Risky Bulletin Newsletter
April 09, 2025
Risky Bulletin: Hackers leak data from major bulletproof hosting provider
Written by

News Editor
You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
An unnamed hacker (or maybe a hacker group, who knows) has leaked internal data from Media Land, one of today's largest bulletproof web hosting providers.
The leaked files contain information on the company's past customers, what type of services they contracted, and what was hosted on the platform.
Threat intel firm Prodaft believes the attacker is the same threat actor that hacked and leaked internal chats from the BlackBasta ransomware group in mid-February.
At the time of writing, it's still unclear if the hacker gained access to Media Land via the compromised BlackBasta servers or the other way around.
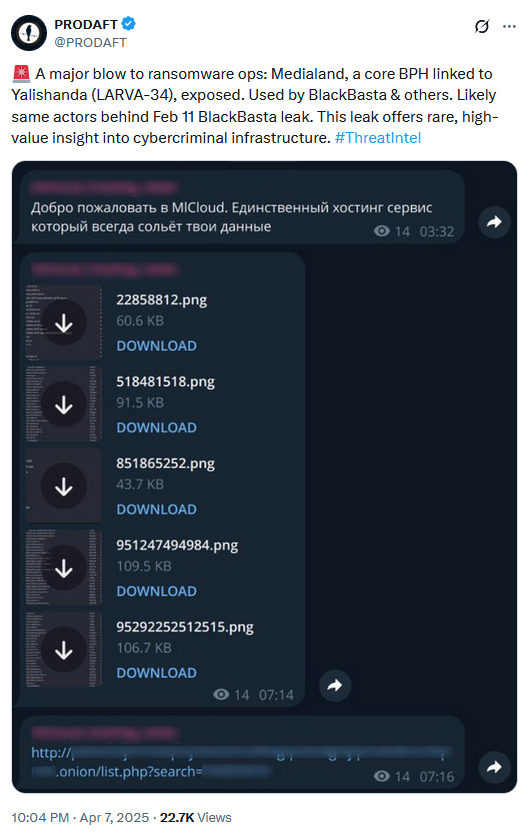
The leak contains files as recent as February this year and confirms that Media Land hosted malware command and control servers, ransomware infrastructure and data leak sites, phishing kits and data exfil servers, and malicious code-signing systems.
Prodaft says the leaked data is a gold mine for threat intelligence professionals. The leaked files will likely aid security researchers conduct extremely accurate investigations and connect the dots between many cybercrime operations.
The data contains records of who bought servers, who paid, with what money, and in some cases, it might even contain the rare personally identifiable information that researchers covet in order to deanonymize cybercrime operators.
The files will also allow researchers to correlate past IOCs to specific threat actors, cluster campaigns together, and help improve threat actor attribution efforts.
Yalishanda, the service's public face and suspected main admin, confirmed in a post on an underground hacking forum that Media Land was dealing with a technical issue.
Media Land (also spelled Medialand) is a Russia-registered company that has been active for more than a decade.
Risky Business Podcasts
Risky Business is now on YouTube with video versions of our main podcasts. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
US Treasury OCC hack: Unknown hackers breached the email systems of the US Treasury's Office of the Comptroller of the Currency (OCC) and intercepted emails for almost 100 of its staff. The breach took place in June 2023 and lasted until CISA discovered it in January this year. The OCC is the third Treasury office to disclose a breach over the past months after the Office of Foreign Assets Control (OFAC) and the Committee on Foreign Investment in the US (CFIUS). The US government blamed Chinese hacking group Silk Typhoon for the first two hacks. [Additional coverage in Bloomberg]
Ransomware (indirectly) hits two banks via their printing vendor: Two Singapore banks have confirmed that a ransomware gang stole the data of some of their customers after an attack on a shared printing service provider. The incident impacted DBS Bank and the Bank of China's Singapore branch. The two banks used the printing service to previously print and send out customer letters. [Additional coverage in The Straight Times]
Czech PM Twitter hack: Hackers have gained access to the Twitter account of Czech PM Petr Fiala and posted messages that Russian forces had attacked the country and that the government was preparing counter-tariffs on the US. The hacker didn't say anything about Slovakia. Everyone in Slovakia is feeling left out and sadge. </s> [Additional coverage in Expats.cz]
Oracle breach notification: Oracle has finally published a statement about a recent breach at their cloud division but they're being little c**ts about the wording.
