Risky Bulletin Newsletter
November 14, 2025
Risky Bulletin: Europol takes down Elysium, VenomRAT, and Rhadamanthys infrastructure
Written by

News Editor
This newsletter is brought to you by cloud security firm Prowler. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
Europol and law enforcement agencies from more than 30 countries have seized servers, domains, and Telegram channels for three malware services—the Rhadamanthys infolstealer, the VenomRAT, and the Elysium botnet.
Authorities say the three malware strains infected hundreds of thousands of users and stole millions of credentials. The stolen credentials were later used to deploy ransomware or steal cryptocurrency.
The takedown was part of Operation Endgame, an Europol-led project that began in 2023 and targets criminal infrastructure that is used to enable ransomware attacks.
In total, authorities seized 1,025 servers, 20 domains, and searched 11 locations. The administrator of the VenomRAT was also arrested following a raid in Greece earlier this month.
News of the impending takedown started to spread on Tuesday, when several infosec professionals noticed that the Rhadamanthys admin had notified all his customers to cease all operations. The admin claimed they lost access to the infostealer's main control panel and websites.
Of the three malware operations that were taken down this month, Rhadamanthys was, by far, the most consequential.
It launched in December 2022, as a small infostealer project, but quickly grew into a massive Malware-as-a-Service, where other cybercriminal groups could rent access to the malware for quite an expensive fee of $300/month or more.
The stealer, for all accounts, was an advanced piece of coding, successful, and widely used by criminal groups. Europol says its admin had collected enough stolen data to have access to more than 100,000 cryptocurrency wallets.
Officials have taken the stolen Rhadamanthys data and shared it with politie.nl/checkyourhack and haveibeenpwned.com, where users can see if their data was stolen in past Rhadamanthys attacks.
Several cybersecurity firms that participated in the recent Operation Endgame 3.0 takedown have also published blog posts on the research they did in tracking the malware: Proofpoint on VenomRAT, Proofpoint on Rhadamanthys, Shadowserver Foundation on Rhadamanthys.
Proud to once again support our LE partners in Operation Endgame Season 3 86M stolen data items from 525K victim IPs across 226 countries included in our new Rhadamanthys Historic Bot Victims Special Report, run overnight 2025-11-12 More details: shadowserver.org/news/rhadama...
— The Shadowserver Foundation (@shadowserver.bsky.social) 2025-11-13T10:13:54.506Z
There is no way Europol made a CGI animation on Rhadamanthys The trolling level is off the charts
— Catalin Cimpanu (@campuscodi.risky.biz) 2025-11-13T13:34:33.566Z
Everyone’s hyped about Rhadamanthys, but has anyone checked on VenomRAT lately? 🍿👀#OpEndgame pic.twitter.com/O6y94GhMnl
— pancak3 (@pancak3lullz) November 13, 2025
Risky Business Podcasts
The main Risky Business podcast is now on YouTube with video versions of our recent episodes. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
Checkout[.]com donates ransom to cybercrime research: Payment provider Checkout[.]com has declined to pay a ransom demand after hackers breached old cloud servers. The company says it will instead donate the requested ransom to cybercrime research. Checkout[.]com says the servers held data from 2020 and impacted less than a quarter of its customers. It linked the incident to a hacking group known as ShinyHunters.
German TV station hacked: A cyberattack has disrupted the broadcast of German radio station Radio Nordseewelle. Hardware components were damaged in the attack and had to be replaced. The broadcaster said it had to rebuild large parts of its IT network. The hack took place days after a similar incident crippled the transmission of Dutch radio and TV station RTV Noord. [Tarnkappe]
General tech and privacy
Google rolls out Private AI Compute: Google has announced a new feature that will take user data and process it on encrypted cloud servers. The new Private AI Compute will allow users to offload heavy-duty AI tasks to Google's servers instead of their own devices. The feature is identical to Apple Private Cloud Compute, which Apple launched last year.
