Risky Bulletin Newsletter
February 26, 2025
Risky Bulletin: Signal threatens to leave Sweden over backdoor request
Written by

News Editor
This newsletter is brought to you by vulnerability management and analysis platform Nucleus Security. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
Signal Foundation president Meredith Whittaker says the secure messaging app will leave Sweden if the government there passes a new surveillance bill.
The Swedish government is scheduled to discuss a bill next month that would force communication providers to allow police and security services access to message content.
Whittaker told Swedish national public television SVT that adding such a backdoor would undermine its entire network and users across the world, not just in Sweden.
This is the second time the Signal CEO has threatened to leave a country over backdoor demands. In 2023, Whittaker also threatened to leave the UK if the government mandated backdoors in its Online Safety Act.
The UK government backed out of the push after Meta also threatened to pull services from the UK market.
The situation in Sweden is also a little bit ironic since the country's armed forces are known to be a big adopter of Signal due to its secure messaging capabilities.
Swedish officials have repeatedly claimed it has become a top priority to access encrypted communications data after the country has seen a rise in criminal activity over the past decade.
Earlier this month, the British government also pressed Apple for access to encrypted cloud data. Instead of complying and degrading their cloud encryption worldwide, Apple removed the option for UK users to encrypt their iCloud backups.
Risky Business Podcasts
Risky Business is now on YouTube with video versions of our main podcasts. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
Paratus Namibia ransomware attack: A ransomware gang has breached the network of Namibian telecommunications provider Paratus. The incident took place last week, and the company says hackers stole over 84GB of data. The Akira ransomware gang took credit for the attack. Paratus is the second Namibian telco to get hacked by a ransomware group over the past two months. The Hunters International group also ransomed Telecom Namibia in December. [Additional coverage in The Namibian]
LANIT hack: Russia's CERT says that LANIT, a major software provider for the Russian financial sector, is dealing with a major cyberattack. The agency has asked LANIT customers to change passwords for any of the LANIT systems they use.
Orange breach: French telecommunications giant Orange has confirmed a security breach after hackers published some internal data on an underground hacking forum. The company says the breach exposed internal documents, user records, and employee data. Most of the data is from Orange's Romanian branch. The hacker published the data after an unsuccessful extortion attempt. The attacker claims they're a member of the HellCat ransomware group. [Additional coverage in BleepingComputer]
DISA breach: US employee screening service DISA Global Solutions has disclosed a data breach that exposed the personal details of 3.3 million users.
Italian priest targeted with spyware: An Italian priest close to the Pope has revealed he was the target of advanced spyware. Father Mattia Ferrari says he received a security alert from Meta that his account was targeted "by unidentified government entities." Father Ferrari serves as chaplain on a migrant rescue ship owned by an NGO. The NGO's founder revealed earlier this month that he was one of the 90 victims targeted with spyware made by the Israel-based company Paragon Solutions. The attacks were initially revealed by Meta's WhatsApp team. Paragon Solutions cut off the Italian government's access to its surveillance tools after several Italian activists said they received Meta's alerts about the attacks. [Additional coverage in The Guardian]
HUD defacements: TV screens at the US Department of Housing and Urban Development were defaced to show a short (allegedly) AI-generated video of President Donald Trump passionately kissing Elon Musk's feet. The video played on screens on the day the agency ended work-from-home programs. Staff went to every floor to unplug the screens after they couldn't figure out how to stop the video loop. [Additional coverage in The Independent]

General tech and privacy
Google to use QR codes for authentication: Google will deprecate SMS messages in favor of QR codes for Gmail logins. The company will ask users to scan a QR code with their phone when logging in or creating a new Gmail account. The change is designed to counter SIM swapping and SMS traffic pumping schemes. The move has no official launch date and is scheduled to arrive "over the next few months." [Additional coverage in Forbes]
Google disabled low-qual results warning: Ahead of the 2024 US election, Google apparently turned off warnings for when people were viewing low-quality search results, a boon for conspiracy theorists and mis/disinformation peddlers. [Additional coverage in Platformer]
Tower dumps ruled illegal: A Mississippi judge has ruled that a law enforcement technique named tower dumps is illegal and makes a "mockery of the Fourth Amendment." The technique involves dumping large quantities of mobile data from cellular towers to find potential criminal activity in nearby locations. The technique has been used for years across the US. The ruling comes six months after the US Court of Appeals for the Fifth Circuit deemed that a similarly broad search technique called geofence warrants is also illegal and unconstitutional. [Additional coverage in CourtWatch]
Wyden rails against bait-and-switch tactics: US Senator Ron Wyden has asked the FTC to investigate tech companies that use bait-and-switch tactics. This refers to the sale of digital goods that vendors reserve the right to pull from a user's inventory at any time. Wyden says the FTC's investigation should target companies that sell TV, e-books, movies, music, and video games.
