Risky Bulletin Newsletter
June 27, 2025
Risky Bulletin: Phishers abuse forgotten Direct Send feature
Written by

News Editor
This newsletter is brought to you by Authentik. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
Phishing gangs are abusing a little-known Microsoft Exchange Online feature to send malicious emails to Microsoft 365 tenants and their employees.
The feature is named Direct Send and allows hardware devices inside a company's network to use the Exchange Online server to send emails. It is typically used by printers and scanners to send scanned documents via email or by phone or video conferencing applications to send invites and reminders to participants.
Direct Send is basically an endpoint that can be accessed via a smart host URL that has the format of tenantname.mail.protection.outlook.com.
Devices and apps on a company's network send emails to this URL, and the Exchange Online service delivers them on their behalf.
To prevent abuse, Microsoft restricts sending emails only to a tenant's users (internal users). You can't send emails meant for external users and expect Direct Send to deliver them as a "relay," as they'll just be dropped.
There are no other checks. No checks to authenticate the user who's sending the email or that the email itself passes SPF, DKIM, or DMARC checks.
In a report published on Thursday, Varonis researchers say they have now spotted at least one threat actor blasting Direct Send URLs with phishing emails that are then distributed to a tenant's employees.
The threat actor is apparently using a PowerShell script that assembles the phishing emails and then sends them to the Direct Send endpoint.
The emails come from a Ukrainian IP address, but because Direct Send only checks that the recipient of the email belongs to the organization, the phishing emails are delivered without any other action. The attacker also spoofed the email sender to pose as another employee to improve the chances that recipients open the emails and are lured to phishing sites.
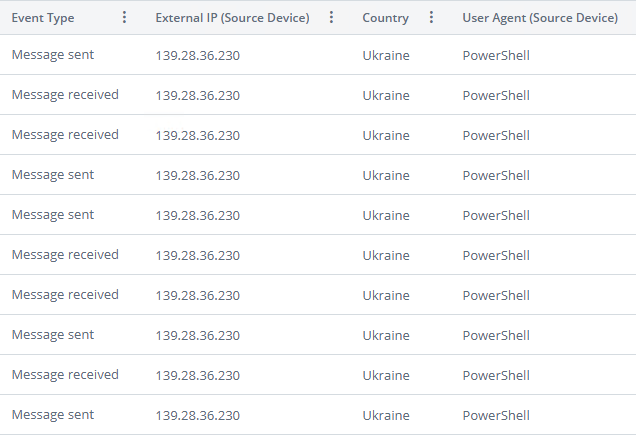
Varonis says the novel phishing campaign has been going on since May and has targeted the employees of more than 70 organizations so far, with most being located in the US.
The attacker only needs to know the tenant's Direct Send URL, which is easy to guess, and the recipient's email address, which most phishers know already.
The Varonis report marks the first time Direct Send is being abused at scale. A 2023 JumpSec report documented initial attacks that exploited Direct Send, but the technique has not caught on with other groups.
Microsoft seems to have seen some sort of abuse targeting this feature ahead of Varonis because the company released in April a "public preview" of a new Exchange Online setting named "Reject Direct Send" that basically allows customers to disable the feature if they're not using or want to take the time to properly configure it.
Risky Business Podcasts
The main Risky Business podcast is now on YouTube with video versions of our recent episodes. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
Patient death linked to Synnovis ransomware attack: The UK National Health Service says that one person died because of a ransomware attack on a major blood analysis lab last year. NHS officials say the patient died unexpectedly after a long wait for blood results. The patient died after the Qilin group ransomed UK blood lab Synnovis last June. The attack caused harm to 170 patients and permanent long-term damage in at least two other cases. [Additional coverage in Sky News]
Scale AI stores customer data in public files: A Business Insider investigation has found that employees and contractors at Scale AI are storing sensitive customer data in public Google Docs. Some of its customers include the likes of Google, Meta, and xAI.
