Risky Bulletin Newsletter
March 03, 2025
Risky Bulletin: Trump administration stops treating Russian hackers as a threat
Written by

News Editor
This newsletter is brought to you by cloud security firm Prowler. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
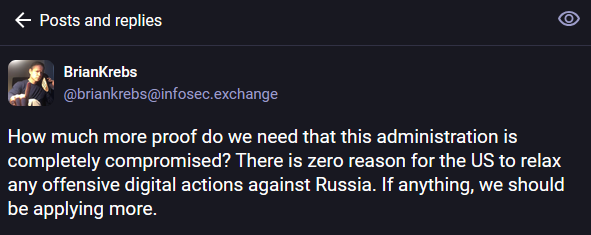
The Trump administration has sent memos to CISA and US Cyber Command instructing cybersecurity staff to stop treating Russian hackers as a threat and halt operations targeting Russia.
Both orders were issued around two weeks ago but were only first reported publicly on Friday.
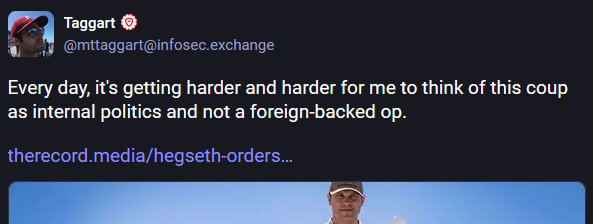
In the first order, Defense Secretary Pete Hegseth ordered Cyber Command to shut down any operations targeting Russia.
Martin Matishak reported for The Record that the exact duration of Hegseth's halt order is unknown but that it is set to be the branch's new policy going forward.
Matishak says that no similar order was issued to the National Security Agency, which is still free to collect intelligence on Russian targets.
The sudden halt of CyberCom Russian operations will most likely impact Ukraine, first and foremost, where the branch has sent several hunt-forward missions since Russia's invasion. The missions have helped Ukraine bolster its cyber defenses against Russian espionage and cyber sabotage operations.
Obviously, this will have a blowback on US cyber defenses, but this will take time to unfold, and the immediate effect should be seen on Ukrainian networks before American ones.
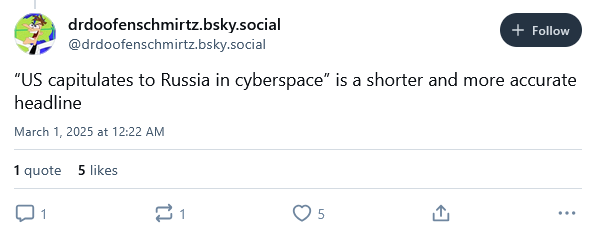
The second order targeted CISA. The Guardian reported that staff received new directives for the agency's priorities that only mentioned tracking Chinese threats and the protection of local systems.
It did not name Russian hackers as US adversaries.
Furthermore, staff were "verbally" told to stop working on anything Russia-related.
"A person familiar with the matter who spoke to the Guardian on the condition of anonymity said analysts at the agency were verbally informed that they were not to follow or report on Russian threats, even though this had previously been a main focus for the agency. The person said work that was being done on something 'Russia-related' was in effect 'nixed'."
The Guardian notes the memo appears to have been sent around the same time window when a US State Department official gave a speech at the UN that only mentioned Iran and China as cyber threats. The speech stood out to US allies because the US had described Russian hackers and its ransomware crews as a major threat to all nations over the past years and had called out Russia's actions in UN forums for years.
The news floored cybersecurity and national security experts, who have been trying to keep Russian hackers out of US networks for over two decades now.
Both stories also broke as US President Trump and Vice-President Vance berated Ukrainian President Zelenskyy with Russian propaganda talking points in the Oval Office, attempting to hold him responsible for Russia's invasion and the subsequent war.
These and many other small statements have been signalling a realignment of US policies, away from its old allies and to a common ground with autocratic regimes like Russia. If not, they are at least designed to help out the Kremlin in its ruinous war in Ukraine.
