Risky Bulletin Newsletter
March 24, 2025
Risky Bulletin: The looming epochalypse
Written by

News Editor
This newsletter is brought to you by Sublime Security, an email security platform that's not a black box. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
I'll start this newsletter edition by saying from the get-go that today's topic—the Year 2038 problem—isn't new at all.
It has a Wikipedia page dating back to 2005, a 2009 XKCD comic, and was at the center of a Guardian article back in 2014.
It was a tweet from security researcher Pedro Umbelino last week that reminded me of this problem and how close to its deadline we have gotten—because, yes, everyone gets old!
For the younglings and padawans in the audience who have never heard of it, the Year 2038 problem, also known as the Epochalypse, is the equivalent of the Y2K bug, but for Linux and other Unix-based systems.
It refers to how these systems store time values in 32-bit integers and how the current time is getting close to reaching that integer's upper limit. From Pedro Umbelino and Trey Darley's write-up:
"Many computer systems track time using a 32-bit signed integer that counts seconds since 1970-01-01T00:00:00Z (known as 'Unix time'). This approach has a mathematical limitation: when this counter reaches its maximum value on 2038-01-19 03:14:08 UTC, affected systems will roll over to negative numbers, causing them to interpret the date as 1901-12-13T20:45:52Z."
As you can imagine, having your devices go haywire because they've been teleported back in time over a century is bound to cause some issues. Computer systems are very likely to fail in various ways when they can't synchronize with upstream or downstream systems to exchange data. This scenario was basically at the center of all the Y2K panic in 1999.
Through an all-hands-on-deck patching effort, thanks to software vendors and sysadmins everywhere, that disaster was avoided. The world didn't crash and burn when we crossed into the year 2000.
Now, a similar event is getting closer, but as Umbelino and Darley point out, the world has changed since then, and the problem is way more complex.
First, there are billions more devices to patch than there were back in 1999. Unix-based systems that use the Unix timestamp format are literally everywhere and in all forms, from medical devices to networking equipment. We're not talking just about some silly desktops and some data center servers. We're talking about ICS/SCADA gear, networking devices installed all over our apartment blocks, and much, much more.
Many of these devices run on extremely limited hardware that cannot even process a larger Unix time integer—so, unlike Y2K, Year 2038 is also now a hardware problem. Many of these systems will need to be physically replaced.
These devices have huge tail-ends. There are devices installed back in the 90s that are still running in networks today, probably on the same software.
Not only will they not be replaced, but many even lack a system to receive firmware updates in the first place.
Yes, this sounds bad, but it's actually worse than I can ever describe it, and once you start taking into account all the places "smart" devices have made their way into since Y2K, a time when the phrase "Internet of Things" sounded like something from an Asimov book.
For infosec practitioners who watched for years how companies have repeatedly failed to patch their systems in the face of APTs and ransomware, we know patches, even if available, won't be enough.
This is why Umbelino and Darley's write-up caught my eye last week. It called Year 2038 a "vulnerability" rather than a bug or problem. We've seen companies fail and fail on various topics, and fixing this requires a sort of coordination this current world hasn't expressed any interest in getting started.
Because it will require a level of coordination that's just a little bit above the regular CERT-issued security advisories.
As Umbelino and Darley point out, there needs to be action on this topic from governments, device manufacturers, importers, distributors, and many other groups.
There should already be some sort of government-issued guidance and even regulation in place mandating 64-bit time implementations for Unix-based devices.
That time is now because the devices that will be running in 2038 are being mass-produced right now. People don't buy devices they throw away after the warranty and EoL expires. These devices typically live three or four times that.
Sorry for the IT fearmongering, but I kind of agree with Umbelino and Darley. Efforts to fix this should be already underway.
Update: Added Trey Darley as one of the Epochalypse Project's creators.
Risky Business Podcasts
Risky Business is now on YouTube with video versions of our main podcasts. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
Changed-Files supply chain attack: The compromise of the Changed-Files GitHub Action was just a stepping stone in a multi-tier supply chain attack that targeted cryptocurrency exchange Coinbase. The attack targeted GitHub actions used by a Coinbase open-source project named AgentKit in the hopes of leaking access tokens for the Coinbase platform. According to security firms Wiz and Palo Alto Networks, the attack failed, and Coinbase was unaffected. Wiz says it also identified the attacker as French and English-speaking, and with working hours aligned to Europe or Africa.