Envato denies breach: Online digital assets marketplace Envato has denied a security breach after a threat actor claimed to have exploited its API to extract 11 million user email addresses. [Additional coverage in CyberDaily]
ABCD app hacked, customer funds stolen: A hacker has breached Indian financial app ABCD and has stolen almost $230,000 from customer accounts. The app's maker says only 435 user accounts were affected. The company described the source of the hack as "technical vulnerabilities." The app had over 1.2 million customers last September. [Additional coverage in The Hindu Business Line]
PACER under constant attack: US officials say that the PACER electronic court documents system is seeing constant attacks from hackers trying to gain access to the system. [Additional coverage in The Record]
Glasgow cyberattack: The Glasgow City Council has taken down several online services offline after a cyberattack on Thursday. Officials say customer data may have been stolen in the intrusion. The attack has impacted the city's systems for paying parking fines and reporting school absences. [Additional coverage in the BBC]
Papa John's Korean breach: Hackers exploited a vulnerability in the South Korean website of pizza franchise Papa John's. The company says hackers stole customer details such as names, contact details, and delivery addresses. The bug existed on the company's website since 2017. South Korea's data protection agency is now investigating the company. [Additional coverage in Korea JoongAng Daily]
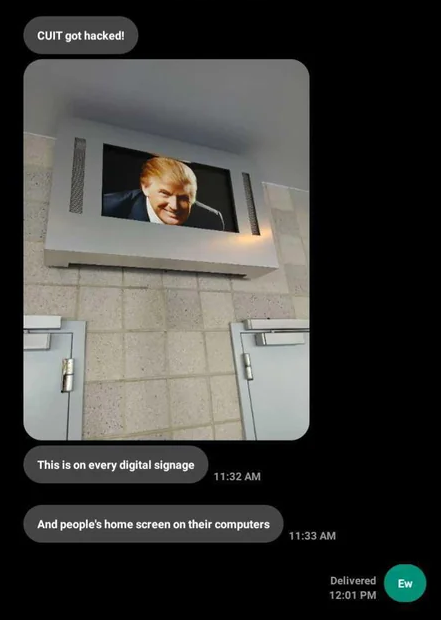
Columbia University hack: Hackers breached the IT systems of Columbia University and defaced computer screens with an image of President Donald Trump. The school's website and student authentication system have been down since Tuesday as well. Sources told The Record there were no signs of a ransomware attack or a sprawling breach.
General tech and privacy
Chrome 138: Google has released version 138 of its Chrome browser. See here for security patches and webdev-related changes. The biggest change in this release is the addition of Google's new Gemini AI mode in the address bar, a new footer for the new tab page, and support for sharing tab groups with other users. This version is also the last Chrome release to be supported for Android 8 and 9.
Google donates A2A protocol: Google has donated the Agent2Agent (A2A) protocol to the Linux Foundation. A2A is a protocol for communication between distinct AI agents.
New PNG format specification: The W3C has released a new specification for the PNG image format. The new PNG v3 specification supports animated PNGs, HDR graphics, and EXIF metadata. [Additional coverage in Phoronix]
Swift coming to Android: Apple is working on porting its Swift programming language to Android.
Data broker registration gaps: A joint EFF and Privacy Rights Clearinghouse investigation has found gaps in US data broker registration laws that allow companies to register as data brokers in some states but not others, allowing them to skirt privacy legislation. [Additional coverage in CyberScoop]
Slack adds AI stuff: Slack is adding AI features to all its users, including free accounts, even if they want it or not.
Let's Encrypt ends email notifications: Free Certificate Authority Let's Encrypt has ended its email notification service that warns users of expiring certificates. The company blamed this on rising costs.