FTC announces Avast refunds: The FTC emailed almost 3.7 million Avast customers who bought the company's antivirus and are now entitled to refunds due to the company illegally selling their personal data. Avast has agreed to pay up to $16.5 million in refunds in a settlement with the FTC last year. US users can claim a refund by June 5.
Outline updates: Alphabet's Jigsaw has updated its Outline anti-censorship technology with new evasion technologies, such as the Shadowsocks-over-WebSockets protocol.
Apple cuts Russian access to ADEP: Apple has cut off access to the Apple Developer Enterprise Program (ADEP) for Russian developers. The platform allowed companies to develop and distribute iOS apps for use within corporate networks without publishing them on the App Store. Apple allegedly previously warned Russian devs of the impending ban. [Additional coverage in RBC]
Microsoft launches ad-supported Office: Microsoft has quietly launched free, ad-supported versions of Office apps Word, PowerPoint, and Excel. The apps have limited features, play video ads, and only let users save files to OneDrive. [Additional coverage in Beebom]
Government, politics, and policy
EU sanctions DPRK RGB chief: The European Union has imposed sanctions on Lee Chang Ho, a general in the North Korean army and the head of the country's intelligence service, the Korean Reconnaissance General Bureau. Officials say Lee commanded North Korean soldiers in Ukraine and previously led cyber-attack units such as the Lazarus and Kimsuky APTs. Lee was one of several North Koreans included in the EU's 16th sanctions package against Russia over its war in Ukraine. [Additional coverage in The Record]
DOGE sets its sights on NIST: A WIRED report claims that Musk's DOGE "agency" (or whatever that thing is) has set its sights on the US National Institute of Standards and Technology and that around 500 employees are set to be fired.
Hikvision surveillance network in Tehran: The Iranian government is installing a sprawling network of Hikvision security cameras across its capital of Tehran, complete with license plate readers and facial recognition features. [Additional coverage via Nariman Gharib]
Australia bans Kaspersky: The Australian government has banned the use of Kaspersky products on government IT systems. Government agencies must uninstall existing Kaspersky software by April 1. Officials said the software poses an unacceptable security risk to Australian government networks, such as foreign interference, espionage, and sabotage. The US and the UK banned the use of Kaspersky on government systems in 2017, and Canada banned it in 2023. [See government order/PDF]

Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Aaron Attarzadeh, Enterprise Security Engineer at Nucleus. Aaron goes into new concepts for the vulnerability management scene, such as asset correlation and asset linking.
Arrests, cybercrime, and threat intel
US charges Genesis user: The US government has charged a US national named Andrew Shenkosky, who purchased stolen credentials from Genesis Market to resell and steal funds from user accounts.
