Risky Bulletin Newsletter
February 20, 2026
Risky Bulletin: RPKI infrastructure sits on shaky ground
Written by

News Editor
This newsletter is brought to you by runZero, the Total Attack Surface & Exposure Management platform. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
The infrastructure that supports the Resource Public Key Infrastructure (RPKI) security standard is not as secure as one would believe and is prone to multiple attacks that could hinder or crash global internet routing.
A new research paper that will be presented next week at the Network and Distributed System Security (NDSS) Symposium looks at a type of server that is part of the RPKI infrastructure known as PP, standing for Publishing Point, and how attacking these servers can prevent routers from validating routing information.
The topic of internet routing and its security protocols is a complex one, so here are the main acronyms and terms that we'll be using and what they mean:
- BPG—stands for Border Gateway Protocol and refers to an internet routing protocol through which routers talk to each other and exchange information about where IP addresses blocks are located across the globe and where they should be sending traffic.
- AS—stands for Autonomous System and refers to a company or organization that owns IP addresses and engages in routing internet traffic or hosting content.
- BGP announcement—refers to messages sent by ASes (and their routers) to other ASes (and their routers) about what IP address blocks they are hosting, inviting others to send data to them.
- RPKI—stands for Resource Public Key Infrastructure and refers to a collection of standards and protocols to secure internet routing.
- ROA—stands for Route Origin Authorization and is a mechanism through which an AS announces and cryptographically attests that it owns and hosts a specific IP address block.
- ROV—stands for Route Origin Validation and refers to the process where an AS/router takes an incoming BGP announcement and verifies the routing information against a list of known ROAs.
- PP—stands for Publishing Point and they are central servers where all the cryptographically-signed ROAs are stored.
- RP—stands for Relying Party and is software that runs on an AS' infrastructure that downloads ROA lists from PP servers, lists that are later used by the ROV mechanism to verify that routing information from a BGP announcement matches the ROA entry.
What the research team looked at was the interaction between RPs and PPs, which is not as simple as running a curl command and downloading a list of signed ROA entries from the PPs. These are multi-step operations that have their own quirks and expose the entire routing validation process to bugs and errors.
"Specifically speaking, the process involves two key sub-processes. The first sub-process is that the RP resolves the domain name of each individual PP through the DNS infrastructure to obtain the PP's IP address. This resolution sub-process involves iterative interactions with authoritative name servers across varying levels of the DNS hierarchy. The second sub-process involves the RP establishing communication with the PP via its IP address to retrieve ROAs using either RRDP or rsync, which we refer to as the download sub-process. To ensure data integrity during the resolution sub-process all involved entities must adopt DNSSEC, which provides cryptographic validation of DNS responses. In contrast, the download sub-process ensures data integrity through RPKI's built-in security mechanisms. Notably, the download sub-process benefits from strong cryptographic protections inherent in RPKI, whereas the resolution sub-process remains vulnerable due to partial DNSSEC deployment on the Internet. To ensure end-to-end connectivity, routing security for all data flows within both sub-processes must be meticulously upheld."
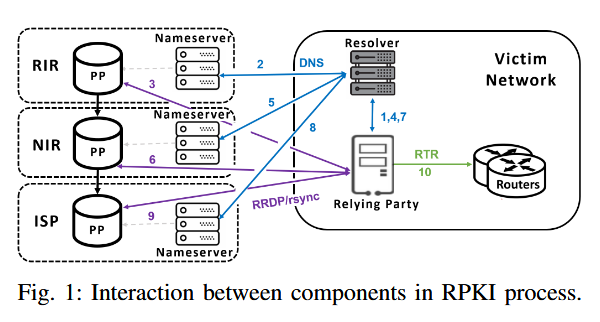
The study created an inventory of all PP servers and tried several attacks to hijack parts of this infrastructure. The results were pretty bad.
From the 64 total PP servers discovered, 31 were vulnerable to DNS spoofing attacks because the PP domain names did not use DNSSEC, a protocol that lets domain owners cryptographically sign their DNS records for authenticity.
