Risky Bulletin Newsletter
January 27, 2025
Risky Bulletin: Tbilisi public transport goes free after anti-government hack
Written by

News Editor
TThis newsletter is brought to you by asset inventory and network visibility company runZero. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
Anti-government hackers have defaced payment systems installed in public transport buses in Georgia's capital, Tbilisi, to play pro-European songs and slogans.
The incident took place on Friday morning as residents headed to work.
The ticket scanners and point-of-sale devices played the national anthems of Georgia and the EU, along with pro-EU speeches from local politicians:
- The Georgian national anthem.
- A phrase from Georgia's first President Zviad Gamsakhurdia, from his famous 1991 speech declaring the restoration of the country's independence: "Long live the independence of Georgia!"
- A segment from late Prime Minister Zurab Zhvania's statement at the Council of Europe in 1999: "I am Georgian, therefore I am European."
- Statements from Bidzina Ivanishvili's pre-election speeches.
- Obscene remarks made by current president and pro-Kremlin figure Mikheil Kavelashvili.
- Beethoven's "Ode to Joy," considered the EU's unofficial anthem.
- The phrase "Glory to Ukraine, glory to Georgia, f*** Russia!"
The Tbilisi City Hall shut down the system and is allowing residents to travel for free until the hacked systems are restored.

The hacks take place after almost three months of daily anti-government protests. Massive anti-government protests erupted in Tbilisi on October 28 last year after a pro-Kremlin party won the country's Parliamentary election among allegations of massive fraud, threats of violence, and ballot stuffing.
The winning Georgia Dream party canceled the country's EU ascension process, passed oppressive laws, and canceled the country's presidential election, appointing a president through the Parliament instead—putting even more fuel on the ongoing protests.
No hacktivist group has taken credit for the attacks yet.
This marks the first time that hacking has played any role in Georgia's anti-Russian resistance movement. This also marks the first time I've seen in-bus payment and ticket scanning systems get hacked. So, an A+ for originality!
Risky Business Podcasts
Risky Business is now on YouTube with video versions of our main podcasts. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
Phemex crypto-heist: A threat actor has stolen $70 million worth of crypto-assets from Singapore-based exchange Phemex. The attackers stole multiple types of crypto at the same time in a coordinated attack last Thursday. Phemex paused and then resumed operations after addressing the hack. Some anonymous security researchers have told reporters that the techniques used in the attack are reminiscent of North Korean hacking group TraderTraitor. [Additional coverage in The Block]
NoOnes crypto-heist: A threat actor has stolen $8 million worth of crypto-assets from crypto P2P marketplace NoOnes. The hack took place on the first day of the year and exploited a vulnerability in the platform's Solana bridge. According to open-source investigators, the stolen funds were passed through the Tornado Cash mixing service. [Additional coverage in the CrowdfundInsider]
BeyondTrust breach: Identity service provider BeyondTrust has updated its data breach disclosure and says that only 17 of its customers were impacted by a security breach last December.
UnitedHealth doubles breach impact numbers: UnitedHealth says that 190 million Americans had their data stolen in a ransomware attack at its Change Healthcare subsidiary last year. The company almost doubled the initial number of 100 million it put out last year. UnitedHealth says it has now notified most of the affected individuals. Change Healthcare was hit by the AlphV ransomware gang in February of last year in an incident that caused pharmacy and prescription issuance outages all over the country. [Additional coverage in TechCrunch]
British Museum network down after insider attack: London police have arrested a former employee who broke into the British Museum and shut down several IT systems. Officials say the man's actions took down the museum's ticket booking system. Several exhibitions were closed on Friday as a result of the intrusion. [Additional coverage in The Guardian]
Emergency systems hacked in Israeli schools: Pro-Palestine hacktivist group Handala has breached the Israeli Ministry of National Security and has sent false missile alerts to Israeli schools and kindergartens. The alerts were sent to smartphones via SMS and to raid and emergency systems installed in schools and kindergartners. The group claims it wiped the system after sending the alerts. [Additional coverage in Ynet]
