Risky Bulletin: Windows Update will soon deliver individual app updates
Written by

News Editor
This newsletter is brought to you by Sublime Security, an email security platform that's not a black box. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
Microsoft will open up the Windows Update mechanism to third-party apps and driver makers so they can deliver updates to users in a faster and more seamless manner.
The new feature is currently under testing and will ship in a future Windows 11 release.
Microsoft has asked developers this week to sign up and help test out the new software update orchestration platform before its official release.
Developers can sign up as an official update provider on the platform and configure how their updates will behave.
The platform—currently has no official name—will handle everything on their behalf. It will scan for new updates on the developer's servers, handle the update installation process, handle user notifications, force device restarts, handle errors and fails, and even impose installation deadlines.
Microsoft says a primary reason why it's finally building and developing this new orchestration platform is for its sysadmin community, which has long requested a centralized method of dealing with software updates.
Until now, Windows developers have had to build and maintain their own update mechanisms, which has often led to a laundry list of issues, from supply chain attacks or entire fleets of PCs running outdated software packages and putting corporate networks at risk.
In the year of the Lord, 2025, there are still thousands of system administrators manually checking app websites for new versions every day, downloading the apps, and then using various custom-made scripts to deploy the update to all their users.
Currently, there are a few Windows app update orchestrator platforms available, but having this one baked right into Windows Update will most likely make it the default going forward.
The new platform will also open a new can of security risks and potential abuses, but we'll have to wait and see how that evolves after it launches.
The new app update system is also the first major product designed and set to launch at Microsoft after the company announced its Secure Future Initiative last year, so this will also serve as a litmus test if that whole thing is legit or just another bag of corporate PR baloney.
This is a cool idea. It's pretty wild how long Windows has lacked a central software update capability—at least a first-party one. But this also maybe feels like a fun attack surface. techcommunity.micros...
— Taggart (@taggart-tech.com) 2025-05-28T13:25:41.000Z
Microsoft just introduced Windows Update orchestration platform. A platform to manage all apps and driver updates. Including MSIX and Win32 (MSI, EXE). This could change few things in the app management space based on the description in the blog.https://t.co/wh2T0vzend
