Risky Bulletin Newsletter
January 26, 2026
Risky Bulletin: EU readies new anti-spyware group, but with even less powers than PEGA
Written by

News Editor
This newsletter is brought to you by Push Security. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
The European Parliament has set up a new internal group tasked with investigating the use of spyware across the EU member bloc.
The new intergroup was set up last week in the aftermath of the Paragon spying scandal in Italy by Sandro Ruotolo, an Italian journalist and current member of the European Parliament for the Group of the Progressive Alliance of Socialists and Democrats.
According to WIRED Italy, Ruotolo will be joined by three other MEPs.
As a first step, the group is asking victims of spyware attacks to come forward and share details with EU officials.
It is an informal group, similar to the old PEGA commission that was established after the Predatorgate scandal in Greece, but has even less powers.
"The European People's Party, now the party with a relative majority, would never have allowed the establishment of a new commission of inquiry," Ruotolo said.
Ruotolo is likely trying to put pressure on the Italian government to be more transparent about its use of spyware rather than kick off an EU-wide investigation—although that would not be a bad thing.
As the years have gone by, more and more EU countries have been caught using spyware to go after political rivals, journalists, activists, and prosecutors. The biggest abuses have been recorded in Greece, Poland, Hungary, and Spain.
Italy joined the list at the start of last year when reports started emerging that it had contracted Israeli spyware company Paragon and was using its Graphite spyware platform to hack members of the civil society, and especially individuals linked to anti-immigration organizations. Victims like priests, business figures, political consultants, journalists, and NGO members were allegedly hacked, which the government admitted in closed Parliament hearings.
The spyware was allegedly used by Italy's intelligence service, which cited its use because of national security concerns related to uncontrolled immigration and human trafficking going on in the Mediterranean.
Italian media, of which Ruotolo was a member, have been critical of the government because some of the infections targeted journalists who were just doing their job. The anger is real in Italy since people who gave food to immigrants got spyware in return, while extreme far-right groups singing fascist songs in the streets saw no repercussions or care from Italian officials.
Risky Business Podcasts
The main Risky Business podcast is now on YouTube with video versions of our recent episodes. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
Major password leak: A security researcher has taken down a database storing more than 149 million stolen credentials. The database was still growing and was likely part of an infostealer malware campaign. Almost a third of the collected credentials were Gmail logins. [ExpressVPN // WIRED]
Under Armour breach: Sportswear company Under Armour is investigating a data breach. More than 72 million records containing Under Armour customer emails and other details were leaked online this month. The files were allegedly stolen in a breach last year, although it's unclear how. [Associated Press]
Dresden museum cyberattack: A cyberattack has crippled the IT systems of the Dresden museum network. The incident took down some of its digital and phone services last week. The Dresden State Art Collections oversees 15 museums and is one of the oldest museum networks in Europe. [The Record]
US investors sue South Korea over Coupang breach: Two US investment firms have sued the South Korean government for investigating retail giant Coupang over a recent data breach. Greenoaks and Altimeter argue the Seoul government is making an example out of the Seattle-based company to boost local competition. They claim the large penalties and statements from government officials are against the US-South Korea trade agreement. The case is set to go into arbitration. [Axios]
Call-On-Doc breach: Hackers claim to have breached the Call-On-Doc telehealth provider and leaked more than 1.1 million patient records, almost 55% of the company's total customers. Call-On-Doc has not yet confirmed the breach. [DataBreaches.net]
Waltio discloses extortion attempt: French crypto tax-filing company Waltio is being extorted by hackers. The company says hackers stole customer tax reports for last year. Waltio said it activated incident response procedures but did not say if it planned to pay the ransom. The ShinyHunters are allegedly behind the hack and extortion. [Protos]
EmEditor watering hole attack: Trend Micro has published an incident report on the watering hole attack that took place on the website of the EmEditor IDE back in December.