The Com member convicted: A UK court has convicted Richard Ehiemere, 21, for his activity in The Com, where he allegedly exchanged CSAM imagery and discussed hacking and selling hacked data. [Additional coverage in This Is Local London]
NCA has released arrest footage after securing the conviction of another member of the harrassment and hacking group called The Com. Richard Ehiemere, 21, was part of the CVLT group as a teenager. He was found to have made 29 sexual images of children and evidence of hacking campaigns on his comp
— Joe Tidy BBC News (@joetidy.bsky.social) 2025-02-25T17:33:44.461Z
Myanmar scam center torturer threats: A Myanmar military-aligned border force has warned that it would detain anyone believed to have been engaged in torture at cyber scam compounds. [Additional coverage in Irrawaddy] [h/t CyberScamMonitor]
2024 OT/ICS attacks: ICS security firm Dragos has published its yearly threat report, and the company says it's now tracking 23 groups with ICS/OT hacking capabilities, nine of which were active last year.

Major Twitter spam wave: Twitter is seeing a giant wave of spam these days—per reports from multiple users.
VBS enclave abuse: Akamai published research into a newly discovered attack vector in virtualization-based security (VBS) enclaves, a Windows security feature that could be abused for malicious purposes and to evade EDR detection.
Poseidon threat on macOS: A Malwarebytes report claims that Poseidon accounted for 70% of all macOS infostealer activity over the past months.
