Risky Bulletin Newsletter
June 20, 2025
Risky Bulletin: Russian hackers abuse app-specific passwords to bypass MFA
Written by

News Editor
This newsletter is brought to you by enterprise browser maker Island. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
Russian cyber-spies have developed a new social engineering technique designed to extract application-specific passwords from their targets.
Also known as app passwords, or ASPs, these allow attackers to bypass multi-factor authentication and access a victim's Gmail accounts.
App passwords are supported on multiple online platforms, but this campaign specifically targeted Google's ASPs. These are 16-character codes that users manually generate from their Google account security page. They can be copy-pasted inside older apps that don't support Google's more modern 2FA/MFA authentication procedures.
For example, older email clients such as Mozilla Thunderbird require an app-specific password to connect to a user's Gmail inbox and interact with Google servers.
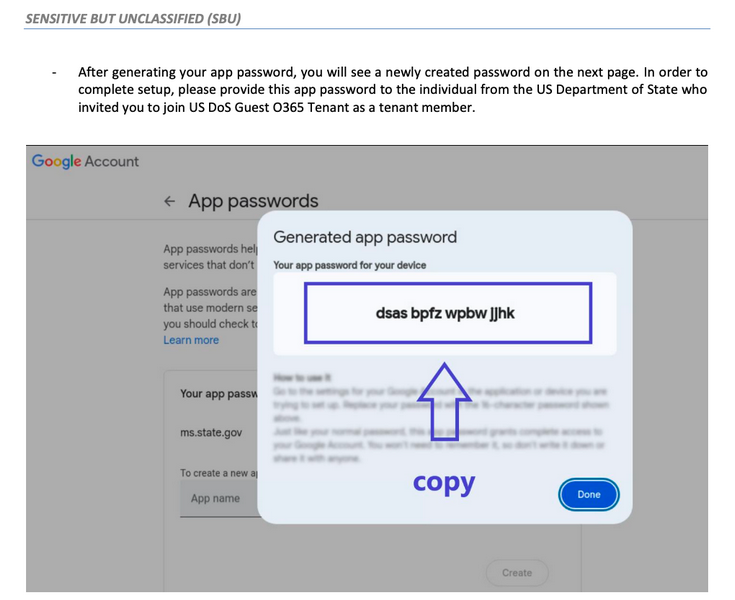
In reports published on Wednesday, CitizenLab and Google say they've spotted a group named UNC6293 pose as the US State Department to approach targets and trick them into generating and handing over an app-specific password.
Google tentatively linked the group to APT29, the cyber branch of the Russian SVR intelligence service.
Targets included experts on Russian politics and the Ukrainian war, which fits the mold of most Russian cyber ops over the past year due to the country's invasion of Ukraine and its need to collect intelligence on Ukraine and its allies.
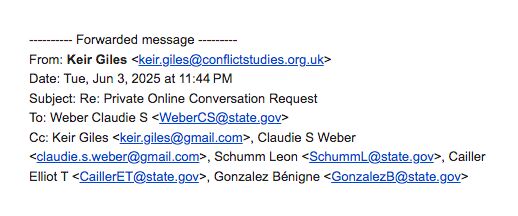
The campaign came to light after Keir Giles, a senior Russia expert with UK think tank Chatham House, fell victim and received a security alert from Google about suspicious activity on his account from an unrecognized IP address.
Giles notified CitizenLab, which then helped him investigate the intrusion together with Google.
In a LinkedIn post over the past weekend, Giles disclosed the hack and warned that Russian intelligence may try to leak the content of his inbox, including altered messages, to fit certain propaganda tunes.
The abuse of app-specific passwords falls in line with recent Russian cyber ops that have adopted extremely complex social engineering techniques and the exploitation of lesser-known authentication methods.
Some of these include tricking victims into approving an attacker's authentication token to their Microsoft Entra account, tricking victims into adding an attacker's device to Signal accounts, tricking victims into generating and handing over Device Code Authentication codes, and tricking victims into handing over OAuth codes for M365 accounts.
Quite the annoying bunch, but it is true that necessity is the mother of invention.