Samsung will purge inactive accounts: Smartphone maker Samsung will purge inactive accounts at the end of July. The company will delete accounts that haven't been logged into for the past two years. Users have until July 31 to log into accounts to keep them alive. Samsung is the latest company after Google, Yahoo, and PhotoBucket to implement such policies. [Additional coverage in SamMobile]
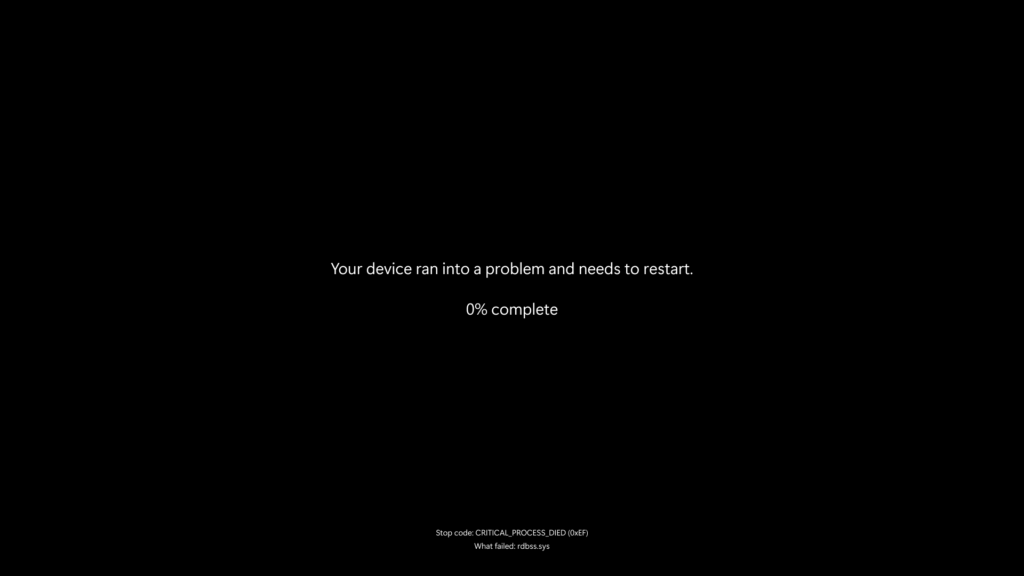
Microsoft redesigns the BSOD: As part of its overhaul of Windows recovery processes, Microsoft has redesigned the BSOD screen, which will now be black, keeping the BSOD acronym intact.
Microsoft offers one year of free Win10 security updates: Microsoft will offer Windows 10 Extended Security Updates for free to home users for the first year. Windows 10 will reach end-of-life on October 15 this year. Extended Security Updates will be available for paying customers for three years. Home users can claim the first year for free if they enroll in the ESU and sync PC settings data to their Microsoft Account. The following two years will cost users $30/year. [Additional coverage in Windows Central]
Government, politics, and policy
Russia's VirusTotal goes under: Russia's government-backed VirusTotal clone has gone offline. Russia's Minister of Digital Development launched the service in 2023 and was scheduled to operate at full capacity this year. The National Multiscanner was shut down this month due to a lack of funding. Russia also abandoned building a GitHub clone last year due to a lack of funding.
RuStore becomes mandatory: All smartphones sold in Russia must include a version of the RuStore app store starting in September. The RuStore is a mobile app store launched by the Russian government that carries Russian apps. Device manufacturers must include the RuStore app but also not take any measures to limit its functionality. The Russian Parliament passed a new law this week mandating the new requirement. The law specifically targets Apple, which restricts third-party app stores on iOS. [Additional coverage in Izvestia]
Armenia's cyber threat landscape: The Media Diversity Institute and CyberHUB-AM have published a cyber threat landscape report for Armenia after the country's recent turn towards the EU and the US. Loads of Russia mentions in there.
Indian state changes law to deal with hackers: India's Supreme Court has upheld a new law in India's Tamil Nadu state that introduces preventive custody for cybercrime-related charges. The new law will allow law enforcement to arrest and detain hackers until investigations are concluded. It replaces current procedures where suspects are left at large. Officials say the new law is needed because cybercrime suspects have often continued their hacking sprees or absconded. [Additional coverage in The 420] [h/t DataBreaches.net]
Lyon abandons Windows: The French city of Lyon will migrate away from Microsoft products as part of a push for digital sovereignty. The city will replace Windows with Linux, Office with an open-source version named OnlyOffice, and Microsoft databases with PostgreSQL. Lyon is the third-largest city in France by population. It joins the Danish cities of Aarhus and Copenhagen in efforts to replace US tech products with open-source alternatives. The EU itself is also looking at migrating from Azure to an EU-based cloud provider.
US government quantum policy: The US GAO has concluded in a report this week that a centralized government office should be in charge of the government's national quantum policy. GAO suggested this task should fall to the Office of the National Cyber Director. [Additional coverage in NextGov]
US & China exploit acquisition comparisons: The Atlantic Council has published a comparison of the zero-day acquisition programs in China and the US. The conclusion is that the US is far behind China, which has "weaponized" its internal vulnerability research community to its advantage.
