Risky Bulletin Newsletter
February 17, 2025
Risky Bulletin: Sandworm deploys Tor nodes on hacked networks
Written by

News Editor
This newsletter is brought to you by Rad Security. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
No intro in this edition since I was traveling over the weekend.

Risky Business Podcasts
Risky Business is now on YouTube with video versions of our main podcasts. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
Ukraine hacks Gazprom contractors: Ukraine's military intelligence agency GUR claims to have hacked Gazstroyprom, Gazprom's main construction contractor. GUR hackers have allegedly wiped over 120 servers and more than 10,000 computers. The attack is believed to have impacted Gazprom's ability to build and maintain its oil and gas infrastructure. The hack comes as Ukraine continues to bomb Russian oil and gas infrastructure using drones. [Additional coverage in UNN]
On-Nara hack: South Korea's intelligence agency is investigating North Korea's possible involvement in the hack of the document management platform On-Nara. [Additional coverage in KBS]
Lee Enterprises cyberattack: US news media giant Lee Enterprises was hit by a cyberattack and was unable to print and deliver some newspapers in due time. [Additional coverage in TechCrunch]
New Paragon victim comes forward: Italy-based David Yambio, a critic of Italy's Meloni government, says he was targeted with spyware. Yambio has documented abuses suffered by migrants and refugees held in Libyan detention camps by the Italian government. [Additional coverage in The Guardian]
zkLend crypto-heist: Hackers have stolen over $8 million worth of crypto-assets from DeFi platform zkLend. [Additional coverage in CoinSpeaker]
Ionic crypto-heist: The Ionic DeFi platform has been hacked for $8.8 million worth of crypto assets. [Additional coverage in CoinCatcher]
Lexipol hack & leak: A furry-themed hacking group has breached and leaked thousands of files from Lexipol, a Texas company that develops manuals and training materials for US police and first responders. The leaked documents contain procedures for dealing with armed assailants, informants, and high-speed chases. The group says it leaked the data because there aren't "enough hacks against the police." [Additional coverage in The Daily Dot]
DOGE defaced: A hacker named "roro" has defaced the DOGE website after taking over its backend database, which the agency's staff left exposed on the internet. [Additional coverage in 404 Media]
Codeberg DDoS: Codeberg, an EU organization supporting open-source projects, has been dealing with a DDoS attack. The incident appears to be linked to a far-right group that has been harassing the organization with spam and hate messages on its issue tracker. This appears to have been happening for more than a month now.
GTA San Andreas leak: The source code of the GTA San Andreas game has been leaked online, in another major security breach for the incident over the past three years. Beware, there was also a similar leak last month that also contained ransomware. [Additional coverage in SporsKeeda]
Doxbin hacked: A hacking group named Tooda has breached and defaced anonymous paste/doxing site Doxbin and doxed the site's alleged two administrators. [h/t vxdb]
General tech and privacy
PSN mega outage: The Play Station Network was out for 18 hours, the second-largest outage in its history, behind its three-week hack outage of 2011. Sony says the outage was caused by an operational issue and not by a cyberattack. [Additional coverage in BizzBuzz]
RedNote security audit: Citizen Lab has published a privacy and security audit of Chinese social media app RedNote. It's not good at all.
Instagram working on downvote button: Meta is working on adding a downvote button to Instagram comments. [Additional comments in The Verge]
Quote-posts coming to Mastodon: The Mastodon team says it is now working on adding quote-posts to the platform after refusing to add the feature for years and years.
Opera Air: Opera has launched a new browser named Opera Air. The browser is designed to help users maintain their health by prompting them to take breaks, follow breathing exercises, take regular breaks, and more.
Android 16 will block side-loading during calls: Google is working on a new security feature for Android that will block users from making sensitive changes to their device during a phone call. Users won't be able to side-load apps and enable device accessibility features during a call. The new feature is designed to counter voice scams and social engineering attacks. The new in-call blocks will launch later this year with the launch of Android 16. [Additional coverage in Android Authority]
Government, politics, and policy
UK asks for Apple encryption backdoor: The UK government has allegedly ordered the UK government to create an encryption backdoor to allow law enforcement access to encrypted cloud backups. [Additional coverage in The Verge]
UK drops military training for cyber staff: The British military has dropped basic military training for new cyber specialist forces. New recruits are now exempt from the mandatory fitness and weapons training that regular military recruits go through. Officials have dropped the basic training requirement to address a shortage of cyber specialists across its navy and air force vacancies. [Additional coverage in The Record]
NY bans DeepSeek: After Texas, the state of New York has now also banned the use of the DeepSeek AI on government-owned devices.