Keenetic leaks user data: Router maker Keenetic has leaked the personal and password data of its users after leaving its mobile app database exposed online without a password. Emails, WiFi keys, and local account MD5 and NT password hashes were exposed in the leak. Most of the affected routers are located in Russia. [Additional coverage in CyberNews]
Zoth crypto-heist: A hacker has stolen $8.85 million worth of crypto-assets from the Zoth blockchain project. The attacker gained access to one of the Zoth internal accounts and deployed a malicious contract that withdrew the platform's funds. The company has offered a $500,000 reward to anyone who can identify the hacker and recover the stolen assets.
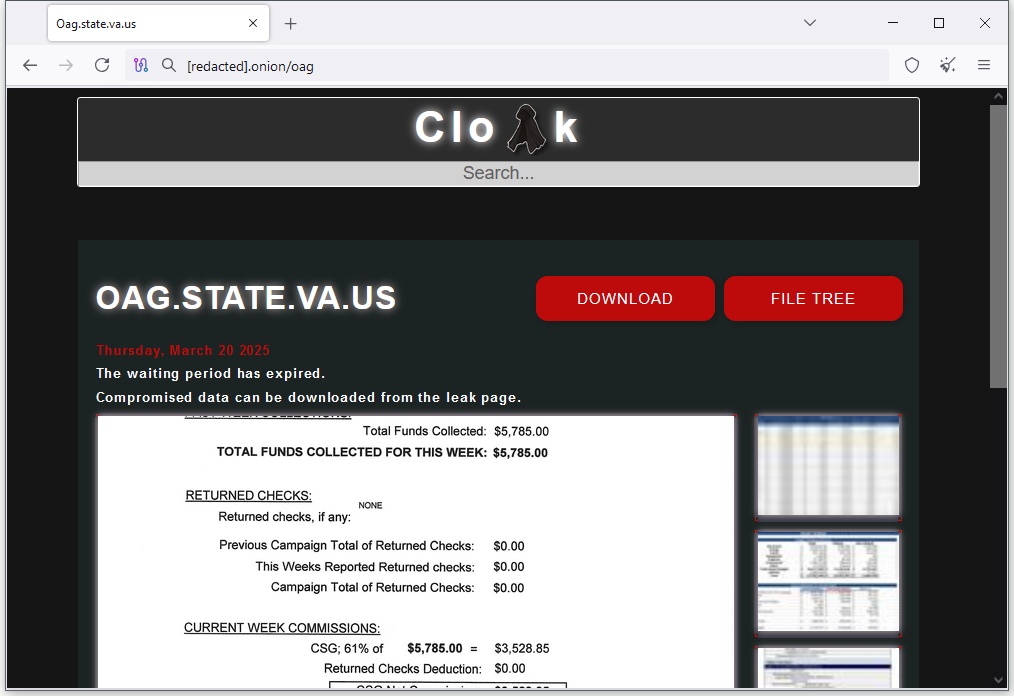
Virginia OAG ransomware attack: The Cloak ransomware gang has taken credit for breaching the Virginia Attorney General's Office last week. The agency took down its computer network and told staff to return to paper court filings while they dealt with the attack. The Cloak gang has dumped all the agency's data, suggesting officials declined to pay the ransom. [Additional coverage in SecurityWeek]
General tech and privacy
Russian internet outages: Several major internet outages across Russia last week have been linked to the country's internet watchdog attempting to ban Cloudflare. [Additional coverage in The Record]
Clearview AI settles privacy lawsuit: Clearview AI has settled a class-action lawsuit in the state of Illinois, and the company has agreed to grant plaintiffs a 23% stake in its future IPO. This marks the first time a major privacy lawsuit has been settled for a company's future value instead of a settlement fund that's distributed to plaintiffs. Clearview has agreed to settle the lawsuit a month after its CEO resigned and was replaced by new management. [Additional coverage in Reuters]
China unveils undersea cable cutter: The Chinese government has unveiled a new device capable of cutting fortified undersea communications cables. [Additional coverage in Yahoo News]
Government, politics, and policy
Turkiye restricts social media: The Turkish government has restricted access to social media networks shortly after authorities arrested Istanbul mayor Ekrem Imamoglu, President Erdogan's main political rival, on likely made-up terrorism charges. Shortly after, "fReE sPeEcH bAsTiOn" Twitter suspended most of the opposition's accounts on the site. Three days later, at the time of writing, the social media restrictions were still live as public protests were underway.