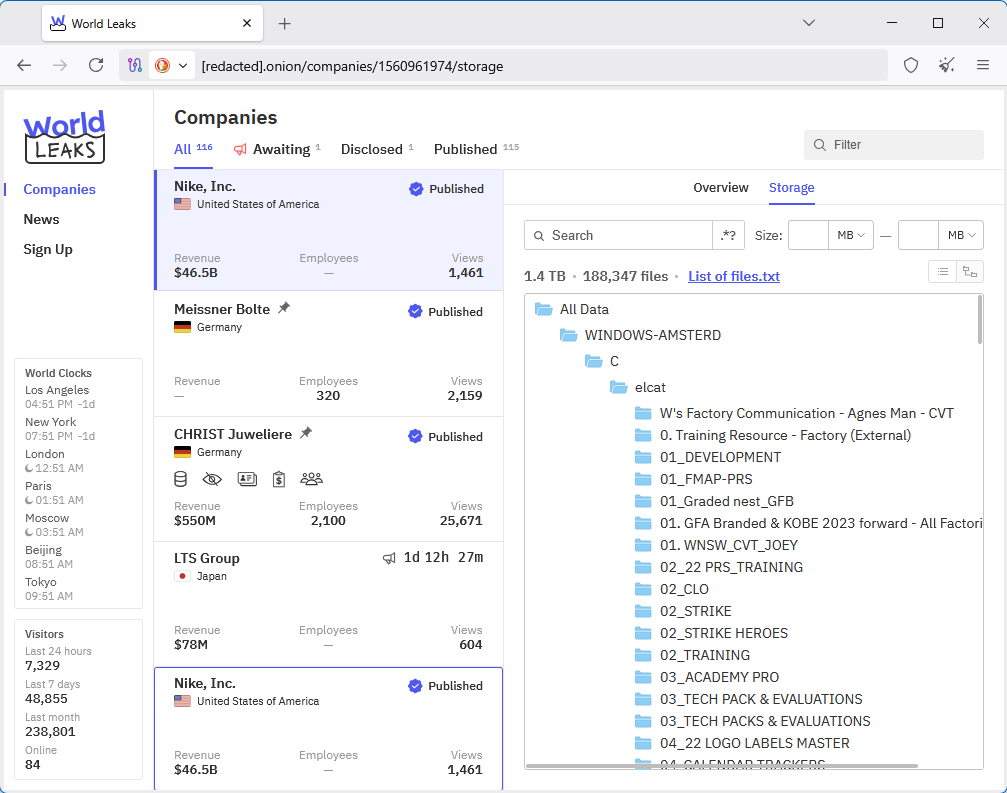
Nike investigates hack: American sportswear giant Nike is investigating a potential security breach. The World Leaks data extortion group published a sample of the company's data on the dark web last week. The group claims it stole more than 1.4TB of data from Nike's clothing manufacturing business. [PCMag]
General tech and privacy
Anguilla getting rich over AI: The Caribbean island state of Anguilla is making around $70 million/year from renting .ai domains. [Sherwood]
1Password adds phishing and spoofing alerts: Password manager 1Password has added a new security feature that warns users when they're on a phishing or spoofed site and they're being asked to enter credentials that don't match the domain.
Ring Verify now available: Amazon has added a new security feature to its Ring security camera service to let users verify if footage came from an authentic cam or was altered in any way.
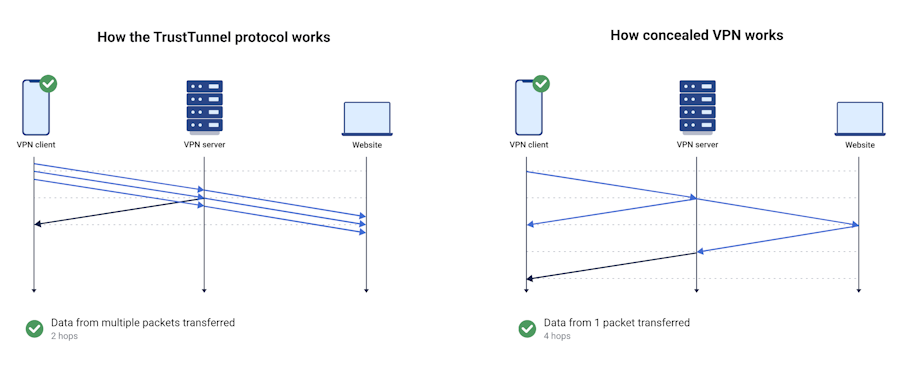
AdGuard open-sources VPN protocol: Ad-blocking company AdGuard has open-sourced TrustTunnel, the tunneling protocol at the heart of its AdGuard VPN service.