NSA Big Delete: The White House has told the NSA to delete websites and internal documents containing a list of 27 "banned" terms. The list includes many generic DEI-related terms and will impact many cybersecurity-related documents and websites (i.e., privilege as in "privilege escalation").
CISA employee backlash: The Trump administration has put 17 CISA employees on leave for their work on election security. According to CyberScoop, the 17 were members of a CISA team that dealt with election-related dis- and misinformation. The move comes after the Justice Department also disbanded its Foreign Influence Task Force, which also fought foreign dis- and misinformation threats targeting US elections.
New cyber director nominee: The White House plans to nominate former GOP lawyer Sean Cairncross for the role of national cyber director. [Additional coverage in NextGov]
FISC opens up: The Foreign Intelligence Surveillance Court (FISC) will allow a few select members of Congress to attend proceedings where FISA surveillance requests are approved. [Additional coverage in The Record]
Cyber Conspiracy Modernization Act: Two US senators have proposed a bill that would toughen CFAA cybercrime penalties, raising the maximum threshold for some crimes to life in prison. [Additional coverage in CyberScoop]
Germany says disinfo is not illegal: Germany's Interior Ministry says that the dissemination of disinformation by foreign states inside Germany is not specifically prohibited and not punishable by law. Officials say this has complicated their response to recent Russian campaigns ahead of the country's election. The Ministry says they are successful only due to the willingness of private companies to act, such as mobile providers and hosting providers. [Additional coverage in Correctiv]
Ukraine struggles with Russian disinfo: Natalia Tkachuk, head of cyber and information security at Ukraine's National Security and Defense Council, says Ukraine is struggling to counter Russian disinformation campaigns without the US government's help. [Additional coverage in The Record]
Thai police scam committee: Thai police have set up a special committee to investigate possible links between its officers and scam compounds activity on the border with Myanmar. [Additional coverage in the Bangkok Post]
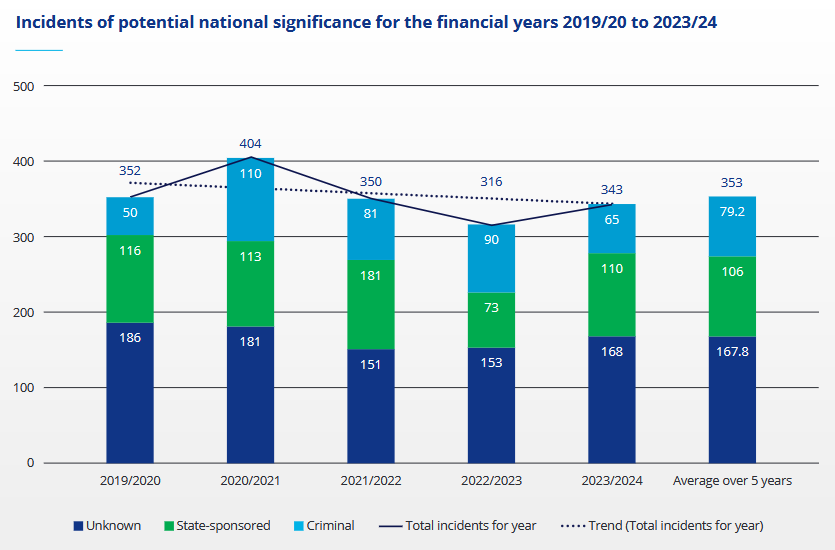
NZ cyber threat report: New Zealand's cybersecurity agency has published its yearly cyber threat report.
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Jimmy Mesta, CTO and Co-Founder of Rad Security (formerly KSOC). Jimmy talks about how companies adopting new AI-based technologies may accidentally expose their infrastructure and data to new threats.