Oracle have finally issued to a written notification to customers about their cybersecurity incident. They are again wordsmithing. OCI is a different org unit in Oracle to Oracle Classic - they’re denying a different scope.
— Kevin Beaumont (@doublepulsar.com) 2025-04-08T11:50:41.665Z
General tech and privacy
Apple appeals UK IPT order: Apple has filed an appeal against a UK government order to create a backdoor in its cloud encryption to help law enforcement investigations. [Additional coverage in AppleInsider]
OpenAI tests image watermark: OpenAI is testing adding a watermark to all images produced by its genAI image generation tools. [Additional coverage in Digital Trends]
Firefox add-on permissions: Mozilla will redesign this year the consent UI used to grant Firefox add-ons access to permissions and user data. No actual details, but Mozilla says the new system will involve less programming and work from the add-on developers.
Thundermail: Mozilla has published official details about its webmail Thundermail service. The service will be modeled after Gmail, with a calendar system, an encrypted file-sharing app, and an AI assistant. The service is also open for beta signups.
Meta expands teen account protections: Meta is expanding its "teen accounts" security protections from Instagram to Facebook and Facebook Messenger accounts. The feature prevents children under the age of 16 from modifying a series of privacy settings on their accounts without a parent's approval. This includes settings related to who can contact the account and what content they see on the site. Meta is also expanding these restrictions, and teens won't be able to live-stream on their sites without a parent's approval.
Government, politics, and policy
DOGE starts spying on US government workers: Elon Musk's DOGE team has deployed an AI tool to surveil the internal communications of at least one government agency. According to Reuters, the tool is designed to monitor chats for disloyalty and negative comments about Donald Trump and Elon Musk. The DOGE team is also allegedly using Signal to communicate, in violation of federal record-keeping laws.
Russia may ban 12 foreign hosting providers: The Russian government may block 12 foreign web hosting providers for failing to register in the country and abide by its laws. The country's internet watchdog says companies must also integrate with its anti-DDoS system and participate in exercises to help strengthen Russia's internet segment. The Roskomnadzor has been threatening foreign web and cloud providers to abide by the rules or face a ban since Russia's invasion of Ukraine. The agency ran a test last month to test if it could block access to Cloudflare infrastructure. [Additional coverage in TASS]
21 countries sign Pall Mall Process: Twenty-one countries have signed the Pall Mall Process, an international agreement to combat the proliferation and irresponsible use of commercial spyware. Major hubs of spyware sales, such as the US, Israel, and Macedonia, did not participate. This is the second agreement of its kind after a similar one signed by 23 countries under the Biden administration in 2023. [Additional coverage in CyberScoop]
Cyber Governance Code of Practice: The UK's cybersecurity agency has published a guide for boards and directors on how to manage digital risks and protect their businesses from cyberattacks.
EU unveils ProtectEU plan: The European Commission has unveiled ProtectEU, a new EU strategy for improving the bloc's overall security practices—across border, physical, and cyber security fields.
This "component" is how the Commission will integrate cyber: as a whole-of-society approach rather than as a dedicated digital policy thingy
— Rayna ¯\_(ツ)_/¯🤓🇪🇺👩💻📚✍️ (@maliciarogue.bsky.social) 2025-04-08T12:41:26.198Z
Highlights from the cyber/CNI/supply chain bits of the EU's new internal security strategy: - Brussels helping members identify entities covered by CER and NIS2. (Wasn't already happening?)
