Risky Bulletin Newsletter
May 21, 2025
Risky Bulletin: EU sanctions more Russian disinformation peddlers
Written by

News Editor
This newsletter is brought to you by SpecterOps, the experts in Attack Path Management. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
The European Union has sanctioned three new clusters associated with Russia's disinformation networks across Africa and Europe.
This is the EU's 17th round of sanctions against Russia over its 2022 invasion and ongoing war in Ukraine. The sanctions are far broader and also target Russia's oil sector, its shadow fleet of oil tankers, and its hybrid warfare activities across Europe, which included extensive sabotage and disinformation campaigns.
We will not cover the entire sanctions package since it's out of the scope of this newsletter, but only the three clusters that are cyber adjacent.
The first cluster revolves around Voice of Europe, a propaganda network operated out of Prague and dismantled by Czech officials last year.
The sites published pro-Kremlin news and opinions from EU politicians demanding that the EU stop financing Ukraine. Several far-right politicians who published opinions were allegedly paid hefty sums by the network.
Czech investigators linked the sites to former Ukrainian politician Viktor Medvedchuk, who they claim ran the entire operation out of Moscow. The EU has sanctioned Medvedchuk, along with Artem Marchevskyi and Oleg Voloshin, two associates who helped him run the Voice of Europe, but also several Ukrainian media outlets that peddled Russian propaganda.
The sanctions package also targeted four individuals who ran news sites and pan-Africanism organizations in Africa but which really spread Russian disinformation and propaganda on a variety of topics.
"In addition, the Council targeted Viktor Lukovenko, the head of listed entity African Initiative, a news agency involved in spreading Russian propaganda and disinformation on the African continent, Justin Blaise Tagouh, CEO of the press group International Africa Media and Mikhaïl Prudnikov have been spreading Russian narrative and anti-western narrative in African countries. Sylvain Afoua, founder of the 'Black African Defense League,' a structure dissolved in 2021 by the French authorities for spreading an ideology calling for hatred, discrimination and violence, was also listed."
Sanctions were also levied against Stark Industries and its two owners, the Neculiti brothers, Iurie and Ivan. According to reports from Correctiv and Brian Krebs, Stark Industries is one of today's largest providers of bulletproof hosting services and has hosted everything from malware to DDoS servers and info-ops.
For example, Stark hosted websites for Russia's Doppelgang disinformation group and many of the pro-Kremlin faketivist groups that launched DDoS attacks against EU and US websites.
The EU was able to sanction these kinds of smaller entities after the bloc expanded its sanctions framework last October specifically to allow itself to go after Russia's hybrid warfare efforts across the EU.
These are the EU's second round of sanctions targeting Russian disinfo operations. It first sanctioned a Russian disinformation network known as "RRN" (Recent Reliable News) in July 2023, but that was possible due to the network's close ties to Russian government bodies, like the GRU military intelligence service.
Other sanctions packages also targeted Russian cybersecurity firms (Positive Technologies, NTC Vulcan, Echelon, Iteranet, and Poisk-IT) and three GRU hackers. The latter are part of a group known as Ember Bear (Cadet Blizzard, Frozenvista, UNC2589, and UAC-0056) and are linked to real-world sabotage operations across Europe and the WhisperGate data wiper deployed ahead of Russia's invasion of Ukraine.
Risky Business Podcasts
Risky Business is now on YouTube with video versions of our main podcasts. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
UK Legal Aid hack: Hackers have stolen a "significant amount of personal data" from people who applied for legal help at the UK Legal Aid agency. The data of both victims and legal councils dating back to 2010 was stolen. The breach took place in late April. The agency disclosed the incident on Monday after learning the intrusion was far larger than previously thought. The incident is suspected to be a ransomware attack.
myGov hacks: Hackers have infiltrated Australian myGov accounts, filed fake tax returns, and redirected refunds to their own bank accounts. The Australian Tax Office has yet to reveal how many accounts were affected or how many funds were misdirected. The agency didn't want to confirm the attacks but urged Australians to use the "highest identity strength" possible when securing their accounts. [Additional coverage in The Australian]
Cellcom hack: American wireless provider Cellcom has experienced prolonged outages after a cyberattack last week. Voice and SMS services have been affected across Wisconsin and Upper Michigan, according to a letter [PDF] from the Cellcom CEO. The company says it has no evidence that customer data was stolen.
