Risky Bulletin Newsletter
October 20, 2025
Risky Bulletin: Prisoner hacks prison IT system, goes wild!
Written by

News Editor
This newsletter is brought to you by Dropzone. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
A convict at a Romanian prison has hacked the country's prisoner management platform in a security breach that has rocked Romania's penitentiary agency.
The incident took place in August and continued through October.
From various reports in Romanian media and a statement released by the national penitentiary police union, the incident appears to have originated in the city of Dej, in Romania's Transilvania region, at a prison hospital complex, where prisoners are sent to treat illnesses and then return to finish their sentence at their normal jails.
A prisoner found a way to hack the tablets and kiosks installed in the Dej hospital prison and at other Romanian penitentiaries. These systems allow convicts to access an online platform managed by the National Penitentiary Association (ANP) using a username and password. Prisoners can file requests, can redeem days off their sentence by performing various jobs, or can add money to a bank account that they can later use to shop for certain goods and services.
The prisoner found that shortly after logging into his account, he could perform specific gestures on the tablet or abuse the Start menu and notification area on the kiosk to send the ANP app into the background and access other apps running on the device.
One of these apps was a browser page with other items shared on the same network, including the hospital prison secretary's office printer system.
This part is unclear in the reporting, but it appears the prisoner accessed a printer's web login page, where he claims he could see other people logging into the device and also see the usernames and passwords they were using. This looks like some F12 DevMode hacking. The other theory is that he found access logs and just took a past admin user's credentials, which turned out to also work on the ANP app itself. The account he chose was for a former director of the Dej prison hospital, which had full admin access to the ANP app.
Since this was an in-and-out temporary stay hospital for prisoners, it looks like this one prisoner, whose name was never shared in the reports, might have told others of how to hack the ANP kiosks and tablets.
One of the people he appears to have told is Aurel Z., a prisoner who was later transferred to the Târgu Jiu prison in July. A month later, the prisoner tries the hacking method on his new prison, and finds out that credentials from the Dej also worked here, since it was a nationwide platform.
The first thing Aurel does is to grant some of his inmate friends the right to access adult content.
Once the big, important stuff is out of the way, he starts modifying financial accounts for selected accounts. He modifies money entries by adding a zero to sums, or he deletes past expenses, effectively re-adding already-spent money back into a prisoner's account.
He also modified entries in the "zile câștig" (won days), which are days that prisoners gain on their sentences for an early release.
According to official statements, Aurel modified accounts for 15 prisoners, but he was caught after getting too greedy.
He added too much money to some accounts, with one account holding 5 million lei ($1.15 million), and his own account spending as much as 10,000 lei ($2,300) a month, an outrageous sum for someone locked up in jail, being almost three times the country's minimum wage.
The hacking spree unraveled when accounts and a representative from the CEC Bank started seeing the irregularities between the money that entered the system, the current total, and the spent amounts.
An investigation began shortly after, and authorities discovered the hacks at the start of October, when they removed keyboards from the kiosks and temporarily removed the tablets from use.
The penitentiary police union claims to have observed hacks at two other prison complexes besides Dej and Târgu Jiu, in Timișoara and in Pelendava, near Craiova.
The union claims the Târgu Jiu hacker alone spent more than 300 hours logged into the system with admin access without being detected.
They have also accused the ANP Director of gross negligence for failing to detect the breach after two supervisors and a shift manager reported rumors they heard from inmates about access to porn sites and modified balances. Furthermore, an informant allegedly reported the hack to the ANP a week before it was discovered, only to be ignored.
Because prison life is about reputation, the original prisoner who found the ANP app loophole has come forward to take credit and tell union members about other ways the app could be hacked. According to media reports, this individual was allegedly jailed for IT-related infractions and presented himself as a member of Anonymous.
Aurel Z. is likely regretting his actions right about now. He was serving a nine-year and ten-month prison sentence for laundering money for the Italian mob and was set to be freed five months from now, in January next year.
