Risky Bulletin Newsletter
January 10, 2025
Risky Bulletin: Over 4,000 backdoors can be hijacked via expired C&C domains
Written by

News Editor
You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
Risky Business Podcasts
Risky Business is now on YouTube with video versions of our main podcasts. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
PowerSchool data breach: Edu software company PowerSchool says hackers breached its SIS student management platform and stole some student records. The company is notifying affected schools, per a DataBreaches.net report.
Gravy Analytics hack: Hackers claim to have breached Gravy Analytics, a company that aggregates and sells access to app location data. [Additional coverage in 404 Media]
UGKK ransomware attack: Slovakia's Geodesy, Cartography, and Cadastre Authority suffered what appears to be a ransomware attack. [Additional coverage in Finsider.sk]
Rosreestr hack: A hacking group known as Silent Crow claims to have hacked and leaked data from Russia's State Registration, Cadastre, and Cartography (Rosreestr) agency. [Additional coverage in Meduza]
RegionTransService hack: Ukraine's military intelligence agency GUR is believed to have hacked and wiped the IT infrastructure of RegionTransService, a company that provides wagon maintenance services to Russian Railways (RZD). [Additional coverage in the Kyiv Post]
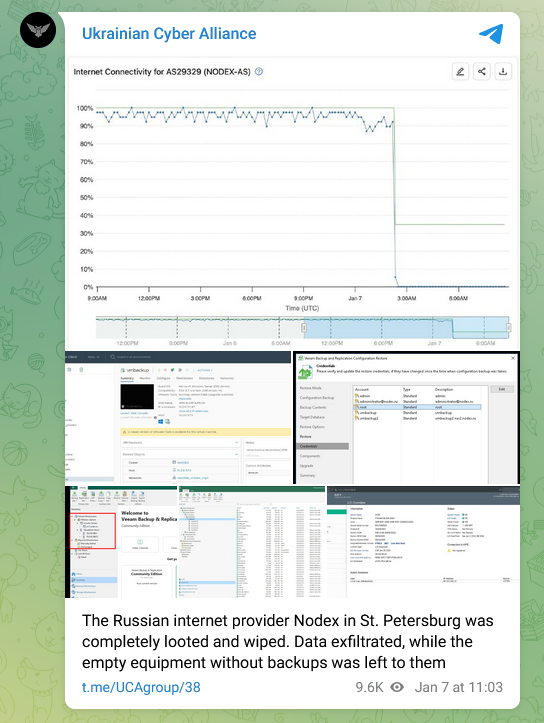
Nodex data wiping attack: A Ukrainian hacking group named the Ukrainian Cyber Alliance has hacked and wiped the infrastructure of a Russian ISP named Nodex.
MetLife denies ransomware attack: US insurance company MetLife has denied that it suffered a security breach on its Latin American division. The denial comes days after the RansomHub gang claimed to have the company's data. [Additional coverage in Cybernews]
OPM payments not claimed: Federal employees impacted by the 2015 OPM hack only claimed 7% ($4.8 million) of the $58.2 million settlement awarded to them in 2022. [Additional coverage in GovExec]
Atos denies cyberattack: French security firm Atos has denied suffering a cyberattack after the Space Bears ransomware claimed it breached the company.
Packers store hack: The online store of the Green Bay Packers NFL team has been hacked and compromised with an e-skimmer. Over 8,500 customers are believed to have had their credit card data stolen.
UN ICAO hack: The United Nations' civil aviation agency ICAO said that hackers gained access to its internal recruitment database following a recent security breach.
Philippines govt hack: Chinese state-sponsored hackers are believed to have breached the Philippines government's internal network in May of last year, according to a Bloomberg report. Sophos believes the government was one of the victims of the Crimson Palace operation.
Three more Salt Typhoon victims: Sources have told the Wall Street Journal the names of three new American telcos that were breached by Chinese espionage group Salt Typhoon last year. They are Charter, Consolidated Communications, and Windstream. The other four known victims include AT&T, Lumen, Verizon, and T-Mobile. Two more telcos need to be named.
