Risky Bulletin Newsletter
August 15, 2025
Risky Bulletin: MadeYouReset vulnerability enables unlimited HTTP/2 DDoS attacks
Written by

News Editor
This newsletter is brought to you by Yubico. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
A new vulnerability in the HTTP/2 protocol can allow threat actors to launch nearly unlimited DDoS attacks to exhaust memory and crash servers.
The new attack is named MadeYouReset, was discovered by researchers at Deepness Lab, and is a variation of a previous attack known as HTTP/2 Rapid Reset.
The Rapid Reset attack was discovered in October 2023 after it was used to launch some of the largest DDoS attacks seen that year (Google, Amazon, and Cloudflare).
Both MadeYouReset and Rapid Reset target a design feature of the HTTP/2 protocol that allows a remote client (user) to connect to a server and open up to 100 connection streams to send and receive data.
Rapid Reset allowed the attacker to open 100 streams, cancel them fast, and then open 100 more before the server could process the cancellations, effectively bombarding the server with connections that exhaust its memory.
MadeYouReset works the same way, but bypasses Rapid Reset patches. Instead of telling the server it wants to cancel a connection, the attacker sends malformed packets to the server, and the server cancels the connections, while the attacker creates new ones—effectively reaching the same results as the old Rapid Reset attack, where the server exhausts its memory and CPU while dealing with a few malicious attackers.
This is basically the dumbed-down explanation, and the technical reports below go through the finer details of the attack.
Akamai says that, unlike Rapid Reset, fewer implementations of the HTTP/2 protocol are vulnerable this time around. For example, due to how it mitigated Rapid Reset, its implementation was not affected.
Fastly, Apache Tomcat, the H2O server, the Netty framework, the Vert.x toolkit, the Varnish cache system, and F5 devices have confirmed so far that they are affected. Others may soon follow in the coming days.
MadeYouReset received the CVE-2025-8671 identifier, but some vendors also issued their own CVEs.
The likelihood that MadeYouReset gets abused in the wild is 100%. The hacktivism scene saw a return to life after Russia's invasion of Ukraine, and DDoS attacks are now a way to annoy foreign adversaries again.
Risky Business Podcasts
The main Risky Business podcast is now on YouTube with video versions of our recent episodes. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
NPD returns: Data broker site National Public Data has returned online after a major leak last year. [Additional coverage in PCMag]
Allianz data leaks: ShinyHunters have leaked the data stolen from Allianz's Salesforce account. [Additional coverage in BleepingComputer]
Iran International doxes attacker: Iranian independent news outlet Iran International tracked down the spies who hacked its journalists last year. The outlet identified a 27-year-old from Tabriz as a member of the Handala Hack group, also known as Banished Kitten (Storm-0842, Dune). Iran International says Ali Bermoode ran the group's Telegram channel and operated under orders from Iran's intelligence agency, the MOIS.
Norway blames dam hack on Russia: Russian hackers took control of a Norwegian dam in April and opened its valves at full capacity. Norway's police say the case is still under investigation and have not named the group. Sources have told Risky Business that the attackers are one of the many pro-Kremlin hacktivist groups that have been active over the past three years. The group, named the Z-Alliance, allegedly took credit for the attack on their Telegram channel shortly after the intrusion. [Additional coverage in VG/English coverage in Politico Europe]
Speed cameras down across the Netherlands: Dozens of speed cameras are down across the Netherlands after a hack at the country's Public Prosecution Office. The cameras are offline after officials disconnected the agency's IT network from the internet last month. Some speed cameras are still online as they are connected to other networks. Dutch officials said that restoring the Public Prosecution Office's network would take weeks. [Additional coverage in NOS]
Italian hotel guest data for sale: A threat actor is selling ID scans from the guests of unnamed Italian hotels. A group calling itself MyDocs claims it obtained the data after hacking three hotels in June and July. MyDocs claims it stole more than 70,000 scanned passports and IDs. It leaked over 7,000 scans on Thursday, according to an Italian government CERT.

