Risky Bulletin Newsletter
March 17, 2025
Risky Bulletin: GitHub supply chain attack prints everyone's secrets in build logs
Written by

News Editor
This newsletter is brought to you by no-code automation platform Tines. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
A threat actor compromised a popular GitHub Action and added malicious code that prints out secret tokens in project build logs.
The incident took place on Friday and impacted tj-actions/changed-files (hereinafter Changed-Files), an automated action used by over 23,000 GitHub projects.
The action works by analyzing pull requests and detecting what files. It is used in complex CI/CD pipelines to trigger other actions based on what files are changed. It is a basic but very important automation script, and the reason why it become one of GitHub's most popular actions.
It's still unclear how the attacker compromised Changed-Files, but once they were inside, they added malicious code to every action version—meaning that repos using old versions were also impacted.
If you haven't heard, there was a fairly impactful breach of the tj-actions/changed-files github action. If you use it, you should definitely remove it and rotate all the secrets your actions have access to.
— Justin (@just-be.dev) 2025-03-15T13:12:57.477Z
Disaster supply chain attack! Backdoor in tj-actions/changed-files repo. When CI/CD triggers it, your secrets are his too. Actions: 1. Use /uses: tj-actions\/changed-files@v/ to find it in your org 2. Rotate & revoke creds 3. Monitor CI/CD
— m19o (أبومُسْلِم) (@m19o.bsky.social) 2025-03-16T07:05:52.833Z
The malicious code downloaded and ran a malicious Python script that dumps' the server memory, scans and then prints out anything resembling a secret token.
All tokens are written in a GitHub project's action build logs. It is very likely that the attacker has already scraped the token dumps.
If a repo is private, the damage is minimal since the build log is also private, although not all of an organization's members may be authorized to see those secrets—but that's another problem.
The real damage was done to public repos, where the build logs are also public. All of these projects will need to scan their build logs and rotate the leaked secrets, which can be anything from API secret tokens to cryptographic keys.
"For organizations that build software, they will likely need to reconfigure their pipelines if they are using the compromised Action," Dimitri Stiliadis, CTO and co-founder of Endor Labs, told RiskyBusiness in an email. "The attack shouldn't generally cause outages for customers but it could block organizations from making other changes."
GitHub's security team took down Changed-Files on Saturday, a day after the attack. The action has since been restored without the malicious code.
The incident was also assigned CVE-2025-30066. There has been no formal attribution of who may have been behind the attack.
At the time of writing, we had a few reports come out on the attack, in case you're looking for finer-grained details and instructions on how to scan your build logs and rotate secrets: AquaSec, EndorLabs, Semgrep, and Step Security.
Risky Business Podcasts
Risky Business is now on YouTube with video versions of our main podcasts. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
Micronesia ransomware attack: A ransomware attack has taken down the health system of Yap, one of the four states of the Pacific nation of Micronesia. Officials have taken the health system's whole network offline following the attack. The island is home to over 12,000 residents. Micronesia is the latest Pacific nation to suffer a crippling ransomware attack after the likes of Tonga, Palau, and Vanuatu.
Edesur Dominicana ransomware attack: Edesur, one of the Dominican Republic's state electricity providers, has confirmed falling victim to a ransomware attack by the Hunters International group. The company says the attack did not impact electricity supply and services. [Additional coverage in El Nuevo Diario]
Twitter DDoS attacker identified: Security researcher Baptiste Robert claims to have identified the person behind the recent DDoS attack on Twitter.
General tech and privacy
RCS adds support for E2EE: The GSM Association has released a new version of the Rich Communication Services (RCS) standard that supports end-to-end encryption (E2EE) communications. Both Apple and Google said they will support encrypted RCS in future Android and iOS releases. Both implementations will be compatible and allow Android and iOS users to exchange secure messages on mobile carrier networks that support it. Google began pushing for RCS as an SMS replacement in the mid-2010s.
Amazon removes Echo privacy setting: Amazon will remove a feature that allows some Echo smart speakers to process Alexa requests locally on the device. The feature will be removed on March 28, following which all Alexa requests will be sent to the cloud. Amazon says the "Do Not Send Voice Recordings" option will be transitioned to "Don't save recordings," which deletes the voice recording from the cloud after it was processed. [Additional coverage in ArsTechnica]
"hysterical laughter* Because it didn't up to this point? Are you fucking shitting me? Chuck the spyware in the bin.
