Risky Bulletin Newsletter
February 03, 2025
Risky Bulletin: CISA & FDA warn of backdoor in patient monitor
Written by

News Editor
This newsletter is brought to you by Thinkst, the makers of the much-loved Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
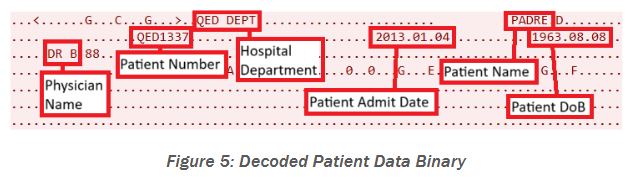
The US government warns that Contec patient monitors contain a backdoor that collects and sends patient data to a remote Chinese IP address and can even secretly download and execute files.
The US Food and Drug Administration (FDA) and the Cybersecurity and Infrastructure Security Agency (CISA) published security alerts last week warning hospitals to disconnect devices from the internet.
The backdoor behavior has been confirmed in Contec CMS8000 patient monitors, but officials say the devices are often re-labeled and sold under other names, such as Epsimed MN-120.
In a technical report [PDF], CISA says it learned of the backdoor from an anonymous security researcher who analyzed recent versions of the Contec firmware.
The researcher found that once Contec devices were connected to the internet, they would take all stored data and send it at regular intervals to the remote IP on port 515.
The researcher also found a hidden mechanism that could copy files from the same IP address and run the file on the system.
CISA says this system "lacks features commonly associated with update mechanisms," such as first checking what firmware version is already running on the device or checking the integrity and authenticity of the downloaded files.
While CISA did not share the IP address embedded in the firmware, former Kaspersky GReAT head Costin Raiu has identified it as 202.114.4.119.
The IP address is currently assigned to CERNET, a Chinese educational and research network managed by the Tsinghua University in Beijing.
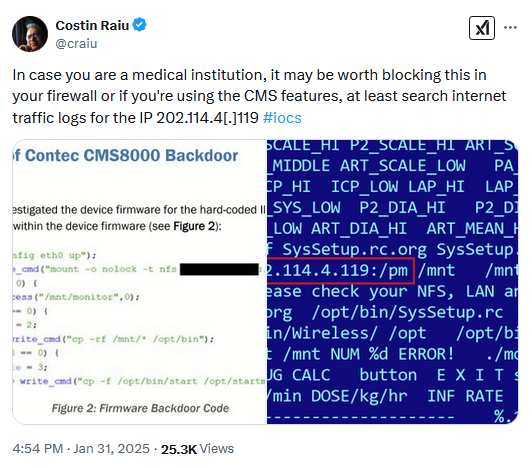
A Google search for this IP address surfaces installation manuals for multiple patient monitor brands—most likely re-labeled Comtec devices.
The IP address is used in connection to a system named the Central Monitoring System (CMS) that aggregates data from a hospital's local patient monitors. Apparently, everything that was aggregated through the CMS was also sent to the remote IP address as well. Backdoor, bad engineering, or a hidden free data analytics pipeline—at this point, it could be one of them or all three at once.
Risky Business Podcasts
Risky Business is now on YouTube with video versions of our main podcasts. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
USAID breach: Hackers breached the US Agency for International Development agency last fall and abused its cloud infrastructure to deploy cryptocurrency miners. The incident incurred around $500,000 in cloud service charges to the agency. The breach was traced back to a brute-force attack that guessed the password to a global administrator account in one of the USAID test environments. [Additional coverage in FedScoop]
Tata ransomware attack: A ransomware attack has impacted several IT systems as Tata Technologies, one of India's ten largest companies. The company took down affected systems and said that no customer services have been impacted. Tata Technologies is a subsidiary in the Tata group that provides engineering services for the automotive and aerospace sectors. [Additional coverage in the Business Standard]
Apex Custom Software hack: Hackers have breached and leaked the code of Texas-based healthcare software provider Apex Custom Software. [Additional coverage in DataBreaches.net]
Gazprom DDoS attack: Ukraine's military intelligence service has allegedly conducted a DDoS attack against the IT network of Gazprom. [Additional coverage in the Kyiv Independent]
Twitter account hacks: Multiple high-profile accounts have been hacked over the past week to promote various memecoins. Known victims so far: Snopes, TIME Magazine, the NASDAQ, the Tor Project, threat intel firm FalconFeeds, former Brazilian president Jair Bolsonaro, Twitch streamer Asmongold, sports journalist Jemele Hill, Breaking Bad actor Dean Norris, and various crypto-bro and smaller accounts.
