Risky Bulletin Newsletter
June 11, 2025
Risky Bulletin: SentinelOne avoids a Chinese APT hack
Written by

News Editor
This newsletter is brought to you by Push Security. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
Cybersecurity firm SentinelOne says it narrowly avoided getting hacked by Chinese government hackers after an APT breached one of its IT vendors that handled hardware logistics for its employees.
The company said it detected and stopped the intrusion before it reached its network.
The incident took place at the start of the year, months after SentinelOne also observed extensive reconnaissance of its internet-exposed servers.
SentinelOne linked the attacks to a cluster of activity linked to Chinese state hackers. Activity from the same cluster, which SentinelOne called PurpleHaze, also hit a South Asian government organization, a European media organization, and over 70 other organizations across different sectors.
Some of the activity was loosely connected to APT15/UNC517, but SentinelOne didn't go as far as to attribute the intrusion to the group.
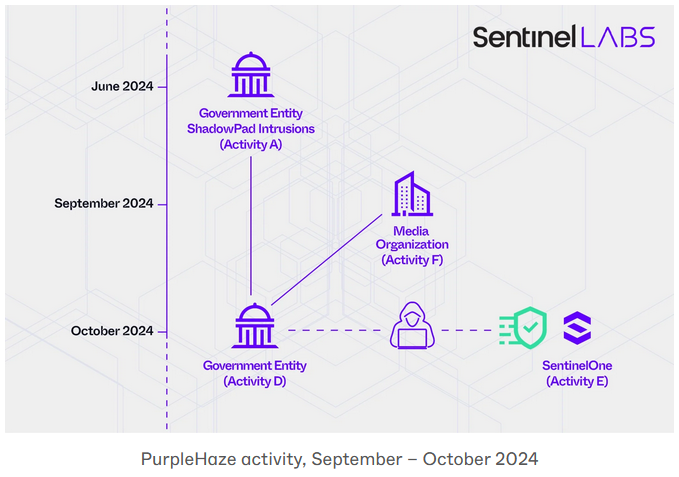
The disclosed incident is the same one that SentinelOne Senior Vice-President of Threat Discovery and Response Steve Stone disclosed in an episode of the Wide World of Cyber podcast recorded live during the RSA security conference this year, see 33:25 timestamp.
The company also published a blog post back in April warning that security firms were now constantly being attacked, with APT groups and financially motivated groups alike seeking to use a security firm's sprawling platforms as entry points into sensitive or high-value networks.
Risky Business Podcasts
The main Risky Business podcast is now on YouTube with video versions of our recent episodes. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
Cyberattack disrupts grocery deliveries: A cyberattack is disrupting the operations of United Natural Foods, a distributor of grocery products in the US. The company says it proactively took some IT systems offline after discovering the attack last week. The downtime is now affecting its ability to fulfill and distribute customer orders. United Natural Foods is the largest grocery carrier and the 14th largest logistics company in the US. [Additional coverage in Transport Topics]
M&S restores website: UK retail chain Marks & Spencer has restored its online store and delivery service six weeks after a devastating ransomware attack.
TxDOT breach: Hackers have stolen over 300,000 crash reports from the Texas Department of Transportation. The breach took place on May 12 after the hacker compromised an employee account. The stolen reports include sensitive details, such as real names, addresses, car license plates, and insurance details. The Department is currently notifying all affected Texans.
New Salt Typhoon victims uncovered: The US government believes that Chinese hackers have breached mass media provider Comcast and data center company Digital Realty. The two companies have not publicly confirmed the breaches, which have been revealed to NextGov by sources inside CISA and the NSA. Officials linked the intrusions to Chinese cyber-espionage group Salt Typhoon. The group's operations were exposed last year, and victims include seven other US telcos and ISPs (Verizon, AT&T, T-Mobile, Spectrum, Lumen, Consolidated Communications, and Windstream).
