Risky Bulletin Newsletter
July 30, 2025
Risky Bulletin: US seizes Chaos ransomware funds
Written by

News Editor
This newsletter is brought to you by vulnerability management and analysis platform Nucleus Security. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
The FBI has seized around $2.4 million worth of Bitcoin from the relatively new Chaos ransomware group.
According to the US Justice Department, the funds were seized back in April, but only now announced. The funds were taken from a crypto-wallet owned by a Chaos member going by the name of Hors.
This seizure is interesting for one very particular reason—namely, that the Chaos ransomware is a new group. We have rarely seen the FBI crack down and go after a group within months of its launch.
According to a recent Cisco Talos report, the Chaos group barely began operations in February before their wallet was seized two months later.
The group is what I call a tentacle. It goes back years and years to now-ancient ransomware operations. In Chaos' case, the gang has its roots in the old Ryuk gang.
Chaos was formed by members who left the BlackSuit ransomware group, which, in turn, was formed by members of the Royal group, which itself was formed by former Conti operators, with Conti being a rebrand of the original Ryuk gang.
Sure, Chaos members may have no connections to old Ryuk members, but they benefit from so-called "institutional knowledge" of running a RaaS (Ransomware-as-a-Service) and carrying out successful ransomware and extortion attacks.
News of the Chaos wallet seizure comes days after US authorities seized the infrastructure of the BlackSuit ransomware, which also kinda tells me authorities had enough clues to track some of the BlackSuit members to the new RaaS platforms they fled. Let's hope more BlackSuit members failed their OpSec and left enough clues around to have their funds seized as well.

Risky Business Podcasts
The main Risky Business podcast is now on YouTube with video versions of our recent episodes. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
Aeroflot cancels flights after hack: Russia's national airline Aeroflot canceled more than 100 flights after a cyberattack. The flight cancellations impacted international and domestic flights landing or taking off from Moscow's main airport. Two hacktivist groups hacked Aeroflot's network and wiped thousands of servers. The Cyber Partisans and Silent Crow took credit for the intrusion. They allegedly wiped systems by rewriting files with anti-Putin insults. The groups also mocked Aeroflot for still using Windows XP and employees for storing passwords in text files. [Additional coverage in The Moscow Times]

A major cyber incident in Russia: two groups, Cyber Partisans & Silent Crow, took credit for a cyber attack on Aeroflot, claiming they destroyed its internal IT systems. Aeroflot didn't acknowledge the attack but canceled nearly 100 flights & delayed some more due to an 'outage'
— Oleg Shakirov (@shakirov2036.bsky.social) 2025-07-28T12:51:27.485Z
After 'Aeroflot' collapse:
— Kate from Kharkiv (@kateinkharkiv.bsky.social) 2025-07-28T14:46:39.418Z
Orange discloses breach: Hackers breached French telecom giant Orange last week, on Friday. The hack disrupted some services to the company's clients in France. Orange is planning to restore the affected services by Wednesday, July 30. The company has notified authorities and says its security teams are working to investigate the incident.
Disruptions in Luxembourg after postal service attack: A cyberattack has disrupted flights, emergency services, internet, and phone access in Luxembourg. The incident took out several services at Post Luxembourg, a state-owned telecommunication and postal service. The company says hackers exploited a vulnerability in a software component and caused a large-scale malfunction across its services. Forty flights were delayed after airline staff had to manually check luggage after airport systems went down. Residents had to visit fire and police stations to request aid. Home and work internet and phone connectivity were out for hours on Friday. [Additional coverage in Luxembourg Times]
Endgame Gear malware incident: The configuration tool for a popular gaming mouse infected users with malware for almost two weeks. A version of the XRed malware was found in the mouse configuration tool for the OP1w 4k v2 mouse model from German company Endgame Gear. The malware was live in the configuration tool between June 26 and July 9. Endgame Gear learned of the compromise after reports on Reddit about antivirus alerts. [Additional coverage in PCMag]
Tea app breach also involved private messages: The Tea dating app has disabled its direct messaging feature in the aftermath of a recent security breach that exposed the personal details and real ID scans of thousands of users. The company says some private messages were also accessed during a hack that took place last week. The data from the hack was leaked on 4chan over the weekend. The hack was advertised as revenge for false and libelous claims made on the app about certain men. The Tea app went viral this month for allowing women to post anonymous reviews of men and their dates. [Additional coverage in CBS News]
SuperRare crypto-heist: Hackers have stolen around $730,000 worth of assets from crypto exchange SuperRare, per Cyvers and PeckShield.