The US halting cyber ops targeting Russia, disbanding the FBI's Foreign Influence Task Force, disbanding the State Department's KleptoCapture Task Force, threatening to cut military aid to Ukraine, threatening to shut off Starlink access for Ukrainian troops, and engaging in a minerals deal extortion passed as faux peace talks are just a few many gestures that seem to be the US giving a helping hand to the Kremlin for no apparent benefit for the US.
Former NSA hacker Jake Williams also points out that halting any cyber ops targeting Russia will also lead to fewer instances where the US calls out or attributes major cyber incidents to the Russian government, another net win for the Kremlin.
It is also a major win for Donald Trump, who has spent years fighting what he describes as the "Russia hoax"—namely, that the Russian government, through its oligarchs, hackers, and troll farms, helped him win the 2016 election.
Obviously, his campaign received indirect help from the DNC hack-and-leak, and Trump itself called on Russian hackers to attack his 2016 election rival, Hillary Clinton, but Donald Trump has never been the man to let facts ruin his day.
The Trump administration's soft spot for Russia is nothing new, but it was never featured as a matter of government policy as it is now.
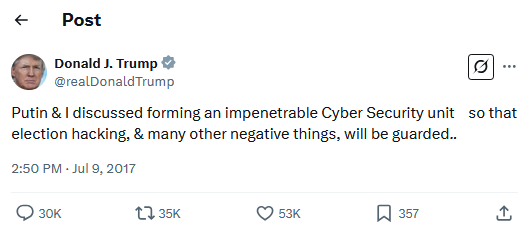
In 2017, President Trump touted the idea of creating a joint cybersecurity unit with Russia, only to drop the idea after massive backlash. This time around, the new Trump 2 administration doesn't seem to care about any backlash or common sense and just pushes through regardless, to the dismay of its own staff, troops, citizens, and allies.
Risky Business Podcasts
Risky Business is now on YouTube with video versions of our main podcasts. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
Spyzie spyware app hacked: A bug in mobile spyware app Spyzie has exposed the email addresses of all its users. The bug was discovered by an anonymous security researcher who exploited the issue to track sign ups to the stalkerware apps. The researcher says Spyzie has over 510,000 registered users. Users are allegedly using Spyzie to spy on over half a million Android devices and thousands of iPhones and iPads. [Additional coverage in TechCrunch]
"For Android users: Even if Spyzie is hidden from view, you can usually dial ✱✱001✱✱ into your Android phone app's keypad and then hit the call button. If Spyzie is installed, it should appear on your screen."
Rubrik breach: Cloud security firm Rubrik says that a threat actor gained access to one of its logging servers but that the logs did not contain any sensitive user data.
Zapier breach: Software automation company Zapier disclosed a security breach after a hacker gained access to its internal code repositories. The company believes the attacker might have gained access to some customer information that was accidentally copied into some repositories. Zapier is notifying customers via email. [Additional coverage in The Verge]
Funds seized from Uranium Finance hack: US authorities have recovered $31 million worth of crypto-assets stolen from Uranium Finance. The funds were stolen in a $53 million crypto-heist in April 2021, shortly after the platform launched. Crypto investigation firm TRM Labs says it spent two years tracking the stolen funds across multiple blockchains.
Ascension Health lookback: Security researcher Will Thomas uses the recent Black Basta chat leak to look back at the 2024 Ascension Health ransomware attack and how the gang reached the conclusion to give the victim a free decryption key.