Treasury is only BeyondTrust govt victim: CISA says the US Treasury Department is the only government agency so far that was impacted by the BeyondTrust breach.
Roomster leak: Roommate finding platform Roomster leaked the data of hundreds of thousands of users via a misconfigured server last year. [Additional coverage in DataBreaches.net]
LoL DDoS attacks: Players part of T1, the League of Legends world champions team, have been unable to stream the game for days after its members have been targeted with DDoS attacks. [Additional coverage in eSports.gg]
General tech and privacy
PyPI Project Quarantine: The Python Software Foundation launched last August Project Quarantine, a new feature for PyPI admins to quarantine suspicious projects. So far, the project has been used to quarantine around 140 libraries.
Firefox 134: Mozilla has released Firefox 133. New features and security fixes are included. The biggest feature in this release is a new New Tab page and improved support for debugging web extensions.
Apple settles Siri privacy lawsuit: Apple has agreed to pay $95 million to settle a lawsuit alleging that its Siri voice assistance recorded private conversations and that some conversations were shared with third parties and used for targeted ads. [Additional coverage in ArsTechnica]
Meta ends fact-checking program: Meta has ended its fact-checking program and is introducing a Twitter-like community notes system. The company justified its move as restoring fReE sPeEcH. The company says it will also allow political content back on the platform and will also relax its moderation practices (aka allow harassment, if you need a translation). Meta says it will also move its moderation centers from California to Texas because of concerns that "biased employees are overly censoring content." Guess Trump threatening Zuckerberg with life in prison worked. I'm honestly surprised the Meta press release didn't encourage a military invasion of Greenland.
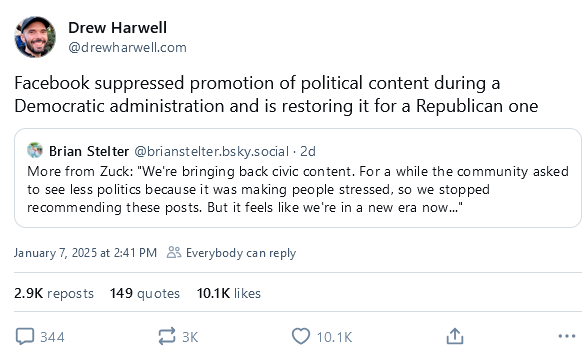

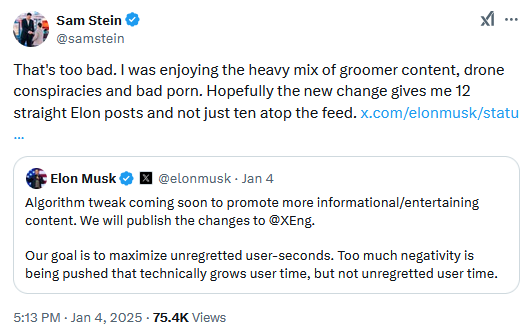
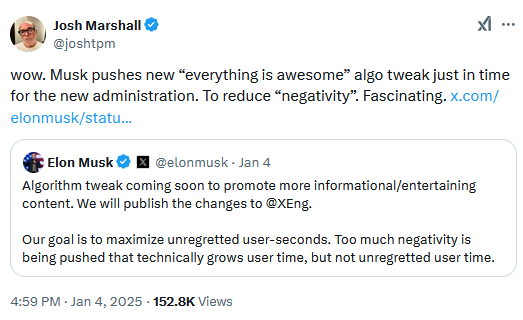
Twitter changes algorithm: Elon Musk says Twitter/X will change its algorithm to promote "informational/entertaining content," aka the stuff you usually find in automated meme accounts. The move comes after Twitter changed its algorithm last year, ahead of the 2024 global election cycle, to promote content from smaller accounts—aka troll farm accounts. Now that the elections are over, nobody needs to see "too much negativity" on the platform, as Musk put it.