Government, politics, and policy
UK House votes to ban social media for <16s: The UK House of Lords has voted to ban social media for children under the age of 16. The new Children's Wellbeing and Schools Bill also includes a provision to ban children under 18 from using VPN apps. The move comes after Australia banned children under 16 from social media at the start of the year. Similar efforts are also underway in France and Russia. The UK bill now moves to the House of Commons. [BBC]
UK to get its own FBI-like force: The UK government will establish a new police force similar to the US' Federal Bureau of Investigations. The new National Police Service will run investigations at the national level, while leaving local police forces to tackle regional crime. Its main focus will be on counter-terrorism, fraud, and organised crime. The existing National Crime Agency will be brought under the new NPS. [Sky News]
New Russian crackdown on VPNs: The Roskomnadzor has found a way to block VPNs disguising themselves as traffic from allowlisted services. The internet watchdog is now requiring Russian cloud providers isolate IP address pools for allowlisted services from the ones assigned to regular customers. Russia is currently blocking more than 400 VPN services. [Durov Code]
Russia delays its Starlink clone: The Russian government has delayed the launch of its first batch of low-orbit satellites. The Rassvet (Dawn) project is meant to create a Russian-owned alternative to the US' Starlink project. The launch of 16 initial satellites has been delayed towards the end of the year. [The Moscow Times]
Hybrid CoE support: Germany and Italy have pledged their support for the European Centre of Excellence for Countering Hybrid Threats, an organization that tracked Russia's disinformation warfare efforts, from which the US pulled out. [Politico]
Italy's new spying/RMM scandal: The Italian government is playing down a recent spying-related scandal related to its Ministry of Justice. Reporters from the Rai 3 TV channel have discovered that the ministry deployed a remote access tool on more than 40,000 computers at Public Prosecutors' Offices and Courts. Officials say the software was used for remote maintenance operations. Critics, including from inside the Prosecutors' Offices, claim the software didn't leave traces of its operations and it's impossible to tell when it was used… or abused to access sensitive judicial systems. The unnamed software has been deployed since 2019. [Il Sole 24 Ore]
Australia launches investigation into Chinese EV buses: Transport Canberra has launched an investigation into its Chinese EV buses after reports that the vehicles can be remotely shut down. Similar investigations are already underway in Norway, the Netherlands, and the UK. The investigations stem from a security audit conducted by Oslo's public transportation agency last year. [SupercarBlondie]
CISA's PQC list: CISA has published a list of product categories and technologies that should incorporate post-quantum cryptography (PQC) standards and protections going forward, if they want to be used by the US government.
US DOD NDS 2026: The US Department of Defense… erm, War… has published its National Defense Strategy for 2026 [PDF]. There's very little attention given to US cyber, besides the few generic "cyber defense" mentions.
CISA won't attend RSAC: CISA has confirmed that none of its employees will attend the RSA security conference this year. The move comes after RSA named former CISA director Jen Easterly as the conference's CEO. CISA said it was backing out of the conference to save costs. FBI and NSA officials have also pulled out of the conference in what appears to be a coordinated White House campaign to put pressure on the conference to ditch Easterly. [NextGov]
Color me skeptical that saving taxpayer money is the real reason for this change that CISA only made after RSAC appointed a Biden official as its CEO.
— Eric Geller (@ericjgeller.com) 2026-01-23T23:07:01.404Z
Sponsor section
In this Risky Business sponsor interview, Casey Ellis is joined by Push Security’s Field CTO, Mark Orlando. They chat about the ways that browser-based attacks are evolving and how Push Security is finding and cataloging them.
Arrests, cybercrime, and threat intel
Microsoft gave the FBI BitLocker keys: Microsoft has handed over BitLocker encryption keys to the FBI as part of a fraud investigation. The keys were saved to the Microsoft cloud and allowed agents to access the suspects' laptops and gather evidence. The company has told Forbes it receives around 20 requests for BitLocker keys per year, but in most cases it can't help because the keys have not been synced to its cloud.
Murder-for-hire group dismantled: Romanian authorities have dismantled a group that ran a murder-for-hire operation. The group operated a website that allowed anonymous users to pay for assassinations using cryptocurrencies. Authorities raided three locations and questioned two individuals behind the scheme. They also seized more than $750,000 in crypto, US dollars, and euros from their homes.

