Risky Bulletin Newsletter
January 21, 2026
Risky Bulletin: Domain resurrection attacks come to Canonical's Snap Store
Written by

News Editor
This newsletter is brought to you by SpecterOps, the experts in Attack Path Management. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
A threat actor is registering expired web domains in order to take over email servers, reset passwords on abandoned developer accounts, and publish malware on the Canonical Snap Store for Linux packages.
At least two developer accounts have been hijacked using this technique, also known as a domain resurrection attack, namely for Snap packages published using email addresses from storewise.tech and vagueentertainment.com.
According to Linux expert and former Canonical dev Alan Pope, the threat actor behind this campaign is a group he believes are located in Croatia.
The group's main target has been cryptocurrency owners, and they've repeatedly deployed malicious crypto-wallets on the Snap Store in the hopes of capturing passwords and recovery phrases they can use to empty accounts.
The attackers have been prodigious and launched several campaigns against Snap Store users over the past two years, using various other techniques, such as publishing packages with typosquatted names or benign-looking packages that turn malicious during a subsequent update.
"The domain takeover angle is particularly concerning because it undermines one of the few trust signals users had: publisher longevity. Canonical needs to address this, whether that’s monitoring for domain expiry on publisher accounts, requiring additional verification for accounts that have been dormant, implementing mandatory two-factor authentication, or something else entirely. I don’t have all the answers, but I know the current situation isn’t sustainable."
The Snap Store joins GitHub, PyPI, and npm as other package repositories that have seen domain resurrection attacks against their users.
As the internet rots away and as developers move from job to job, or email provider to email provider, they don't always update all their accounts with a newer email address.
A 2022 academic study found over 2,800 npm developer accounts that were set up using email addresses whose domains had since expired.
In June of last year, the Python security team removed more than 1,800 email addresses from developer accounts that had expired and were prone to hijacking, forcing developers to re-verify their email with a live domain the next time they logged in.
Risky Business Podcasts
In this special documentary episode, Patrick Gray and Amberleigh Jack take a historical dive into hacking in the 1980s. Through the words of those that were there, they discuss life on the ARPANET, the 414s hacking group, the Morris Worm, the vibe inside the NSA and a parallel hunt for German hackers happening at a similar time to Cliff Stoll’s famous Cuckoo’s Egg story.
The main Risky Business podcast is now on YouTube with video versions of our recent episodes. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
Hackers disrupt Iranian state TV: Hackers have disrupted the broadcast of Iran's state TV channel to show anti-government propaganda. The hacks showed messages from the country's exiled crown prince urging the military to join the anti-regime protests. The Iranian military shot and killed thousands of protesters across multiple Iranian cities last week. [Ynet]
Another Apple contractor gets ransomed: A major Apple iPhone assembler has fallen victim to a ransomware attack. The RansomHub group claims to have stolen circuit board designs and internal documents from Chinese company Luxshare. The stolen files allegedly include data Apple and NVIDIA products for the past six years. [Cybernews]
Makina Finance crypto-heist: The Makina Finance DeFi platform lost $4.2 million worth of cryptocurrency in a security breach over the weekend. It's still unclear what happened but the platform didn't seem to have been affected and continued operating normally. [CoinSpeaker]
SK telecom appeals breach fine: SK Telekom has appealed a $91 million fine imposed by the South Korean government over a major security breach last year. [The Korea Times]
General tech and privacy
Nothing in this edition.
Government, politics, and policy
CISA CIO on the chopping block: CISA acting head Madhu Gottumukkala tried to forcibly reassign the agency's chief information officer last week. Robert Costello was given the choice to accept a management-directed reassignment or resign by Friday. Gottumukkala backed down after huge pushback from the agency's senior officials. Costello has been the CISA CIO for the past four years. [Politico]
New CISA 2015 extension: Congress is preparing to extend the CISA 2015 information-sharing law again, set to expire at the end of the month. [The Record]
Ireland passes new lawful interception law: The Irish government has passed a new lawful interception law. The new legislation grants law enforcement and intelligence agencies the power to surveil any type of modern communications channel. It also grants the agencies the right to use covert software for their operations, such as spyware. The new law will also require communication service providers to work closely and aid any government operation.
EDRi asks for spyware ban: The European Digital Rights (EDRi) group has asked EU lawmakers to ban the use of spyware across the bloc.
Report Fraud launches in the UK: The British government has launched a new service for reporting online scams, cybercrime, and fraud. The new Report Fraud service soft-launched in December and was made broadly available this week. It will replace the UK's older cybercrime reporting tool Action Fraud. The new service features a more streamlined process that also allows victims to submit evidence for criminal investigations.