Fifty-five PP servers also relied on DNS servers that lacked ROA coverage, meaning you could use a BGP hijack to take over the servers meant to protect against BGP hijacks.
Four of the PP servers themselves were on networks that didn't use ROAs, leading to the same attack scenario.
Researchers also evaluated the practicality of an attack against PP servers. Results showed that attacking the most vulnerable PP server would impact ROV operations of up to 65% to 83% of all ASes due to dependencies among PPs that would trigger cascading failures in the entire PP ecosystem.
The research team, all from the Tsinghua and Fudan universities in China, offered some recommendations for strengthening the RPKI/PP ecosystem. Some of the most important included rolling out DNSSEC for the PP domain names, covering the PP and their DNS servers with ROA protections, and avoiding hosting PP servers on CDNs.
Risky Business Podcasts
The main Risky Business podcast is now on YouTube with video versions of our recent episodes. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
Angolan journalist hacked with Predator spyware: The Predator spyware was used to hack the personal phone of a prominent Angolan journalist and activist. According to an Amnesty International investigation, Teixeira Cândido's phone was infected in mid-2024 after he received and clicked on a malicious link on WhatsApp. The spyware was removed after Cândido restarted the phone. Predator maker Intellexa says it only sells the spyware to government clients.
YouX hack: The personal information of more than 440,000 Australians was exposed after a breach at Sydney finance tech company youX. The breach took place last week. Hackers are now selling the data on underground forums. The stolen data includes the personal details of loan applicants, including ID scans. [News.com.au]
Ravenna Hub leak: School application platform Ravenna Hub has fixed an IDOR vulnerability that exposed applicants' personal data. [TechCrunch]
Figure breach: The ShinyHunters group leaked the personal details of 967,000 customers of blockchain company Figure after the group failed to extract a ransom from the company—as is their usual modus operandi.
Ransomware hits US tribal systems: A ransomware attack has disrupted the IT systems of the Cheyenne and Arapaho Tribes of Oklahoma. The incident took place last December and took down access to the tribal government's IT, phone, and email systems. The incident primarily impacted its higher education program, delaying the processing of spring scholarships. Officials have now restored access to 80% of affected systems. The Rhysida group took credit for the attack. [DisruptionHub] [h/t DataBreaches.net]
UMMC closes clinics: The University of Mississippi Medical Center has closed all clinics and canceled patient care following a cyberattack. All surgeries and appointments will be rescheduled for later dates. The hospital chain says it lost access to all IT systems, including its Epic electronic medical records system. UMMC operates 35 clinics and employs more than 10,000 staff. [WLBT]
Moldovan government leak: There appears to be some drama about a leak of user data from Moldovan's government portals. The government denies it and the hackers' claims don't line up with facts. [DataBreaches.net]
Breach at the French Ministry of Economy: Hackers have compromised an official at the French Ministry of Economy and accessed a database of French bank accounts. The database stored information on more than 1.2 million accounts. It contained names, account numbers, and home addresses. The government will notify all affected owners. [Le Monde]
Deutsche Bahn DDoS attacks: A coordinated DDoS attack is disrupting the ticket and real-time information systems of Germany's national rail operator. Deutsche Bahn describes the attack as taking place in waves and of considerable scale. No group has yet taken credit for the attacks. It also took place on the day the company laid off 6,000 of its 14,000 employees from its freight cargo division. [DW]
Copilot bug exposed confidential emails: A Copilot bug uploaded private confidential emails to Microsoft servers for summarization. [Office365ITPros]
Mysterious SSN DB leak: Upguard has found a mysterious database exposed on the internet with 2.7 billion records containing Social Security numbers and 3 billion username-credential pairs.
Cline supply chain attack: A threat actor has hijacked the GitHub repository of the Cline AI coding agent. The attacker used the GitHub repo to push a malicious update to Cline's npm library. The update didn't deploy malware but deployed a version of the OpenClaw AI agent on Cline customer systems. The attacker stole the project's GitHub publish token after reading a blog post by security researcher Adnan Khan. The vulnerability in Khan's blog had already been patched but the token remained in the GitHub Actions cache.