Risky Business Podcasts
The main Risky Business podcast is now on YouTube with video versions of our recent episodes. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
Viasat is 10th Salt Typhoon victim: US satellite and wireless networking company Viasat has been identified as the latest victim of Chinese espionage group Salt Typhoon. The company is the group's tenth known victim after its hacking spree was uncovered last year. The previous nine include Verizon, AT&T, T-Mobile, Spectrum, Lumen, Consolidated Communications, Windstream, Comcast, and data center provider Digital Realty. [Additional coverage in Bloomberg]
Chain IQ hack impacts Swiss banks: A hacker has stolen data from two Swiss banks after breaching a common IT contractor named Chain IQ. The hacker stole the data of 130,000 UBS employees and tens of thousands of invoices for Pictet suppliers. Chain IQ is a major international IT provider and lists many Fortune 500 companies as customers. [Additional coverage in SwissInfo]
Erie Insurance breach: US insurance provider Erie Insurance recovered from a security breach that took place at the start of the month. The company says it has now regained control over its systems. Erie says it found no evidence of a ransomware attack.
Episource breach: Healthcare software provider Episource says hackers have breached its systems and stolen the data of over 5.4 million patients. The breach took place in late January and lasted for almost two weeks. Stolen data included personal details along with insurance and medical records.
Scania insurance arm breach: A hacker is selling data from the insurance arm of Swedish truck maker Scania on an underground hacking forum. [Additional coverage in Cybernews]
Carrefour fined for data breach: Spain's data protection agency has fined French retail giant Carrefour €3.2 million for a past security incident. The agency says Carrefour failed to roll out protections against brute-force attacks for its customer accounts. Hackers allegedly gained access to over 119,000 accounts over the course of five different brute-force attacks in 2023. [More in the AEPD decision/PDF]
Asana MCP misconfiguration: AI-based work management platform Asana misconfigured its MCP server and leaked customer data to other platform users, per an UpGuard report.
IRIB hacked: Suspected Israeli hackers have hijacked on Wednesday the broadcast signal of Iran's state television channel IRIB. The hackers aired footage of the 2022 Mahsa Amini women's protests. The footage urged the population to take to the streets and rise against the regime. The interruption only lasted a few minutes. [Additional coverage in i24NEWS]
Happening now 🚨
— Jonathan Harounoff (@JonathanHaroun1) June 18, 2025
Iranian state TV has been hacked, taking a break from its regular propaganda programming to broadcast iconic scenes from the “Woman, Life, Freedom” uprising. #WomanLifeFreedom #زن_زندگی_آزادی @KasraAarabi pic.twitter.com/eT1AEfQxo6
Predatory Sparrow hacks Iranian crypto exchange: Hacktivist group Predatory Sparrow has stolen and burnt $90 million worth of crypto assets from Iranian exchange Nobitex. The group claims it hacked the platform because the Iranian government was using it to avoid sanctions and finance terrorist groups abroad. Predatory Sparrow also dumped the platform's source code on Telegram. A day earlier, the group also hacked Iran's largest bank—Bank Sepah. Iran cut off internet access on the same day to block Israeli cyberattacks and surveillance. [Additional coverage in CyberScoop]
General tech and privacy
Paddle fined for facilitating tech support scams: The US Federal Trade Commission has fined UK payment processor Paddle $5 million for processing payments linked to tech support scams. Paddle is required to implement effective client screening and monitoring going forward. It must also get explicit user consent before enrolling them in recurrent payments and provide ways to cancel subscriptions.
US healthcare privacy is non-existent: An investigation from The Markup has found that the websites of many US state-run healthcare providers use intrusive analytics scripts from Google and social media companies that basically track what users are doing on those sites and collecting information on health issues and drugs they take.
TikTok deal deadline extended for third time: US President Donald Trump says he will extend the deadline for a TikTok sale for a third time, which is apparently very illegal. [Additional coverage in the BBC]
Telegram in trouble in Malaysia: The Malaysian government has obtained a court order to block two Telegram channels and Telegram itself after the company failed to take down the accounts. This might be the legal precursor to authorities blocking the service in the country. [Additional coverage in Reuters]
New Psylo iOS browser: Mysk launched Psylo, a new private browser for iOS.
"In Psylo, each tab is its own silo with isolated storage, cookies, and even its own IP address. Psylo introduces advanced anti-tracking and anti-fingerprinting features that go beyond what a VPN can offer, thanks to the deep integration between Psylo and our own Mysk Private Proxy Network."
Passkeys for Meta apps: Meta has added support for passkeys for the Android and iOS versions of its main Facebook app. Passkeys will come to Facebook Messenger later this year.