— Hemlock Autumn (@hemlockautumn.bsky.social) 2025-03-15T11:04:12.039Z
Government, politics, and policy
White House goes back on cyber staff hirings: The White House has told federal agencies to refrain from firing their cybersecurity staff. US federal chief information officer Greg Barbaccia told agencies in a letter that the work of cybersecurity staff is national security-related and they should be exempt from future layoffs. Former NSA Director of Cybersecurity Rob Joyce warned Congress earlier this month that the mass firings would leave government networks exposed to attacks from foreign adversaries. [Additional coverage in Reuters]
Cybersecurity certifications for sea cable operators: The US Federal Communications Commission is working on new rules for submarine cable operators and plans to require cybersecurity and risk management compliance certifications before issuing new licenses. [Additional coverage in Industrial Cyber]
Turkiye passes controversial cybersecurity law: The Turkish Parliament passed last week a new national cybersecurity law. The new law grants the country's Cybersecurity Directorate the power to search and collect any digital records. It also introduces prison sentences of up to five years for people who report on security incidents the government has not first confirmed or wishes to confirm. Officials fast-tracked the law, which passed in less than six weeks. The country's opposition voted against the bill, arguing it provides a legal foundation to restrict free speech and establish a sprawling surveillance apparatus. They said the law paves the way for a "super dictatorship." [Additional coverage in Turkish Minute]
India cancels cyber reporter's citizenship: Reuters cybersecurity reporter Raphael Satter has sued the Indian government for canceling his overseas citizenship. Satter received Indian overseas citizenship through marriage. Indian officials canceled Satter's citizenship in December 2023 after the Reuters team published a story exposing Indian company Appin as a provider of hacker-for-hire services. Officials claimed Satter's work created "adverse and biased opinion against Indian institutions in the international arena." [Additional coverage in The Guardian]
IT security excluded from Germany's debt brake: Germany's ruling coalition has excluded IT security from its national debt brake agreement. Government agencies will be able to borrow unrestricted in order to boost their cybersecurity. IT security is one of the several sectors that have been excluded from the debt brake as Germany seeks to raise defense spending and rearm in the face of Russian aggression. [Additional coverage in Heise]
EU continues US data flows: EU lawmakers are committed to honoring a 2023 agreement on EU-US data flows, despite the US dark side turn against democracies and toward authoritarian rule. Give it time! The EU will see it soon. [Additional coverage in The Record]
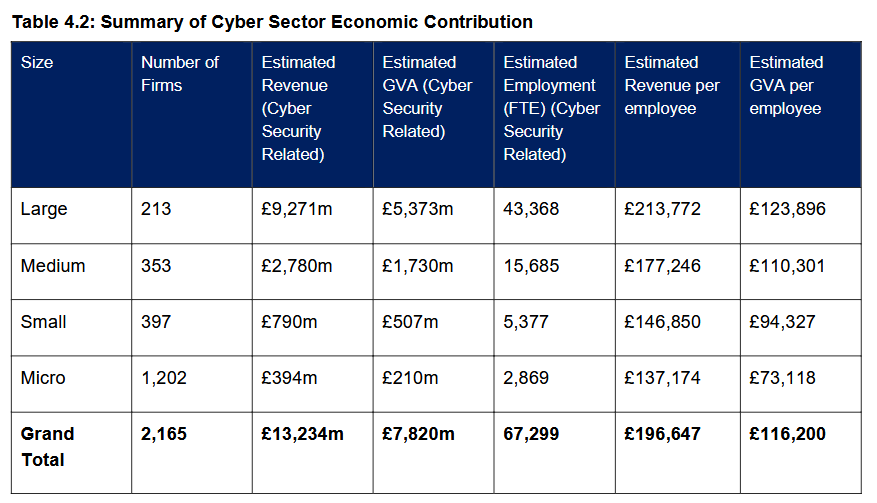
UK cybersecurity sector analysis: The UK government has published a 73-page analysis of its cybersecurity sector.
- The UK cyber security sector generated revenue of £13.2 billion, up 12% since last year;
- There are 74 new cyber security firms, bringing the total to 2,165, up 3.5% from 2,091 last year;
- The sector employs 67,300 people (full-time equivalents), up 11% since last year, an increase of around 6,600 jobs;
- The total gross value added (GVA) for the sector has reached c. £7.8 billion, an increase of 21% since last year;
- GVA per employee has increased from £106,300 to £116,200, an increase of 8%;
- In terms of investment, £206 million was raised across 59 deals within dedicated cybersecurity firms in 2024.
