Risky Bulletin Newsletter
October 31, 2025
Risky Bulletin: Russia arrests Meduza Stealer group
Written by

News Editor
This newsletter is brought to you by Knocknoc. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
Russian authorities have arrested three individuals believed to have created and sold the Meduza infostealer.
The suspects were arrested this week in the Moscow metropolitan area, according to Russia's Interior Ministry. A video from the raids is available on the Ministry's media portal.
The Ministry's spokesperson, Irina Volk, said the malware was used in attacks against at least one government network in the Astrakhan region.
If found guilty, they can face prison sentences of up to five years.
This is no surprise since the group appears to have failed to implement a "don't s**t where you eat" policy when they rented access to their infostealer via their Telegram channel.
A report from Russian security firm BI.ZONE published last September, found that Meduza was used in multiple attacks targeting Russian organizations last year.
Prior to its arrest, Meduza was a mid-tier infostealer. It had advanced data collection and theft capabilities, but was never widely adopted by more than a handful of customers.
It launched in June 2023 and was advertised on underground hacking forums and rented through a Malware-as-a-Service model, via a dedicated Telegram channel.
According to reports, that channel disappeared in April, suggesting the group suspected something was happening and prompting its existing customers to suspect an exit scam.



Risky Business Podcasts
The main Risky Business podcast is now on YouTube with video versions of our recent episodes. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
Merkle breach: Data broker Merkle has suffered a security breach, according to a brief announcement from its parent company, Dentsu.
Ribbon breach: A state-sponsored hacking group has breached Ribbon Communications, a major US telecommunications services company. The intrusion occurred in December of last year but was discovered only last month. Ribbon provides voice and data transfer services between different platforms and providers. According to Reuters, the hackers managed to move downstream to at least three of Ribbon's customers.
ICS hacks in Canada: Hacktivist groups have breached three ICS networks across Canada over the past weeks. Attackers changed the water pressure at a water facility and modified a tank gauge, triggering a false security alarm at an oil and gas company. They also changed temperature and humidity levels at a farm's grain drying silos. All the hacked systems were exposed on the internet. Canada's cybersecurity agency has urged organizations this week to review ICS systems and make sure they use strong authentication.
US hacked Venezuela's intel service: The CIA hacked and disabled the computer network of Venezuela's intelligence service in 2020. US CyberCommand also carried out a cyberattack during that cutoff satellite communications for Russian Wagner troops stationed in Venezuela around the same time. Sources told CNN that the cyberattacks were ways to placate President Trump in his first term, when he pushed for military actions against the Maduro regime.
General tech and privacy
Firefox goes SafeBrowsing v5: Firefox will support the SafeBrowsing v5 security protocol to detect phishing and malware on the web. It's currently under testing in nightly releases.
Tor gets locked tabs: The Tor Browser on Android can now lock a user's tabs when they switch away from the browser to other apps. The new feature works if the device has a screen lock enabled. Users will be prompted to unlock the tabs using their normal screen lock challenge.
Czech police forced to turn off facial recognition: Czech authorities have been forced to turn off facial recognition cameras at the Prague airport after the system was found to be in violation of privacy laws. The most abhorrent part is that the Czech data protection agency took four years to inspect the system after an initial complaint.
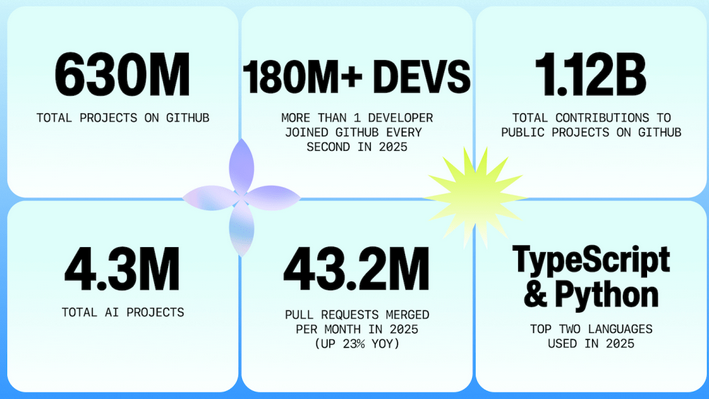
GitHub total users: GitHub said in its yearly report that it now has more than 180 million users, hosts more than 630 million projects, and that TypeScript has now become to top programming language on the platform, dethroning Python.
