Risky Bulletin Newsletter
August 27, 2025
Risky Bulletin: FCC removes 1,200 voice providers from US phone network
Written by

News Editor
This newsletter is brought to you by Okta. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
The US Federal Communications Commission has banned more than 1,200 voice service providers from the US telephone network after they failed to deploy robocall protections.
The number is almost half of the 2,411 voice providers the agency notified and ordered last year to become compliant with its new anti-robocall rules.
Voice providers had to deploy the STIR/SHAKEN protocol, provide accurate registration and ownership details, and a contact for reporting robocall abuse and issues.
STIR/SHAKEN deployment was the main issue here—a suite of telephony security protocols that use digital certificates and cryptography to authenticate callers and prevent caller ID spoofing.
Providers that filed all the needed paperwork were included in the FCC Robocall Mitigation Database, which verified their compliance with the agency's rules.
The FCC has now removed the 1,200+ providers from this same database, which means the other providers will refuse to route their traffic.
The big ban comes after an initial test earlier this month, when the FCC removed an initial 185 providers.
The ban marks a first major victory for the agency against robocallers and the providers that unabashedly support their services and abuse.
The FCC has been trying to crack down on robocallers for almost a decade and is now reaping its first rewards after years of lobbying telcos to adopt STIR/SHAKEN.
According to the agency's yearly report, the number of robocall complaints has been steadily going down since 2021, a year after it passed rules requiring telcos to implement the protocol.
Risky Business Podcasts
The main Risky Business podcast is now on YouTube with video versions of our recent episodes. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
Salesloft hack: Hackers have breached sales AI and automation platform Salesloft and pivoted to its customers' Salesforce accounts. The attackers are harvesting Salesforce data and other credentials to pivot to other cloud platforms. Google says the attackers pivoted to Salesforce using OAuth tokens from the Salesloft AI chat agent. Salesloft has now revoked all Drift Salesforce connections and asked customers to reauthenticate and reconnect their apps. Google linked the attack to a group it tracks as UNC6395.
Farmers Insurance breach: Hackers have stolen the data of 1.1 million Farmers Insurance customers. The breach took place at the end of May and targeted the company's Salesforce account. According to the company's data breach notification letter, stolen data includes names, addresses, dates of birth, driver's license numbers, and the last four digits of Social Security numbers.
Rimon ISP hacked: An Iranian hacking group has claimed responsibility for an attack on Israeli internet service Rimon. The company's services have been down since the attack on August 23. A group named Promised Revenge has taken credit for the attack. Rimon is a so-called "kosher" ISP that intercepts and heavily filters internet traffic for the orthodox jew community. [Additional coverage in Israel National News] [h/t DataBreaches.net]
Mysterious Russian TV station hack: The Kyiv Independent has a report on a mysterious group of Russian partisan hackers who hacked an unnamed local TV station to broadcast "the truth" about Russia's war in Ukraine. [h/t DrDoctor]
Maryland Transit Administration cyberattack: A cyberattack has disrupted the activity of the Maryland Transit Administration. Core public transportation services were not affected. The incident mainly impacted Mobility, a system used to organize transportation for disabled people. No threat actor has taken credit for the attack. [Additional coverage in The Record]
Nevada government cyberattack: The Nevada state offices and public counters were closed on Monday and Tuesday after a cyberattack on the state government's network. The incident took down official websites, phone lines, and several backend systems. The state did not provide details about the nature of the cyberattack, but ransomware is very likely due to the sprawling nature of the outage. [Additional coverage in Carson Now] [h/t Troy]

General tech and privacy
Aussie uni tracked protesters with WiFi network: The Office of the Victorian Information Commissioner in Australia has declined to go after the University of Melbourne for using WiFi signals to track and identify the participants of a sit-in protest last year. [h/t TigrayMM]
Microsoft asks FBI for help: According to Bloomberg, Microsoft has asked the FBI for help to track and identify employees who participated in anti-Israel protests on its campus.
Flock stops government cooperation: License plate reader provider Flock paused its cooperation with US law enforcement after reports that ICE and other agencies were using its tools to track immigrants. [Additional coverage in Yahoo News]
YouTube tampered with people's videos: According to reports, YouTube used AI tools to modify some of its creators' videos without telling them. The company said it only used tools that reduced blur and audio noise. [Additional coverage in ArsTechnica]
New Android developer verification feature: Google will verify the real-world identities of all Android app developers starting September 2026. The new rule will apply to all apps, even those distributed outside of the official Play Store. Future Android OS versions will not load apps from unverified developers. The developer verification process will open in March next year. It will go into effect in September in four countries, with more being added gradually in the following months. The initial countries are Brazil, Indonesia, Singapore, and Thailand.
