Risky Bulletin Newsletter
January 16, 2025
Risky Bulletin: UK proposes ransomware payment ban for public bodies
Written by

News Editor
You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
Risky Business Podcasts
Risky Business is now on YouTube with video versions of our main podcasts. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
Five hacks linked to the DPRK: The US, South Korea, and Japan have linked five 2024 crypto-heists to North Korean hackers. This includes DMM Bitcoin ($308mil), WazirX ($235mil), Upbit ($50mil), Radiant Capital ($50mil), and Rain Management ($16mil).
Synnovius attack fallout: The UK NHS says that a ransomware attack on lab service provider Synnovis last year has had an impact on the health of several patients, including permanent long-term damage in at least two cases. [Additional coverage in Bloomberg]
Fico blames Ukraine for cyberattack: Slovakia's PM Robert Fico has blamed Ukraine for a ransomware attack that crippled its cadastre agency earlier this year. As local media puts it, Fico, who is a known Putin fanboy and a pro-Kremlin propaganda mouthpiece, has cited no evidence.
Luxembourg DDoS attacks: Pro-Kremlin "hacktivists" have launched a series of DDoS attacks against Luxembourg government websites. [Additional coverage in the Luxembourg Times]
PoE2 hacks: A threat actor has hacked the admin account of the Path of Exile 2 game, reset user passwords, and stole valuable in-game items from dozens of user accounts. [Additional coverage in 404 Media]
CFIUS hack: Silk Typhoon, the Chinese hacking group that breached the US Treasury OFAC bureau, also breached the Committee on Foreign Investment in the US (CFIUS), the US government office that reviews foreign investments for national security risks. [Additional coverage in CNN]
Roseltorg hack: Pro-Ukrainian hackers have breached Roseltorg, Russia's main electronic trading platform for government and corporate procurement. [Additional coverage in The Record]
Orange Finance crypto-heist: Cryptocurrency platform Orange Finance has lost $830,000 worth of assets after a leak of one of its private keys.
STIIIZY data breach: Cannabis store STIIIZY has disclosed a data breach. The incident took place in November last year via a vendor of point-of-sale processing services.
Unacast breach: Location data tracking company Unacast has confirmed a security breach of its Gravy Analytics service. [Additional coverage in NRK]
Nominet breach: British domain registrar Nominet has disclosed a security breach. The incident appears to be linked to a recent wave of attacks against Ivanti VPN devices. [Additional coverage in TechCrunch]
Scholastic breach: A threat actor has allegedly hacked and stolen the data of 8 million customers from book publishing company Scholastic. [Additional coverage in The Daily Dot]
Telefonica breach: Spanish telco Telefonica has confirmed that data from an internal ticketing system was leaked online.
General tech and privacy
Microsoft to force-install new Outlook client: Microsoft will force-install a new Outlook email client on both Windows 10 and Windows 11 on February 11 and January 28, respectively.
"Currently, there isn't a way to block the new Outlook from being installed - if you prefer not to have new Outlook show up on your organization's devices, you can remove it after it's installed as part of the update."
Texas sues Allstate over privacy: The Texas OAG has sued insurance company Allstate for "unlawfully collecting, using, and selling data about the location and movement of Texans' cell phones through secretly embedded software in mobile apps."
VKontakte passes YouTube: After Russian officials throttled YouTube traffic, VKontakte has finally passed YouTube in Russian traffic rankings for the first time. [Additional coverage in RBC]
DJI gives the middle finger to US: Facing an impeding ban in the US, Chinese drone maker DJI has removed firmware restrictions preventing its drones from entering no-fly zones.
Meta blocks competitor: After going full-MAGA last week, Meta is now blocking links to Pixelfed, an Instagram competitor. How very non-anticompetitive and non-monopoly.