GitVenom campaign: A threat actor has created hundreds of GitHub repositories that infect users with an infostealer that collects their passwords, clipboard data, and cryptocurrency wallet information. The repositories contain functional projects that target engineers, gamers, and cryptocurrency enthusiasts. Named GitVenom, the campaign has been active for months.
Operation SalmonSlalom: Kaspersky looks at Operation SalmonSlalom, a malware delivery campaign targeting the ICS sector across APAC.
LARVA-208/EncryptHub: Prodaft has published a profile on LARVA-208 (EncryptHub), a known affiliate of the RansomHub and Blacksuit ransomware operations. The group is known to run phishing pages targeting enterprise VPN login pages.
UAC-0173 attacks: A financially motivated group (UAC-0173) is hacking notary offices in Ukraine to make changes to government state registers. CERT Ukraine believes the hacks are part of a hacker-for-hire scheme where the group makes unauthorized changes to government databases in exchange for a fee. The agency says attacks targeting Ukrainian notaries with malware have ramped up in the second half of January.
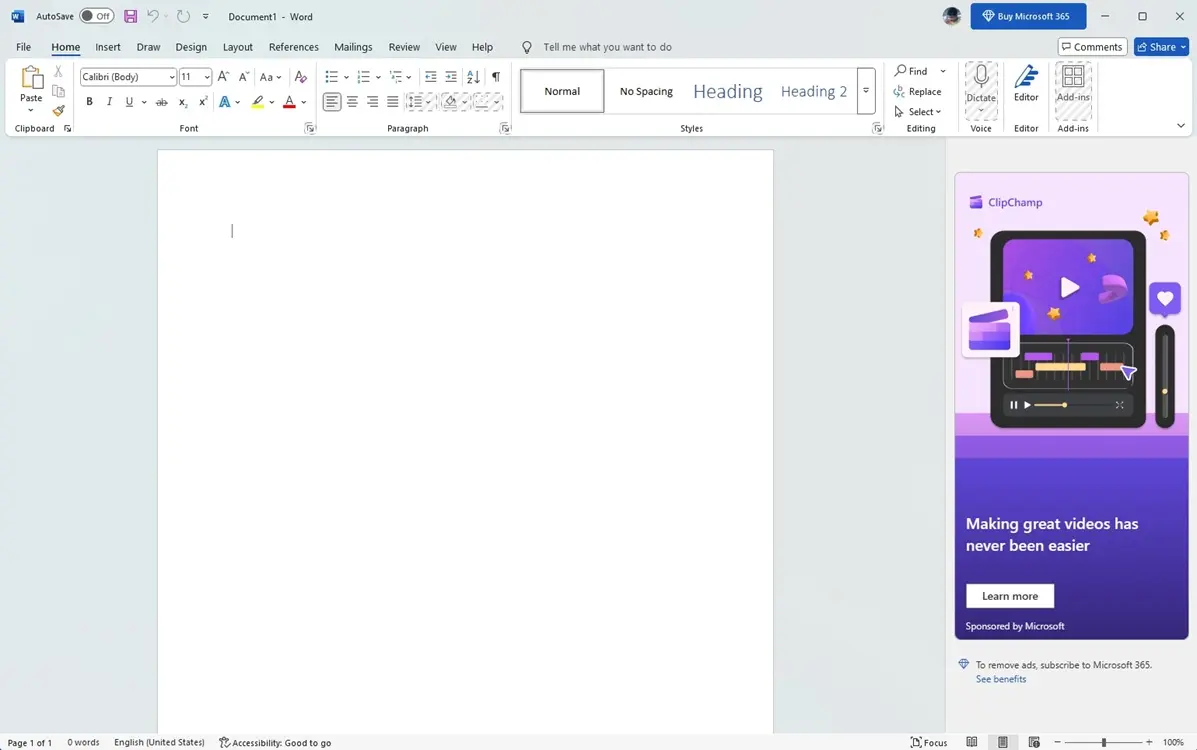
RU-UA hacktivism goes down: Three years after Russia's invasion of Ukraine, the number of hacktivist groups involved in the conflict has gone down from its peak of 130 to only 80 active groups, per CyberKnow. The most active group remains Noname057(16), a so-called faketivist group linked to Russian military intelligence services.
Malware technical reports
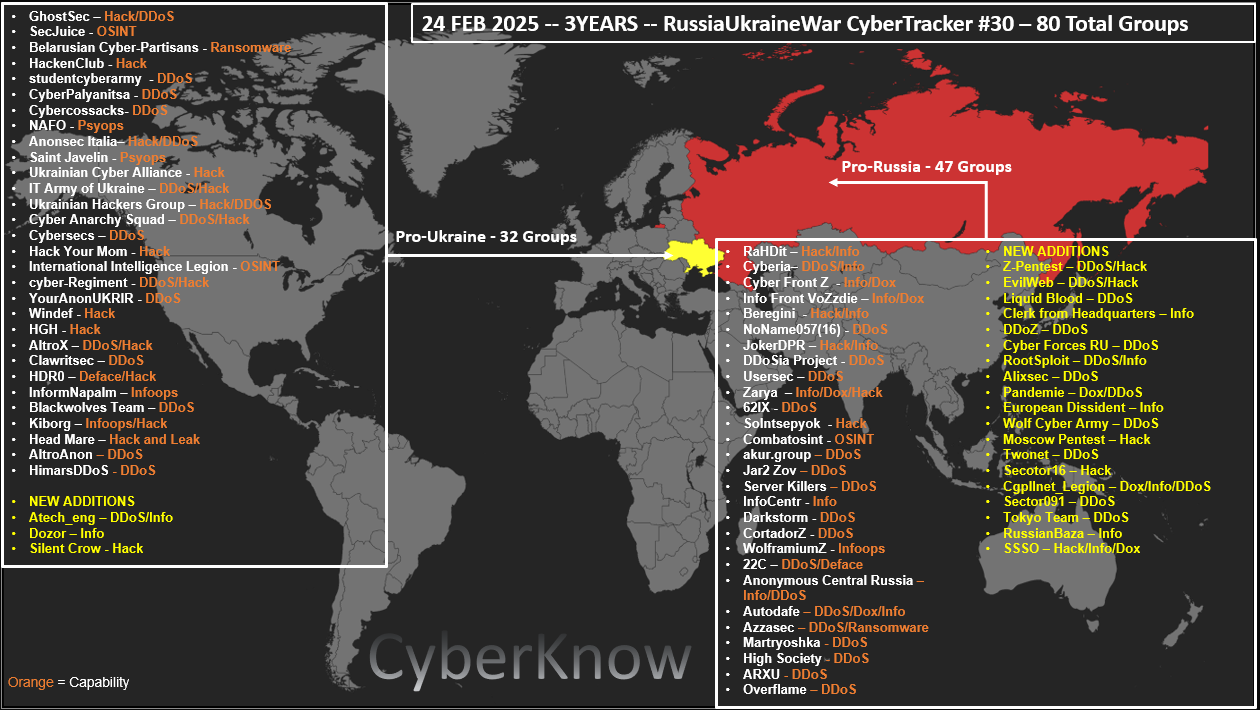
TgToxic Android banker: Intel471 looks at how the TgToxic Android banking trojan was updated to use a DGA instead of a dead-drop C2 system.
