Risky Bulletin Newsletter
November 26, 2025
Risky Bulletin: Sha1-Hulud npm worm returns, with destructive behavior
Written by

News Editor
Risky Business Podcasts
The main Risky Business podcast is now on YouTube with video versions of our recent episodes. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
Another Salesforce breach: Hackers are pilfering data from Salesforce customers again, this time after they've breached Gainsight, the maker of a Salesforce app. More than 200 customers were affected. The Scattered Lapsus$ Hunters group took credit for the hack, the same group that breached Salesforce earlier this year as well. [Salesforce//TechCrunch]
CrowdStrike fires malicious insider: Security firm CrowdStrike has fired an employee who was feeding information to the Scattered Lapsus$ Hunters hacking group. The company discovered the insider after screenshots of its internal systems were posted on the group's Telegram channel. [BleepingComputer]
SitusAMC hack impacts Wall Street: Hackers have stolen sensitive data from fintech company SitusAMC. Its main customers include banks and real estate loan platforms. [CNN]
Police raid KT offices: South Korean police have raided two offices of mobile operator KT seeking evidence in a case involving the company's concealment of a major security breach this year. [The Korea Herald]
CBO breach finally contained: Phillip Swagel, the director of the US Congressional Budget Office, says the agency's security team has finally contained its recent breach and evicted hackers from its network. The hack was discovered at the start of the month and attributed to a foreign APT group. [Politico]
CodeRED breach: Hackers have stolen data from OnSolve CodeRED, an emergency notification platform used by some US law enforcement agencies. The platform has been down since the hack, per an alert sent to police departments.
Iberia Airlines breach: Spanish airline Iberia has notified customers of a breach at one of its suppliers that exposed their personal data. Exposed data included names, emails, and loyalty card data. [BleeingComputer]
Dartmouth College joins Clop list: Dartmouth College in the US has disclosed a breach. The hack was the work of the Clop gang and its use of recent Oracle EBS zero-days to pilfer data from cloud systems. American business conglomerate Cox also admitted it was hacked by the group.
GANA crypto-heist: Hackers have stolen $3.1 million worth of crypto assets from the GANA Payment DeFi platform. [The Crypto Basic]
Crypto site hacks: A threat actor has hijacked the domains/frontends of Aerodrome and Velodrome, two DEX portals. [The Block]
Comcast fined for 3rd party breach: The FCC has fined Comcast $1.5 million for a breach at a third-party vendor that exposed the data of 237,000 current and former customers. [Reuters]
General tech and privacy
TP-Link sues Netgear for smear campaign: TP-Link has sued Netgear over an alleged smear campaign. The Chinese company claims its American competitor is behind rumors and accusations over its connections to the CCP. TP-Link expects to lose over $1 billion this year alone from the smear campaign. [The Business Times]
Google Quick Share now works with Airdrop: Google has hacked its way through Apple's Airdrop protocol and has updated Android Quick Share to allow users to easily share files to and from Apple devices.
Mozilla shuts down Monitor Plus: Mozilla is shutting down Monitor Plus, a service that removed user data from data broker portals. The service was offered through a partnership with Onerep, a controversial company that was running a people search engine. [KrebsOnSecurity]
Meta ordered to pay news outlets: A court in Spain has ordered Meta to pay €481 million ($554 million) to 81 local news outlets as damages for unfair competition. [ABC News]
Meta settles Cambridge Analytica case: Meta has agreed to pay $190 million to settle a lawsuit filed by its shareholders over the Cambridge Analytica scandal. [Outlook Business]
Cisco's Resilient Infrastructure: Cisco has announced Resilient Infrastructure, a project modeled after Microsoft's Secure Future Initiative program that aims to improve the security of its products. This includes "increasing default protections, removing legacy insecure features, and introducing advanced security capabilities which reduce the attack surface and enable better detection and response."
Australia expands kids social media ban to Twitch: Australia's eSafety Commission has expanded the country's kids social media ban to video streaming service Twitch. The companies must block Australian users under the age of 16 from their platform starting on December 10. Australia's kids social media ban will be enforced on ten platforms. The other nine are Facebook, Instagram, Snapchat, Threads, TikTok, X, Reddit, Kick, and YouTube.