— Ravi Nayyar (@ravirockks.bsky.social) 2025-04-05T05:00:01.266Z
Risky Business podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq look at the idea of 'false scarcities' in cyber security. Are bugs and talent rare? Or is our thinking blinkered?
Arrests, cybercrime, and threat intel
Australia deregisters 95 companies linked to cyber scams: Australia's financial regulator has pulled the licenses of 95 companies with suspected links to online investment and romance scams. Many of the companies were associated with apps and websites used during the scamming process. ASIC says the companies were designed to provide a "veneer of credibility" for the apps and websites.
Spain arrests investment scammers: Spain's National Police arrested the members of a criminal group who allegedly stole over €19 million via cryptocurrency investment scams. Six suspects were detained across Spain, including the gang's leader, a female who was preparing to leave the country for Dubai. The group allegedly used AI tools to create deepfake ads of Spanish celebrities that lured victims to fake investment portals.
UK convicts romance scammers: The UK government has convicted five suspects of romance scams and money laundering offenses. Officials say the group stole and laundered over £3.25 million from almost 100 victims.
VS Code extensions spread crypto-miners: Security researchers have spotted ten VSCode extensions available through the official store that deployed crypto-miners on users' PCs. The extensions were published through three accounts and accumulated over one million installs. Security firm ExtensionTotal says the install numbers were artificially inflated over a short period of time in an attempt to establish credibility.
TVT DVR exploitation wave: Security firm GreyNoise has detected a spike in exploitation targeting TVT-branded DVRs. The company has linked the activity to a Mirai botnet cluster.
Biometrics abuse: Europol has published a report looking at all the ways criminal groups could abuse biometric systems.