General tech and privacy
Meta seeking permanent NSO ban: Meta is seeking a permanent injunction against Israeli spyware maker NSO Group from all its platforms. The social media company has asked a judge to bar NSO from interacting or using any of its platforms. NSO can't interact with Meta's WhatsApp platform based on a temporary injunction put in place in 2019 after Meta sued the spyware maker. In December of last year, a judge found NSO Group liable for attacks that targeted over 1,400 WhatsApp users. Meta is now seeking to lift the temporary WhatsApp injunction into a permanent ban for all Meta platforms. [Additional coverage in the Daily Journal]
Apple overhauls child accounts: Apple has made it easier for parents to set up child accounts and control what they see online, including rolling out a new API that can allow developers to confirm age ranges and deliver appropriate experiences. [Additional coverage in MacRumors]
Mozilla TOS debacle: Mozilla updated its terms of service last week to allow itself to use some user data. The update sparked outrage due to some vague language that suggested that Mozilla was allowed to use any data submitted through the browser. The company later clarified that this is not the case, but the company has not explained why it deleted the section from its TOS that prevented it from selling user data.
Red Alert code open-sourced: EA has released the source code for its "Command and Conquer: Red Alert" game.
QWAC standard draft: The European Telecommunications Standards Institute (ETSI) has published the first draft of the QWAC (Qualified Certificates for Website Authentication) standard [PDF], a new type of digital certificate that the EU wants browser makers to support just for EU audiences. [h/t FeistyDuck]
Microsoft starts disabling Manifest V2 extensions: Following in Google's footsteps, Microsoft is now forcibly disabling extensions built on the old Manifest V2 API in people's Edge browsers. This includes a bunch of powerful ad blockers that "accidentally" managed to block both Google and Bing ads. What a happy coincidence for these "browser makers" and definitely not ad companies.
New CA drama: Certificate authority Sectigo says it received a cease and desist letter from its competitor Digicert after one of its employees reported a bug in Digicert's infrastructure. Digicert claims that the employee posted misleading information about its services, even if the company eventually had to revoke some of its certificates. Despite the letter, Sectigo refused to censure its employee. [h/t Xarph]
Microsoft retires Skype: Microsoft will shut down its Skype instant messaging app on May 5 in order to focus on its Teams service. The company has urged users to migrate to a Teams account or export their content. Skype launched in 2002 and had over 300 million active users at its peak. Microsoft acquired the app in 2011 for $8.5 billion and used it as a backbone to launch its Teams collaboration platform in 2017.
Government, politics, and policy
New EU cybersecurity blueprint: The EU launched a new cybersecurity blueprint for the management of cybersecurity crisis situations.
US cancels foreign cybersecurity aid: The US government has canceled a $95 million contract with IBM designed to bolster the cybersecurity defenses of European and Asian allies. The contract allowed IBM to deploy cybersecurity experts in several countries to bolster their cybersecurity defenses. Countries like Albania, Moldova, Azerbaijan, and Kosovo benefited from the contract. The contract was provided through the USAID agency and was canceled as part of the White House's efforts to cut down government spending. [Additional coverage in NextGov]
Memecoins are not securities: The US SEC says that memecoins are not covered by securities law, which opens the doors to a bunch of fraud and manipulation. Great job, USA! Put more crypto edgelords in the administration and see what happens next.
Government internet shutdowns get worse: According to a new AccessNow report, 2024 was the worst year in terms of government-mandated internet shutdowns across the globe, with 296 internet shutdowns recorded in 54 countries.
Iranian government seizes dissidents' Instagram accounts: The Iranian government is seizing the Instagram accounts of anti-government dissidents. The procedure involves arrests and the extraction of passwords during interrogations. Authorities access an account, delete all posts, and post a confiscation message on the user's profile. The seizures of individual accounts are the first of their kind reported across any autocratic regime. [Additional coverage via Nariman Gharib]

Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Toni de la Fuente, founder and CEO of cloud security firm Prowler. Toni talks about his company's latest effort, the Open Cloud Security Movement, an initiative to get more cloud security vendors to open-source their core projects.
