Risky Bulletin Newsletter
April 30, 2025
Risky Bulletin: French government grows a spine and calls out Russia's hacks
Written by

News Editor
This newsletter is brought to you by Dropzone AI. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
After years and years of pretending like nothing serious happened, the French government has finally grown a spine and formally called out Russia for using military cyber units to meddle in its elections and to carry out destructive cyberattacks against French targets—a big no-no for countries not at war.
In a statement on Tuesday, the French Ministry of Foreign Affairs says that hackers linked to Russia's GRU military intelligence agency were behind some of the most notorious hacks in France's history, such as:
- MacronLeaks: a hack-and-leak operation that tried to sway voters ahead of France's 2017 presidential election using over 20,000 emails stolen from the Macron campaign.
- TV5 hack: a destructive hack that almost took offline French broadcaster TV5. The hack was conducted by GRU hackers under the guise of an ISIS hacktivist group named the Cyber Caliphate.
- Paris Olympics hacks: a mix of DDoS attacks and influence operations meant to disrupt and downplay the success of the 2024 Paris Olympic Games.
"These destabilizing activities are unacceptable and unworthy of a permanent member of the UN Security Council. They are also contrary to the United Nations standards on the responsible behaviour of states in cyberspace, to which Russia has subscribed."
French officials blamed these attacks, and more, on a GRU hacking group known as APT28.
The attribution does not surprise anyone with a mild connection to the infosec space, but it does mark the first time that French authorities have publicly attributed these hacks.
For the past 6-7 years, countries part of the Five Eyes intel-sharing alliance, and sometimes others like Japan, Germany, Poland, and the Netherlands, have repeatedly called out Russia for its overly aggressive hacks that often crossed diplomatic lines, going beyond espionage into the realm of sabotage and pure pettiness (see WADA and the other Olympics-related operations).
In most of those incidents, the French government, for reasons unknown, has not joined its Western allies.
The sudden change in policy is taking place for several reasons, which I'm now going to try and make an educated guess on.
For starters, France's cybersecurity agency has invested quite a lot of research time over the past years into studying Russian state operations. Its cybersecurity agency, ANSSI, has been publishing reports on Russian APT activity for several years. France is (still) one of the few countries that has a cyber unit (named VIGINUM) dedicated to studying online influence and disinformation operations. This research work is the basis of all state-backed attribution efforts. You can't blame countries for offensive cyber operations without doing the work before, and France has done so.
Second, France is actively trying to establish itself as Europe's new leader as the US is pulling from international politics. Calling out Russia for its past misdeeds is a good way to make friends in Europe these days.
Third, you need public statements of blame before putting out new sanctions, and there have been some rumblings among EU diplomat circles about new cyber sanctions being in the works.
Risky Business Podcasts
Risky Business is now on YouTube with video versions of our main podcasts. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
Marks & Spencer sends staff home after hack: British retailer Marks & Spencer has told 200 employees to stay home this week as the company is still dealing with the aftermath of a major cyberattack. The employees work for one of its logistics hubs in central England and deal with fulfilling online orders. The company stopped taking online orders last week after disclosing a security breach. Sources claim the incident was caused by a member of the Scattered Spider hacking group, who deployed a version of the DragonForce ransomware on the company's network. Marks & Spencer lost almost £500 million in market value due to the disruption. [Additional coverage in Sky News and Bleeping Computer]
SK Telecom to replace all customer SIM cards: South Korea's largest carrier, SK Telecom, will replace SIM cards for all customers following a data breach earlier this month. The company launched an online portal where customers can make reservations to have their SIM card replaced. SK is currently dealing with a SIM card shortage and can only provide replacements for 1 million of its 23 million customers. [Additional coverage in France24 and KBS]
4chan returns after hack: 4chan is back online after getting hacked by a rival forum earlier this month. The site also published a post-mortem of the hack.
