Risky Bulletin Newsletter
May 12, 2025
Risky Bulletin: Kaleidoscope ad fraud network infects 2.5mil new devices each month
Written by

News Editor
This newsletter is brought to you by Corelight. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
Security researchers have discovered a new ad fraud operation named Kaleidoscope that uses the "evil twin app" technique to disguise the origin of its ad impressions.
The botnet consists of clean apps uploaded to the official Play Store and doppelgangers distributed through third-party stores.
These clones are the heart of the botnet and are the ones that use a malicious advertising SDK to bombard users with unwanted and unskippable ads.
Both the legitimate apps and their rogue clones use the same advertising IDs as a way to disguise the origin of the ad impressions and generate revenue through behavior that isn't tolerated by the ad industry.
Researchers at Integral Ad Science (IAS) have linked the Kaleidoscope botnet to 130 app IDs, which are bringing in around 2.5 million installs every new month.
"Over 20% of these impacted users were located in India, with significant clusters observed in Indonesia, the Philippines, and Brazil. The infections primarily stemmed from malicious app installations via third-party app stores, likely driven by aggressive malvertising."
IAS researchers have traced many of the rogue ads shown through Kaleidoscope-infected apps to a Portuguese advertising company named Saturn Dynamic (saturndynamic.pt).
All of Kaleidoscope's wrongdoing works because of a malicious SDK that allows them to muddle up and share the app ID across multiple apps and then aggregate the app impressions.
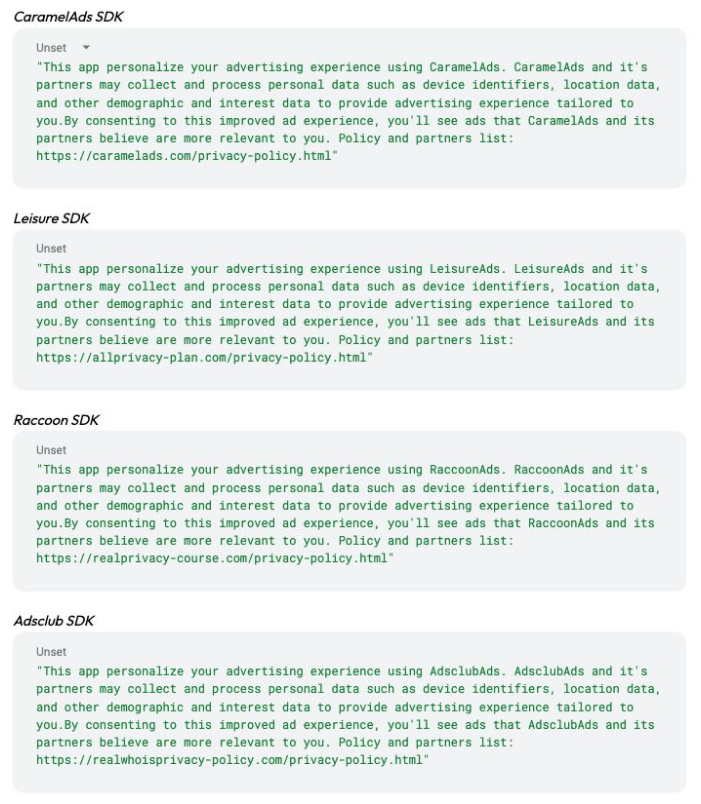
IAS researchers say Kaleidoscope apps have used three different SDKs to show these days, namely Leisure, Raccoon, and Adsclub.
Various clues in their code suggest these are modified versions of the older CaramelSDK, which was at the heart of the Konfety ad fraud operation, unmasked by HUMAN Security last July. It's still unclear if Kaleidoscope is just a new branch of the older Konfety operation trying to rebuild its business after Google took down its apps last year, but there are strong signs to suggest so.