Lockbit infection: The DFIR Report team has published an analysis of a Lockbit ransomware infection that came in via a hacked Atlassian Confluence server, exploited via CVE-2023-22527.
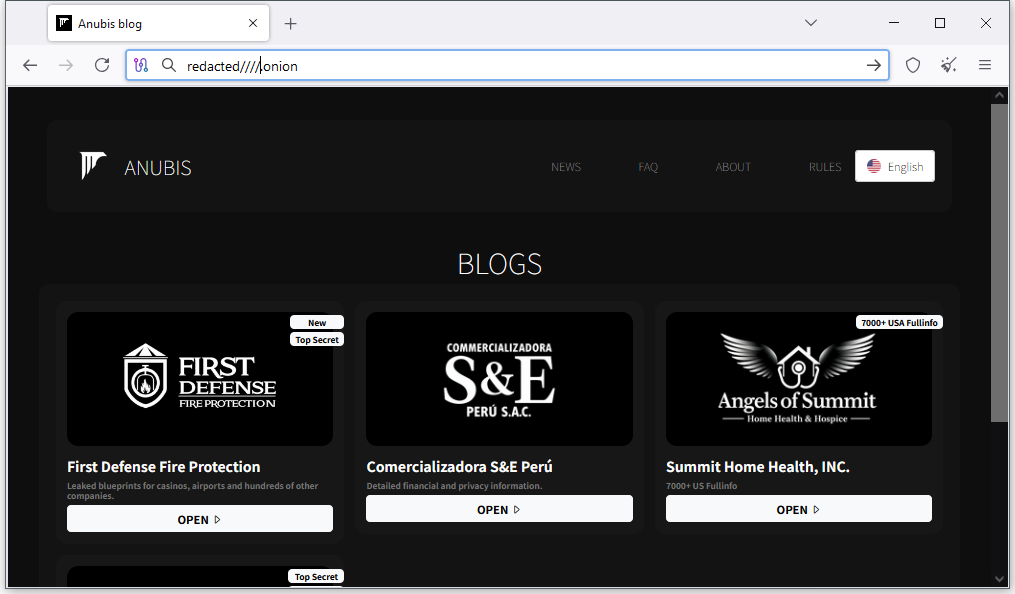
Anubis ransomware: KELA has spotted the launch of a new ransomware group named Anubis. So far, the group has only four victims listed on its dark web leak site and is heavily advertising its service on XSS, Twitter, and Ramp.
Truesight EDR killer campaign: Check Point has uncovered a malware gang that is behind a large-scale campaign that deploys an outdated driver on infected systems. The group is using the driver to gain SYSTEM privileges on the infected hosts and disable local antivirus and EDR products before deploying its own malware. The campaign installs an old Truesight driver from the RogueKiller, a security tool ironically designed to remove rootkits and malware. Check Point says that most victims are located in Asia, with around three-quarters located in China.