Scoop: U.S. agencies assessed that Salt Typhoon likely hit data center giant Digital Realty and mass media provider Comcast, marking a potentially major expansion of the Chinese hacking group’s initial telecom intrusions discovered last year.⬇️
— David DiMolfetta (@ddimolfetta.bsky.social) 2025-06-09T17:20:49.155Z
General tech and privacy
Ofcom to investigate 4chan: The UK's telecommunications watchdog has started an investigation of online message board 4chan. Ofcom says it's investigating the site for hosting potential illegal content under the UK Online Safety Act. The same investigation also targets seven file-sharing providers and adult video hosting service First Time Videos.
YouTube quietly relaxed content moderation: Google has quietly told employees to relax moderation rules. The change in moderation policy took place in mid-December, after Donald Trump won last year's presidential election, according to the New York Times. The new relaxed rules are meant to benefit political commentators, but experts say they benefit disinformation peddlers.
YouTube declares open season on disinformation, slurs, and pseudoscience:
— Lindsay Beyerstein (@beyerstein.bsky.social) 2025-06-09T10:19:30.659Z
This story points out a thorny moderation challenge for YouTube and other platforms. There are so many conspiracists running for office that a blanket ban on conspiracy speech is becoming unworkable because people need to know what their platforms are.
— Lindsay Beyerstein (@beyerstein.bsky.social) 2025-06-09T13:33:28.600Z
Telegram's shadowy contractor: An Important Stories investigation has found that one of Telegram's technical infrastructure providers is a major FSB contractor. Telegram's response to the story is here.
NEW: The Telegram messaging app has a reputation for security — but Important Stories found that its technical infrastructure is run by a man whose companies closely collaborate with Russian intelligence services. Meet Vladimir Vedeneev 👇
— Organized Crime and Corruption Reporting Project (@occrp.org) 2025-06-10T07:24:48.174Z
Twitter's encrypted DMs: After a write-up from Matthew Garrett, cryptographer and Johns Hopkins University professor Matthew Green has published his own analysis of the encryption "promised" for Twitter's upcoming encrypted messaging service, XChat.
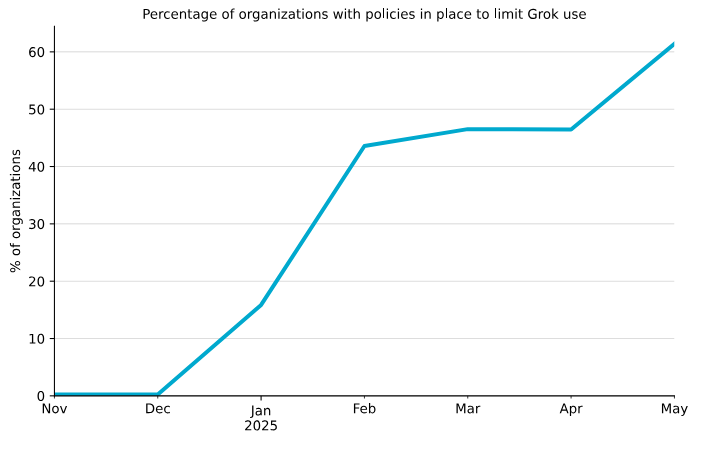
Grok is getting blocked: Netskope says companies are starting to block genAI apps, with Grok seeing a surge in blocks.
Meta's ad problems again: Meta has removed hundreds of ads for AI nudify apps from its platform after a CBS News investigation. It is the latest report on Meta's lackadaisical and almost non-existent ad moderation practices.
Outlook to block more file attachments: Microsoft will block two more file extensions in Outlook due to increased abuse. Starting July, Outlook will block library-ms and search-ms file types. Both file types have been used to launch and abuse Windows features and install malware. [Additional coverage in Bleeping Computer]
Android 16 launched: Google launched Android 16... on the second day of Apple's developer conference. Is it intentional... who knows.
Apple Containerization Framework: Apple has announced the Containerization Framework, a new developer tool to help developers run Linux container images on macOS. The other WWDC25 press releases are here.
