Risky Bulletin Newsletter
December 16, 2024
Risky Bulletin: Secret ransomware campaign targeted DrayTek routers for a year
Written by

News Editor
You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
Threat actors have secretly abused a suspected zero-day in DrayTek routers since August of last year to hack devices, steal passwords, and then deploy ransomware on connected networks.
According to a joint report from Forescout and PRODAFT, the attacks were carried out by a threat actor known as Monstrous Mantis—believed to be linked to the Ragnar Locker ransomware group.
The attacker used the zero-day to extract and crack the passwords of DrayTek Vigor routers and then hand out the credentials to selected collaborators.
Two of these partners have been identified as longtime affiliates of various Ransomware-as-a-Service programs. The two used the router passwords to breach corporate networks and then deploy ransomware such as RagnarLocker, Qilin, Nokoyawa, or RansomHouse.
The first partner group was identified as Ruthless Mantis (PTI-288), a former affiliate of the REvil gang, which used the credentials to breach at least 337 organizations.
The second partner was identified as LARVA-15, also known as Wazawaka, a Russian national named Mikhail Matveev, who was arrested and charged at the end of November in Russia for recent ransomware-related activities.
Forescout and PRODAFT say that Matveev didn't deploy ransomware himself but acted as an intermediary and distributed the credentials to other threat actors.
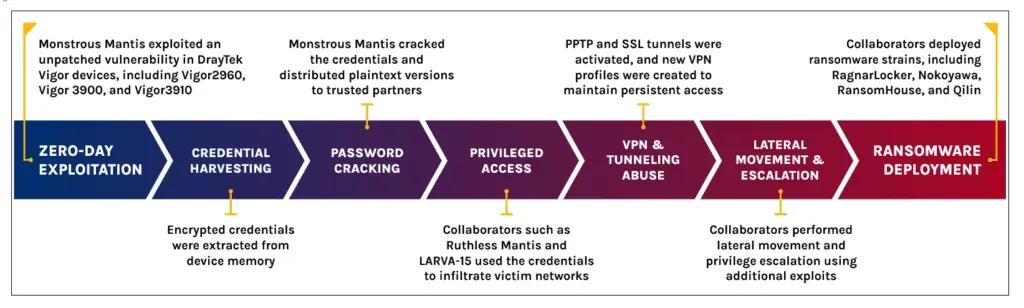
Forescout says it was unable to identify or link the zero-day to a known CVE, and it's unclear if it was ever patched.
The zero-day allegedly targeted a router firmware component (mainfunction.cgi) known to contain a large number of past security flaws.
One of the victims of this massive DrayTek hacking spree was identified as the Greater Manchester Police Department, which was hit by ransomware in September of last year.
Risky Business Podcasts
Risky Business is now on YouTube with video versions of our main podcasts. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
Clober DEX crypto-heist: The Clober DEX platform lost $500,000 worth of crypto assets after an attacker exploited a vulnerability in one of its smart contracts.
LKQ cyberattack: Autoparts company LKQ says a cyberattack has disrupted operations at its Canadian units. The incident took place last week, and no ransomware gang has yet to take credit for it.
Rhode Island data breach: Rhode Island officials have disclosed a security breach after hackers gained access to RIBridges, the state's portal for applying for public assistance programs. Officials have taken down the portal after receiving a security alert from one of its cybersecurity vendors. According to multiple reports in local media, the hackers are trying to extort state officials for a ransom. The attackers are believed to have stolen the personal data of thousands of state residents. Rhode Island has almost 1.1 million residents.
CSDN hack: A watering hole attack has been discovered on CSDN, China's largest IT community portal. An unknown threat actor has added malicious code to one of the site's JavaScript files to target selected users linked to media organizations. According to Chinese security firm QiAnXin, the malicious code showed a fake error message that prompted users to download and install malware on their systems. It is still unknown how the attackers managed to corrupt and edit the CSDN's JavaScript files.
General tech and privacy
Amazon stops Office rollout: Amazon has delayed for a year the deployment of Microsoft Office 365 software to staff. According to a Bloomberg report, Amazon paused the rollout after Russian hackers gained access to Microsoft's internal staff emails. The retail giant signed a $1 billion contract last year to move its roughly 1.5 million staff from in-house Microsoft tools to the cloud version of Office. The move is now scheduled for next year.
Horny soldiers are exposing their location: Reporters from Follow The Money have tracked the movements of hundreds of Western soldiers through dating apps like Tinder.
Google suspends Play payments in Russia: Google will cease all payments to Play Store app developers with Russian bank accounts on December 26. The decision comes in response to new international sanctions on the Russian banking sector. Major payment processors like Mastercard and Visa have left the country after the Kremlin's invasion of Ukraine in 2022. [Additional coverage in the Kyiv Independent]
Threads copies BlueSky: Despite all its overpaid UI/UX designers, Meta has copied and re-implemented BlueSky's starter packs inside Threads.
