Risky Bulletin Newsletter
May 14, 2025
Risky Bulletin: EU launches its own vulnerability database
Written by

News Editor
This newsletter is brought to you by Corelight. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
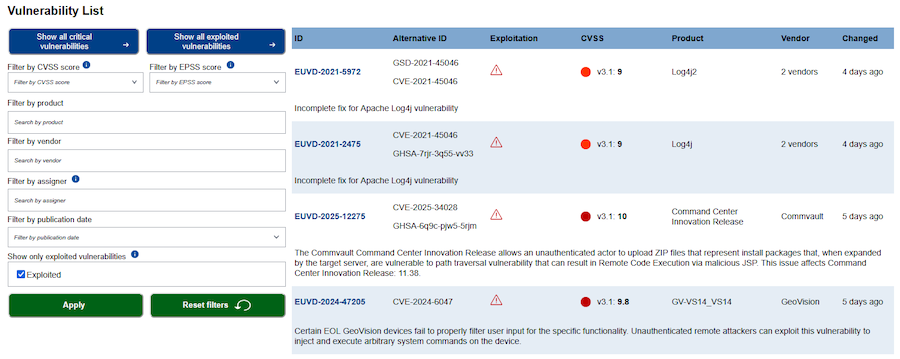
The EU's cybersecurity agency ENISA has launched its own vulnerability database designed to aggregate information on software bugs across the European ecosystem.
Although some infosec researchers might think this is the EU's reaction to the recent MITRE funding issues in the US, the new EUVD database was coming anyway, regardless of what was happening to the CVE program.
The EU actually ordered ENISA to create the new database via the NIS2 directive that passed in December 2022—see paragraphs 62 and 63.
From the get-go, the EU was aware that similar vulnerability databases existed but wanted one under its direct control and subject to its transparency rules.
EU officials may not say it, but they suspect that US and Chinese counterparts may be delaying the listing of vulnerabilities in their national databases in order to exploit them in attacks, which is kinda true for both countries.
Having your own separate database will allow ENISA to spot reporting gaps in other DBs and (maybe) run a more complete system. But this is me theory-crafting since it's not clear how all the moving parts will work.
We'll have to wait for September this year when, thanks to the EU Cyber Resilience Act, software manufacturers will be required to report exploited bugs.
NIS2 actually mandates ENISA to establish and operate a European Vulnerability Database! Hopefully this gives them even more incentive to launch sooner than later. (Combined with the upcoming vuln reporting obligations under the CRA this has the potential to be a real game changer).
— mxrt (@mxrt.bsky.social) 2025-04-15T19:10:06.439Z
Cybersecurity companies focused on vulnerability management services will be very delighted to have a new and reliable source of new information, especially one coming from such a huge market.
The EUVD can issue its own CVEs—since it's also an authorized MITRE CNA—but it will also run its own vulnerability numbering and ID system, which will not mirror the CVE and might create some confusion.
Right now, the EUVD is not completely independent. It looks more like a central aggregator for bugs first disclosed somewhere else. How this evolves will most likely depend on how strict the EU will be with upholding NIS2 and CRA.
Risky Business Podcasts
Risky Business is now on YouTube with video versions of our main podcasts. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
Mobius crypto-heist: Hackers have exploited a vulnerability in the Mobius platform to steal $2.15 million worth of crypto tokens. [Additional coverage in CoinTelegraph]
Alabama cybersecurity event: Alabama state officials are investigating a security breach after IT staff detected suspicious network activity at the end of last week. Officials said attackers obtained credentials for some state employees. The personal data of state residents appears to be untouched, according to a preliminary investigation. [Additional coverage in StateScoop]
Dior China breach: A hacker has stolen customer data from the Chinese branch of French fashion house Cristian Dior. Stolen data included names, emails, phone numbers, and home addresses. The company notified users last week and asked customers to be vigilant for possible phishing emails. [Additional coverage in Global Times]
General tech and privacy
Microsoft Teams to add screen capture protection: Microsoft will add a new feature to the Teams messenger to block users from taking screenshots during meetings. The new feature is named Prevent Screen Capture and will work by turning the meeting screen black whenever a user tries to take a screenshot. The feature is set to roll out for all platforms in July this year.