DeepSeek DDoS attacks: Chinese AI platform DeepSeek has been dealing with a week-long DDoS attack that has targeted its API and public-facing websites. The attacks started on January 25 and took place in small bursts of massive traffic of over 30 minutes or more. According to security firm NSFOCUS, the attacker showed "great pertinence and high tactical literacy."
Casio website skimmer: Security firm Jscrambler has found a web skimmer installed on the website of Casio UK. The same skimmer was also found on 16 other websites and was observed sending collected payment data to a Russian IP address.
AngelSense leak: GPS tracking service AngelSense has accidentally exposed an internal database with the personal and location details of thousands of users. Security firm UpGuard says the leak originated with an ElasticSearch database hosting over 120 million log entries. The exposed data ranged from real names to home addresses, GPS coordinates, and even account passwords. The AngelSense app is advertised as a real-time tracker for children and adults with special needs. [Additional coverage in TechCrunch]

General tech and privacy
Amazon Redshift secure defaults: AWS is enforcing new secure defaults for all new Redshift data lakes. The new defaults include disabling public access, enabling database encryption, and enforcing secure connections for all new instances. The new settings will also apply to clusters restored from snapshots.
New Chromium text contrast: Microsoft says it rolled out a new text rendering engine for all Chromium-based browsers that features improved text contrast.
OAuth 2.0 Security becomes an RFC: A guide on how to properly secure OAuth 2.0 systems is now an official IETF standard as RFC 9700.
Government, politics, and policy
Europol blames data volume and encryption: Europol and Eurojust say that massive volumes of data and anonymization and encryption services are their primary challenges in fighting cybercrime operations. The two bodies say that many law enforcement agencies do not have the resources to either store or process vast quantities of data needed to tackle cybercrime. Agencies cited technical difficulties in dealing with carrier-grade NAT, anonymized WHOIS databases, and new and more secure DNS technologies. Europol has also asked lawmakers to find lawful ways to access encrypted communication. This marks the second year in a row when Europol made the demand in an official report.
Poland arrests ex-minister in Pegasus probe: Polish authorities have arrested the country's ex-justice minister on charges of using the Pegasus spyware to spy on the opposition. Zbigniew Ziobro was arrested Friday in Warsaw after leaving the headquarters of a right-wing TV station. He was justice minister's between 2017 and 2023 and the country's previous government led by the Law and Order (PiS) party. Under his watch, law enforcement agencies acquired the spyware and used it to spy on over 600 targets. [Additional coverage in Onet/English coverage in Anadolu Agency]
CISA workers exempt from resignation program: CISA workers have been told they are not eligible for a government worker resignation program put forward by the Trump administration. The program will allow government workers to retain their pay and benefits until the end of September if they resign by February 6. In an email last week, CISA told employees they are considered national security staff and are not eligible for the program. [Additional coverage in The Record]
Cyber scam international coordination center: Law enforcement agencies from 18 countries have launched an international coordination center to combat online cyber scam operations. The center will operate from Thailand, one of the hotspots for such activity. Members include China, Russia, the US, and several Southeast Asian nations. [Additional coverage in Khaosod]
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Thinkst CTO Marco Slaviero about a concept called Defending off the Land, a way to detect attacks and even deceive and frustrate attackers.