Meta to stop penalizing misinformation: Meta has taken down a system that can identify viral hoaxes on its platform and has updated its algorithms to stop penalizing misinformation. [Additional coverage in Platformer]
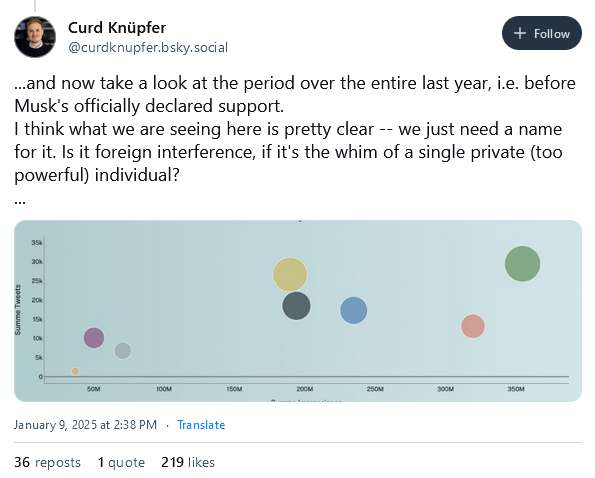
Musk meddles in another election: After Elon Musk showed public support for German far-right party AfD, the visibility of AfD tweets on Twitter exploded, while all other German parties fell into oblivion. This mirrors similar pattern observed ahead of the US presidential election, where tweets from Republicans had views stats in the billions while tweets from Democrats were in the low millions.
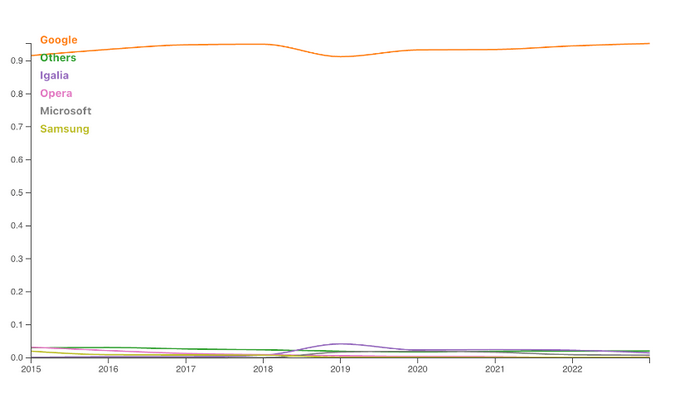
Google still dominates Chromium work: According to a Google blog post, its engineers still account for roughly 94% of all code commits to the Chromium open-source web browser project. In the meantime, the Linux Foundation has announced an initiative to support open-source projects that adopt the browser.
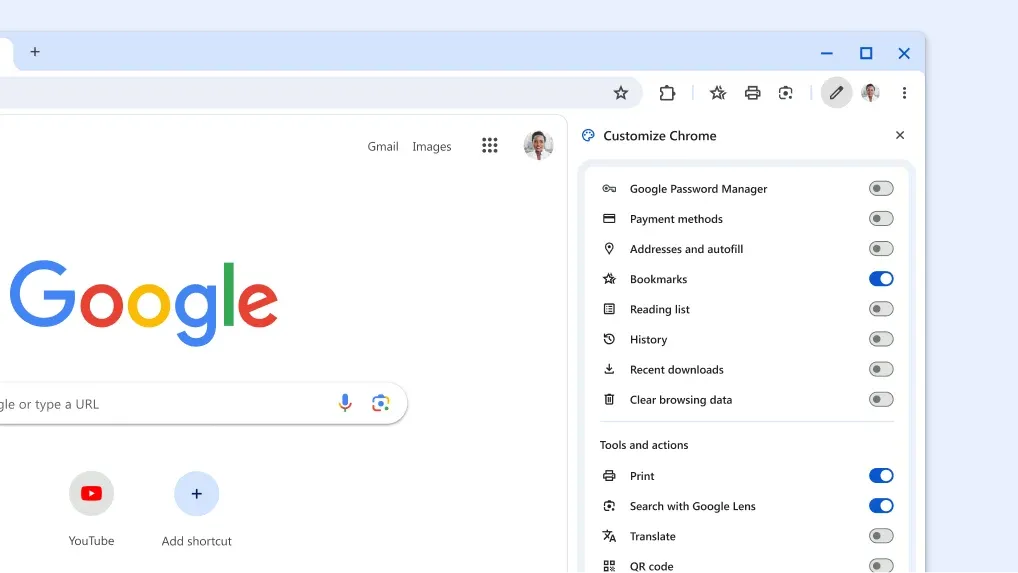
Chrome 132: Google has released version 132 of its Chrome browser. See here for security patches and webdev-related changes. The biggest changes in this release include a new way to edit the Chrome toolbar, the ability to share Chrome passwords via a QR code, and a security update that sandboxes Chrome's Network Service on Windows.