— Toms Knostenbergs (@TomsKnostenberg) May 28, 2025
Risky Business Podcasts
The main Risky Business podcast is now on YouTube with video versions of our recent episodes. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
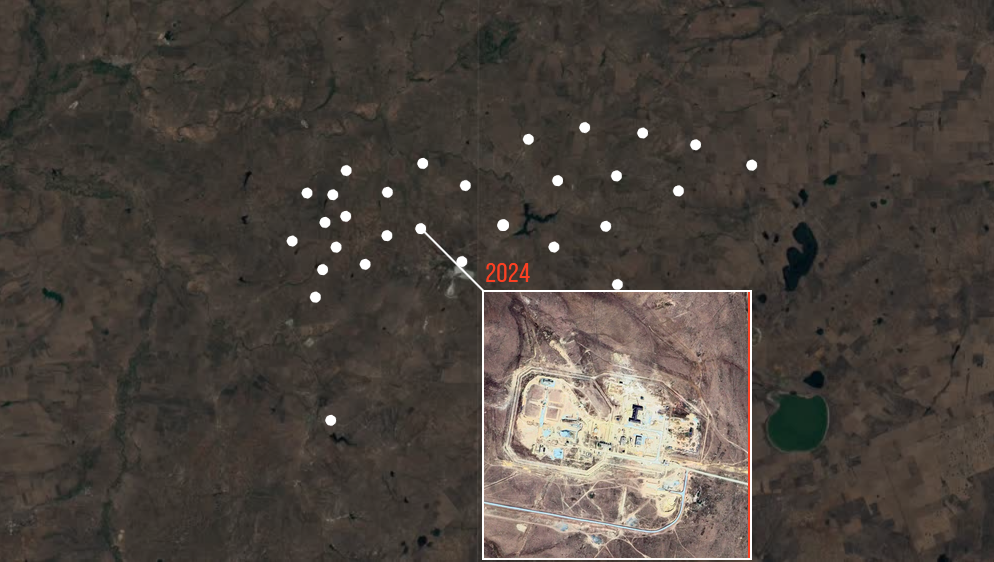
Public DB exposes Russia's nuclear bases: Over two million documents with extremely sensitive details on Russia's nuclear weapons bases have leaked online via an internet-exposed database. The documents contain extremely detailed blueprints and layout information on all of Russia's nuclear missile sites. They include details on recent repairs, new buildings, and even new bases. The leaky server was discovered by Danish journalists who spent months exfiltrating the data and analyzing it together with Der Spiegel. The leak was described as "absolutely incredible" and is the first time since the 70s that Western countries have accurate blueprints of Russian nuclear bases. [Additional coverage in Danwatch] [Archive]
ConnectPatch discloses APT breach: IT software company ConnectWise says that a suspected state-sponsored group has breached its ScreenConnect remote access platform. The company said the breach affected only a very small number of customers. ConnectWise has already notified all affected customers and is now working with Mandiant and law enforcement to investigate the breach. [Additional coverage in CRN]
Cork Protocol crypto-heist: Hackers have stolen more than $12 million worth of crypto-assets from the decentralized finance platform Cork Protocol.
The Salvation Army ransomware attack: The Chaos ransomware group has listed the Salvation Army on its dark web leak site. The organization has yet to confirm an official incident.
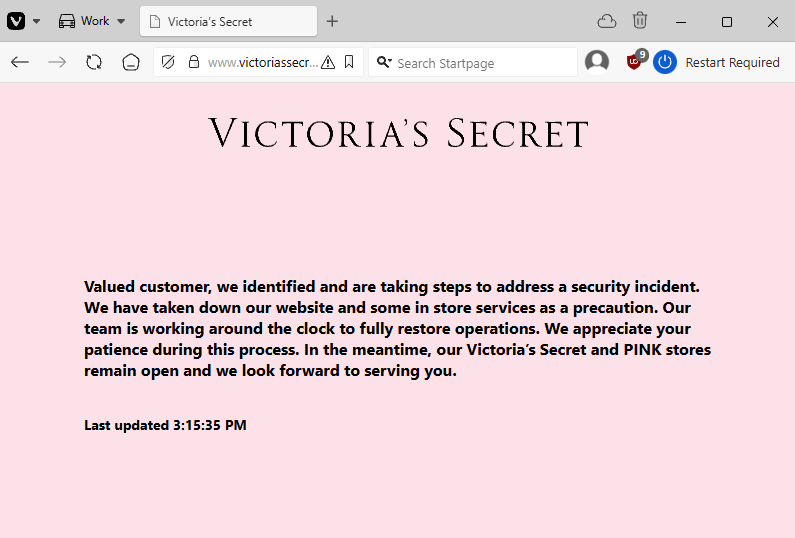
Victoria's Secret cyberattack: Lingerie company Victoria's Secret has taken down its US website in the aftermath of a cyberattack. Stores are still open for business, but some in-store services have been halted as the company restores IT systems. The company did not provide additional details. Victoria's Secret operates over 1,300 retail stores across 70 countries. [Additional coverage in the BBC]
General tech and privacy
Oregon bans the sale of precise location data: The US state of Oregon has banned the sale of precise geolocation data. It's the second state after Maryland to pass such a law. [Additional coverage in The Record]
Mass shooting lawsuit goes after tech platforms: A gun safety group has sued several tech platforms (Meta, Amazon, Discord, Snap, 4chan, and others), arguing that their algorithms radicalized a mass shooter who then ended up killing 10 people in Buffalo, New York, in 2022. [Additional coverage in The Verge]
Windows Backup for Organizations: Microsoft has released in public preview a new enterprise tool named Windows Backup for Organizations. The tool allows companies to backup and restore the PC settings of every Entra-joined device.