Risky Business Podcasts
The main Risky Business podcast is now on YouTube with video versions of our recent episodes. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
Hackers leak ICE employee data: Hackers have leaked the personal details of hundreds of DHS, ICE, FBI, and DOJ officials. The leaked data includes names, phone numbers, and even home addresses. The leakers go by Scattered LAPSUS$ Hunters and are the group that tried to extort Salesforce and its customers earlier this month. It's unclear from where the group got its data. [Additional coverage in 404 Media]
KT breach got larger: A security incident at South Korea's second-largest mobile operator is far larger than initially reported. Around 22,200 Korea Telecom customers have had their personal data harvested after connecting to 20 fake mobile towers across the country. The number is far larger than the two fake towers and 5,500 users initially disclosed by KT in August. Users who connected to the fake towers reported unauthorized micro-payments from their accounts. South Korea's government launched an investigation against KT last week for obstructing its probe into the matter. [Additional coverage in the Korea JoongAng Daily]
South Korea confirms Onnara hack: Hackers have breached an internal platform used by the South Korean government to exchange documents, as well as the government's public key infrastructure (GPKI). The country's intelligence agency confirmed the breach two months after an exposé in the Phrack hacking magazine alluded to a suspected breach. The article pointed the finger at North Korea, but new evidence suggests it might have been Chinese hackers. Officials fear stolen digital certificates might have been used to hack other agencies. [Additional coverage in the Digital Daily/English coverage in the Korea JoongAng Daily]
China accuses NSA of hacking time center: The Chinese government has accused the NSA of hacking its National Time Service Center. Officials claim the NSA infiltrated its network and spied on staff since at least 2022. The NSA allegedly exploited vulnerabilities in a messaging service running on staff phones. It then used 42 "cyber weapons" to move laterally, including attempts to gain access to China's high-precision ground timing systems. Officials claim the US was prepositioning to disable or sabotage the system. [Additional coverage in ABC News]
Verisure Alert Alarm breach: Hackers have stolen the personal data of more than 35,000 current and former customers of the Verisure Alert Alarm system. The data was taken from a third-party billing provider and only covers the company's Swedish customers. Verisure says the Alert Alarm intrusion and emergency alert system only has 6,000 customers and is separate from the main Verisure alert systems. [h/t A.S.]
Russian SMS aggregators hacked: Two Russian SMS aggregation services were allegedly hacked and their data put up for sale on hacking forums.
Envoy Air joins Oracle bloodbath: Envoy Air has come out as a victim of the recent Oracle EBS zero-day attacks carried out by the Clop data extortion gang. [Additional coverage in BleepingComputer]
Court orders NSO to stop targeting WhatsApp: A US judge has issued a permanent injunction banning the NSO Group from targeting the WhatsApp platform. The judge also reduced punitive damages the spyware maker owes Meta from $167 million to just $4 million. Meta won the damages in a jury trial that concluded in May. NSO representatives said the order could put the company out of business. [Additional coverage in Reuters]
It's been quite a number of years since we've seen how the Pegasus client panel looks. Document from the WhatsApp lawsuit. (p15 storage.courtlistener.com/recap/gov.us...)
— Jurre van Bergen (@jurrevanbergen.nl) 2025-10-18T21:50:59.429Z
General tech and privacy
Flock teams up with Ring: Flock has partnered with Amazon Ring and will allow its law enforcement customers to access Ring camera footage/streams. [Additional coverage in CNBC]
EFF sues Trump admin over social media surveillance: The Electronic Frontier Foundation has sued the Trump administration over a social media surveillance program. The lawsuit alleges the US government is using social media activity to intimidate union workers, permanent residents, and other valid visa holders based on their political beliefs. The plaintiffs say they were forced to cut down or abstain from their social media posting due to the government's surveillance. They argue the government's actions infringe on their First Amendment.
Experian fined for GDPR violations: The Dutch data protection agency fined Experian's local division €2.7 million for breaking GDPR illegally collecting and selling personal information to assess creditworthiness.
Mozilla to support Firefox on Windows 10: Mozilla says it will continue to support Firefox on Windows 10 installations despite the OS reaching EoL. Per Mozilla data, the OS is still used by almost 37% of all Firefox users.
WhatsApp bans chatbots: Meta has updated the WhatsApp Business API to ban general-purpose AI chatbots. The new terms will go into effect on January 15, next year. After that, Meta will delist any AI chatbot that uses external models. [Additional coverage in TechCrunch]
Ruby team takes control of package repos: The main team behind the Ruby programming language has taken ownership of the Bundler and RubyGems package installers after Shopify attempted a forced corporate-sponsored takeover.
www.ruby-lang.org/en/news/2025... As someone who spent a bunch of time talking before and after this all went down with current and past RubyGems maintainers, RubyCentral employees, gem.coop maintainers and Ruby Core folks: this seems like the best outcome that was actually attainable.
— Mike McQuaid (@mikemcquaid.com) 2025-10-17T13:06:59.735Z
Government, politics, and policy
Russia cracks down on Apple: The Russian government has sent Apple a letter demanding the ability for Russian search engines be installed and used on the company's devices. [Additional coverage in Interfax]
France activates extended data retention rules: The French government has ordered ISPs and mobile operators to store connection and location data for at least a year. The government cited a threat to national security to expand the normal internet logging requirements. The government activated a state of emergency after multiple days of street protests.