Wikipedia attacks: American right-wing think tank the Heritage Foundation, which produced Project 2025, plans to "identify and target" Wikipedia editors. The organization plans to use the guise of "antisemitism" to go after editors, but American right-wing figures like Trump and Musk have attacked the site for hosting information on some of their past actions they'd like expunged from the public record.
"Employees of Heritage, the conservative think tank that produced the Project 2025 policy blueprint for the second Trump administration, said they plan to use facial recognition software and a database of hacked usernames and passwords in order to identify contributors to the online encyclopedia, who mostly work under pseudonyms."
Government, politics, and policy
Taiwan reports doubling in cyberattacks: Taiwan's National Security Bureau says the average number of daily cyberattacks targeting Taiwan's government network doubled to 2.4 million in 2024, with China being behind most of the attacks. [Additional coverage in FocusTaiwan]
US looks to ban Chinese drones: The US Commerce Department says it is looking into issuing a national ban on the sale of Chinese-made drones due to national security concerns.
US raises Treasury hack with China: US Treasury Secretary Janet Yellen had a virtual meeting with Chinese Vice Premier He Lifeng and called out the country's recent hack of the US Treasury network.
UK outlaws creating sexually explicit deepfakes: The UK government announced this week plans to outlaw the creation of sexually explicit deepfake images of videos. Perpetrators face up to two years behind bars under new offenses for taking an intimate image without consent and installing equipment to enable these offenses.
Russian SORM tech across LATAM: A Recorded Future report highlights how Russia's surveillance tech platform SORM has been deployed across LATAM in Cuba and Nicaragua.
Lithuania launches Cyber Command: The Lithuanian government has launched LTCYBERCOM, a new military unit dedicated to cyber operations. [Additional coverage in The Defense Post]
Risky Business Podcasts
Brian A. Coleman, Senior Director for Insider Risk, Information Security, and Digital Forensics at Pfizer, talks to us about how his security team is experimenting with AI to improve their insider risk detection systems. The system Brian and his team put together can detect sensitive information or documents handled by unauthorized accounts, but can also spot documents moving around and ending up where they shouldn't be - either by accident, malice, or as a result of a security breach.
Arrests, cybercrime, and threat intel
Song hacker sent to prison: British authorities have sentenced 22-year-old Skylar Dalziel to 21 months in prison for hacking and stealing unreleased music from famous artists like Coldplay and Bebe Rexha. [Additional coverage in the BBC]
MSFT disrupts AI hacking-as-a-service scheme: Microsoft's legal team is seeking a court order to seize servers and domains used by a hacking-as-a-service portal that sells stolen Azure OpenAI API keys. [Additional coverage in CyberScoop]
Malicious npm packages: Socket devs have found new malicious npm packages targeting Ethereum developers by impersonating Hardhat plugins and the Nomic Foundation. The end goal was to steal private wallet keys. Another campaign targeting Solana devs was also spotted by Sonatype.
Muddling Meerkat: Infoblox has published a new report on Muddling Meerkat, a Chinese threat actor conducting DNS operations via the Chinese Great Firewall. Recent operations involve the use of domain spoofing for malicious spam campaigns.
Tycoon 2FA: Validin has published a new analysis of the Tycoon 2FA Phishing-as-a-Service platform.
EC2 Grouper: Fortinet has published a report on EC2 Grouper, a threat actor specialized in hacking AWS infrastructure.
Moscow Pentest: A new pro-Kremlin hacktivist group named Moscow Pentest has emerged in underground circles.
Apos RaaS: A new RaaS platform launched last year named Apos. It was mostly inactive throughout the year before adding new victims at the start of 2025.
Abandoned C2s: watchTowr has identified over 4,000 live backdoors in the wild that use expired C&C domains, which means they could be hijacked by new cybercrime groups.