Government, politics, and policy
New lead for the FBI's cyber division: The FBI has named Brett Leatherman to lead the agency's cyber division. Leatherman is an FBI 22-year veteran and was involved in the LockBit, Salt Typhoon, and Volt Typhoon investigations. He replaces Bryan Vorndran, who left to become Microsoft's new deputy chief information security officer. [Additional coverage in CyberScoop]
Gabbard pushes IC to outsource: US DNI Tulsi Gabbard says the US intelligence community should stop building its own tools and rely on the private sector to create its tools. US Director of National Intelligence Tulsi Gabbard says the US intelligence community should move away from building its own tools. Gabbard says agencies should focus on buying tools from the private sector and focus on their core missions instead. Gabbard remarks echo similar ones from predecessors. Avril Haines, the DNI during the Biden administration, also urged agencies to tap the private sector for more advanced knowledge and capabilities. [Additional coverage in NextGov]
EU blueprint on cyber crisis management: ENISA has published a blueprint for cyber crisis management to help organizations respond to large-scale incidents.
Paragon and Italy cut ties: Italy and spyware maker Paragon Solutions have ended their contract. Paragon cut the Italian government's access to its platform in February after reports that the government had targeted journalists and activists. The Israeli spyware maker said it ended the contract after the Italian government refused its help in investigating the alleged abuses. Italian officials have already contracted local Italian company Negg to provide it with new surveillance capabilities. [Additional coverage in TechCrunch]
Russia denies entry to users who wiped phones: Russian border authorities are denying entry to Ukrainians with clean phones. According to court documents, authorities denied entry to users who wiped their image galleries, messenger chats, or deleted their YouTube watch history. Almost a dozen users challenged the border entry denials in court but lost their cases. [Additional coverage in Ria Novosti]
China sells firewall bypass: Authorities in the Hainan island province are selling access to Global Connect, a service that provides access to the global internet, uncensored by the country's national firewall system. [Additional coverage in SCMP]
Sponsor section
In this sponsored interview, Casey Ellis interviews Push Security co-founder and Chief Product Officer Jacques Louw about how good phishing crews have gotten at evading detection. Attackers are hiding their payloads behind legitimate bot-detection tools to stop things like email security gateways from seeing them, as well as locking up phishing pages behind OAuth challenges. Push sees all this because it's installed as a browser plugin and sees what users see.
Arrests, cybercrime, and threat intel
Kazakhstan arrests 140 selling citizen data: Kazakh authorities have detained 140 suspects for allegedly selling citizen personal data on Telegram. The group allegedly extracted data from government databases. Some of the data was also shared with debt collection agencies. [Additional coverage in The Record]
Five scammers plead guilty: Five men have pleaded guilty to laundering $36.9 million linked to investment scams.
Extortionist sentenced: South African authorities have sentenced a local man to eight years in prison for hacking and ransoming his former employer. [Additional coverage in ITWeb] [h/t DataBreaches.net]
Over 40k cams expose feeds online: Bitsight researchers have found over 40,000 security cameras available online that are exposing their video streams.
"The United States leads the charge with roughly 14,000 exposed online cameras, followed by Japan, Austria, Czechia, and South Korea."
Scammers target app testers: Scammers are tricking mobile app testers into infecting their phones with malicious apps that steal money from their bank accounts. The scammers use ads posted on Telegram channels and job portals to lure users into installing their apps. Security firm F6 says the scheme appears to be limited and targets Russian citizens only—for now.
New GhostVendors group: SilentPush has spotted a new group named GhostVendors that uses Facebook ads impersonating major vendors to lure users to scam stores.