Arrests, cybercrime, and threat intel
No prison time for WazaWaka and Ermakov: Russian authorities have handed down light sentences to two well-known ransomware gang members. Lockbit affiliate Mikhail "WazaWaka" Matveev was sentenced to 1.5 years of restriction of freedom. He is not allowed to travel and will have to register with authorities each month. REvil affiliate Alexander Ermakov was also sentenced to 2 years of restriction of freedom for his role in developing the SugarLocker ransomware. WazaWaka is known for his attack on the Washington DC police, while Ermakov was behind the Medibank ransomware attack. Both were detained last year for charges unrelated to cases filed in the US. [h/t Oleg Shakirov]
CSAM site admin sentenced: US authorities have sentenced a California man to 24 years in prison for operating four websites dedicated to sharing CSAM.
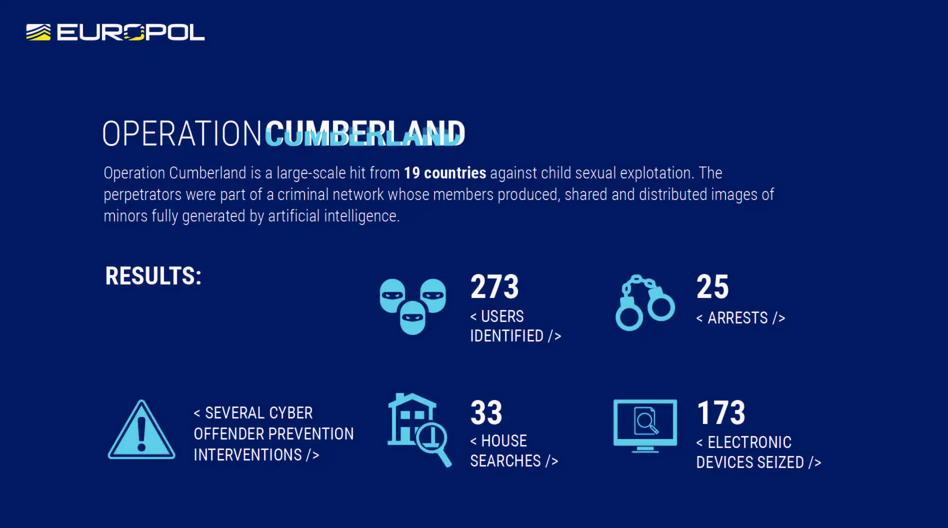
Operation Cumberland arrests: Europol has detained 25 suspects across 19 countries who used generative AI services to produce and distribute CSAM imagery. The content was distributed via an online platform run by a Danish national. He was arrested in November of last year, along with some of the platform's users.
New npm malware: Ninty-five malicious npm packages were discovered and taken down last week. Check out the GitHub security advisory portal for more details.
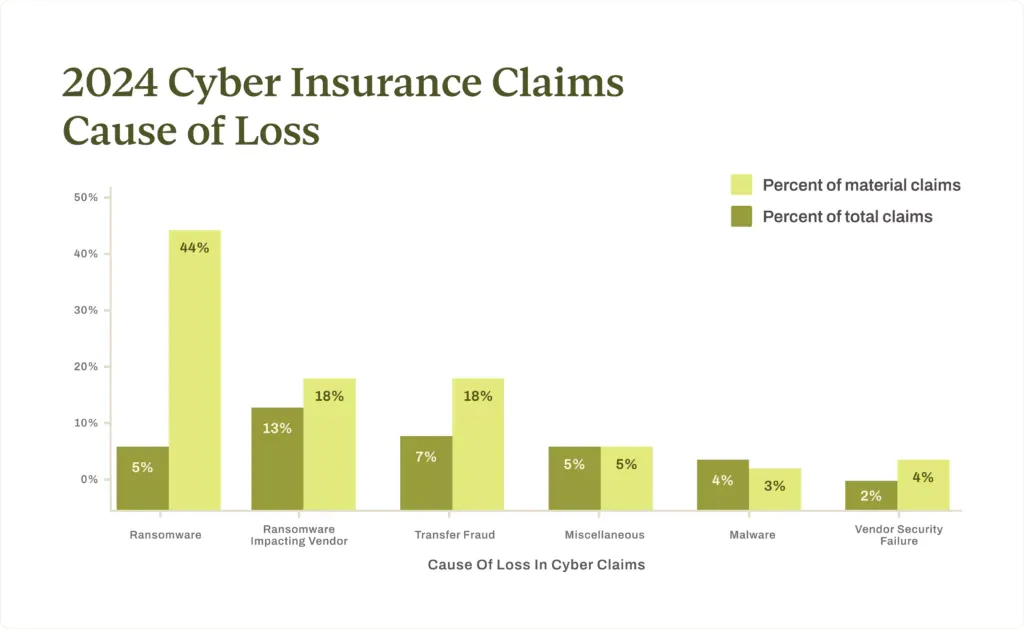
Ransomware remains top threat to cyber insurers: Security breaches at third-party providers accounted for nearly a third of all cyber insurance claims last year. Cyber insurance provider Resilience says it paid insurance claims for third-party incidents for the first time last year. Claims for third-party incidents accounted for nearly a quarter of all claims paid last year. Ransomware still accounted for the vast majority of material claims.
