Risky Bulletin Newsletter
May 26, 2025
Risky Bulletin: SVG use for phishing explodes in 2025
Written by

News Editor
This newsletter is brought to you by Sublime Security, an email security platform that's not a black box. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
Over the course of the past six months, the SVG image format has become a favorite method of hiding and delivering malicious code for email phishing campaigns.
More than a dozen cybersecurity firms have now noted the rise in SVG payloads in their email security detections: AhnLab, Cloudflare, Forcepoint, Intezer, Kaspersky, Keep Aware, KnowBe4, Mimecast, Sophos, Sublime Security, Trustwave, and VIPRE.
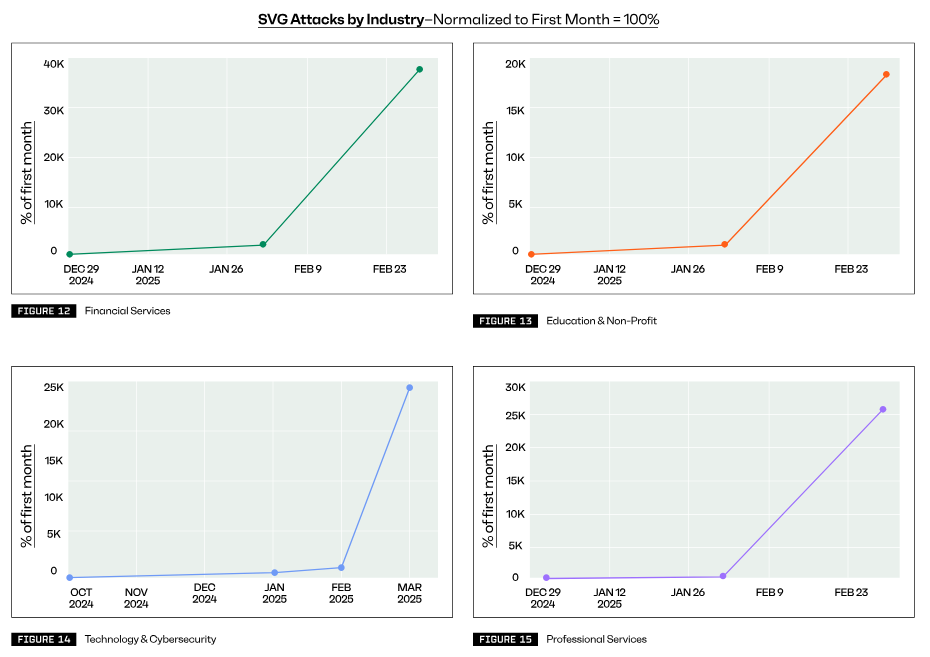
In its Q1 2025 trends report, Sublime Security says SVG payloads now account for 1% of all phishing attempts the company sees.
While two reports warned about a rise in SVG payloads in November last year, that was only a prelude for the explosion that came this year.
The same Sublime says that SVG payloads in phishing emails saw a massive 47,000% rise this year compared to the last quarter of 2024.
The reason for this massive uptick lies in the image format itself—which is less than an image and more like ActiveX for the browser, reborn.
Inherently, SVG is an XML-based file that renders geometric shapes using mathematical equations. There is no actual image. An app—in this case, a browser or an email client—reads the SVG code and renders an image from the contained equations. SVGs are just pure code with no actual bitmap pixels. Everything is drawn on the screen at runtime. Your app sees the SVGs, reads it, and executes the code.
But what many people don't know, and something that threat actors recently realized, is that you can also store all other kinds of other type of code in an SVG file. For example, you can store HTML and JavaScript code, which are the building blocks of the modern web.
Why bother luring users to your phishing pages with your cleverly worded emails when you can bring the phishing page inside the SVG? Well, threat actors are doing exactly this.