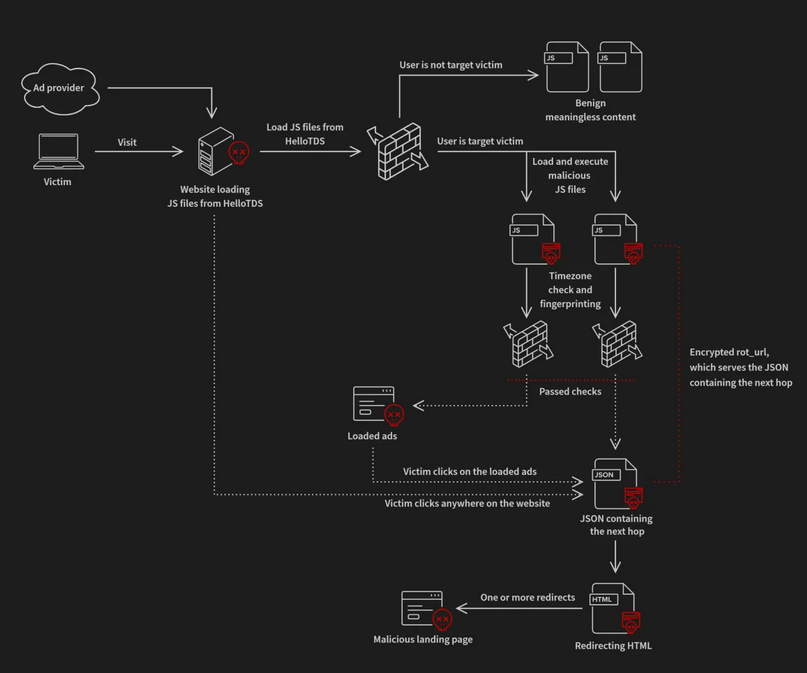
HelloTDS: Gen Digital has spotted a new traffic distribution system named HelloTDS that's being used by cybercrime groups to hijack traffic from legitimate sites and send them to ClickFix campaigns.
Librarian Ghouls steal data at night: A hacking group is breaching Russian companies using special malware designed to steal data only at night. Librarian Ghouls (Rare Wolf and Rezet) uses scripts that wake up infected systems between 1AM and 5AM to steal data while employees are at home. The group is primarily focused on stealing credentials and crypto-wallet data and then deploying crypto miners. The group has been active since October 2018, and its primary targets are companies in Russia and former Soviet states.
FIN6's social engineering: DomainTools looks at how the FIN6 group is using social engineering for their intrusions, targeting the recruiters in HR departments.
npm malware, again: Veracode looks at two malicious npm packages that infected systems with a remote access trojan. The packages used an elaborate multi-stage infection mechanism and Unicode obfuscation using Japanese Katakana and Hiragana characters.
BlackSuit adopts social-engineering attacks: The BlackSuit ransomware group is now heavily using social-engineering attacks as an initial entry point in corporate networks. Rapid7 believes the change in tactics may be linked to recent BlackBasta RaaS members who joined BlackSuit in the aftermath of BlackBasta's demise earlier this year.
Tomcat brute-force campaign: GreyNoise has spotted a large-scale brute-force campaign targeting the management panel of Apache Tomcat servers. The campaign lasted almost a week and rotated through a cluster of 400 malicious IPs. The Apache Tomcat Manager web app allows developers to manage their Tomcat servers via a classic admin panel.
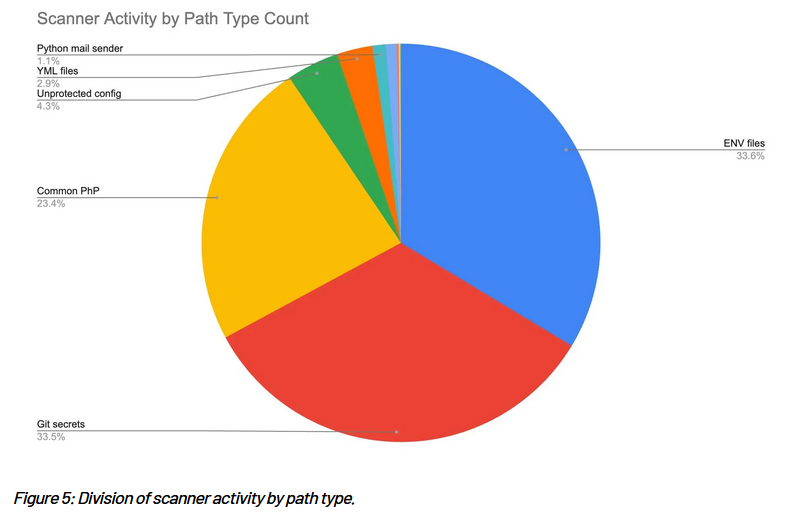
Most internet scans target Git and env files: Mass internet scans for Git secrets and environment files account for two-thirds of all online reconnaissance activity. These files contain credentials that can be used to enable other future intrusions. HUMAN Security says that mass internet scans now account for almost 70% of all bot traffic the company sees. One of the biggest sources of internet scans this year has been the hacked network of a major Romanian distillery.