⚠️ Update: it has now been 40 hours since Turkey imposed widespread social media and messaging restrictions amidst the detention of political opposition figures including Istanbul mayor Imamoglu; the incident continues to severely limit the public's ability to access information
— NetBlocks (@netblocks.org) 2025-03-20T20:07:19.379Z
French lawmakers reject narcotrafficking law: The French Parliament has rejected a proposed anti-drug-trafficking bill that would have mandated messaging services to create encryption backdoors. France is one of the many European countries that have discussed such laws over the past years after the Netherlands, Sweden, and the UK. Ahead of the vote, Signal threatened it would pull out of France if the law passed. [Additional coverage in Le Monde/English coverage in EFF]
White House shifts cyber responsibility to states: US President Donald Trump signed an executive order last week that shifts responsibility for managing critical infrastructure from federal agencies to states and local governments. Local and state governments will now be in charge of defending and responding to cyber attacks, wildfires, hurricanes, and other events. The executive order comes after the White House ordered sprawling cuts to the US federal government workforce. [Additional coverage in BankInfoSecurity] [h/t DataBreaches.net]
US removes Tornado Cash sanctions: The US Treasury has removed sanctions on the Tornado Cash cryptocurrency mixing service. The agency removed the sanctions after a US court ruled last year that the Treasury overstepped its authority when it sanctioned the service in September 2022. Tornado Cash has been linked to massive crypto money laundering operations, ranging from drug cartels to state-sponsored hacking groups.
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Josh Kamdjou, co-founder and CEO of Sublime Security. Josh goes over recent trends in email badness, such as the increase in QR code abuse and the rise of SVG smuggling.
Arrests, cybercrime, and threat intel
Former Michigan coach charged with hacking: The US Department of Justice indicted a former football coach for the University of Michigan on hacking-related charges. Officials claim Matthew Weiss hacked and downloaded the personal data of over 150,000 student-athletes from a third-party provider. Weiss used the stolen data to hack the social media and email accounts of over 3,300 students, from where he downloaded intimate photos and videos. The hacks took place over a period of eight years, between 2015 and January 2023.
Tap-to-Pay ring members detained: Authorities in two US states have detained over a dozen Chinese nationals who were part of a tap-to-pay mobile fraud scheme. The suspects allegedly used their mobile devices to buy gift cards and other products using payment details relayed to their phones from devices in China. The scheme is known as tap-to-pay fraud and was previously only observed in Southeast Asia. [Additional coverage in KrebsOnSecurity]
Crypto-scam money mules detained Ukraine: Ukrainian authorities arrested three locals who served as money mules in a cryptomining scam that targeted EU countries.
Google sues scam network: Google filed a lawsuit against a criminal group that ran thousands of scams on the company's Maps service. The group ran fake companies that overcharged and scammed users under duress, such as those needing locksmiths and towing services. Google discovered the network last year and has since removed over 10,000 scam listings. [Additional coverage in CBS News]
Semrush malvertising campaign: Threat actors are targeting SEO professionals with malicious Google search ads for the Semrush SEO/SERP service.
Steam removes another malicious game: Steam has removed the demo of an upcoming game named "Sniper: Phantom's Resolution" for installing malware on user devices. Valve has removed the game after reports on Reddit that the demo was installing an infostealer. This is the second malicious game removed from Steam this month, a rare occurrence for the usually clean platform. [Additional coverage in TheGamer]
New npm malware: One hundred seventy-five malicious npm packages were discovered and taken down last week. Check out the GitHub security advisory portal for more details.