They are embedding HTML and JavaScript code in the SVGs they send to your inbox. Think of a logo in someone's signature. When you open the message, the browser or email client reads that code and renders a phishing page locally, on your PC, without you needing to visit a malicious domain. These local phishing pages will send any credentials you enter to the attacker, and some can even bypass multi-factor authentication.
While this is complex, SVGs are also used to automatically redirect a victim to a phishing URL without them needing to click anything. Victims just open their email, the SVG executes, and the user is sent without notice to a phishing domain.
Cloudflare's security team puts it very concisely when they describe SVGs not as images but as "programamable documents."
"When rendered in a browser, they aren't just images - they become active content, capable of executing scripts and other manipulative behavior. In other words, SVGs are more than just static images; they are also programmable documents."
While we've seen various "payloads" come and go when it comes to phishing variety, this one seems one that's likely to stay, mainly due to its effectiveness.
I don't see this going down any time soon unless major email providers like Gmail, Hotmail, and iCloud Mail start aggressively scanning SVG content, ban SVG interactive content, or put their foot down and ban SVGs outright.
Risky Business Podcasts
Risky Business is now on YouTube with video versions of our main podcasts. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
Silk Typhoon hacked Commvault: A Chinese cyber-espionage group known as Silk Typhoon hacked backup software company Commvault. The group gained access to Commvault's Azure servers in February. According to CISA, the intrusion was part of a larger campaign targeting SaaS providers. Silk Typhoon (APT27) previously hacked the US Treasury Department at the end of last year. [Additional coverage in NextGov]
General tech and privacy
Twitter outage: Twitter experienced a major outage on Friday after a data center fire. [Additional coverage in The Verge]
Government, politics, and policy
US government to audit NIST NVD: The US government has launched an audit of the National Institute of Standards and Technologies (NIST) over its management of the US National Vulnerability Database (NVD). The audit will target NIST processes for managing NVD submissions after the agency developed a huge backlog last year. The audit will be conducted by the US Department of Commerce Office of Inspector General.
Major CISA exodus: Several high-ranking officials are leaving the US Cybersecurity and Infrastructure Security Agency at the end of May. The heads of three of CISA's six main divisions and leaders of most of CISA offices are departing. Top CISA officers for finance, strategy, human resources, and contracting are also leaving, according to an internal memo obtained by the Washington Post.
Vietnam blocks Telegram: The Vietnamese government has ordered local telecom companies to block access to the Telegram instant messenger. Officials say the company has failed to comply with law enforcement requests in cases related to fraud, drug trafficking, and terrorism. The ban enters into effect on June 2. Telegram told Reuters it was "surprised" by Hanoi's decision.
Russia deploys mobile jammers to stop exam cheating: Russian authorities deployed over 11,500 mobile signal jammers in schools to prevent students from cheating during the country's yearly exams. Mobile jammers were installed in exam rooms and even in some bathrooms. They were designed to stop phone signals and block students from cheating using wireless hidden earpieces. [Additional coverage in TASS]
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Bobby Filar, Head of Machine Learning at Sublime Security. Bobby takes us through the rising problem of spam bombing, or email bombing, a technique threat actors are increasingly using for initial access into corporate environments.
Arrests, cybercrime, and threat intel
CryLock ransomware trial in Belgium: Belgian authorities are seeking 13 and 10 years in prison, respectively, for the Russian couple behind the CryLock ransomware. The man developed the ransomware, and the woman advertised it online and negotiated with victims. The couple are believed to have infected over 400,000 users and earned over €3 million from attacks. The two were detained in Spain in 2023 and extradited to Belgium to face trial. [Additional coverage in VRT]
Russian leaker sentenced: Russian authorities have sentenced a man to 14 years in prison for uploading the personal data of Russian citizens to a Telegram channel managed by Ukraine intelligence. The man, 37, worked as a programmer for one of the hospitals in Russia's Irkutsk region. The man was found guilty of high treason after the data also included details of Russian military members. [Additional coverage in TASS]
ATM skimmers detained in Australia: The Australian Federal Police has arrested two Romanian nationals for installing skimming devices at ATMs across Sydney and the Illawarra region. The two also allegedly cloned bank cards with the stolen data and stole more than AUS$800,000 from victims. The two had been under investigation for a month before they were detained after multiple banks filed reports about tampered ATMs.