South Korea mulls scam compound sanctions: The South Korean government is considering joining the US and UK in sanctioning businesses associated with the cyber scam compound ecosystem. [Additional coverage in the Korea Times]
Hackers extorted Bolton: Hackers breached the personal AOL email account of former national security advisor John Bolton. The breach took place in July 2021, two years after he was fired from the job. The hackers tried to extort Bolton by threatening to release sections removed from a book because they contained classified material. Bolton's camp believes the hackers are Iranian. [Additional coverage in Kim Zetter's Zero Day]
The John Bolton indictment released on Thursday contains a lot of interesting info about the AOL email account prosecutors say he used to send classified info to his wife and daughter while national security advisor - an email account that Iran allegedly hacked. I wrote about the indictment here:
— Kim Zetter (@kimzetter.bsky.social) 2025-10-18T13:20:12.998Z
Sponsor section
In this Risky Business sponsored interview, Tom Uren talks to Edward Wu, CEO and founder of Dropzone AI, about a study that measured how AI practically helps SOC analysts triage real-world problems. Analysts were faster, more accurate and got less tired with AI assistance. Edward thinks the technology won’t replace human analysts, but will speed their skill development.
Arrests, cybercrime, and threat intel
Operation SIMCARTEL: Latvian police have arrested seven individuals who ran a SIM farm that was used in online fraud. Officials seized more than 1,200 SIM boxes and hundreds of thousands of SIM cards. The group used two public websites (gogetsms[.]com and apisim[.]com) to rent access to phone numbers from 80 countries. Numbers rented through the service were linked to multiple forms of fraud and scams. Europol says the SIM farm numbers were linked to 49 million online accounts and that the group caused almost €5 million in damages in Austria and Latvia alone. [Additional coverage by VXDB]
ShinyHunters case in France: There's some weird story coming out of France, where a man arrested in June claims he's not the ShinyHunters admin, as the group kept hacking after he was detained. It's weird because I went back and read the press releases, and French authorities never claimed they arrested the ShinyHunters admin, but four major BreachForums users. [Additional coverage in DataBreaches.net]
CryLock couple profile: The Financial Times published a profile on a Russian couple that ran the CryLock (Cryakl) ransomware. The couple was arrested in Spain and extradited to Belgium. Vadim Sirotin received seven years in prison, while Elena Timofeeva received five years. The two allegedly made a whopping $64 million from 400,000 victims and were early pioneers of the RaaS model.
This is a well written article about the story of two Russians, a couple, who wound up running a ransomware gang from Spain. They may have been undone by targeting Russians, there’s some dangling threads about how they were caught.
— 💀 realhackhistory.org (@bsky.realhackhistory.org) 2025-10-18T09:46:19.494Z
New npm malware: Eighty malicious npm packages were discovered and taken down last week. Check out the GitHub security advisory portal for more details. Some of these packages were caught deploying AdaptixC2, a new C2 framework that launched this year, according to Kaspersky.
Capita hack IR report: Will Thomas has published a summary with the main lessons from the Capita 2023 hack, based on an ICO 136-page report [PDF] released last week, when the ICO also fined Capita £14 million.
Operation MotorBeacon: Seqrite looks at a phishing campaign targeting Russia's automotive sector with the CAPI backdoor.
Zendesk email bomb attacks: Hackers are abusing Zendesk installations to send email bombs. Zendesk says the attackers are exploiting a normal Zendesk feature that allows anyone to create support tickets. According to KrebsOnSecurity, the company is also failing to validate sender emails and impose rate limits on outgoing emails.
20 ASNs responsible for all the badness: Just 20 networks (ASNs) are responsible for 80% of all malicious password spraying activity. According to Microsoft's yearly Digital Defense report, only 1.5% of password spraying attacks are blocked because the user has MFA enabled. This also highlights the still-low adoption of MFA.
Lumma dwindles after doxing campaign: Usage of the Lumma infostealer has declined after hackers took over the malware's Telegram account and started doxing its members. Details of five Lumma Stealer devs were posted on a website called Lumma Rats. Leaked data included real names, photos, passport numbers, bank accounts, email addresses, and links to online profiles. Trend Micro says it recorded a drop in Lumma payloads since the doxing began in late August, as known Lumma customers migrated to other rival infostealers.

Malware technical reports
New infostealer feature: SANS ISC researchers have spotted an infostealer with a novel feature that, besides text, also retrieves image-based content from an infected user's clipboard.
Sponsor section
In this sponsored product demo, Dropzone founder and CEO Edward Wu walks Risky Business podcast host Patrick Gray through the company's AI SOC analyst.
APTs, cyber-espionage, and info-ops
Brickstorm update: Cloud data management company Rubrik has found traces of the Brickstorm backdoor inside its customers' backups. Brickstorm is the backdoor planted inside networks hacked by a Chinese cyber-espionage group.
WaterPlum's OtterCandy: NTT's security team looks at OtterCandy (OtterCookie), a backdoor used by the WaterPlum APT, aka Famous Chollima. There's a similar report on this from Cisco Talos as well.