Risky Business Podcasts
Risky Business is now on YouTube with video versions of our main podcasts. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
Japanese brokerage hacks go brrr: The hacking spree targeting Japanese brokerage accounts intensified last month. Hackers have continued breaking into accounts to manipulate stock prices using the account holder's assets. Japanese financial authorities say over 6,000 accounts have been hacked this year, and the amount of illegal trades is close to reaching $2 billion, up from $700 million reported three weeks ago.
Pearson security breach: Hackers have gained access and stolen data from the internal network of education platform Pearson. The incident took place earlier this month, and the company says the attacker stole mainly legacy data. This is the company's second security breach this year.
The DOGE that keeps on giving: Privacy activist Micah Lee has found hacked credentials belonging to DOGE employee Kyle Schutt in public leaks. The credentials originate from infostealer logs as recent as 2023, suggesting Schutt may have had his devices hacked as recently as two years ago.
iClicker ClickFix hack: A threat actor has hacked the iClicker student engagement platform and added a fake CAPTCHA to university portals across the US. The CAPTCHA instructed visitors to copy and paste malicious commands in their Windows terminals. Also known as a ClickFix attack, the commands downloaded and installed malware on user PCs. The malicious CAPTCHA was live on all iClicker portals for five days between April 12 and 16. Among the incident's most known victims is the prestigious University of Michigan.
General tech and privacy
Google settles Texas privacy lawsuit: Google will pay a $1.375 billion fine to the US state of Texas for tracking users' geolocation, incognito searches, and collecting biometric data. The fine will settle two lawsuits filed by Texas in 2022. Texas also secured a $1.4 billion settlement from Meta last year after the company collected facial scans from users without their permission.
And yet people complain about EU regulations 🙃
— Ray Minehane (@rayminehane.bsky.social) 2025-05-09T23:36:56.699Z
Wikipedia sues the UK government: The Wikimedia Foundation has filed a lawsuit against the UK government over its implementation of the Online Safety Act. The new UK law enters into effect next year and will require Wikimedia to verify the identity of Wikipedia users. The Foundation says the new law puts the privacy of its users in danger, with some users relying on anonymity as they operate from hostile governments. The new law would decimate its staff and open the door for content manipulation and vandalism.
Bluetooth 6.1 adds privacy feature: SIG has released version 6.1 of the Bluetooth protocol, which now includes a new privacy feature that will randomize the time a device changes its Bluetooth address changes to prevent advanced tracking technologies.
New Firefox privacy prompts: Mozilla is testing a new extension installation consent prompt to improve the descriptions of what data extensions are accessing.
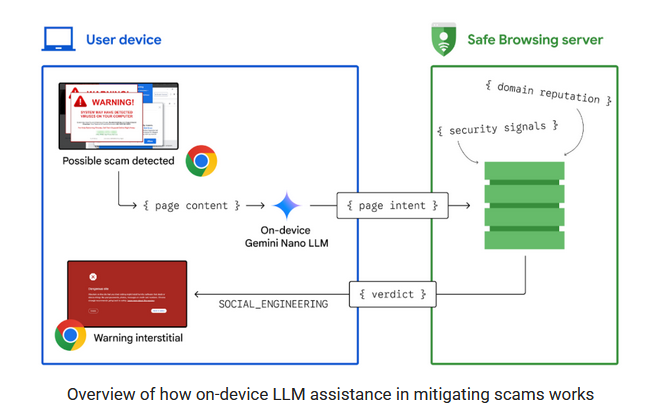
Chrome to use AI against tech scams: Google will use on-device LLMs to detect potential tech support scams and alert Chrome users to possible dangers. The company says on-device LLMs will help it detect these sites faster, most of which take hours to be indexed by the Safe Browsing API. The new feature is scheduled to arrive with Chrome 137 later this month.
Government, politics, and policy
US seeks to ban DeepSeek for contractors: Two US senators have introduced a bill that would ban government contractors from using AI tools developed by Chinese company DeepSeek for any government-related work. US lawmakers say DeepSeek poses a national security threat because Chinese companies are mandated to share all their data with the Chinese government. Similar legislation introduced in February also seeks to ban the use of DeepSeek by US government workers. Several US states have banned employees from using DeepSeek already.