New CISA guidance: CISA and the NSA have published a joint guide to help organizations migrate their software development to memory-safe programming languages.
Workforce cuts have decimated US cybersecurity: The US private sector and operators of US critical infrastructure have reduced or stopped sharing sensitive information with the US government. According to a CybersecurityDive investigation, the change comes after the US government eliminated CIPAC, a framework that allowed private companies to share cyber and threat intel without legal penalties. Cuts to the US government workforce, especially CISA, have also had an impact. Points of contact have been fired, and CISA has stopped attending meetings with private sector partners.
Trump's workforce overhaul and political reorientation have seriously weakened CISA, the lead infrastructure protection agency, according to my sources. People say they barely recognize their once-reliable partner. "With CISA, there is no partnership. It’s gone."
— Eric Geller (@ericjgeller.com) 2025-06-25T16:01:52.870Z
Sponsor section
In this Risky Bulletin sponsor interview, Fletcher Heisler, CEO of Authentik, talks to Tom Uren about the inflection points that make organizations consider rationalizing their Identity Providers (IdPs). The pair also discuss sovereign tech stacks and how to earn the trust of customers.
Arrests, cybercrime, and threat intel
BreachForums top users arrested: French authorities have arrested five high-ranking members of BreachForums, an online community for selling hacked data. Forum users ShinyHunters, Hollow, Noct, and Depressed were arrested this week. A fifth suspect and the site's administrator was arrested in February. He went on the forum as IntelBroker but has now been identified as a 25-year-old British man named Kai West. BreachForums has been offline since April after allegedly getting hacked by a rival platform.

Student hacks Aussie uni: Australian police have arrested a 27-year-old woman for allegedly hacking the Western Sydney University. Birdie Kingston, 27, allegedly first hacked the school to get discounted parking on campus. She escalated her hacks to alter school results and later extorted the university by threatening to sell student data on the dark web. The hacking spree began in 2021 and continued up to this year. [Additional coverage in ABC]
Nonprofit hacker pleads guilty: A Kansas City man has pleaded guilty to hacking a nonprofit and a health club business.
AI Black Hat SEO: Per a new Zscaler report, threat actors are using Black Hat SEO to poison search engine rankings for AI keywords to spread malware. These campaigns have distributed malware like Vidar, Lumma, Legion Loader, and cryptominers.
New AI scanner evasion technique: Check Point researchers have discovered a malware strain that embedded AI prompt injections in its source code in an attempt to evade detection by AI-based malware scanners. The malware tried to order the AI scanner to "ignore all previous instructions" and return a "no malware detected" result. The malware was designed to open Tor-based backdoors on infected Windows systems.
MOVEit scans surge: GreyNoise has spotted a surge in scans for MOVEit file transfer servers. The scan activity started on May 27 and is still ongoing. Active exploitation from the scanning cluster was also spotted on June 12, but only on that day.
CL-CRI-1014: Palo Alto Networks has published a profile on CL-CRI-1014, a threat actor targeting African financial institutions and selling access to their systems on the dark web.
DPRK IT worker case: The Ketman Project has spotted a DPRK IT worker account hijacking and taking over a dead crypto project named the Keeper Wallet.
Zoom Events phishing abuse: Recon Infosec has spotted a phishing campaign that abused the infrastructure of the Zoom Events feature.
New SilverFox campaign: Netskope has spotted a new campaign from SilverFox, a financially motivated group targeting Chinese users. Final payloads include the Sainbox RAT and the Hidden rootkit.
Malware technical reports
Androxgh0st: CloudSEK published a report on the recent changes to the Androxgh0st botnet.
Odyssey Stealer: CyFirma researchers have spotted Odyssey Stealer, a rebrand of the older Poseidon Stealer, an infostealer targeting macOS systems.
Dire Wolf ransomware: Trustwave researchers have published an analysis of Dire Wolf, a new ransomware group that began attacks at the end of May.
Sponsor section
Authentik is an open-source identity provider that is also offered with paid enterprise features. In this demo, CEO Fletcher Heisler and CTO Jens Langhammer walk Risky Business host Patrick Gray through an overview and a demo of the technology.