Google EU fine to stay: The European Court of Justice advocate proposed that the court dismiss Google's appeal and uphold a €4.1 billion fine for its monopoly over the mobile OS market through its control over the Android OS and the Google Play Store. [Additional coverage in CNBC/Decision PDF]
FPTrace fingerprinting research: A team of academics has published research on FPTrace, a system to detect the use of browser fingerprinting online. While not a new technique, the research finds that the practice is more widely used than previously thought before, especially after Google threatened to remove support for third-party cookies. [More on the Texas A&M blog]
Government, politics, and policy
DHS warns of signal jammers: The DHS says Chinese tech companies are trying to subvert the inspection or try to smuggle illegal signal jammers into the US. The agency has recorded an 830% increase in seized signal jammers since 2021. Some of the devices are used to jam law enforcement responses and during bank robberies.
DOJ to fight tower dumps ruling: The US Department of Justice plans to file an appeal against a decision that banned it from using cell phone tower dumps as an investigative measure. [Additional coverage in CourtHouseNews]
US enforces social media reviews: The US State Department plans to review the social media activity of all incoming exchange students.
Iran blocks Western apps: The Iranian government has blocked access to the Apple and Google app stores and several Western apps. Officials previously told citizens to uninstall WhatsApp and Instagram from their devices. The government warned that Israeli intelligence services were using location data gathered through the app to track and identify targets. The Tehran regime also cut off nearly all internet access in the country following hacks at its biggest bank and cryptocurrency exchange. [Additional coverage in NBC News]
Dutch sovereign cloud: The Dutch government is building its own local sovereign cloud that will store data for its military forces.
NZ adopts minimum cyber standards: New Zealand has adopted minimum cybersecurity standards for government agencies. The new standards will apply to all business-critical and external-facing systems. Agencies will have to inventory their assets, apply timely patches, deploy MFA, and other basic protection steps. The new standards will apply from October 30.
Russia wants exact ISP network maps: Russia's communications watchdog will require local telecom operators to provide accurate maps of their network infrastructure. The Roskomnadzor wants to make sure that all traffic passes through their network traffic surveillance equipment. Telecom operators will have to provide lists of all equipment, complete with MACs, IP addresses, and device characteristics. [Additional coverage in Vedomosti]
Bolsonaro charged with illegal spying: Brazil's federal police charged former President Jair Bolsonaro with illegal spying on political rivals, journalists, and environment protection activists. Bolsonaro and the country's spy chief allegedly created a "parallel structure" inside the ABIN intelligence agency that spied on over 30,000 people. The secret ABIN unit allegedly used a spying tool named FirstMile, developed by Israeli company Cognyte. [Additional coverage in Al Jazeera]
"The far-right former president is accused of using Brazil’s intelligence agency to conduct illegal spying." Using Cognyte's FirstMile product which is an SS7 geolocation. Previousy known as SkyLock www.aljazeera.com/news/2025/6/...
— Jurre van Bergen (@jurrevanbergen.nl) 2025-06-19T14:57:41.607Z
Sponsor section
In this Risky Bulletin sponsor interview, Michael Leland, Field CTO of Island, talks about how Island manages risks from extensions, phishing, and infostealers. Even when credentials are stolen, it is still not game over, and there are still ways to prevent data loss and breaches.
Arrests, cybercrime, and threat intel
US seizes crypto scam funds: The US government has seized more than $225.3 million in cryptocurrency stolen through crypto investment scams. The sum represents the largest cryptocurrency seizure against crypto scam operations in US history. The sum was seized from accounts linked to Asia-based scammers.
Ryuk member arrested in Ukraine: Ukrainian authorities have arrested a 33-year-old man for his role in Ryuk ransomware attacks. The suspect was arrested in Kyiv in April and extradited to the US this month. Ukrainian officials say the suspect worked as an initial access broker who breached networks and then passed access to other individuals to launch the ransomware attacks.

Malicious domains for Trump-v-Elon feud: BforeAI spotted a surge in newly registered malicious domains that tried to capitalize on the Trump-v-Elon feud. Yeah! Remember that one? It was two weeks ago. Feel old yet?
New crypto-drainer campaign targets Europeans: Group-IB has spotted a phishing campaign targeting crypto users and impersonating European tax authorities. Victims are lured to phishing sites that run crypto-drainer phishing kits.