Government, politics, and policy
New RuNet disconnection test: Russian officials have carried out a new test to disconnect the Russian RuNet from the main internet.
UN spyware meeting: The UN Security Council held its first-ever meeting on the proliferation and misuse of commercial spyware.
UK proposes ransomware ban: The UK government has put forward a proposal to ban public government bodies from making ransomware payments. The ban is an expansion of the current ban on payments by government agencies and will apply to schools, hospitals, local councils, and critical infrastructure operators.
US mulling Salt Typhoon response: The US government is looking into what kind of response or sanctions it should take against a private Chinese company it believes is behind the Salt Typhoon APT and the attacks against US telcos. [Additional coverage in WaPo]
New chip export controls: The White House has introduced new export control rules for AI models and chips as part of its economic war with China. [Additional coverage in CyberScoop]
IMSI catcher at DNC convention: WIRED reports that an IMSI catcher device was discovered at the 2024 DNC convention in Chicago last year.
"Initial tests conducted during the DNC revealed no conclusive evidence of cell-site simulator activity. However, months later, EFF technologists reanalyzed the raw data using improved detection methods."
CISA AI playbook: CISA has published a playbook for how companies should work together to deal with AI-related cybersecurity incidents and vulnerabilities.
CISA performance report: CISA claimed it recorded progress across its efforts to decrease critical infrastructure organizations' exposure to actively exploited CVEs and cut remediation times, according to its annual performance report. [Additional coverage in CybersecurityDive]
Risky Business Podcasts
Brian A. Coleman, Senior Director for Insider Risk, Information Security, and Digital Forensics at Pfizer, talks to us about how his security team is experimenting with AI to improve their insider risk detection systems. The system Brian and his team put together can detect sensitive information or documents handled by unauthorized accounts, but can also spot documents moving around and ending up where they shouldn't be - either by accident, malice, or as a result of a security breach.
Arrests, cybercrime, and threat intel
PlugX takedown: The DOJ has confirmed that the FBI used Sekoia's data and control over a PlugX command-and-control server to disinfect systems across the US after a similar operation took place in France with the help of French law enforcement. Sekoia has volunteered to help law enforcement take down the botnet and it's nice to see that some people took them on their offer.
Base station smishers detained in Thailand: Thai officials have detained two Chinese nationals for driving around Bangkok, posing as tour guides, and using a base station to blast SMS spam to nearby phones. This is the second group caught doing this after initial arrests this past November. [Additional coverage in Khaosod]
Deepfake group detained: Hong Kong officials have detained a group of 31 suspects for allegedly using deepfake technology to defraud victims across Southeast Asia via romance and investment scams. [Additional coverage in The Star]
Blender/Sinbad admins charged: The US Justice Department has charged three Russian nationals for operating the Blender and Sinbad cryptocurrency mixing services.
Barcelona's spyware hub: After a first Haaretz report last month, TechCrunch also looks at how Barcelona has become a hub for spyware companies over the past year.
CrowdStrike alert: Security firm CrowdStrike says it detected a phishing campaign using its name to lure victims into infecting themselves with a cryptominer.
Chinese malware network: DomainTools' security team has published a report covering a threat actor involved in the delivery of malware to Chinese-speaking audiences.