US bill to aid victims of identity theft: A group of ten US senators has introduced a bill to create a single point of contact for identity theft victims. The bill aims to address a situation at the US Social Security Administration where victims are often asked to call multiple numbers to report a crime. If passed, the Social Security Administration would have to create a single point of contact for reporting identity thefts and the theft of their Social Security numbers.
Florida encryption backdoor law fails: The Florida state legislature has not passed a bill that would have required online companies to backdoor their encryption. The US government pressuring the UK not to pass its own encryption backdoor law made this whole thing stink of hypocrisy, to be honest. [Additional coverage in TechCrunch]
India bans Pakistani content: The Indian government has ordered online platforms to remove any kind of Pakistani content inside India. [Additional coverage in the Times of India/ Original government order PDF]
Sponsor section
In this Risky Bulletin sponsor interview James Pope, Director of Technical Enablement, talks to Tom Uren about his experience running networks and security centres at Black Hat conferences around the world. Pope talks about the challenges of running a SOC at a hacker conference, how conference networks around the world have a different character and talks about all the weird and wonderful security snafus he has found.
Arrests, cybercrime, and threat intel
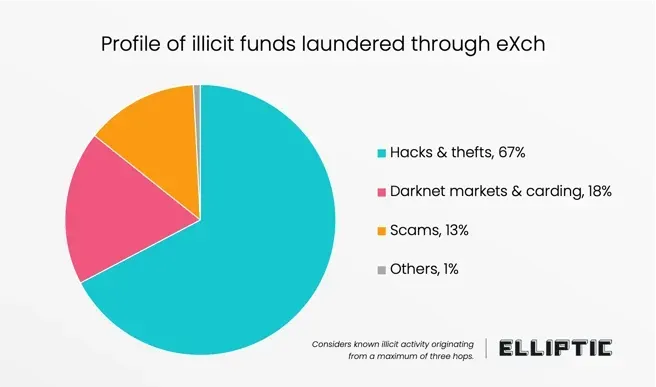
Germany seizes eXch mixer: German authorities have seized the servers of the eXch cryptocurrency mixing service. According to blockchain investigations firm Elliptic, 98% of funds that passed through the service were linked to criminal activity. German police rushed to seize the service, fearing it would lose evidence after eXch admins announced they would shut down. Officials say they now seized 8TB of data and €34 million worth of assets.
Ransomware suspected detained in Moldova: Moldovan authorities arrested a man last week suspected of being involved in ransomware attacks against Dutch companies back in 2021. [Post-publication edit: This turned out to be a DoppelPaymer affiliate.]
Ransomware/malware seller sentenced in Ireland: Irish authorities have sentenced a 43-year-old man to two years in prison on cybercrime-related charges. Suleman Mazhar ran a website that sold malware, ransomware, and fake bank and credit card data. Officials arrested Mazhar in 2022 with the help of the FBI. He also pleaded guilty to money laundering charges. [Additional coverage in RTE]
Philippines raids online scam center: Philippines authorities have raided an online scam center in Makati City and detained 31 individuals. All the suspects are foreigners and most are Chinese nationals. Officials said they were acting on a presidential directive to crack down on international cybercrime syndicates that have begun moving and setting up bases in the country.