Even if they're trying to "combat fraud' by getting a corporate ID registered (DUNS), this immediately halts tons of 3rd party devs who do not even have a registered company of any kind, while also failing to actually stop fraud since fraudsters are used to using shell companies and hidden behavior
— Natanael, Tech janitor (@natanael.bsky.social) 2025-08-25T19:24:13.910Z
Government, politics, and policy
US AGs warn AI chatbot makers: Attorneys General from 44 US states have sent letters to 11 AI chatbot and social media companies. Officials pledged to go after companies that develop AI chatbots that engage in harmful behavior against children and teens. The letter comes after reports that Meta's AI chatbot engaged in sexually inappropriate conversations with kids. The letter was sent to Anthropic, Apple, Chai AI, Google, Luka Inc., Meta, Microsoft, Nomi AI, Open AI, Perplexity AI, Replika, and xAI.
Keep Call Centers in America Act: Two US lawmakers have introduced a bill to require American companies to locate call centers in the country. The Keep Call Centers in America Act will also require companies to disclose upfront if users will be talking to AI. Companies with existing call centers overseas will be required to move them to the US and notify the Department of Labor.
Trump threatens sanctions over EU DSA: The White House has threatened EU officials with sanctions if they enforce the EU Digital Services Act on US tech companies. This is the least unhinged thing that came out of the White House this week. [Additional coverage in Reuters]
The DSA doesn’t “censor Americans”. The people who’ve been pushing this BS the longest have been Michael Shellenberger, CBR Chair of Censorship Hoaxes at UATX, and Mike Benz aka Frame Game, who thought Hitler had some good points & wants to help his far right friends www.reuters.com/world/us/tru...
— Renee DiResta (@noupside.bsky.social) 2025-08-26T11:26:36.790Z
Russia does a China: Security cameras deployed across Sankt Petersburg now have an ethnicity facial recognition feature, similar to the one deployed across China. [Additional coverage in 78.ru]
Russia's Max app tracks everything: The Russian government's Max app is constantly monitoring and logging all user activity. According to a technical analysis received by Forbes, the app doesn't use encryption and tracks user location in real-time and with high accuracy. The app has been made mandatory and must be installed on all mobile devices sold in Russia after September 1. In other totally normal news, the Russian Orthodox Church called for Russians to pray for the messenger.
🚨NEW🚨 Russia is mandating a new VK messaging app called Max. We had some researchers take a look and—surprise, surprise—it's tracking basically everything users do. “This app just gathers all the data and logs it. I don’t remember seeing that in any messenger app." www.forbes.com/sites/thomas...
— Thomas Brewster (@thomasbrewster.bsky.social) 2025-08-26T18:24:09.836Z
Sponsor section
In this Risky Business sponsor interview, Tom Uren talks to Brett Winterford, Okta's VP of Threat Intelligence, about FastPass. Brett explains what it is, how Okta uses it, and why threat actors avoid it.
Arrests, cybercrime, and threat intel
DSLRoot profile: Brian Krebs looks at DSLRoot, an online service that pays users to host laptops at their homes in some sort of weirdly run residential proxy network. The network seems to have connections back to Moscow.
ShadowCaptcha campaign: Israel's National Digital Agency has sent out a warning about the increase in ClickFix campaigns.
Google Classroom phishing abuse: Threat actors are piggybacking on the infrastructure of Google Classroom to send out spam and phishing emails. Check Point has spotted a campaign that sent over 115,000 emails to more than 13,500 organizations this month.
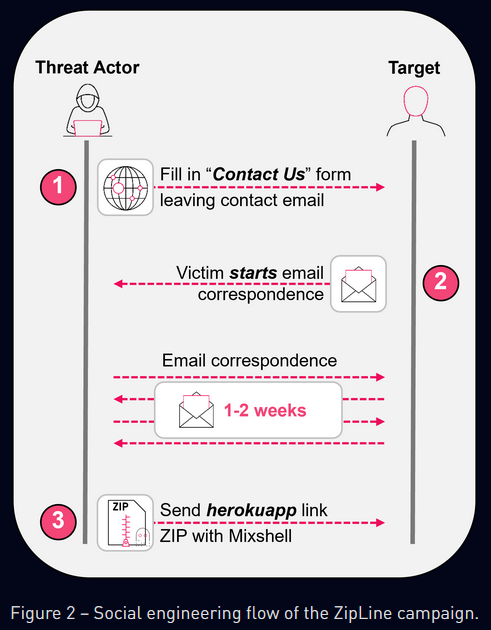
ZipLine campaign: Check Point has spotted a stealthy spear-phishing campaign targeting the supply chain of critical manufacturing companies in the US. The campaign leverages long conversation threads before tricking victims into running malicious ZIP files that deploy the Mixshell malware.