Microsoft layoffs: Microsoft has laid off ~6,000 employees, or around 3% of its 228,000 global employees. [Additional coverage in CNBC]
Google confirms Android Advanced Protection: Android 16 will launch with a new security feature named Advanced Protection that enables more powerful protections for Android devices. We reported this back in April, and confirmed this week by Google.
Government, politics, and policy
US Army deactivates information warfare center: The US Army has deactivated its information warfare center, known as 1st Information Operations Command. The center was established in 2002 and was tasked with providing information warfare capabilities and training for Army operations. Its functions will be taken over by the broader Army Cyber Command. The order to deactivate the center was given out in 2024, before the second Trump administration. [Additional coverage in DefenseScoop]
CBP confirms using TeleMessage: The US Customs and Border Protection agency has confirmed it was one of the several government agencies using the TeleMessage service to log conversations taking place in secure messengers. TeleMessage was hacked twice earlier this month. [Additional coverage in WIRED]
CISA updates: CISA announced on Monday that it would stop updating its RSS feeds and websites and only share updates via Twitter and email. The agency changed its mind a day later after the huge community backlash. (I did my part o7)
US bill wants to criminalize pornography: A Republican senator has introduced a bill to criminalize pornography, both producing and consuming it. Spear-phishing operators are gonna have the easiest lay-up in history if this one passes. [Additional coverage in Gizmodo]
A tiny GFW in Henan: Academics have discovered a local Great Firewall-like censorship system deployed exclusively in China's Henan region, working independently and about ten times more aggressively than China's main Great Firewall.
Spain to probe cyber's role in energy grid collapse: Spain's cybersecurity agency is probing small and medium electricity providers on their cybersecurity practices. The inquiry is part of an investigation into the nationwide collapse of the country's power grid at the end of April. According to the Financial Times, officials have yet to identify the root cause and have not fully excluded a possible cyberattack.
ENTSO-E expert panel initiates the investigation into the causes of Iberian blackout - First information on the chronology of events leading to the blackout www.entsoe.eu/news/2025/05...
— Stephan Beirer (@beirer.bsky.social) 2025-05-10T18:59:20.148Z
Sponsor section
In this Risky Bulletin sponsor interview, James Pope, Director of Technical Enablement, talks to Tom Uren about his experience running networks and security centers at Black Hat conferences around the world. Pope talks about the challenges of running a SOC at a hacker conference, how conference networks around the world have a different character and talks about all the weird and wonderful security snafus he has found.
Arrests, cybercrime, and threat intel
Russian cadet detained for selling MOD hack tool: Russian authorities have arrested a cadet from the A.F. Mozhaisky Military Space Academy for selling a hacking tool designed to access government networks. The tool allegedly allowed attackers to bypass security systems on the Russian Ministry of Defense network and access classified information. The student sold the tool on the Avito classified ads portal for only $100 before he was detained by the FSB last week.
BlackDB admin extradited: US officials have extradited a Kosovo man on charges of running BlackDB, an online marketplace for selling hacked accounts, hacked servers, and stolen payment card details. Liridon Masurica was arrested at the end of last year. If convicted in the US, he faces up to 55 years in prison.
DragonForce threatens affiliates: The DragonForce group has tried to distance itself from the possible use of its ransomware in attacks targeting hospitals, critical infrastructure, or Russian companies. In a forum post, the group said any such attacks are against its rules and will likely be the work of an unruly and unscrupulous partner. Similar attacks have usually been the downfall of other major ransomware operations. The group is one of today's most known ransomware groups thanks to its recent attacks against UK retailers. [Additional coverage in the Daily Mail]
Telegram takes down crypto-scam laundering channels: Telegram has taken down thousands of accounts used by crypto scammers to launder proceeds from pig butchering operations. The channels laundered over $35 billion worth of cryptocurrency originating from online scams and cryptocurrency hacks. Blockchain investigations firm Elliptic says some of the channels were run by Huione Guarantee, a Cambodian company sanctioned by the US earlier this month. Another set of accounts was run by Xinbi Guarantee, a similar operation that catered to Chinese-speaking scammers.