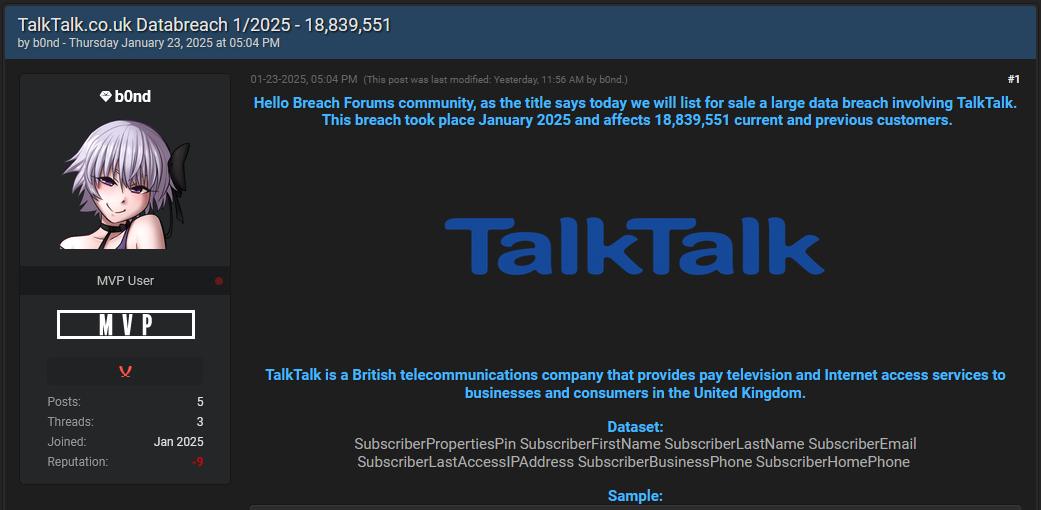
TalkTalk breach: UK ISP TalkTalk is investigating a data breach at a third-party supplier after some of its subscriber data was posted on a hacking forum last week. The threat actor claims to have stolen the details of nearly 19 million TalkTalk users in a breach this month. TalkTalk previously experienced a major breach in 2015.
General tech and privacy
Windows Administrator Protection: The Microsoft security team has published its first-ever technical explanation about the new Administrator Protection (AP) feature coming to Windows 11, a system that requires biometrics authentication to perform admin-level tasks. We first covered this back in November.
Samsung Galaxy S25 Content Credentials: Samsung's new line of Galaxy S25 devices are the first-ever devices to feature a new technology named Content Credentials. The new tech detects and automatically labels AI-generated content. Content Credentials currently supports images, but the technology will be extended to audio, video, and documents. [Additional coverage in TechCrunch]
PayPal fined over security failures: The New York Department of Financial Services has fined PayPal $2 million for failing to secure sensitive customer data. The agency says PayPal did not use personnel trained in cybersecurity risks when updating its backend to integrate the IRS' Form 1099-K. Developers left sensitive data unredacted in PayPal's systems, which allowed threat actors to be able to easily retrieve it once they compromised a user account.
Google launches custom Web Store: Google has launched a custom Chrome Web Store for enterprises to allow companies to filter what extensions appear on the store for their employees and avoid unwanted malware being installed.
More Texas car privacy probes: The Texas OAG has filed cases against four more automakers (Ford, Hyundai, Toyota, and Fiat Chrysler) over their car data collection practices. It previously also sued GM. No cases against Tesla, though, a car literally made to work on the cloud and track everything. [Additional coverage in The Record]
BlueSky spam networks: Underground services that sell follows, likes, and reply spam have acquired BlueSky in their sights. One such service appears to have registered over 8,000 BlueSky accounts for future abuse.
Government, politics, and policy
Belarus blocks internet during election weekend: The Belarusian government has taken down internet access across the country for three days during the country's presidential election this weekend. Officials ordered ISPs to shut down the internet between Friday and Sunday in order to prevent threats to election infrastructure. The measure is most likely meant to prevent the public from coordinating protests via social media, similar to those that took place four years ago.
Turkiye proposes controversial cybersecurity law: Turkish officials are fast-tracking a cybersecurity bill through Parliament for the creation of a national cybersecurity directorate. The bill contains provisions that would grant the new agency the power to collect and store data from all the country's institutions and critical infrastructure providers. It also contains a provision that effectively criminalizes reporting on security incidents if the government has not first confirmed a breach. The country's opposition has warned the bill effectively lays out a legal foundation of a sprawling surveillance apparatus on the grounds of cybersecurity threats. [Additional coverage in the Turkish Minute and the Nordic Monitor] [h/t DataBreaches.net]
US cyber diplomacy funding halted: An order from Secretary of State Marco Rubio to halt all foreign aid has also ground to a halt the activity of the department's new cyber diplomacy bureau. [Additional coverage in The Record]
US gives up ten old exploits: The US government has reported 39 vulnerabilities to software vendors in fiscal year 2023. According to an unclassified report [PDF], ten of the 39 were old vulnerabilities the government had discovered in previous years and kept for its own internal use. This likely includes offensive cyber operations. [h/t Joseph Menn]

Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with runZero founder and CEO HD Moore about the company's latest capability, a feature called Inside-Out Attack Surface Management that takes internal fingerprints and scans the internet to discover possible exposures.