Steam makes big moves: Steam announced three new hardware products—a new controller, a new VR headset, and a new gaming console to take on the Xbox and the PlayStation. [The Verge]
Google backs off mandatory Android dev registration: Google is easing upcoming restrictions for Android developers. The company announced in August plans to block all Android users from installing apps from unverified developers starting next year. In a blog post this week, Google says it changed its mind following feedback and will allow some developers to go unverified, such as students and hobbyists. The company will also allow "experienced users" to install apps from unverified developers. The company changed its mind after the mobile development community created a website to help mass-report Google to antitrust agencies across the world. [Android Authority]
Third-party passkey managers: Microsoft has announced that Windows 11 will support third-party apps for passkey management.
Twitter botches security key enrollment: Twitter/X's engineering staff has botched an operation to force all users to re-enroll their security keys and put all users in an enrollment loop for hours on end. [TechCrunch//Reddit//HackerNews]
Government, politics, and policy
EU anti-disinfor group participation not mandatory: EU member states won't be required to participate in the bloc's new anti-disinformation group. Plans for the new Democracy Shield initiative are set to be unveiled this week. Participating countries will share guidance and alerts on election meddling, foreign interference, and disinformation campaigns. [Politico Europe]
UK plans new cyber laws: The UK government plans to pass new cybersecurity laws to strengthen the cyber defences for essential public services. The proposed laws will target healthcare, drinking water, transport, and energy providers. They will also target some of their suppliers, such as IT companies, help desk support, and cybersecurity providers. All entities will have to meet minimum security requirements or face turnover-based fines.
UK to test AI products for CSAM potential: The UK government will update its crime laws to tackle AI-generated child sexual abuse imagery. The government will allow tech companies and child safety organizations to test whether AI tools can be used to produce CSAM. The UK will maintain a list of authorized testers that can engage in such activity.
ASIO chief says China probed Aussie networks: Chinese state-sponsored hackers have attempted to breach Australia's telcos and critical infrastructure. The head of Australia's Security Intelligence Organisation, Mike Burgess, warned of possible economic disruption and sabotage. Burgess linked the attacks to groups such as Salt Typhoon and Volt Typhoon. [Reuters]
RGB is now RGIB: North Korea has reorganized its military intelligence agency. The Reconnaissance General Bureau is now the Reconnaissance Information General Bureau. Under the new structure, the RGIB will handle signals, cyber, and human intelligence operations, but also satellite surveillance and data analysis. [DailyNK]
China accuses US of stealing stolen crypto: The Chinese government says the US unduly seized crypto-funds that actually belonged to a Chinese crypto-mining company. The US Justice Department seized $15 billion worth of Bitcoin from the operator of scam compounds last month. The US claimed the funds were owned by the Prince Group and its CEO, Chen Zhi. In a report last week, China's CERT says the funds could be traced back to the 2020 hack of Chinese crypto-mining company LuBian. The report echoes a similar blog post from blockchain analysis firm Elliptic. [Editorial note: The machine translation of the CERT China report seems to suggest in one sentence that the US hacked LuBian. I believe that's a mistranslation and not in the tone of the rest of the report, which just wants to shame the US for seizing the wrong funds.]
Russia imposes SIM card cooldown: Russia will block all Russian SIM cards re-entering the country from connecting to mobile networks for at least 24 hours. The new rule was set in place to prevent Ukraine from using Russian SIM cards to guide drone strikes. Russia imposed a similar 24-hour cooldown for foreign SIM cards entering the country last month. Users can restore connectivity faster by completing a CAPTCHA challenge. [Novaya Gazeta]
US establishes Scam Center Strike Force: The US government has established a new task force to target scam compound operators across Southeast Asia. The Scam Center Strike Force will work under the Department of Justice to track down and prosecute individuals and entities supporting the scam ecosystem. Officials say the strike force has already seized more than $400 million tied to crypto scams.
US sanctions the DKBA: The US Treasury has sanctioned a Myanmar military group for running scam compounds. Sanctions were levied on the Democratic Karen Benevolent Army (DKBA) and four of its senior leaders. Additional sanctions were also imposed on three companies and a Thai national for helping the military group build the scam centers.
Senator urges Dems to block ICE data hoovering: Forty Democrat senators have urged state governments to block ICE from accessing their states' DMV data.
New CyberCommand and NSA favorite: Army Lt. Gen. Joshua Rudd has emerged as the new main favorite candidate for the dual role of US Cyber Command and NSA head. [The Record]
Sponsor section
In this Risky Business sponsor interview, Casey Ellis chats with Toni de la Fuente, founder and CEO of Prowler, an open source platform for cloud security. They chat about how and why Prowler selectively applies AI to ensure it adds value rather than just because they can.
