Risky Bulletin Newsletter
April 07, 2025
Risky Bulletin: Hackers hit Australia's superannuation pension funds
Written by

News Editor
You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
A wave of credential-stuffing attacks targeted Australian pension funds last week, resulting in the theft of some customer retirement funds.
The attacks targeted superannuation accounts, a private pension fund system used in Australia where employees store money that is made available to them when they retire.
Five major superannuation pension funds confirmed the attacks.
The Australian Retirement Trust, AustralianSuper, Hostplus, Insignia Financial [PDF], and Rest said they saw attacks on their online customer portals.
Two other funds—Hesta and Mercer—said their members weren't affected, although they didn't deny being targeted.
Not all organizations provided technical details about what happened, but AustralianSuper said the attackers used "stolen passwords to log into [customer] accounts" and attempt to steal funds.
So far, Australian news outlets estimate the total losses of up to AUS$500,000. The biggest theft impacted an AustralianSuper customer, who lost AUS$300,000 in last week's intrusions. The total tally is likely to be even larger since those pension funds can be large, and the older the owners, the more likely they are not using a unique password or multi-factor authentication.
A Reuters source claims the hackers breached up to 20,000 accounts, although it's unclear how many they managed to empty before the organizations caught on and started blocking transfers.
The threat actor behind the attacks has not been identified.
The Australian government is said to be investigating the attacks and has already tasked several agencies with getting to the bottom of it.
In the meantime, the Association of Superannuation Funds of Australia, an industry group for superannuation fund managers, has confirmed the theft of customer funds and has told members to shore up their cyber defenses.
Risky Business Podcasts
Risky Business is now on YouTube with video versions of our main podcasts. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
Europcar breach: A hacker has leaked the GitLab repos of Europcar, one of Europe's largest car rental businesses. The repos allegedly contain the source code for the company's Android and iOS applications. They also contained the personal data of almost 200,000 customers. The threat actor released the data after failing to extort the company. [Additional coverage in Bleeping Computer]
Sondeos Global hack: Hackers breached SMS gateway provider Sondeos Global to intercept SMS messages, bypass MFA, and hijack online accounts. The breach took place on March 24 and lasted for two days. The company says the attackers intercepted over 30,000 SMS messages while they had access to its servers. In a report last week, the Security Alliance found that a group named Slovenly Comet hacked an Argentinian SMS gateway provider. Sondeos Global operates in Argentina and is likely that company. [Additional coverage in ElHacker]

General tech and privacy
Altair BASIC source code: Bill Gates has released the source code for Altair BASIC, the version of the BASIC programming language created by him and Paul Allen for Microsoft products.
PyPI will support SBOMs: The Python Software Foundation will add a dedicated directory inside package metadata structures (.dist-info/sboms) where maintainers can add information about their software bill of materials (SBOM). In addition, the Python team is also adopting a universal lock file format across all its package managers. This should allow coders to reproduce installs with the developer's original settings to avoid errors or extract more accurate dependency trees.
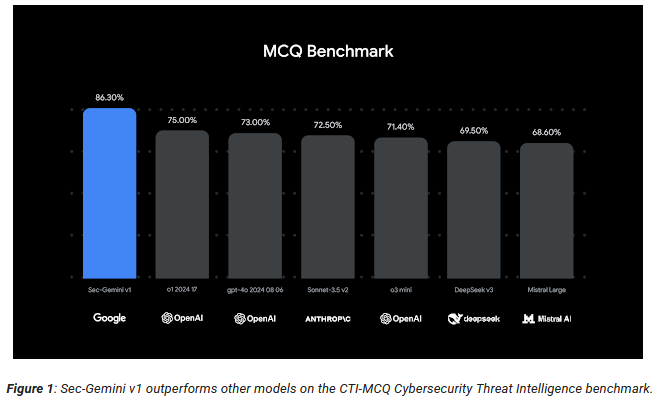
Google releases Sec-Gemini: Google has released Sec-Gemini, a new experimental AI model for cybersecurity professionals. Google says the model outperforms any other product due to the company's extensive cybersecurity portfolio and access to real-time threat intelligence. Sec-Gemini is currently available as early restricted access.
Government, politics, and policy
Trump fires CyberCom and NSA leadership: US President Donald Trump has fired both the director and deputy director of the NSA. Air Force general Timothy Haugh and deputy director Wendy Noble were both fired on Thursday. The dismissals come one year into what are traditionally three-year roles, and the White House has not said why Haugh and Noble were terminated. The Trump administration named Army Lieutenant General William Hartman as acting head of Cyber Command and the NSA. According to the Washington Post, far-right activist Laura Loomer urged Trump to fire Haugh and others she considered disloyal to the president.