Zeppelin ransomware leader pleads guilty: A Russian national has pleaded guilty to leading the Zeppelin ransomware groups. Ianis Aleksandrovich Antropenko has admitted to hacking over 50 victims during a four-year period between 2019 and 2022. He was detained in August of last year but released on bail the same day. Authorities have seized $2.8 million in crypto from Antropenko. He now faces up to 25 years in prison. [CyberScoop]
Two ATM hijackers sentenced: A US judge has sentenced two Venezuelan nationals for their role in an ATM jackpotting scheme. Luz Granados was sentenced to time served and Johan Gonzalez-Jimenez received an 18-month prison sentence. The two operated across four US states. The two visited ATMs during the nighttime, opened their cases, and installed malware using a laptop.
PhaaS providers integrate vishing support: The makers of various phishing kits have now implemented support for voice-based social engineering operations (aka vishing) in their products, according to a new Okta report. According to another report, the ShinyHunters group is one of the threat actors heavily abusing these tools to breach corporate networks.
AiTM phishing attack abuses SharePoint: Microsoft's security team looked at a sophisticated campaign that abused SharePoint infrastructure to lure victims on AitM phishing pages that collected credentials that were later used for BEC attacks.
React2Shell in Russia: Russian security firm BI.ZONE looks at how React2Shell was exploited to target Russian companies. Most of the attacks deployed XMRig-based cryptominers. In some cases, the final payloads were the Kaiji and Rustobot botnets and the Sliver implant.
Common TTPs: The Cisco Splunk team looks at the shared TTPs across 18 of the most common RAT and infostealer families.
Scattered Spider infrastructure: Team Cymru has published a profile and infrastructure TTPs used by the Scattered Spider groups.
MSFT Teams VoIP numbers abused for scams: Scam groups are using VoIP phone numbers linked to the Microsoft Teams service to carry out PayPal refund and other related scams. The phone numbers are linked to the old Skype service. According to anti-scam group Demurrage, Microsoft has been failing to answer abuse reports about the activity. [CommsRisk]
MaliciousCorgi campaign: Two malicious VSCode extensions that worked as functional AI coding assistants secretly tracked and uploaded their users' activity to servers in China.
"Moving fast with AI tools is good. Moving fast without visibility into what they're actually doing with your code is how 1.5 million developers ended up with their workspaces harvested."
Malware technical reports
Amnesia RAT: Fortinet's security team looks at a campaign targeting Russian users with the Amnesia RAT and, sometimes, ransomware.
Stanley toolkit: A threat actor is selling access to a toolkit that can build malicious Chrome extensions that pass the Web Store verification process. The extensions can be used to spoof websites and help deploy malware on victims systems. The toolkit is being sold on a Russian-speaking hacking forum for prices ranging from $2,000 to $6,000.
MacSync: Daylight Security has published a report on MacSync, a macOS infostealer formerly known as Mac.c Stealer and currently distributed via SEO poisoning campaigns.
HijackLoader: There's a new campaign going on using the GPUGate technique to deliver the HijackLoader malware loader.
Sponsor section
In this wholly sponsored Soap Box edition of the show, Patrick Gray chats with Adam Bateman and Luke Jennings from Push Security.
APTs, cyber-espionage, and info-ops
DynoWiper used against Poland's energy grid: Russian hackers have deployed a data wiper in an attack against Poland's energy grid at the end of last year. The attack was blocked, but if successful, it would have cut power to half a million Poles. Security firm ESET linked the malware to Sandworm, an offensive cyber unit inside Russia's military intelligence service GRU. The incident marks the first time Russian hackers try to deploy wipers against an EU country's energy infrastructure. [Zero Day]
Exclusive: A cyberattack targeting Poland's energy infrastructure in December used wiper malware that would have erased grid computers and rendered them inoperable had it not been thwarted, a researcher at @ESET told me. The researcher calls the attack "unprecedented" for Poland and "substantial"
— Kim Zetter (@kimzetter.bsky.social) 2026-01-23T16:33:21.229Z
SyncFuture campaign: eSentire documents a cyberespionage campaign targeting India where the final payload is the SyncFuture TSM (Terminal Security Management System).
"While marketed as a legitimate enterprise tool, it is repurposed in this campaign as a powerful, all-in-one espionage framework. By deploying this system as their final payload, the threat actors establish resilient persistence and gain a rich feature set to monitor victim activity and centrally manage the theft of sensitive information."