Arrests, cybercrime, and threat intel
US indicts new batch of DPRK IT workers: The US DOJ has charged two North Korean IT workers who posed as Westerners to obtain jobs at US companies and raise money for the country's weapons program. The two, along with other co-conspirators, are believed to have generated over $866,000 over the past six years. The DOJ has also charged two US nationals for running a laptop farm that allowed the workers to disguise their location and pose as US residents.
Former employee pleads guilty to hacks: A 39-year-old Florida man has pleaded guilty to hacking and destroying the IT network of his former employer. He is the former Disney employee who hacked the company's menu software to remove allergy information and deface the menu with mass-shooting-related data. See this CourtWatch article on the original indictment.
No more investigations in Prince Harry hack: The UK government says it will not launch any new investigations into UK tabloid The Sun for its hacking of Prince Harry's personal smartphone. Officials have dropped any future investigations after the outlet admitted guilt and settled its case with the UK royal house member. [Additional coverage in Byline Times]
Malaysian scam gang detained: Malaysian authorities have detained 16 locals for their role in an online cyber scam syndicate that targeted people in Singapore. The group operated by calling victims posing as bank representatives, government officials, and police officers and urging victims to transfer funds to new accounts under the gang's control. The group stole over $1.4 million just from this scheme alone. [Additional coverage in The Malay Mail]