Dutch DDoS attacks: Russian group NoName launched DDoS attacks and took down the public websites of several Dutch provinces. The attacks were confirmed by some provinces, such as Zeeland, Groningen, Noord-Holland, and Noord-Brabant. Outages didn't last more than five hours, though. [Additional coverage in AD.nl]
Indian websites defaced: Several Indian government websites have been defaced or targeted with DDoS attacks by Pakistan-linked hacktivist groups. The attacks are taking place in the aftermath of a terrorist attack that claimed the lives of 26 Hindu tourists in the city of Pahalgam last week. Indian authorities accused Pakistan of sponsoring the attack.
Iran repels cyberattack: The Iranian government claims it repelled a cyberattack on its critical infrastructure on Sunday. The attack allegedly happened a day after a major explosion and large fire at the Bandar Abbas container port. Officials described it as "one of the most widespread and complex cyber attacks" the country has faced. [Additional coverage in Iran International]
No cyberattack in Spain and Portugal power outages: Spanish officials have ruled out a cyberattack as the source of a major power outage that knocked out electricity across Spain and Portugal for most of the day on Monday, per the New York Times.
Loopscale crypto-heist: Hackers have stolen $5.8 million worth of crypto-assets from DeFi platform Loopscale. The attacker exploited a bug in one of the platform's price control contracts. The stolen assets represent almost 12% of the company's funds.
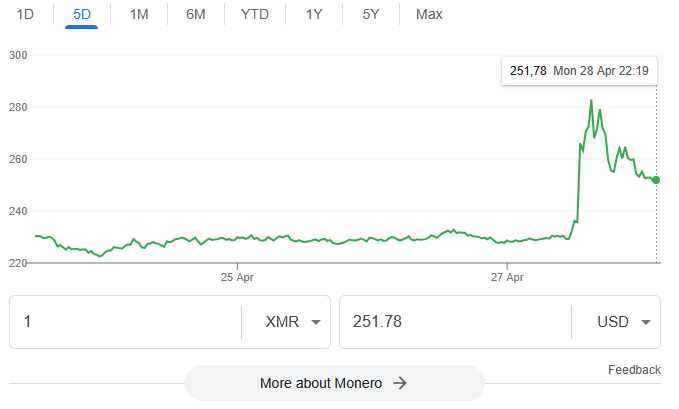
Monero price spikes after hack: The Monero exchange rate spiked by 50% on Monday after a hacker laundered the haul of a major heist. The mysterious attacker converted $330 million worth of stolen Bitcoin into the privacy coin. The funds were stolen on Sunday from a private, unnamed Bitcoin investor.
General tech and privacy
Android to block USB access on locked phones: Google is adding a new security feature to Android 16 that will block USB access on locked phones. The new feature is designed to protect phones against USB devices that can bypass lock screens and extract data from stolen or seized phones. Android 16 will be released later this year. The feature will be part of Advanced Protection Mode, Android's version of Apple's Lockdown Mode. [Additional coverage in Android Authority]
Meta chatbots will sex-talk minors: We all know Meta is a pretty shitty and creepy company by now, but there are always new lows. According to the WSJ, Meta has hit a new one with its "AI companions," which apparently can use celebrity voices and engage in spicy sex talks with underage users. How... on brand!
Law enforcement can retrieve car data: WIRED has obtained records showing how US cops are trained to retrieve data from modern, internet-connected cars—sometimes without even a warrant. This includes data from ISPs, car subscriptions, and tower dumps.
Warning about Chinese smart cars: A UK defense contractor has told staff not to charge or connect mobile phones to Chinese smart cars due to the risk of data theft and espionage. [Additional coverage in The i Paper]
Oracle blunder deletes data from 45 hospitals: Oracle engineers accidentally deleted the EHR data storage of 45 hospitals owned by US healthcare provider Community Health Systems. It took five days to restore the data, during which time all hospitals were sent back into the 80s and had to rely on pen and paper. Please sell TikTok to this company! Plz, plz, plz! [Additional coverage in Becker's Hospital Review]
Windscribe VPN case dismissed: A Greek court has dismissed a criminal case against Yegor Sak, the founder and CEO of VPN service provider Windscribe. Greek prosecutors sought a criminal conviction against Sak after his company failed to provide information on a customer who used Windscribe servers to send email spam. Sak argued he was innocent because Windscribe runs on a no-log policy, and there's no law requiring them to store logs.