Everest RaaS website defaced: An anonymous hacker has defaced the website of the Everest ransomware gang with the text "Don't do crime CRIME IS BAD xoxo from Prague." [Additional coverage in TechCrunch]
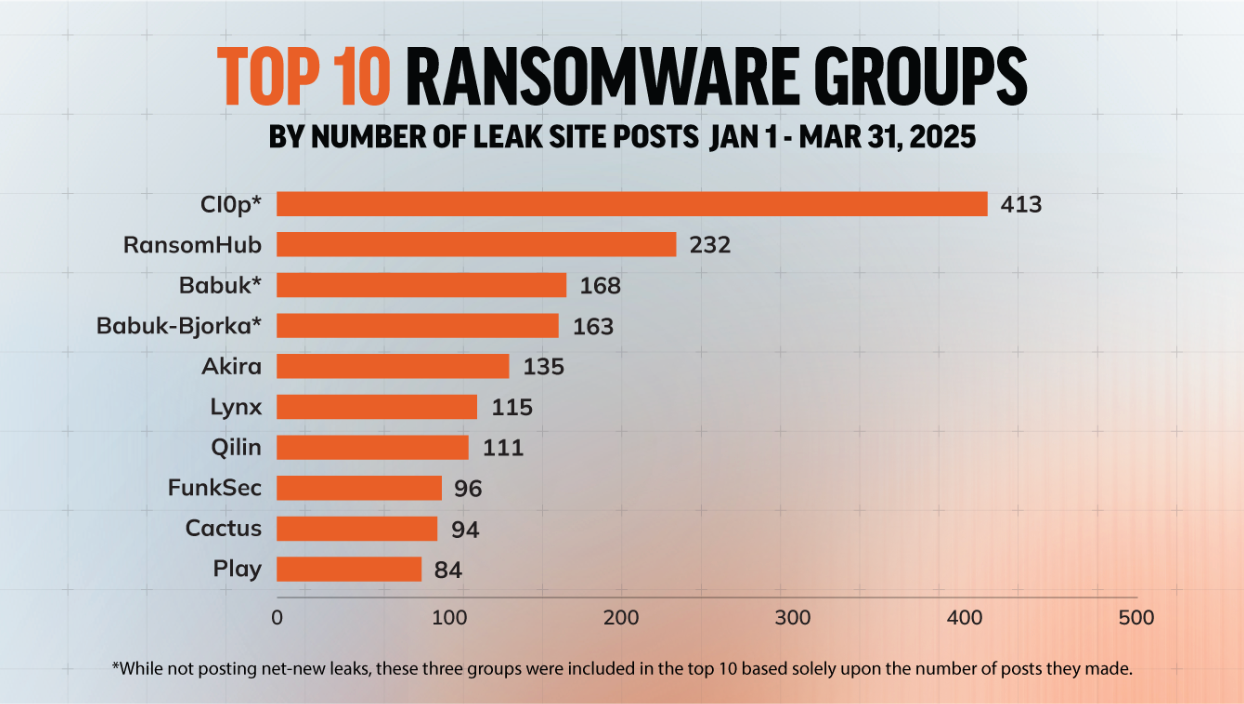
RansomHub loses affiliates: After it had its dark web leak site hacked by rival group DragonForce, GuidePoint researchers are reporting that the RansomHub gang is starting to lose affiliates to other groups.
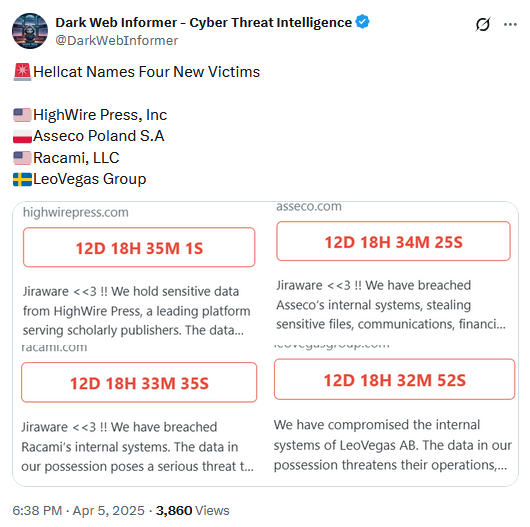
Hellcat's Jira hacking spree: The Hellcat hacking group is using Jira credentials collected via infostealer malware to breach major companies across the world. The group acquires the credentials from underground shops, accesses corporate networks, steals sensitive data, and then extorts the companies. Hellcat's hacking spree has been going on for over a month and has hit tens of companies. The most well-known victims include Telefonica, Orange, Schneider Electric, and Jaguar Land Rover.
Scattered Spider remnants still active: Despite recent law enforcement arrests, remnants of the loosely associated Scattered Spider group are still active and carrying out multiple spear-phishing operations targeting major companies.
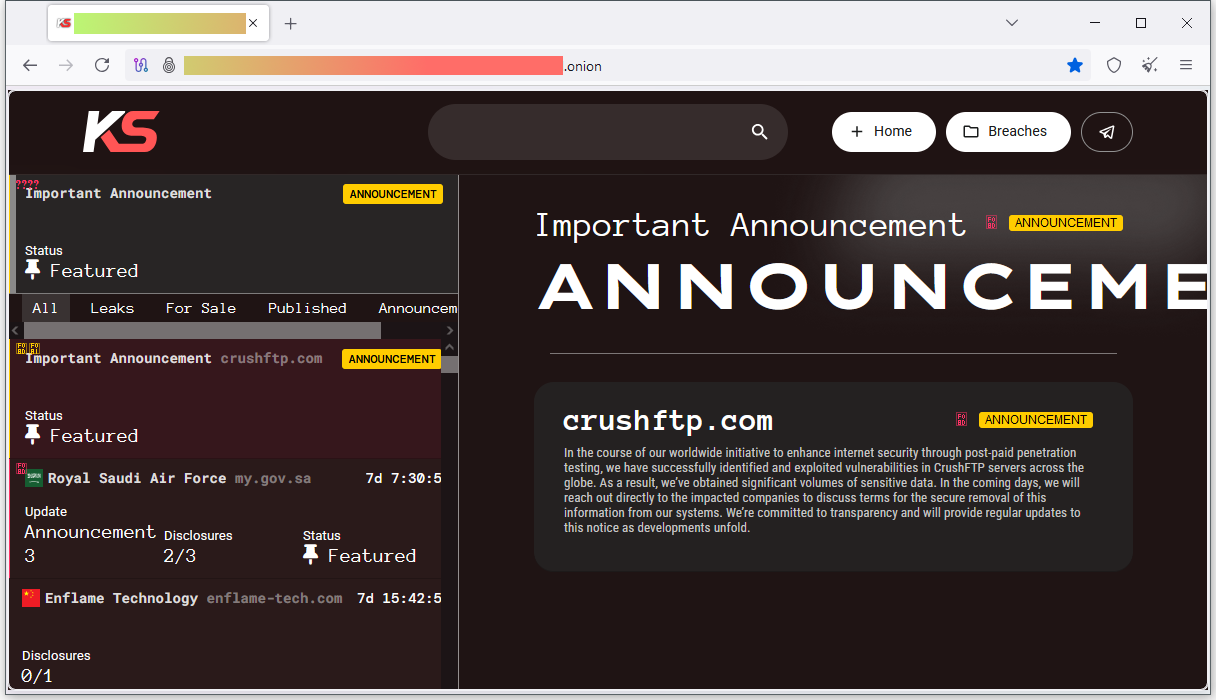
Kill Security takes credit for CrushFTP attacks: A threat actor named Kill Security has taken credit for exploiting a recent CrushFTP zero-day. The group claims it stole "significant volumes" of data and is now threatening to extort victims in the coming days. In the meantime, CrushFTP is dealing with some drama of its own after it worked to invalidate an initial CVE issued for the bug (CVE-2024-2825) just because it was requested by a security vendor. It has now issued a new one (CVE-2025-31161), issued by itself, which has now broken a lot of security tools meant to scan for the vulnerability.