Arrests, cybercrime, and threat intel
8Base takedown: European and US law enforcement agencies have seized server infrastructure linked to the 8Base ransomware gang. Thai police detained four Russian nationals linked to the scheme. The four suspects are aged between 27 and 39 and were arrested in the city of Phuket earlier this month. The group allegedly ransomed more than 1,000 victims and made over $16 million from ransom payments. The 8Base ransomware launched in early 2023 and is a variant of the older and prodigious Phobos strain.

Serial swatter pleads guilty: A US judge has sentenced a California teen to four years in prison for orchestrating hundreds of bomb threats and swatting attacks across the US. Alan Filion made over 375 swatting and bomb threats over a period of 18 months between 2022 and 2024. Officials described the 18-year-old as one of the most prolific swatters in American history. According to Wired, he also operated Torswats, a Swatting-as-a-Service operation hosted on Telegram.
AI voice scam targets Italy's elites: Scammers have used AI voice cloning technology to impersonate Italy's Defense Minister and request money from Italy's richest businessmen to free kidnapped journalists. The scheme targeted the owners of companies such as Prada, Armani, Inter Milan, arms maker Beretta, and pharma giant Menarini. Targets were asked to transfer €1 million to the scammers' accounts, and at least one victim paid. [Additional coverage in Euronews]
Prisoner swap: The Trump administration will swap a major Russian cybercriminal for the release of an American teacher detained in Russia. US officials will set free Alexander Vinnik, the founder of former cryptocurrency exchange BTC-e. Vinnik pleaded guilty to money laundering charges last year. His platform laundered over $4 billion worth of Bitcoin, including ransomware payments. [Additional coverage in the BBC]
Zservers takedown and sanctions: Dutch police seized the server infrastructure of Russian bulletproof hosting provider Zservers. Australia, the US, and the UK have also imposed sanctions on Zservers, its UK front company xHost, two admins, and four employees. All are Russian nationals. Officials say the service has provided server infrastructure for many cybercrime operations, including the infamous LockBit ransomware gang. The Sydney Morning Herald has published a profile on Zservers and how Australian officials deleted the Medibank stolen data off their servers when they were out drinking, so they couldn't respond in time.

SEC hacker pleads guilty: Alabama man Eric Council pleaded guilty to hacking the SEC Twitter account last year to publish a hoax that the agency had approved the trade of crypto ETFs.
Victims rescued from Myanmar scam centers: Myanmar police rescued 261 victims who were kidnapped and forced to work in online scam compounds operating in the country's Myawaddy region. The victims were handed to Thai authorities for repatriation. [Additional coverage in VOA]
DPRK laptop farmer pleads guilty: An Arizona 48-year-old woman pleaded guilty to operating a laptop farm for North Korean IT workers.
DOGE staffer linked to The Com: One of Elon Musk's DOGE staffers has been linked to The Com, an underground community linked to swatting, death threats, and cyberattacks. [Additional coverage in KrebsOnSecurity]
Election-themed scams: Online scammers are using political and election-themed Twitter ads to lure victims on crypto investment scam portals. Per Infoblox, the campaign only targets Canada.
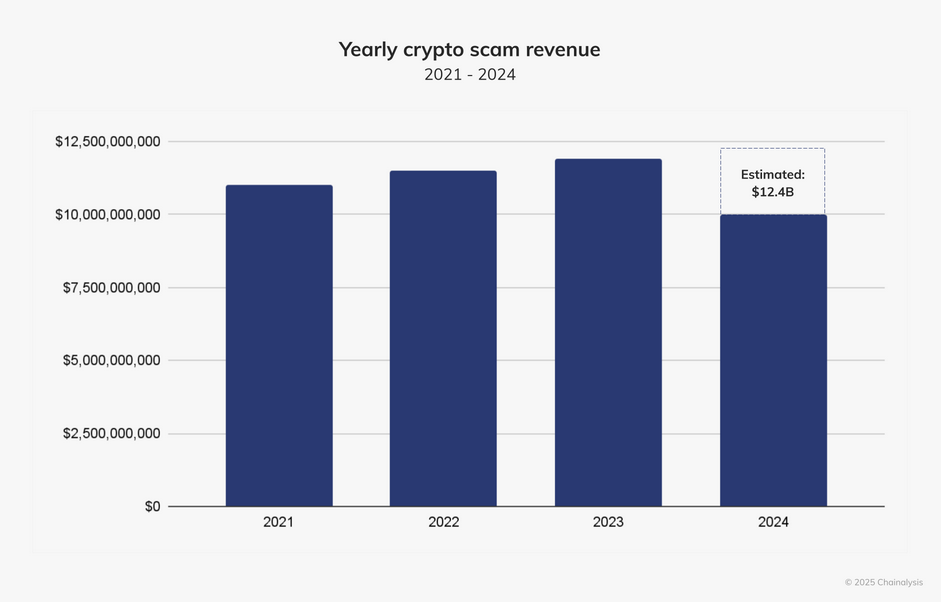
Cyber scam profits: Chainalysis has found over $9.9 billion worth of crypto-assets last year linked to online scam gangs. Almost 85% of the funds are linked to investment and romance scam operations. The company expects the number to grow to$12.4 billion as it uncovers new cryptocurrency addresses in the coming months.