JavaGhost: A hacking group named JavaGhost has switched from website defacements to running a Spam-as-a-Service operation on top of hacked AWS environments. The group is using leaked AWS credentials to take over customer accounts and deploy email phishing infrastructure. According to Palo Alto Networks' security team, the switch occurred in 2022.
Malicious traffic redirected through Kaspersky's network: A major bulletproof hosting provider named Prospero is routing its malicious traffic through networks owned by Russian security firm Kaspersky. [Additional coverage in KrebsOnSecurity]
Malicious GitHub repos: A security researcher has discovered over 1,100 GitHub repositories containing malware. The repositories targeted Russian audiences and offered game mods and pirated software. Once installed, the apps would deploy an infostealer named Redox that would collect crypto wallet private keys, bank account details, and browser passwords.
Krpano attacks: Hackers are exploiting a reflected XSS vulnerability in the Krpano JS library to inject malicious code into hundreds of websites. According to security researcher Oleg Zaytsev, the attackers are using the hacked websites to push porn ads at scale. The Krpano library is a tool used to build VR environments and virtual tours.
Astrill VPN IP list: Security firm Silent Push has released a list of IP addresses linked to Astrill, a VPN service often used by North Korean IT workers to hide their location. Spur also released a similar list last December.
Forged documents ecosystem: French security firm LEXFO has published a report that analyzes the underground world of document forgers. Most of this ecosystem appears to have moved from the dark web to the clear web—for some reason.
The evolution of Russian cybercrime: Intel471's Jeremy Kirk has published an interview with threat intel veteran Roman Sannikov on the evolution of Russia's cybercrime ecosystem. Highly recommend a listen!
Malware technical reports
Behinder web shell: Kaspersky looks at the PHP and JSP versions of the Behinder web shell, also known as Rebeyond, Ice Scorpion, 冰蝎 (Bīng xiē).
Winos: Fortinet's security team has published a report on Winos, an advanced malware framework used in recent campaigns targeting Taiwanese companies.
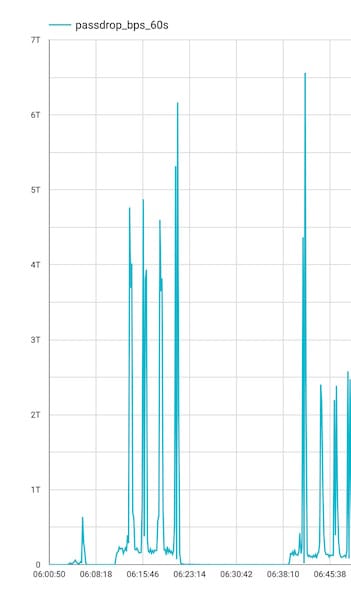
Eleven11bot: A new botnet named Eleven11bot has infected over 30,000 devices and is being used to launch large-scale DDoS attacks against telecom providers and gaming platforms. Most of the infected devices are security cameras and network video recorders (NVRs), with a vast chunk being located in Iran. According to Nokia's Deepfield DDoS mitigation service, the botnet was behind a DDoS attack that peaked at 6.5 Tbps—the largest volumetric DDoS attack ever documented. The previous record was 5.6 Tbps, recorded by Cloudflare at the end of October last year. [h/t Jérôme Meyer]
Sponsor section
In this sponsored product demo, Prowler founder and CEO Toni de la Fuente walks Risky Business host Patrick Gray through the company's open-source cloud security platform. Toni demonstrates how Prowler can identify and remediate security issues across AWS, Azure, GCP, and Kubernetes. There's a pointy-clicky GUI interface and a CLI, and both come in handy in different ways. The Prowler platform is completely free and open source, but there is a hosted version you can pay for if you don't want to run it yourself.