Scammers target Middle East students in the US: Scammers posing as DHS agents are contacting foreign students in the US with fake immigration issues and demanding payments to settle immigration issues. Victims are threatened with prosecution or deportation unless payments are made to settle paperwork and other legal fees. The scammers are primarily targeting students from Middle East countries and are taking advantage of recent ICE raids targeting pro-Palestinian protesters.
Malware technical reports
Pupkin Stealer: CyFirma put out an analysis of Pupkin Stealer, a .NET-based stealer coded by a Russian-speaking developer.
Chihuahua Stealer: G DATA also published a report on Chihuahua Stealer, which appears to be their own name for the same Pupkin Stealer from above.
Lumma Stealer: The Cloudflare security team has published a technical analysis of Lumma Stealer, one of today's most widely used infostealers.
Tycoon 2FA: ANY.RUN looks at how the Tycoon 2FA PhaaS has evolved its evasion techniques over the past months.
Sponsor section
Volt Typhoon, a Chinese APT targeting critical infrastructure, is exploiting unmanaged appliances and evading EDR. Learn how the best defense against this and other advanced attacks is your network. Learn more.

APTs, cyber-espionage, and info-ops
Swan Vector APT: Seqrite researchers have published a report on Swan Vector, a suspected Chinese APT campaign targeting organizations in Japan and Taiwan.
Chinese APT behind NetWeaver attacks: Following an initial report from Forescout, EclecticIQ has now also confirmed that a Chinese APT was behind a recent SAP NetWeaver zero-day (CVE-2025-31324).
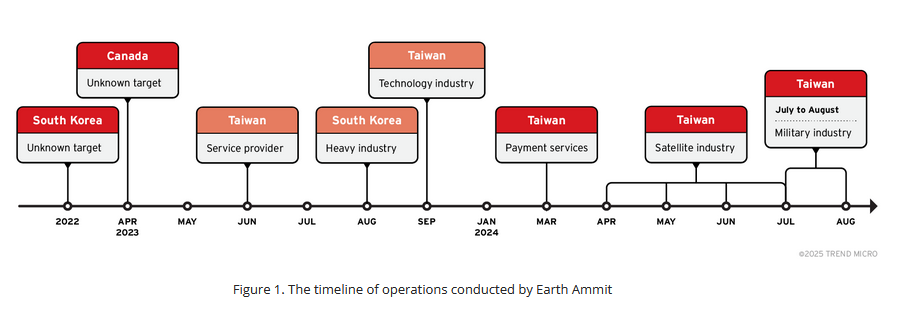
Earth Ammit targets Taiwanese drone industry: Earth Ammit, a threat actor linked to multiple Chinese cyber-espionage groups, has targeted the Taiwanese software and drone industry over the past two years. The attacks stood out because of the group's abuse of fiber-based APIs in Windows to bypass EDRs.
North Korea sends APTs to Ukraine: A North Korean APT is targeting the Ukrainian government in a campaign designed to collect intelligence on the progress of the Russian invasion. The group, known as Konni or TA406, has a history of targeting Russia, but this marks the first time it's targeting Ukrainian government entities. The shift in operations took place in February, a few months after North Korea committed troops to assist Russia's invasion.