Apple OS version numbers change: Apple will switch OS version numbers to the current year, which means this year's editions will be iOS 26 and macOS 26. [Additional coverage in Bloomberg]
PQC Migration Roadmap: The Post-Quantum Cryptography Coalition has published a PQC Migration Roadmap.
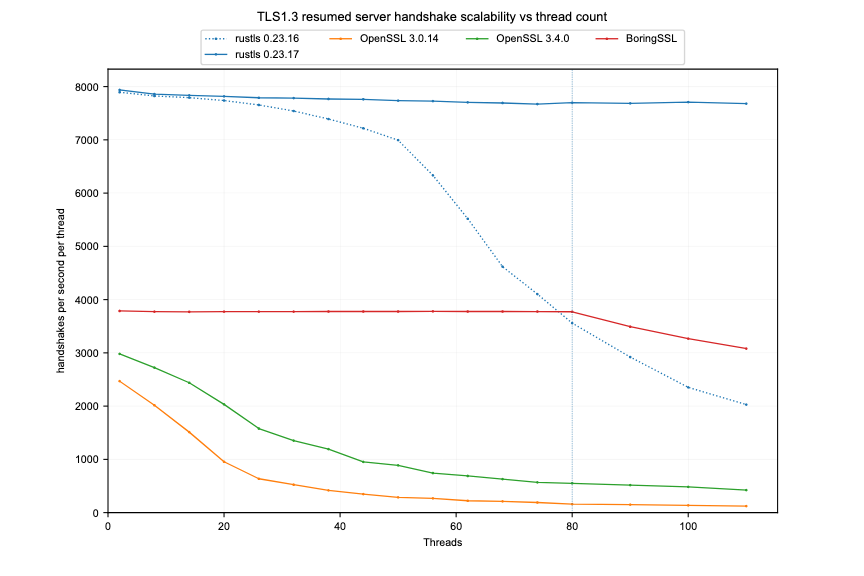
Rustls performance gains: The Rustls project claims that recent versions of its library now rival the performance of major TLS projects.
Government, politics, and policy
Czechia accuses China of 2022 MFA hack: The Czech Republic has accused China of hacking its Ministry of Foreign Affairs. The hack took place in 2022, breached an unclassified network, and also impacted a Czech critical sector operator. Officials attributed the hack to APT31, a cyber-espionage group linked to China's Ministry of State Security. NATO and the EU have issued statements of solidarity with the Czech Republic.
NATO proposes cybersecurity to be included in spending target: NATO has proposed that expenditures on cybersecurity, border, and coastal security be considered towards the alliance's defense spending target. The new spending target will be 5% of GDP, with 3.5% on hard defense expenditures and the rest on defense-related items. Cybersecurity investments will count towards this latter category. Member states are set to vote on the new spending target at a NATO summit to be held in The Hague in June. [Additional coverage in Bloomberg]
New UK Cyber and Electromagnetic Command: The UK government has established a new cyber warfare structure inside its armed forces. The new Cyber and Electromagnetic Command will be responsible for coordinating defensive and offensive cyber operations to support military missions. The new cyber branch will be led by General Sir James Hockenhull. The UK government also plans to invest £1 billion in new battlefield systems to interconnect its military branches.
Texas passes and signs age verification law: Texas Governor Greg Abbott has signed a bill into law that will require mobile app stores to verify the age of their users before they can download apps. The law will enter into effect next year and impacts Apple and Google primarily. Both companies criticized the law because it would force them to collect vast amounts of personal information on every user. A similar law was also passed in Utah earlier this year. [Additional coverage in CNN]
US banks as SEC to rescind cyber disclosure rule: Five US banking associations have asked the US Securities and Exchange Commission to rescind its cyber incident disclosure rule. The rule was adopted last year and requires US businesses to disclose data breaches to the SEC within four business days of determining material impact. Banks claim the rule raises incident complexity and puts a strain on their resources. It also creates additional risk, with some ransomware groups leveraging unfulfilled SEC disclosure requirements to put additional pressure on victims during the extortion process. [Letters from ABA, BPI, ICBA, IIB, SIFMA]
CBP collects genetic data from migrant children: A WIRED investigation has found that the US Customs and Border Protection agency has collected DNA samples from over 133,000 migrant children and added them to a criminal database.