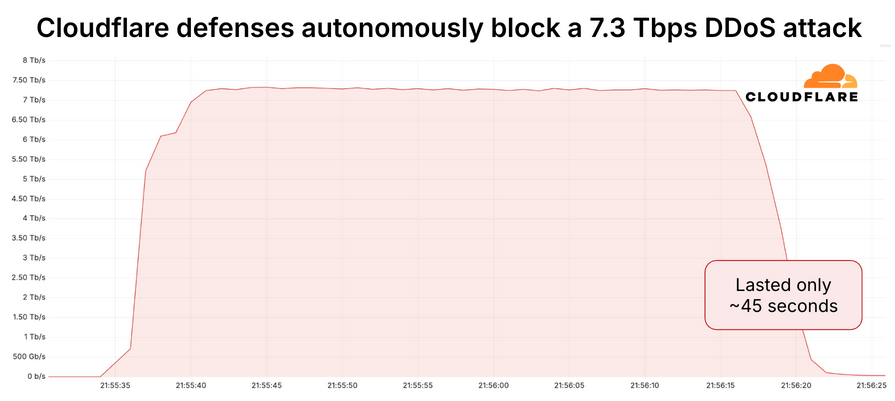
New DDoS record: Internet infrastructure company Cloudflare says it mitigated a DDoS attack that clocked at 7.3 Tbps. The attack smashes the previous DDoS record by a full 1 Tbps. The incident took place in mid-May, lasted only 45 seconds, and targeted an unnamed web hosting provider.
Mocha Manakin group: Red Canary has spotted a new threat actor group named Mocha Manakin. The group uses ClickFix campaigns to deploy a custom NodeJS-based backdoor named NodeInitRAT. Some of its infections have been used as initial access entry points by the Interlock ransomware gang.
Banana Squad group: ReversingLabs researchers discovered more than 60 GitHub repositories that contain hundreds of trojanized files. This seems to be part of the same campaign spotted earlier this month by Sophos and Trend Micro. ReversingLabs calls this group Banana Squad.
SERPENTINE#CLOUD group: Securonix has spotted a new threat actor named SERPENTINE#CLOUD involved in phishing campaigns that abuse Cloudflare Tunnels to deploy Python-based malware on infected hosts.
Shadow Vector campaign: The Acronis security team has published a report on Shadow Vector, a phishing campaign targeting Colombia with malicious SVG files that help deploy various RATs.
Malicious Minecraft mods: Check Point has uncovered a campaign using boobytrapped Minecraft mods to infect gamers with infostealers.
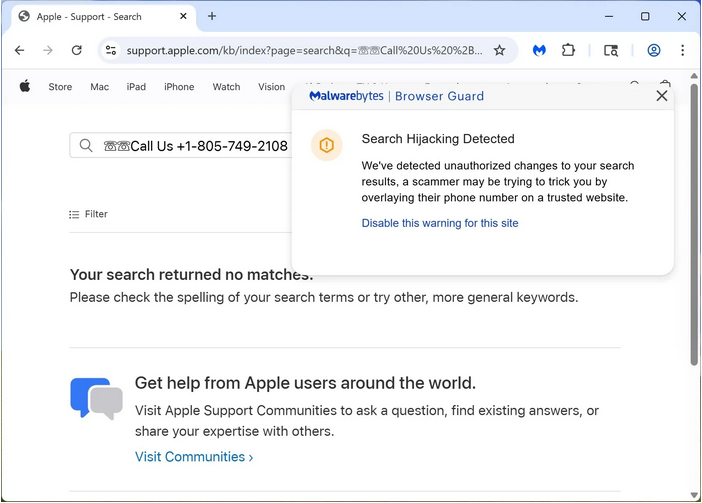
Scammers abuse search parameter injections: Malwarebytes has spotted online tech support scammers use malicious ads that redirect users to legitimate domains. The scammers are abusing a technique named search parameter injection to display malicious phone numbers inside a legitimate website's search field.
Tinker profile: Intel471 has published a profile on Tinker, a member of the Black Basta group who operated call centers, drafted phishing content, and strong-armed ransomware victims into paying.