APTs, cyber-espionage, and info-ops
Dark Caracal: Russian security firm Positive Technologies has published a report on Dark Caracal campaigns delivering the Poco RAT to Spanish-speaking audiences across Latin America.
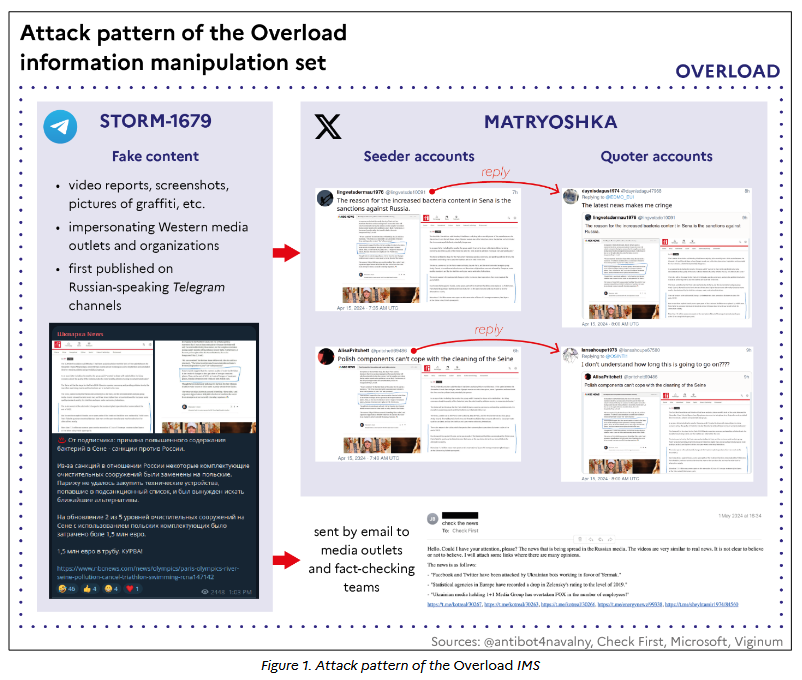
Doppelgänger: French security firm Intrinsec looks at Doppelganger disinformation campaigns targeting multiple European countries. The company looks at the linguistic characteristics of fake articles promoted by the group and concludes they "were translated from Russian or edited by Russian natives, reinforcing the hypothesis that they are of Russian origin."
VIGINUM Russian info-ops report: France's disinformation investigations team VIGINUM has published a report on the three years of Russian disinformation campaigns since the country's invasion of Ukraine. An English version PDF is available.
Vulnerabilities, security research, and bug bounty
Cellebrite zero-days: Researchers at Amnesty International have found three zero-days used by Serbian authorities to unlock the phones of anti-government protesters. All three zero-days are in the Linux USB stack but were used to hack Android devices. Two of the zero-days were fixed in the Linux kernel last year, while the third was patched in the Android OS this month. The zero-days were part of a phone unlocking tool sold by Cellebrite to law enforcement agencies. The company banned Serbian authorities from its service last week after learning of the misuse.