Brute-force campaign: The Shadowserver Foundation has spotted a massive brute-forcing campaign targeting Palo Alto Networks, Ivanti, and SonicWall network devices.
New exploitation surge: GreyNoise has spotted a new wave of attacks targeting ThinkPHP-based websites and ownCloud servers.
More HuggingFace badness: ReversingLabs has discovered a new batch of malicious ML models on the HuggingFace portal.
Malware on Steam: Steam has removed the PirateFi game from its portal after users found malware in the game's files. [Additional coverage in Gizmodo]
New npm malware: Fifty-three malicious npm packages were discovered and taken down last week. Check out the GitHub security advisory portal for more details.
Astaroth: SlashNext looks at Astaroth, a new 2FA phishing kit that can target Gmail, Yahoo, AOL, O365, and other third-party services.
Spyware vendor shuts down: Spanish spyware vendor Variston has been formally liquidated, according to paperwork filed in Barcelona. [Additional coverage in TechCrunch]
New spyware vendor discovered in Italy: An Italian company named SIO is behind a spyware strain named Spyrtacus. According to a TechCrunch investigation, the company appears to be a provider of spyware tools to the Italian government. The spyware was found hidden in Android apps posing as WhatsApp and customer support tools provided by cellphone providers. A 2024 Kaspersky report claims the spyware also has iOS, macOS, and Windows versions.
Malware technical reports
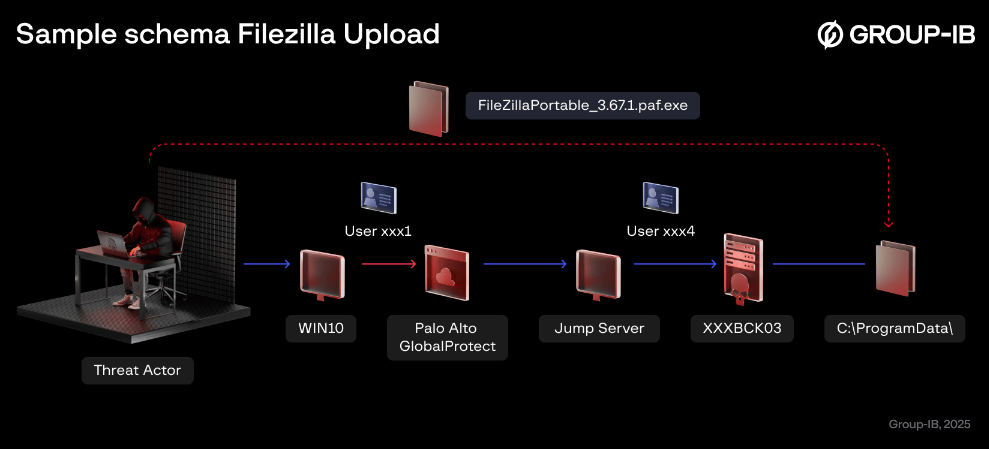
RansomHub: Group-IB has published a profile on RansomHub, the RaaS that replaced AlphV and LockBit at the top of the ransomware world last year. The report looks at recent operations that involved the acquisition of source code from the Knight/Cyclops platform, the use of FileZilla for data exfiltration, and the use of the PCHunter tool to bypass and stop EDR solutions.