Government, politics, and policy
Crossed Swords 2024: NATO's CCDCOE kicked off its Crossed Swords 2024 offensive cyber exercise in Tallinn last week.
"This year's exercise is designed to train military command elements in the command and control of offensive cyberspace capabilities as well as support the development of other operational domain and tactical skills related to cyberspace, such as information operations. The exercise is integrated with a concurrent Special Forces exercise with the aim of strengthening collaboration between kinetic and cyber units within the context of multi-domain operations."
Trump admin spying: An MSNBC report claims the first Trump administration had spied on the phone records of both Democrat and Republican lawmakers.
CISA RFC: CISA has requested public comments on its proposed National Cyber Incident Response Plan (NCIRP). [h/t Ravi Nayyar]
Cambodia blocks 16 crypto exchanges: The Cambodian government has blocked access to 16 crypto exchanges, including some large portals such as Coinbase, Binance, and OKX. The ban was enforced by the country's financial regulator after the companies failed to register with local authorities. The 16 sites are part of a larger ban of over 100 websites. Most of the banned sites are gambling-related. [Additional coverage in Nikkei Asia]
Russia blocks Viber: Russia's telecommunications watchdog has blocked access to the Viber secure messaging application as part of its latest crackdown against Western services. Roskomnadzor claims the app was being used to sell drugs and recruit Russian citizens for terrorist and extremist purposes. According to reports, Viber had over 14.5 million Russian users, which accounted for a quarter of all Russians who used a secure messenger.
Risky Business Podcasts
In this podcast, Tom Uren and Adam Boileau talk about the continued importance of hack and leak operations. They didn't really affect the recent US presidential election, but they are still a powerful tool for vested interests to influence public policy.
Arrests, cybercrime, and threat intel
DPRK IT workers charged: The US Justice Department has indicted 14 North Korean nationals who were part of a scheme to bypass international sanctions by working in IT jobs at Western companies. Officials say the workers used false identities and laptop farms to hide their identity from foreign companies, sometimes working for multiple companies at once. They generated money through the salaries they earned and by stealing data and extorting victims. The 14 men are believed to have generated at least $88 million over the past six years for the North Korean regime. The State Department has also put up a $5 million reward for any information on the 14 and similar schemes.

Rydox takedown: Law enforcement authorities have seized the infrastructure of Rydox, an online marketplace that sold hacking tools, carding data, and personal information. Three of the site's administrators were also arrested, two in Kosovo and one in Albania. Officials say Rydox made over $230,000 in sales since its launch in early 2016.
ABK captured and extradited: US authorities have extradited a Nigerian national from Ghana to face charges for a large-scale BEC campaign. Known as ABK, Abiola Kayode has been on the FBI's Cyber Most Wanted list since 2020, prior to his arrest. Kayode was part of a six-man group that stole over $6 million from over 70 businesses. Four of the six members have been detained and received lengthy prison sentences.

Scam farms are downsizing in the Philippines: Filipino government officials said in a press conference last week that online cyber scam gangs are downsizing operations to avoid detection by local authorities. Several groups have abandoned larger office compounds for smaller buildings in isolated locations. Foreign observers estimate that over 15,000 foreign nationals are trapped in scam compounds in the Philippines. [Additional coverage via the AFP]
Scam infrastructure takedown: Thai officials have raided and seized a bunch of IT infrastructure that was supposed to be used for building illegal scam compounds. They also found and removed cables strung across a bridge to Myanmar that were used to provide internet access to some of the compounds.
New npm malware: Forty-four malicious npm packages were discovered and taken down last week. Check out the GitHub security advisory portal for more details.
Netscaler brute-force attacks: Enterprise software maker Citrix has warned customers about an increase in password-spraying attacks against NetScaler appliances. The warning comes days after a similar alert was issued by the BSI, Germany's cybersecurity agency. The company has told customers that even if they enable multi-factor authentication, they should still expect interruptions to appliances due to resource consumption.
Threat actor steals from other threat actors: A threat actor has stolen almost 400,000 WordPress account credentials from other threat actors through backdoored GitHub projects. Tracked as MUT-1244, the threat actor used multiple malicious repos advertising hacking tools, such as exploit POCs and account checkers. Victims included legitimate academic and security researchers but also other threat actors. According to DataDog's security team, the campaign is still ongoing.
Virtual card clone campaign targets Russia: Russian bank VTB has spotted a new scam where threat actors are calling customers, tricking them into installing spyware on their phones, scanning their cards, sharing the PIN, and then using the data to create virtual card clones for illegal purchases. [Additional coverage in Kommersant]
CISA warns of exposed WWS HMIs: CISA and the EPA have put out a joint advisory on Friday about the large number of human-machine interfaces exposed on the internet belonging to organizations from the US water and wastewater sector.