Trump cyber nominees status: Two nominees chosen for cybersecurity roles in the new Trump government structure are expected to testify before a Senate panel next week. This includes Sean Cairncross, picked to be the National Cyber Director, and Sean Plankey, picked for CISA Director. [Additional coverage in NextGov]
US State Department threatens visa restrictions: The US State Department has threatened foreign officials with visa restrictions if they dare to "censor" Americans online by requesting that US social media companies adopt "global content moderation policies." Translated to regular words—leave MAGA's propaganda machine alone to attack EU democratic governments with blatant lies and disinformation campaigns.
This should terrify every European who believes in democracy and the rule of law. The US state department, whose soldiers occupy bases on European soil across the continent, is effectively calling on its "civilisational allies" (the far-right) in Europe to turf out centrist governments.
— Dave Keating (@davekeating.substack.com) 2025-05-28T13:10:58.993Z
Mandatory CCTV camera testing enters into effect in India: India enacted a new law in April that requires all foreign CCTV camera makers to submit products for testing before being allowed on the market. The tests are conducted in government labs and are mandatory for any internet-connected CCTV model. Companies must submit source code for all camera firmware and must also allow Indian officials to audit factory processes. Several manufacturers have expressed concerns about the slow pace of the tests and factory visits and warn of future supply disruptions. [Additional coverage in Reuters]
Vietnam enforces security standards for CCTV cameras: Something we missed back in February was that Vietnam passed new rules enforcing strict cybersecurity standards for any surveillance cameras produced or imported into the country. This includes unique per-device passwords, regular security updates, secure deletion protocols, and more. This will go into effect in 2026. [Additional coverage in Vietnamnet Global]
Russia to create a national VPN policy: The Russian Parliament plans to publish a national policy on the use of VPN products across the country. Per Interfax, the new policy will be ready within six months. The new policy will most likely ban regular users from VPNs and keep the technology accessible to Russia's private sector only.
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Bobby Filar, Head of Machine Learning at Sublime Security. Bobby takes us through the rising problem of spam bombing, or email bombing, a technique threat actors are increasingly using for initial access into corporate environments.
Arrests, cybercrime, and threat intel