RTE ransomware incident: Irish broadcaster RTE has fallen victim to a ransomware attack. A new ransomware group called Global took credit for the attack via a post on the dark web. The broadcaster says it's investigating the incident together with law enforcement. There was no disruption to the organization's live programming.
Albavision ransomware incident: The same group also took credit for an attack against Albavision, a major LATAM broadcaster based in Miami.
General tech and privacy
Data brokers ignore data deletion requests: Data brokers are in "rampant non-compliance" with new US state privacy laws. Companies are registering with state officials but are not following regulations. Data brokers are not honoring requests to opt out of tracking and delete existing user data. According to a new study from the University of California, Irvine, in 40% of cases, data brokers didn't even reply to user requests. [Additional coverage in CyberScoop and the UCI paper]
Android to let users disable Failed Authentication Lock: Google will soon let Android users disable a security feature that automatically locks devices after too many failed logins. The Failed Authentication Lock was added and turned on by default in Android 15, released last year. It was advertised as an anti-theft protection system. Many users have locked themselves out of their own devices after they forgot lockscreen PINs, passwords, and access patterns. [Additional coverage in Android Authority]
Government, politics, and policy
Senator asks Musk to cut Starlink access for scam compounds: A US Senator has urged SpaceX to block Starlink access to cyber scam compounds operating in Southeast Asia. Senator Maggie Hassan cited a 2024 UN report that found scam compounds relying on Starlink for internet connectivity. Cyber scam cartels migrated to Starlink after local authorities started cutting their fiber optic connections.
Minnesota activates National Guard after cyberattack: The US state of Minnesota has activated the National Guard to help the city of St. Paul deal with a cyberattack.
NSA top lawyer fired: The US government has fired the NSA's top lawyer, April Falcon Doss. Doss was fired just like her former boss, NSA Director Gen. Timothy Haugh—after complaints from right-wing conspiracy theory lunatics Laura Loomer and The Daily Wire. [Additional coverage in The New York Times]
Plankey nomination status: The US Senate Homeland Security Committee will hold a vote on Wednesday to decide if it will forward the nomination of Sean Plankey for CISA Director to the Senate floor. CISA will also be releasing a telco security report from 2022. Sen. Ron Wyden said he would put a hold on Plankey's nomination if CISA would not release the previously private report.
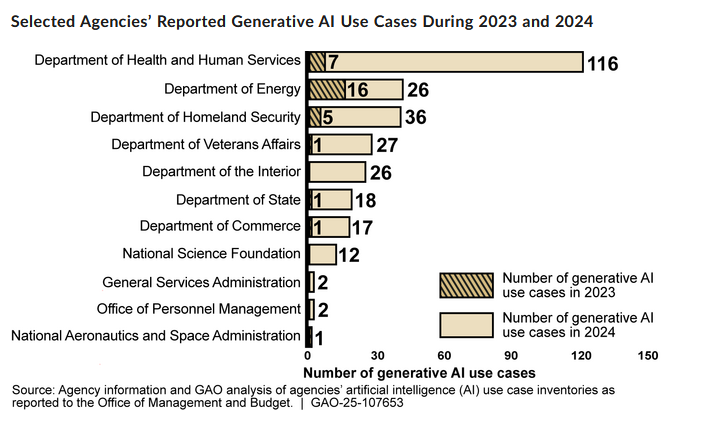
US AI govt usage doubles: A recent GAO report found that the use of generative AI in the US government has doubled from 2023 to 2024.