Cyber angle spotted at today’s DC protest
— Patrick Howell O’Neill (@patrickhowelloneill.com) 2025-04-06T00:22:27.211Z
CISA set to fire up to 1,300 employees: The US government is preparing to fire as many as 1,300 CISA employees in the coming weeks. According to Politico, the new layoffs will impact the agency's threat-hunting teams. CISA previously fired 130 employees in February and another 300 in March. At this pace, the agency is set to lose almost half of its previous 3,400-strong workforce. [Additional coverage in CBS News]
Getting rid of threat hunting increases government efficiency, just not for the US government.
— Joe Uchill (@joeuchill.bsky.social) 2025-04-05T18:10:25.109Z
Lawmakers seek to expand Secret Service powers: Two US lawmakers have re-introduced a bill that would grant the US Secret Service more powers to investigate cyber laundering operations. [Additional coverage in The Record]
ICC draft on cyber-enabled crimes: The International Criminal Court (ICC) published a first draft policy on cyber-enabled crimes. [Additional coverage in Lawfare Media]
EU GDPR headed for the chopping blocks: Politico reports that the EU is thinking of killing or seriously nerfing its GDPR law as part of its attempt to simplify the business environment, and 100% not because the White House is pressuring them at the behest of US tech giants who like to guzzle and gargle personal data for their profits. That's just a giant coincidence.
France explains itself: After it cut off TikTok access in New Caledonia last year, the French government explained the three conditions it used as the base for the decision. It didn't rule out using it in the future again. The three are:
- events are of a serious gravity;
- no other technical means can be taken;
- the interruption is only for a limited period of time.
Risky Business podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq look at all the strands of evidence that make people think the NSA is a top-tier cyber actor.
Arrests, cybercrime, and threat intel
Pharmacist investigated for installing spyware: The FBI is investigating a former pharmacist for allegedly installing spyware on over 400 computers at the University of Maryland Medical Center. Dr. Matthew Bathula allegedly activated webcams to watch and record female staff undress and pump breastmilk. He also used the compromised staff computers to gain access to home security systems to watch his coworkers having sex, and hacked into other online accounts using passwords collected by the spyware. Six of the women have filed a class-action lawsuit against the hospital for negligence after learning of the hacks from the FBI. [Additional coverage in The Baltimore Banner]
Scattered Spider member pleads guilty: A Florida hacker has pleaded guilty to cryptocurrency theft charges and has agreed to return more than $13 million back to 59 victims. Noah Michael Urban went online as King Bob and Sosa and was a member of the Scattered Spider group. He was arrested in January of last year and charged in November in an FBI crackdown against the group's members. He also gained a reputation online for leaking music by rap stars Playboi Carti and Lil Uzi Vert ahead of their official release.
Aeza Group arrests: Russian authorities have detained the CEO of IT company Aeza Group on charges of creating a criminal group and drug trafficking. Yuri Bozoyan was detained on Friday in St. Petersburg under a two-month arrest warrant. Aeza founder Arseny Penzev was also arrested. Security researchers previously linked the Aeza Group to bulletproof hosting services for cybercrime groups and Russian disinformation operations. According to the Mash Telegram channel, the two were detained because their company hosted an online drug store named BlackSprut. [Additional coverage in TASS]
Russian man sentenced for DDoS attacks: Russian authorities have sentenced a man from Rostov for launching DDoS attacks against a Russian company last April. [Additional coverage in Interfax]
CrazyHunter ransomware linked to Chinese man: Taiwanese authorities have identified the operator of the CrazyHunter ransomware as a 20-year-old Chinese man. The suspect is allegedly named Lo and works for a cybersecurity company in China's Zhejiang province. Officials say he orchestrated ransomware attacks against 11 Taiwanese organizations in February and March this year. His most devastating attacks crippled the operations of three hospitals, including the island's biggest medical center. [Additional coverage in Taiwan Focus] [h/t DataBreaches.net]
New npm malware: One hundred twenty-one malicious npm packages were discovered and taken down last week. Check out the GitHub security advisory portal for more details.
PoisonSeed campaign goes after crypto seed phrases: A threat actor has launched a phishing campaign that targets crypto users and seeks to obtain their crypto-wallet seed phrases.
Masslogger campaign: Broadcom spotted a Masslogger campaign targeting organizations in Romania, posing as a local bank.
Smishing Triad: Resecurity researchers say the Smishing Triad gang is now focusing its efforts on toll payment services.
Router mayhem: A woman from Estonia reportedly received a €1,000 phone bill after her SIM-capable router got hacked and was used to send thousands of international SMS messages as part of a botnet. [Additional coverage in DigiGeenius]
EncryptHub profile: Outpost24 has published a follow-up on their initial profile of EncryptHub, a fin-crime group also known as Water Gamayun and Larva-0208. They seem to believe the group is led by an Ukrainian fro m Kharkiv.