Chinese hacktivism scene: The Oxford China Policy Lab has published an analysis of the Chinese hacktivism scene, from its grassroots in the 90s to recent leaks from government systems and contractors as a silent sign of dissent against an ever-increasing oppressive regime.
"The increase in state-critical hacktivism demonstrates that a new generation has returned to hacking to freely share sentiments that would otherwise be unacceptable. Through carefully coordinated leaks, these hacktivists can draw international attention to the scale of China's surveillance apparatus."
Lumma Stealer says authorities wiped its backups: Law enforcement agencies allegedly hacked the Lumma Stealer backend servers after they couldn't physically seize the group's infrastructure earlier this month. In a message posted in their Telegram channel, the Lumma Stealer admins claim the FBI used an exploit in Dell's iDRAC technology to collect data and wipe backup servers twice. Lumma claims law enforcement deployed a phishing page on its portal to collect data on customers when they didn't find what they were looking for. This happened roughly a week before authorities took down the Lumma Stealer operation.
Silent ransom group goes after law firms: The Silent data extortion has been targeting US companies with callback phishing attacks for over two years. The FBI says the group calls employees with urgent messages and tricks them into infecting themselves with malware, stealing data, and ransoming their victims. While attacks have hit multiple sectors, most victims are US law firms. The group is also known as Luna Moth. [FBI industry alert/PDF]
New npm malware: Three hundred fifty malicious npm packages were discovered and taken down last week. Check out the GitHub security advisory portal for more details. Socket Security has a report on 60 of these that could exfiltrate an infected user's hostname information.
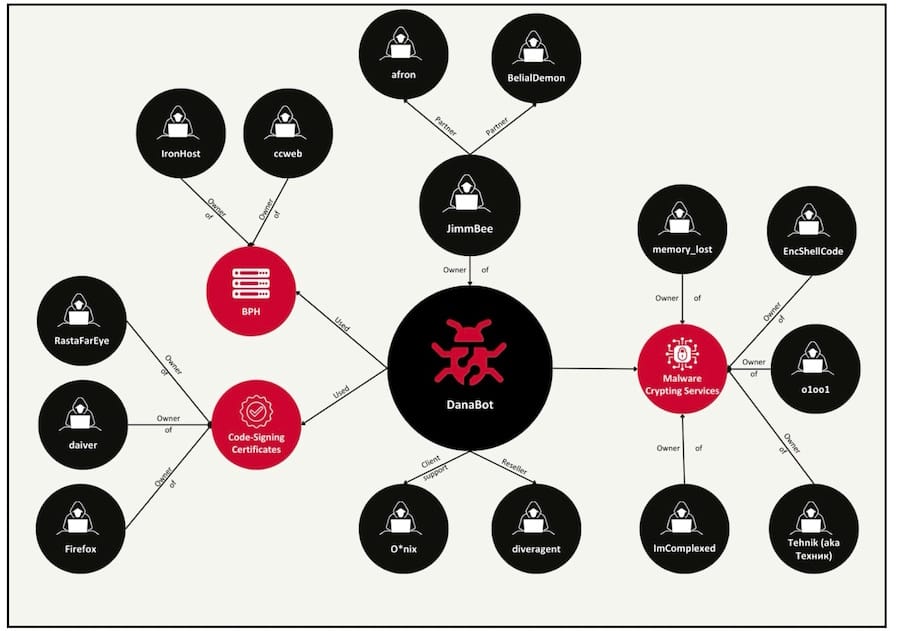
DanaBot group: Intel471 looks at the structure of the DanaBot botnet, which was dismantled by authorities last week.