Cloudflare found liable for piracy: A Tokyo court has found Cloudflare liable for ignoring takedown requests and aiding and protecting a manga piracy site. [TorrentFreak]
Pressure campaign for Archive[.]today: After the FBI began an investigation to unmask the owners of Archive[.]today, ad-blocking service AdGuard says it's also been pressured to block the site by a mysterious entity.
Shopify internal fraud: Shopify fired salespeople who inflated the value of deals to receive higher commissions. [The Logic]
CounterStrike market crash: The market of expensive CounterStrike items lost $2 billion overnight thanks to a change in Valve's policies. [The Conversation]
Unused SSDs will lose data: Unused SSDs that are not powered on at regular intervals to receive electrical power will eventually slowly lose stored data. The data loss can occur anytime from 1 to 3 years of keeping the SSDs unpowered. [XDA Developers]
New Tor crypto: The Tor Project replaces the Tor relay encryption with a new algorithm named the Counter Galois Onion. CGO prevents attackers from tampering with encrypted traffic, adds forward secrecy, and upgrades Tor's encryption to modern practices and standards.
Tor is introducing "Counter Galois Onion", making Tor traffic immune to marking the ciphertext and making it much harder to forge cells :floof: https://blog.torproject.org/introducing-cgo/
— Latte macchiato :blobcoffee: :ablobcat_longlong: (@privateger.plasmatrap.com.ap.brid.gy) 2025-11-24T21:56:07.805Z
Government, politics, and policy
EU lawmakers seek to replace Microsoft and US gear: A pretty sizeable group of EU lawmakers has sent a letter to the European Parliament and urged officials to replace Microsoft software with European alternatives, in the aftermath of recent US bullying tactics. The letter also mentions hardware gear from other American giants such as Dell, HP, and LG. [Politico Europe]
EU GDPR overhaul proposal: The EU has published the first draft of its GDPR overhaul.
UK ban ticket resales: The UK government has banned the resale of event tickets in a move to stifle the ticket scalping and fraud industry. [Reuters]
ICE goes after cyber talent: The US ICE is planning to use the DHS Cyber Talent Management System to hire more cybersecurity specialists in the coming months. [NextGov]
GridEx attendance grows: Attendance for the GridEx VIII electric grid cybersecurity exercise was up by 42% this year, per E-ISAC.
FCC votes down telco cybersecurity rules: The new FCC leadership voted along party lines to rescind a Biden-era rule that introduced cybersecurity requirements and rules for US telcos.
Breaking: The FCC has voted 2-1 along party lines to eliminate cybersecurity requirements for telecom companies that the commission adopted at the end of the Biden administration. Telecoms had lobbied for the change. Democrats said it would invite another Salt Typhoon. Story coming shortly.
— Eric Geller (@ericjgeller.com) 2025-11-20T16:23:11.855Z
Risky Business podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about the differences between telcos and cloud companies. Does the nature of the business force cloud companies to be bettez at security?
Arrests, cybercrime, and threat intel
Former Google CEO accused of hacking: Michelle Ritter, a former romantic partner, has accused former Google CEO Eric Schmidt of hacking her email and computer to spy on her and steal business secrets. A lawsuit is underway. [LA Times]
Mayor sentenced to life in prison for scam compounds: A Chinese woman who posed as a local and was elected as mayor for the city of Bamban was sentenced to life in prison for running a huge cyber scam compound. [BBC]
Former contractor pleads guilty to revenge hacking: Maxwell Schultz, a former IT contractor for an American waste disposal company, pleaded guilty to hacking his former employer after he was fired to reset passwords and delete logs. An Iowa man was indicted with similar charges a day later, in another incident of revenge hacking.
TfL hackers plead "not guilty": Two members of the Scattered Spider hacking group—Thalha Jubair, 19, and Owen Flowers, 18—pleaded "not guilty" to hacking Transport for London earlier this year. [Sky News]
Samourai Wallet founders sentenced to prison: A US judge has sentenced the founders of the Samourai Wallet crypto-mixing service, CEO Keonne Rodriguez and CTO William Lonergan Hill, to five and four years in prison, respectively. Their service was used to launder more than $237 million worth of crypto-assets from crypto heists, and the two actively advertised the service as a way to launder and hide funds from authorities.