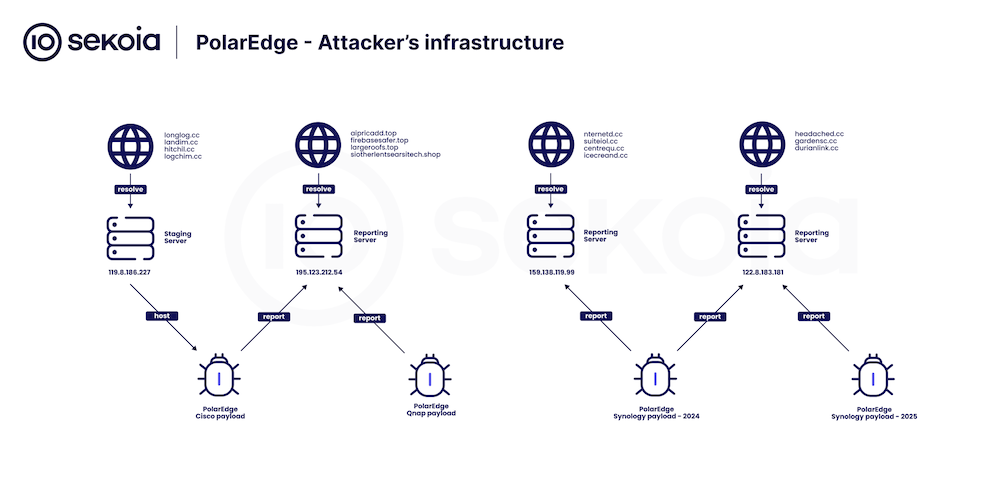
PolarEdge botnet: A new botnet named PolarEdge has secretly infected over 2,000 devices over the past two years. French security firm Sekoia has found the botnet's malware on Cisco and ASUS routers, and QNAP and Synology NAS devices. The botnet has been active since at least the end of 2023, and most of its infected devices are based in the US. Its creator and purpose are still unknown.
Mirai brute-force botnet: A botnet of over 130,000 compromised devices is conducting password-spray attacks against Microsoft 365 accounts. The botnet targets an account's Basic Authentication feature to evade multi-factor authentication prompts. The botnet was built with the Mirai malware and uses credentials stolen by infostealers. According to SecurityScorecard, clues suggest ties to China-affiliated threat actors.
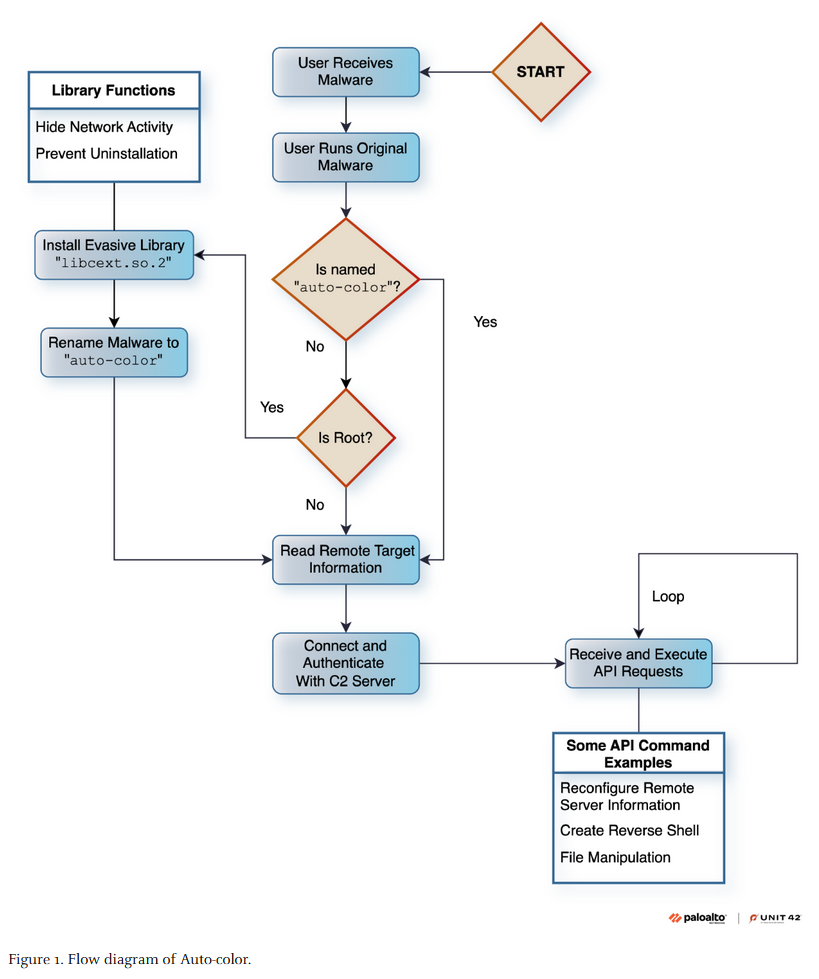
Auto-color backdoor: Palo Alto Networks has discovered a new Linux backdoor named Auto-color that was deployed in the wild at the end of last year. The malware was used to target universities and government offices in North America and Asia. The company has yet to find out how Auto-color is deployed on hacked networks.
Sponsor section
Nucleus Security's COO Scott Kuffer shows Patrick Gray their vulnerability management platform. It ingests scan outputs from a number of vulnerability identification tools, normalizes that information and then allows vulnerability management teams to do things like assign responsibility for certain types of bugs to the correct people.
APTs, cyber-espionage, and info-ops
Lazarus Bybit hack infra: Security firm Silent Push claims it found some of the server and phishing infrastructure used by the Lazarus APT in its mega hack of cryptocurrency exchange Bybit last week.
Erudite Mogwai: Rostelecom's security team has published a report on the recent campaigns of Erudite Mogwai, a Chinese APT group that has been targeting Russia since 2017. The APT is also tracked as Space Pirates.