Pakistan arrests HeartSender members: Pakistan authorities have arrested 21 suspects linked to a phishing group known as HeartSender. The arrests come after Dutch and US authorities seized the group's servers in January this year. The group sold phishing kits and phishing templates and also maintained a marketplace to sell stolen credentials. HeartSender has been linked to more than $50 million in losses in the United States alone. [Additional coverage in KrebsOnSecurity]
US sanctions cyber scam hosting provider: The US government has imposed sanctions on a Philippine CDN and its administrator for providing server infrastructure to cyber scam compounds. Sanctions were levied against Funnull Technologies and its administrator, Liu Lizhi. Officials have linked Funnull servers to over $200 million in victim-reported losses. The FBI has released pages and pages of IOCs related to cyber scam infrastructure hosted on Funnull servers between October 2023 and April 2025. [FBI flash alert/PDF]
Indian police raids cyber scam compound: Indian authorities have raided a cyber scam compound in the city of Visakhapatnam. More than 100 suspects were detained and questioned. The group allegedly ran call centers that defrauded users in English-speaking languages for the past two years. Authorities described the call centers as a smaller version of the scam compounds operating in Cambodia and Myanmar. [Additional coverage in the Times of India]
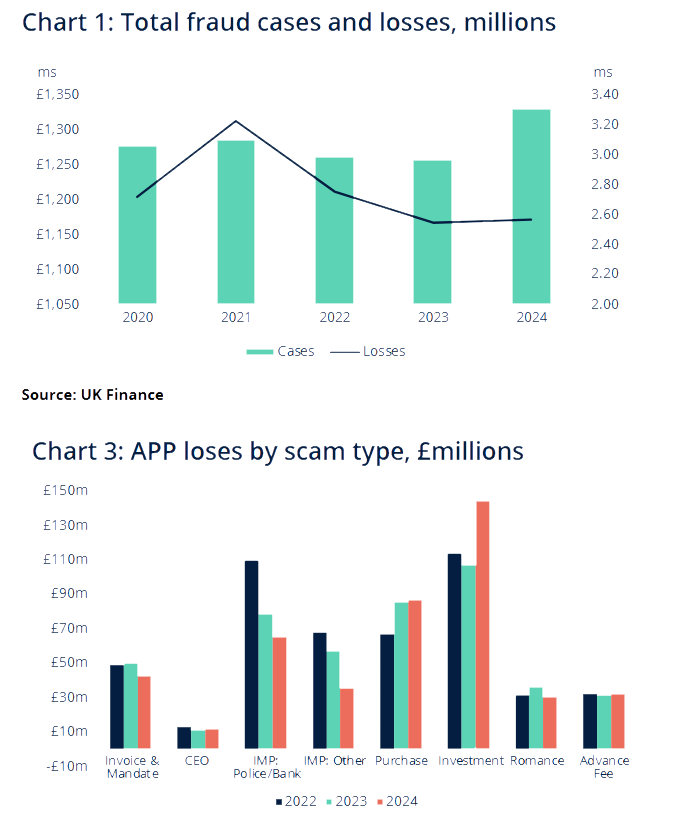
UK loses £1.17bil to fraud: UK companies have lost £1.17 billion ($1.58 billion) to online fraud across over 3.3 million reported cases. The most losses were linked to investment scams, a category that also topped the FBI's cybercrime report. According to the OCCRP, fraud now accounts for 41% of all reported crime in the UK. [Additional details in UK Finance's report]
UNC6032: Google Cloud has published a profile on UNC6032, a threat actor using AI video generator websites to distribute infostealers. Many of the sites are advertised on Facebook and LinkedIn. The group has been active since mid-2024 and has a Vietnam nexus.
Same tactic, other groups: Similar to the Google report above, Cisco Talos looks at multiple other groups using the same technique of "free AI tools" to deliver infostealers, RATs, and even ransomware.
Google Apps Script abuse: Cofense has spotted a phishing campaign that hosts malicious pages on the Google Apps Script development platform.
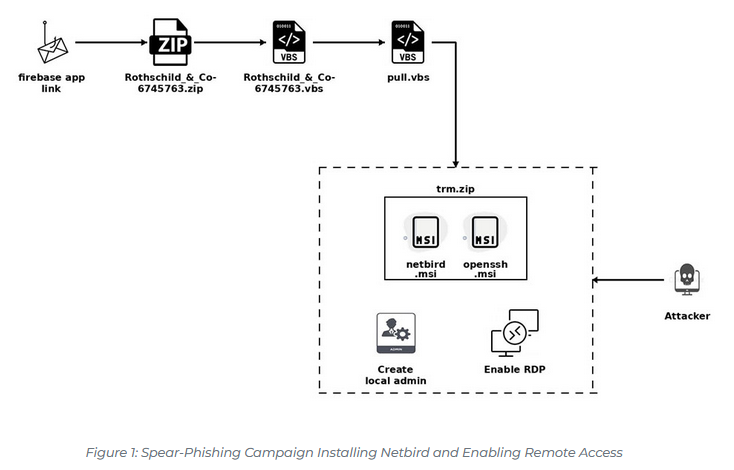
Phishing campaign targets CFOs: Security firm Trellix has spotted a spear-phishing campaign targeting the CFOs and finance executives of companies across the globe. The campaign started in mid-May and targeted companies in the banking, energy, insurance, and investment sectors. Threat actors seek to infect victims with a version of the NetBird remote access trojan.