Crypto launderer pleads guilty: A California man named Kunal Mehta pleaded guilty to laundering cryptocurrency from online scams and hacks. He was one of eight members in the scheme and laundered at least $25 million stolen from a haul of $263 million in crypto assets.
Russian money laundering network exposed: The UK has exposed two companies, Smart and TGR, which laundered money from cybercrime, drug operations, and firearms smuggling, to create "clean" crypto that the Russian government could then use to evade international sanctions. As part of this operation, the two entities acquired banks in Kyrgyzstan to pose as legitimate operations.
Russian cyber expert arrested for "treason": Russian authorities have arrested and charged a Russian cybersecurity expert on "treason" charges. The case is classified, but the suspect allegedly criticized the state's national messenger app Max and its recent attempts to regulate and "nationalize" the vulnerability disclosure process. [The Record]
ATM jackpotting incident: The Fairfax County Police Department (in Virginia) is looking for help in identifying suspects part of a group that installed malware on ATMs to carry out jackpotting attacks.

Piracy site crackdown: Europol has taken down 69 piracy sites and 25 IPTV services. They also seized €47 million from the sites' operators.
Media Land BPH sanctioned: The US, the UK, and Australia have imposed sanctions on Media Land, a Russia-based bulletproof hosting provider that has hosted ransomware infrastructure.
BPH guidance: Cybersecurity agencies from the Five Eyes have released joint guidance on how to deal with bulletproof hosting providers.
EtherHiding technique: Censys looks at how the EtherHiding technique is being used in some real-world campaigns to hide malicious code and payloads on the blockchain, in most cases via smart contracts deployed on the Binance Smart Chain testnet.
Malware found in Blender files: Morphisec has found the StealC infostealer hidden in malicious Blender 3D model files uploaded on the CGTrader marketplace.
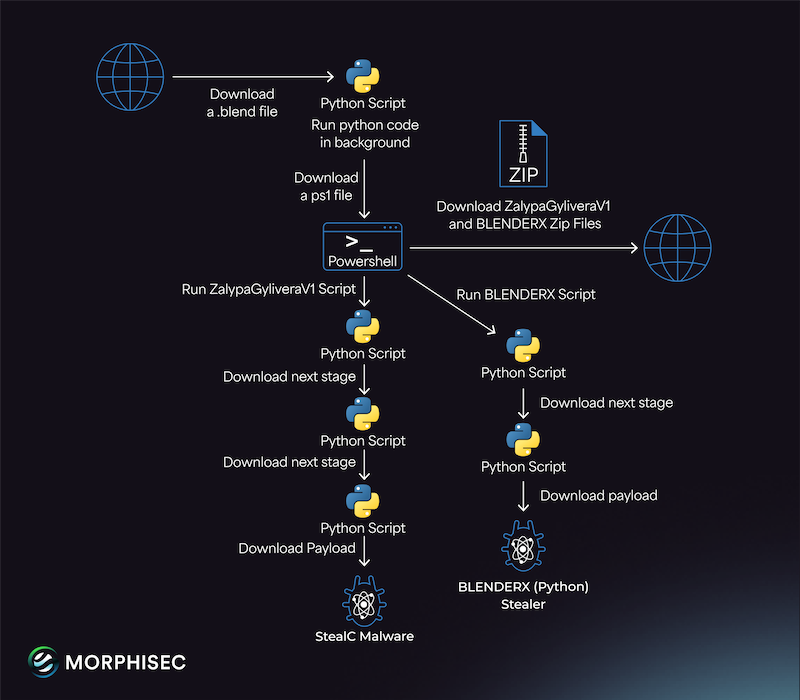
TamperedChef group still active: Acronis says the TamperedChef group is still active, using poisoned SERP and malvertising to lure victims to websites that distribute malware-laced app installers.
New NetMedved group: Positive Technologies has discovered a new threat actor targeting Russian companies with various infostealers. They're tracking the group as NetMedved.