General tech and privacy
Apple gets into the surveillance business: Apple is allegedly working on a smart pendant, smart glasses, and new AI-based AirPods. All products will be equipped with a camera that will feed data into an AI system. It's unclear what the AI will be useful for except being creepy. [Bloomberg]
Firefox support ends for old Windows versions: Mozilla is ending support for Firefox on old Windows OS versions like 7, 8, and 8.1 at the end of this month.
Spain orders VPNs to block illegal content: A Spanish court has ordered ProtonVPN and NordVPN to block IP addresses linked to pirate sites streaming local soccer matches. [TorrentFreak]
TeamSpeak reaches maximum capacity: TeamSpeak says it has reached maximum server capacity after it saw a giant influx of new users following Discord's announcement that they will start verifying users' ages and demanding face scans or real IDs. [PCGamer]
Russia accidentally blocks Linux kernel site: As part of its internet crackdown, it appears that Russia's internet watchdog accidentally blocked the official website of the Linux kernel. The block has been lifted after Russian IT engineers reminded Roskomnadzor that all of the country's native OS distros run on Linux. [Durov Code]
K8s Ingress NGINX retirement: The Kubernetes project is retiring the Ingress NGINX controller in March this year after the project failed to attract maintainers for years. Kubernetes has warned administrators that continuing to use the controller will leave them exposed to attacks. Developers will need to migrate to a new NGINX controller, which will require them to recode their applications since there's no drop-in replacement.
"Unfortunately, the flexibility Ingress NGINX was designed with, that was once a boon, has become a burden that cannot be resolved. With the technical debt that has piled up, and fundamental design decisions that exacerbate security flaws, it is no longer reasonable or even possible to continue maintaining the tool even if resources did materialize."
Twitter/X algorithm manipulation: Here's another piece of academic research looking at how Twitter/X is boosting right-wing and conservative content.
X's algorithm is in fact doing what you think it's doing. www.nature.com/articles/s41...
— Jon Green (@jongreen.bsky.social) 2026-02-18T17:24:02.214Z
Government, politics, and policy
Russia turns on Telegram: FSB chief Alexander Bortnikov has accused Telegram of harboring criminal activity and failing to act on reports from Russian authorities. Bortnikov says Telegram ignored more than 150,000 requests for removal from Russian authorities. Russian officials also claimed that foreign intelligence services have read Telegram messages exchanged by soldiers on the front. Telegram called the statement a complete fabrication. Russia started blocking and throttling Telegram traffic last week. [TASS // Durov Code // Reuters]
UK wants tech platforms to take down revenge porn in 48h: Tech platforms will have to remove unconsensual nude content of UK users within 48 hours. The British government is updating its Crime and Policing Bill to accommodate the new requirement. Companies that fail to act on reports risk fines up to 10% of their worldwide revenue. Platforms that don't pay their fines can also be blocked in the UK.
Texas sues TP-Link: The US state of Texas has sued Chinese router maker TP-Link. Texas Attorney General Ken Paxton claims the company has granted access to American's data to the Chinese government and its intelligence services. He also claims the devices have been used by Chinese hackers to attack Americans. Paxton's office also sued Anzu Robotics for helping DJI sell its drone technology in the US and skirt a US ban.
West Virginia sues Apple: The West Virginia Attorney General has sued Apple for failing to detect child sexual abuse material on iCloud. Attorney General JB McCuskey claims Apple knew of the issues but failed to act. McCuskey says Apple reported only 267 CSAM cases on its platform while Google and Meta reported millions in the same period.