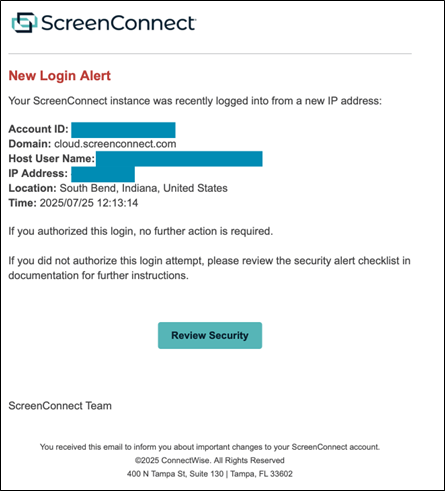
Low-volume ScreenConnect phishing campaign: A long-running spear-phishing campaign is targeting ScreenConnect cloud administrators. The campaign has been active since 2022 and targets up to 1,000 accounts per run. It uses fake ScreenConnect security alerts to lure ScreenConnect admins to phishing sites that intercept credentials and MFA challenges. The compromised accounts have been used as an initial access and entry point for ransomware attacks. The campaign was spotted by Mimecast, but there's also a different one targeting ScreenConnect admins with other lures, spotted by AbnormalAI.
Malware technical reports
PromptLock ransomware: ESET researchers have spotted a ransomware strain named PromptLock that uses LLMs to generate malicious Lua scripts that enumerate, steal, and encrypt data.
#ESETResearch has discovered the first known AI-powered ransomware, which we named #PromptLock. The PromptLock malware uses the gpt-oss:20b model from OpenAI locally via the Ollama API to generate malicious Lua scripts on the fly, which it then executes 1/7
— ESET Research (@esetresearch.bsky.social) 2025-08-26T15:37:50.069Z
Cephalus ransomware: Huntress researchers have discovered a new ransomware strain going by the name of Cephalus. The group seems to use compromised RDP accounts for initial access and does not operate a leak site (yet).
Trigona ransomware: Security researcher Cryptax has published a technical report on the Trigona ransomware.
Underground ransomware: The Team Underground ransomware group has had a recent resurgence in activity, per AhnLab. The group launched last year and had gone semi-dormant for the past months.
Warlock ransomware: Quorum Cyber has published a threat actor profile on the Warlock ransomware group.
RewardDropMiner: ThreatFabric has spotted a new Android dropper and cryptominer named RewardDropMiner.
UpCrypter: Fortinet's security team has spotted phishing campaigns delivering a new loader named UpCrypter. The final payloads are various RATs.
Hook banking trojan: Zimperium has spotted version 3.0 of the Hook Android banking trojan. The new version supports ransomware-style overlays that display extortion messages and fake NFC overlays to trick victims into sharing sensitive data.
Sponsor section
In this sponsored product demo, Okta's Harish Chakravarthy and Brett Winterford walk through four new features Okta introduced in the wake of the emergence of modern attacker techniques targeting identity providers. These features will help you to prevent or limit the damage to your environment if an attacker manages to compromise a session token. If you're an Okta shop, you should absolutely watch this video.
APTs, cyber-espionage, and info-ops
FIMI report on Polish elections: DFRLab has published a report on the foreign information manipulation and interference (FIMI) during the 2025 Polish presidential election. It's Russia. All of it.
Romania/Moldova info-op campaign: A network of pro-Russian accounts has been pushing an influence operation targeting Romanian-speaking audiences in Moldova and Romania, claiming that Moldovan President Maia Sandu meddled in Romania's presidential election against the pro-Kremlin candidates. The same network later switched to showing support for several pro-Kremlin figures detained in Moldova and in promoting a "#StopCensorship" campaign and a #NoToTheEU" campaign. Gee, I wonder who's behind this campaign!
"Altogether, the evidence gathered shows that a complex and industrialized disinformation community, active in Moldova, has deployed known methods to impersonate and mislead online audiences. That involved accusing heads of state of election interference in other countries within the EU and spreading anti-EU messaging."
Epstein Files talks disappear: Dis/misinformation research group Open Measures says discussions about the Epstein Files have practically disappeared from alt-right platforms after Trump showed displeasure with the topic. This includes Truth Social, 4chan, Gab, and Gettr. It's like... they're all controlled from a central location and they're not actual users, or something.