Sponsor section
In this Risky Business News sponsor interview, Tom Uren talks to Matt Muller, field CISO of Tines. He explains how governments are using carrots and sticks to improve the security of enterprise software. Matt discusses CISA's 'Secure by Design' pledge and the UK NCSC's effort to quantify 'unforgivable bugs'
Arrests, cybercrime, and threat intel
Lockbit dev extradited to US: US authorities have extradited a dual Russian and Israeli national for his role in developing the Lockbit ransomware. Rostislav Panev was initially arrested in Israel in August last year. Israeli investigators allegedly found evidence at his home linking him to LockBit ransom notes and payments.
Banshee Stealer admin's alleged arrest: Russian authorities have allegedly arrested the new administrator of the Banshee Stealer malware. Police detained the suspect after the malware was supposedly used to target Russian users. The Banshee Stealer is one of the few infostealer that can target and steal credentials from macOS systems. According to security researcher g0njxa, the malware's original author sold the source code to a new owner in December. The Banshee source code leaked online a month later. It's unclear if authorities detained the malware's new owner or an individual who used the leaked code to create a new variant.

Meta seeks monetary damages from NSO: Meta is seeking financial damages of $444,719 from Israeli spyware maker NSO Group. The sum represents response costs related to investigating a wave of WhatsApp account hacks in 2019 using an NSO exploit. Meta sued NSO in late 2019, and a US judge found the Israeli company liable for the hacks after years of stonewalling US courts.
AWS late to act on spyware leaks: AWS has failed to take down the servers of three spyware companies that are leaking victim data, weeks after initial reports. [Additional coverage in TechCrunch]
Deepseek re-tooled for malware: Tenable says one of its employees used Deepseek's AI service to develop malware, such as a keylogger and ransomware.
OBSCURE#BAT: Securonix has published a report on OBSCURE#BAT, a threat actor that seeks to trick users into running malicious batch files that deploy a user-mode rootkit and all sorts of other malware on targeted systems.