Malware technical reports
New NodeSnake variants: Quorum Cyber has spotted two new versions of NodeSnake, a RAT previously used by the Interlock ransomware group.
PyBitmessage backdoor: AhnLab has published a breakdown of a new backdoor deployed alongside a cryptominer on hacked servers. The backdoor uses the Bitmessage P2P protocol for C&C communications.
DOUBLELOADER and ALCATRAZ: The Elastic security team has published a report looking at the DOUBLELOADER malware and its use of the ALCATRAZ open-source obfuscator.
AppleProcessHub Stealer: Kandji researchers have spotted a new macOS infostealer, currently tracked as AppleProcessHub Stealer.
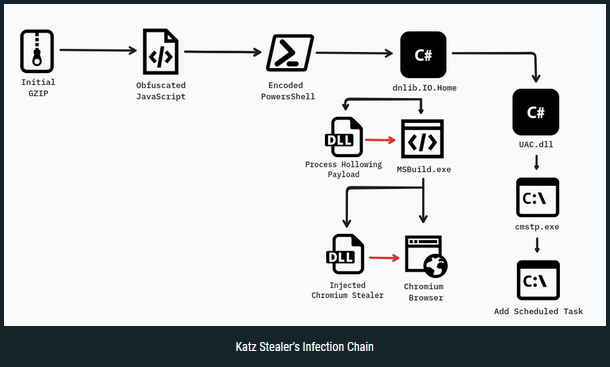
Katz Stealer: Nextron Systems has published an analysis of Katz Stealer, a new infostealer sold through a MaaS model.
Sponsor section
Gain essential visibility into evolving email threats, targeted industry attacks, and sophisticated evasion techniques observed across Q1 2025. Get the "Sublime Email Threat Research Report: Emerging trends & key insights" report here.
APTs, cyber-espionage, and info-ops
Sandworm was top APT in Ukraine: Ukraine's SSSCIP agency has published an overview report on the cyber threats it faced three years since Russia's invasion of Ukraine. The agency says that, by far, the most active Russian APT has been Sandworm (UAC-0002). Another interesting tidbit, Russia hacked 12 Ukrainian telecoms in the span of three months back in 2023.
Romanian post-election info-ops: DFRLab has spotted a cluster of fake news sites pushing info-ops related to the Romanian election. The message is that the "election was stolen" after the pro-Kremlin candidate lost. Sounds familiar?
Info-ops targeting Australia and Canada: A Russian disinformation group named Pravda has generated large amounts of English fake news content about the 2025 Australian and Canadian elections. Most of the content was shared on Russian social network VK, where it got limited visibility. Disinformation study group Open Measures believes the content was created to poison English LLMs with pro-Kremlin content.
Careto APT linked to Spain: The Spanish government is behind a cyber-espionage group known as Careto (The Mask). The group has been active since at least 2007, but its operations are rare and far between. Its primary targets have been Spain's neighbors and Spanish-speaking countries. Talking to TechCrunch, Kaspersky described the group as very small compared to Lazarus and APT41 but far more sophisticated.
UAC-0050 phishing campaign: The Digital Security Lab Ukraine has spotted a massive phishing campaign posing as the Ukrainian tax service and trying to infect users with the NetSupport RAT. The organization tentatively linked the campaign to UAC-0050.
New Kimsuky op: AhnLab has published a report on a new malware delivery campaign linked to the Kimsuky APT that abuses the certificate of a legitimate company to avoid sample detection.