LightSpy expands capabilities: Hunt.io researchers have spotted an updated version of the LightSpy surveillance framework, a tool used by an eponymous Chinese APT. The new features include the targeting of Facebook and Instagram application database files for data extraction and the doubling of supported C2 commands from 55 to over 100.
Mustang Panda: Cado Security has published a report on a Mustang Panda APT campaign targeting the Royal Thai Police.
SilverFox APT targets DICOM viewers: A suspected China-based APT group has exploited medical devices (Philips DICOM Viewers) to deploy backdoors, keyloggers, and crypto-miners on targeted networks.
ReaverBits: Russian security firm F6 (formerly FACCT) has published a report on the attacks of a threat actor named ReaverBits against Russian companies. The final payload was a malware strain named ReaverDoor.
New Sandworm attacks: CERT Ukraine says it detected new Sandworm APT attacks targeting the suppliers of automation and process control solutions for Ukrainian critical infrastructure organizations. Targeted suppliers are located in Serbia, Czechia, and Ukraine.
Ghostwriter returns: After many reports on Ghostwriter's info-ops, SentinelOne has seen the group returning to malware delivery, this time with a campaign targeting opposition activists in Belarus as well as Ukrainian military and government organizations. The Ghostwriter APT is also tracked as UNC1151/Mandiant and UAC-0057/CERT-UA and is believed to operate out of Belarus.
"While Belarus doesn't actively participate in military campaigns in the war in Ukraine, cyber threat actors associated with it appear to have no reservation about conducting cyberespionage operations against Ukrainian targets. The campaign described in this publication also serves as confirmation that Ghostwriter is closely tied with the interests of the Belarusian government waging an aggressive pursuit of its opposition and organizations associated with it."
Vulnerabilities, security research, and bug bounty
KEV update: CISA has updated its KEV database (twice)with four vulnerabilities that are currently exploited in the wild. These include a 2017 Adobe ColdFusion bug, an Oracle Agile Product Lifecycle Management (PLM) from last year, a 2024 bug in the Microsoft Partner Center, and a 2023 Zimbra XSS.