LDAPNightmare fake PoC: Someone is using a fake PoC for the LDAPNightmare exploit to infect researchers and threat actors with an infostealer.
Hangro: A security researcher has looked at the infrastructure of Hangro, a VPN app that North Korean authorities use to hide their communications.
Magecart attack status: Trustwave has published a top-down look at the state of Magecart (e-skimmer) attacks these days. tl;dr: They're still going.
CWS manipulation: Security researcher Wladimir Palant details a new technique used by various threat actors to manipulate the Chrome Web Store search results and rank above legitimate extensions.
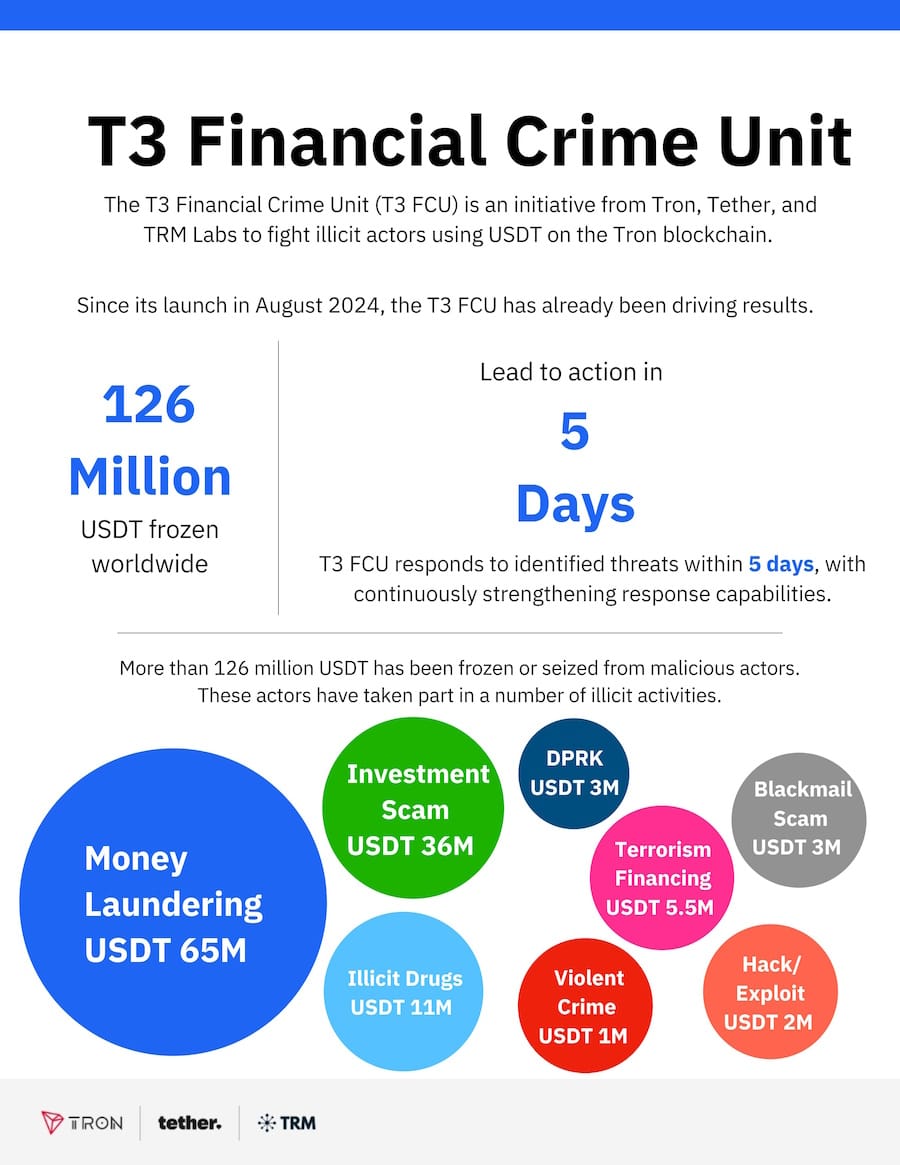
Crypto seizures last year: The T3 Financial Crime Unit, a collaboration between TRON, Tether, and TRM Labs, has frozen more than $126 million in criminal assets globally last year.