Canada investigates Parliament hack: Canadian authorities are investigating a security breach of the Parliament's House of Commons. Hackers exploited a recent Microsoft vulnerability to gain access to a central database. They allegedly stole non-public data on government employees and government-managed devices. The hack took place last Friday, according to an email obtained by the CBC. [h/t Brettmnx]
BtcTurk hacked again: Turkish cryptocurrency exchange BtcTurk has been hacked for $49 million. The company suspended operations on Thursday morning after the funds were taken from its hot wallets. This is the second time the platform has been hacked after it also lost $55 million in June last year. [Additional coverage in The Record]
Poland stops cyberattack on city's water supply: Polish officials say they blocked a cyberattack that aimed to cut water supply to one of its larger cities. Deputy Prime Minister Krzysztof Gawkowski declined to name the city for fear of creating panic. He also didn't name the attackers. [Additional coverage in Onet/English coverage in Reuters]
Colt cybersecurity incident: A cybersecurity incident is disrupting the operations of cloud service provider Colt. The incident has impacted the company's customer support portal and its Voice API platform. Both services have been down for at least three days. Colt says it's working with cyber experts to investigate the incident.
General tech and privacy
Linux ASI optimizations: Google says it cut down the performance overhead of the Linux kernel Address Space Isolation feature from 70% to just 13%.
Chrome incognito mode script blocking: Google is testing a new feature to block fingerprinting script blocking in Chrome's incognito mode.
Next Windows leak: Per Windows Latest, the next Windows OS version will be centered around AI and voice commands... so get acquainted with Linux, boys and girls!
Monero hashrate control: A company named Qubic claims it now controls the majority of the hashrate for the Monero cryptocurrency. Users are now worried the company may be able to execute a 51% attack to rewrite the Monero blockchain or censor transactions. The company called the takeover a proof of concept and experiment. [Additional coverage in CoinDesk] [h/t Koriolanis]
NIST IoT crypto finalized: The US National Institute of Standards and Technology (NIST) has finished work on the Ascon cryptographic standard. The standard contains four cryptographic algorithms designed to be used on low-memory IoT devices. The agency has been working on the standard since 2023. It can work with devices as small as RFID tags and implanted medical devices.
Government, politics, and policy
US puts tracking devices in chip shipments: US authorities are secretly placing tracking devices in chip shipments. The devices are meant to track shipments diverted to China and other US adversaries. The trackers will help identify and build cases against companies that violate sanctions. According to Reuters, trackers have been found in shipments of Dell and SuperMicro servers.
Data brokers in trouble: Following an investigation from The Markup, US Senator Maggie Hassan has asked data brokers to explain why they're hiding user opt-out pages from search engines. [Hassan letter PDF]
FCC wins telco lawsuit: The FCC won a lawsuit against telco industry groups that challenged its new data breach reporting requirements. [Additional coverage in Bloomberg Law]
US industry group urges cybersecurity deregulation: An industry lobbying group made up of US big tech orgs has urged the White House to scrap the incoming Cyber Incident Reporting for Critical Infrastructure Act (CIRCIA) and adopt AI for cybersecurity defense. This is very obviously terrible and would make CISA a bystander in the US government structure, but it's also in tune with the GOP's obsession with deregulation and the US tech market's obsession with AI these days. [Additional coverage in CybersecurityDive]
UK deploys facial recognition vans: The UK government is deploying ten live facial recognition vans across the country. The vans are equipped with cameras that scan the faces of people walking by. They will be deployed on special investigations to scan crowds and help catch wanted suspects.
Russia blocks WhatsApp and Telegram calls: Russia's internet watchdog has started restricting voice and video calls on WhatsApp and Telegram. Roskomnadzor said the two messengers were used to commit fraud and organize terrorist activities. Forbes Russia reported on Monday that Russia's four largest telcos allegedly petitioned the government for the ban. They argued that a ban would return traffic to the phone networks and increase their revenue. The ban also comes as the Russian government is pushing users to its national instant messenger, an app called Max. [Additional coverage in the Associated Press]
Kremlin orders Telegram exodus: The Kremlin has ordered government officials to move their Telegram channels to the country's domestic messaging app Max. Officials will be allowed to have accounts on other platforms, but the Max channels are now mandatory. The official Max accounts are expected to go live in the coming weeks, when the Max app is expected to come out of beta and become broadly available to the public. [Additional coverage in The Moscow Times] [h/t S.L.]