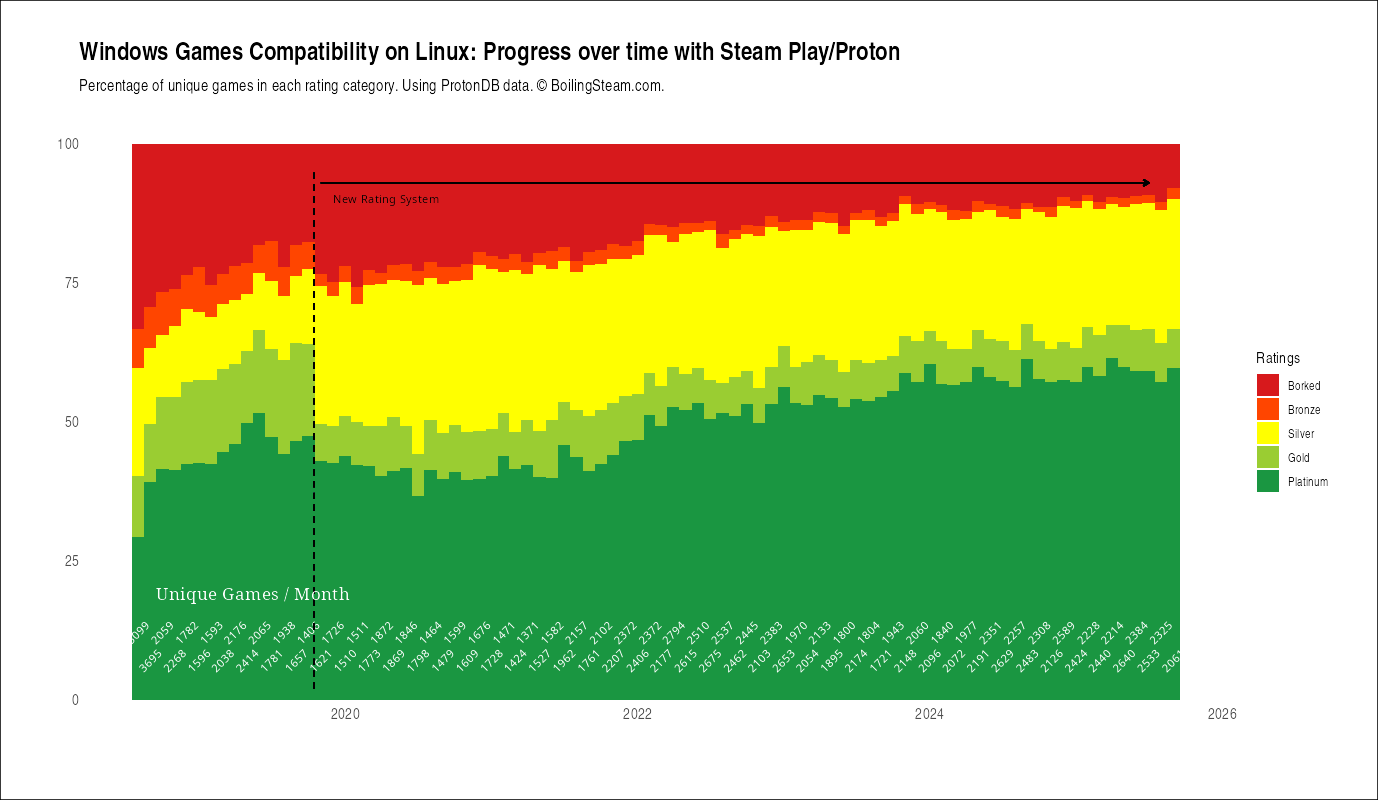
Linux gaming update: Close to 90% of Windows Steam games can now run on Linux.
WhatsApp adds passkey backups: Meta will allow users to encrypt WhatsApp backups using a passkey. The 200 people who use that site are gonna be ecstatic!
Disappearing posts on Threads: Meta is adding support for disappearing posts on its Threads social media network.
Simpler update titles: Microsoft has updated the titles of its security updates to provide clearer information on what users are installing.