Malware technical reports
Gayfemboy: QiAnXin researchers have published a report on a new Mirai-based botnet that is exploiting zero-days in Four-Faith industrial routers.
PEAKLIGHT/Emmenhtal: TRAC Labs has published a report on PEAKLIGHT (aka Emmenhtal), a relatively new PowerShell-based loader. Also, check out previous reports on the same loader from Sekoia and Google.
Banshee Stealer: Check Point researchers have published a technical analysis of a new version of Banshee, an infostealer targeting macOS users.
"This new version had been undetected for over two months until the original version of Banshee Stealer was leaked on XSS forums, which resembled similarities with the malware's core functionality."
NonEuclid RAT: CyFirma has spotted a new RAT named NonEuclid.
"This RAT, developed using C# and built for the .NET Framework 4.8, is designed to operate with minimal security checks, making it more difficult for security systems to detect and block its activities."
PacketCrypt Classic returns: SANS ISC has spotted new versions of the PacketCrypt Classic cryptominer being deployed on hacked PHP servers.
HIVE: Nextron Systems has discovered a new version of Xdr33, a variant of the CIA's HIVE malware toolkit that appears to have been modified and is being used by a third party.
NoviSpy: The spyware used against Serbian activists is now on VirusTotal.
Hunters International: Forescout has published an analysis of Hunters International, a ransomware group that had an uptick in activity last year.
Risky Business Podcasts
In this podcast, Tom Uren and Adam Boileau talk about the continued importance of hack and leak operations. They didn't really affect the recent US presidential election, but they are still a powerful tool for vested interests to influence public policy.
APTs, cyber-espionage, and info-ops
IT Army of Ukraine: The IT Army of Ukraine claims its cyberattacks last year on Russia inflicted twice the economic damage than the two previous years combined.
EagerBee backdoor: Kaspersky has published a technical breakdown of EagerBee, a new backdoor used by an unnamed APT in cyber-espionage campaigns targeting Middle Eastern governments and telcos.
Ocean Lotus ops on GitHub: Weibu's security team says Vietnamese APT group Ocean Lotus is using malware-laced GitHub repos to target Chinese developers and organizations.
US sanctions Flax Typhoon-linked company: The US Treasury has imposed sanctions on Beijing-based cybersecurity company Integrity Technology Group. Officials say the company built and operated a botnet named Raptor Train that was used in attacks by a Chinese cyber-espionage group known as Flax Typhoon. The FBI and the Justice Department disrupted the botnet in September of last year.
MirrorFace attacks in JP: Japanese authorities say a Chinese hacking group known as MirrorFace has targeted 210 organizations since 2019.
RedDelta: Recorded Future looks at RedDelta campaigns targeting Mongolia, Taiwan, Myanmar, Vietnam, and Cambodia with the PlugX backdoor. The company classifies RedDelta as a Chinese state-sponsored group.
APT-C-26 (Lazarus): Qihoo360 has published a report on a recent APT-C-26 campaign using malicious IPMsg installers to target and infect victims with backdoors.
Vulnerabilities, security research, and bug bounty
New Ivanti zero-day: Ivanti has released two security updates for its Connect Secure, Policy Secure & ZTA gateways, including a fix for an actively exploited zero-day (CVE-2025-0282). Google has linked the attacks to a Chinese APT cluster it tracks as UNC5221.
GFI Kerio Control firewall exploitation: Threat actors are exploiting a recently disclosed vulnerability (CVE-2024-52875) in GFI Kerio Control firewalls.