Chamilo vulnerability: The Chamilo LMS has patched an unauthenticated blind SSRF vulnerability discovered by Positive Technologies.
Exim security update: The Exim email server project has released a security update for an SQLi tracked as CVE-2025-26794.
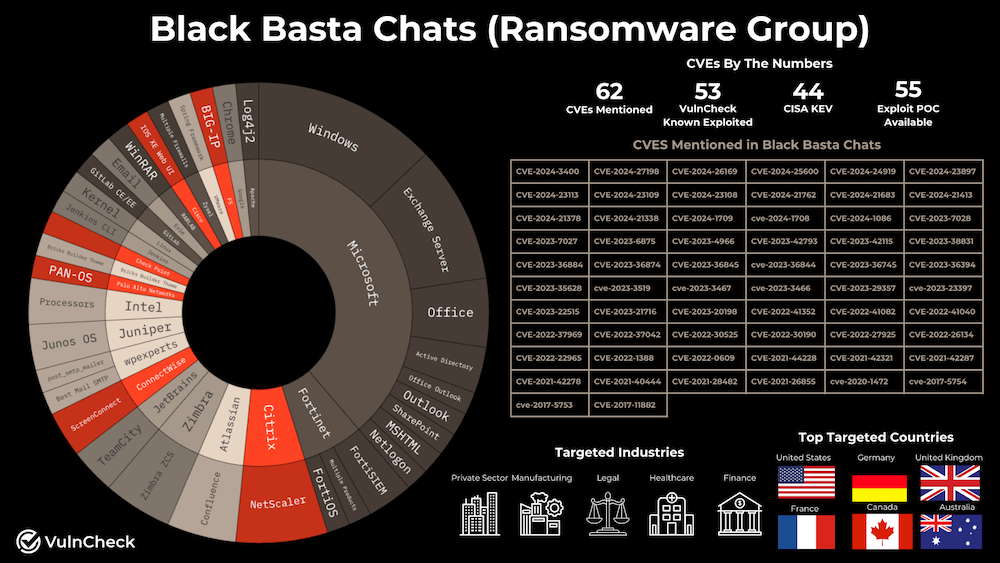
BlackBasta's CVEs: VulnCheck has extracted and made a list of all the CVEs mentioned in a recent leak from the internal Matrix chat server of the BlackBasta ransomware group. The list includes 62 vulnerabilities for products such as firewalls, enterprise gear, and Microsoft Windows. VulnCheck says the group focuses on CVEs with already public exploits.
Infosec industry
Threat/trend reports: Dragos, Palo Alto Networks, ReliaQuest, and Tamnoon have published reports and summaries covering various infosec trends and industry threats.
Skybox Security shuts down: Israeli cybersecurity company Skybox Security has shut down and fired all its 300 employees. The company developed a Continuous Exposure Management platform, which it sold to fellow Israeli cybersecurity company Tufin before shutting down. Skybox was founded in 2002 and raised $280 million over its lifespan. [Additional coverage in Ynet]
New tool—Sonicrack: BishopFox has open-sourced Sonicrack, a tool to decrypt SonicOSX NSv firewall firmware.
NDC Security 2025 videos: Videos from the NDC Security 2025 security conference, which took place in January, are available on YouTube.
Risky Business Podcasts
In this podcast, Tom Uren and Patrick Gray talk about the idea of launching a retaliatory campaign to hack Chinese telcos in response to Salt Typhoon's targeting of US ones. US Senator Mark Warner floated the idea as a way to persuade the Chinese government to pull back Salt Typhoon, but we think that kind of campaign has merit regardless.
In this edition of Between Two Nerds, Tom Uren and The Grugq examine the fundamental principles of network exploitation as described in Matthew Monte's "Network Attacks and Exploitation: A Framework" book.