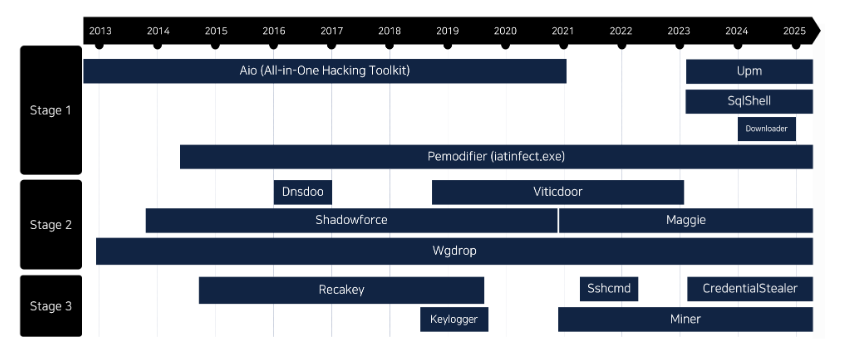
TA-ShadowCricket profile: AhnLab and South Korea's National Cyber Security Center (NCSC) have published a profile on TA-ShadowCricket (Shadow Force), a suspected Chinese threat actor that has been active since 2012. The group mainly targets MSSQL servers, where it deploys backdoors. AhnLab says the group operates at the line between cyber espionage and financial attacks since it also deploys cryptominers on infected hosts.
Vulnerabilities, security research, and bug bounty
Atlassian security updates: Atlassian released eight security updates last week, part of the company's May Patch Tuesday.
vBulletin RCE write-up: Security researcher Egidio Romano has published an analysis of an RCE in the vBulletin forum software that was patched last year. The RCE allows attackers to abuse a core PHP 8.1.x feature to abuse vBulletin's internal API.
tachy0n zero-day impact on Apple: iOS security researcher Siguza has published a retrospective on how the tachy0n exploit changed Apple's stance on iOS security and all the protections it added following it.
"But the allocator wasn't the only thing that changed, it was the approach to security as a whole. Apple no longer just patches bugs, they patch strategies now. You were spraying kmsg structs as a memory corruption target as part of your exploit? Well, those are signed now, so that any tampering with them will panic the kernel. You were using pipe buffers to build a stable kernel r/w interface? Too bad, those pointers are PAC'ed now. Virtually any time you used an unrelated object as a victim, Apple would go and harden that object type. This obviously made developing exploits much more challenging, to the point where exploitation strategies were soon more valuable than the initial memory corruption 0days."
Fascinating retrospective read on an iOS exploit, but the most interesting part might be the Aftermath section. Apparently Apple shifted gears with iOS 14 and started implementing deep mitigations, which despite not perfect really changed the game. blog.siguza.net/tachy0n/#:~:...
— Filippo Valsorda (@filippo.abyssdomain.expert) 2025-05-25T11:32:34.573Z
Android code exec: GitHub's Man Yue Mo has published a technical analysis of CVE-2025-0072, a vulnerability in the Arm Mali GPU that can be used to bypass the Android Memory Tagging Extension (MTE) memory safety protection and run malicious code in the kernel.
Election ballot research: Princeton's CITP team looks at the idea of using patterns, grooves or UV particles, in the ballot paper to track voting fraud attempts.
AI finds Linux kernel flaw: Security researcher Sean Heelan used OpenAI's o3 API to find and help patch a vulnerability in the Linux kernel's SMBv3 component.
Infosec industry
New tool—Claws: FinTech company Betterment has released Claws, a static analysis tool to help you write safer Github Workflows.
New tool—SharpSuccessor: IBM X-Force's Logan Goins has released SharpSuccessor, a .NET tool for executing BadSuccessor attacks against Windows Server 2025.
Threat/trend reports: Dragos, Messente, NCC Group, Red Canary, SSSCIP, ThreatMon, and TIOBE Index have recently published reports and summaries covering various infosec trends and industry threats.
Risky Business podcasts
Tom Uren and Patrick Gray talk about how Telegram took down the two largest ever criminal marketplaces recently. The pair discuss why Telegram is now cooperating with authorities after historically being reluctant and whether this assistance will continue.
In this edition of Between Two Nerds, Tom Uren and The Grugq examine what makes it hard for even competent hackers to contribute to state-backed espionage agencies.