Paragon Partition Manager abuse: Ransomware groups are using old versions of the Paragon Partition Manager driver in BYOVD attacks. The attacks are leveraging an EoP vulnerability tracked as CVE-2025-0289.
New VSCode bootstrapping attack: Security researcher Cas van Cooten has developed a technique that abuses the VSCode bootstrapping functionality to silently load malicious extensions.
Substack domain takeover: Software engineer Joren Vrancken has found a bug that can allow threat actors to hijack the subdomains of inactive Substack accounts that use a custom domain.
Draytek router vulnerabilities: Faraday Security has found nine vulnerabilities in Draytek Vigor routers. Some of the vulnerabilities include insecure password storage, predictable 2FA code generation, and loads of memory bugs.
Teammate app disclosure drama: The CEO of the Teammate business compliance app has emailed customers to blame a security researcher for a recent security breach. The email accused security researcher JayeLTee of hacking Teammate servers and threatened to report him to authorities. The researcher claims there was no hacking involved since the company left its MongoDB database exposed online without a password.
Wallbleed research: A team of academics has exploited a memory leak in equipment used for China's Great Firewall to learn about its internal architecture and DNS injection capabilities.
Infosec industry
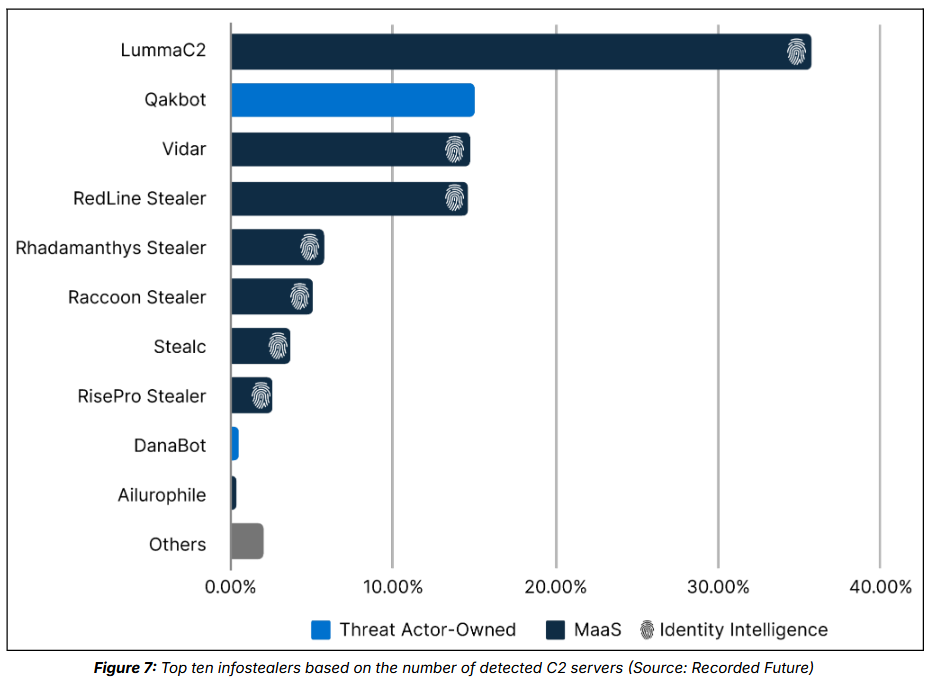
Threat/trend reports: AccessNow, Cloudflare, CNIL, F5, LayerX, Nozomi Networks, Recorded Future, and Resilience have recently published reports and summaries covering various infosec trends and industry threats.
Risky Business Podcasts
Tom Uren and Patrick Gray talk about the White House apparently considering kicking Canada out of the Five Eyes intelligence alliance to apply pressure on the country. It's a terrible idea, and even thinking about it undermines the strength of the alliance.
In this edition of Between Two Nerds, Tom Uren and The Grugq examine the fundamental principles of network exploitation as described in Matthew Monte's "Network Attacks and Exploitation: A Framework" book.