Arrests, cybercrime, and threat intel
Google sues Lighthouse PhaaS: Google has filed a lawsuit against a Chinese Phishing-as-a-Service platform. The Lighthouse is allegedly behind recent waves of SMS spam that targeted users across the world, posing as Google, USPS, and other services. The service made over 1 million victims across 120 countries. Google is seeking a court order to shut down Lighthouse's infrastructure and is seeking injunctions against 25 individuals.
Car thieves detained: French and Italian police have arrested five members of an international car thieves network. The suspects allegedly built reprogrammed speakers and other devices that could decode keys and unlock cars. The group sold the devices for up to €50,000 to car thief networks across 17 countries.
SMS blaster detained in Vietnam: Vietnamese authorities have arrested a man using SMS blasters to send phishing messages across the country's capital, Hanoi. The man was caught hauling an SMS blaster inside a travel suitcase across the city's most crowded areas. The SMS phishing messages impersonated Vietnam's national bank and national post service. The suspect was identified only as a foreign national. [VietnamNet]

Malicious Chrome extension: Socket Security has spotted a malicious Chrome extension posing as an Ethereum wallet that was designed to steal seed phrases. The extension was still live.
ACSC phishing: Australia's cybersecurity agency says scammers are posing as Australian police to scam Australians out of their cryptocurrency.
GFW analysis: The DomainTools security team has published part three of its analysis of more than 500GB of data that was leaked from Chinese companies managing China's national firewall system, aka the Great Firewall.
IndonesianFoods campaign: Endor Labs has spotted a campaign that flooded the npm portal with more than 43,000 packages as part of a scheme to generate Tea cryptocurrency tokens. These tokens provide rewards to developers based on the popularity of their projects. The campaign started in April 2024, and some of the packages are still live.
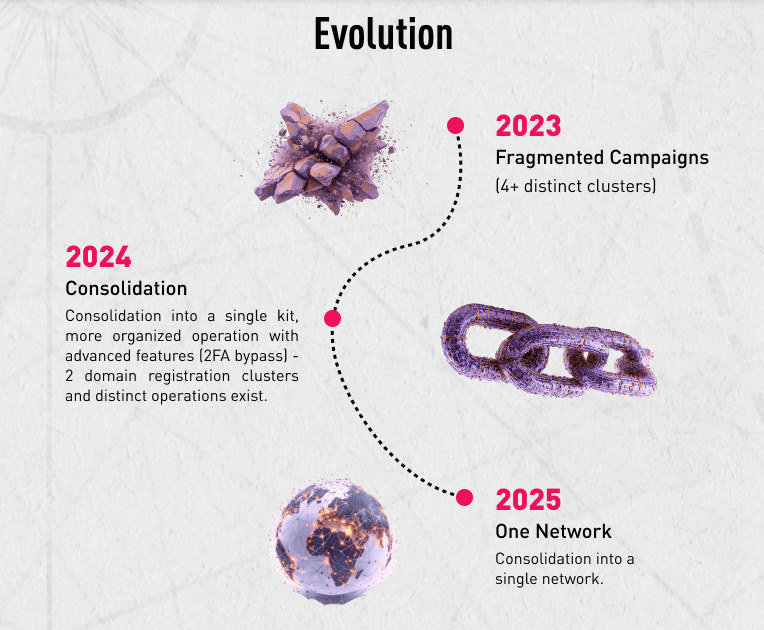
Payroll Pirates: A new threat actor has used malvertising and dedicated phishing kits to target the users of payroll systems, credit unions, and trading platforms. The Payroll Pirates group has been active since 2023 and appears to be based in Ukraine. According to Check Point, the group operated using four different clusters before merging infrastructure this year.
Malware technical reports
Cephas phishing kit: Email security firm Barracuda looks at two phishing kits, the good ol' Tycoon 2FA, and Cephas, a relatively newer operation that launched in August last year.
NovaStealer: Security researcher Bruce Ketta has published an analysis of NovaStealer, an infostealer targeting the macOS space.