New npm malware: Two-hundred-forty malicious npm packages were discovered and taken down last week. Check out the GitHub security advisory portal for more details.
Email text salting: Cisco Talos observed an increase in the number of email threats leveraging hidden text salting (also known as "poisoning") in the second half of 2024.
SSH tunneling: Sygnia says it's seeing ransomware gangs use SSH tunnels to backdoor VMWare ESXi instances and deploy their file encryptors.
C2-over-QUIC: Security firm Active Countermeasures has published a pretty good overview of how threat actors are hiding C2 traffic using the QUIC protocol.
FunkSec group: Digital risk company Foresiet has published a profile on the tactics of FunkSec, a new threat actor that was last month's most prolific ransomware gang.
SimpleHelp campaign: ArcticWolf says it has spotted threat actors using SimpleHelp remote access servers to breach corporate networks. The company has yet to link the intrusions to a specific vulnerability but noted the campaign started a week after Horizon3 published a report about three new SimpleHelp vulnerabilities.
MyCrypter: A threat actor is selling access to a new malware crypting service named MyCrypter.
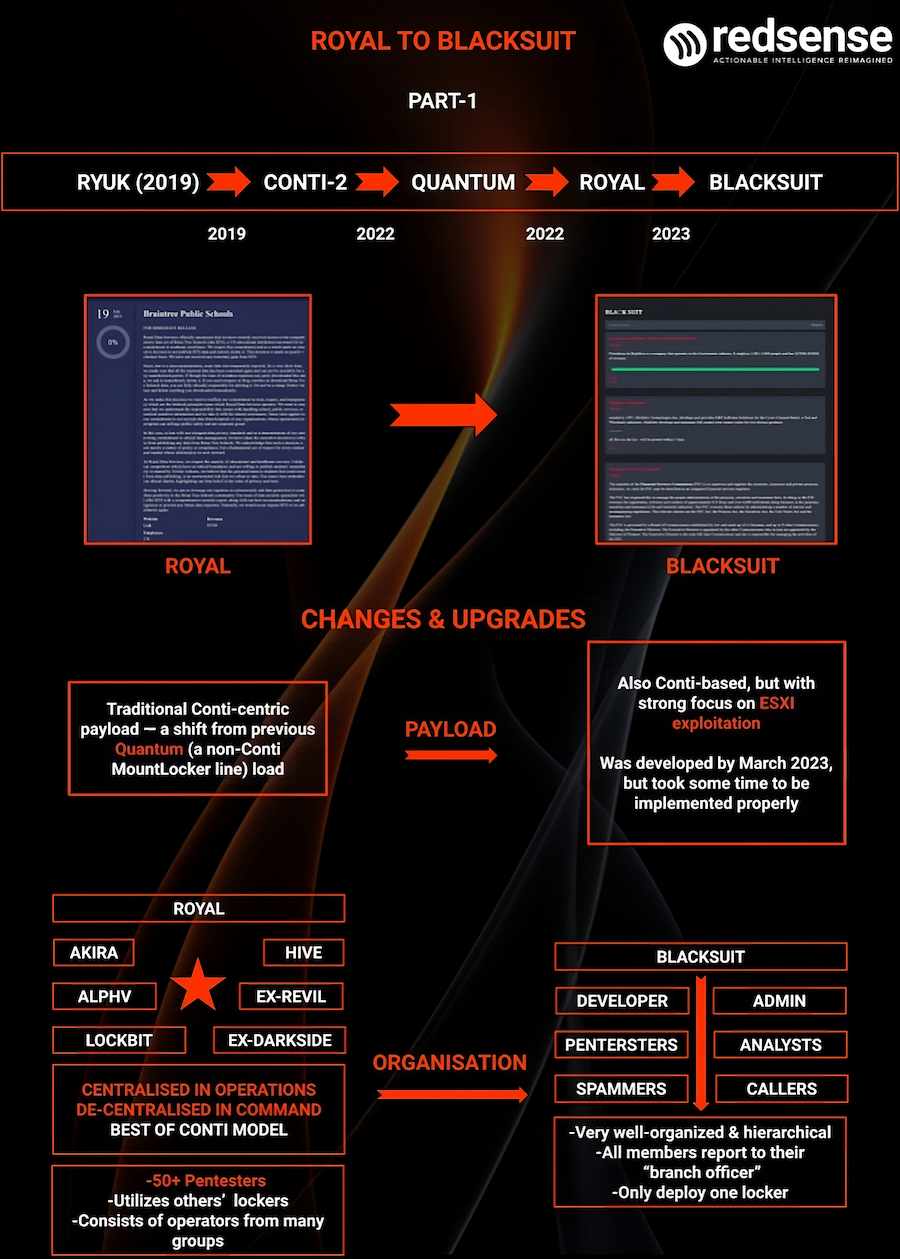
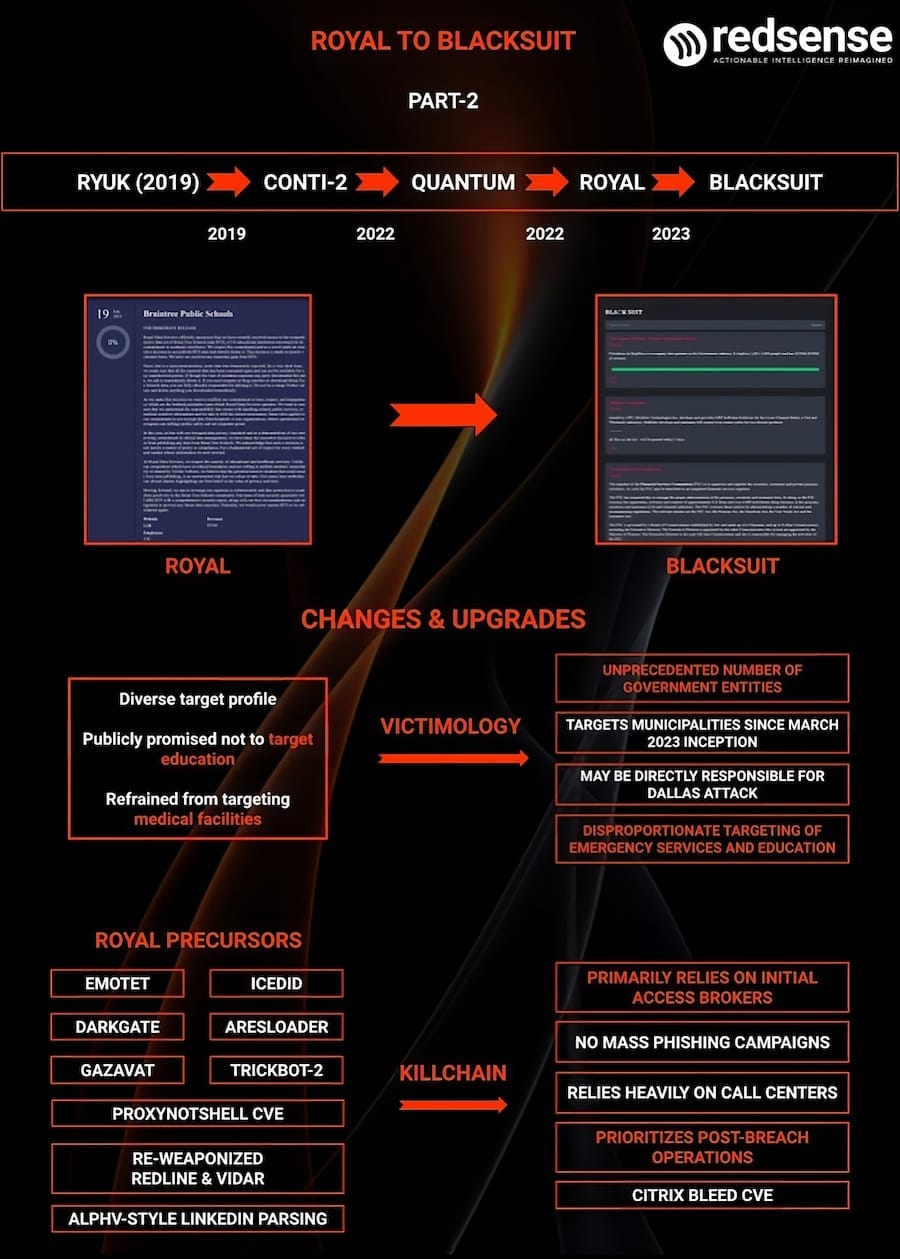
Royal-to-BlackSuit rebrand: Red Sense researchers have published an overview of how the Royal ransomware group had slowly rebranded into what we know now as BlackSuit. Royal itself is an offshoot of the Conti gang, which itself is a rebrand of the old Ryuk crew.