Kali Linux changes signing key: The Kali Linux project changed its signing key after it "lost" the previous one.
Yahoo wants to buy Chrome: Yahoo (yeah, they're still around) has offered to buy Chrome if the DOJ forces Google to sell it. [Additional coverage in The Verge]
Government, politics, and policy
UK commissioner calls for ban on AI nudification tools: The UK Children's Commissioner has called for a ban on AI tools that can generate nude photos of children. Dame Rachel de Souza says "there is no positive reason for these particular apps to exist." De Souza urged the government to introduce a bill to force AI companies to introduce safeguards that prevent their tools from being used to nudify children's images. [Additional coverage in The Guardian]
Congress passes TAKE IT DOWN Act: The US Senate and House have passed the TAKE IT DOWN Act, a bill that criminalizes posting nonconsensual sexual images online, including deepfake content. The bill will require social media platforms to swiftly remove any reported content. The bill now heads to the White House to be signed into law. First lady Melania Trump supported the bill and President Trump said he would sign it.
House passes ROUTERS Act: The US House passed the ROUTERS Act, a bill that would instruct the US Department of Commerce to study the national security risks associated with routers and modems manufactured overseas.
India blocks ProtonMail: An Indian court has ordered a national block of secure email provider ProtonMail following a complaint from a local Indian architecture firm. Employees of New Delhi-based M Moser Design Associates claimed that ProtonMail refused to help identify the senders of obscene and vulgar content. The block has not yet been enforced. This is the second time that ProtonMail is blocked in India after a first attempt last year. [Additional coverage in TechCrunch]
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Edward Wu, founder and CEO of Dropzone AI. Edward talks about the impact of AI in modern-day SOC teams and how its role slowly becomes a force multiplier and productivity boost rather than workforce replacement.
Arrests, cybercrime, and threat intel
Poland dismantles cyber scam ring: Polish authorities have dismantled a cyber scam ring operating inside the country. The group stole $666,000 from victims by posing as police officers and bank employees. Authorities charged 46 individuals and detained 9. Most of the suspects were foreign nationals from Ukraine, Moldova, Georgia, and Azerbaijan.

Belarussian sentenced to prison for ransomware attacks: French authorities have sentenced a Belarussian man to five years in prison for ransomware attacks against French companies. Yauhen Horbach broke into companies via unsecured RDP connections and deployed a version of the Ako ransomware. Horbach used the hacker pseudonym of "JohnSmith" and worked with at least two other accomplices. He was detained in Georgia in August 2022 and extradited to France a year later to face charges. [Additional coverage in ZDNet France] [h/t Gabriel Thierry]
AT&T, Verizon hacker sentencing rescheduled: US authorities have rescheduled the sentencing of a notorious hacker for later this year as they bring in additional charges. Cameron Wagenius admitted in February to hacking US carriers AT&T and Verizon and leaking their data on hacking forums. Going online as Kiberphant0m, Wagenius was one of the two individuals who hacked cloud storage provider Snowflake, stole its data, and then tried extorting its customers last year. The sentencing meeting was set for September 10.
Scammer sentenced to eight years: US authorities have sentenced a Nigerian man to 97 months in prison for scamming elderly across the US.
Phisher sentenced in the Netherlands: Dutch authorities have sentenced a 24-year-old man to 18 months in prison on cybercrime charges related to planning bank fraud and phishing attacks.
FBI ran 17 disruptions last year: Speaking at RSA this week, FBI Deputy Assistant Director for Cyber Operations Crime Brett Leatherman said the agency conducted 17 operations to disrupt state-sponsored and cybercrime groups last year.
Pig butchering comes to Russia: Russian security firm Angara says investment and romance scams carried out by cyber scam call centers across Southeast Asia are now regularly targeting Russian citizens. [Additional coverage in Ria Novosti]
FBI swatting alert: The FBI has issued an alert on the widespread use of swatting these days.