Administrator Protection goes live: The Administrator Protection security feature is now live in Windows 11. The feature will require admins to enter a password, PIN, or other form of authentication if they want to perform highly sensitive actions. It's designed to prevent threat actors from abusing compromised admin accounts by requiring extra authentication steps. This feature is turned off by default. [Additional coverage in BleepingComputer]
Government, politics, and policy
New NSA favorites emerge: The White House is looking at two officials to head the US Cyber Command and the US National Security Agency. According to The Record, Army Lt. Gen. Paul Stanton and Air Force Lt. Gen. Thomas Hensley have emerged as favorites. Gen. Stanton is the current leader of US Cyber Command's network defense arm. Gen. Hensley is the head of the Air Force's information warfare command. The Cyber Command and NSA dual-hat role has been vacant since President Trump fired Air Force Gen. Timothy Haugh in April. The nomination of Army Lt. Gen. William Hartman for the role lost support over the past months, and a new search was started.
US TP-Link ban getting closer: More than half a dozen US federal agencies have shown their support for banning the sale of TP-Link products in the US. The Commerce Department claims TP-Link products are a national security risk. The Department started an investigation into the company's products and practices earlier this year. TP-Link, a Chinese company with close ties to the CCP, called the potential ban "nonsensical." [Additional coverage in WaPo]
FCC blocks additional Chinese gear: The FCC has voted to block approvals of new devices for the US retail market that contain parts from sanctioned Chinese companies. The agency will also look into revoking authorizations for previously approved devices. Chinese companies on the FCC's so-called Covered List include Huawei, ZTE, China Mobile, and China Telecom. Earlier this month, the FCC warned US retailers to remove devices from these companies from their stores. [Additional coverage in Reuters/FCC decision PDF]
FCC to vote down new cybersecurity rules: The FCC will vote next month to eliminate new cybersecurity requirements for US telcos. The agency says the telcos have strengthened their cybersecurity defenses on their own, and there is no need for the new requirements. The new rules were passed by the previous FCC panel days before the Biden administration left office, following a string of hacks at several US telco operators.
CBP device searches: The US Customs and Border Patrol conducted more border device searches than ever over the past year. [Additional coverage in WIRED]
"Newly published CBP figures show that for the full fiscal year of 2025—running from October 2024 to the end of September 2025—border agents conducted around 55,424 searches of electronic devices. This is up from around the 47,000 searches that were completed during the government's 2024 fiscal year."
Exchange hardening guide: Cybersecurity agencies from Australia, Canada, and the US have published a joint guide [PDF] on securing Microsoft Exchange servers.
Israel's "winking system": The Israeli government created a secret system with Amazon and Google to get notifications when the cloud providers shared Israeli data with foreign courts and law enforcement. The system used payments sent to the Israeli government, where the sum started with the telephone dialing code of the country that requested data. Amazon and Google were required to accept the secret "winking mechanism" in order to receive Israeli government contracts. [Additional coverage in The Guardian]
Denmark formally withdraws Chat Control: The Danish government, which is currently holding the European Council's rotating presidency, has formally withdrawn its Chat Control legislation. The proposal failed to garner majority support among EU bloc members and was never submitted for a vote. [Additional coverage in Euractiv]
Sponsor section
In this Risky Business sponsor interview, Patrick Gray chats with Knocknoc CEO Adam Pointon about why true Zero Trust architectures never really got there. Spinning up ZTNA access to core applications and slapping SSO prompts on everything else is great, but if we're honest, it's not really Zero Trust. So, how and why did we get here?
Arrests, cybercrime, and threat intel
L3Harris manager pleads guilty to exploit thefts: A former manager at a US defense contractor has pleaded guilty to selling exploits to a Russian zero-day broker. Peter Williams, a 39-year-old Australian, worked as a general manager for American company L3Harris Trenchant. He allegedly made $1.3 million from eight exploits sold to Russian company, Operation Zero. According to his plea deal, he could be sentenced for up to nine years. [Additional coverage in Seriously Risky Biz]
Btw if you're wondering what Williams spent his $1.3m on, turns out the answer is lots of watches, a Louis Vuitton handbag, a lot of very expensive jewelry from Tiffanies, and some things from Mocler. And when I say lots of watches, I mean *lots* of watches. Guy really liked watches.
— Pwnallthethings (@pwnallthethings.bsky.social) 2025-10-30T00:21:19.773Z
Memento CEO confirms Kaspersky report: The CEO of Italian spyware company Memento Labs has confirmed that Kaspersky caught the company's spyware. Paolo Lezzi told TechCrunch the spyware was deployed by a government customer. Lezzi says the customer used an older version of the Dante spyware that Memento plans to deprecate by the end of the year. Kaspersky and other Russian security firms found the spyware in attacks against Russian and Belarusian targets.