Lynx ransomware: Fortinet researchers have published a report on the relatively new Lynx ransomware.
Xloader: Zscaler researchers have published part two (part one is here) of their analysis of v6 and v7 of the Xloader malware.
I2PRAT: Sekoia has published a deep dive of I2PRAT, a remote access trojan using the I2P network for C2 comms.
FinStealer: CyFirma has published an analysis of FinStealer, a Kotlin-based Android infostealer.
LummaStealer: CloudSEK researchers have published a deep dive into a phishing campaign targeting the edu sector with the LummaStealer.
BadIIS backdoor: Trend Micro has published a report on BadIIS, a new IIS backdoor used mainly to manipulate SEO results.
GhostWeaver backdoor: TRAC Labs has spotted a new final payload being dropped by the SocGolish (FakeUpdates) network. The new malware is being tracked as GhostWeaver, it is written in PowerShell, and usually deployed via an intermediary step (via the MintsLoader).
Prometei: Security researcher Cryptax has published a two-part analysis of the Prometei botnet.
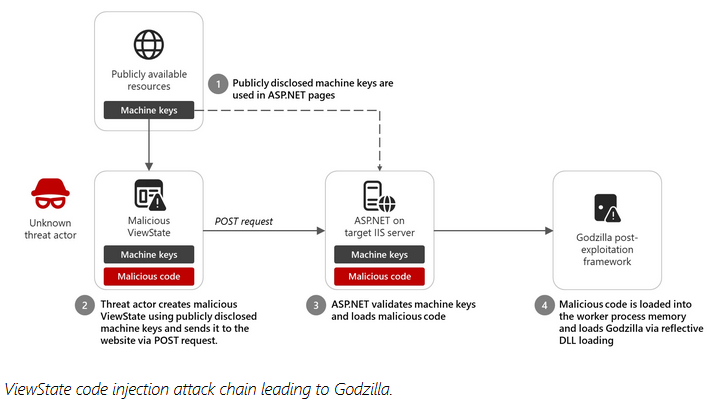
Godzilla: Microsoft looks at a campaign targeting ASP.NET servers and deploying the Godzilla webshell. Don't ask me why Microsoft classifies Godzilla as a post-exploitation framework.
Sponsor section
Explore the future of cloud security with signatureless, behavior-based threat detection. In this video, we tackle the pressing question: "Is the cloud too noisy for behavioral detection to work?" We'll break down the limitations of signature-based methods and introduce runtime verification as a more effective solution for identifying threats in dynamic cloud environments.
APTs, cyber-espionage, and info-ops
FINALDRAFT and REF7707: Elastic's security team looks at FINALDRAFT, a new post-exploitation toolkit used by an APT group the company tracks as REF7707. The novelty here is the use of Outlook as a communication channel via the Microsoft Graph API.

Salt Typhoon (RedMike) still active: The Salt Typhoon Chinese cyber-espionage group is still active and hacking new internet service providers. The new campaign took place between December 2024 and January 2025 and is exploiting unpatched Cisco networking devices. According to Recorded Future, the group has targeted over 1,000 Cisco devices globally. Confirmed victims include telcos in the UK and South Africa.
Chinese APT tools found in ransomware attacks: Symantec has found hacking tools typically used by Chinese cyber-espionage groups in a ransomware attack in South Asia. The tool is a recent version of PlugX, a backdoor used by Chinese APTs for over a decade. Researchers believe the APT used the ransomware to hide a potential espionage operation or deployed it as part of a separate financially motivated attack designed to subsidize future operations.
RedCurl/EarthKapre: eSentire researchers look at a recent killchain used by the RedCurl (EarthKapre) espionage group.
Winnti's RevivalStone campaign: Japanese IT company LAC has published a report on RevivalStone, a Winnti APT campaign targeting Japanese companies.
Emerald Sleet adopts ClickFix: A North Korean APT group named Emerald Sleet (aka Kimsuky) has adopted the ClickFix social engineering technique in recent operations, becoming the second known APT group after APT28.