FBI releases LabHost domains: The FBI released a list of 42,000 phishing domains linked to the LabHost phishing-as-a-service (PhaaS) platform, which they seized last April. [Alert PDF/Actual list CSV]
Threat actors sell access to EDR admin panels: Threat actors are compromising and selling access to EDR admin panels from where companies manage their infrastructure. The panels are used to disable protections for a company, hide alerts, and test attacks. Security firm SentinelOne has spotted ads that sell access to EDR panels for its own products, but also Microsoft, CrowdStrike, Fortinet, and Check Point. Access to these panels is acquired through infostealer logs or by bribing employees. In addition, threat actors are also renting access to EDR testing environments in what could be called EDR-Testing-as-a-Service platforms.

Reckless Rabbit and Ruthless Rabbit: Infoblox has published a report on Reckless Rabbit and Ruthless Rabbit, two threat actors running investment scams across Europe.
SessionShark PhaaS: SlashNext has discovered a new PhaaS named SessionShark.
Scam Empire VoIP providers: Qurium looks at five VoIP providers who worked with a major cyber scam operation known as the Scam Empire.

Grinex linked to Garantex: TRM Labs claims the new Grinex cryptocurrency exchange is a rebrand of Garantex, a Russia-based exchange that was sanctioned and taken down by US authorities earlier this year.
Git config scan spike: Security firm GreyNoise reports seeing increased scan activity searching for exposed Git config files.
Minhook campaign: Sophos looks at a mysterious campaign that was using a rare DLL sideloading technique and which suddenly switched to targeting entities in Sweden after spending months going after Chinese and Taiwanese targets.
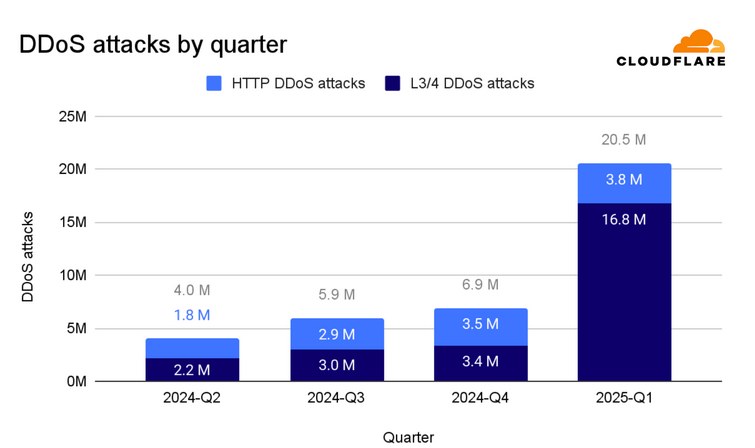
State of DDoS attacks: Internet infrastructure company Cloudflare says it mitigated more DDoS attacks in Q1 2025 than all of last year combined. One of those attacks peaked at 5.8 Tbps, the largest DDoS attack ever recorded. The most complex DDoS campaign lasted 18 days, targeted Cloudflare infrastructure directly, and accounted for almost a third of all attacks this year.
Malware technical reports
Pentagon Stealer: ANY.RUN has published a technical breakdown of Pentagon Stealer, a Python and Golang-based infostealer.
Gremlin Stealer: PAN Unit42 researchers look at Gremlin Stealer, a new C# infostealer that popped up for sale in Telegram channels last month.
Hannibal Stealer: And there's another one of these s**t stealers, this one coded in C# and named Hannibal Stealer. Truly, infostealers are modern-day cyber roaches! You just can't get away from them.
Fog affiliate leak: The DFIR Report team has published a report on the contents of an open directory that stored tools and scripts used by one of the Fog RaaS affiliates.
Outlaw crypto-miner: Kaspersky has published a technical breakdown of Outlaw, a crypto-mining botnet currently going through a revival.