Pakistani APTs: Indian officials claim to have identified seven Pakistani APTs attacking Indian IT infrastructure in the aftermath of the Pahalgam terror attack. Details are scarce and this smells like propaganda. [Additional coverage in Times of India]
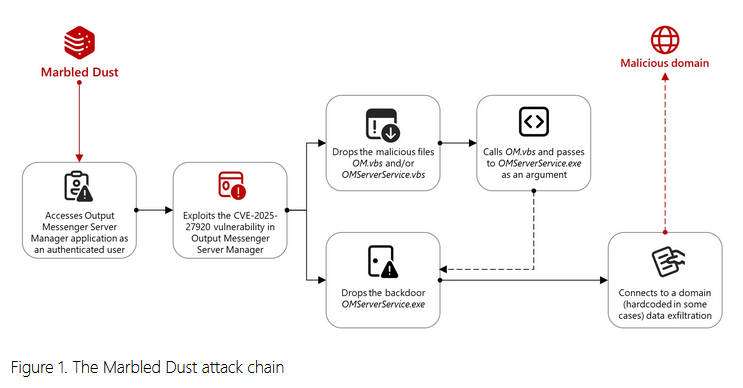
Marbled Dust deploys zero-day in Iraq: A Turkish cyber-espionage group exploited a zero-day vulnerability in the Output Messenger to target members of the Kurdish military in Iraq. Tracked as CVE-2025-27920, the zero-day allowed the group to deploy malicious files, backdoor Output Messenger servers, and steal and compromise connected clients. The attacks took place last year, and the zero-day was patched in December. Microsoft's security team attributed the operation to a group it tracks as Marbled Dust, also known as Sea Turtle and UNC1326.
Vulnerabilities, security research, and bug bounty
Patch Tuesday: Yesterday was the May 2025 Patch Tuesday. We had security updates from Adobe, Apple, Microsoft, SAP, Ivanti, Fortinet, Supermicro, Intel, AMD, Arm, Zoom, Dell, ASUS, Schneider Electric, and Siemens. The Android Project, Cisco, Juniper, Ubiquiti, SonicWall, AWS, Fortra, NVIDIA, Elastic, Drupal, Kubernetes, Chrome, Firefox, and Moxa released security updates last week as well.
Microsoft Patch Tuesday: This month, Microsoft patched 71 vulnerabilities, including five zero-days:
- CVE-2025-30400: Microsoft DWM Core Library Elevation of Privilege Vulnerability
- CVE-2025-32701: Windows Common Log File System Driver Elevation of Privilege Vulnerability
- CVE-2025-32706: Windows Common Log File System Driver Elevation of Privilege Vulnerability
- CVE-2025-32709: Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability
- CVE-2025-30397: Scripting Engine Memory Corruption Vulnerability
FortiVoice zero-day: Fortinet has patched a zero-day vulnerability exploited in attacks against FortiVoice phone systems. Tracked as CVE-2025-32756, the zero-day allows remote unauthenticated attackers to run malicious code using specially crafted HTTP requests sent to the device API. Attacks were spotted targeting FortiVoice devices, but Fortinet says FortiMail, FortiNDR, FortiRecorder, and FortiCamera are also vulnerable to the same issue.
Invati EPMM zero-day: Ivanti has released a security update to fix two zero-days in its mobile device management platform EPMM. Attackers are chaining the two zero-days to bypass authentication (CVE-2025-4427) and run malicious code on EPMM servers (CVE-2025-4428). Ivanti says the zero-days are located in two open-source libraries used by its EPMM software. It did not name the two libraries.
Spectre v2 returns: Security researchers have found a new technique to execute Spectre v2 CPU side-channel attacks. The new Training Solo technique bypasses all current mitigations, including domain isolation protections. Arm and Intel processors are vulnerable, including Intel's latest generation Lion Cove series.
"Unlike previous Spectre-v2 attacks, 'Training Solo' shows how to bypass (even perfect) domain isolation without needing to cross privilege boundaries. We re-enable Spectre-v2 attacks from entirely within the victim domain."
Another Spectre v2 attack: But Training Solo is not the only new Spectre v2 attack, there's also another one from ETH Zurich researchers. This one impacts Intel CPUs and is described as a branch privilege injection flaw (CVE-2024-45332).