SK Telecom hack lasted three years: In an update for its catastrophic breach, South Korean telco SK Telecom says hackers breached and planted malware on 27 of its servers back in 2022. Still no formal attribution of the hack. [Additional coverage in Hankyoreh]
TeleMessage hacked data available: The Distributed Denial of Secrets project has obtained over 410 GB of data that was stolen from software company TeleMessage. The data contains archives of encrypted conversations logged by TeleMessage customers. The data may contain conversations from several US government agencies, including top White House officials. At least two different hackers breached TeleMessage earlier this month after journalists spotted the company's app on a high-ranking US official's phone. DDoSecrets says it will make the data available to journalists and researchers only.
Peter Green Chilled ransomware attack: UK logistics firm Peter Green Chilled has been hit by a ransomware attack. The company is a supplier for UK supermarkets such as Tesco, Sainsbury's, and Aldi. Peter Green Chilled says deliveries have gone unaffected, but new orders can't be processed. [Additional coverage in the BBC]
Arla Foods cyberattack: A suspected ransomware attack has halted production at an Arla Foods factory in Germany. Arla is the fifth biggest dairy company in the world. [Additional coverage in JustFood]
DDoS attack disrupts multiple Russian state websites: A coordinated DDoS attack disrupted multiple Russian government portals on Tuesday. Outages were reported at the Russian Federal Tax Service, SBIS (or Saby), a system for exchanging documents between Russian companies, and GosKey, Russia's digital key signing service. Disruptions were also reported at EMIAS, a state service for managing medical records, and EGAIS, a state system for controlling the sale of alcoholic beverages. Russian officials are still investigating the attacks, but they were most likely the work of pro-Ukraine hacktivist groups. [Additional coverage in RTVI/English coverage in The Record]
Brian Krebs has all the fun: Infosec reporter Brian Krebs says his blog was hit again with a massive DDoS attack, this one clocking at around 6.3 Tbps. The first wave of attacks back in 2015 gave the world the gift that never ends—the Mirai IoT DDoS malware.
Chinese sci-tech company hacked: A threat actor has allegedly breached and disrupted the backend systems of a sci-tech company based out of Guangzhou, China. Chinese officials claimed the hack had a "clear political background and [showed] distinct signs of cyber warfare." They described the intruders as overseas hackers but did not attribute the attack to any specific foreign nation. [Additional coverage in Xinhua News and the Global Times]
"the technical team's analysis indicates that the attacker's methods and related technical proficiency were relatively low-level." Nothing in the article to explain what makes this "cyber warfare".
— Danny Moore (@moore.bsky.social) 2025-05-20T14:01:36.357Z
RVTools incident: Dell has taken the website for the RVTools VMware management and reporting tool offline after a report that the official installer might have been used to deliver the Bumblebee malware. [Additional coverage in Arctic Wolf]
Curve Finance DNS hijack: A threat actor has hijacked the DNS records of the Curve Finance crypto platform to redirect users to a suspected phishing site.
Stalkerware trio goes offline: A trio of spyware apps have shut down and taken servers offline after getting hacked in February this year. Cocospy, Spyic, and Spyzie offered what security researchers call stalkerware, apps that can track and spy on the devices of employees or loved ones. The apps collectively leaked the data of over 3.2 million of their users. [Additional coverage in TechCrunch]
DOJ to investigate Coinbase over hack: The US Department of Justice has started an official investigation of Coinbase over its recently disclosed hack. [Additional coverage in PYMNTS]
Predatorgate lawsuit delayed: A Greek court has indefinitely postponed the lawsuit filed against spyware provider Intellexa by local victims. The court delayed the trial after two of the four appointed interpreters refused to work on the case. The interpreters were allegedly tasked on short notice to translate a huge collection of Intellexa documents into English. According to DNews, the defense lawyers blamed the Supreme Court Prosecutor's Office for the procedural lapse after it failed to notify the court that key documents needed to be translated.