"In the course of our worldwide initiative to enhance internet security through post-paid penetration testing, we have successfully identified and exploited vulnerabilities in CrushFTP servers across the globe. As a result, we've obtained significant volumes of sensitive data. In the coming days, we will reach out directly to the impacted companies to discuss terms for the secure removal of this information from our systems. We're committed to transparency and will provide regular updates to this notice as developments unfold."
Malware technical reports
Neptune RAT: CyFirma looks at Neptune RAT, a new .NET remote access trojan advertised via GitHub, Telegram, and YouTube.
"Neptune RAT incorporates advanced anti-analysis techniques and persistence methods to maintain its presence on the victim's system for extended periods and comes packed with dangerous features, including a crypto clipper, password stealer with capabilities to exfiltrate over 270+ different applications' credentials, ransomware capabilities, and live desktop monitoring, making it an extremely serious threat."
Vidar Stealer: G DATA has published a technical deep dive of Vidar Stealer's latest version.
Cryptominers on SourceForge: Kaspersky has spotted a malicious app on SourceForge infecting users with a cryptominer.
CrazyHunter ransomware: TeamT5 published a technical analysis of the CrazyHunter ransomware attacks on Taiwanese hospitals in February and March this year.
Risky Business Podcasts
Tom Uren and Patrick Gray discuss how North Korean IT worker scam is shifting towards Europe and employing tactics that make it more dangerous.
APTs, cyber-espionage, and info-ops
Chinese info-op targeting Canadian elections: A Chinese info-op is trying to influence the political views of Chinese communities in Canada ahead of the country's upcoming federal election. The campaign is taking place on WeChat, an app used by Canadian-Chinese citizens to keep in contact with family members at home. The info-op is attacking Mark Carney, the prime minister candidate for Canada's Liberal Party. Canada's election task force has linked the campaign to the Chinese Communist Party's Central Political and Legal Affairs Commission (CPLAC).