Russia to use AI to detect VPN traffic: Russia's internet watchdog will use AI technology to analyze internet traffic and automatically detect VPN users. The Roskomnadzor will spend close to $30 million to develop the system this year. The Russian government has blocked access to tens of VPN apps and considers it a crime to share information on how to use VPNs to circumvent its internet censorship system. [Forbes Russia]
Millions of cards blocked in Russia: Russian banks have blocked access to almost 3 million cards and bank accounts since the start of the year. The banks acted on new banking fraud detection rules issued by the Russian Central Bank. The new rules doubled fraud detection rules from six to twelve. This resulted in almost 2% of Russia's population having their cards blocked, with some Russians reporting their card getting blocked after mundane operations like paying for goods online. [Kommersant]
The funny thing is that I specifically remember going "they'll botch this 100%... just wait" when I added this to the newsletter Well, I waited... they botched it 🤣
— Catalin Cimpanu (@campuscodi.risky.biz) 2026-01-20T16:44:16.034Z
Sponsor section
In this Risky Business sponsor interview, Tom Uren talks to Justin Kohler, Chief Product Officer at SpecterOps, about how attack paths exist in the seams between different identity or permissions management domains.
Arrests, cybercrime, and threat intel
SMS blasters arrested in Greece: Greek authorities have arrested two Chinese nationals for sending SMS spam. The suspects drove with an SMS blaster in their car around Athens suburbs. The device was discovered by accident after the two were questioned by police in a mall and later had their car searched. [CommsRisk]
Victim wants its ransom back: Real estate company Minto Holdings is seeking to recover a ransom payment from the developer of the Qakbot malware. The company is seeking $830,000 from Rustam Rafailevich Gallyamov, a 49-year-old Moscow resident. Gallyamov was charged last year with running Qakbot, a botnet that infects corporate networks and facilitates ransomware attacks. [h/t CourtHouseNews]
New scam compound investigation in Cambodia: The Cambodian government has started an investigation into how Chinese nationals who were major figures in the country's local scam compound operations obtained their citizenship. [KiriPost]
All of the other senior figures in the Prince network have Cambodian citizenship, as do many other figures linked to the scam industry. It might be time for a review of the thousands of passports issued to foreigners over the last decade. 2/2
— Cyber Scam Monitor (@cyberscammonitor.bsky.social) 2026-01-19T08:12:46.855Z
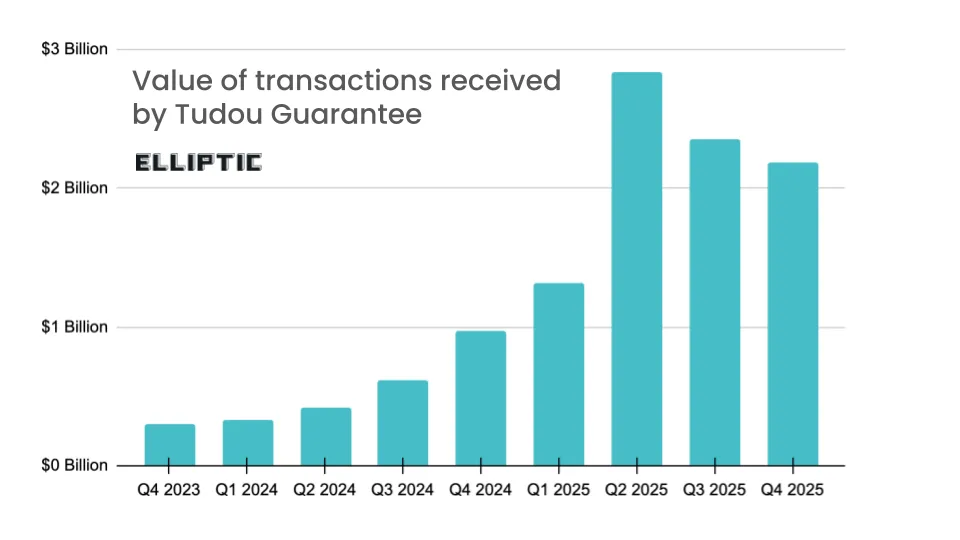
Tudou Guarantee shuts down: A Telegram-based marketplace that provided cyber scam and other illicit services appears to have shut down most operations. Prior to its shutdown, the marketplace processed more than $12 billion in user transactions. According to Elliptic, this makes Tudou the third-largest illicit marketplace of all time. Tudou launched last year after Telegram shut down the Huione Guarantee marketplace, even a larger service that processed $27 billion worth of similar transactions.
Belarus arrests HAM radio operators: The Belarusian government, for some yet unknown reason, has started arresting HAM radio operators and charging them with treason. [Siarhei Besarab]
Russian hacktivists are still at it: The UK NCSC says pro-Kremlin hacktivists are still engaging in DDoS attacks, reiterating a warning it sent out last year.