Arrests, cybercrime, and threat intel
WhatsApp detects Paragon attacks: Over 90 journalists and members of civil society have been targeted with spyware made by Israeli company Paragon Solutions. The attacks allegedly used a zero-click exploit. Victims received malicious documents sent via WhatsApp that deployed Paragon's new Graphite spyware. Meta sent Paragon a cease-and-desist letter and is now notifying targeted users. US private investment company AE Industrial Partners acquired Israeli spyware company Paragon Solutions last year for $900 million. [Additional coverage in The Guardian]
Turkiye arrests state DB hackers: Turkish authorities have arrested a cybercrime group that breached MERNIS, a government database that stores information on citizens and their ID numbers. Officials say the group ran queries on the database for money, and the data was used for making threats and blackmail. Forty-four suspects were placed under arrest, and six were released under judicial control. [Additional coverage in Anadolu Agency]
FUNNULL: Security firm Silent Push has discovered a Chinese CDN that rents IPs from major cloud providers and makes them available to various cybercrime operations. Named FUNNULL, the company has hosted phishing portals, online romance scams, and gambling sites linked to money laundering operations. Most of FUNNULL's rented IP spaces belonged to major providers such as AWS and Azure.
New npm malware: Six malicious npm packages were discovered and taken down last week. Check out the GitHub security advisory portal for more details.
Google malvertising campaign: Malwarebytes has discovered a coordinated Google Ads malvertising campaign targeting owners of Microsoft Ads (formerly Bing Ads) accounts.
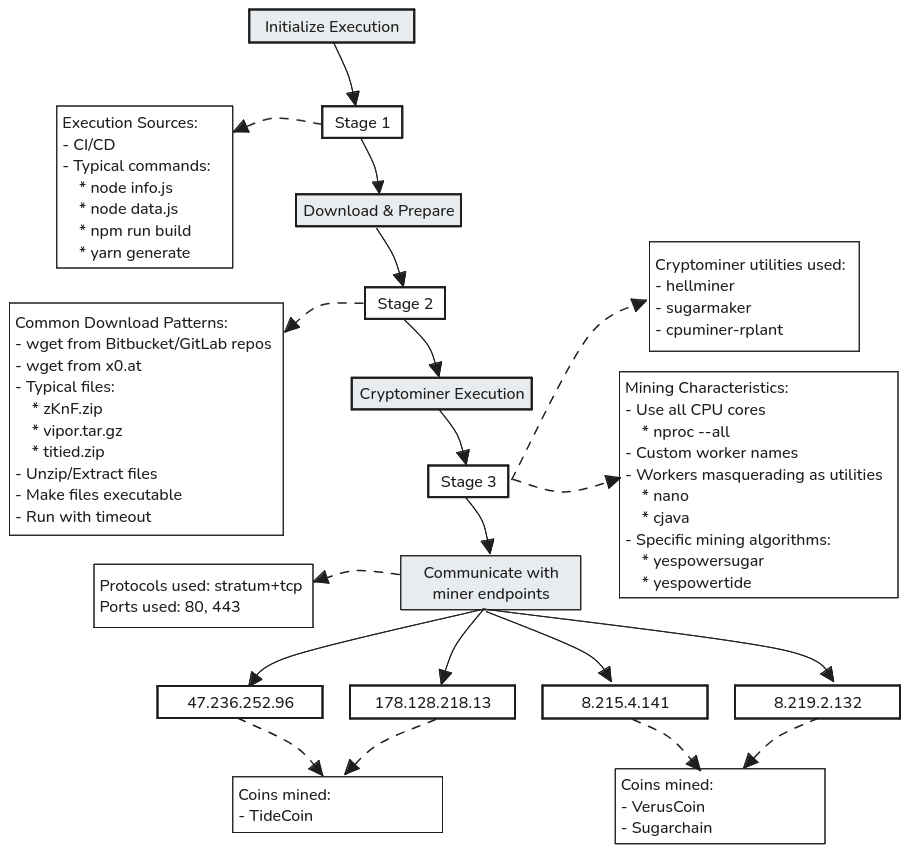
Cryptomining campaign: Netlify researchers have spotted a new cryptomining campaign targeting cloud SaaS infrastructure since July 2021, with several activity spikes last fall. [h/t Mike Gualtieri]
Malware technical reports
Banshee rewritten in Rust: After the Objective-C source code of the Banshee macOS infostealer was leaked online, Kandji researchers discovered a new version of the infostealer written in Rust.