UAC-0226: A new cyber-espionage group is targeting Ukrainian government, military, and law enforcement organizations located along the country's border with Russia. The attacks began in February and involved phishing lures related to Russia's invasion, such as UAV production, demining operations, and compensation for destroyed property. Victims were infected with GIFTEDCROOK, an infostealer meant to gather data from their systems.
UNC5837: Google Cloud looks at a recent operation from a Russia-linked APT named UNC5837 that targets victims with rogue RDP config files. These configs allow the group to connect to victim systems via hidden RDP connections and rummage through and steal their data. The technique is named Rogue RDP and is a known TTP of Russian APTs.
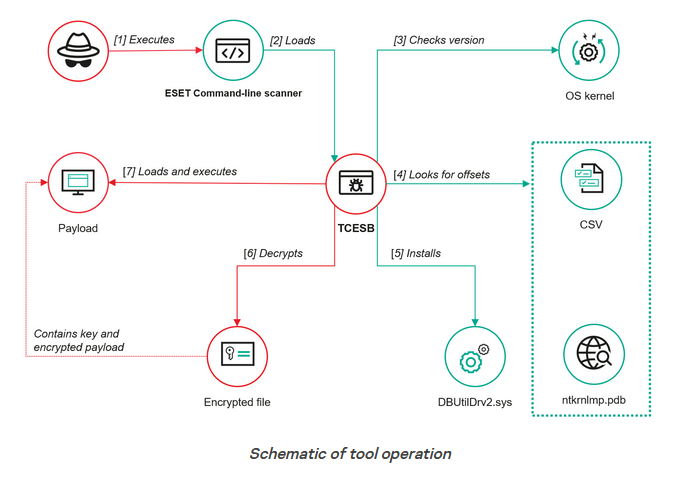
ToddyCat abuses ESET CLI scanner: The ToddyCat cyber-espionage group has abused an ESET security tool to gain admin privileges on compromised hosts. ESET released a security update last week to fix the issue exploited in its TCESB command-line interface scanner. The technique fits the pattern of a BYOVD attack, which many APT groups are now adopting.
Vulnerabilities, security research, and bug bounty
Patch Tuesday: Yesterday was the February 2025 Patch Tuesday. We had security updates from Adobe, Microsoft, SAP, Ivanti, Fortinet, VMware, AMD, Arm, Schneider Electric, Siemens, and Elastic. The Android Project, Apple, Cisco, Chrome, Firefox, Splunk, Moxa, Synology, Zoom, Veeam, WinRAR, Apache Parquet, Jenkins, and Drupal.
Microsoft Patch Tuesday: This month, Microsoft patched 126 vulnerabilities, including an actively exploited zero-day—tracked as CVE-2025-29824, an EoP in the Windows Common Log File System driver. According to Microsoft's security team, the zero-day was exploited by the RansomEXX ransomware group.
Android patches zero-day: Google has patched two zero-days in this month's Android Security Bulletin. One of the fixes is a patch for a Cellebrite exploit used by Serbian authorities to unlock the phones of journalists and anti-government protesters. The exploit and the hacks were first detailed in an Amnesty International report in February. There are no details on the second zero-day, which impacts the Android kernel USB-audio driver code. This is the third month in a row that Google fixes zero-days in the Android OS.
WhatsApp security update: Meta has rolled out a security patch for WhatsApp to fix a spoofing bug that showed received files with an incorrect file type. Meta says the bug could have been abused to trick users into executing malicious code on their devices. The issue—tracked as CVE-2025-30401—affected its Windows desktop app.
Vasion vulnerabilities: Security researcher Pierre "Kim" Barre has found 83 vulnerabilities in Vasion's cloud printing clients and SaaS platform. The research spans vulnerabilities discovered as far back as 2021.