AS phishing campaign: Proofpoint has detected a spear-phishing campaign that targeted at least 20 Autonomous System (AS) owners, predominantly Internet Service Providers (ISPs). The campaign spoofed the communications of other ISPs on the NOC mailing list.
Okta warns of impersonation attacks: Okta warned its customers last week of a social engineering campaign where threat actors are posing as its support staff and asking victims for MFA codes.
Kuksov profile: The Times of Malta has published a profile on Semen Kuksov, a Russian national who acquired Maltese citizenship and who is part of a money laundering network for Russian gangsters and cybercriminals (per the UK NCA).
Malware technical reports
PUMAKIT: Elastic's security team has discovered a new Linux rootkit uploaded on VirusTotal. It's unclear if the new PUMAKIT rootkit was used in the wild, but its advanced and sophisticated build suggests so.
SADBRIDGE: The same Elastic security team has also discovered SADBRIDGE, a new Windows malware loader used to deploy new Go-based versions of the Quasar RAT against Chinese targets.
Mauri ransomware: A threat actor is targeting unpatched Apache ActiveMQ servers to deploy a version of the Mauri ransomware. The attacks are exploiting CVE-2023-46604 to run malicious code that creates a backdoor account on the ActiveMQ server. According to security firm AhnLab, the Mauri ransomware is a version of MauriCrypt, an open-source ransomware strain released in 2017.
Cloak ransomware: Halycon researchers have spotted a new version of the Cloak ransomware, now with the ability to execute from virtual hard disks (VHDs) to avoid detection.
HeartCrypt: PAN's Unit42 has published a write-up on a new packer-as-a-service (PaaS) called HeartCrypt.
VIPKeyLogger: Forcepoint has published a write-up on the VIPKeyLogger malware.
DarkGate vishing: Trend Micro looks at a voice phishing (vishing) campaign targeting corporate employees via Microsoft Teams. The campaign's end goal is to trick employees into installing remote access software on their systems, which are then used to deploy the DarkGate malware.
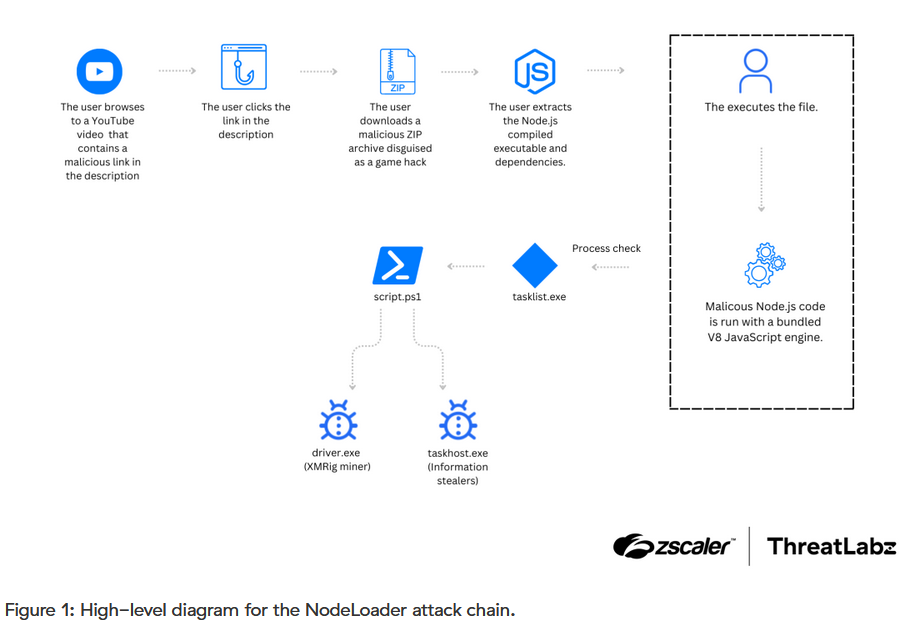
NodeLoader: Zscaler has discovered a new malware family named NodeLoader that's written in Node.js and works to distribute crypto-miners and information stealers to infected Windows systems.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about how states have very different approaches to controlling cyber operations.
APTs, cyber-espionage, and info-ops
Yokai backdoor: The Netskope security team has discovered a new backdoor named Yokai that's getting side-loaded through legitimate versions of iTop Data Recovery apps. The malware appears to have been used for cyber-espionage, being used to target Thai government officials.
Nomad Panda: Securite360 has published an analysis of a malicious QuickHeal app with links to a PLA-linked group tracked as Nomad Panda (Needleminer, RedFoxtrot).