Malicious VSCode extensions: ReversingLabs researchers have found two malicious extensions on the official VSCode Marketplace that attempted to deploy ransomware on its users' systems. The security firm says the ransomware was still in development. Microsoft removed both extensions after the company's report.
⚠️🧵 RL researchers have found 2 malicious #VSCode extensions, "ahban.shiba" & "ahban.cychelloworld," that deliver #ransomware in development to it's users. #Dev #SoftwareSupplyChainSecurity
— ReversingLabs (@reversinglabs.com) 2025-03-19T13:46:11.612Z
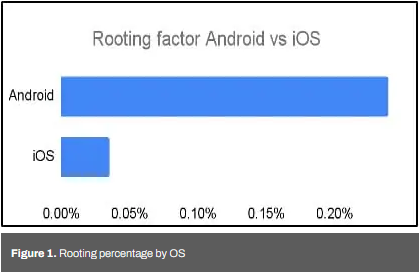
Rooted smartphones: Mobile security firm Zimperium says that one in 400 Android devices is rooted, while one in 2,500 iPhones has been jailbroken.
Malware technical reports
Albabat ransomware expands targetting: Trend Micro has spotted new versions of the Albabat ransomware that can also target macOS and Linux, besides its usual Windows targets. The ransomware has been around since 2003.
BlackLock (ElDorado) ransomware: DarkAtlas has published a report on BlackLock, a ransomware that appeared last March as ElDorado and rebranded to its current name in September. You can also check out this ReliaQuest report on the same gang, too.
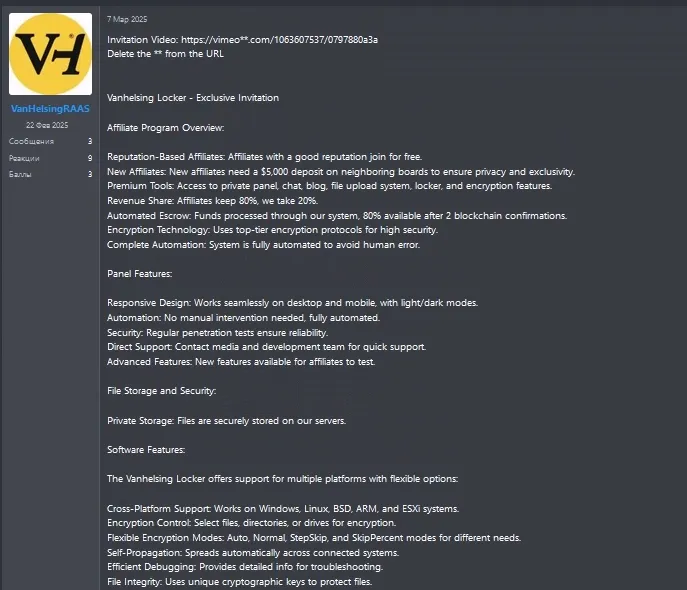
VanHelsing ransomware: Check Point researchers have spotted a new ransomware strain named VanHelsing. You can also check out this CyFirma report on the same gang, too. The group launched its RaaS on March 7 and only lists three victims on its dark web leak site.
ABYSSWORKER: Elastic's security team has published a report on ABYSSWORKER, a custom-made malicious driver used by the Medusa ransomware gang to disable EDR solutions on compromised networks.
SvcStealer: Seqrite researchers have published an analysis of a new infostealer named SvcStealer.
Latrodectus: Microsoft's security team has spotted Storm-0249 distributing the Latrodectus trojan using a new method.

Sponsor section
Sublime Security explores a new type of attack observed in the wild—the embedding of malicious JS code within SVGs to deliver adversary-in-the-middle credential phishing attacks.
APTs, cyber-espionage, and info-ops
i-SOON's Operation FishMedley: ESET has published a report named Operation FishMedley that details a 2022 cyber-espionage campaign by Chinese APT group FishMonger—the name ESET uses for Chinese private cyber contractor i-SOON.