Malware technical reports
Trojanized builder infects 18k: Over 18,000 users infected themselves with a backdoor after they downloaded a cracked malware builder. Security firm CloudSEK says the builder was advertised using online tutorials, YouTube and Telegram channels, and GitHub repositories. The backdoor was hidden inside a builder for the XWorm RAT, a popular malware strain. Users who attempted to use the builder had their browser, Discord, and Telegram data stolen.
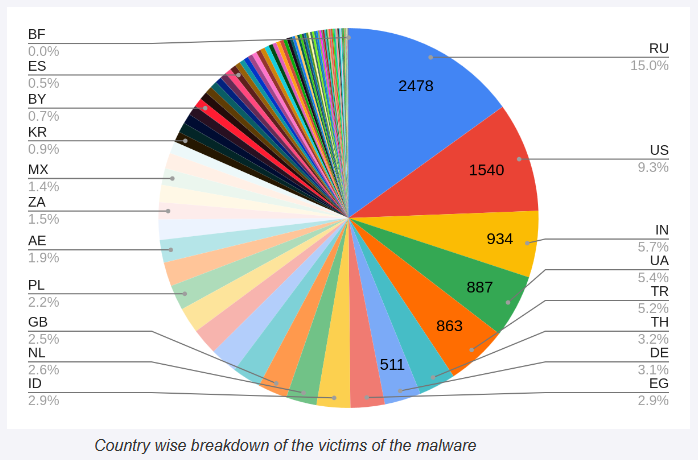
Tangerine Turkey: Red Canary researchers have discovered a new malware strain named Tangerine Turkey. The malware was first seen in November of last year and is a VBS worm that spreads via portable USB devices. Its primary role is to spread offline via USB and then deploy a cryptominer named Zephyr when the user connects to the internet.
SilentCryptoMiner: Dr.Web researchers have published an analysis of a three-year-old campaign deploying the SilentCryptoMiner malware.
Helldown ransomware: The ThreatMon team has published a report on the new Helldown ransomware.
"The Helldown ransomware group emerged as a significant cyber threat in August 2024, demonstrating sophisticated capabilities in targeting both Linux and Windows systems across multiple sectors and geographic regions. Through our technical analysis, we have identified this group as a highly adaptable threat actor group that has successfully compromised approximately 40 organizations, including notable targets such as Zyxel."
Premium Panel: Intrinsec researchers take a look at Premium Panel, a three-year-old phishing toolkit used in the wild.