WantToCry ransomware goes after NAS devices: The WantToCry ransomware gang is hacking systems with misconfigured SMB shares to encrypt files and demand ransom payments. According to security firm Seqrite, the group gains access to systems via SMB services left exposed on the internet with no authentication or with weak or default passwords. Once inside, the gang encrypts any shared drives and connected NAS devices. The WantToCry group has been active since late 2023 but has recently intensified attacks.
Lockbit: Red Sense researchers have published a report on the Lockbit gang and its RaaS operation.
AsyncRAT: Forcepoint looks at a new AsyncRAT version that uses Python tools and TryCloudflare tunnels to avoid detection.
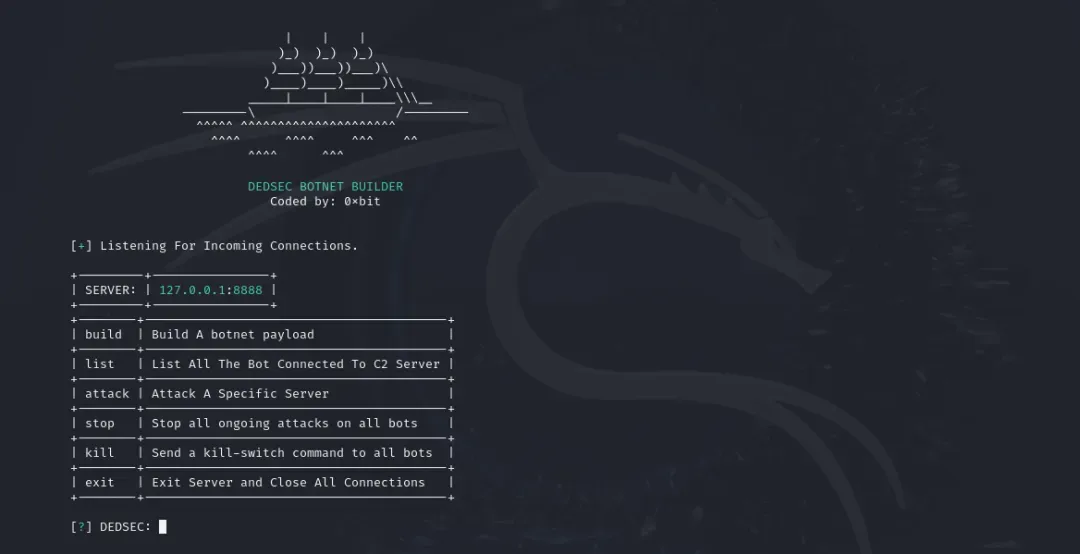
DEDSEC_BOTNET: Panda Zhengzheng researchers have published a report on DEDSEC_BOTNET, a builder for creating IoT/DDoS malware payloads and a backend for controlling the bots.
Sponsor section
In this Soap Box edition of the podcast, Patrick Gray chats with Thinkst Canary founder Haroon Meer about his "decade of deception."
APTs, cyber-espionage, and info-ops
Rezet: Russian security firm FACCT has published a report on Rezet, an APT group targeting Russian companies. The group has been active since October 2018 and is also known as Rare Wolf.