Malware technical reports
Mirai botnet targets Wazuh SIEMs: Akamai has spotted two Mirai botnets abusing a recently patched RCE (CVE-2025-24016) in the Wazuh SIEM.
Skitnet/Bossnet: WardenShield has published a technical report on Skitnet (Bossnet), a new malware loader that has been sold under a MaaS model on underground forums since April 2024.
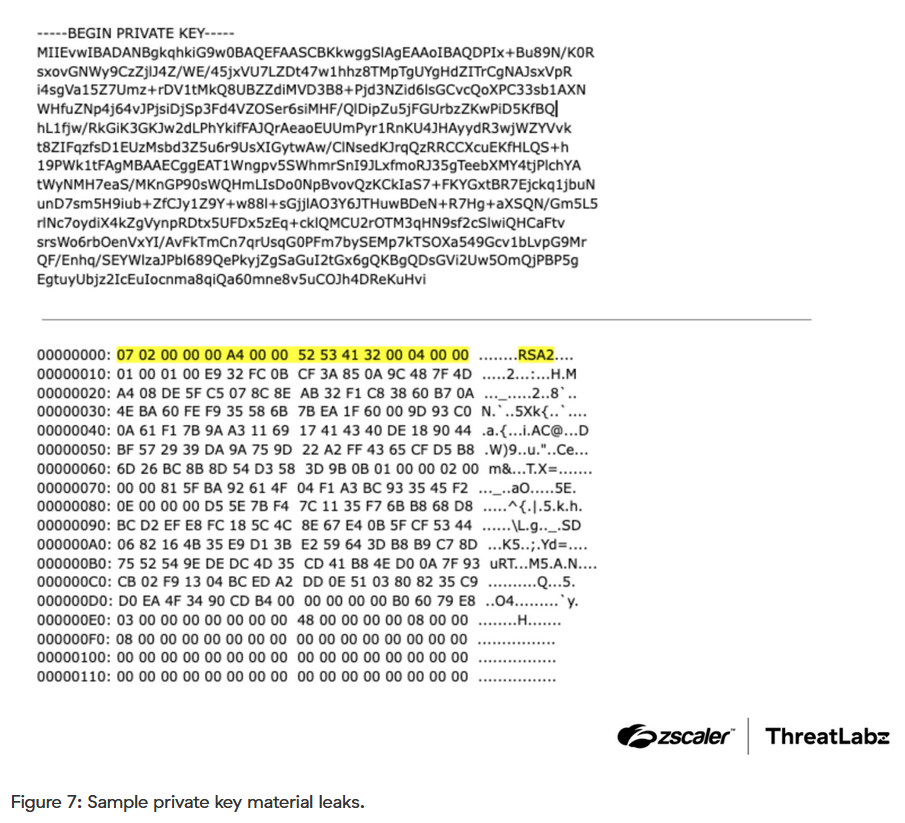
DanaBleed vulnerability in DanaBot: The DanaBot malware command-and-control servers leaked sensitive data about its operators via a HeartBleed-like vulnerability. Security firm Zscaler says it silently exploited the bug for three years to collect data on the malware's operators. The vulnerability exposed details such as threat actor names, their IP addresses, and cryptographic private keys. Authorities seized DanaBot infrastructure in May and charged 16 suspects.
Sponsor section
In this on-demand webinar, Push Security VP of R&D Luke Jennings walks you through the common TTPs used by the Scattered Spider group this year and how you can defend against them.
APTs, cyber-espionage, and info-ops
Stealth Falcon's WebDAV zero: A cyber-espionage group has exploited a Windows WebDAV zero-day vulnerability in phishing attacks this year. Users who clicked on malicious WebDAV links had malware installed on their systems. Check Point linked the attacks to a veteran APT group named Stealth Falcon, also known as FruityArmor. Microsoft released patches for the zero-day in this month's Patch Tuesday.
New Kimsuky ops: South Korean security firm Genians has spotted a new Kimsuky operation that targeted users across Facebook, Telegram, and their email accounts over the past three months.