Poland detains investment scammers: Polish authorities have arrested 11 suspects who ran an investment scam scheme. The group used call centers located abroad to trick Polish citizens into investing their money in fake investment websites. The gang allegedly made more than $20 million from at least 1,500 victims.
AFP cracks crypto-wallet: Australian police have cracked a criminal's crypto-wallet and recovered $6 million worth of crypto. The wallet stored crypto payments from renting the Ghost encrypted comms app to other criminals around the world. Officers found an encoded version of the wallet password stored as blocks of random text inside a password-protected note on his phone. AFP's tech team cracked the wallet after they realized the suspect added numbers manually to the start of some sequences.
Malicious VS Code extensions: HelixGuard researchers have found 12 malicious VS Code extensions on the official store. Four of the extensions are still up, according to the company.
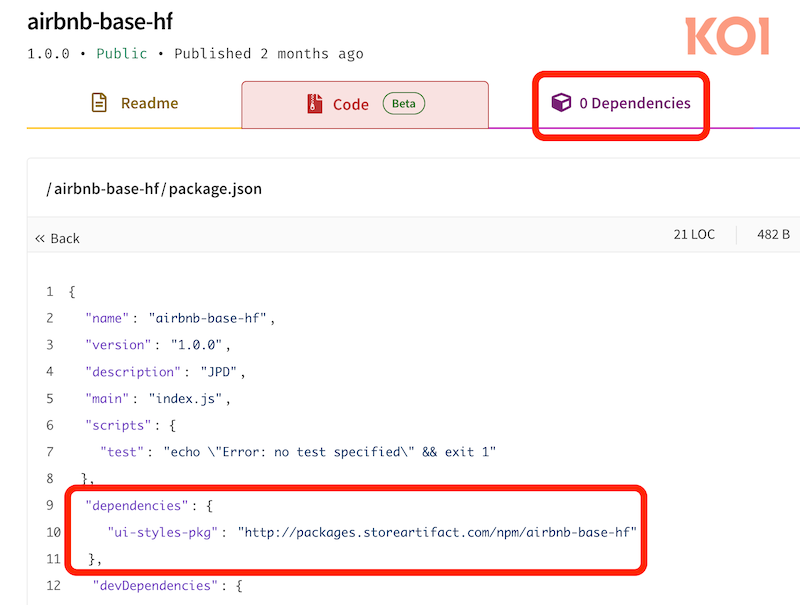
npm malware distributed via invisible dependencies: A cluster of 126 malicious npm packages infected their users with malware using invisible dependencies. The technique relied on using malicious dependencies hosted on custom domains instead of the main npm repo. These libraries are not shown in dependency counters and are not scanned by most npm security tools. According to Koi Security, the malicious packages dropped malware that stole authentication tokens, CI/CD secrets, and GitHub credentials.
Aisuru gets proxy features: The Aisuru DDoS botnet has added the ability to turn infected devices into proxy nodes, probably as a new monetization option. [Additional coverage in KrebsOnSecurity]
Hezi Rash hacktivist group: Check Point has published a profile on Hezi Rash, a pro-Kurdish hacktivist group behind some recent DDoS campaigns.
Tangerine Turkey does cryptomining: Cybereason has published a profile and technical dive of the operations of Tangerine Turkey, a group involved in cryptomining operations targeting Windows devices.
LinkedIn phishing campaign: Push Security has spotted a sophisticated phishing campaign targeting LinkedIn users.
AdaptixC2 abuse: SilentPush has linked some of the recent abuse of the AdaptixC2 red-team framework to Russian cybercrime crews.
macOS infostealer scene: Threat intel firm KELA has published a report looking at how the macOS infostealer scene has evolved from 2-3 threats to a sprawling ecosystem with tens of commercial MaaS platforms renting access to highly professional and efficient stealers.
NFC relay apps explode: Zimperium has discovered more than 760 Android apps that steal and relay NFC data to a remote attacker. The stolen NFC data is used to withdraw funds from a user's accounts or make purchases in their name. The apps are part of a growing trend in the Chinese and Russian fraud markets.
GFW analysis: The DomainTools security team has taken a look at more than 500GB of data that was leaked from Chinese companies managing China's national firewall system, aka the Great Firewall.