Malicious PyPI packages: Checkmarx has spotted multiple malicious Python libraries uploaded to PyPI that pose as the famous Colorama package.
"Payloads allow persistent remote access to and remote control of desktops and servers, as well as harvesting and exfiltrating sensitive data. Windows payloads attempt to bypass antivirus/endpoint protection controls to avoid detection."
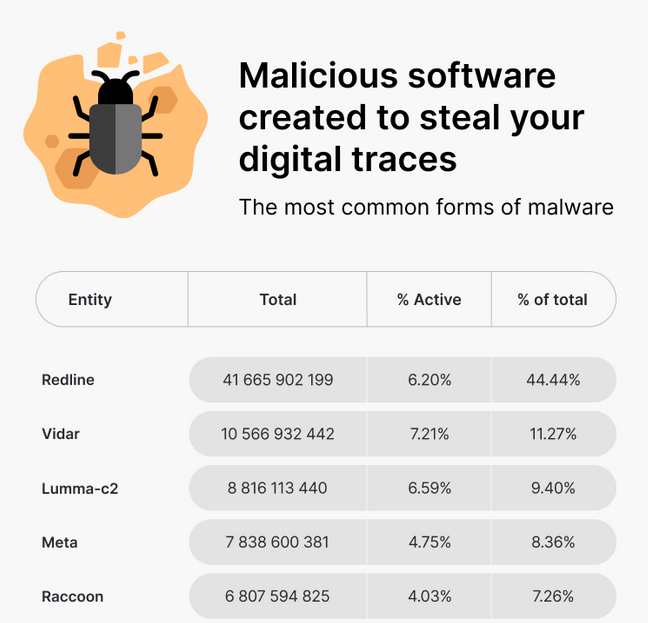
Stolen cookies statistics: According to a report from NordVPN, there are now 93.7 billion stolen cookies circulating or being sold on the dark web, with almost half coming from infections with the Redline Stealer.
PhaaS connections: Trustwave has found links between the Dadsec and Tycoon2FA phishing-as-a-service platforms.
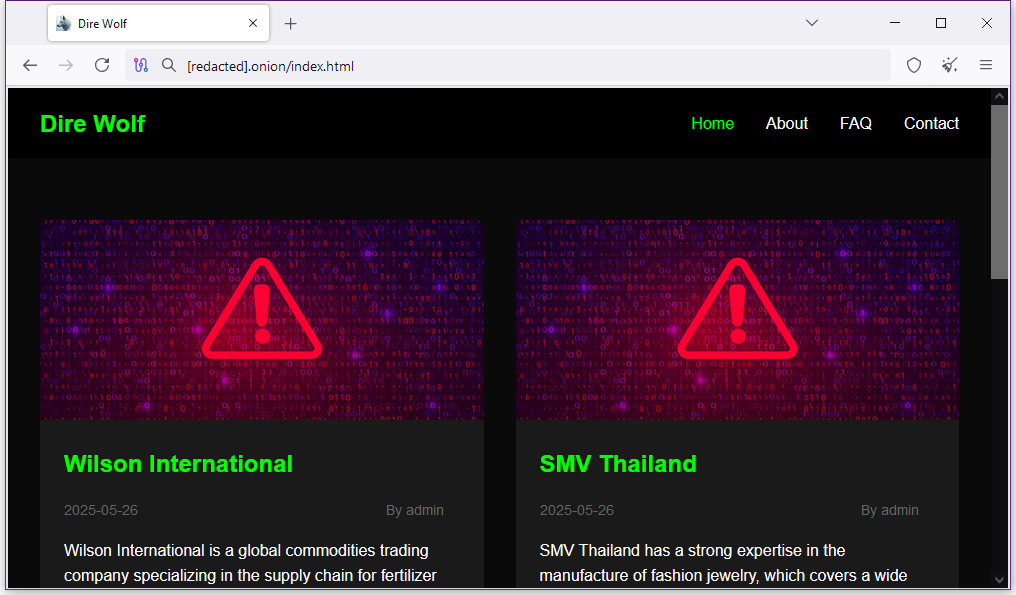
New Dire Wolf ransomware gang: A new ransomware operation named Dire Wolf launched this week. Its dark web leak site currently lists four victims.