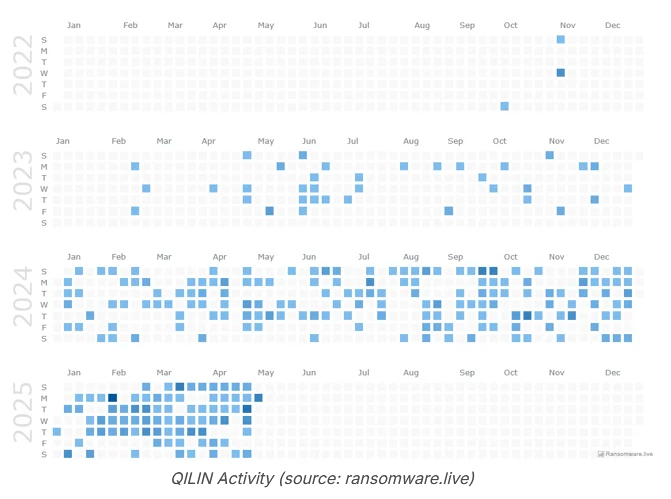
Qilin rises to the top: The Qilin ransomware has become one of the biggest RaaS platforms today. Attacks with the Qilin ransomware strain are at an all-time high, with increased activity after February this year. Security firm Cybereason says the group has seen an influx of new members after rival platforms got hacked earlier this year and affiliates went looking for a new stable service.
Malware technical reports
Meowstorio: Threat intelligence analyst g0njxa has published an analysis of the Meowstorio traffic distribution system.
LightPerlGirl: Todyl has published a report on LightPerlGirl, a new PowerShell-based Windows trojan.
Docker crypto-miner: Trend Micro has published a technical analysis of a cryptominer being deployed from Tor to misconfigured Docker instances.
GodFather banking trojan: Zimperium has spotted a new Android banking trojan that uses virtual machines to steal logins and funds from mobile users. The new GodFather malware installs app virtualization tools on infected devices. When users start a legitimate app, the malware replaces it with a version running in its own container, where it intercepts credentials and steals funds. The GodFather malware has been active in the wild since November last year and can target banking, crypto, and social media apps.
Sponsor section
APTs, cyber-espionage, and info-ops
Balkanization of APT names: Oleg Shakirov looks at how countries and security firms are aligning APT naming schemes within their own national spheres and interests. Honestly, this has been going on for over a decade but is now more pronounced than ever due to the political tensions and ongoing wars.
Argentina arrests Russian disinfo group: Argentina's intelligence service has detained a group of Russian spies conducting disinformation campaigns against the country's government. The group called itself "The Company" and had ties to Project Lakhta and the old Yevgeniy Prigozhin Internet Research Agency cluster. The Company allegedly disseminated Russian propaganda online and was working to recruit local citizens and NGOs. [Additional coverage in La Derecha Diario, The Moscow Times]
SHOE RACK and UMBRELLA STAND: The UK NCSC has published reports on two new pieces of malware found on hacked Fortinet devices. The first is SHOE RACK [PDF], a post-exploitation tool for remote shell access and TCP tunneling through a victim device. The second is UMBRELLA STAND [PDF], a remote shell targeting Fortinet devices. Both were deployed on systems also infected with COATHANGER [PDF], a malware strain linked to Chinese state hackers.
Famous Chollima's PylangGhost: Cisco Talso looks at PylangGhost, a new RAT used by North Korean APT group Famous Chollima in recent campaigns. The RAT is a Python clone of a similar RAT named GolangGhost and was used in attacks targeting the crypto and its adjacent industries. Most of the victims were from India.
BlueNoroff Zoom attack: Huntress has posted an IR report from a BlueNoroff APT intrusion where the group tricked an employee at a crypto firm into downloading a malicious Zoom extension.