US cyber offense policy: Speaking at the CyberScoop CyberTalks event, ONCD principal deputy assistant national cyber director Alexandra Seymour said the US response in cyber space will depend on the adversary's actions and will happen after coordinating with the private sector. [NextGov]
US does dumb things, part 332737232: The US State Department plans to launch an online platform to let users in that mean place called the EU view content banned by their governments. That content includes terrorist propaganda that the US itself also bans, violent videos, Grok-generated CSAM and pr0n, and a bunch of pirating sites that EU countries banned at the pressure of US companies to begin with. [Reuters]
Finally a home for Grok-generated CSAM the EU doesn't want you to see
— Casey Newton (@caseynewton.bsky.social) 2026-02-18T23:40:13.807Z
If you’re reading Reuters coverage of “freedom dot gov” today & wondering about the U.S. commitment to free speech online this is the context. Trump has gutted funding for people in authoritarian countries to dodge censorship, instead we get this vague nonsense. www.theguardian.com/world/2026/f...
— ⸻realhackhistory.org (@bsky.realhackhistory.org) 2026-02-19T11:37:41.806Z
Sponsor section
In this Risky Business sponsor interview, Casey Ellis chats to Todd Beardsley, VP of Security at RunZero about Kevology, the company’s analysis of CISA’s KEV list. Kevology lets you easily identify and fix vulnerabilities from the list that are urgent and relevant to you.
Arrests, cybercrime, and threat intel
Spain arrests hotel hacker: Spanish police have detained a 20-year-old who hacked a hotel reservation platform to book rooms at luxury hotels for prices as low as one cent. The suspect allegedly manipulated the site's payment system to make rooms appear as paid. Police arrested him at a Madrid hotel on Wednesday where he caused damage of more than €20,000. [RFI]
Nigerian hacker sentenced to 8 years: A Nigerian hacker was sentenced to eight years in prison for hacking five Massachusetts tax preparation firms. Matthew A. Akande used stolen tax records to file fraudulent tax returns with the US IRS. He made almost $1.4 million before being arrested in Mexico in October of 2024.
Cybercrime arrests in Africa: Interpol and law enforcement agencies from 16 African countries have arrested 651 suspects involved in cybercrime activities. The suspects were part of groups linked to investment scams, mobile fraud, and fraudulent loan applications. Authorities also recovered $4.3 million in stolen assets.
GoldFactory campaigns hit Indonesia: Hackers have stolen up to $2 million from Indonesian users by posing as the country's tax platform. A large-scale phishing operation targeting Android users began in January this year, ahead of the country's tax season. Security firm Group-IB has linked the attacks to a group it tracks as the GoldFactory.
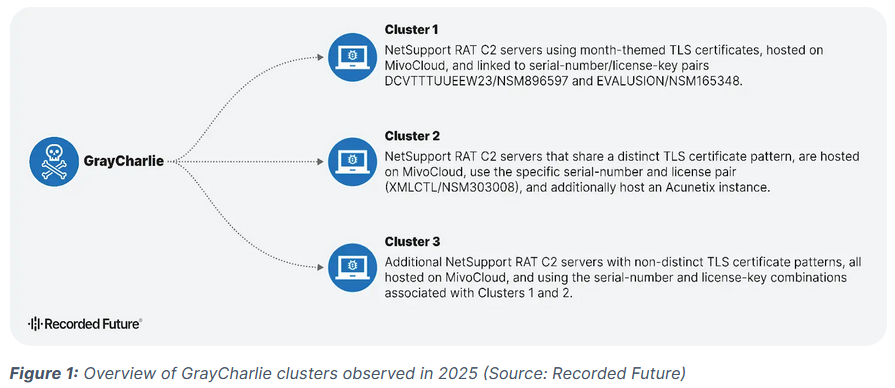
GrayCharlie profile: Recorded Future has published a profile of GrayCharlie, a financially motivated threat actor that hacks WordPress sites to redirect visitors to fake browser update pages, where it tries to infect users with various RATs.
Atlassian spam: Threat actors are abusing Atlassians' Jira Cloud infrastructure to abuse its trusted domain and relay spam campaigns.
AI platforms as C2s: New Check Point research looks at how threat actors could abuse AI platforms as a command-and-control system.
"This technique was demonstrated against platforms such as Grok and Microsoft Copilot, leveraging anonymous web access combined with browsing and summarization prompts."
AI-generated passwords suck: Research from Irregular found that passwords generated by LLMs are predictable and easy to guess, with the same passwords being generated for multiple users.