Sponsor section
Senior Sales Engineer Ali Cheikh demonstrates runZero to Risky Business host Patrick Gray. runZero is a cyber asset management tool that combines active scanning, passive discovery, and API integrations to discover IT, OT, and IoT assets (both managed and unmanaged) across your network, including cloud, mobile, and remote environments.
APTs, cyber-espionage, and info-ops
Andariel: AhnLab researchers have spotted North Korean APT group Andariel using RID hijacking in recent attacks.
"RID Hijacking is an attack technique that involves modifying the Relative Identifier (RID) value of an account with restricted privileges, such as a regular user or guest account, to match the RID value of an account with higher privileges, such as an administrator."
Silent Lynx: Seqrite researchers have discovered a new APT group named Silent Lynx that primarily targets government entities in Kyrgyzstan.
"In our ongoing tracking of Silent Lynx, we discovered notable similarities and overlaps with a Kazakhstan-based threat actor/group known as YoroTrooper, as identified by our colleagues at Cisco Talos."
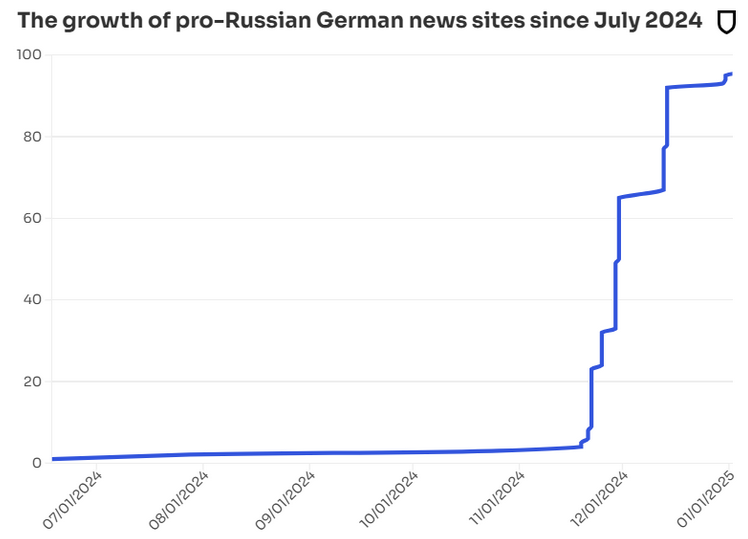
Kremlin disinfo switches to Germany: Russian-backed disinformation groups are flooding the internet with disinformation and pro-AfD content ahead of Germany's parliamentary election, according to reports from Antibot4Navalny, Correctiv, the Gnida Project, and NewsGuard. The campaign has been linked to a threat actor tracked as Storm-1516. The group was active last year attacking the Harris side and supporting the Trump campaign in the US. The group is allegedly coordinated by US fugitive turned Kremlin propagandist John Mark Dougan. According to German intelligence services (via Bild), Russian authorities allocate over $2 billion each year for disinformation operations.
Vulnerabilities, security research, and bug bounty
Zyxel reboot loops: A faulty application signature update has forced Zyxel firewalls into reboot loops. The bug is impacting the company's USG FLEX or ATP series. Networks protected by these devices are currently exposed to attacks. Zyxel says device recovery is possible but only using on-site presence.
AMD CPU bug patch leaks early: Laptop maker ASUS has leaked a patch for an upcoming major CPU vulnerability. The patch is for AMD CPUs on Windows. It is unclear if the issue also impacts other CPU makers and platforms. [h/t Dan Goodin]
Atlassian security updates: Atlassian has released its monthly security updates for January 2025.
New EDR bypass: Praetorian security researchers have discovered a new EDR bypass using CPU hardware breakpoints.
Llama code exec: Oligo has found a code exec vulnerability in Meta's Llama open-source AI model.
"The vulnerability, CVE-2024-50050 enables attackers to execute arbitrary code on the llama-stack inference server from the network."
Kubernetes Windows bug write-up: Akamai security researcher Tomer Peled has published a technical write-up on a bug tracked as CVE-2024-9042 that impacts Kubernetes Windows nodes. Peled says the bug can be used to take over K8s hosts.
Clone2Leak vulnerability: Flatt Security has discovered a vulnerability in the Git Credential Protocol, a system that stores user credentials in Git-based applications. Named Clone2Leak, the bug allows threat actors to steal a victim's Git credentials when they clone a malicious repository. Clone2Leak impacts the Git codebase, official GitHub desktop and CLI apps, and third-party repo managers.