Malware technical reports
Zanubis: Kaspersky has published a report looking at the evolution of the Zanubis Android banking trojan, which was first spotted back in 2022.
PureHVNC RAT: Netskope has spotted new campaigns delivering the PureHVNC RAT. The infections involve fake job offers from multiple brands.
EDDIESTEALER: No newsletter edition without an infostealer report. This one on EDDIESTEALER, a new Rust-based stealer spotted by Elastic in some ClickFix campaigns.
Lyrix ransomware: CyFirma looks at Lyrix, a new Python-based ransomware strain spotted in the wild.
PumaBot: Darktrace has identified a Go-based Linux botnet named PumaBot that is targeting embedded Linux IoT devices via SSH brute-force attacks.
AyySSHush botnet: More than 9,000 ASUS routers have been infected by a new botnet named AyySSSHush. The botnet has been active since March and appears to be another branch of a honeypot botnet that Sekoia calls VisciousTrap. GreyNoise believes the botnet may be the work of an APT group. A smaller number of Cisco, D-Link, and Linksys devices have also been infected.
Sponsor section
Gain essential visibility into evolving email threats, targeted industry attacks, and sophisticated evasion techniques observed across Q1 2025. Get the "Sublime Email Threat Research Report: Emerging trends & key insights" report here.
APTs, cyber-espionage, and info-ops
Reports on Western APTs decline: Academics have noticed a decline in the number of reports on the activity of Western APTs.
"The findings point to a transition from an earlier 'Age of Innocence' driven by business motives to a decision-making process that is increasingly influenced by geopolitical considerations. This shift introduces systematic biases into the threat reporting landscape, involving political distortions that impact the broader comprehension of cyber conflict dynamics."
Bitter APT: Indian APT group Bitter has been observed targeting the Pakistan Telecommunication Company (PTCL) in the aftermath of Operation Sindoor.
Belarus state-media disinformation: DFRLab has spotted Belarus state media using TikTok, YouTube, X, and Facebook to push pro-Kremlin propaganda and disinformation in advance of the upcoming Polish elections.
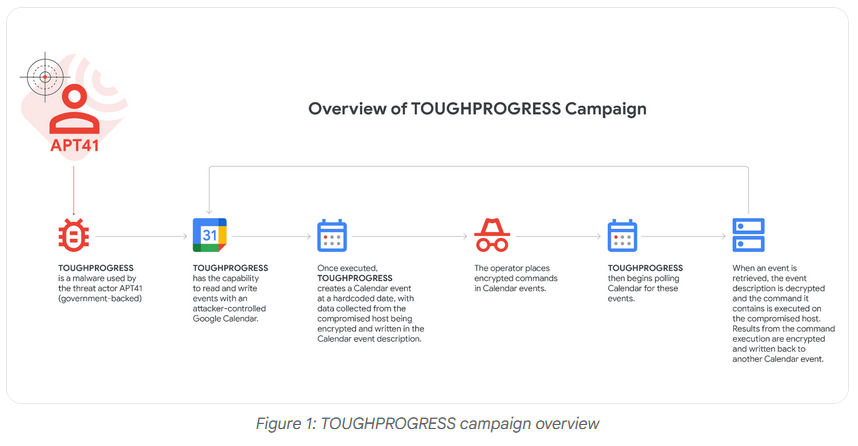
APT41 uses Google Calendar as C2: The Google Cloud security team has spotted Chinese cyber-espionage group APT41 deploy the TOUGHPROGRESS malware in recent attacks, a backdoor that uses Google Calendar as a command-and-control channel.