China proposes new global AI org: China wants to create a global organization to govern AI development as an alternative to US-led groups. At least 30 countries appear to be interested. [Additional coverage in Reuters]
EU age verification app criticized: Thousands of developers have shown their discontent on GitHub after the developers of the EU's upcoming age verification app wanted to use built-in Google and Apple APIs to help verify user device authenticity. The reasons vary from tech sovereignty to pigeon-holing the verification process to just two specific mobile operating systems.
Kyrgyzstan takes full control over internet access: The Kyrgyzstan government has nationalized access to the internet for one year. Through a presidential decree, the government was given full control of all internet infrastructure until August 14, next year. State-owned telecom company ElCat will become the sole supplier of international internet access in the country. Other telecoms will have to route traffic through ElCat and block access to sites according to government orders. As its first move, Kyrgyzstan has blocked access to online pornography. [Additional coverage in Barron's]
UK government ponders a VPN ban: You probably know by now that the UK government introduced age verification requirements last week for users accessing the internet, and especially for sites hosting adult content or other sensitive materials. VPN usage surged over the past week in the UK, so the UK government is now looking at banning VPN apps. [Additional coverage in BirminghamLive]
Classic! Our stupid idea has caused a very foreseeable consequence; let's propose ANOTHER possibly stupider idea to deal with that🙃
— Sarah (@sarahskeeter.bsky.social) 2025-07-29T14:00:41.708Z
Emphatically agree - the public haven't heard of the new rules, but they like the sound of banning things
— Will (@will-rich.bsky.social) 2025-07-29T08:09:23.486Z
Sponsor section
In this Risky Business sponsor interview, Nucleus Security co-founder and COO, Scott Kuffer, joins Casey Ellis to chat about how vulnerability management evolved into quite a lot more than just patch prioritization.
Arrests, cybercrime, and threat intel
Kazakhstan arrests ransomware suspect: Kazakhstan authorities have arrested a suspect for ransomware attacks. The suspect was identified as a man from the city of Almaty. He is accused of hacking the servers of foreign companies, encrypting data, and requesting a ransom. Officials didn't specify which country issued the arrest warrant. [h/t Ilya S.]
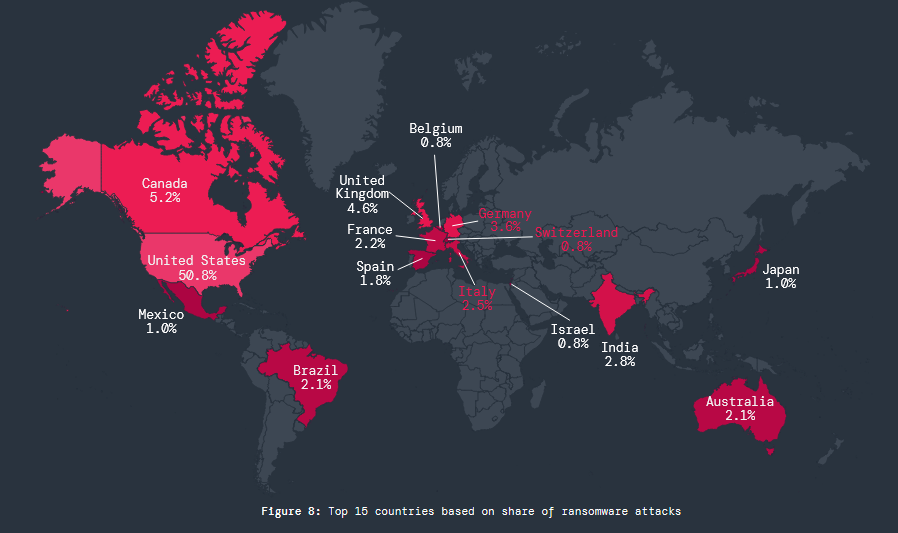
Port cybersecurity brief: NATO's cyber defense center has published an overview of the cybersecurity of maritime ports, which are key hubs in the alliance's logistics, troop, and weapons movements. [Additional coverage in Industrial Cyber/Report PDF]
"Maritime ports handle 80% of global trade and serve as critical nodes in NATO's defence logistics network, yet they face unprecedented cybersecurity threats from state-linked actors. Recent intelligence shows a high frequency of cyber attacks affecting port facilities across Europe and the Mediterranean, with a significant proportion of these attacks traced back to threat actors originating from Russia, Iran, and China. This trend highlights the pressing need for coordinated policy and security responses."