IntelBroker profile: Threat intel company KELA has published a profile on IntelBroker, a notorious data broker active on the BreachForums underground data trading hub.
BIScience profile: Security researcher Wladimir Palant has published a profile on BIScience, a "data broker that owns multiple extensions in the Chrome Web Store (CWS) that collect clickstream data under false pretenses."
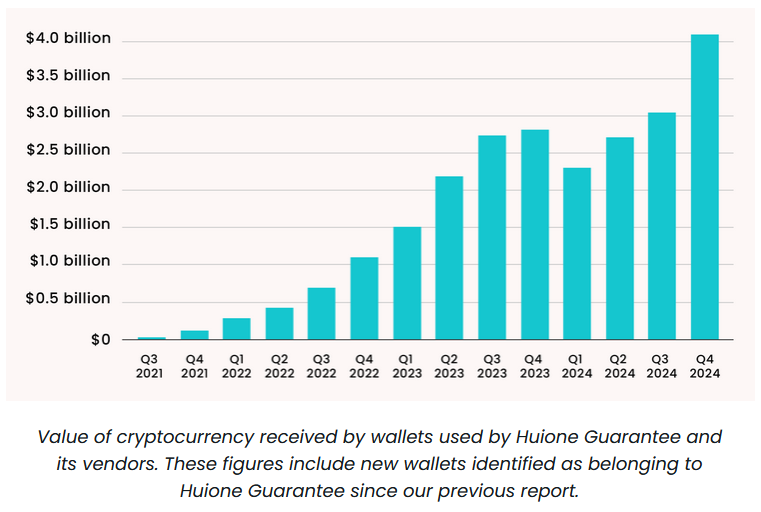
Huione Guarantee: Elliptic has published a profile on Huione Guarantee, a Telegram-based marketplace serving fraudsters and online scam compounds across Southeast Asia.
Fasthttp abuse: Security firm SpearTip has detected threat actors abusing the Fasthttp library to carry out and manage brute-force attacks on Microsoft 365 infrastructure.
Codefinger: A threat actor tracked as Codefinger is breaking into AWS S3 buckets and encrypting user data as part of a wide-ranging data extortion campaign against companies running unsecured infrastructure.
FunkSec: Check Point has published a report on FunkSec, a ransomware group that launched in late 2024 and has already listed over 85 victims on its leak site.
Malware technical reports
WP3.XYZ: Security firm c/side has published an analysis of WP3.XYZ, a piece of JS malware they found deployed on over 5,000 WordPress sites.
AIRASHI: QiAnXin has published a report on AIRASHI, a huge DDOS botnet that was used to attack Steam during the launch of the Black Myth Wukong video game last year.
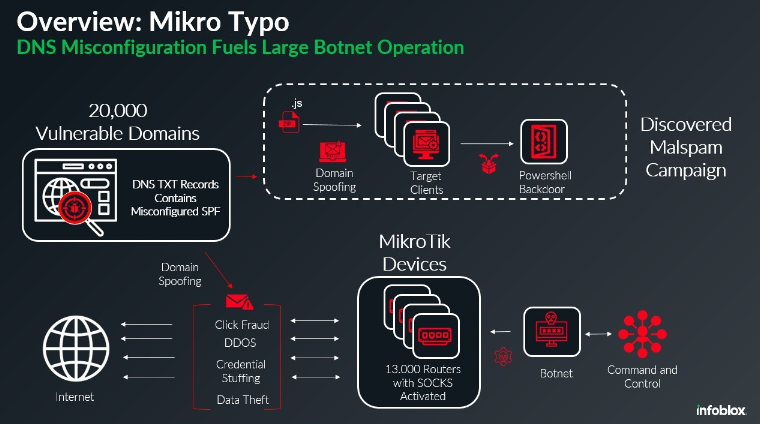
Mikro Typo: Infoblox has discovered a botnet named Mikro Typo comprised of over 13,000 compromised MikroTik devices and 20,000 domains involved in sending spoofed emails.