VasyGrek (Fluffy Wolf): Russian security firm F6 has published a profile on VasyGrek (Fluffy Wolf), a Russian-speaking threat actor who is behind attacks on Russian companies. The Wolf name suggests this is an e-crime actor and not a state-backed espionage operation. The group is apparently a customer of the Pure malware family.
Abandoned iCal-related domains: Bitsight has discovered 390+ abandoned domains related to iCalendar sync requests for subscribed calendars, receiving daily sync events, and potentially putting ~4 million devices at risk.
Devs leak passwords via code beautification sites: watchTowr Labs has found thousands of secret tokens and credentials shared publicly on code formatting and beautification sites, such as JSONFormatter and CodeBeautify.
Tycoon2FA is top dog: Microsoft's security team says the Tycoon2FA was this year's most active phishing platform. CyFirma also published a report on the PhaaS and its operations.
Phantom stores: Ad security company Confiant looks at the seasonal surge in fake storefronts ahead of the Black Friday and Cyber Monday holidays.
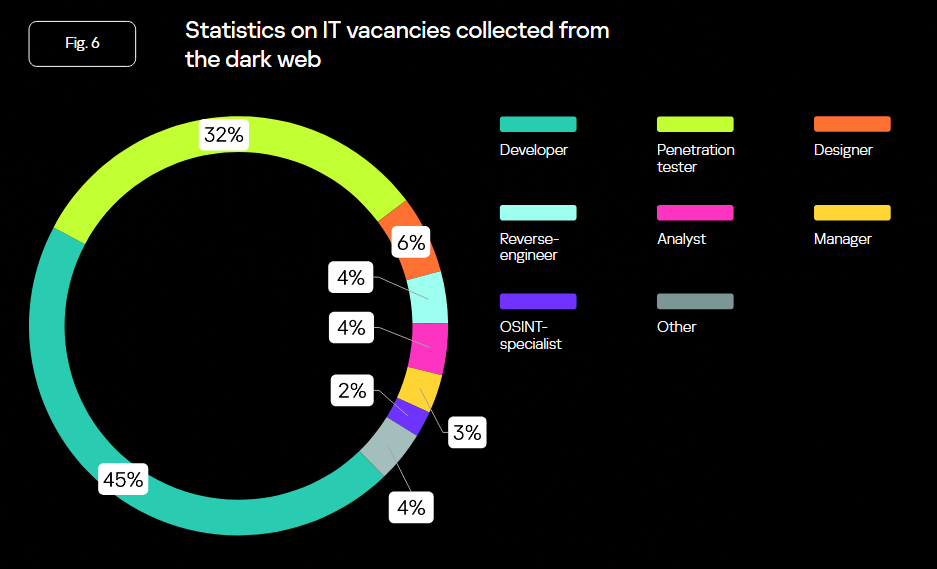
Dark web job market: Kaspersky looks at the underground job market for cybercrime roles advertised on dark web portals.
Malware technical reports
Sha1-Hulud worm returns: More than 800 npm libraries have been infected with the Sha1-Hulud worm. This is the second Sha1-Hulud outbreak after the first incident at the end of October. This time around, the malware comes with destructive behavior if it can't steal creds or gain persistence. [HelixGuard//Socket Security//Google Wiz//Aikido Security//Step Security//Koi Security//Semgrep]
"In other words, if Sha1-Hulud is unable to steal credentials, obtain tokens, or secure any exfiltration channel, it defaults to catastrophic data destruction. This marks a significant escalation from the first wave, shifting the actor's tactics from purely data-theft to punitive sabotage."
RondoDox IoT botnet: F5 has published a report on the recent activities of the RondoDox IoT botnet and the big update to its exploit arsenal.
Tsundere botnet: Kaspersky looks at Tsundere, a Node.js-based malware strain that uses npm to host malicious payloads that target Windows systems.
QuietEnvelope: ESET has found a malware strain named QuietEnvelope that was specifically developed to target the MailGates email protection system of OpenFind email servers. This is very likely the work of a Chinese APT.