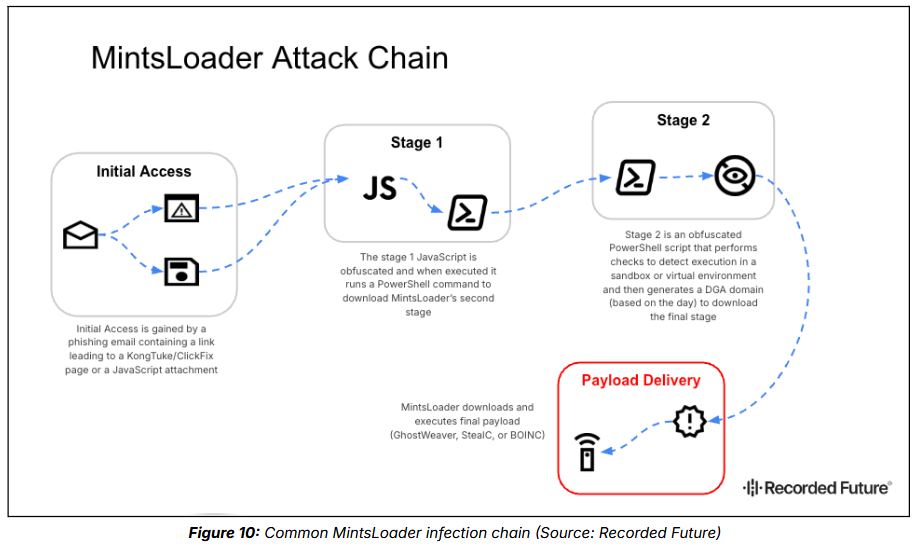
MintsLoader: Recorded Future has discovered a new malware strain named MintsLoader. The malware has been traced back to phishing and drive-by download campaigns dating back to last year. It's typically used to deliver various backdoors and infostealers. Its main customer appears to be the TAG-124 group.
Sponsor section
COACH is an AI-powered security mentor that guides SOC analysts through alert investigations, turning every security alert into a learning opportunity. Available as a free Chrome extension with zero data retention
APTs, cyber-espionage, and info-ops
China accuses US of hacking encryption provider: Chinese authorities have accused US intelligence services of hacking a major Chinese cryptography provider. The hack allegedly took place between March and September last year. US hackers allegedly exploited a zero-day in the company's CRM app to deploy backdoors and steal data. Stolen data included source code, customer data, and order details. [Additional coverage in ECNS and Global Times]
New Uyghur spying: Hackers likely aligned with the Chinese government infected members of the Uyghur minority with malware. The operation targeted senior members of the World Uyghur Congress (WUC) living in exile in Europe. According to CitizenLab, hackers allegedly hid the malware inside trojanized versions of a popular Uyghur word processing and spell check tool.
Salt Typhoon: Censys has published a pretty comprehensive report on the few IOCs connected to Salt Typhoon, the Chinese APT behind the hacks of several US telcos last year.
Vulnerabilities, security research, and bug bounty
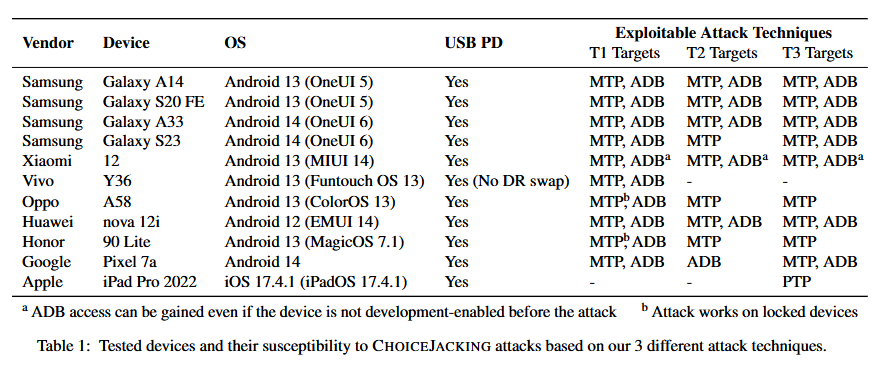
ChoiceJacking attack bypasses juice jacking defenses: A team of academics from the Graz University of Technology has developed an attack named ChoiceJacking that can bypass juice jacking defenses in modern smartphones. The attack allows a malicious charger to access data on a connected smartphone. ChoiceJacking exploits implementation loopholes in Android and iOS. Both Google and Apple released security updates last year to block the attack. [Additional coverage in ArsTechnica/Full paper PDF]
AirBorne vulnerabilities in AirPlay: Oligo security researchers have disclosed over two dozen vulnerabilities in the Apple AirPlay protocol and SDK. Collectively named AirBorne, the vulnerabilities can allow attackers on the same network to run malicious code on any Apple device that supports AirPlay. Some of the bugs require no interaction and can be chained in wormable exploits that spread on their own as users travel between WiFi networks. Apple released fixes for all throughout the past months.