Sponsor section
In this Risky Business sponsor interview, Tom Uren talks to Derek Hanson, Yubico's Field CTO, about making account recovery and onboarding for employees phishing-resistant. They also discuss the problems and opportunities of syncable passkeys.
Arrests, cybercrime, and threat intel
US sanctions Grinex exchange: The US Treasury Department has sanctioned Russian cryptocurrency exchange Grinex. The platform launched days after the FBI seized the Garantex platform in March. The US Treasury says it saw Garantex funds move to Grinex wallets shortly after the takedown. The US previously sanctioned Garantex in 2022 for laundering illicit funds linked to hacks and ransomware. Sanctions were also imposed on three Garantex executives and six associated companies.
NY AG sues Zelle for enabling fraud: The state of New York has sued payments operator Zelle for enabling fraud. New York Attorney General Letitia James says scammers stole over $1 billion from Zelle users between 2017 and 2023. James claims Zelle prioritized attracting new users over basic anti-fraud safeguards. The platform allegedly ignored reports of fraud and refused to help or reimburse users. Zelle is owned and operated by a group of four American banks— JPMorgan Chase, Bank of America, Capital One, and Wells Fargo.
SMS blasters detained in Bangkok: Thai authorities have arrested two local men for sending fraudulent SMS messages. The two drove around Bangkok with an SMS blaster in the back of a Mazda car. The two were allegedly recruited on Telegram by a Chinese man who paid them $75/day. They were arrested last week after a local telco tracked down their device and alerted police. [Additional coverage in CommRisk]
VexTrio affiliate network: Infoblox looks at another part of the VexTrio TDS network, its affiliate advertising platform.
Fake law firm crypto-scams: The FBI warns that scammers are using fake law firms to contact victims of crypto-scams and revictimize them by claiming they can retrieve their stolen funds for a fee.
Criminals are selling access to police accounts: Abnormal AI looks at a flourishing underground economy of selling access to hacked government and law enforcement accounts. The accounts are either compromised through phishing or through infostealer infections.

Malware technical reports
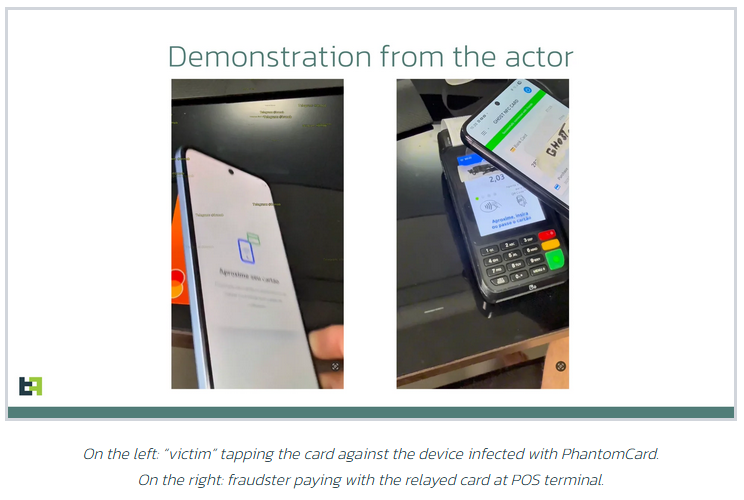
PhantomCard: A new Android trojan capable of intercepting and relaying NFC payment transactions has been spotted in Brazil. According to security firm ThreatFabric, the new PhantomCard trojan is based on a similar trojan active on the Chinese underground. The trojan's author is an individual who is known for taking foreign malware and porting it to the Brazilian ecosystem. The number of malware strains capable of intercepting and stealing NFC transactions has slowly grown over the past year. It has now been seen in Russia, China, Indonesia, and Czechia.
New LummaStealer variant: No newsletter edition without an infostealer report. Today is a new LummaStaler variant caught in the wild by CyFirma.