The-dog-ate-my-homework pretext for delaying the spyware abuse trial in Greece. One of the rare cases in Europe that made it to the court. Most spyware victims have no real legal remedy, impunity reigns for spyware abuse.
— Sophie in't Veld (@sophieintveld.bsky.social) 2025-05-19T20:08:46.712Z
General tech and privacy
WSL goes open-source: Microsoft has open-sourced the Windows Subsystem for Linux, the component that lets users run Linux CLI tools on Windows.
Microsoft adopts MCP: Microsoft announced plans to support the Model Context Protocol (MCP) for the company's AI tools. MCP is an open protocol designed to allow AI tools to exchange data with other tools or AI agents.
Microsoft confirms admin protection feature: We featured this last November, but Microsoft has now formally confirmed a new Windows 11 feature named Administrator Protection. The feature works basically like sudo, taking all elevated privileges admin needs and putting them into a super admin account that users can elevate to after additional authentication.
Windows adds PQC support: Microsoft is adding post-quantum cryptography support to the Windows operating system. The company will support new cryptographic algorithms that will be able to protect data from powerful quantum computers. New algorithms like ML-KEM and ML-DSA will be tested in Windows Insiders builds before being made available to Windows users. Some of the libraries Microsoft is updating will also trickle down to the Linux ecosystem.
Durov claims: Telegram founder Pavel Durov claims the French government tried to "silence conservative voices in Romania" ahead of the country's election last week. French officials denied making any such request and described Durov's statements as "unfounded allegations." Durov was detained in France last year on charges of failing to moderate Telegram.
Government, politics, and policy
FBI closes FISA watchdog office: FBI Director Kash Patel has closed an internal watchdog office that tracked the agency's use of FISA surveillance powers. The Office of Internal Auditing was shut down as part of a larger reorganization inside the Bureau. Congress grilled the FBI last year for its misuse of FISA Section 702 surveillance powers before eventually extending the surveillance program until April next year. [Additional coverage in the New York Times]
NSO US lobby effort fails: According to WaPo, the Trump administration told NSO execs visiting this week in Washington that it does not intend to lift sanctions on the company.
Trump signs Take It Down Act: US President Donald Trump has signed the Take It Down Act that criminalizes sexually explicit deepfake imagery. Congress passed the bill last month. [Additional coverage in NBC News]
NOLA secret surveillance project: The New Orleans police department ran a secret project for years that used facial recognition to scan CCTV footage and identify potential crime suspects. The project initially used still photos and then expanded to live feeds from over 200 private security cameras deployed across the city. According to the Washington Post, the project ran despite a local moratorium on using facial recognition for police work.
Federal Cyber Workforce Training Act: US lawmakers have proposed the Federal Cyber Workforce Training Act, a bill that would require the US National Cyber Director to submit to Congress a plan to establish an institute to serve as a centralized training center for the US cyber workforce.
Coast Guard warns of growing cyber threats: In its yearly maritime environment report, aka CTIME, the US Coast Guard says that the growing adoption of new technologies is increasing cyber risks in maritime operations. The main sources of headaches are cyber supply chains and increased ship connectivity.
UK says NHS cyberattacks endangered patients: The UK government says that two cyberattacks targeting the National Health System last year put patients at risk of clinical harm. The term refers to the aggravation of an existing condition after delays in care due to the two security incidents. According to a FOIA request from The Record, the UK didn't register any cybersecurity incident that could have led to excess fatalities or casualties.
Chinese intel recruits US laid-off govt workers: Chinese intelligence is using a network of front companies to recruit laid-off US government workers on "consulting work," per a new FDD report. The UAE is also doing this, but they're not a nuclear power and sworn enemy of the US. Although...
The general was apparently given permission by the Pentagon to recruit former members of Defense Digital Service to work on AI for UAE military despite warnings last year from US spy agencies/lawmakers that UAE could share AI tech with China and despite UAE's disturbing history of recruitment
— Kim Zetter (@kimzetter.bsky.social) 2025-05-20T11:20:12.105Z
Sponsor section
In this Risky Bulletin sponsor interview, Justin Kohler, Chief Product Officer at SpecterOps, talks to Tom Uren about the impossible challenge of managing identity directory services securely. Organizations try to implement the principle of least privilege but have no idea if they have done a good job. Justin talks about approaches SpecterOps is developing to address this problem.