Telegram vulnerability: There's apparently some infosec drama in Russia where Telegram is denying a report from an anonymous security researcher who claimed you can access user accounts without a password or MFA challenge. [Additional coverage in SecurityLab]
Vaultwarden bug write-up: Russian security firm BI.ZONE analyzes two Vaultwarden vulnerabilities that were disclosed by security researcher Dani Garcia earlier this year. The two, an EoP and RCE, can be combined to take over the password manager's server. The company looked at the two because of the password manager's popularity inside Russia.
GFI MailEssentials vulnerabilities: Code White security researcher Frycos has helped patch three vulnerabilities in the GFI MailEssentials email malware scanning engine.
KEV update: CISA has updated its KEV database with three vulnerabilities that are currently exploited in the wild. All are 2025 bugs—in Brocade switches, Commvault backup servers, and Active! Mail email servers.
JPMorgan CISO tells SaaS providers to bolster security: In an open letter, JPMorgan CISO Patrick Opet has urged SaaS providers to invest and prioritize cybersecurity before their products become a weak point in the global economic system.
"We must establish new security principles and implement robust controls that enable the swift adoption of cloud services while protecting customers from their providers' vulnerabilities. Traditional measures like network segmentation, tiering, and protocol termination were durable in legacy principles but may no longer be viable today in a SaaS integration model. Instead, we need sophisticated authorization methods, advanced detection capabilities, and proactive measures to prevent the abuse of interconnected systems."
AWS default roles problems: AquaSec researchers have found that several AWS services deploy service roles with overly broad permissions, including full access to S3 buckets. This included service roles for AWS CDK, AWS Glue, AWS Lightsail, AWS EMR, and AWS SageMager. Amazon restricted some roles and updated its documentation to warn customers where it could not change permissions.
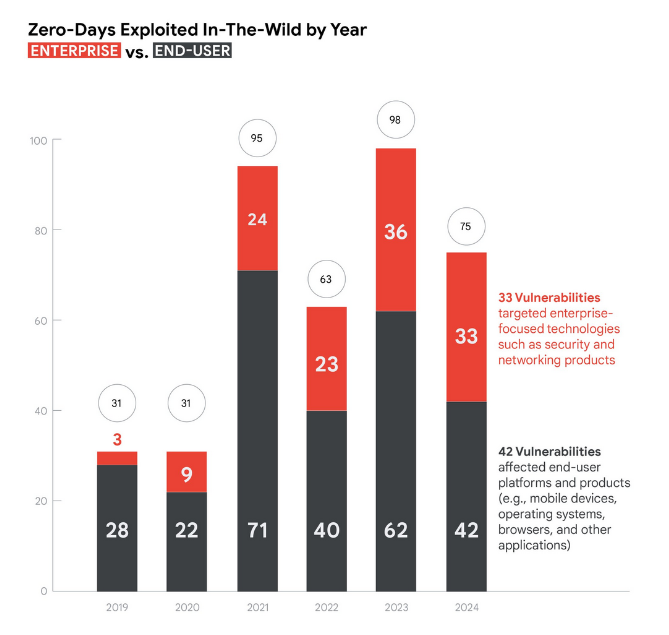
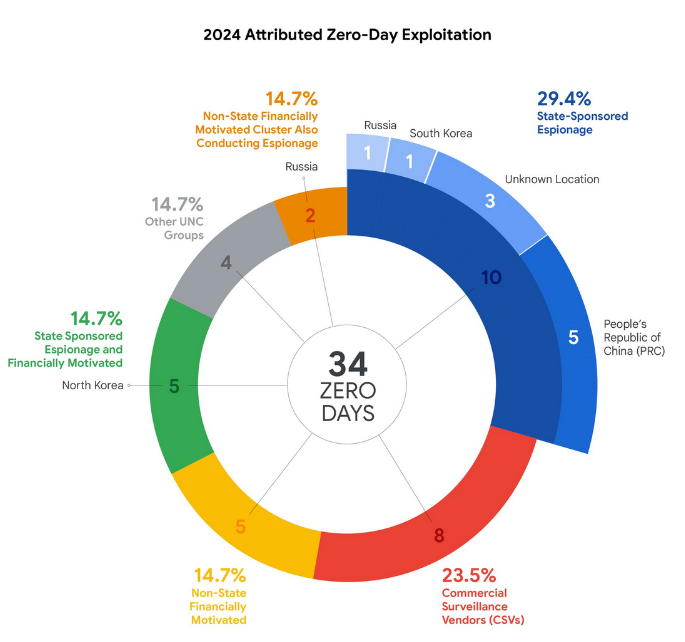