Scattered Spider profile: The NCC Group [PDF] and several law enforcement agencies have published profiles on Scattered Spider and their recent TTPs.
Trickbot's crucial role in ransomware operations: Akamai says that ransomware groups that relied on TrickBot for initial access into targeted networks managed to extort $726 million from victims since 2016.
Qwins bulletproof hoster: Threat intel analyst Vasilis Orlof has published a profile of Qwins Ltd, a UK-registered company that appears to be hosting a ton of malware campaigns on its IP space.
A7A5 money laundering: Blockchain security firm Elliptic looks at A7A5, a newly established crypto token that was linked to sanctioned Moldovan-Russian oligarch Ilan Sor. Per Elliptic, the token is now moving roughly $1 billion per day in dark money. [h/t Anca R.]
NEW: Do you want to know how a businessman wanted for a billion-dollar fraud in Moldova, accused of enabling Russian political influence and working with a Russian state-owned military bank is linked to a new cryptocurrency in Kyrgyzstan? Then I've got the OSINT investigation for you 1/
— Elise Thomas (@elisethomas.bsky.social) 2025-06-25T06:00:49.083Z
A7A5's project director Leonid Shumakov has publicly stated that the reason for registering A7A5 in Kyrgyzstan rather than in Russia is because it is a "friendly jurisdiction that is not so subject to sanctions."
— Elise Thomas (@elisethomas.bsky.social) 2025-06-25T06:10:22.977Z
PyPI phishing campaign: The Python Software Foundation warns of a phishing campaign targeting PyPI users. The phishing domain is pypj[.]org, an obvious mispelling of pypi[.]org.
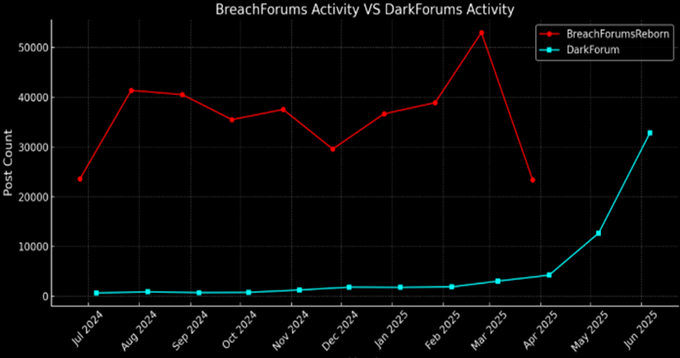
DarkForums replaces BreachForums: DarkForums has replaced BreachForums as the go-to place for the trade of hacked data. According to threat intel firm KELA, the forum saw a 600% rise in activity after law enforcement took down BreachForums in April. DarkForums launched in 2022 and was initially managed by members of the D4rk4rmy hacking group.