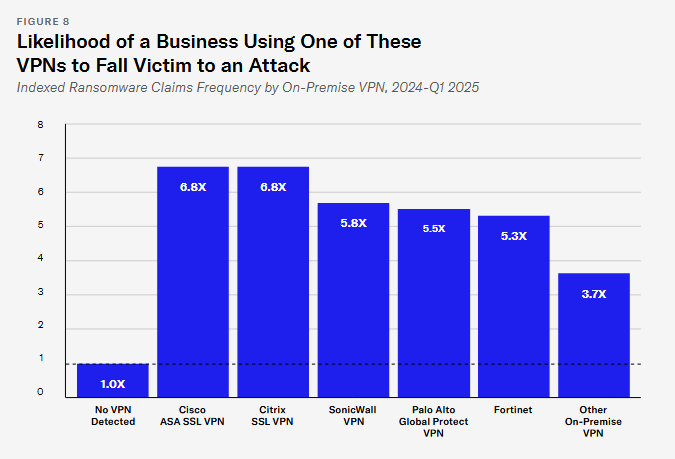
VPNs are a major ransomware entry point: Remote access devices like VPNs were the primary entry point for ransomware attacks last year. Cyber insurance provider At-Bay says four in five ransomware attacks were traced to remote access devices, and four in five of those originated via VPN servers. The insurer has recorded a gradual shift away from RDP to VPN as the main entry point over the past five years. Companies running Cisco and Citrix VPNs face a higher risk and are more likely to fall victim to an attack, according to the company.
Malware technical reports
Warlock ransomware: Malware analyst Vlad Pasca has published an analysis of Warlock, the ransomware allegedly deployed by a state-sponsored group via the recent ToolSheel exploit.
Global ransomware: Intrinsec has published a 49-page report on Global, a new ransomware group that launched in June. The company believes the group is a rebrand of older operations such as Mamona, Black Lock, and Eldorado.
DeliveryRAT: Russian security firm F6 has discovered DeliveryRAT, a new Android remote access trojan that was seen in the wild in the second half of the year.
BankBot-YNRK: CyFirma has a report on a new Android banking trojan they're tracking as BankBot-YNRK.
"The analyzed samples, collectively identified as Android/BankBot-YNRK, represent a highly capable Android banking trojan designed to achieve full remote control of infected devices. [...] Its ability to masquerade as legitimate applications (e.g., Google News) further enhances user deception and trust. Communication with the C2 server enables it to receive a wide range of commands for data exfiltration, device manipulation, and cryptocurrency theft. Overall, Android/BankBot-YNRK exhibits a comprehensive feature set aimed at maintaining long-term access, stealing financial data, and executing fraudulent transactions on compromised Android devices."
Kinsing (H2Miner): AhnLab says the Kinsing (H2Miner) cryptomining botnet is now targeting ActiveMQ serves.
PolarEdge's RPX_Client: The PolarEdge botnet has a new reverse proxy component named RPX_Client. The component is already on more than 25,000 systems.
New malware loader: IIJ-SECT has spotted a new, still unnamed malware loader that was used to deploy stuff like TorNet and PureVNC.
PureHVNC: And speaking of the devil, IBM's X-Force has published a report on one of these PureVNC payloads, this one used in campaigns targeting Brazil.
Minecraft RAT: ReversingLabs analyzes Minecraft RAT, a new RAT sold by a threat actor going by the name of STD Group. An older name for this is UwUdisRAT, while newer ones are also called Propionanilide RAT.
Lampion updates: Bitsight looks at recent changes in the Lampion banking trojan, which made a comeback earlier this year via ClickFix campaigns.
Sponsor section
In this sponsored product demo, Knocknoc CEO Adam Pointon walks Patrick Gray through the Knocknoc secure access platform. Knocknoc is a platform that restricts network and service availability to authenticated users via existing network security equipment. Users don't need to install an agent. It also has an identity-aware proxy component that supports web applications and RDP.
APTs, cyber-espionage, and info-ops
Airstalk malware linked to APT group: Palo Alto Networks has discovered a new malware strain named Airstalk that the company believes was created by a state-sponsored APT group and deployed via a still-uncovered supply chain attack.
Cloud Atlas targets Russia, again: After earlier this year, Positive Technologies caught the Cloud Atlas APT target Russia's military-industrial complex, security firm F6 says the group has expanded its focus towards the country's agro-industrial sector as well.
New Sandworm ops: Carbon Black and Symantec have found new Sandworm attacks targeting Ukraine. The goal was espionage and data collection. No destructive attack, this time.
Bronze Butler (Tick) behind Lanscope zero-day: A Chinese cyber-espionage group is behind a recent zero-day in the Motex Lanscope Endpoint Manager. The attacks began in mid-2025. Security firm Sophos linked the attacks to a group known as Bronze Butler. The group is also known as Tick and has a long history of targeting Japan and South Korea.