New Russian disinfo op launched: Russia's propaganda machine has launched a heavy disinformation operation this week in the aftermath of a political stunt the Kremlin pulled over the weekend. Russian trolls everywhere are now spinning the narrative that Ukraine doesn't want peace or to recover its POWs. This comes after Russian authorities moved POWs and dead soldiers to an agreed spot days before the planned exchange and then claimed Ukraine didn't want to take them. [Additional coverage in Espreso Global]
Vulnerabilities, security research, and bug bounty
Patch Tuesday: Yesterday was the February 2025 Patch Tuesday. We had security updates from Adobe, Microsoft, SAP, Ivanti, Salesforce, Fortinet, Supermicro, Dell, SolarWinds, Intel, AMD, Firefox, Schneider Electric, Siemens, GeoServer, Autodesk, Elastic, and Apache Kafka. The Android Project, Arm, Chrome, Cisco, Splunk, Kubernetes, Apache InLong, QNAP, HPE, Jenkins, Qualcomm, and Moxa released security updates last week as well.
Microsoft Patch Tuesday: This month, Microsoft patched 66 vulnerabilities, including one actively exploited zero-days—CVE-2025-33053, a WebDAV RCE discovered by Check Point, which the company linked to the Stealth Falcon APT.
Switch 2 exploit found day one: Security researcher David Buchanan has found the first exploit for Nintendo's Switch 2, the first day after the product's launch. [Additional coverage in Tom's Hardware]
OpenPGP.js vulnerability: Codean Labs researchers have found a vulnerability (CVE-2025-47934) in the OpenPGP.js library that could be abused to spoof valid signature verification results.
Apple accused of silently patching major bug: A security researcher has accused Apple of silently patching a zero-click iMessage exploit. Joseph Goydish claims the exploit could have allowed remote code execution attacks and the theft of Secure Enclave keys and crypto-wallet data. Apple allegedly patched two bugs related to the exploit chain in April without any credit or acknowledgment despite responsible disclosure.
New Secure Boot bypass #1: Binarly researchers have discovered a new Windows Secure Boot bypass (CVE-2025-3052) to run unsigned code during the boot process.
New Secure Boot bypass #2: Security researcher Nikolaj Schlej has discovered a vulnerability in the Insyde H2O UEFI firmware that can lead to a Windows Secure Boot bypass (CVE-2025-4275). The vulnerability is known as Hydroph0bia.
Google patches bug exposing users' phone numbers: Google patched a bug that could have allowed attackers to discover any user's real name and phone number. The attack abused the Google Looker Studio to reveal a user's name and the password recovery screen from Google's no-JavaScript login form to reveal the phone number. The bug was discovered by a security researcher named Brutecat, who received a $5,000 reward for his finding.
Infosec industry
New tool—CoverDrop: The Guardian has released CoverDrop, a secure whistleblowing IM app to allow users to secure contact newsrooms or journalists. On a side note, I can also see this being used for threat intel, like sources in the hacking underground securely contacting a security firm.
We launched CoverDrop 🎉 providing sources with a secure and anonymous way to talk to journalists. Having started five years ago as a PhD research project, this now ships within the Guardian app to millions of users—all of which provide cover traffic. Paper, code, and more info: www.coverdrop.org
— Daniel Hugenroth (@lambda.bsky.social) 2025-06-09T13:00:45.257Z
New tool—dark-kill: Security researcher Saad Ahla has released dark-kill, a rootkit and user-mode code to shut down EDR processes.
New tool—JonMon-Lite: Security researcher Jonathan Johnson has released JonMon-Lite, a PoC technique that can collect EDR security-related data from remote endpoints without deploying an EDR agent.
Threat/trend reports: Bitsight, CardinalOps, Check Point, HUMAN Security, Malwarebytes, and Sumo Logic have recently published reports and summaries covering various infosec trends and industry threats.
Risky Business podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq take a deep dive into the hackers of Unit 29155, Russian military intelligence's sabotage and assassination group.
In this edition of Seriously Risky Business, Tom Uren and Patrick Gray talk about how Operation Endgame, the multinational law enforcement effort to tackle ransomware, is approaching the problem holistically. It's tackling the enablers of ransomware, and although it won't eliminate the crime, it'll make it harder for criminals.