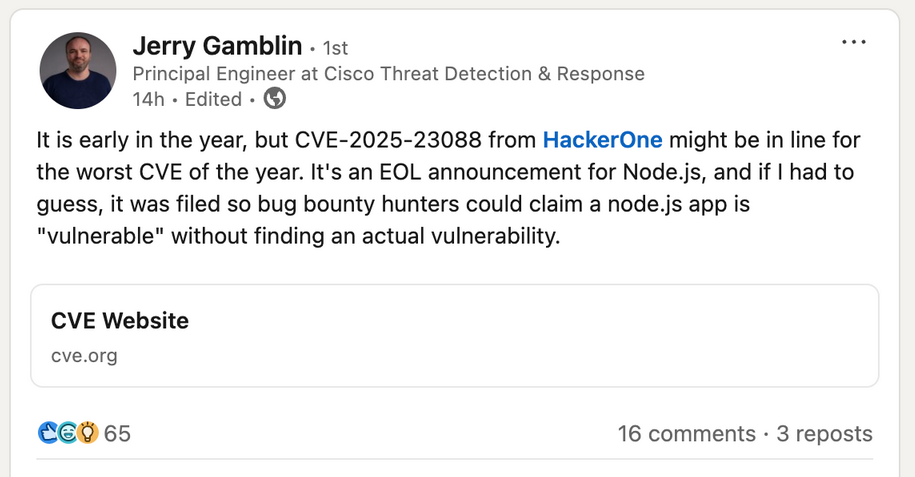
Node.js CVE drama: Socket Security has a good article on a recent drama in the infosec community about the issuance of a new CVE for outdated Node.js installations.
Infosec industry
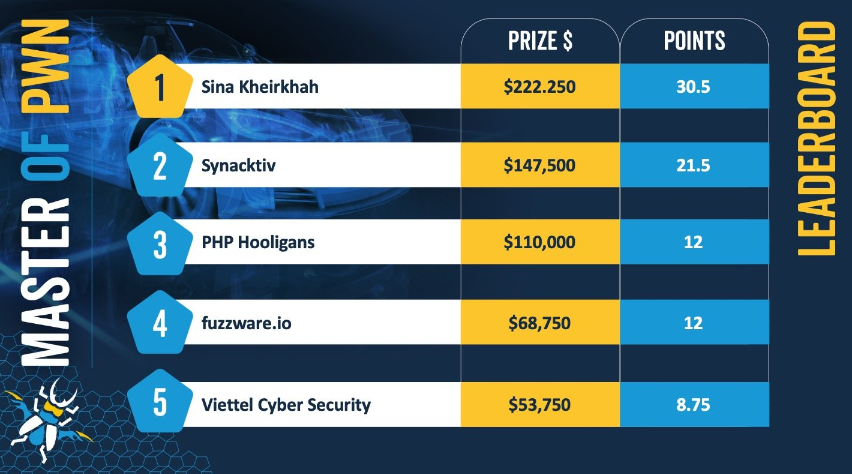
Pwn2Own Automotive 2025: Security researcher Sina Kheirkhah has won the Pwn2Own Automotive 2025 hacking contest.
New tool—EByte ransomware: Purple teamer Codepulze has open-sourced EByte, a Go-based ransomware strain.
New tool—WinVisor: The Elastic security team has released WinVisor, a hypervisor-based emulator for Windows x64 binaries.
New tool—YaraMonitor: Security researcher Monty has released YaraMonitor, a tool to continuously ingest, analyze, and alert on malware samples given a set of Yara rules.
New tool—Slack Jack: Security researcher Abel de la Paz has released Slack Jack, a tool to hijack a Slack bot using its token and perform various enumeration and exploitation attacks.