EU releases disinformation report: The EU says China and Russia have been the most common sources of disinformation and foreign interference that targeted the EU and partner countries last year. The EU's External Action team has uncovered over 38,000 online channels involved in the spread of disinformation across the EU. Ukraine and Russia's invasion remained the top priority for the third year in a row. Twitter, Facebook, and third-party websites were the most used channels to spread disinformation. [More in the EU's EEAS report]

Vulnerabilities, security research, and bug bounty
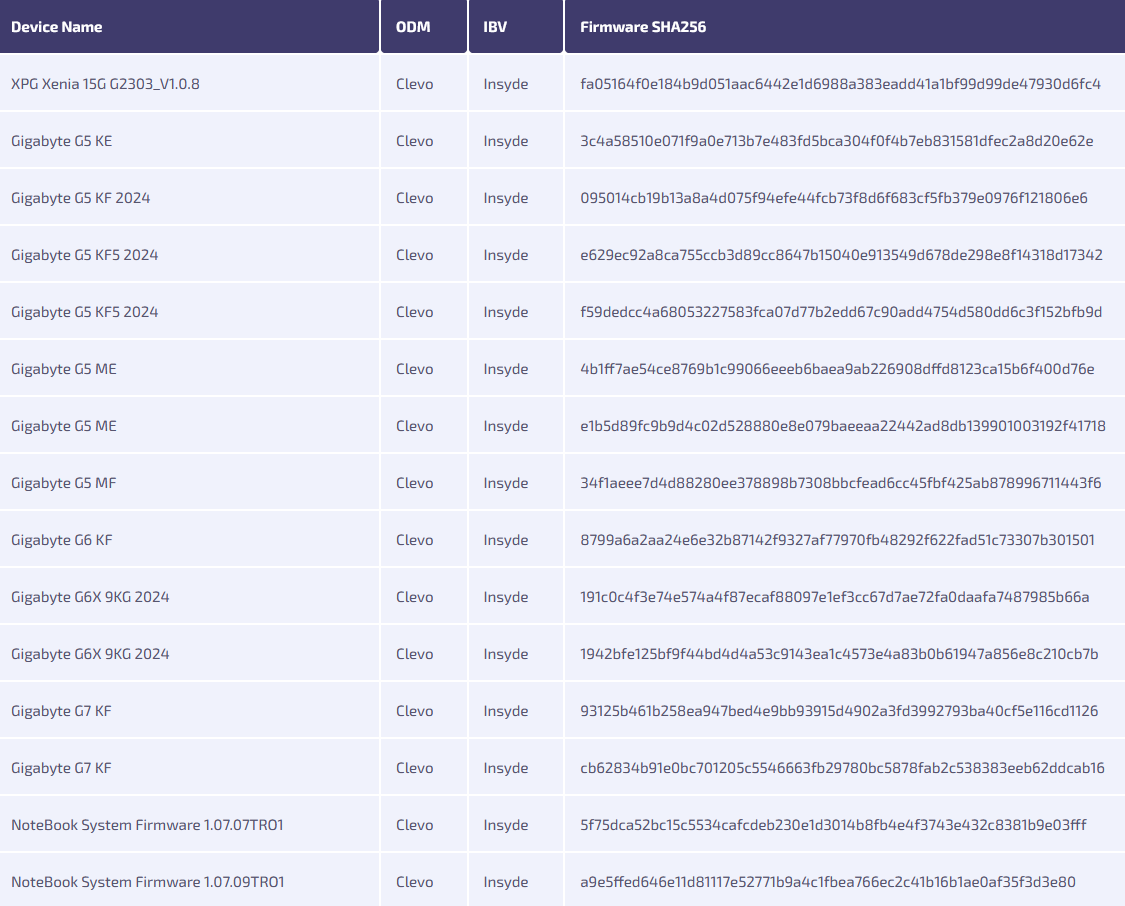
Clevo leaks private keys: ODM laptop maker Clevo has leaked boot-related private keys through some of its firmware updates. Attackers can use the leaked keys to sign malicious firmware that runtime validation. Security firm Binarly scanned the company's inventory and found private keys in 15 firmware images corresponding to 10 device models, most of which are Gigabyte-branded laptops.
Cisco SLU exploitation: Threat actors have started targeting two vulnerabilities in the Cisco Smart Licensing Utility that were patched last September.