APTs, cyber-espionage, and info-ops
Contagious Interview campaign on npm: Socket Security has spotted 35 malicious JavaScript packages uploaded on the npm portal by North Korean state hackers. The company linked the incident to a DPRK campaign known as Contagious Interview. These attacks target developers via fake job offers and coding tests laced with malware.
Educated Manticore: An Iranian APT group named Educated Manticore has launched an email and WhatsApp spear-phishing campaign targeting Israeli journalists, high-profile cyber security experts, and computer science professors from leading Israeli universities. The group is also known as APT42, Charming Kitten, and Mint Sandstorm.
Operation Overload adopts AI: CheckFirst says a Russian disinformation operation known as Operation Overload has adopted AI to generate massive amounts of Russian propaganda and disinformation on Western democracies. The operation has now also expanded from Twitter and Telegram to BlueSky and TikTok.
Vulnerabilities, security research, and bug bounty
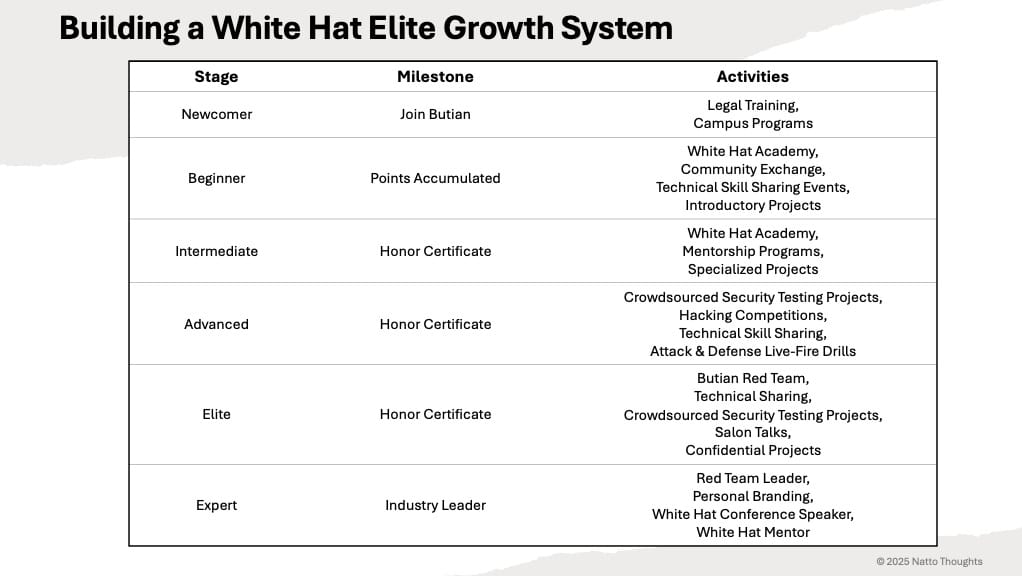
Butian profile: Natto Thoughts has published a profile on Butian, a bug bounty and hacker training platform operated by Chinese security firm QiAnXin.
Cisco security updates: Cisco has released two security advisories for various products. One of them is an unauth RCE in the Cisco Identity Services Engine.
KEV update: CISA has updated its KEV database with three vulnerabilities that are currently exploited in the wild. They include a 2019 Fortinet hardcoded creds bug, a 2024 D-Link router path traversal, and a 2024 AMI MegaRack auth bypass.
Citrix exploitation: Citrix says a bug tracked as CVE-2025-6543 is now being exploited in the wild.
Wire persistence issues: Security firm Almond has found that the Wire secure messaging platform does not delete shared files from its servers after users delete them.
XSS in Palo Alto GlobalProtect VPN: XBOW, the AI company that recently became number one on HackerOne through its automated reports, has published a write-up on how its AI systems found several XSS vulnerabilities in Palo Alto's GlobalProtect VPN firmware.
n0Auth exposure two years later: Security firm Semperis says it scanned 104 SaaS apps and found that nine were vulnerable to n0Auth, a two-year-old vulnerability that can let attackers hijack user accounts via Entra ID. Semperis anticipates that thousands more apps are also still vulnerable.
OpenVSX takeover: The OpenVSX platform has patched a vulnerability that could have allowed attackers to hijack its infrastructure. The platform is an independent marketplace for VS Code extensions. According to Koi Security, attackers could have abused the access to take control over all extensions and deploy malicious code to over eight million developers.