Malware technical reports
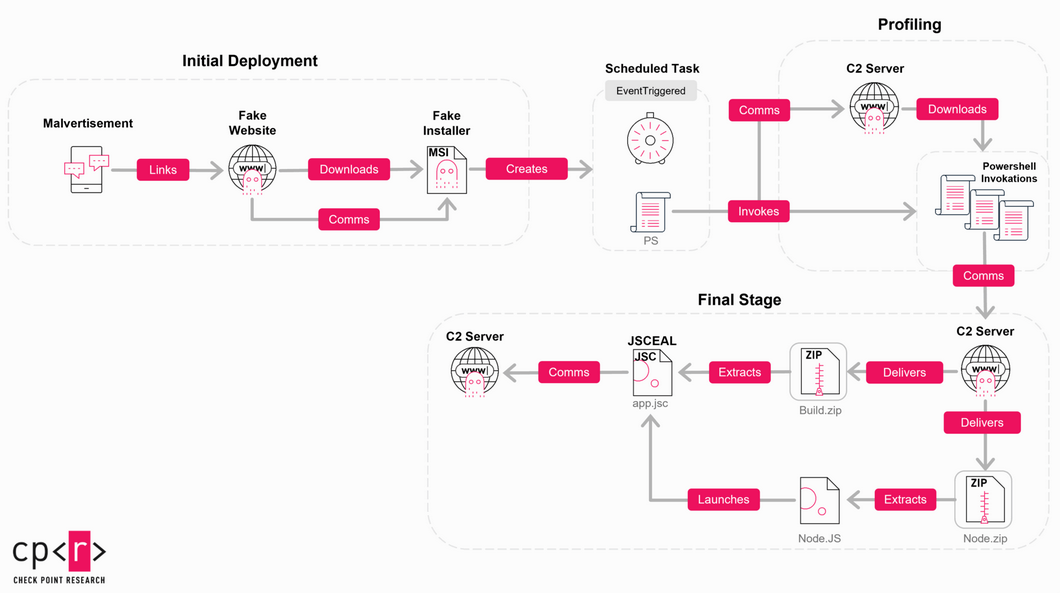
New JSCEAL malware: A threat actor is using a new malware strain named JSCEAL to target the cryptocurrency community. The malware is hidden inside malicious copies of more than 50 popular cryptocurrency trading apps. Users are lured to the apps using malicious social media ads. Once infected, the JSCEAL malware can steal sensitive credentials, log keystrokes, and manipulate crypto-wallets.
Auto-Color backdoor: Threat actors are exploiting SAP NetWeaver servers to deploy the Auto-Color backdoor.
XWorm V6: Netskope has spotted a new version of the XWorm malware—namely V6. The new version introduced new features such as process protection and better anti-analysis capabilities.
0bj3ctivityStealer: We're continuing our tradition of not having a newsletter edition without an infostealer report. This time, it's 0bj3ctivityStealer, courtesy of the Trellix team.
ToxicPanda Android malware: Per Bitsight, the ToxicPanda banking trojan has recently infected over 4,500 Android devices, with most located in Europe after a shift to the region from Southeast Asia last year.
Gunra ransomware Linux variant: The Gunra ransomware now has a Linux variant, spotted by Trend Micro in recent intrusions.
FunkSec ransomware decrypter: Avast has released a free decrypter for the FunkSec ransomware. The ransomware was first spotted in December. It listed over 100 victims on its leak site before going inactive in March. Avast believes FunkSec was created with the help of AI coding tools.
Sponsor section
July 30 Webinar: Why 71% say reducing risk is hard – and how agentic AI can help. Register now.

APTs, cyber-espionage, and info-ops
UNC3886 profile: Trend Micro has published a profile of UNC3886, an APT that recently breached several critical infrastructure operators in Singapore. This intrusion campaign appears to have heavily relied on VMware vCenter and ESXi hacking. Sygnia has a profile on the same APT. The group also has a history of targeting Fortinet and Juniper devices as well.
Kimsuky ClickFix campaign: South Korean security firm Genians has published a report on a Kimsuky campaign that used the ClickFix tactic to infect victims with malware—in this case, the BabyShark backdoor.
Vulnerabilities, security research, and bug bounty
Google P0 changes reporting rules: Google's security team has updated its vulnerability reporting rules. The Project Zero team says it will publicly disclose the names of vendors and software a week after they report a security flaw. The team also plans to share the date when the bug report expires, and details will be made public. Google says the new rules are to help close the patch gap. Downstream vendors are expected to prepare for incoming security patches and incorporate them faster.