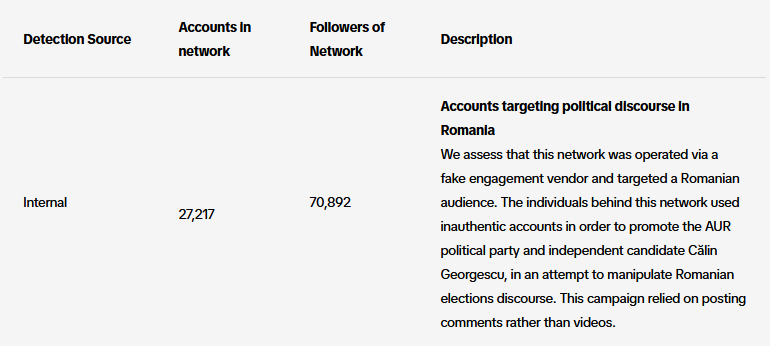
TikTok info-ops summary: TikTok has published its monthly report on covert influence operations the company has spotted on its platform. TikTok botnets taken down last month targeted Romania, Moldova, Indonesia, Irak, and Ukraine. All campaigns were designed to manipulate political speech in those countries. Many were run by political parties from those countries.
Vulnerabilities, security research, and bug bounty
Crescendo jailbreak: PAN Unit42 researchers have published details on Crescendo, a new LLM jailbreaking technique—this one tested against DeepSeek. Two previous jailbreaking techniques named Deceptive Delight and Bad Likert Judge also worked against DeepSeek.
RCE in NetAlertx: Rhino Security has discovered a remote code execution bug (CVE-2024-46506) in NetAlertx, an open-source Wi-Fi / Local Area Network (LAN) intruder detector.
Marvel Rivals LAN RCE: A group of security researchers have found a LAN-exploitable RCE in Marvel Rivals, one of today's most popular FPS games.
BIND9 security updates: The BIND project has released security updates for its DNS server technology.
VMware security updates: VMware has released security updates for its Aria products.
GarageBand security update: In a rare patch, Apple has released a security update for its GarageBand app to address a vulnerability that could have allowed a maliciously crafted image to execute code on a user's device.
Infosec industry
Threat/trend reports: CIS, IBM+Palo Alto Networks, ImmuneFi, NCC Group, Spamhaus, and VulnCheck have published reports and summaries covering various infosec trends and industry threats.
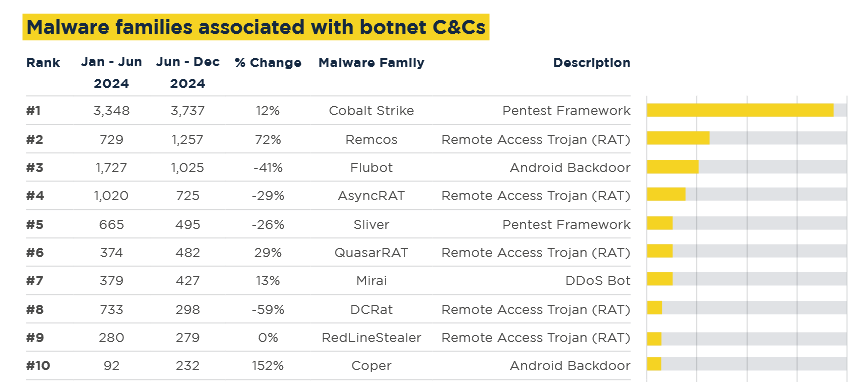
New tool—Adaptix: Pen-tester RalfHacker has released Adaptix, an extensible post-exploitation and adversarial emulation framework made for penetration testers.
New tool—Rösti: Security researcher Johannes Bader has released Rösti (Repackaged Öpen Source Threat Intelligence), a tool that scans infosec reports and extracts IOCs and YARA rules.
LABScon24 videos: Videos from SentinelOne's LABScon 2024 security conference, which took place last September, are slowly making their way on YouTube—see bottom of this playlist.
Risky Business Podcasts
In this podcast, Tom Uren and Adam Boileau talk about the continued importance of hack and leak operations. They didn't really affect the recent US presidential election, but they are still a powerful tool for vested interests to influence public policy.
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about the evolution of Russian cyber operations during its invasion of Ukraine.