Lazarus npm attacks: SecurityScorecard has published a report on the Lazarus APT group's operations involving malicious npm packages.
Muscular approach: In a blog post last week, CrowdStrike has called for "either more effective diplomacy or a more muscular approach to states like China, Russia, Iran, and North Korea" when it comes to cyber.
Mythic Likho: Kaspersky has published a report on Mythic Likho, a group targeting the Russian private sector. The new attacks have leveraged the Mythic red-team framework and Loki, a new version of the older Merlin backdoor.
Russian disinfo ops expand to BlueSky: At least two Russian disinformation groups are targeting German audiences ahead of the country's upcoming federal elections. The campaign used deepfakes and fake news sites to push fake narratives ahead of the election. The narratives promoted far-right and pro-Kremlin party AfD and attacked Germany's current pro-EU ruling alliance. Security firm Recorded Future (and others) have linked the info-ops to groups tracked as CopyCop and Doppelganger. The German campaign marks the first time Russian disinfo groups targeted BlueSky audiences.
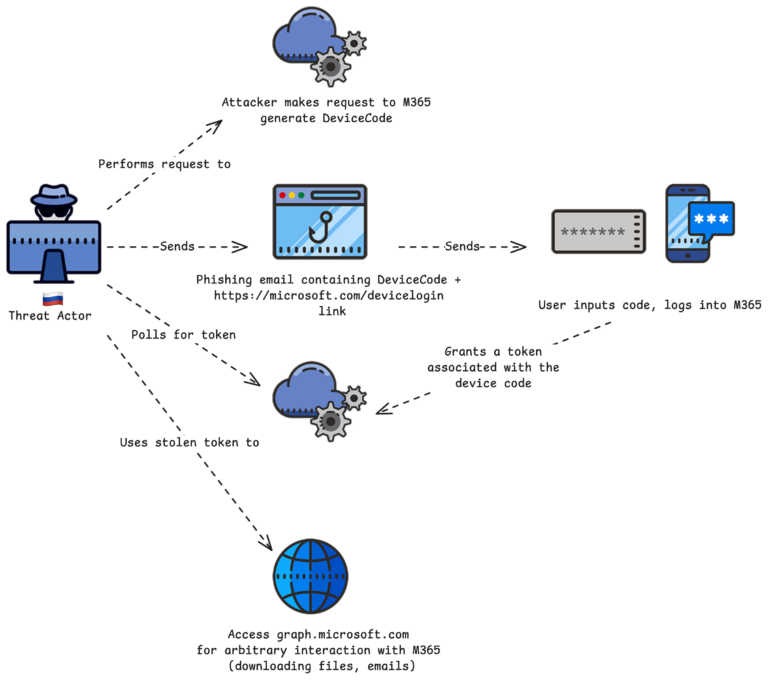
Russian APTs adopt DCA phishing: Russian APT groups have adopted Device Code Authentication phishing as part of recent operations. The technique involves tricking victims to authenticate on Microsoft servers as coming from an input-constrained device such as a smart TV, IoT device, or printer. Victims share a one-time passcode with the attackers that grants them access to their accounts. Security firm Volexity has linked recent attacks to at least three Russian APT groups, including APT29, a cyber-espionage unit inside Russia's SVR intelligence agency. Microsoft has attributed the campaign to something called Storm-2372.
Russian APTs delve into the cybercrime underground: A Google Cloud report looks at the increasing trend of Russian APTs leveraging underground cybercrime services and tools for their main cyber-espionage goals. A similar trend was also spotted across Iranian and Chinese APTs but to a smaller degree.
Sandworm: EclecticIQ looks at a new Sandworm (APT44) campaign targeting Ukrainian organizations.