#ESETresearch discovered unique toolset, QuietEnvelope, targeting the MailGates email protection system of Taiwanesw co OpenFind. The toolset was uploaded in an archive, named spam_log.7z, to VirusTotal from Taiwan. It contains Perl scripts, 3 stealthy backdoors, argument runner, and misc files. 1/8
— ESET Research (@esetresearch.bsky.social) 2025-11-24T17:57:04.325Z
Eternidade Stealer: Trustwave has discovered a new infostealer and banking trojan named Eternidade Stealer that is currently targeting the Brazilian scene using WhatsApp phishing.
Astaroth campaign: The same poor Brazilian users are also being targeted with the Astaroth banking trojan, also with WhatsApp lures.
Obscura ransomware: Coveware has published a technical analysis of the new Obscura ransomware.
Akira ransomware: PAN's Unit42 looks at an attack with the Akira ransomware that was traced back to a ClickFix fake CAPTCHA challenge.
ShinySp1d3r ransomware: The ShinyHunters group has launched its very own RaaS, named ShinySp1d3r. [BleepingComputer]
Matrix Push C2: Threat actors are using a new C2 platform named Matrix Push C2. The platform is one of a kind because it uses the web push notification system to send malicious links to users who accidentally or were tricked into subscribing to a site's push notifications.
SkyWalk adware: Security firm DoubleVerify has found SkyWalk, a network of iOS games that serve ads inside invisible windows. The malicious code was traced back to the UniSkyWalking iOS mobile framework.
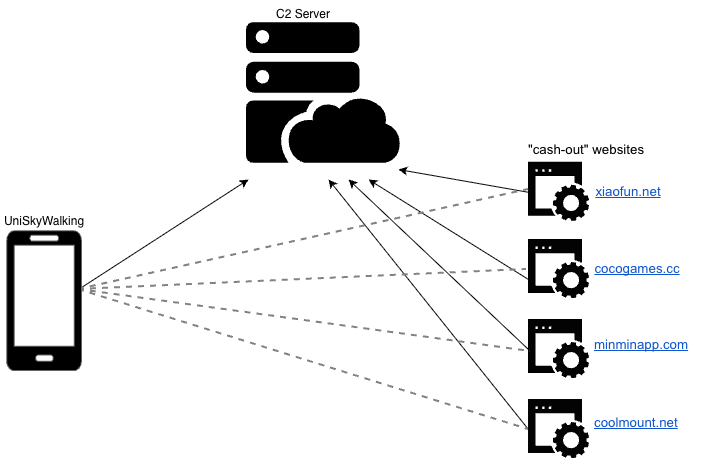
GhostAd is still alive: The GhostAd Android adware is still alive and kicking, even making it on the official Play Store. [Check Point]
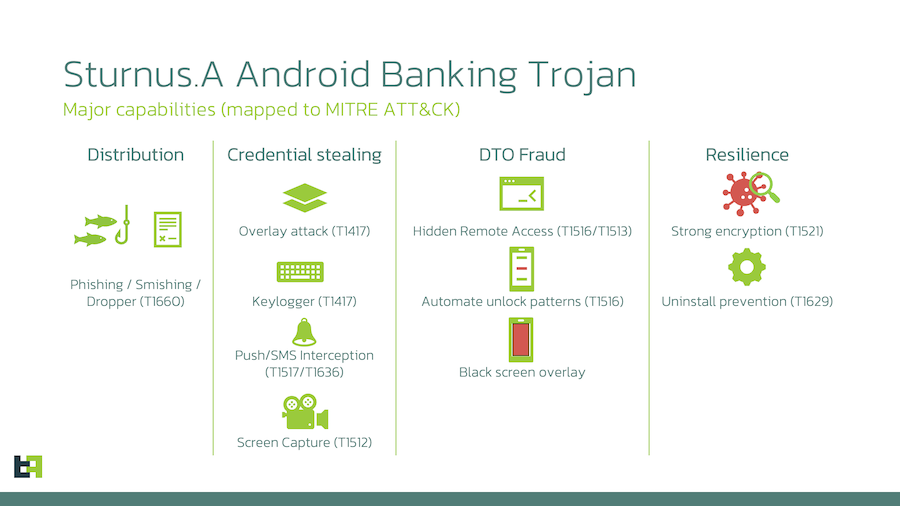
Sturnus: ThreatFabric has discovered Sturnus, a new Android banking trojan that also comes with the ability to dump chats from secure messengers like Telegram, Signal, and WhatsApp.
