Risky Bulletin Newsletter
January 19, 2026
Risky Bulletin: Germany seeks more hacking and surveillance powers for its intel service
Written by

News Editor
This newsletter is brought to you by SpecterOps, the experts in Attack Path Management. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
German lawmakers are working on a new law that will grant the country's intelligence agency new and extensive hacking and surveillance powers.
The primary intent of the new law is to free up the Bundesnachrichtendienst (BND) from relying on the US National Security Agency (NSA) for threat information and bring its interception capabilities on par with other European countries, such as France, Italy, the Netherlands, and the UK.
According to a draft of the new law obtained by German media, the BND will have the power to intercept full internet communications and not just metadata as it is allowed today.
The agency will also be allowed to store the data for up to six months, which will allow it to better index and search it for threat intel.
The BND will also have its offensive hacking mandate extended. The law will allow the agency to hack foreign internet service providers and retrieve information about its targets if the companies do not cooperate or provide the requested data.
According to reports, this provision will apply to major US companies and infrastructure providers like Google, Twitter, and Meta, which have been known to be prickly around surrendering such information in the past.
The agency could previously intercept the communications of individuals abroad, but now the BND will also be allowed to put any foreigner in Germany under surveillance.
The same goes for journalists working for foreign state-run media organizations, which German lawmakers say are acting more like "agents" of a foreign state than independent reporters.
Last, BND agents will also be allowed to enter apartments and deploy their "federal trojan" on a target's device.
According to reports, the new law's draft is 139-pages long and almost doubles the BND's previous capabilities.
[h/t Vas Panagiotopoulos]
Risky Business Podcasts
In this special documentary episode, Patrick Gray and Amberleigh Jack take a historical dive into hacking in the 1980s. Through the words of those that were there, they discuss life on the ARPANET, the 414s hacking group, the Morris Worm, the vibe inside the NSA and a parallel hunt for German hackers happening at a similar time to Cliff Stoll’s famous Cuckoo’s Egg story.
The main Risky Business podcast is now on YouTube with video versions of our recent episodes. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
GrubHub breach: Hackers are extorting food delivery platform GrubHub. The ShinyHunters group is threatening to release files stolen from the company's Salesforce and Zendesk accounts last year. The company didn't comment if it would pay or not. [BleepingComputer]
Eurail breach: A hacker has stolen the personal information of Eurail customers. The European rail company has started notifying affected travelers last week. The hacker has collected reservation information, including names, contact details, and even passport copies. [h/t Manish]
Alaska PD cyberattack: The Alaska Police Department is dealing with a cyberattack on some of its servers. The agency blamed the issue on a third-party service provider.
Mysterious crypto-heist: A hacker has stolen $282 million from the owner of a private hardware wallet. The funds were stolen on January 10 and immediately laundered using Monero. The laundering caused the price of Monero to spike up to 70% over the next four days. [CoinDesk]
Georgia investigates "cyberattack": The country of Georgia has opened an investigation after its website leaked information on gas purchases, showing how the government had bought gas from Russia's Gazprom, a sanctioned company. Officials from the pro-Kremlin government claimed documents on one of its official websites were altered through a "cyberattack." Ok, buddy! If you say so! [OCCRP]
OCCRP DDoS: Investigative news outlet the Organized Crime and Corruption Reporting Project has faced a wave of DDoS attacks last week. The wave lasted for days.
For the last few days, we’ve been fighting a DDoS attack from highly resourced actors trying to make OCCRP’s reporting inaccessible. Your backing makes it possible for us to fight back more effectively. If you’d like to help strengthen our efforts, you can donate here: buff.ly/2BWJueR
— Organized Crime and Corruption Reporting Project (@occrp.org) 2026-01-16T13:05:45.085Z
General tech and privacy
Grok still generates nudes and CSAM: Twitter's Grok AI has continued to allow paying users to generate photos of nude women and children, even after the company promised it would stop. This is the umpteenth example of the company and its shitstain owner giving the middle finger to regulators and doing whatever they want. [The Guardian]
TikTok rolls out age estimation technology: Chinese social media company TikTok rolled out its age estimation technology last week. The new tech will be used to prevent children under the age of 13 from registering on the site. TikTok says it already removes around six million underage accounts every month.