MCP misconfigurations: Backlash Security looks at the various MCP server misconfigurations it has spotted in the wild.
Unpatched Kerio Control firewall bug: Security researchers have discovered a major vulnerability in Kerio Control firewalls. The vulnerability can allow attackers to bypass authentication and gain root access to the device through its proxy server component. Researchers have published details and proof-of-concept code after the vendor failed to release a patch. There are almost 300 Kerio Control firewalls currently exposed on the internet and likely vulnerable.
BLE vulnerability in Airoha chips: Bluetooth headphones using Airoha chips are vulnerable to attacks that can extract data from paired smartphones or turn the headphones into listening devices. The issues reside in a custom protocol that ships with the Airoha chips. Security firm ERNW says the protocol isn't authenticated and can be manipulated via both BLE and Bluetooth Classic connections. The vulnerabilities impact headphones, earbuds, dongles, and microphones sold by Sony, Marshall, JBL, and Beyerdynamic. Exploiting the bugs requires proximity to the target, which is usually up to 10 meters. [Additional coverage in Heise]
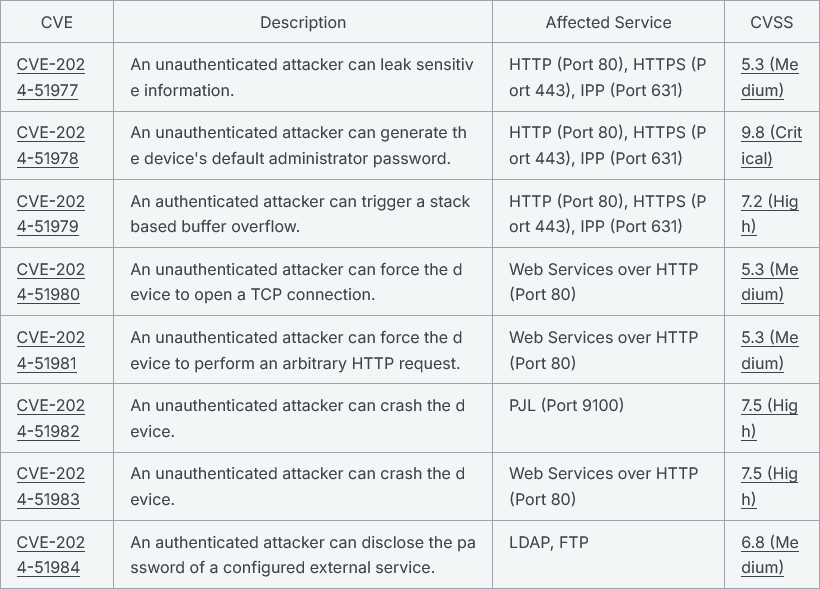
Printer vulnerabilities: Rapid7 researchers have found eight vulnerabilities that impact 748 printer models across five different vendors. The most affected vendor is Chinese company Brother, with 689 different models. The worst of the vulnerabilities is an authentication bypass that can be used to leak a printer's serial number. The serial number can then be used to generate a device's default admin password.
Infosec industry
Threat/trend reports: CyberHUB-AM, CYE, Forescout, NCC Group, SecurityScorecard, and Trustwave have recently published reports and summaries covering various infosec trends and industry threats.
New tool—OWASP AI Testing Guide: The OWASP Foundation has released the OWASP AI Testing Guide, a framework to test AI systems for security, ethics, reliability, and compliance.
AWS re:Inforce 2025 videos: Talks from the AWS re:Inforce 2025 developer and security conference, which took place this month, are available on YouTube.
CornCon 2024 videos: Talks from the CornCon 2024 security conference, which took place last October, are available on YouTube.
Risky Business podcasts
In this edition of Seriously Risky Business, Tom Uren and Patrick Gray talk about a new report that compares Chinese and American 0-day pipelines. The US is narrowly focused on acquiring exquisitely stealthy and reliable exploits, while China casts a far broader net. That was fine in the past, but as 0-days get harder and harder to find, the report argues that the US needs to change the way it goes about getting them.
In this edition of Between Two Nerds, Tom Uren and The Grugq dive into the motivations and actions of Predatory Sparrow, a purported hacktivist group that has been attacking Iran for the last five years and has leaped into the Iran-Israel work.