75 zero-days exploited last year: Threat actors exploited 75 zero-days last year, with 33 of those targeting enterprise products. Windows was the most targeted product, accounting for a third of all zero-days last year. Most zero-days were used individually and exploit chains were mostly used in attacks against mobile devices. According to Google, cyber-espionage groups remain the top group behind zero-day attacks.
Infosec industry
Acquisition news: Palo Alto Networks has announced plans to acquire AI security company Protect AI.
EFF calls for support for Chris Krebs: Over 40 infosec experts have signed an open letter asking the White House to end its investigation of former CISA Director Chris Krebs. The EFF is keeping the letter open and is encouraging others to add their names to it.
Sign your names or you’re a toaster, American cyber pros. https://www.eff.org/press/releases/eff-leads-prominent-security-experts-urging-trump-administration-leave-chris-krebs
— Lesley Carhart :unverified: (@hacks4pancakes.infosec.exchange.ap.brid.gy) 2025-04-29T03:34:41.000Z
New tool—EntraFalcon: Security firm Compass Security has released EntraFalcon, a PowerShell toolkit to evaluate the security of a Microsoft Entra ID environment.
New tool—HANAlyzer: Security firm Anvil Secure has released HANAlyzer, a tool to audit SAP HANA databases.
New tool—KYE: Cloud security firm Zoph has released KYE (Know Your Enemies), a tool to analyze IAM Role trust policies and S3 bucket policies in an AWS account to identify third-party vendors with access to your resources.
New tool—Fake-SystemUpdate-Malware-Simulator: Security researcher Alhanouf Alshaikh has released Fake-SystemUpdate-Malware-Simulator, a proof-of-concept malware disguised as a fake system update executable.
Threat/trend reports: Cloudflare, Fortinet, KELA, Netscout, OpenLogic, Trellix, US NIST, and Zimperium have recently published reports and summaries covering various infosec trends and industry threats.
Risky Business podcasts
Tom Uren and Adam Boileau talk about how scam compound criminal syndicates are responding to strong government action by moving operations overseas. It's good they are being affected, but they are shifting into new countries that don't have the ability to counter industrial-scale transnational organized crime.
In this edition of Between Two Nerds, Tom Uren and The Grugq discuss the Southeast Asian criminal syndicates that run online scam compounds. Should organizations like US Cyber Command or the UK's National Cyber Force target these gangs with disruption operations?