ClickFix was the entry point in 50% of cases: The ClickFix technique was the entry point for 53% of all malware infections spotted by Huntress Labs last year. The technique was spotted in 2024 and has since exploded in popularity. It relies on using fake errors to trick users into copy-pasting malicious commands on their Windows or macOS terminals.
ATM jackpotting attacks rise across the US: The FBI says that ATM jackpotting attacks have increased across the US. More than 700 attacks were recorded last year alone, accounting for $20 million in losses. Last year accounted for a third of all ATM jackpotting attacks reported since 2020. [FBI industry alert/PDF]
Google Play enforcement: Google says it banned more than 80,000 developer accounts from the Play Store for policy violations. The company also blocked more than 1.75 million apps from being published to the store. [Google Play yearly review]

Malware technical reports
Starkiller PhaaS: AbnormalAI researchers have discovered a new phishing kit named Starkiller. The kit is advertised online and includes support for templates, URL masking, MFA phishing, and cookie theft.
Arkanix Stealer: Kaspersky looks at Arkanix Stealer, a new infostealer launched in October that is being advertised on Discord.
AstarionRAT: Huntress Labs has spotted the new AstarionRAT being distributed via ClickFix campaigns in the wild.
"AstarionRAT is a new, full-featured RAT with 24 commands, including credential theft, SOCKS5 proxy, port scanning, reflective code loading, and shell execution, with RSA-encrypted C2 communication disguised as application telemetry."
Remcos updates: There's new versions of the Remcos RAT in the wild.
Noodlophile operator gets angry: The operator of the Noodlophile infostealer has padded the malware's file size with a Vietnamese phrase repeated million of times that reads "f*** you, Morphisec" after the security firm exposed their operation last year.
TrustConnect MaaS: Proofpoint has discovered a new Malware-as-a-Service operation trying to discover its remote access trojan (RAT) as a legitimate remote monitoring and management (RMM) tool named TrustConnect. The company linked the new MaaS to a former user of the Redline infostealer.
"Disruptions to MaaS operations like Redline, Lumma Stealer, and Rhadamanthys, have created new opportunities for malware creators to fill gaps in the cybercrime market. While these disruptions are effective and impose cost on adversaries, emerging malware shows threat actors will always be looking for new ways to compromise victims."
PromptSpy: ESET has discovered a new Android remote access trojan that abuses Google Gemini to remain active on infected devices. The new PromptSpy uses Gemini to analyze the user's screen and make sure its parent app remains pinned in the Recent Apps list. This prevents the Android OS from shutting down its process. The malware is distributed outside of the Play Store and was used in campaigns targeting Argentina.
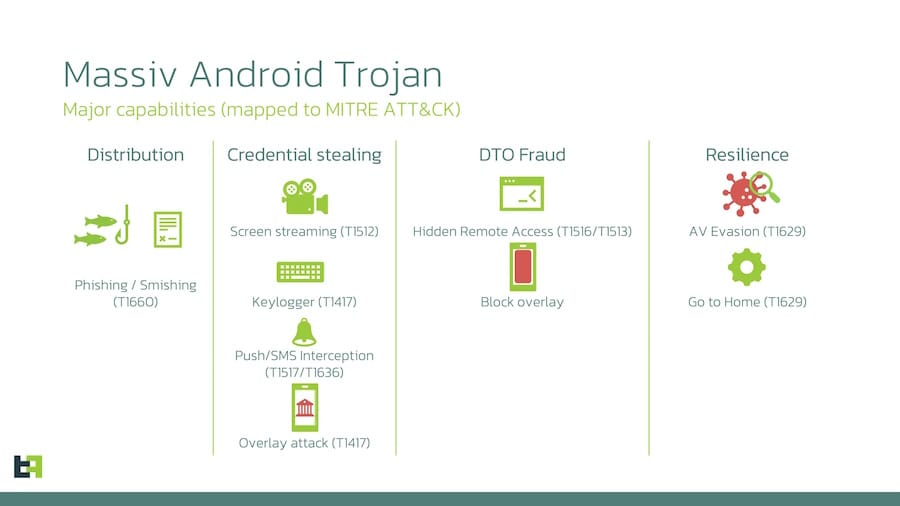
Massiv: ThreatFabric has discovered a new Android RAT distributed inside IPTV Android apps. Named Massiv, the malware is used to gain access to the device and steal funds from mobile banking apps.