Train maker sues security researchers: Polish train maker Newag is suing a local security research group and a repair company. Newag claims the two infringed on its copyright when they bypassed software locks to fix the firmware of trains sold to Polish railway companies. The Dragon Sector security group found in 2023 that Newag included firmware code that bricked trains if they were fixed by unauthorized repair shops or traveled a certain distance without repairs. Newag is now seeking €1.37 million in reputational damages over the unauthorized repairs and claims it intentionally bricked its product. [Additional coverage in Rolling Stock World] [h/t Andrzej LM]
Apple security updates: Apple has released security updates for its main operating systems on Tuesday. No zero-days were included/disclosed.
KEV update: CISA has updated its KEV database with three vulnerabilities that are currently exploited in the wild. This includes two recent Cisco ISE vulnerabilities and a 2023 PaperCut CSRF.
SonicWall patches pre-auth SMA bugs: SonicWall has patched three vulnerabilities in its SMA appliances. The bugs can allow threat actors to run crash or run malicious code on customer devices before the authentication process. Two of the bugs require no user interaction. All three issues were discovered by WatchTowr Labs, and a detailed write-up is available.
Xorux vulnerabilities: Xorux has released security patches to patch three vulnerabilities in its LPAR2RRD IT monitoring solution [1, 2, 3] and two vulnerabilities in the XorMon-NG firewall [1, 2].
Adobe Experience Manager Forms vulns: Searchlight Cyber's Assetnote team has published a technical write-up on three bugs they found and helped patch in the Adobe Experience Manager Forms component back in April.
Sploitlight macOS TCC vulnerability: Microsoft's security team has disclosed another vulnerability in Apple's macOS Transparency, Consent, and Control (TCC) framework. Tracked as CVE-2025-31199, the vulnerability allows malicious apps to bypass the TCC and access a user's sensitive macOS data. The vulnerability exploits overprivileged plugins for the macOS Spotlight search engine. Apple patched the bug, codenamed Sploitlight, in March.
Base44 AI platform vulnerability: Google's Wiz division has uncovered a vulnerability in the Base44 AI vibe coding platform that could have allowed malicious users access to other people's private apps. The kink? Wiz discovered the bug in July, a month after it acquired Base44.
Gemini AI CLI hijack: Tracebit researchers have discovered a vulnerability in the Google Gemini CLI client that could have allowed attackers to run malicious code on developer systems.
"[T]hrough a toxic combination of improper validation, prompt injection and misleading UX, inspecting untrusted code consistently leads to silent execution of malicious commands."
Sex toy leaks user emails: The Lovense sex toy app leaks a user's email address. Attackers only need a user's profile name to retrieve the email via the app's built-in XMPP server. A separate issue also allowed attackers to generate an auth token with only the user's email. Lovense patched the takeover bug after a researcher named BobDaHacker disclosed the issue in a blog post. The email disclosure is still unpatched.
Infosec industry
Threat/trend reports: Akamai, Bitsight, Google Cloud, Lab 1, Positive Technologies, RSAC, Sysdig, Transmit Security, and Zscaler [PDF] have recently published reports and summaries covering various infosec trends and industry threats.
Haugh joins VC space: Former NSA Director and CyberCom Commander Gen. Timothy Haugh has joined cybersecurity venture capital firm Ballistic Ventures as a Strategic Advisor.
Abuse.ch gets a commercial feed: Abuse.ch is partnering with Spamhaus to provide a commercial version of its feed to organizations currently not contributing to its open-source service.
New tool—Penguin: A team of academics from the US has released Penguin, a tool for (re)hosting firmware in interactive virtual environments for monitoring and security research.
New tool—EXEfromCER: Jean-Luc Dupont released EXEfromCER, a proof of concept to deliver a binary payload via an X.509 TLS certificate.
New tool—MistWalker: A security researcher going by Hybryx has released MistWalker, a tool to acquire Entra ID access tokens from Microsoft 365 environments.
PETS 2025 videos: Talks from the Privacy Enhancing Technologies Symposium, which took place earlier this month, are available on YouTube.
Risky Business podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq discuss whether China's 'cyber militia' makes sense and what they could be good for.