Risky Business podcasts
In this edition of Seriously Risky Business, Tom Uren and Amberleigh Jack talk about Anthropic's discovery of an "AI-orchestrated" cyber espionage campaign.
APTs, cyber-espionage, and info-ops
Iran's cyber-to-kinetic campaigns: The AWS security team has spotted two Iranian APTs (Tortoiseshell and MuddyWater) carrying out cyber operations and then using stolen data and digital infrastructure to orchestrate kinetic attacks against targets. This includes passing data to Houthi rebels to target ships and using hacked Jerusalem CCTV streams for missile strikes.
IRGC Department 40: A secretive unit inside Iran's IRGC cyber branch is responsible for using hacked data for assassination operations. [Iran International//Nariman Gharib]
"The exposure also reveals the direct connection between cyber operations and terrorism. These hackers build the intelligence infrastructure that enables assassination operations. Every breached airline database, every compromised hotel booking system, every hacked medical clinic feeds into a system designed to locate and kill people the Iranian regime considers enemies."
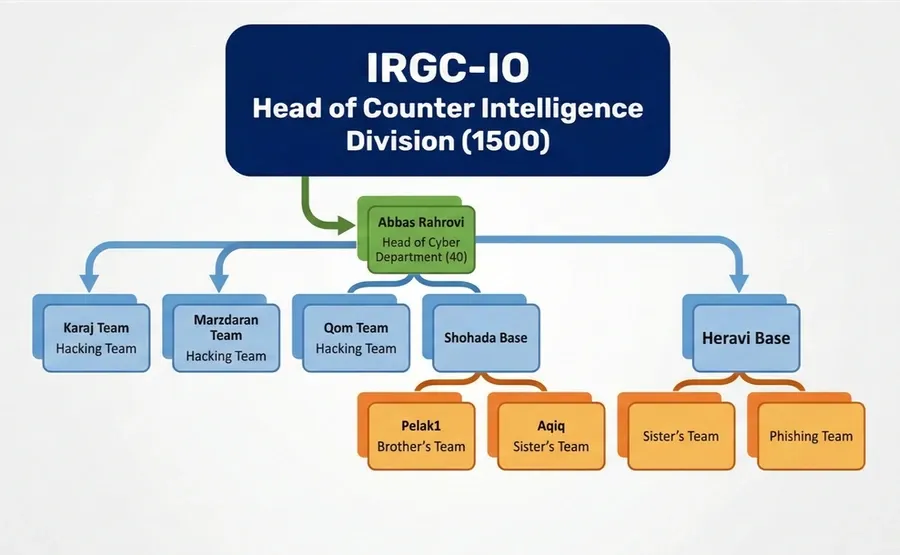
APT35 leak analysis: The DomainTools security team has analyzed the recent leak of APT35 internal documents and how the documents map out to past campaigns and infrastructure, as well as how they reveal more of the internal structure of Iran's cyber apparatus.
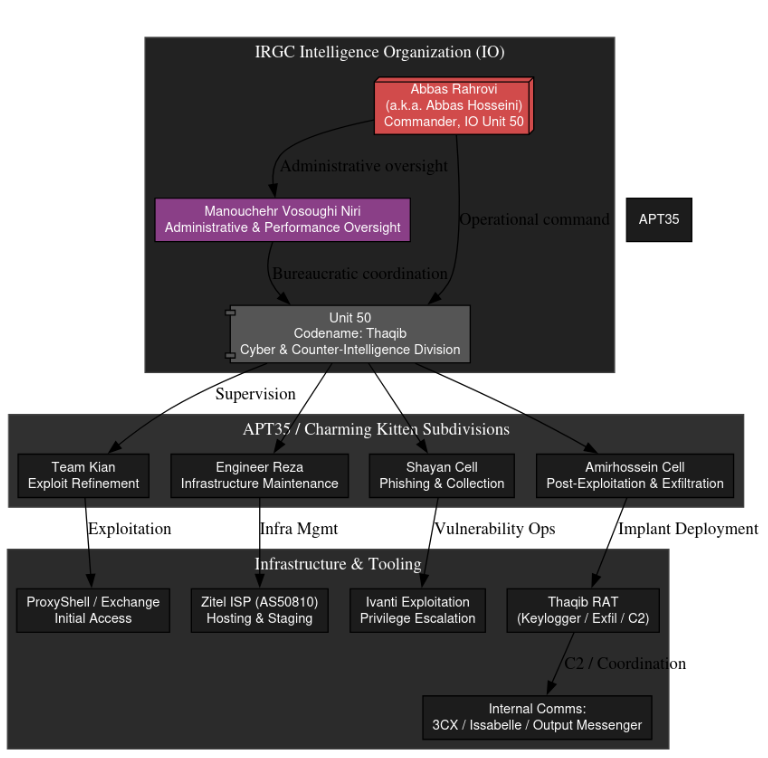
KittenBusters profile: On the same note, FalconFeeds has published a profile on KittenBusters, the leakers of the APT35 files.