LummaStealer returns: Trend Micro says it's seeing a new surge in LummaStealer activity. This is surprising since the stealer was pronounced dead and buried after its developer was doxed on underground forums.
DarkComet RAT: PointWild researchers look at a campaign using boobytrapped crypto apps to deliver the DarkComet RAT.
Yurei ransomware: AhnLab has published a technical analysis of Yurei, a new Go-based ransomware strain.
Akira ransomware: CISA has updated its report on the Akira ransomware.
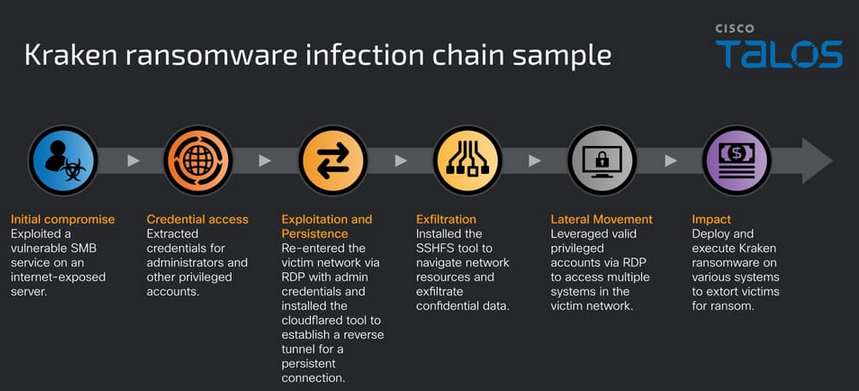
Kraken ransomware: Cisco Talos looks at Kraken, a ransomware group that emerged in February out of the ashes of the old HelloKitty gang.
Sponsor section
In this sponsored product demo, Prowler founder and CEO Toni de la Fuente walks Risky Business host Patrick Gray through the company's open-source cloud security platform. Toni demonstrates how Prowler can identify and remediate security issues across AWS, Azure, GCP, and Kubernetes. There's a pointy-clicky GUI interface and a CLI, and both come in handy in different ways. The Prowler platform is completely free and open source, but there is a hosted version you can pay for if you don't want to run it yourself.
APTs, cyber-espionage, and info-ops
Google disinfo bulletin: Google TAG has published its disinfo disruption report for the third quarter of the year.
Contagious Interview update: NVISO researchers have spotted new phishing campaigns part of the DPRK's Contagious Interview effort.
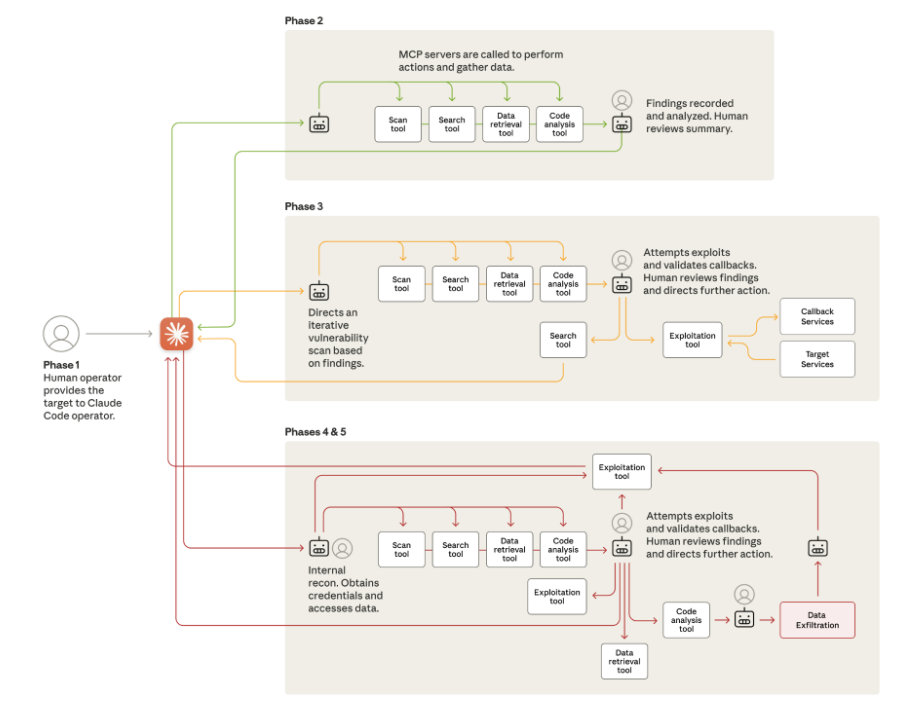
Anthropic disrupts Chinese APT campaign: A suspected Chinese APT group abused the Claude Code tool in a campaign that targeted corporate environments. The campaign targeted 30 targets and was successful in a handful of cases. Anthropic says this was the first APT campaign that abused an AI agent at scale, rather than a per-target basis. The unnamed APT used Claude to scan targets, map the attack surface, breach networks, harvest networks, move laterally, and collect and exfil data, all with minimal human interaction.