Bugcrowd enforces MFA: Bug bounty platform Bugcrowd is enforcing mandatory multi-factor authentication for all user accounts. Users without an MFA method will receive a password reset request this week that will also force them to enable an MFA method.
SmartScreen explainer: Microsoft security engineer Eric Lawrence has published an explainer on how the Windows SmartScreen technology works.
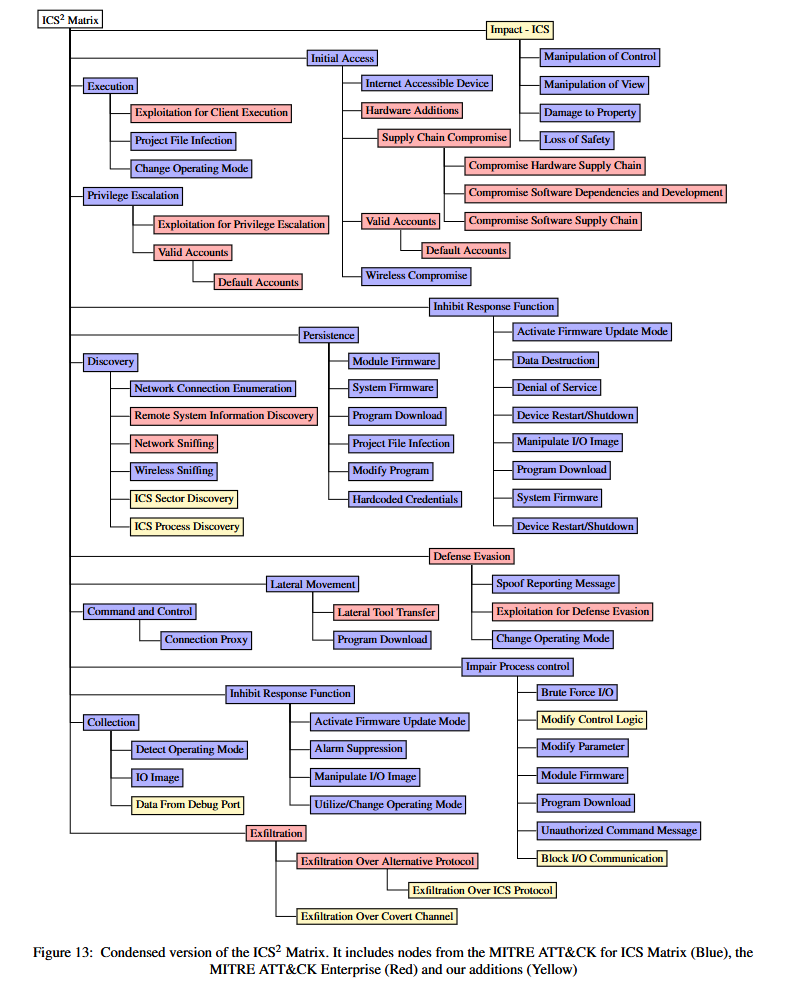
PLC attack surface research: A team of academics has conducted a review of 133 papers, 119 attack methods, and 70 defense methods that target PLCs to assess the actual impact of a possible cyberattack targeting these devices. The research found that even if most PLCs have built-in access control features, most of these have been shown to be ineffective. Where encryption has been used, the algorithms are often ineffective. Disabling unused protocols and monitoring HMI data is the best way to prevent and detect attacks.
Infosec industry
New tool—BlackCat: Security researcher Rogier Dijkman has released BlackCat, a PowerShell module designed to validate the security of Microsoft Azure environments.
New tool—ShareFiltrator: Friends & Security has released ShareFiltrator, a tool for the enumeration and bulk download of sensitive files from SharePoint servers.
Threat/trend reports: Akamai, BI.ZONE, CyberCX, Rapid7, S2W, and SANS ISC have recently published reports and summaries covering various infosec trends and industry threats.