Salt Typhoon: Rapid7 has published a report on the Salt Typhoon Chinese cyber-espionage group.
UNC6384: A suspected Chinese APT group (UNC6384) has hacked Belgian and Hungarian diplomatic entities using a Windows shortcut vulnerability disclosed back in March.
But I thought Microsoft said it wasn't worth fixing? "Microsoft classified this as low severity and this will not be patched in the immediate future." arcticwolf.com/resources/bl...
— The Dustin Childs (@dustinchilds.bsky.social) 2025-10-30T19:42:28.163Z
Vulnerabilities, security research, and bug bounty
Tata Motors exposed servers: Indian car maker Tata Motors has fixed several vulnerabilities that were exposing its server infrastructure and user data on the internet, according to security researcher Eaton Zveare.
- 2 exposed AWS keys on public-facing websites revealed 70+ TB of sensitive information and infrastructure across hundreds of buckets.
- Pointless AWS key encryption easily defeated.
- Tableau backdoor made it possible to log in as anyone without a password, including the server admin. This exposed countless internal projects, financial reports, and dealer dashboards.
- Exposed Azuga API key compromised test drive fleet management system.
Two-face Rust binaries: Synacktiv researchers have published details on a technique that can be used to generate Rust binaries that are clean on most systems but can run malicious code on specific hosts.
KEV update: CISA has updated its KEV database with two vulnerabilities that are currently exploited in the wild. This includes bugs in XWiki and VMWare Aria Operations.
Jenkins security updates: The Jenkins project has published 13 security updates for various plugins.
OpenVPN security update: The OpenVPN security team has released a patch to fix a command injection bug on its POSIX (BSD, Linux, MacOS) clients.
LUKS2 vulnerabilities: Two vulnerabilities allow threat actors to break the LUKS2 encryption in eight confidential computing projects. The vulnerabilities allow attackers to trick a trusted execution environment into encrypting data with a null cipher. Attackers can then extract or modify data inside secure environments.
Vulnerability in WP security plugin: An EoP vulnerability was discovered in a WordPress security plugin named "Anti-Malware Security and Brute-Force Firewall," installed on more than 100,000 sites.
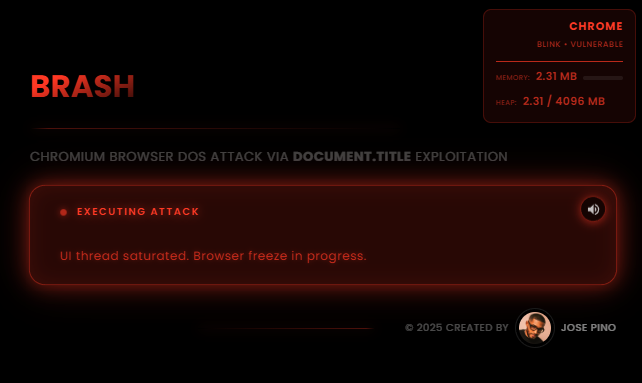
Brash attack: Security researcher Jose Pino has found a Blink engine bug that can crash Chromium-based browsers after roughly 15-60 seconds on a page. The bug is named Brash, and a demo page is here (Careful! This may crash your browser, obviously!!!).
Infosec industry
Threat/trend reports: At-Bay, Barracuda, Firefox, KELA, and Positive Technologies have recently published reports and summaries covering various threats and infosec industry trends.
New tool—UnderlayCopy: Security researcher Kazem Fallahi has open-sourced UnderlayCopy, a PowerShell toolkit to extract locked Windows files and artifacts using MFT parsing and raw disk reads.
OpenSSL Conference presentations: Presentations from the OpenSSL Conference, which took place earlier this month, are available on the conference's website.
Acquisition news: Francisco Partners has acquired Apple product security firm Jamf and will take the company private. Jamf stockholders will receive $13.05 per share in cash.
Risky Business podcasts
In this edition of Seriously Risky Business, Tom Uren and Amberleigh Jack talk about Peter Williams, the general manager of vulnerability research firm Trenchant, who has pleaded guilty to selling exploits to the Russian zero-day broker Operation Zero. It's a terrible look, but it doesn't mean the private sector can't be trusted to develop exploits.
In this edition of Between Two Nerds, Tom Uren and The Grugq dissect a recent Chinese CERT report that the NSA had hacked China's national time-keeping service.