KazakRAT: The Ctrl-Alt-Int3l research group has discovered KazakRAT, an Android trojan most likely used for cyber-espionage operations.
"We coined this sample “KazakRAT” as this was used in a campaign against Kazakh entities and we observed Kazakh victim IP addresses beaconing in. However, KazakRAT has also likely been used elsewhere within the globe. This RAT is not specific to Kazakhstan, but it sounds cool."
Andariel's European victim: WithSecurity looks at the malware used by the Andariel APT group in an intrusion of a European victim from the public/legal sector.
Contagious Interview: Threat intel analyst OZ has published a report looking at a Contagious Interview, a North Korean hacking group seeking to infect job seekers in the developers space with malware.
Vulnerabilities, security research, and bug bounty
New Zimbra attacks: Threat actors are exploiting a recently patched vulnerability in the Zimbra collaboration platform. Tracked as CVE-2025-68645, the vulnerability is a local file inclusion issue that allows attackers to run malicious code on the server. Active exploitation was reported by CISA last week. It was one of five (four+one) new 2025 vulnerabilities that CISA said were now seeing abuse.
osTicket vulnerability: A vulnerability (CVE-2026-22200) in a popular osTicket open source helpdesk system allows anonymous attackers to exfiltrate data or run malicious code on unpatched servers. Attackers can inject malicious PHP expressions into a ticket and then export its contents as a PDF. The bug has been patched this month but thousands of osTicket instances will need to be updated.
Microsoft retires MDT after bug reports: Microsoft has retired the Microsoft Deployment Toolkit, a tool to automate the deployment of Windows operating systems and applications across Windows fleets. The company retired the tool after researchers at SpecterOps discovered multiple vulnerabilities in the legacy tool. The vulnerabilities can allow attackers to take over MDT servers and deploy malware to managed hosts.
SMS delivery endpoints are leaking sensitive data: Academics have discovered more than 700 servers used to deliver SMS messages that are leaking data on the internet. Some of the leaked data included authentication links delivered to users via SMS. Many of the authentication links were also enumerable, expanding the initial breaches even more. Of the 150 online services that used the leaky servers, only 18 responded to researchers and took action. [ArsTechnica // arXiv paper]
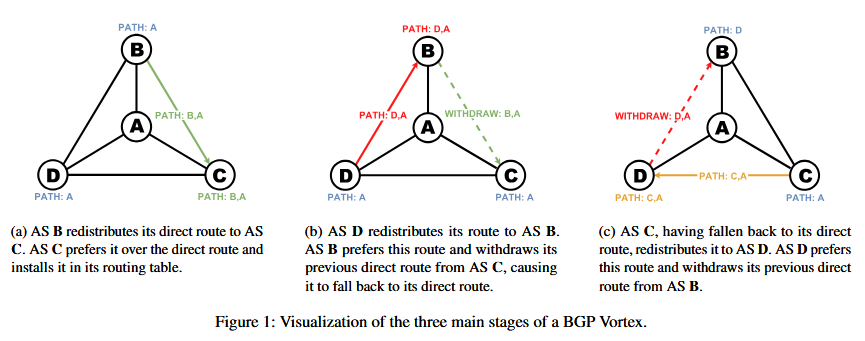
BGP Vortex attacks: Twenty-one of today's top largest internet networks are vulnerable to BGP vortex attacks that can cripple the global internet. These attacks leverage legitimate BGP configurations to reroute internet traffic in a loop between a handful of networks. According to a team of academics from the EU and US, a coordinated attack could bring down almost 96% of all internet networks.
NIST wants to transfer NVD enrichment to CNAs: The US National Institute of Standards and Technology is seeking help from third-parties in managing the US National Vulnerability Database. The agency wants to transfer its vulnerability-enrichment responsibilities to CVE Numbering Authorities, also known as CNAs. Since February 2024, NIST has fallen behind in enriching vulnerability with metadata and additional details. The agency says budget cuts have forced it to prioritize only the most critical reports. [CybersecurityDive // CyberScoop]
As new vulnerabilities flood NIST faster than it can analyze them, the agency is developing a triage process — and planning to cede the responsibility in the long term. My report from NIST's Thursday briefing to an advisory board about a critical project: www.cybersecuritydive.com/news/nist-cv...
— Eric Geller (@ericjgeller.com) 2026-01-23T16:30:49.005Z
Infosec industry
Threat/trend reports: BlackBerry, NordPass, Positive Technologies, PwC, and Red Canary have recently published reports and summaries covering various threats and infosec industry trends.