Roll your own crypto research: A CitizenLab research project has found that many Chinese mobile apps from the Mi Store are using their own cryptographic protocols instead of the more established TLS. Why? Because it allows network eavesdropping and interception. Enjoy using those Xiaomi store apps, folks!
"We analyzed the 18 most popular protocols from WireWatch, which belonged to 9 protocol families, including cryptosystems designed by Alibaba, iQIYI, Kuaishou, and Tencent. We found that 8 of these protocol families sent requests that allowed network eavesdroppers to decrypt underlying data, including browsing data and device metadata, among various other issues, such as being downgradable, not validating TLS certificates, and the use of RSA without OAEP."
Zoom VDP: Video conferencing software Zoom has published its yearly report on its vulnerability disclosure program.
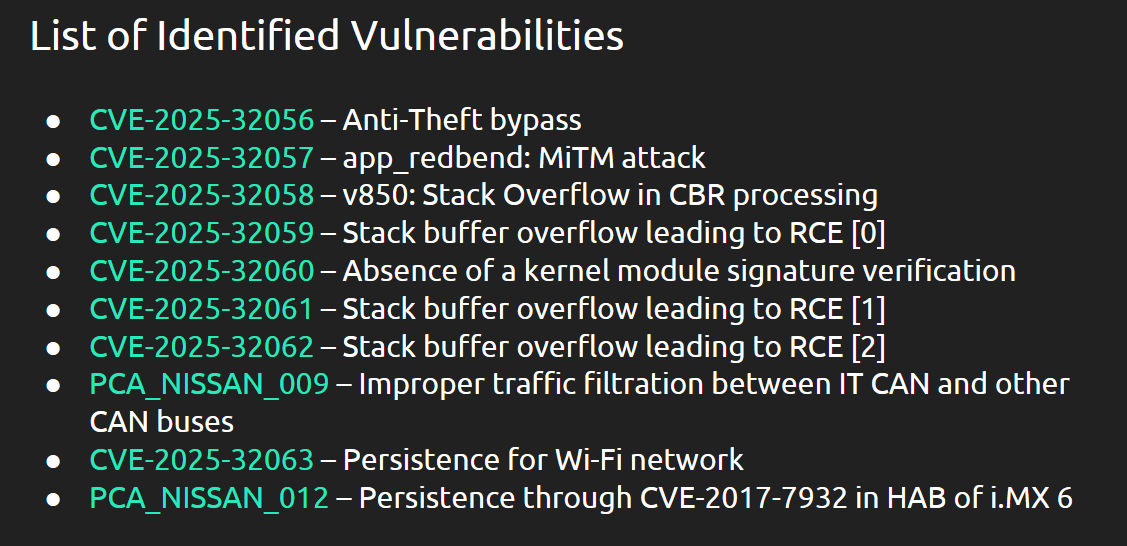
Nissan LEAF hacking: Security researchers from Hungarian security firm PCAutomotive have discovered eight vulnerabilities in Nissan LEAF car models. The bugs allow control over the car's telematic unit, the infotainment systems, and even its most sensitive component, the CAN bus. An attacker could track and geolocate vehicles and record conversations inside the car. They could also control core vehicle features, such as opening doors, starting wipers, and even turning the wheel while the car is in motion. [Additional coverage in Electrek]
Infosec industry
New tool—IntuneRBAC: Software engineer Ugur Koc has released IntuneRBAC, a PowerShell-based tool for managing and auditing Role-Based Access Control (RBAC) in Microsoft Intune.
Threat/trend reports: Abnormal AI, Black Kite, OAIC, and PeckShield have recently published reports and summaries covering various infosec trends and industry threats.
Risky Business podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq examine whether the US should steal intellectual property from Chinese companies.
Tom Uren and Patrick Gray talk about how the US is planning to take the gloves off in cyberspace and conduct much more aggressive offensive cyber operations. US responses to cyber espionage have not been very aggressive to date, but Tom is not convinced that cyber punches are required, so much as blows that really hurt.