Vulnerabilities, security research, and bug bounty
Qingyuan Polytechnic profile: Natto Thoughts has published a profile on Qingyuan Polytechnic, a small vocational college in China's Guangdong region, which has become a powerhouse in training Chinese teens to become vulnerability researchers.
IBM Tivoli RCE: IBM has patched a remote code execution in its Tivoli Monitoring platform. The issue was found by Kaspersky and received a severity score of 9.8. [h/t cR0w]
Apache Commons security update: The Apache Foundation has released a security update for the Apache Commons BeanUtils component.
Cisco IOS XE write-up: Horizon3 has published a technical analysis of CVE-2025-20188, a pre-auth arbitrary file upload vulnerability found in Cisco IOS XE Wireless Controller Software. This one has a CVSS score of 10 and is likely to get exploited.
Rockwell vuln write-up: Rockwell Automation power monitoring devices are vulnerable to denial of service and remote code execution attacks that can disrupt industrial activity. Attacks can take down affected devices and open factory grids to surges or other types of electrical failures. The vulnerabilities have been patched last December, but many devices are likely still vulnerable today. [Detailed write-up via Claroty]
Safari BitM attack: According to SquareX, Safari is vulnerable to Browser-in-the-Middle (BitM) attacks. This attack puts the browser window in fullscreen mode and reproduces the browser UI inside the fullscreen page to trick the user into thinking they're interacting with the real page. Users are then tricked into performing malicious actions.
OneDrive file picker vulnerability: A vulnerability in the official OneDrive file picker component can be abused to access a user's entire OneDrive account rather than just the selected files. The bug exists due to the lack of fine-grained OAuth scopes for the OneDrive service. Security firm Oasis discovered and reported the bug to Microsoft, which promised future improvements to OneDrive and the affected component. Apps like Slack, Trello, and ChatGPT use the component.
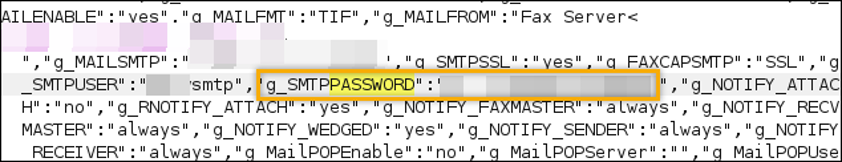
MICI declines to patch fax server RCE: Taiwanese company MICI Networks has declined to patch three vulnerabilities in its NetFax server product. The three vulnerabilities can be chained for remote code execution attacks on the device. Authentication is required for a successful exploit, but Rapid7 researchers say the server leaks default credentials in cleartext, and this is not a barrier to attackers.
Infosec industry
Threat/trend reports: BforeAI, Cyolo, Forescout, Gen Digital, Guidepoint Security, IANS, and UK Finance have recently published reports and summaries covering various infosec trends and industry threats.
BlueHat India 2025 videos: Talks from the BlueHat India 2025 security conference, which took place last earlier this month, are available on YouTube.
Acquisition news #1: Cybersecurity firm Zscaler has acquired MDR provider Red Canary.
Acquisition news #2: American defense corp Leidos will acquire Kudu Dynamics to boost its AI and cybersecurity capabilities.
SentinelOne outage: SentinelOne has had a major outage of its customer console. This is nowhere near as big as the CrowdStrike outage.
Risky Business podcasts
In this edition of Seriously Risky Business, Tom Uren and Patrick Gray talk about Russian DanaBot malware developers making a tailored variant of their malware specifically for espionage. This fills in some of the blanks on the exact relationship between Russian criminals and the country's intelligence services.
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about cyber's 'hard problems' and why they are intractable.