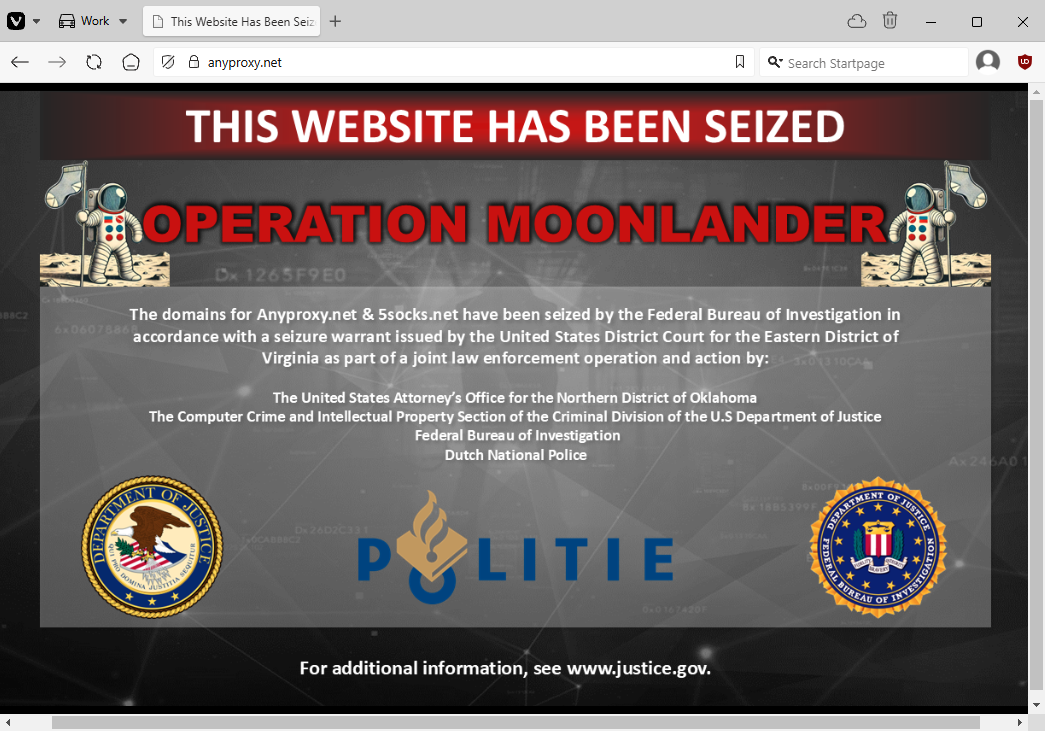
US dismantles Anyproxy botnet: The FBI has seized the server and domain infrastructure of the Anyproxy botnet. Authorities also filed charges against three Russians and a Kazakh national for allegedly running the botnet. The four allegedly hacked home routers and used them as the backbone of online portals that rented access to residential proxy servers. The four launched their business over two decades ago and are believed to have more than $46 million from renting access to hacked devices. According to Lumen's Black Lotus Labs, the botnet wasn't that large but maintained a daily population of over 7,000 proxies.
NATO cyber chief confirms Russian state-cybercrime connections: For years, there have been rumors that the Kremlin was protecting its cybercrime crews from Western repercussions. In an interview with ERR, Mart Noorma, director of the NATO Cooperative Cyber Defense Center of Excellence (CCDCOE), confirms that this is true and is happening, with some of the cybercrime proceeds being "divided among state agencies."
ATG exposure: More than 8,000 automated tank gauge (ATG) systems are exposed on the internet without proper authentication mechanisms. Most of the exposed systems are from Veeder-Root, a major supplier of gas and fuel dispensers in the US. Security firm DIVD says it notified vendors and is working to advise on proper security controls.
New npm malware: Ninety-four malicious npm packages were discovered and taken down last week. Check out the GitHub security advisory portal for more details.
New Conti leaks: A new Twitter account is leaking what they claim are videos of Conti ransomware gang members and loads more. I don't know if this is real, but it sure is entertaining. I'm gonna leave confirming this to the threat intel analysts and law enforcement people in my sub list whose job this is.
Malware technical reports
BrazilMob: There's a new Android banking trojan targeting Brazilian audiences, aptly named BrazilMob.
Noodlophile Stealer: Morphisec researchers have discovered a new infostealer named Noodlophile that is currently being distributed via boobytrapped genAI apps.
Lumma Stealer: Sophos has published a report on a recent ClickFix campaign spreading the annoying Lumma Stealer.
Sponsor section
The Corelight team has put together a guide [PDF] on how SOC teams could hunt and protect their networks against Volt Typhoon, a Chinese APT targeting critical infrastructure.