Wagmi Team: TRAC Labs has published a profile on the Wagmi Team, a traffer group that has been operating since early 2023. The group was previously known as Triple Culture and is made up of psychopaths who like to use dark purple text on a dark background.
Defunct.dat mass scanning: Threat actors are mass-scanning websites for the presence of the configuration files for the GSocket backdoor. Attackers extract connection keys from the qfile and defunct.dat files and then initiate a GSocket reverse shell from the exposed server. Security firm Sansec says 45 websites have already been compromised this way.
DragonForce strikes again: The DragonForce ransomware group has hacked another one of its competitors, the RansomHub RaaS. This is their third victim after previously also hacking Mamona and BlackLock.
Malware technical reports
LegionLoader: Netskope researchers look at a ClickFix campaign spreading the LegionLoader malware.
Grandoreiro: Lab52 has published a report on the Grandoreiro banking trojan, now with infostealer capabilities. Forcepoint has also published a report on this malware's sudden resurgence.
Betruger backdoor: ThreatMon has published a report on Betruger, a new backdoor used by the RansomHub gang. Broadcom has also released a report on this last month.
RolandSkimmer: Fortinet researchers have discovered a cluster of Chrome, Edge, and Firefox extensions that install a local web skimmer named RolandSkimmer inside a user's browser. Most of these attacks were spotted targeting users in Bulgaria.
VortexCrypt ransomware: Panda Zhengzheng researchers have published a technical analysis of the VortexCrypt ransomware.
CrazyHunter ransomware: WithSecure threat intel analyst Jeremy Ong has published a technical analysis of the CrazyHunter ransomware—the one we mentioned in a piece earlier in this newsletter.
Risky Business Podcasts
Tom Uren and Patrick Gray discuss how North Korean IT worker scam is shifting towards Europe and employing tactics that make it more dangerous.
APTs, cyber-espionage, and info-ops
Russia's info-ops in Romania: Social media accounts that previously boosted pro-Kremlin candidate Calin Georgescu are now pushing blatant pro-Putin, anti-NATO, and anti-EU narratives. This comes after the Georgescu camp denied receiving support from the Kremlin for his campaign. This network is quite active and bombarding any nook and cranny of the Romanian internet space, both social media and the comments section of major news outlets.
Lazarus on npm, again: Socket Security looks at yet another Lazarus APT operation that uploaded malicious JS libraries on npm. This time, it's a batch of 11 packages but only 5,600 downloads.
BeaverTail and Tropidoor: AhnLab looks at a campaign using fake recruiting emails to infect victims with the BeaverTail and Tropidoor malware—both strains typically associated with North Korean APTs.
Red Delta: Validin researchers have found what they described as "potential operational overlaps between Red Delta and APT41."
Captured Ukrainian drones (probably don't) carry malware: Captured Ukrainian drones are apparently deploying malware on the PCs of Russians investigating their software. We're dubious this actually happens, but a video in a Reddit post claims the drones are set up to over-volt and burn the USB port when plugged in. The video also claims the drones somehow prevent Russian operators from reflashing and reprogramming the drone. The video goes on to assert that the masterful Ukranian uber-malware can also survive reflashing and then reveal its location and its Russian operator's location to Ukrainian troops. Sounds like propaganda designed to scare Russians to us. [Breathless coverage in Forbes expresses no doubts as to its authenticity.]
Russian complaining that Ukrainian FPV combat drones are often infected with computer viruses. Variants include burning out the USB port, preventing reflashing, or hijacking the repurposed FPV and revealing the operator location.
by u/esporx in ukraine
Vulnerabilities, security research, and bug bounty
Splunk security updates: Cisco has patched two vulnerabilities in the Splunk SIEM platform.
Apache Parquet RCE: The Apache project has released a security update to fix a remote code execution (CVE-2025-30065) in the Parquet data storage format.
PyTorch deserialization issues: The CMU CERT/CC team says the PyTorch Lightning project is vulnerable to deserialization attacks via malicious model files.
"Users of PyTorch Lightning should use caution when loading models from unknown or unmanaged sources."
Ivanti zero-day write-up: watchTowr Labs has published a write-up on an Ivanti zero-day (CVE-2025-22457) the company disclosed last week. It's hilarious, just like all of the company's previous write-ups.
"This is why they initially deemed the vulnerability 'unexploitable' - the vulnerable buffer can be overflowed only with digits and a full stop (or a 'period', for our friends over the pond)."