Arrests, cybercrime, and threat intel
Authorities seize assets linked to Riot Games hacker: Australian authorities have seized assets from an Australian man, Shane Duffy, 32. Duffy was previously convicted for hacking Riot Games in 2018. Authorities have seized his house, his car and cryptocurrency believed to be stolen from a French crypto-exchange in 2013. The French exchange lost 950 Bitcoin in the 2013 incident, which is now worth about $100 million. Duffy has not been charged over the bitcoin theft. [Additional coverage in 7News]
Anonsec member detained in India: Indian authorities have arrested an 18-year-old in the city of Nadiad. The teen was allegedly a member of Anonsec, a hacktivist group that launched DDoS attacks on over 20 Indian government websites. The attacks took place on May 7, the day when India launched Operation Sindoor—military strikes across Pakistan. [Additional coverage in the Hindustan Times]
Scam network: Recorded Future looks at a cluster of scam sites impersonating various large brands.
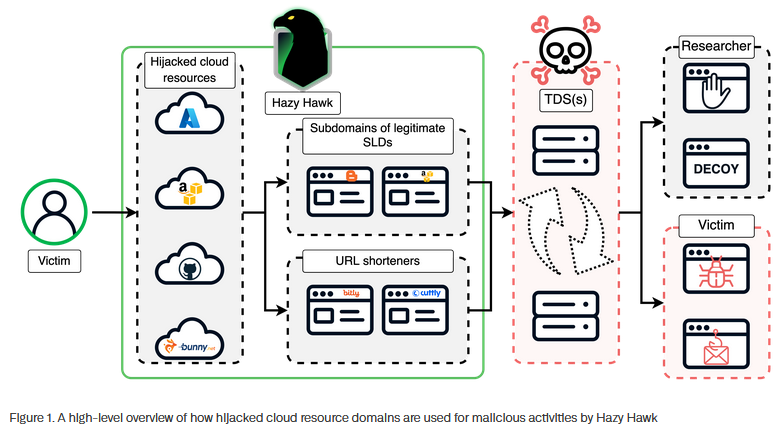
Hazy Hawk: Infoblox has published a profile on Hazy Hawk, a threat actor that hijacks DNS-misconfigured cloud resources to redirect users to scam sites. The hacked resources belonged to government agencies across the globe, large universities, and international companies. The hacks have been allegedly taking place since December 2023.