6-day certs are here: Let's Encrypt has started offering six-day certificates last week.
Spotify monetization stats: Around 88% of songs on Spotify are demonetized and don't receive any royalties from the platform because they don't receive more than 1,000 streams/year. [Musically]
Google traffic to news sites craters: Referral traffic from Google to news sites has fallen by a third in 2025, mainly due to the company's new AI summaries feature. [PressGazette]
YouTube embraces cesspit future: YouTube has modified its policy and will allow users to monetize channels and videos showing sensitive topics like self-harm, suicide, domestic violence, sexual abuse, and abortion. [TubeFilter]
Metaverse VR goes down: Meta has shut down its metaverse virtual reality ecosystem after nobody adopted it. It fired staff of its VR division and will no longer sell its headsets and business SaaS. Gee, I wonder who saw this coming! Not Zuckerberg, that's for sure. /s [The Verge]
Government, politics, and policy
Finland intends to criminalise disinformation: The Finnish Ministry of Justice intends to criminalize the dissemination of false information on behalf of a foreign government. The law will be designed to counter foreign disinformation operations aided by local operatives. It's unclear if prison sentences will be handed down. The Supo intelligence service is also contributing to the proposal. [Yle]
Iran plans permanent internet cutoff: The Iranian government plans to permanently disconnect from the internet. Access will be a "government privilege" and will be granted only to vetted individuals. The internet has been down in Iran for more than a week as the ruling regime is clamping down on a new wave of protests. [The Guardian // Filter Watch]
The mysterious Venezuela cyberattack: A New York Times report claims that the US military used cyberattacks to turn out the lights in Venezuela and jam military radars during their arrest of Nicolas Maduro. This is not a particularly credible report, since the outage has been linked with photo evidence to kinetic strikes on transformers. The NYT has never had a good record of cyber reporting, and the paper has turned into a Trump regime propaganda outlet last year, so I'm gonna wait for additional reporting before taking this at face value.
Trump cyber officials consider boycotting RSAC: Trump top cyber officials are considering canceling their attendance at the RSA cybersecurity conference. Officials are evaluating their presence after former CISA Director Jen Easterly was named the conference's CEO. Easterly served as CISA Director during the Biden administration. [NextGov]
Scoop: Top Trump cyber officials are in discussions to cancel their attendance at the RSAC Conference in March after a top Biden-era cyber leader was named as CEO of the conference ⬇️
— David DiMolfetta (@ddimolfetta.bsky.social) 2026-01-16T02:35:04.917Z
France drops tech giant tax: The French government has dropped GAFAM, a plan to raise taxes on US tech giants from 3% to 15% after pressure last fall from the US Congress. GAFAM had a majority support in the French Parliament before the Trump admin threw a hissy fit. [FranceInfo]
EU seeks Chinese equipment ban: The EU is preparing to ban the use of Chinese equipment in telecommunications networks, solar energy systems, and security scanners. The ban would apply to Chinese companies such as Huawei and ZTE. The provision will be part of a draft of the EU Cybersecurity Act, set to be unveiled this week. [Financial Times]
If it's only going after Chinese vendors and not also US and Israeli vendors then it's based on an out of date threat model.
— Lee (@justlee.bsky.social) 2026-01-17T08:25:43.802Z
Sponsor section
In this Risky Business sponsor interview, Tom Uren talks to Justin Kohler, Chief Product Officer at SpecterOps, about how attack paths exist in the seams between different identity or permissions management domains.
Arrests, cybercrime, and threat intel
Jordanian hacker pleads guilty: A Jordanian man has pleaded guilty in the US to selling access to more than 50 hacked networks. Feras Khalil Ahmad Albashiti worked as an initial access broker under the name of "r1z." He was arrested in the country of Georgia and extradited to the US last year. He faces up to 10 years in prison.