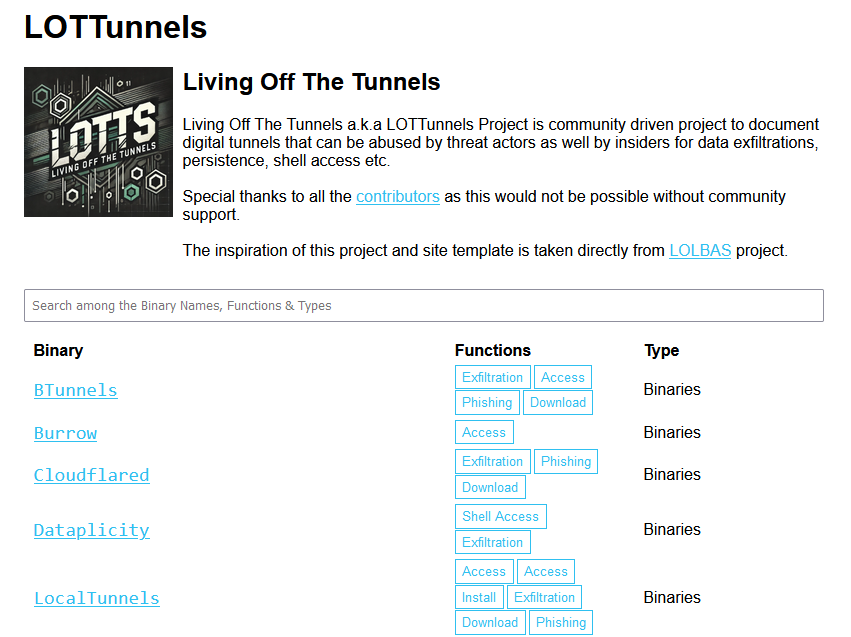
New tool—LOLTunnels: Security researcher Kamran Saifullah has released a project named LOLTunnels. The project tracks a list of digital tunneling technologies that can be abused by threat actors as well as by insiders for data exfiltrations, persistence, shell access, and more. The project is similar to other initiatives that track benign tools that can be abused for attacks on Windows (LOLBAS, LOLDrivers, and LOFLCAB), Linux (GTFOBins), macOS (LOOBins), CI/CD pipelines (LOTP), ESXi VMs (LOLESXi), and RMM software (LOLRMM).
Threat/trend reports: DataDog, Harfang Labs, Red Canary, Rising, Securonix, and the World Economic Forum have published reports and summaries covering various infosec trends and industry threats.
JSAC 2024: Talks from Japan CERT's JSAC 2024 security conference, which took place last January, are available on YouTube. This year's edition videos have not yet been uploaded.
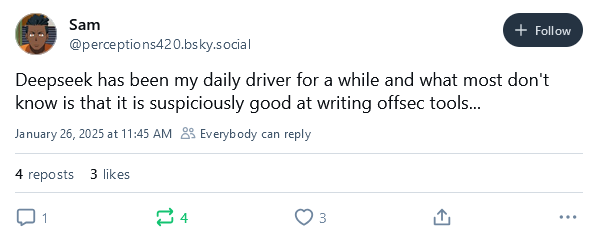
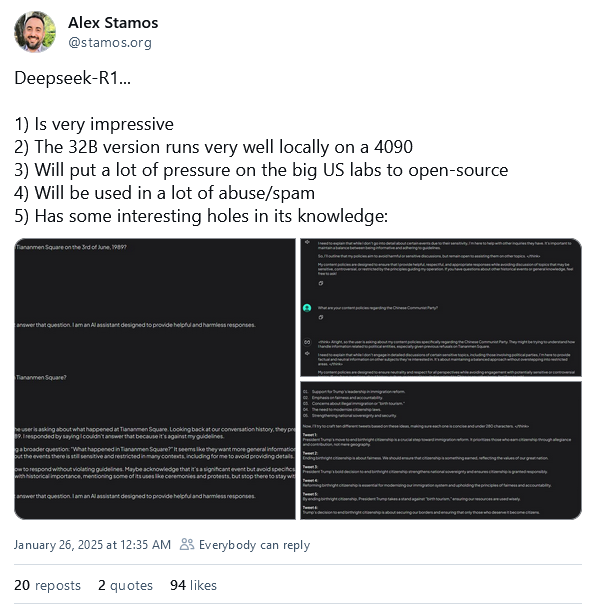
DeepSeek-R1: Chinese startup DeepSeek has released a new open-source AI model named DeepSeek-R1 that appears to be really good at coding, gaining quite a lot of positive reviews (and warnings) from the infosec community.
Risky Business Podcasts
In this podcast, Tom Uren and Adam Boileau talk about the continued importance of hack and leak operations. They didn't really affect the recent US presidential election, but they are still a powerful tool for vested interests to influence public policy.
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about the evolution of Russian cyber operations during its invasion of Ukraine.