Sponsor section
In this product demo Patrick Gray hosts Ali Cheikh while he shows off how you can use runZero to scan for and manage vulnerabilities in your environment.
APTs, cyber-espionage, and info-ops
PseudoSticky mimics Ukrainian APT: A mysterious threat actor is mimicking the tactics of a Ukrainian APT group to attack Russian organizations. Russian security firm F6 says despite the mimicry, there is no connection between the new PseudoSticky group and Ukraine's Sticky Werewolf APT. The group has been active since November and also employs LLMs as part of its arsenal.
NATO info-ops attribution framework: NATO's StratCom center has published a framework on how to attribute Russian disinformation and influence operations.
Pro-China influence operation: Graphika has linked a network of 43 domains posing as Western news outlets to Chinese public relations company Haixun. There's also a podcast on this.
Vulnerabilities, security research, and bug bounty
Invanti zero-days exploited since last summer: Two recent zero-days (CVE-2026-1281 and CVE-2026-1340) in the Ivanti EPMM platform have been exploited in the wild since at least the summer of 2025. Germany's cybersecurity agency has found evidence of compromise while investigating the attacks. The two zero-days have been linked to recent hacks of the Dutch data protection agency and the European Commission. Palo Alto Networks has some details on the attacks, which now includes both espionage and cybercrime activity.
KEV update: CISA has updated its KEV database (twice) with six vulnerabilities that are currently exploited in the wild. This includes a recent Chrome and Dell zero-day, but also a 2008 ActiveX bug that's now under attack [insert_shocked_face].
Jenkins security updates: The Jenkins project has published two security updates for the project's core files. These include an XSS and a build information disclosure.
Unpatched OpenID auth bypass: A vulnerability in an OpenID plugin for Tomcat allows threat actors to bypass authentication. According to security firm ERNW, the OpenID Connect Authenticator for Tomcat library treats JWT tokens with unknown signature algorithms as valid. The issue was discovered in September but remains unpatched after the library's developer could not be contacted for months.
AI recommendation poisoning: Microsoft has found a new attack named AI recommendation poisoning that can be used by attackers using malicious and coordinated prompts to alter the agent's future recommendations.
Bug leads to bad crypto debt: The Moonwell DeFi platform found itself with $1.78 million of bad debt after they misconfigured a smart contract priced cbETH tokens at $1 instead of $2,200. [Decrypt]
Major crypto bug impacts 723,000 projects: More than 723,000 open-source projects use cryptographic libraries with insecure defaults. The aes-js and pyaes libraries use the same key and IV when developers don't set their own. According to Trail of Bits, the issue has been known to the developers since 2022 but was never fixed.
Grandstream vulnerabilities: Grandstream has patched an unauth remote code execution bug in its GXP1600 VoIP phone. Security firm Rapid7 found the vulnerability and has a write-up on it.
PDF engine vulnerabilities: Novee says its researchers found three vulnerabilities in PDF engines, then they trained an AI agent and found 13 more bugs. The bugs impacted Apryse WebViewer (PDFTron) and the Foxit PDF.