APTs start cooperating: Gen Digital's Avast looks at how multiple APT groups are now starting to cooperate instead of running operations in isolation. To be noted, the cooperation typically takes place between APTs from the same country.
State actor abuses Factory AI infrastructure: AI company Factory has detected multiple threat actors abusing its free tiers to automate cyberattacks, including "at least one state‑linked actor."
ToddyCat evolution: Kaspersky says the ToddyCat APT has evolved its tactics to go after the cloud infrastructure of targeted entities. The report also looks at the group's TomBerBil family of tools.
UAC-0241's Sumy campaign: Ukraine's cybersecurity agency has spotted the UAC-0241 threat actor targeting residents of the Sumy region.
Storm-1516 disinformation campaign: Per the Gnida Project, there's a new Russian disinformation campaign targeting Armenia's current pro-Western political leadership.
APT38 money laundering ops: Blockchain investigator ZachXBT has published a report on how the APT38 (Bluenoroff) group laundered $200 million worth of crypto from 25+ hacks to fiat between 2020 and 2023.
Operation WrtHug: SecurityScorecard has spotted a report on Operation WrtHug, an ORB (Operational Relay Box) botnet designed to hide espionage operations. This one is around 50,000 bots and primarily made up of hacked ASUS routers.
New ShadowPad campaign abuses WSUW bug: A suspected Chinese APT group has abused a recent WSUS vulnerability (CVE-2025-59287) to deploy the ShadowPad malware. [AhnLab]
China's attack-defense labs: Natto Thoughts has published a report on "attack-defense labs," divisions inside Chinese cybersecurity firms, and their role in China's offensive cyber operations.
"China's cybersecurity industry has evolved around the idea that offense and defense develop together. This mindset has shaped how companies organize, how talent is trained, and how capabilities ultimately flow into state activity. Attack-defense labs sit at the center of this system: they drive commercial innovation while generating tools, techniques, and expertise that both strengthen defensive capabilities and enable state-sponsored operations."
APT24's Taiwan pivot: Google looks at the three-year operations of Chinese group APT24, targeting Taiwanese organizations using watering hole attacks, supply chain compromises, and cloud compromises.
APT31 targets Russia: According to Russian security firm Positive Technologies, Chinese hacking group APT31 has gone after Russian IT firms, such as "contractors and integrators of government decision makers."
Autumn Dragon APT: CyberArmor has published a report on Autumn Dragon, a China-nexus threat actor targeting governments and media.
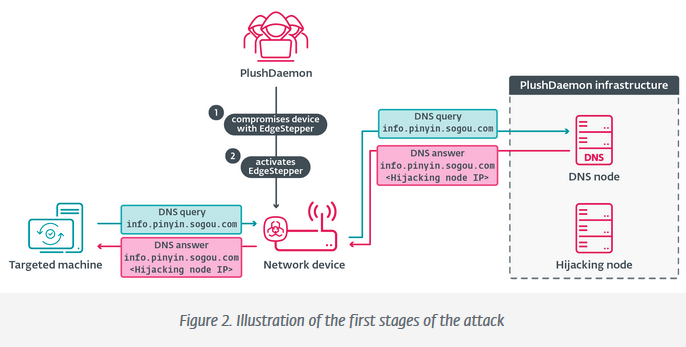
PlushDaemon APT: ESET says a Chinese APT group tracked as PlushDaemon is hijacking software update traffic by deploying an implant named EdgeStepper on a victim's networking devices (routers, gateways, etc.).