Next.js authorization bypass: The Next.js team has rolled out a fix for an authorization bypass in its extremely popular JavaScript framework. Technical details are available in the researcher's write-up.
"It is possible to bypass authorization checks within a Next.js application, if the authorization check occurs in middleware."
Next.js dropped a CVSS 9.1 authentication bypass vulnerability (CVE-2025-29927) over the weekend. This flaw is trivially exploitable by sending the header `x-middleware-subrequest: true`. Over 300k hits in Shodan, find more at:
— HD Moore (@hdm.io) 2025-03-23T02:42:56.152Z
macOS password leak: Security researcher Noah Gregory has published a write-up on CVE-2024-5447, a macOS bug that could have allowed malicious apps to leak user passwords. This was patched last year.
Linux EoP: SSD has published details on a new Linux bug (CVE-2025-0927) that can be used to elevate privileges on compromised accounts.
Nakivo bug exploited in the wild: CISA warns that threat actors have started exploiting a dangerous vulnerability in the Nakivo backup and replication software. The vulnerability (CVE-2024-48248) allows attackers to retrieve a backup server's password or the backup files themselves. Nakivo silently patched the bug without responding to the researchers who found it and only acknowledged it a week after it was disclosed. NAS maker QNAP says it temporarily removed the Nakivo backup system from its software until it receives a fixed version from the company.
Exploit reseller seeks Telegram zero-days: A Russian exploit reseller will pay up to $4 million for Telegram zero-days and exploit chains. The exploits must run on Windows, Android, or iOS. The company is suspected of supplying Russian state agencies and previously claimed it only sells exploits to non-NATO countries. It regularly offers higher prices than rival vendors, mostly due to its association with Russian authorities. [Additional coverage in TechCrunch]
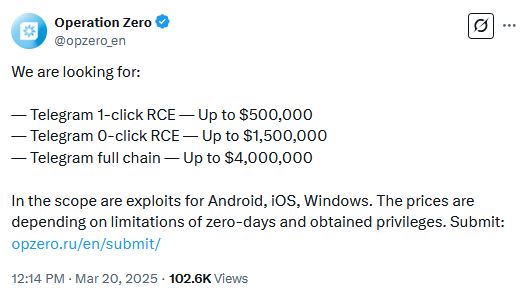
Zerodium goes dark: In the meantime, probably the most well-known US-based exploit reseller has gone dark and has taken down its exploit price list.
The official website of zero-day broker Zerodium has been updated in December of last year. There are no price lists nor any information anymore, just an email and a PGP public key. 🤔 If you know what's happening there...let me know. Zerodium.com
— Lorenzo Franceschi-Bicchierai (@lorenzofb.bsky.social) 2025-03-20T21:05:37.785Z
Infosec industry
New tool—glppwnme: Orange's security team has released glppwnme, a tool to check for vulnerabilities in the GLPI open-source IT inventory management system.
New tool—GREASE: Security firm Galois has released GREASE, an open-source binary reverse-engineering tool.
New tool—VAIBE: Verizon's security team has released VAIBE (Verizon AI Burp Extensions), a collection of Burp extensions designed for penetration testers and security researchers for working with AI tools.
New tool—Landrun: AI and blockchain software expert Armin Ranjbar released Landrun, a lightweight, secure sandbox for running Linux processes.
Threat/trend reports: Bridewell, F5, Jet Infosystems, Kaspersky, Menlo Security, Red Canary, and Zimperium have recently published reports and summaries covering various infosec trends and industry threats.
Risky Business Podcasts
Tom Uren and Patrick Gray discuss how China's Ministry of State Security is increasingly doxxing and threatening Taiwanese APT operators. In some ways, this mirrors the US strategy of naming and shaming Chinese cyber operators in indictments that contain lots of supporting information. But although MSS statements are filled with propaganda rather than technical detail, naming Taiwanese military hackers has some bite.
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about how offensive cyber operations could do so much more than just "deny, disrupt, degrade, and destroy." Grugq thinks this thinking is rooted in US military culture, and he wonders why cyber operations are always so mean.