New FireWood variant: Intezer has spotted a new version of the FireWood Linux RAT.
New PS1Bot malware: Cisco Talos has discovered a new malvertising campaign that deploys the new PS1Bot malware framework. The malware has been active since the start of the year and comes with components for screen capture, keylogging, crypto-wallet dumping, infostealing, and persistence.
CrossC2: JPCERT/CC looks at CrossC2, an unofficial Beacon and builder compatible with Cobalt Strike that expands the framework to Linux and macOS hosts. The organization has seen the malware in attacks since at least September of last year. CrossC2 is open-source.
Kinsing: Russian security firm looks at the Kinsing crypto-miner botnet's activity in Russia.
Crypto24 ransomware: Trend Micro looks at Crypto24, a ransomware operation that launched in April.
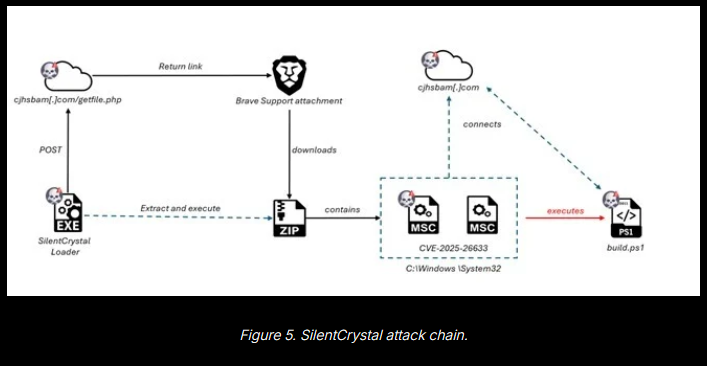
EncryptHub's SilentCrystal: Trustwave has spotted the EncryptHub threat actor using vishing to target cryptocurrency and web3 developers with malware. The final payload in some of these attacks was SilentCrystal, a loader that stores payloads on the Brave browser's tech support platform.
Sponsor section
In this sponsored interview, Patrick Gray talks to Yubico's COO and President, Jerrod Chong, about a new YubiKey feature: pre-registration. You can now ship pre-registered Yubikeys to your staff, so you don't need to rely on your staff to enrol them. They've achieved this with really slick Okta and Entra ID integrations.
APTs, cyber-espionage, and info-ops
Mustang Panda's ToneShell: Three security researchers have published a technical analysis of Mustang Panda's ToneShell backdoor, first spotted in April by Zscaler.
Vulnerabilities, security research, and bug bounty
N-able zero-days: Threat actors are exploiting two zero-days in the N-able N-central remote monitoring and management platform. CISA says the zero-days allow attackers to carry out insecure deserialization and command injection attacks against N-central servers. A patch was released on Wednesday. N-able says the zero-days impact only on-prem servers and require threat actors to authenticate first before an attack.
ScriptCase exposure: Hundreds of ScriptCase web apps are vulnerable to major vulnerabilities a month after patches were released. The two bugs allow attackers to reset passwords and inject malicious commands without needing to authenticate. According to VulnCheck, exploitation is simple and only requires a few curl commands.
FortMajeure vulnerability: Fortinet has patched a major security flaw in its FortiWeb firewalls. The vulnerability allows attackers to forge session cookies and bypass authentication on the device. The bug (CVE-2025-52970) was named FortMajeure and was discovered by security researcher Aviv Y.
Fortinet warns of exploit code: Fortinet has urged customers to patch their FortiSIEM devices. Customers were asked to apply a security update released on Tuesday that patches a command injection attack. Practical exploit code exists online, and exploitation is expected to follow. [See CVE-2025-25256]
Fortinet zero-day rumors: And while Fortinet is patching all those bugs, there are reports that a threat actor is advertising a Fortinet zero-day on hacking forums. Unclear how credible these are.
Xerox FreeFlow Core unauth vulnerabilities: Xerox has released security updates for the FreeFlow Core print orchestration platform. The update patches two vulnerabilities that can allow unauthenticated attackers to run malicious code on the platform. Security firm Horizon3 has released a technical write-up and proof-of-concept for both vulnerabilities.