Vulnerabilities, security research, and bug bounty
Oracle Identity Manager zero-day: Threat actors are exploiting a zero-day in the Oracle Identity Manager server to bypass authentication. The zero-day was discovered by Searchlight Cyber, and the attacks confirmed by CISA and SANS ISC. The zero-day is tracked as CVE-2025-61757 and was patched in October. Adding ";.wadl" to any URL allows attackers to bypass authentication and access sensitive resources.
Unpatched Twonky Server admin auth bypass: Twonky has failed to patch an admin authentication bypass in the company's media server.
Unpatched Tenda router bugs: Tenda has failed to patch two vulnerabilities in its 4G03 Pro portable 4G LTE router. The bugs can lead to arbitrary command execution as root.
Bitcoin Core audit: Quarkslab conducted the first public third-party security audit of Bitcoin Core.
"The security assessment focused on a specific scope, the P2P part and on most impactful attack scenarios altering consensus or protocol availability. No high-impact issues were found, but marginal gain was brought on existing fuzzing harnesses as well as new ones to cover untested scenarios like chain reorganization. Also, some alternative testing approaches were explored like ensemble fuzzing and differential testing."
Amazon's Autonomous Threat Analysis system: Amazon is using an internal AI system named the Autonomous Threat Analysis to discover and patch bugs on internal systems. [WIRED]
Important security updates: 7-ZIP, ABB, ASUS, AudioCodes, Bitdefender, D-Link, Fluent Bit, Fortinet, GitLab, Grafana, GRUB2, OpenOffice, RSA, SonicWall.
Infosec industry
Threat/trend reports: Bitdefender, BforeAI, CyFirma, Emsisoft, Immersive Labs [PDF], Kaspersky, Kaspersky, Red Canary, RT-Solar, SAS, and WaterISAC have recently published reports and summaries covering various threats and infosec industry trends.
SEC drops SolarWinds lawsuit: The US SEC has dropped its lawsuit against SolarWinds and its CISO, Tim Brown, over the company's 2020 security breach that led to supply chain attacks against large companies and US government agencies.
NSO appeals WhatsApp ruling: Israeli spyware maker NSO Group has filed an appeal against WhatsApp and the injunction that prevents it from targeting the app and its customers. [The Record]
Acquisition news: Palo Alto Networks will acquire Chronosphere, an observability and telemetry platform for Kubernetes and cloud platforms, for $3.35 billion.
Kurtz buys Mercedes F1 shares: CrowdStrike CEO George Kurtz has acquired 5% of the Mercedes F1 team. The shares were acquired from the ownership stake of Mercedes F1 boss Toto Wolff. [CNBC]
HOPE conference banned at venue: The Hackers on Planet Earth (HOPE) security conference says it was banned from its regular venue at St. John's University because of its "anti-police agenda." You can watch the conference's last edition here. [404 Media]
"HOPE was held at St. John's University in 2022, 2024, and 2025, and was going to be held there in 2026, as well. The conference has been running at various venues over the last 31 years, and has become well-known as one of the better hacking and security research conferences in the world."
New tool—HCLI: IDA maker Hex-Rays has released HCLI, a command-line interface for managing Hex-Rays software, licenses, and plugins.
VirusBulletin videos: Talks from the VirusBulletin 2025 security conference, which took place at the end of September, are available on YouTube.
Hexacon videos: Talks from the Hexacon 2025 security conference, which took place last month, are available on YouTube.
BSides Canberra videos: Talks from the BSides Canberra 2025 security conference, which took place in September, are now available on YouTube.
TROOPERS videos: Videos from the TROOPERS 2025 security conference, which took place at the end of June, are available on YouTube.
NYMJCSC2025 videos: Talks from the 2025 New York Metro Joint Cyber Security Conference, which took place at the end of October, are available on YouTube.