World Leaks profile: Security firm Lexfo has published a profile on World Leaks, a rebrand attempt from the Hunters International gang. Lexfo says that despite claims that it would be a pure extortion-only group, World Leaks has been linked to classic data encryption ransomware attacks. Lexfo also found links to a known ransomware affiliate known as Secp0.
VanHelsing RaaS publishes its source code: The operators of the VanHelsing ransomware have published the source code of their operation and shut down all servers. The group's move comes after one of its customers tried to sell it a few hours earlier on a known hacking forum. The VanHelsing gang has been active for almost two months and only made a handful of victims. It promised to relaunch the service on new code. [Additional coverage in Bleeping Computer]
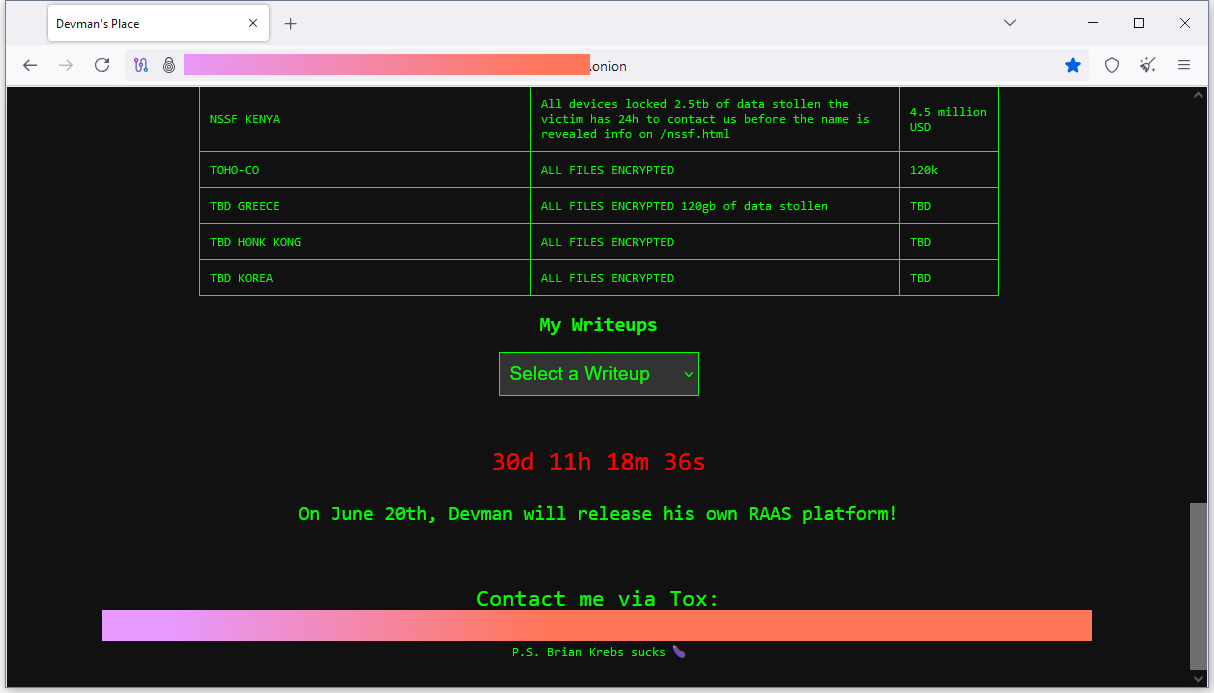
New Devman ransomware group: An initial access broker known as Devman is preparing to launch a new RaaS in June. In the meantime, they're maintaining a separate website where they list victims from past intrusions carried out via other RaaS.
Another Facebook malvertising campaign: A threat actor is using Facebook ads to redirect users to a website offering malicious versions of the Kling genAI software. Per Check Point, the campaign seems to originate from Vietnam.
Malicious Chrome extensions: The DomainTools security team looks at a cluster of over 100 websites peddling malicious Chrome extensions.
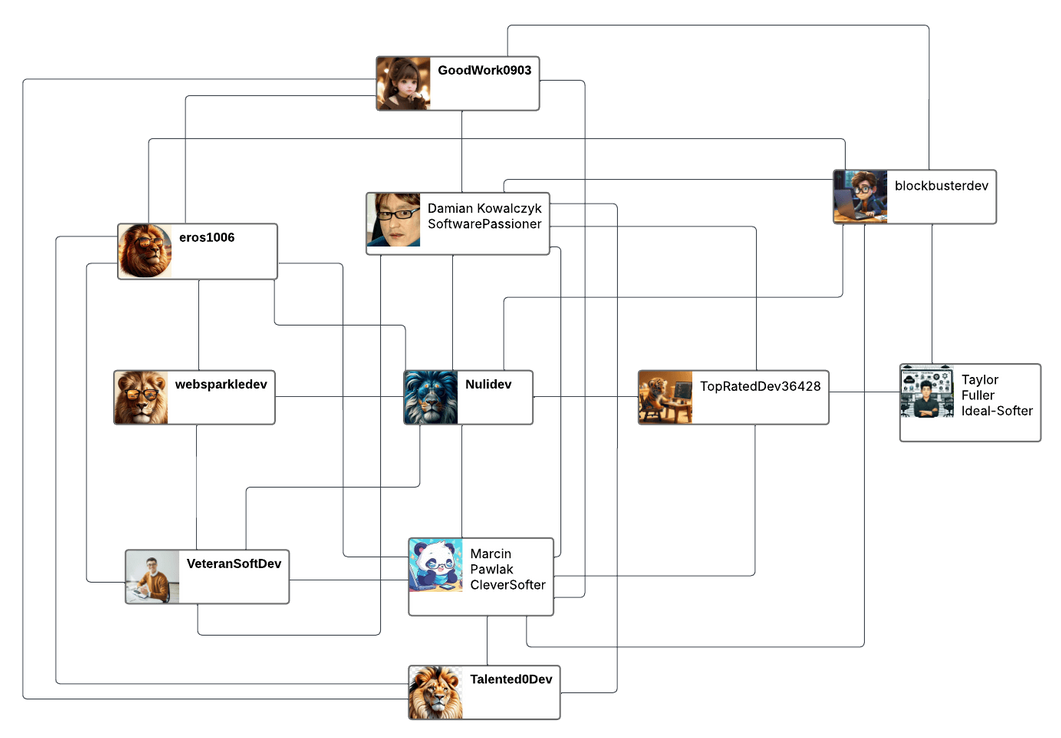
Saja DPRK employment network: Nisos has spotted a new cluster of North Korean IT workers seeking employment at Western companies. Some of the Saja group's main characteristics are below.