APTs, cyber-espionage, and info-ops
SideCopy activity: In the backdrop of a new military conflict between India and Pakistan, security researchers are reporting a flurry of activity from Pakistani APT group SideCopy.
Gamaredon's PteroLNK: Harfang Labs has published a report on PteroLNK, a VBScript malware strain, and its supporting infrastructure.
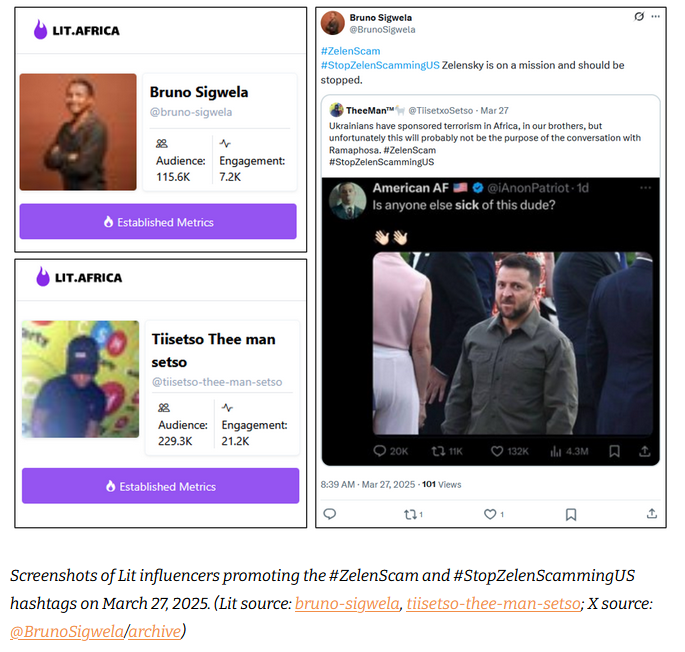
Info-op targets Zelenskyy: DFRLab has published a report on an influence operation that used South African influencers-for-hire to attack Ukrainian President Volodymyr Zelenskyy for refusing to accept Russia's terms. We covered the growing problem of "influencers" selling their "opinions" as a national security problem last December.
Vulnerabilities, security research, and bug bounty
Unitree removes Go1 robot backdoor: Chinese robot maker Unitree has removed a problematic component from the firmware of its Go1 robot dog that could have allowed remote attackers to take over the robot. [Additional coverage in SCMP]
Libexpat security update: A security update is available for the Libexpat XML parsing library to fix a memory stack overflow bug.
RCE in ASUS preinstalled software: A software engineer from New Zealand has found a one-click RCE vulnerability in ASUS DriverHub, a piece of software preinstalled on all ASUS gear.
Infosec industry
Threat/trend reports: APWG [PDF], Check Point, CyFirma, EDPS [PDF], Logicalis, and NewsGuard have recently published reports and summaries covering various infosec trends and industry threats.
New tool—Qtap: Security firm Qpoint has released Qtap, an eBPF agent that captures pre-encrypted traffic flowing through the Linux kernel.
New tool—Lodestar Forge: Kroll security engineer Jamie Pegg has released Lodestar Forge, a platform for deploying red team infrastructure.
CYBERUK 2025 streams: Live streams from the CYBERUK 2025 security conference, which took place last week in Manchester, are available on YouTube.
CactusCon 13 videos: Talks from the CactusCon 13 security conference, which took place in mid-February, are available on YouTube.
Risky Business podcasts
Tom Uren and Patrick Gray talk about how the US is planning to take the gloves off in cyberspace and conduct much more aggressive offensive cyber operations. US responses to cyber espionage have not been very aggressive to date, but Tom is not convinced that cyber punches are required, so much as blows that really hurt.
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about an in-depth report on a Ukrainian hacking control panel. The panel shows how the Ukrainian group thinks about hacking operations, and the pair discuss why the report exists and what it achieves.