Ramadam scams: CloudSEK looks at a wave of Ramadan-related crypto, e-commerce, and donation scams the company has spotted online this month.
Coinbase wallet migration scam: Cryptocurrency exchange Coinbase has told users to be aware of a new type of scam that tricks users into moving funds into a wallet set up by attackers in advance. Users reported receiving emails last week posing as Coinbase official communications and asking users to migrate funds to a self-custodial wallet. Users are given recovery phrases generated by the attackers in advance. Once users move their funds, the attackers use the same recovery phrases to access the wallet and steal any deposited assets.
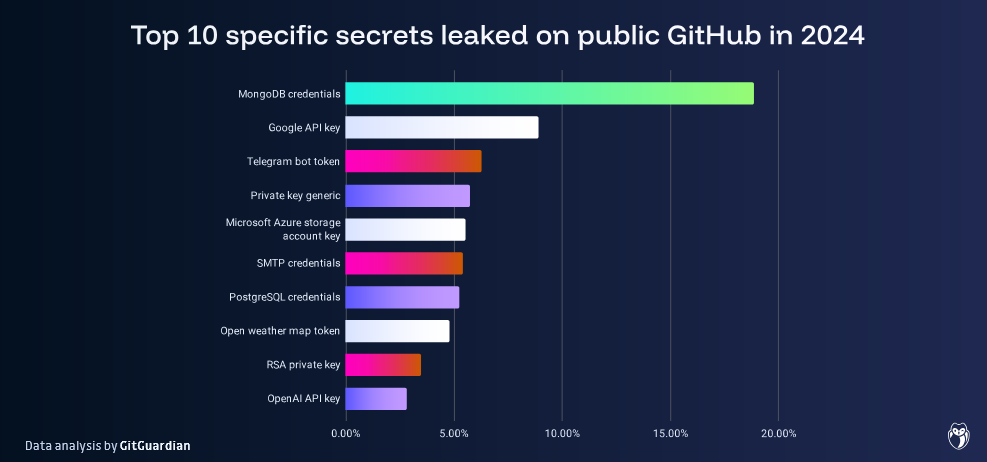
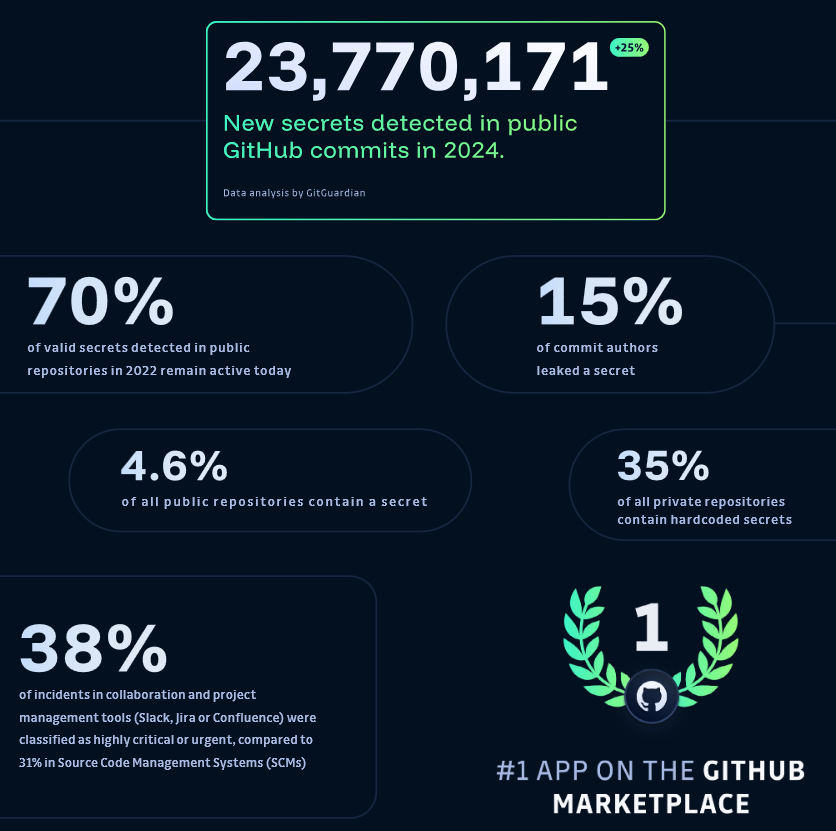
GitHub secret leaks are getting worse: Companies and developers leaked almost 23.8 million hardcoded secrets via GitHub repositories last year, a 25% surge from the previous year. The top most common secrets leaked in 2024 were ODBC connection strings and AWS IAM credentials. Security firm GitGuardian says secret leaks are steadily worsening over time despite GitHub's efforts to stop secret leaks during the push stage. The company also says that 70% of the secrets detected in public repos in 2022 remain active even today.
Microsoft apologizes for banning popular extension: Microsoft has apologized and restored two popular VSCode extensions after it took them down two weeks ago. The company blamed the incident on a false positive that detected the two extensions as malware. The two extensions—Material Theme and Material Theme Icons—were some of the most popular extensions on the VSCode Marketplace, each with millions of downloads.
New npm malware: Two hundred-nine malicious npm packages were discovered and taken down last week. Check out the GitHub security advisory portal for more details.
Malicious Maven package: Socket Security has discovered a malicious Java library on the Maven repository that is secretly stealing OAuth credentials on the 15th of each month. The package mimics the name of a popular OAuth library and has been available on the Maven portal since January 2024. Since its discovery, the project has now been taken down from both Maven Central and GitHub.