- Mainly pose as US and Polish nationals.
- Claim to work for a freelance company named Inspiration With Digital Living.
- Members tend to use accounts with lion-themed avatars.
- Members typically ran accounts in multiple persona names for broader and more efficient targeting.
Malware technical reports
ELPACO-team ransomware: The DFIR Report team has published a look at the ELPACO-team ransomware, a variant of the older Mimic ransomware. The report looks at one of the group's intrusions that breached a company's network via its Atlassian Confluence server.
PureRAT: Kaspersky has spotted new attacks delivering the PureRAT malware to Russian organizations.
Hannibal Stealer: Security researcher Shubho57 has published an analysis of Hannibal Stealer, a rebranded version of the older Sharp Stealer. Both, obviously, are written in C#.
3AM ransomware: Sophos looks at the 3AM ransomware and its adoption of email bombing and vishing.
Sponsor section
Justin Kohler, VP of Product at SpecterOps, shows how BloodHound Enterprise can be used to find and fix Active Directory (mis)configurations that could let attackers easily own your entire enterprise.
APTs, cyber-espionage, and info-ops
APTs in the last six months: In its 2024 Q4 and 2025 Q1 report, ESET noted a trend of Chinese APTs shifting targeting towards European organizations.
Doppelganger targets Poland's presidential election: Ukraine's military intelligence agency has spotted Russian disinformation group Doppelganger targeting Polish users with fake news ahead of the country's first round of presidential elections over the weekend. The group also targeted Romania before its presidential election, too. In Romania, the group is now pushing the same ol' tired narrative that the election was stolen since the Kremlin's preferred candidate didn't win.
Russia's cyber posture in 2025: The Atlantic Council published a report on Russia's cyber capabilities in 2025, three years after its invasion of Ukraine. [Summarized coverage in NextGov]
Rather than a streamlined Russian command structure, the report describes a fragmented system driven by bureaucratic turf wars, shifting criminal alliances and inconsistent oversight — making Russia’s cyber operations messier than officials once assumed: www.nextgov.com/cybersecurit...
— David DiMolfetta (@ddimolfetta.bsky.social) 2025-05-20T11:38:34.798Z
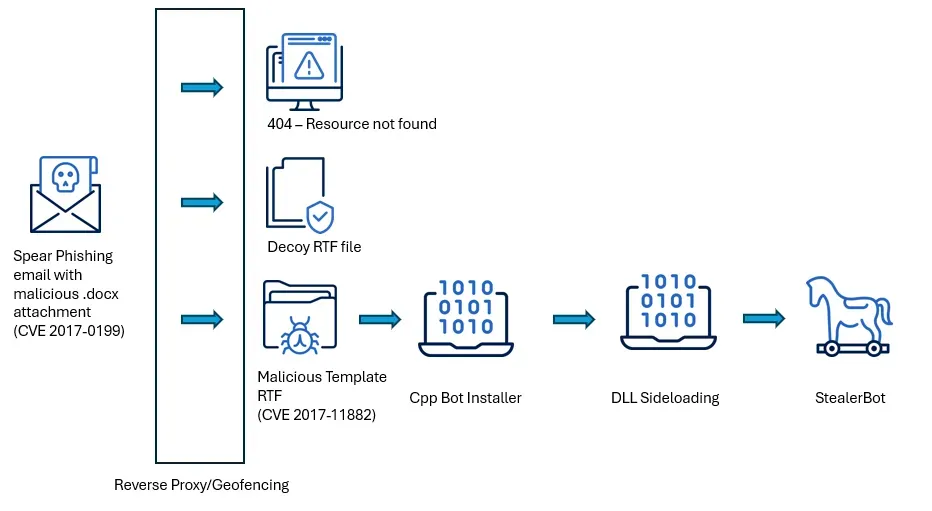
SideWinder activity: The Acronis security team has spotted Indian APT group SideWinder launch a spear-phishing campaign against government organizations in Sri Lanka, Bangladesh, and Pakistan. The campaign used 2017 Word exploits to deploy the StealerBot malware.