TAG-144 (Blind Eagle): Recorded Future has identified five new distinct clusters linked to TAG-144 (Blind Eagle).
PhantomCore arsenal: Russian security firm Positive Technologies has published a technical report analyzing a recent malware strain used by the PhantomCore APT in attacks against Russian orgs.
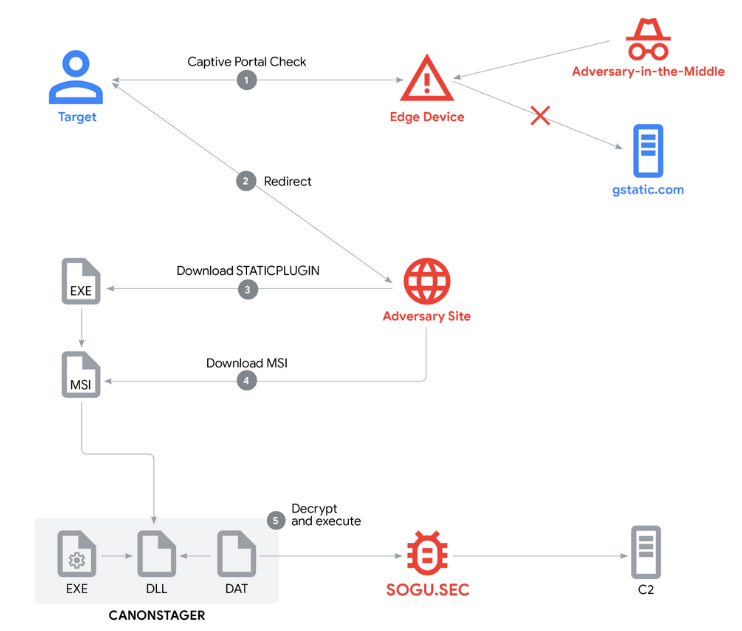
UNC6384 uses captive portals for malware delivery: A Chinese cyber-espionage group has used hacked edge devices to redirect users to captive portals and trick them into installing malware. The campaign took place this March and targeted diplomats in Southeast Asia. Google linked the attacks to a group it tracks as UNC6384. The final payload was the infamous PlugX, a malware long-associated with Chinese espionage operations.
Vulnerabilities, security research, and bug bounty
Perplexity Comet vulnerability: AI company Perplexity has patched a vulnerability in its agentic AI browser Comet. The flaw allowed threat actors to hide malicious prompts inside a website's source code that would be executed by the browser. The bug could have been abused to steal credentials or trick the browser into taking other unwanted actions. The issue was discovered by the Brave browser team. Security firm Guardio warned last week that most agentic AI browsers are vulnerable to this type of attack, which they called Scamlexity.
KEV update: CISA has updated its KEV database (twice) with four vulnerabilities that are currently exploited in the wild. This includes two 2024 Citrix bugs, a Git vulnerability from last month, and a recent iOS zero-day from last week.
ESET security update: ESET has released a security update for its PROTECT EDR dashboard to address a few Tomcat bugs.
Unpatched TheTruthSpy security flaw: A vulnerability in TheTruthSpy spyware app can allow hackers to take over any account and retrieve collected victim data. The vulnerability exploits the app's password recovery process to change the password of any account. TheTruthSpy told TechCrunch it can't fix the bug because it "lost" the app's source code.
New Citrix zero-day: Citrix has released security updates on Wednesday to patch an actively exploited zero-day in its NetScaler products. Tracked as CVE-2025-7775, the vulnerability is a pre-auth RCE that has been used to deploy webshells on Citrix NetScaler devices. Customers are advised to install the patches and start incident response procedures to search for signs of possible compromise.
Infosec industry
New tool—BruteForceAI: Security researcher Mor David has open-sourced BruteForceAI, a tool that uses LLMs for brute-force and password-spraying attacks.
New tool—BlockEDRTraffic: Security researcher Jony Schats has released BlockEDRTraffic, a tool that (obviously) blocks network traffic originating from EDRs.
Threat/trend reports: Censys, Cisco Duo, Incogni, Proofpoint, and Wallarm have recently published reports and summaries covering various infosec trends and industry threats.
Risky Business podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about how the teenage hacking groups Scattered Spider, Lapsus$, and ShinyHunters are collaborating.
In this edition of Seriously Risky Business, Tom Uren and Amberleigh Jack talk about a new report that looks at how Russian cybersecurity firms have adapted since the country's invasion of Ukraine. These firms are doing surprisingly well financially.