Malware technical reports
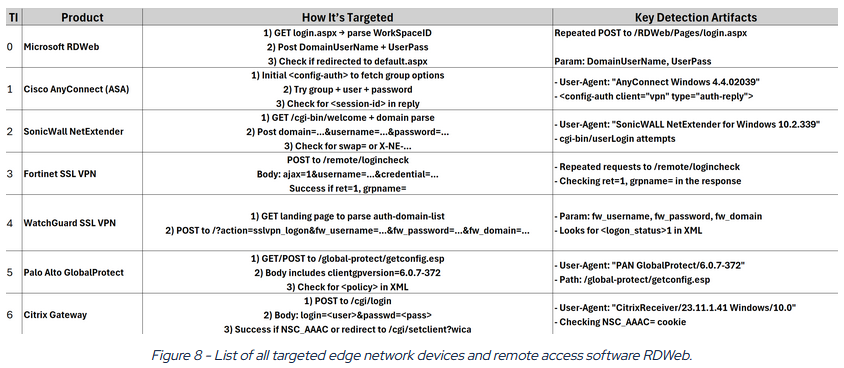
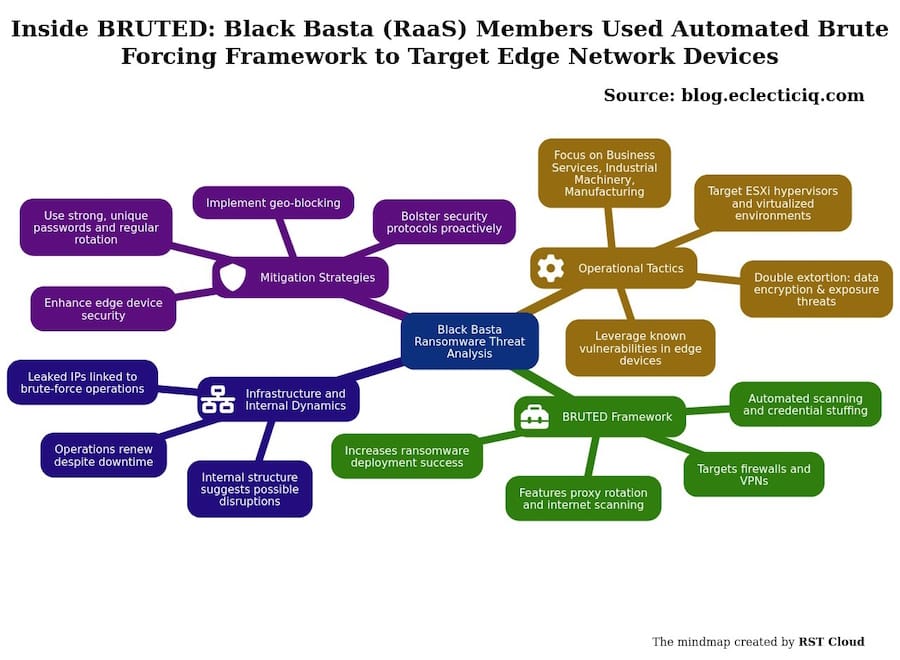
BlackBasta's brute-forcing tool: The BlackBasta ransomware gang developed and used its own custom tool to brute-force enterprise firewalls and VPN remote-access products. Security firm EclecticIQ discovered the tool while analyzing chat logs leaked from the gang's internal servers. Named Bruted, the tool was written in PHP and could launch brute-force attacks against Microsoft RDWeb pages and devices from Cisco, SonicWall, Fortinet, Citrix, and others.
LockBit "Green" v4: Security researcher Chuong Dong published a technical analysis of a v4 of the LockBit ransomware, also known as LockBit Green.
SocGolish to RansomHub: A Trend Micro report looks at how threat actors are using the SocGolish MaaS to infect systems and deploy the RansomHub ransomware.
Net Emmenthal version: Orange's CERT has spotted a new version (v3) of the Emmenthal loader being distributed in the wild. The company previously covered the malware in an August 2024 report.
Anubis backdoor: Prodaft has published a technical analysis of Anubis, a new Python-based backdoor linked to Savage Ladybug (FIN7) operations.
New malware: Palo Alto Networks looks at some unusual malware samples its Unit42 security team has discovered recently. This includes a new passive IIS backdoor, a Linux bootkit, and a new Windows implant from a cross-platform post-exploitation (red-team?) framework.
Akira decrypter: Security researcher Yohanes Nugroho has published details on a way to brute-force the encryption of the Akira ransomware and recover original files. The technique isn't universal, requires extensive HPU computing power, and only works with Akira 2024 variants. The decrypter is available on GitHub, and using it should cost around ~$1,200 worth of GPU computing time. A glorious meme from Nugroho's blog is below.

Sponsor section
In this product demo CEO Eoin Hinchy shows how Tines' Workbench can integrate an LLM into security workflows to gather, analyze, and act on data from both inside and outside your company. This demo includes grabbing IOCs from an external webpage, comparing them to your companies' own incidents, and taking actions like resetting passwords.