Vulnerabilities, security research, and bug bounty
New vulnerability metric: CISA and NIST have proposed a new security metric to describe the likelihood that a vulnerability has been exploited in the wild, even if tangible evidence is absent. The new Likely Exploited Vulnerabilities metric is designed to help enhance CISA's current KEV system. LEV is currently undergoing standardization at NIST.
KEV update: CISA has updated its KEV database with six vulnerabilities that are currently exploited in the wild. This includes two Ivanti EPMM zero-days from last week, a zero-day in the Srmiax Output Messenger exploited by a Turkish APT, zero-days in the Zimbra and MDaemon email server exploited by a Russian APT, and a 2023 path traversal bug in the ZKTeco BioTime attendance management software.
Unpatched Foscam bugs: Security researchers have published details and proof-of-concept code for three vulnerabilities in Foscam X5 security cameras. The vulnerabilities are still unpatched after the vendors failed to respond to the researchers. If exploited, the bugs can allow hackers to hijack security cameras, deploy malware, and enroll them in IoT botnets.
SAP NetWeaver zero-day: OP Innovate has published a report looking at how the Qilin ransomware is exploiting a recent SAP NetWeaver zero-days (CVE-2025-31324) in its intrusions.
Oracle TNS write-up: Driftnet researchers have published a detailed write-up on CVE-2025-30733, an info leak in the Oracle Transparent Network Substrate (TNS) protocol used by Oracle's DB products. Oracle patched the bug back in April.
Go crypto security audit: Security firm Trail of Bits has performed a security audit of the Go suite of cryptography packages. Results are now live on the Go blog.
Three Trail of Bits engineers audited core Go cryptography for a month and found only one low-sev security issue... in unsupported Go+BoringCrypto! 🍾 Years of efforts on testing, limiting complexity, safe APIs, and readability have paid off! ✨ Yes I am taking a victory lap. No I am not sorry. 🏆
— Filippo Valsorda (@filippo.abyssdomain.expert) 2025-05-19T19:07:59.246Z
Infosec industry
Threat/trend reports: The US Coast Guard, CrowdStrike, ESET, and Varonis have recently published reports and summaries covering various infosec trends and industry threats.
New cyber industry group: Several US cybersecurity companies have formed the Strategic Cybersecurity Coalition, a new industry group to lobby the US government. The group's main stated goal is to help the US government reform and simplify the process of providing cyber aid to allied countries and promote the use of US cybersecurity products. Founding members include Carahsoft, Dell Technologies, Forescout, Google Cloud, Trellix, and Velos.
New tool—ENISA handbook: The EU's cybersecurity agency has published a handbook to help government agencies and companies test systems and become NIS2 compliant.
New tool—PowerDodder: Security researcher Itay Migdal has released PowerDodder, a post-exploitation persistence utility designed to stealthily embed execution commands into existing script files on the host.
Tool update—Frida: Version 17.0 of the Frida open-source instrumentation and reverse engineering tool is out.
OffensiveCon 2025 videos: Talks from the OffensiveCon 2025 security conference, which took place last week, are now available on YouTube.
Risky Business podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq examine what makes it hard for even competent hackers to contribute to state-backed espionage agencies.
In this special edition of the Seriously Risky Business podcast, Patrick Gray speaks with former NSA Cybersecurity Director Rob Joyce and former director of the CIA's Center for Cyber Intelligence Andy Boyd.