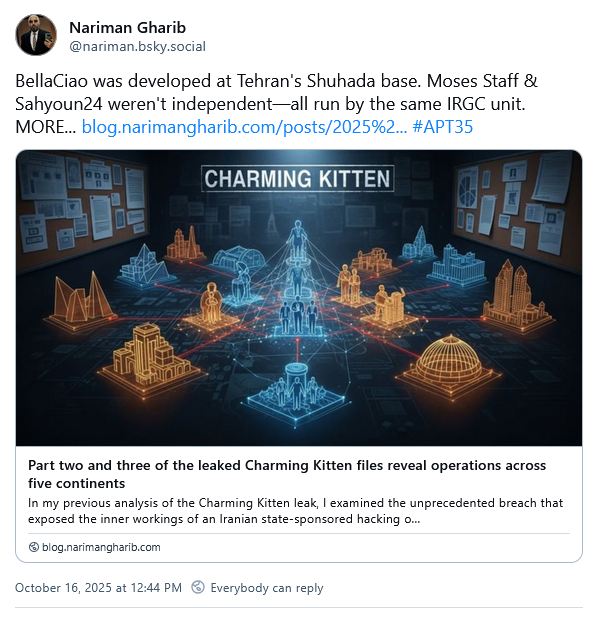
KittenBusters leak: Nariman Gharib has published an analysis of Episodes 2 and 3 of new leaks from the Charming Kitten (APT35) Iranian cyber-espionage group.
"According to exclusive information obtained by me, the BellaCiao malware was developed by a team operating from the Shuhada base in Tehran. This detail provides geographic attribution for where Iranian cyber weapons development occurs, complementing the technical attribution of the malware itself. The Shuhada base connection suggests a degree of organizational structure and permanence to Iran's offensive cyber capabilities, with dedicated facilities for malware development separate from the operational teams deploying it."
Vulnerabilities, security research, and bug bounty
AMD RDSEED vulnerability: The Linux kernel has patched a bug in the RDSEED entropy generator that caused AMD Zen5 chips to fail to produce random numbers. Only a few Zen5 chips were thought to be impacted initially, but now all Zen5 models have been confirmed to be affected. The patch disables RDSEED and forces all AMD Zen5 processors to use RDRAND for generating random numbers. [Additional coverage in Phoronix]
Dolby zero-click vulnerability: Google's Project Zero team has discovered a zero-click exploit in the Dolby Unified Decoder. The exploit allows attackers to run malicious code by sending users malcrafted audio files. No user interaction is required on Android. The issue has been patched in Chrome and Windows, while the Android team is still working on a fix.
7-Zip write-up: A security researcher going by Dominik has reverse-engineered a July 7-Zip security update to look for details about two bugs that can be exploited for remote attacks.
SimpleHelp vulnerabilities: Tenable researchers have discovered two vulnerabilities in SimpleHelp's remote support tool that can be chained for remote code execution on customer devices.
ConnectWise security update: ConnectWise has released a security update to patch two vulnerabilities, including one that could have reverted the app to using cleartext HTTP traffic.
Infosec industry
Threat/trend reports: Check Point, Elastic, Elliptic, Ernst&Young, IANS, NCC Group [PDF], and Zscaler have recently published reports and summaries covering various threats and infosec industry trends.
More companies are getting deputy CISOs: Almost 40% of Fortune 500 companies have named a deputy CISO or similar roles. The role is designed to step in when the CISO is unavailable and act as an eventual successor. According to IANS Research and Artico Search, almost 95% of CISOs now regularly work with C-suite executives and the board on regulatory and other matters. [Additional coverage in CybersecurityDive]
New tool—Project CodeGuard: Cisco has announced Project CodeGuard, a new framework for securing AI code generators and coding agents.
New tool—Sketchy: Security firm Adversis has released Sketchy, a tool that scans and warns about malicious dependencies when users try to clone a repo.
New tool—ReflectSonar: Security researcher Ata Seren has open-sourced ReflectSolar, a tool to create detailed PDF reports of SonarQube scans.
Usenix WOOT videos: Talks from the Usenix Workshop on Offensive Technologies 2025 security conference, which took place in August, are available on YouTube.
Usenix VehicleSec videos: Talks from the Usenix VehicleSec 2025 security conference, which took place in August, are available on YouTube.
Risky Business podcasts
In this edition of Seriously Risky Business, Tom Uren and Amberleigh Jack talk about First Wap, a Jakarta-based company that is selling surveillance-as-a-service. The good news is that it appears that government and media attention have had an impact on high-profile spyware vendors like NSO Group. The bad news is that these smaller players are flying under the radar and aren't afraid of selling to sketchy customers.
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about how different cybercriminal groups are looking for insiders to provide network access.