"User input passed to these pages via the 'dest' GET parameter is not properly sanitized before being used to generate a 'Location' HTTP header in a 302 HTTP response. Specifically, the application does not correctly filter/remove linefeed (LF) characters. This can be exploited to perform HTTP Response Splitting attacks, which in turn might allow to carry out Reflected Cross-Site Scripting (XSS) and possibly other attacks."
Android Security Bulletin: Google has released the Android security updates for January 2025.
GitLab security updates: GitLab has released security updates to patch four vulnerabilities in its main product.
SonicWall security updates: SonicWall has released four security updates for its SonicOS products.
Cisco security updates: Cisco has released three security advisories for various products.
Splunk security updates: Cisco has released two security advisories for its Splunk SIEM platform.
Moxa security updates: Moxa has released two security updates for its industrial routers. The patches fix hardcoded credentials and an OS command injection.
KEV update: CISA has updated its KEV database (twice) with four vulnerabilities that are currently exploited in the wild. This includes the Ivanti zero-day, two Mitel MiCollab vulns, and a 2020 Oracle WebLogic issue.
Nuclei vulnerability: ProjectDiscovery has patched a vulnerability (CVE-2024-43405) in the Nuclei vulnerability scanner that could have allowed threat actors to hide malicious code in Nuclei signatures that runs malicious code on systems where the Nuclei scanner executes.
Illumina BIOS/UEFI vulnerabilities: Eclypsium has identified BIOS/UEFI vulnerabilities in Illumina DNA gene sequencers.
"More specifically, we found that the Illumina iSeq 100 used a very outdated implementation of BIOS firmware using CSM mode and without Secure Boot or standard firmware write protections. This would allow an attacker on the system to overwrite the system firmware to either 'brick' the device or install a firmware implant for ongoing attacker persistence."
AWS snafu: According to Giraffe Security, AWS staff have somehow managed to re-introduce the same dependency confusion to RCE vulnerability into its platform three times over the past four years.
Spyndicapped technique: CICADA8 researchers have developed Spyndicapped, a new keylogging technique that works on top of the Microsoft User Interface Automation framework. A proof-of-concept is available on GitHub.
KernelSnitch: Academics have disclosed a new software side-channel attack named KernelSnitch [PDF]. The attack targets kernel data structures such as hash tables and trees.
"These structures are commonly used to store both kernel and user information, e.g., metadata for userspace locks. KernelSnitch exploits that these data structures are variable in size, ranging from an empty state to a theoretically arbitrary amount of elements."
LDAPBleed and LDAPNightmare: Cato Networks has published a report on LDAPBleed (CVE-2024-49112) and LDAPNightmare (CVE-2024-49113), two vulnerabilities (RCE and DoS) Microsoft patched in the Windows LDAP service last month.
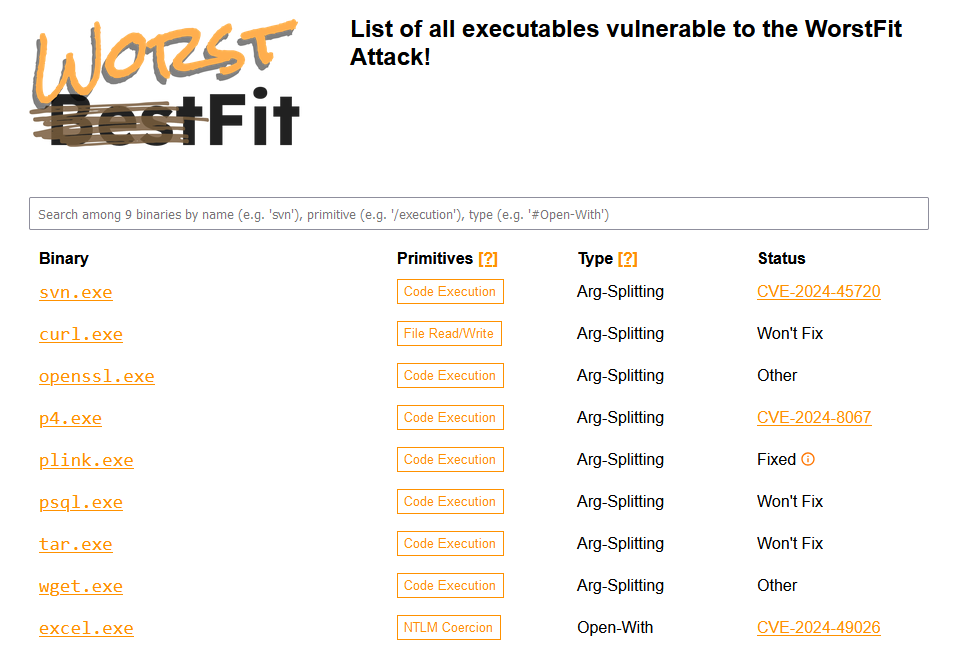
WorstFit: DEVCORE has published details on WorstFit, a new attack that abuses the Windows Best-Fit charset conversion feature for various types of attacks, such as path traversal, RCE, and argument injection.