More details on US Supreme Court hacker: A Tennessee man who hacked the US Supreme Court also breached the AmeriCorps system at the Department of Veterans Affairs. Nicholas Moore took data from both networks and published it on the @ihackthegovernment Instagram account. He pleaded guilty last week. Moore faces a maximum sentence of one year in prison and a maximum fine of $100,000. [TechCrunch]
911 S5 botnet admin fights US extradition: A Singapore court has dismissed an appeal filed by the administrator of a malware botnet that the seizure of his property was unlawful. Wang Yunhe has been under arrest in Singapore since May 2024 and is currently fighting his extradition to the US. The US DOJ has indicted the Chinese national for running the 911 S5 proxy botnet. [ChannelNewsAsia]
Black Basta raids: Ukraine's cyber police have raided the homes of two individuals involved in ransomware attacks. The two are allegedly linked to the Conti and Black Basta groups. They allegedly cracked hashed passwords to later breach corporate networks.
ATM jackpotters plead guilty: Five Venezuelan nationals have pleaded guilty to hacking ATMs across the US state of Georgia. The group deployed malware or accessed the ATM's supervisor mode to force the device to dispense their cash. Members of the group were caught on camera carrying out the attacks and were identified based on fingerprints left behind. They face up to 30 years in prison.
New ClickFix variant "CrashFix": Huntress has spotted the KongTuke threat actor using a new variant of the ClickFix social engineering technique. Instead of using fake CAPTCHA pages to trick users into running malicious PowerShell commands, KongTuke is using fake browser crash pages instead. The company calls this new version "CrashFix," for obvious reasons.
Malicious Chrome extensions target HR and ERP systems: A cluster of five malicious Chrome extensions are targeting the users of popular HR and ERP platforms. The extensions contain code to steal cookies, hijack sessions, and block access to the platform's security and admin pages. Services like Workday, NetSuite, and SuccessFactors were targeted. According to Socket Security, the extensions reached only around 2,300 users.
RedLineCyber: CloudSEK has uncovered RedLineCyber, a threat actor distributing a clipboard hijacker across Discord crypto and blockchain communities.
Cybercrime leaks: Analyst1 has an interesting report on how data from two leaks at major cybercrime operations—Black Basta and Media Land—connects to each other.
"These two leaks gave us a rare and extremely useful look into how Russian-speaking ransomware groups work closely with bulletproof hosting providers. The two leaks are connected because Media Land, also known by its underground name Yalishanda, provided the actual infrastructure and support that BlackBasta relied on to run its ransomware operations."
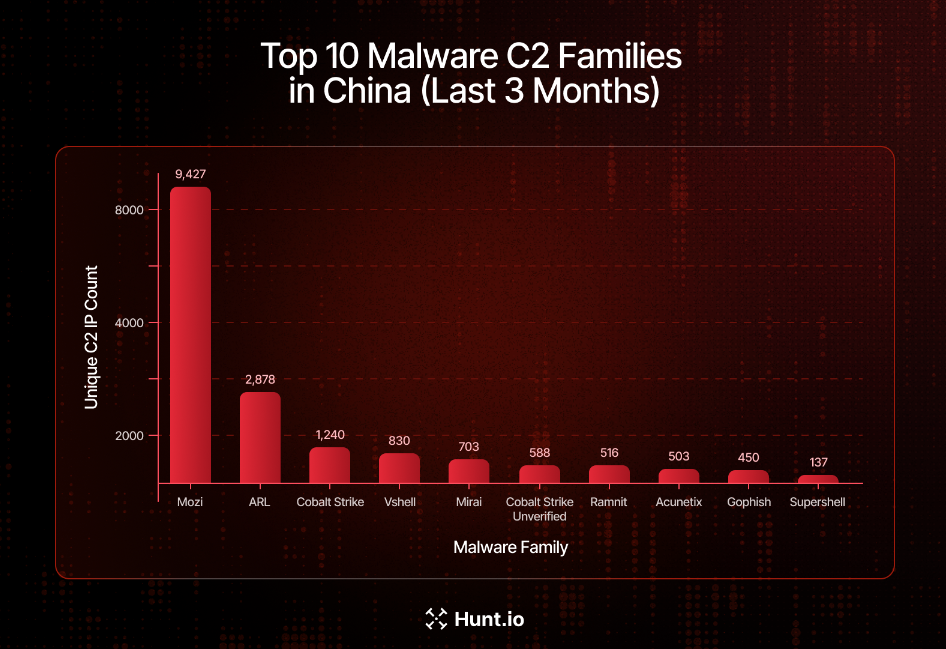
China's C2 overview: The Chinese internet space is hosting more than 18,000 active command and control servers across 48 different providers. China Unicom hosts nearly half of all observed servers. More than half of the servers are used to control Mozi IoT botnets.