NVD gives up on a third of all CVEs: US NIST has abandoned adding metadata to all CVEs issued before January 1, 2018. The agency will add a "deferred" status to all the older CVEs that have not been enriched already. According to Socket Security and VulnCheck, the designation will impact up to 100,000 CVEs, almost a third of the entire US vulnerabilities database.
Infosec industry
Cyber insurance market expected to double: The global cyber insurance market is expected to reach over $16.3 billion in gross written premiums this year. Insurance company Munich Re expects the market to double in size to over $32.4 billion in premiums by 2030. The company expects to see huge losses across all main categories—ransomware, scams, data breaches, and supply chain incidents. [Additional coverage in Risk & Insurance]
NIST IR recommendations: US NIST has finalized a revision of SP 800-61, which describes how to incorporate incident response recommendations into cybersecurity risk management activities in alignment with CSF 2.0.
New tool—Loki: IBM X-Force researcher Bobby Cooke has released Loki, a C&C system for backdooring Electron applications.
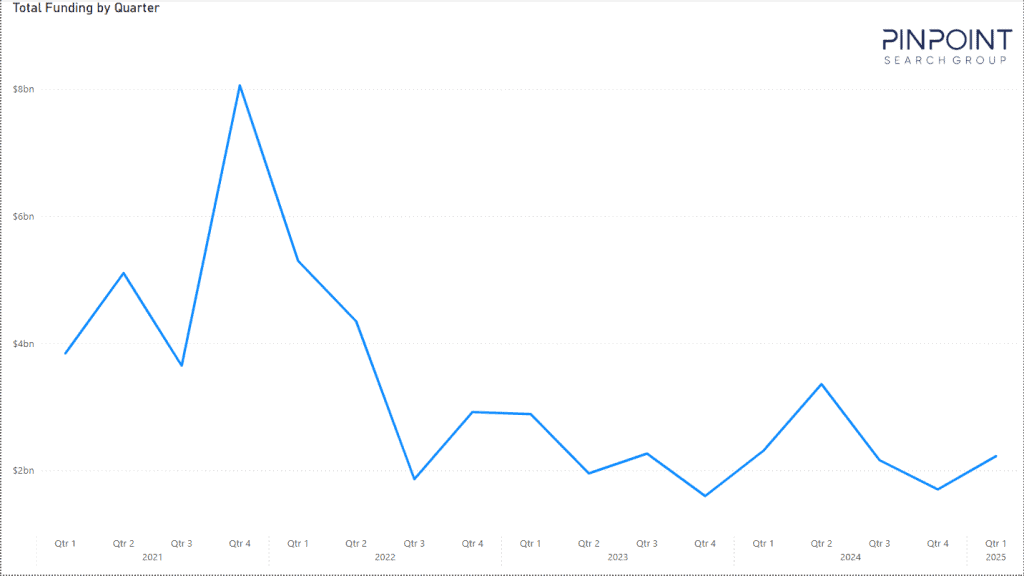
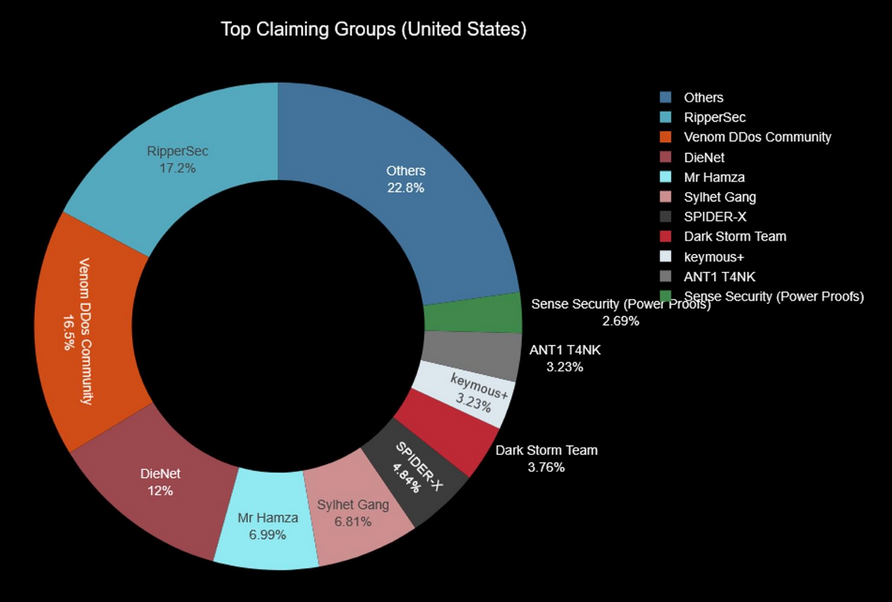
Threat/trend reports: Munich Re, Netscout, Pinpoint, and Radware have recently published reports and summaries covering various infosec trends and industry threats.