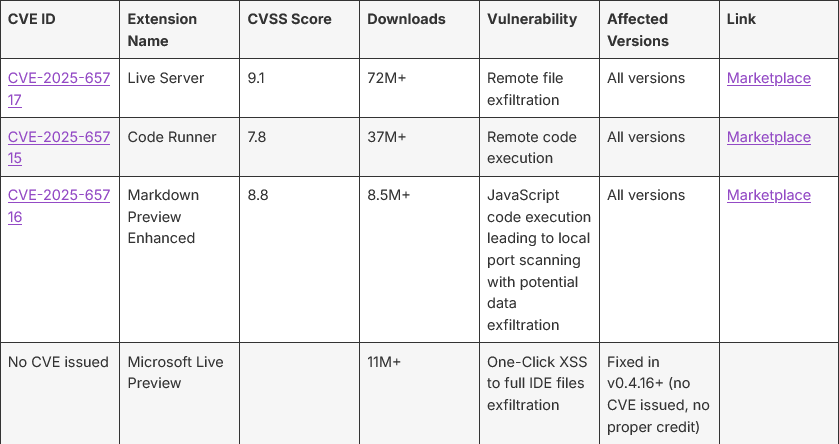
IDE vulnerabilities: OX Security has found vulnerabilities in four popular VS Code extensions that can be abused to steal user files.
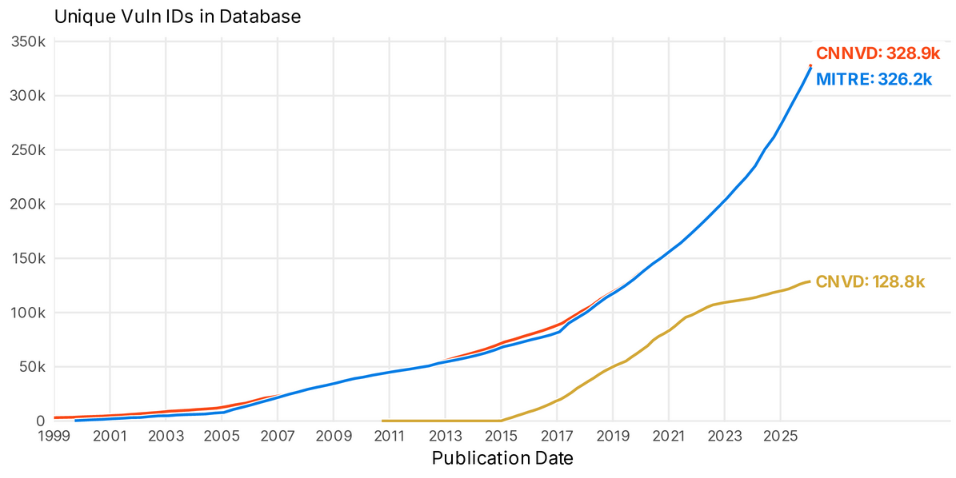
Chinese vulnerability databases: Bitsight looks at two Chinese vulnerability databases, CNVD and CNNVD, and how they compare to MITRE's CVE.
"This foray into one country’s dissemination of vulnerability information gives us a glimpse into what the attack surface landscape might be outside of the United States and Europe. Given the current worries among some about the future of the CVE program, it is certainly worth it to simply look at what else is out there."
Infosec industry
Threat/trend reports: Android, Azure, Dataminr, the Global Anti-Scam Alliance, Group-IB, and Recorded Future have recently published reports and summaries covering various threats and infosec industry trends.
DEFCON bans hackers mentioned in Epstein Files: The DEFCON security conference has banned three individuals mentioned in the Epstein Files from attending its events. Vincenzo Iozzo, Joichi Ito, and Pablos Holman were added to the organization's ban list this week. None of the individuals were charged by US authorities but files released by the DOJ revealed they were in close contact with the late Jeffrey Epstein. [NextGov]
New tool—Sage: Gen Digital's Avast has released Sage, an EDR-like toolkit for AI agents, aka an ADR, an agent detection & response.
New tool—EVMbench: AI giant OpenAI has launched EVMbench, a benchmark for testing an AI agent's ability to find and patch security flaws.
Risky Business podcasts
In this edition of Seriously Risky Business, Tom Uren and Amberleigh Jack talk about a groundswell of calls from officials that European countries need to build cyber capabilities to strike back against adversaries. They also talk about 'distillation attacks' the way that AI developers can steal the secret sauce of advanced models just by asking questions.
In this edition of Between Two Nerds, Tom Uren and The Grugq discuss whether middle powers should be investing in military cyber capabilities.