Malware technical reports
More VoidLink: Sysdig has published its own insight on the new VoidLink Linux malware, first documented by Check Point last week.
Remcos RAT: There's a new Remcos RAT campaign going on, the RAT that will never die.
MonetaStealer: Iru researchers have published a report on MonetaStealer, a new infostealer that appeared this year and is targeting macOS devices.
SolyxImmortal: CyFirma has spotted a new Python-based infostealer named SolyxImmortal.
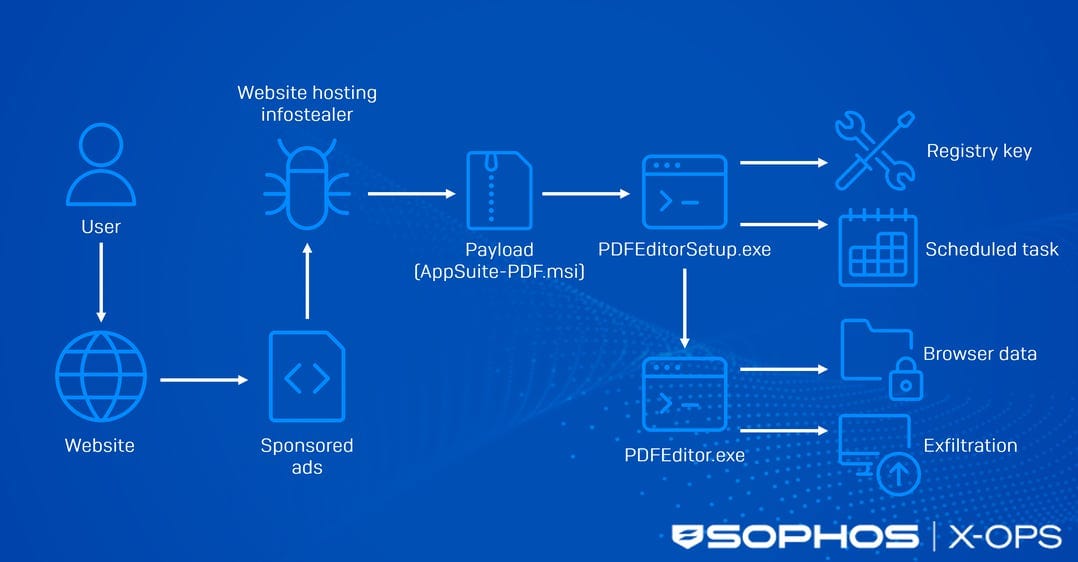
TamperedChef infostealer: Sophos has spotted the TamperedChef infostealer being distributed via malicious Google ads.
"According to Sophos telemetry, the majority of victims affected by this campaign are in Germany (~15%), the United Kingdom (~14%), and France (~9%). Although the data highlights a significant concentration in Germany and the UK, it likely reflects the campaign’s widespread global reach, rather than any deliberate targeting of specific regions; we identified 19 countries affected in total."
Sponsor section
Justin Kohler, VP of Product at SpecterOps, shows how BloodHound Enterprise can be used to find and fix Active Directory (mis)configurations that could let attackers easily own your entire enterprise.
APTs, cyber-espionage, and info-ops
French "patriotic" accounts go silent: A cluster of French "patriotic" accounts went silent on Twitter after Iran cut internet access in the country. The accounts posed as French people and were heavily involved in stoking anti-government protests. A similar cluster promoting the Scottish independence movement also went inactive at the same time. [Liberation] [h/t AngryVichy]
Gamaredon: Synaptic Systems looks at a Gamaredon campaign using the Windows BITS service to deliver payloads on infected systems.