APTs, cyber-espionage, and info-ops
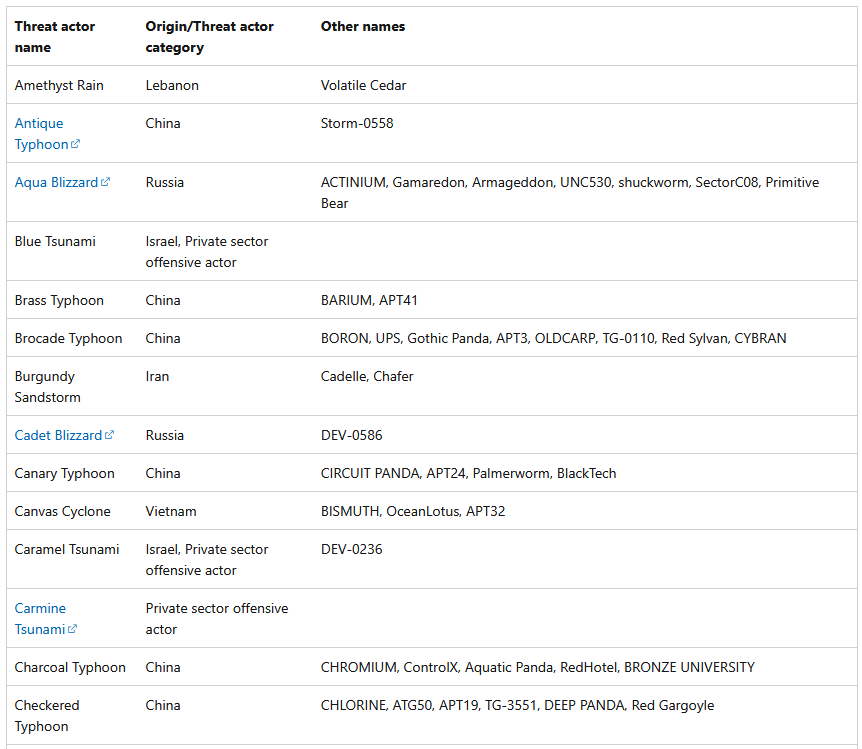
Microsoft's APT names: It looks like Microsoft has been quietly updating its 2023 new APT naming scheme table with new entries. The table used to have 20-30 entries, and it has now grown to quite an impressive length. [h/t Ryan Dewhurst]
Vulnerabilities, security research, and bug bounty
Ruby-SAML auth bypass: GitHub's security team has discovered a combo of two bugs in the Ruby-SAML library that can be used to bypass authentication in apps that use the library.
"Attackers who are in possession of a single valid signature that was created with the key used to validate SAML responses or assertions of the targeted organization can use it to construct SAML assertions themselves and are in turn able to log in as any user. In other words, it could be used for an account takeover attack."
Picklescan vulnerabilities blind scanners to malware: Sonatype researchers have discovered a quartet of vulnerabilities in Picklescan, a security tool for scanning Python pickle files for malicious content. Attackers can abuse the vulnerabilities to bypass the scanner and even run remote code on the scanning server. The scanner is used on HuggingFace, a repository of open-source ML models.
Edimax zero-day exploited for months: Multiple botnets have exploited a zero-day vulnerability in Edimax security cameras for months. The earliest evidence of exploitation was traced back to October of last year, although public proof-of-concept had been available for over a year before that. Tracked as CVE-2025-1316, the zero-day is a command injection vulnerability that can be exploited via unsanitized network requests.
Infosec industry
Unciphered co-founder: WaPo says one of the co-founders of the Unchiphered cryptocurrency recovery firm is Morgan Marquis-Boire, a controversial cybersecurity figure who disappeared from the limelight after being accused of sexual assault and rape.
It's been a mystery what happened to Morgan Marquis-Boire when he disappeared yrs ago after being accused of rape. Turns out he secretly co-founded Unciphered, which cracks crypto wallets for owners who lost passwords. He used a fake name to hide his identity from employees until they unmasked him
— Kim Zetter (@kimzetter.bsky.social) 2025-03-14T15:57:44.950Z
Uber CSO conviction upheld: A US appellate court has upheld a previous conviction for obstruction of justice for former Uber CSO Joe Sullivan over the company's 2016 hack. [Additional coverage in The Record]
New tool—Cradle: Security firm Prodaft has released Cradle, a collaborative platform for sharing cyber threat intelligence.
New tool—Seized.fyi: A software developer known as Mat has launched Seized.fyi, an online archive of website seizure banners used by law enforcement in their actions. The site currently stands at 181 entries.
Threat/trend reports: Dashlane, F6 (formerly FACCT), GitGuardian, IPA, Marsh, MetricStream, Positive Technologies, and SI CERT have recently published reports and summaries covering various infosec trends and industry threats.
Risky Business Podcasts
Tom Uren and Patrick Gray discuss how X is actively engaging in political interference outside the US. The risks mirror those of TikTok. American legislators moved against TikTok because it could potentially be a powerful tool for the Chinese government to interfere with American political discourse. X is a realized threat, not a potential one, so we expect that foreign governments will start to consider a ban.
In this edition of Between Two, Nerds Tom Uren and The Grugq talk about what Europe should do given that US security guarantees are evaporating. Should Europe grow its cyber capabilities, what would it get out of it, and how should it go about doing it?