Risky Business Podcasts
In this podcast, Tom Uren and Adam Boileau talk about the continued importance of hack and leak operations. They didn't really affect the recent US presidential election, but they are still a powerful tool for vested interests to influence public policy.
APTs, cyber-espionage, and info-ops
APT28/UAC-0063: Sekoia looks at an APT campaign targeting Central Asia, including Kazakhstan, and its diplomatic and economic relations with Asian and Western countries.
"We assess it is possible that this campaign was conducted by a Russia-nexus intrusion set, UAC-0063, sharing overlaps with APT28."
Sticky Werewolf: Russian security firm FACCT says it discovered new Sticky Werewolf campaigns targeting Russian entities. The company previously linked the group to Ukraine.
NICKEL TAPESTRY: SecureWorks has linked some of the North Korean IT worker groups to known artifacts of an APT it tracks as NICKEL TAPESTRY.
RedCurl: Huntress has published new details and IOCs from a RedCurl APT campaign that targeted Canada over the past two years.
Reward for Flax Typhoon-linked company: The US State Department has put up a $10 million reward for additional information on Beijing-based cybersecurity company Integrity Technology Group. US officials claim the company is behind the Flax Typhoon APT group.
Pro-Kremlin disinformation: Researchers have found pro-Kremlin disinformation campaigns targeting Croatia ahead of its presidential election. The pro-Kremlin candidate won. There's also another Russian disinfo group targeting Poland's upcoming election. EU officials believe more elections will likely be canceled in the future because of foreign meddling and disinformation campaigns.
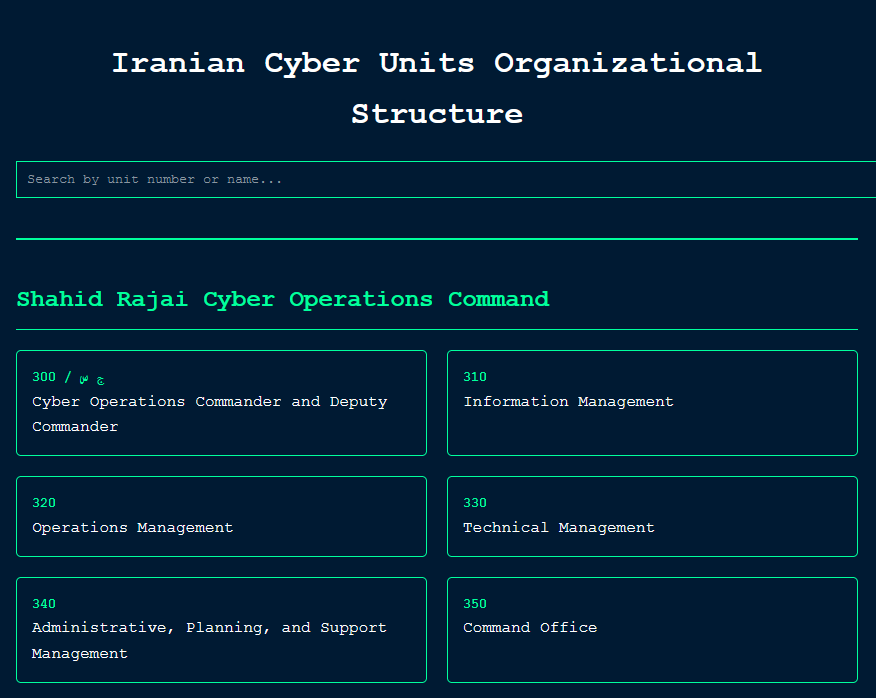
Iranian Cyber Units Organizational Structure: Iranian threat intel analyst Nariman Gharib has published a chart detailing the structure of Iran's cyber and cyber-electronics units.