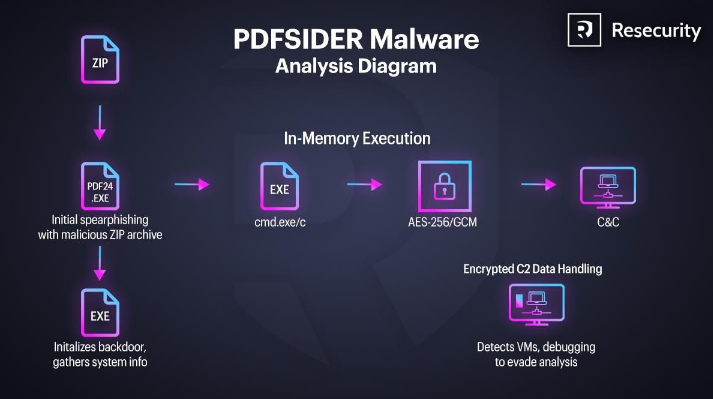
PDFSIDER: Resecurity has spotted a new backdoor named PDFSIDER. The company believes the malware has been created by an APT group, but no other details are provided except that the malware was deployed in a failed attack at a Fortune 100 company.
Iranian phishing op: TechCrunch looks at a WhatsApp and Gmail phishing op that targeted Iranian experts across the Middle East during the recent protests.
APT-C-06 (DarkHotel): Chinese security firm Qihoo 360 has spotted the DarkHotel APT group using malware-infected USB thumb drives to distribute its payloads. The report covers attacks in early 2025.
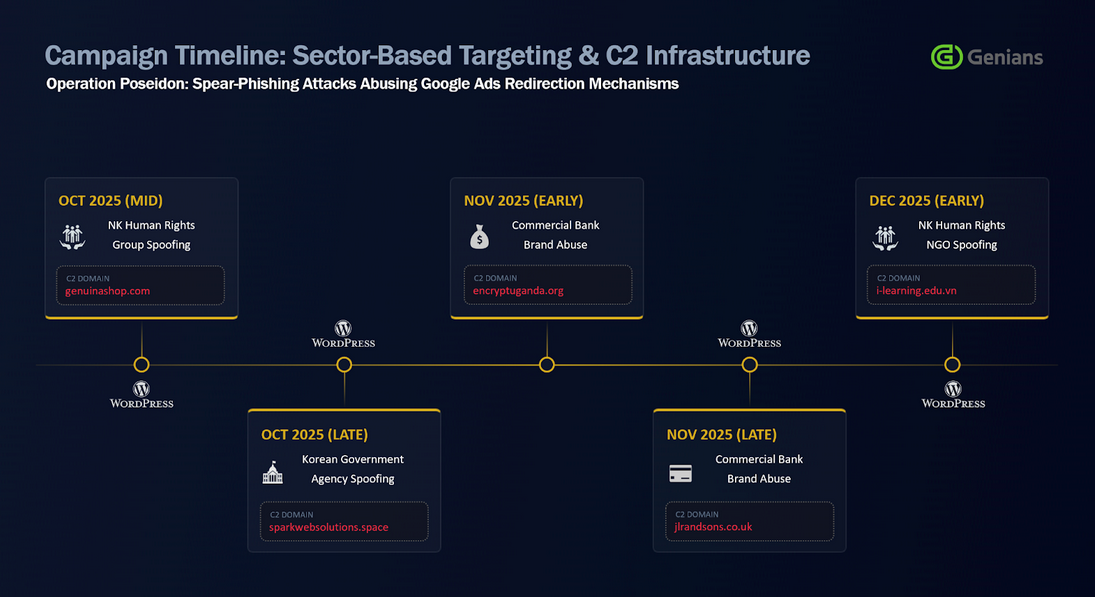
Operation Poseidon: A North Korean APT group has used advertising-related URLs to hide malicious URLs and bypass email security filters. The campaign used Naver and Google DoubleClick domain redirection features to redirect links inside emails to malicious domains. South Korean security firm Genians linked the months-long spear-phishing campaign to a group known as Konni.
Vulnerabilities, security research, and bug bounty
StackWarp attack: A team of academics has discovered a vulnerability that can allow threat actors to run malicious code inside the AMD Secure Encrypted Virtualization (SEV) platform. The StackWarp attack can be used to expose secrets from SEV-secured environments and compromise virtual machines hosted on AMD-powered cloud environments. All AMD processors from the Zen 1 to Zen 5 are affected when hyperthreading is enabled. AMD has released firmware updates last week.
CodeBreach vulnerability: Amazon has fixed a misconfiguration in its GitHub repositories that could have allowed attackers to take over crucial AWS resources. The vulnerability resided in how the AWS CodeBuild CI pipelines handled build triggers. Two missing characters in a regex filter could have allowed remote attackers to take over AWS repos with admin access. The repos hosted JavaScript resources that powered both customer accounts and the AWS backend console itself.