Tracking ransomware affiliates guide: The Ransom-ISAC team has published a guide on how threat intel analysts could track ransomware affiliates properly, without exposing themselves.
New tool—Malicious Extension Bot: There's a cool Mastodon account named Malicious Extension Bot that sends out notifications whenever new malicious browsers and IDE extensions are detected.
New tool—CERT UEFI Parser: The Software Engineering Institute at Carnegie Mellon University has open-sourced the CERT UEFI Parser, a tool for inspecting firmware ROM images, installers, and related files, especially those associated with UEFI.
New tool—Awesome Deception: Security firm Tracebit has published a collection of articles, papers, conferences, guides, and tools relating to deception in cybersecurity.
New tool—BaconSampler: Security firm Logisek has released BaconSampler, a tool to sniff outbound traffic for suspicious Cobalt Strike-like beacon callbacks.
New tool—Just the Browser: Software developer Corbin Davenport has released Just the Browser, a collection of browser configuration files, guides, and setup scripts that remove intrusive AI features and telemetry from browsers like Chrome, Firefox, and Edge.
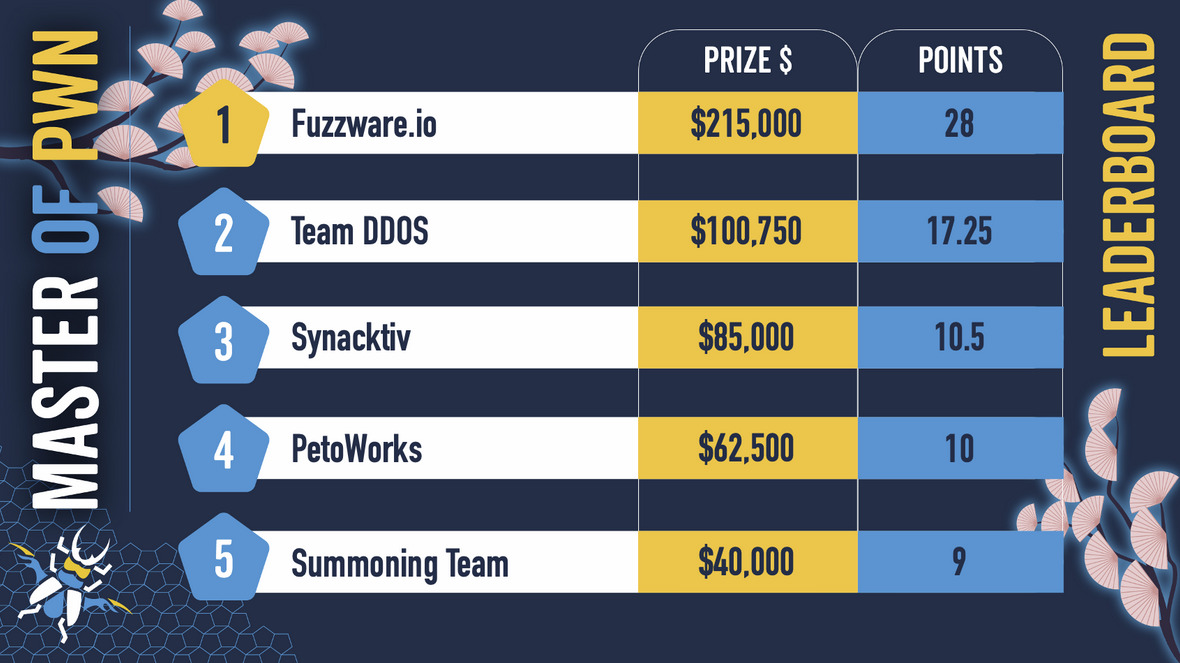
Pwn2Own Automotive results: The Fuzzware.io team has won this year's edition of the Pwn2Own Automotive hacking contest. The results from days one, two, and three are linked. This year, researchers won $1,047,000 for 76 unique bugs.
Risky Business podcasts
In this edition of Seriously Risky Business, Tom Uren and Amberleigh Jack talk about the rise of technologies that can undermine internet blackouts such as Starlink and its relatively new direct-to-cell service.
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about what information warfare even is, revisit a 30-year-old paper and examine why Western governments struggle with the concept.