Vulnerabilities, security research, and bug bounty
Patch Tuesday: Yesterday was the January 2025 Patch Tuesday. We had security updates from Adobe, Microsoft, Chrome, SAP, Ivanti, Fortinet, Cisco, Juniper, Supermicro, NVIDIA, Schneider Electric, Siemens, Moxa, Zyxel, Zoom, Rsync, and Veeam. The Android Project, Firefox, Kubernetes, Splunk, SonicWall, ASUS, SimpleHelp, and GitLab released security updates last week as well.
Microsoft Patch Tuesday: This month, Microsoft patched 159 vulnerabilities, including three actively exploited zero-days.
- CVE-2025-21333, CVE-2025-21334, CVE-2025-21335 - All three are described as a Windows Hyper-V NT Kernel Integration VSP elevation of privilege vulnerability.
Fortinet zero-day: Arctic Wolf says threat actors are using a new Fortinet zero-day to mass compromise of Fortinet FortiGate firewalls. Tracked as CVE-2024-55591, the zero-day is an authentication bypass exploited via the firewall's Node.js websocket module. A patch is now available.
Aviatrix exploitation: Cloud security firm Wiz has detected active exploitation of an Aviatrix Controller unauthenticated RCE vulnerability (CVE-2024-50603) that was initially disclosed last week. The flaw is being used to gain access to AWS customer backends.
Apple SIP bypass: Microsoft security researcher Jonathan Bar Or has published details about a new SIP bypass impacting macOS. It's the third bypass the researcher has found in macOS over the past years.
Sign in with Google hijack: TruffleSecurity's Dylan Ayrey has found a way to abuse the "Sign in with Google" feature and access data from failed companies. The idea is to re-register expired domains for failed companies, stand up a Google Workspace for that domain, and use the domain and the new Google mail address to access data from the failed company's leftover online infrastructure. This includes stuff like Zoom, HR systems, Slack channels, and more.
Facebook ad platform hack: Two bug hunters have found a vulnerability that allowed them to pivot from Facebook's ad platform to the company's internal server network. Meta awarded the two $100,000 for their work. [Additional coverage in TechCrunch]
BlinkenCity research: Positive Security has published details about BlinkenCity, a technique that uses rogue radio signals to shut down renewable power management devices and streetlights in some European cities.
VPN tunneling vulnerabilities: Two KU Leuven academics have discovered that over four million VPN servers and home routers can be abused to re-route malicious traffic and carry out DoS attacks via modified tunneling packets. [Additional coverage in Top10VPN/Full research paper PDF]
"The discovered hosts also facilitate new Denial-of-service (DoS) attacks. Two new DoS attacks amplify traffic: one concentrates traffic in time, and another loops packets between vulnerable hosts, resulting in an amplification factor of at least 16 and 75, respectively. Additionally, we present an Economic Denial of Sustainability (EDoS) attack, where the outgoing bandwidth of a host is drained. Finally, we discuss countermeasures and hope our findings will motivate people to better secure tunnelling hosts."
Infosec industry
Threat/trend reports: The Cyber Threat Alliance, IANS Research+Artico Search, Ukraine's SCPC, and the US NMFTA have published reports and summaries covering various infosec trends and industry threats.
Tool update—HIBP: The Have I Been Pwned portal is now indexing leaked or public stealer logs.
New tool—raink: Security firm BishopFox has released raink, a tool to help researchers solve ranking problems that are otherwise difficult for LLMs to process.
New tool—What is this Stealer: The MalBeacon team has released What is this Stealer, a GitHub repo containing formats used by infostealer malware, designed to allow security researchers to easily identify infections.
New tool—Sunder: Security researcher Cole Houston has released Sunder, a Windows rootkit modeled after the Lazarus Group's FudModule rootkit.
New tool—EarlyCascade: Security researcher Abdallah Elsharif has released a PoC for the EarlyCascade process injection technique.
ShmooCon 2025 streams: Live streams from the last ShmooCon security conference, which took place last week, are available on YouTube.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about the evolution of Russian cyber operations during its invasion of Ukraine.