Infosec industry
RIP Amit Yoran: Tenable CEO Amit Yoran has passed away after a fight with cancer. His obituary is here.
Marc Rogers accident: Defcon head of security Marc Rogers, aka cjunkie, has suffered a spinal cord injury in a car accident. A GoFundMe page has been set up to help the family with medical expenses.
Acquisition news: UK threat intel firm Darktrace is acquiring Cado Security, a US-based cloud IR service provider.
New tool—MLOKit: IBM's X-Force Red security team has released MLOKit, a toolkit that can be used to attack machine learning operations (MLOps) platforms by taking advantage of available REST APIs.
New tool—DOMspy: Dreadnode security researcher Ads Dawson has released DOMspy, a Chrome DevTools extension for DOM security research and analysis.
New tool—CF-Hero: Security researcher Musa Şana has released CF-Hero, a reconnaissance tool to discover the real IP addresses of web applications protected by Cloudflare.
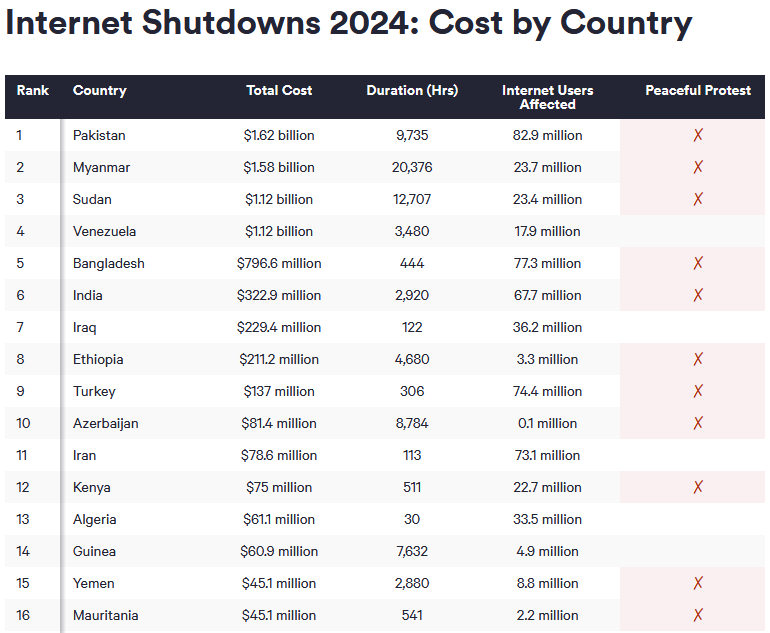
Threat/trend reports: Cyabra, Emsisoft, FalconFeeds, Netskope, Objective-See, Pinpoint Search Group, ScamSniffer, Top100VPN, and TRM Labs have published reports and summaries covering various infosec trends and industry threats.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about the evolution of Russian cyber operations during its invasion of Ukraine.