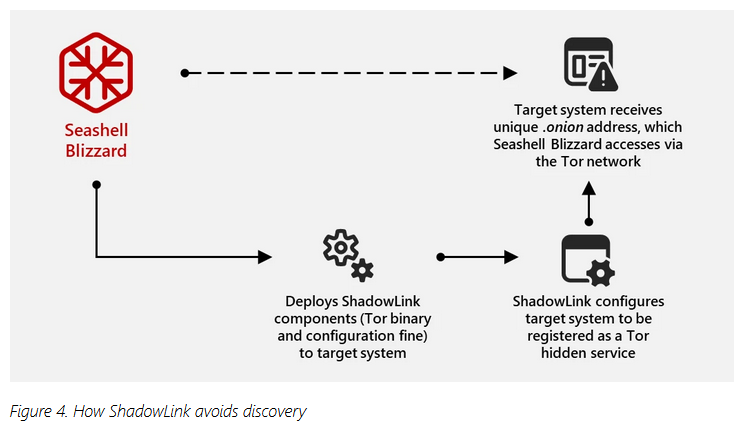
Seashell Blizzard BadPilot campaign: A unit inside Russia's Sandworm espionage group is hacking networks and deploying webshells and backdoors as part of a large initial access campaign. Some of the intrusions stand out because of a new command and control (C&C) method called ShadowLink. The technique involves installing a Tor hidden service on a compromised host and assigning each host a unique Tor onion address. Microsoft says the ShadowLink technique allows Sandworm to create a secret tunnel to the host with minimal opportunity for detection.
Vulnerabilities, security research, and bug bounty
Patch Tuesday: Yesterday was the February 2025 Patch Tuesday. We had security updates from Adobe, Apple, Microsoft, SAP, Ivanti, Fortinet, Cisco, Palo Alto Networks, Supermicro, SolarWinds, CrowdStrike, NVIDIA, Intel, AMD, Schneider Electric, Siemens, Drupal, Magento, GitLab, and OpenSSL. The Android Project, Arm, Chrome, Firefox, F5, Juniper, Progress, Moxa, Zyxel, Synology, Zoom, and Veeam released security updates last week as well.
Microsoft Patch Tuesday: This month, Microsoft patched 67 vulnerabilities, including two actively exploited zero-days.
- CVE-2025-21391 - Windows Storage Elevation of Privilege Vulnerability
- CVE-2025-21418 - Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability
Unpatched Windows zero-day: Security firm ClearSky says it found a Chinese APT exploiting a new Windows UI zero-day that survived unpatched through last week's Patch Tuesday. The attribution is Mustang Panda, but that remains to be confirmed since this is somewhat of a generic APT attribution, just like Lazarus. [Additional coverage in SecurityWeek]
Apple patches iOS zero-day: Apple has released a security update to patch an actively exploited zero-day in its iOS mobile operating system. Tracked as CVE-2025-24200, the zero-day can be used to disable USB Restricted Mode on a locked device if an attacker has physical access to the device. Apple's patch comes a week after Google also patched a similar zero-day that targeted the Android USB component. Apple credited Bill Marczak of Citizen Lab with finding the zero-day. Quarkslab has also published a first deep dive into the zero-day's details here.
PostgreSQL zero-day: Rapid7 has discovered a second PostgreSQL zero-day exploited in the BeyondTrust hack last year. The initial patch blocks both zero-days, although the second one wasn't publicly known (CVE-2025-1094).
Fortinet zero-day: Fortinet says hackers are exploiting a second zero-day in the websocket module of FortiOS to hijack its firewalls and networking gear. This is the second zero-day in this module after CVE-2024-55591, patched last month. This one has a CVE of CVE-2025-24472.
PAN auth bypass under attack: Threat actors are actively exploiting a new vulnerability in Palo Alto Networks firewalls. The attacks began a day after security firm Assetnote published a write-up on the bug and a day after Palo Alto released patches. Tracked as CVE-2025-0108, the bug is an Nginx/Apache path confusion vulnerability that can lead to an authentication bypass in the affected firewalls.
SonicWall devices under attack: The same thing also happened with a SonicWall vulnerability (CVE-2024-53704) from January that came under attack a day after security firm BishopFox published a write-up and PoC this week.
Meta bug bounty program review: Meta says it paid over $2.3 million via its bug bounty program last year, topping $20 million in bug payouts since 2011.
Copilot bug bounty program: Microsoft has raised the payouts for its Copilot AI bug bounty program.
CertiK apologises for security audit: Blockchain security firm CertiK has publicly apologised for conducting a paid security audit for a stablecoin launched by Cambodian cryptocurrency exchange Huione, a company linked to laundering the profits of Southeast Asian cyber scam compounds. [Additional coverage in DLNews]
NVIDIA AI vulnerability: Wiz has published a report on a critical severity vulnerability (CVE-2024-0132) in the NVIDIA Container Toolkit and GPU Operator, affecting cloud service providers.