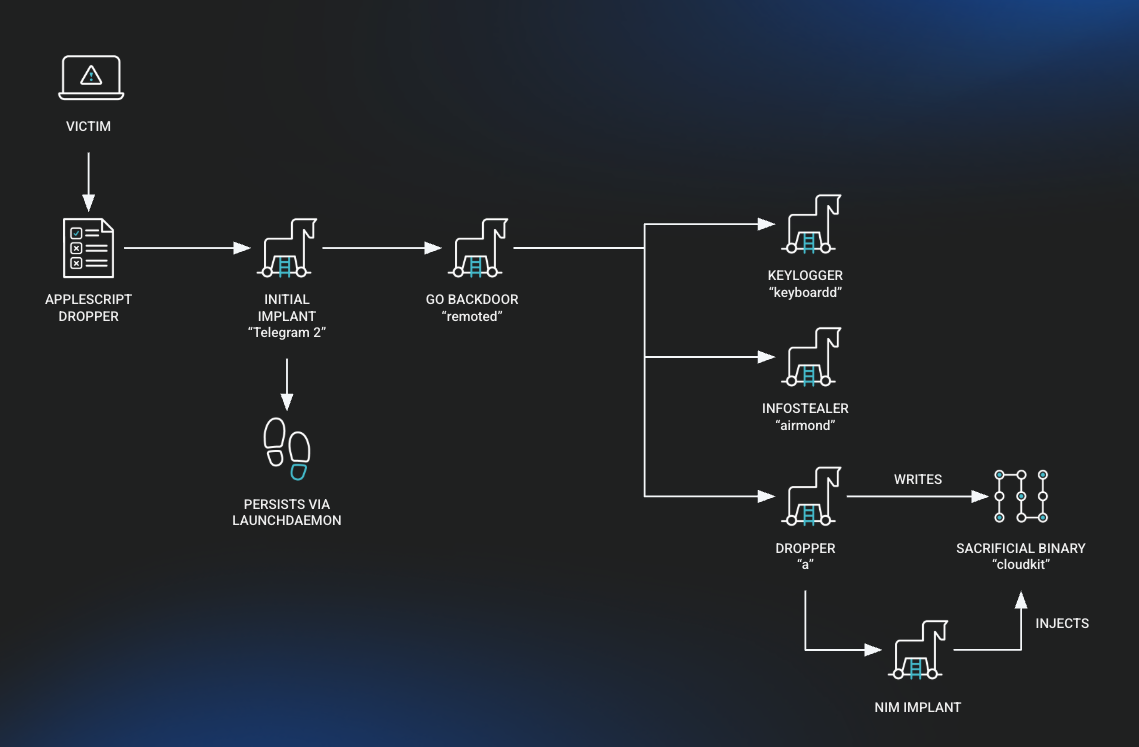
North Koreans reportedly host fake Zoom meeting featuring multiple deepfake colleagues. Target’s microphone doesn’t work so the colleagues talk them through installing malicious fix. www.huntress.com/blog/inside-...
— John Hultquist (@hultquist.bsky.social) 2025-06-19T10:41:53.852Z
Vulnerabilities, security research, and bug bounty
BeyondTrust RCEs: Software company BeyondTrust has released a security update to patch a remote code execution bug in its remote desktop applications. The bug (CVE-2025-5309) was discovered by security firm Resilion and impacts the BeyondTrust Remote Support and Privileged Remote Access products. It allows remote attackers to inject malicious code into the BeyondTrust template engine and take over unpatched servers.
Linux LPEs: Qualys has found two local privilege escalation (LPE) flaws in Linux, including one that grants root access.
Citrix NetScaler update: Citrix has released a security update for its NetScaler product line to patch three vulnerabilities.
Another dumb Erlang/OTP bug: Jonatan Männchen has found a bug in the Erlang/OTP standard-library ZIP routines that allows for absolute-path traversal attacks—allowing attackers to overwrite or create any path they want.
Patchless AMSI Bypass Attacks: CrowdStrike researchers have an overview of an offensive technique known as patchless AMSI bypass, its recent abuse, and ways to detect it.
Cisco security updates: Cisco has released two security advisories for various products.
KEV update: CISA has updated its KEV database (twice) with three vulnerabilities that are currently exploited in the wild. This includes a Linux kernel bug from 2023, a TP-Link 2023 command injection, and an Apple iMessage zero-day patched this month.
Infosec industry
Threat/trend reports: Cisco Talos, the Foundation for Defense of Democracies, EAST [PDF], Gartner, Ireland's DPC, and Tenable have recently published reports and summaries covering various infosec trends and industry threats. From the Gartner report:
"By 2027, 50% of business decisions will be augmented or automated by AI agents for decision intelligence. [...] By 2027, organizations that emphasize AI literacy for executives will achieve 20% higher financial performance compared with those that do not. [...] By 2029, 10% of global boards will use AI guidance to challenge executive decisions that are material to their business."
Acquisition news: Romanian security firm Bitdefender has acquired Irish email security firm Mesh.
New tool—MemLoader: Security researcher ntDallas has released MemLoader, a proof-of-concept framework for running native PE executables or .NET assemblies entirely from memory.
Risky Business podcasts
In this edition of Seriously Risky Business, Tom Uren and Patrick Gray talk about a Minnesota man who used people-search services to locate, stalk, and eventually murder political targets. They also discuss the purported hacktivist group Predatory Sparrow weighing in on the Iran-Israel conflict.
In this edition of Between Two Nerds, Tom Uren and The Grugq take a look at a new AI-powered covert influence campaign and compare it to World War 2 efforts.