Cisco patches zero-day: Cisco has released a security update for a zero-day the company disclosed in mid-December. The zero-day (CVE-2025-20393) affects Cisco email security products, such as the Secure Email Gateway and the Cisco Secure Email and Web Manager. It allows the attackers to run commands as root on the devices if certain ports are open on the internet. Cisco linked the attacks to a Chinese espionage group it tracks as UAT-9686.
0-click Android exploit: Google Project Zero has released a zero-click exploit that can compromise Android smartphones via the Dolby audio decoder. The exploit works because most Android communication apps now automatically process incoming audio attachments in the background. The exploit was tested on a Pixel 9 but Google researchers say the attack should be universal against most Android devices. [Part 1 // Part 2 // Part 3]
FortiSIEM exploitation: Threat actors are exploiting a recently patched vulnerability in Fortinet FortiSIEM devices. Tracked as CVE-2025-64155, the vulnerability was fixed on Patch Tuesday. Attacks started days after security firm Horizon3 published a write-up and proof-of-concept code. The vulnerability allows threat actors to remotely run OS commands on the device without authentication.
Loads of Meta bugs: Bug hunter Youssef Sammouda has published write-ups on three issues he found and reported in Meta's services. The first is a two-click account takeover bug in FXAuth, the shared authentication backbone of all of Meta's social media sites. The second is an Instagram account takeover attack by abusing the Meta Pixel script. The third is a leak of Meta user data to outside sites.
CISA tool bug: CISA has patched an XSS vulnerability in its Software Acquisition Guide: Supplier Response Web Tool. [CyberScoop]
Unpatched Laravel Livewire bug: An unpatched security flaw was disclosed in Livewire, a file manager component for Laravel-based websites. The vulnerability can allow threat actors to upload malicious PHP files on a remote server and easily trigger its execution. Laravel is today's most popular PHP framework. Neither the Livewire nor the Laravel teams responded to researchers.
Infosec industry
Threat/trend reports: Allianz, Comparitech, Dr.Web, Flashpoint, ITRC, and SafeBreach have recently published reports and summaries covering various threats and infosec industry trends.
CrowdStrike wins shareholder lawsuit: A judge has dismissed a lawsuit brought by CrowdStrike shareholders against the company's July 2024 IT outage. The incident crashed more than 8 million Windows computers and impacted flights and hospitals across the world. Shareholders argued the company had lied about its cybersecurity testing practices, causing their stocks to devalue. The judge dismissed the case because shareholders failed to prove that CrowdStrike management's statements were "motivated by an intent to defraud." [Yahoo Finance]
Synacktiv diversifies: French cybersecurity company Synacktiv plans to enter the phone data recovery market. [Intelligence Online]
New tool—One WSL BOF: SpecterOps' Daniel Mayer has released One WSL BOF, a Cobalt Strike beacon file to enumerate and execute commands on Windows Subsystem for Linux (WSL) hosts.
New tool—Husn Canaries: The IOActive team has released Husn Canaries, a defense-in-depth framework for AI coding assistants.
"We propose using Husn Canaries, a centralized detection and policy service in which organizations register hard-to-notice patterns already present in their codebases (e.g., tokens or comments, regular expressions, and intentionally placed signatures). Participating AI providers call the Husn API during code indexing and request handling. When Husn identifies pattern matches, it returns policy decisions (e.g., allow with logging, require approval, or block) and emits tamper-resistant alerts back to the organization."
Tianfu Cup lives: After rumors that it was shutting down, China's top hacking competition, the Tianfu Cup, is coming back for another year.
Risky Business podcasts
In this edition of Seriously Risky Business, Tom Uren and Amberleigh Jack talk about the Chinese government's reactive approach to tackling scam compounds. It's driven by bad news on domestic media and therefore focuses on the compounds that are targeting Chinese citizens. Rather than eliminating the industry, that may instead be shaping the industry to focus on other countries and particularly Americans.
In this edition of Between Two Nerds, Tom Uren and The Grugq about the role of cyber operations in the US capture of Venezuela’s president Nicolas Maduro.