Vulnerabilities, security research, and bug bounty
Amazon AI bug bounty: Amazon has launched a bug bounty program for its AI products and models.
New Citrix bug: WatchTowr Labs has published a technical write-up on CVE-2025-12101, a reflected XSS bug in Citrix NetScaler.
AWS honeypot data spots zero-days: The AWS security team dug through its honeypot data and confirmed that CVE-2025-5777 (a Cisco ISE RCE) and CVE-2025-5777 (a memory leak in Citrix NetScaler) were, indeed, exploited as zero-days before their patches. Nothing new here except the confirmation that an APT was behind the attacks.
CheckSum vulnerability: SilverFort researchers have found a vulnerability named CheckSum in the Kerberos constrained delegation mechanism, allowing them to hijack temporary delegations and gain domain admin rights. This was patched this month as CVE-2025-60704, and more details will be presented at Black Hat Europe.
Sora system prompts: Mindgard researchers reverse-engineered and extracted Sora's internal system prompts. These prompts could be abused by threat actors to make Sora agents perform sensitive or dangerous operations.
Cisco security updates: Cisco has released five security advisories for several of its products.
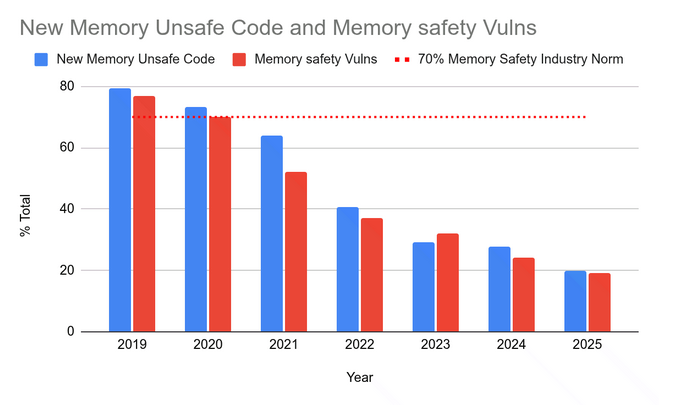
Rust pays off in Android: The number of memory safety vulnerabilities has fallen under 20% for the first time in the Android project's history. Google credited the improvement to its adoption of Rust code. Besides better security, Google says Rust has also cut down code reviews by 25% and code rollback rates by four times.
Infosec industry
Threat/trend reports: Check Point, Google TAG, Harness, LayerX, Panaseer, Rapid7, Recorded Future, and UpGuard have recently published reports and summaries covering various threats and infosec industry trends.
Deepwatch layoffs: Cybersecurity firm Deepwatch has laid off almost a quarter of its 250 staff. CEO John DiLullo says the firings are part of a realignment on AI and automation. Deepwatch is the second cybersecurity company after CrowdStrike to directly attribute layoffs to AI investments. [TechCrunch]
New tool—SharpParty: LevelBlue has released SharpParty, a C# implementation of the PoolParty process injection techniques.
Ekoparty videos: Talks from the Ekoparty 2025 security conference, which took place earlier this month, are available on YouTube.
Risky Business podcasts
In this edition of Seriously Risky Business, Tom Uren and Amberleigh Jack talk about a new Reuters report that reveals how Meta is knowingly raking in cash from scam advertisements. It's around $16 billion worth, and in documents, Meta calculates that it outweighs the costs of possible regulatory action.
In this edition of Between Two Nerds, Tom Uren and The Grugq discuss how cyber criminals and even state actors are being dumb about using AI.