Zero-click NTLM credential leak: Cymulate researchers have published a write-up of CVE-2025-50154, a zero-click NTLM credential leak they found in Windows. The bug was patched in this month's Patch Tuesday.
RoboDuck AIxCC bugs: South Korean security firm Theori has published a review of all the bugs its RoboDuck AI vulnerability scanner found during DARPA's two-year AIxCC contest. The bugs are in SQLite, NGINX, FreeRDP, Apache Tomcat, and Apache Tika.
"During an AIxCC practice round, we were given a version of SQLite with a harness that allowed running arbitrary SQL queries. There were some injected bugs by the organizers that we identified, but what was more interesting for us were the bugs the organizers did NOT inject. Our LLM agents actually found lots of unintended ways to crash this, though most of them were not security critical."
NAA abuse: SpecterOps has researched several ways to abuse Microsoft's new nested app authentication (NAA) system to move laterally inside cloud environments. NAA allows users logged into one app to pivot to other Microsoft apps without authenticating again.
"Nested app authentication can open more opportunities for resource access by using the brokering process Microsoft implemented. Internally, we have been referring to this as brokered client IDs or BroCI since it works similarly to FOCI. With work on tooling by other researchers, this method is ready to use in a variety of applications."
Cisco security updates: Cisco has released 21 security advisories for its firewall products. One of them is a CVSS 10/10 remote code execution in the RADIUS subsystem implementation of Cisco Secure Firewall Management Center (FMC) Software.
GitLab security updates: GitLab has released security updates to patch 12 vulnerabilities in its main product.
Matrix security update: The Matrix Foundation has released a security update for the Matrix messaging protocol, widely used for many government communication platforms across the globe. [Additional coverage in The Record]
I could be wrong, but if I remember correctly, Ukraine's DELTA system still relies or has relied on Matrix for their encrypted chat platform. I wonder if the Matrix Foundation warned the UKR Ministry of Defense and Armed Forces as well. https://t.co/KuVVofuacE
— Stefan Soesanto (@iiyonite) August 13, 2025
Infosec industry
Threat/trend reports: Abnormal AI, the Australian Institute of Criminology, Kaspersky, and Proofpoint have recently published reports and summaries covering various infosec trends and industry threats.
BeyondTrust rumors: Bloomberg is reporting that private equity firm Francisco Partners is exploring a sale of cybersecurity firm BeyondTrust.
New Trellix CISO: Security firm Trellix has hired Michael K. Green as its new CISO. He previously served as interim CISO and CTO for CxOCyber.
New tool—OT Asset Inventory Guidance: CISA, the FBI, the NSA, and others released guidance to help critical infrastructure operators create inventories for their complex OT networks.
"This guidance outlines the process to create an OT asset inventory, develop a taxonomy of OT systems, and create a modern defensible architecture by providing net defenders with digestible foundational elements and best practices."
New tool—NCSC Citrix scripts: The Dutch cybersecurity agency has released three scripts for checking Citrix NetScaler appliances for common signs of compromise. The scripts check core dumps, disk images, and the app's Bash history.
New tool—ATEAM: Security firm NetSPI has released ATEAM, a Python reconnaissance tool designed to discover Azure services and tenant ownership information based on their responses.
New tool—Kurasagi: A security researcher named Wane has released a PatchGuard bypass for Windows 11 24H2. It's called Kurasagi and available on GitHub.
New tool—Rubberduck: Zipstack has released Rubberduck, a local LLM caching reverse proxy server designed to emulate major LLM providers for advanced testing scenarios.
Tool update—Hashcat 7.0.0: The Hashcat project has released version 7.0.0 of its password cracking tool.
FIRSTCON25 videos: Talks from the FIRSTCON 2025 security conference, which took place in June, are available on YouTube.
VULNCON25 videos: Talks from the VULNCON 2025 security conference, which took place in April, are available on YouTube.
Risky Business podcasts
In this edition of Seriously Risky Business, Tom Uren and Amberleigh Jack talk about a recent hack of the US Courts' document management system.