Google plugs YouTube email leak: Two bug hunters found a bug in the Google Internal People API that could have been abused to leak any YouTube user's email address.
npm crypto private key leak: The Elliptic npm cryptography library has patched a bug that could have leaked private keys from JSON network strings.
Libarchive vulns in Windows 11: Taiwanese security firm DEVCORE looks at several vulnerabilities in Microsoft's integration of Libarchive in Windows 11, a library the company is using to support additional file archive formats.
whoAMI attack: DataDog researchers have found a way to exploit the process of retrieving Amazon Machine IDs (AMI) to run malicious code on AWS instances. They named the attack whoAMI.
Infosec industry
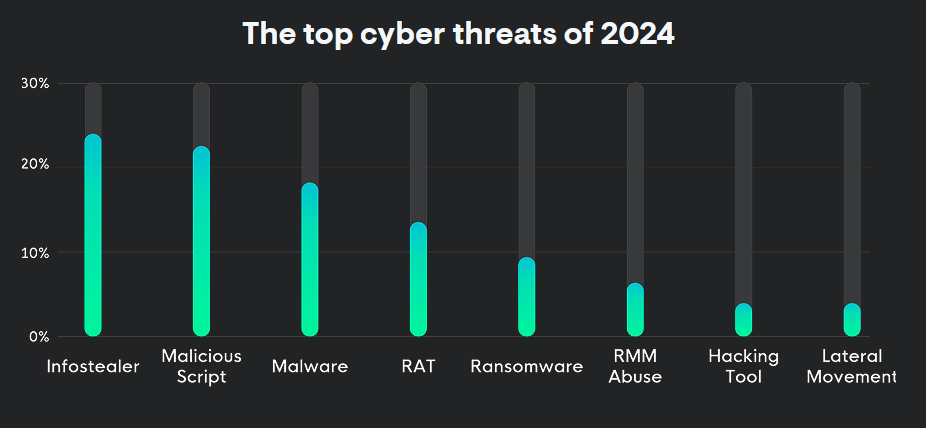
Threat/trend reports: Abnormal Security, Akamai, AU10TIX, Backblaze, Black Kite, Chainalysis, CyberCX, Forescout, Gen Digital, Google Cloud, Huntress, Mimecast, NICT, NCC Group, NZ NCSC, Selectel, and Wiz have published reports and summaries covering various infosec trends and industry threats.
Acquisition news #1: Israeli security firm CyberArk has acquired Zilla Security, a provider of Identity Governance and Administration (IGA) solutions.
Acquisition news #2: Risk management platform Drata has acquired SafeBase, a company for building security questionnaires and trust programs.
NanoLock shuts down: Cybersecurity startup NanoLock has ceased all operations. [Additional coverage in Calcalist]
New tool—LOLC2: DFIR specialist Mthcht has released LOLC2, a collection of C2 frameworks that leverage legitimate services to evade detection.
New tool—Raccoon: LRQA's Nettitude team has open-sourced Raccoon, a C# tool for extending the screenshot functionality of Command and Control (C2) frameworks.
New tool—Stifle: IBM X-Force researcher Logan Goins has released Stifle, a .NET post-exploitation utility for abusing explicit certificate mappings in ADCS.
New tool—SiphonDNS: TTP Report has released SiphonDNS, a tool to exfiltrate data via DNS.
"Some of them can be hidden behind trusted public DNS servers like Google and OpenDNS, others will require direct connection to your authoritative server."
BSides Budapest videos: Talks from the BSides Budapest 2024 security conference, which took place last May, are available on YouTube.
Risky Business Podcasts
In this podcast, Tom Uren and Patrick Gray talk about Apple's refusal to obey a UK government order to provide the capability to access encrypted iCloud data. It's the latest round in the ongoing government vs technology fights over warrant-proof encryption, and again, it looks like governments will lose.
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about Israeli spyware vendor Paragon, how and why it positions itself to sell to the US market, and how its capabilities might work.