UnitedHealthcare CEO murder campaign: According to a Forbes report citing research from Cyabra, networks of fake accounts on Twitter and Facebook are using the murder of UnitedHealthcare CEO Brian Thompson to urge further violence against other executives.
Vulnerabilities, security research, and bug bounty
Apache Struts vulnerability: Authorities from Australia and Belgium have warned organizations to urgently patch an Apache Struts vulnerability that can lead to RCE attacks. Tracked as CVE-2024-53677, the bug was patched at the end of November but generally went under the radar all this time. The vulnerability can allow attackers to manipulate file upload parameters and place files on Struts servers that can get automatically executed.
Discord RCE: Bug hunter Mohan Sri Rama Krishna Pedhapati has repurposed an old V8 exploit to achieve RCE attacks on Discord, where the exploit executes when users open a new message.
Weasis write-up: PartywaveSec has published a write-up on CVE-2024-55557, a hardcoded key found in Weasis, an open-source web-based viewer for DICOM medical imagery. A PoC exploit is also available on GitHub.
Ruijie Cloud vulns: Claroty has published a write-up on 10 vulnerabilities impacting Ruijie devices that connect to the company's cloud platform.
Fortra GoAnywhere updates: Fortra has released a patch for an information disclosure bug in its GoAnywhere file-sharing MFT.
Suricata security updates: The Suricata network analysis and threat detection software has released a security update to patch five issues.
Supermicro: Supermicro—of "grain of rice" fame—has released security updates for its products containing AMD processors. This patches the BadRAM attack on AMD SEV-SNPs.
Cleo exploitation: Arctic Wolf has published its own report on the attacks on Cleo file-transfer servers using CVE-2024-50623.
Mullvad VPN security audit: X41 D-Sec has published a security audit of the Mullvad VPN app source code.
"A total of six vulnerabilities were discovered during the test by X41. None were rated as having a critical severity, three as high, two as medium, and one as low. Additionally, three issues without a direct security impact were identified."
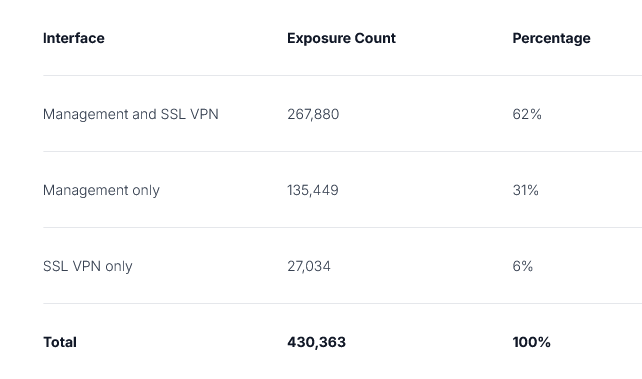
SonicWall firewall exposure: Over 430,000 SonicWall firewalls are currently connected to the internet and are exposing their management and SSL VPN interfaces online. Over half are exposing both interfaces. Security firm BishopFox warns that many systems are running older hardware and firmware versions and are vulnerable to attacks using several recently disclosed vulnerabilities.
"Overall, the results of our internet-wide survey tell us that the state of SonicWall security, while showing signs of progress, still faces significant challenges. The simple fact that over 430,000 firewall appliances are publicly accessible is cause enough for concern, but when you add that more than half are running on outdated hardware, and more than a quarter are affected by serious vulnerabilities, the big picture looks rather worrisome."
Infosec industry
Yahoo security team layoffs: Yahoo has slowly laid off over the past year almost a quarter of its internal security team, known as The Paranoids. According to a TechCrunch report, somewhere between 40 and 50 employees were let go since the start of the year. The company has laid off its entire red team and is now outsourcing all offensive pen-testing operations. The layoffs are part of a larger company downsizing. Yahoo laid off over 1,600 employees throughout the year, representing a fifth of its global workforce.
Acquisition news: Gen Digital, the parent company of Avast, Avira, and Norton, has acquired small loans and financial tech company MoneyLion.
New tool—XRefer: Google security researcher Muhammad Umair has open-sourced XRefer, an IDA Pro plugin to analyze binary files with the help of Google's Gemini AI assistant.
New tool—PyTune: Secureworks Japan has released PyTune, a post-exploitation tool for enrolling fake devices into Microsoft Intune. The tool was presented at Black Hat Europe last week.
New tool—FileRenameJunctionsEDRDisable: Security researcher Rad has released FileRenameJunctionsEDRDisable, a tool to disable EDR products by abusing the file renaming process.
Threat/trend reports: Corvus Insurance, Experian, HP Wolf Security, SentinelOne, The Software House, and Wordfence have recently published reports and summaries covering various infosec trends and industry threats.