WP badness: GreyNoise looks at a cluster of malicious infrastructure that is carrying out large-scale scans and exploitation of WordPress sites.
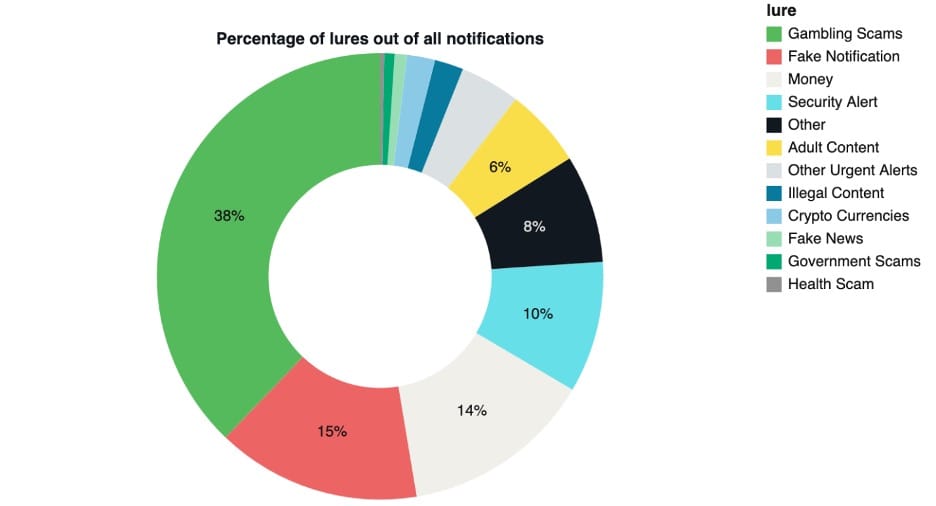
Push spam network profile: Infoblox was able to infiltrate a giant operation that pushed browser push notification spam across the globe. According to collected data, the operation was sending roughly 140 push notifications to each victim every day. It sent notifications in 60 languages and on a wide variety of topics, from gambling to malware.
Malware technical reports
Mamba PhaaS: CyFirma has spotted a new Phishing-as-a-Service provider named Mamba. The service supports Attacker-in-the-Middle capabilities and appears to be in its early stages of development.
VoidLink created using AI: Security firm Check Point believes the new VoidLink malware framework was almost entirely coded using AI tools. The malware was discovered this month and was designed to specifically target Linux servers running in cloud environments. Despite its complexity, Check Point believes the malware is the work of a single developer using the TRAE AI-based IDE.
Evelyn Stealer: Trend Micro has spotted a new infostealer named Evelyn Stealer that is currently being distributed via malicious VSCode extensions.
Lockbit 5.0: South Korean security firm S2W has published a technical analysis of the Lockbit 5.0 ransomware.
"The update from LockBit 4.0 to 5.0 significantly enhances analysis evasion and attack efficiency. It adds numerous new features like Mutex, Execution Delay, Status bar, Delete TEMP, and Wiper, while also overhauling the volume shadow copy deletion method and large file encryption logic."
Sponsor section
Justin Kohler, VP of Product at SpecterOps, shows how BloodHound Enterprise can be used to find and fix Active Directory (mis)configurations that could let attackers easily own your entire enterprise.
APTs, cyber-espionage, and info-ops
Operation Nomad Leopard: Seqrite looks at an APT group targeting Afghanistan government bodies. The campaign delivers malicious attachments via email to infect victims with the FalseCub backdoor.
North Korea's VSCode abuse: Jamf looks at a North Korean op using VSCode project files to deploy malware.
Iranian hackers coming through Starlink: Iranian hacking group Handala is carrying out attacks via Starlink connections. According to security firm Check Point, activity from the group stopped when the Iranian regime cut off the internet across the country. New Handala attacks were spotted a few days later coming from Starlink IP ranges. The Handala group poses as a hacktivist group but is secretly run by Iran's MOIS intelligence service.
Iran’s internet has gone dark and Iranian hackers are using #Starlink.
— Check Point Research (@_CPResearch_) January 19, 2026
After a week of quiet we are seeing that “Handala Hack” of MOIS is back, operating from Starlink IP ranges and hitting targets across the Middle East.
We continue tracking. pic.twitter.com/H2luLmeLJs
Vulnerabilities, security research, and bug bounty
Glibc patches 30yo bug: The GNU C Library has patched a bug in its code dating back to 1996. Per reports, exploitation scenarios are limited, so it's not really much of a big deal. [Phoronix]
TP-Link security updates: TP-Link has released a security update for its VIGI cameras to patch a critical device takeover vulnerability. The bug can allow attackers on the same LAN to bypass authentication during the password reset process. The vulnerabilities impact 32 VIGI camera models. [SecurityWeek]
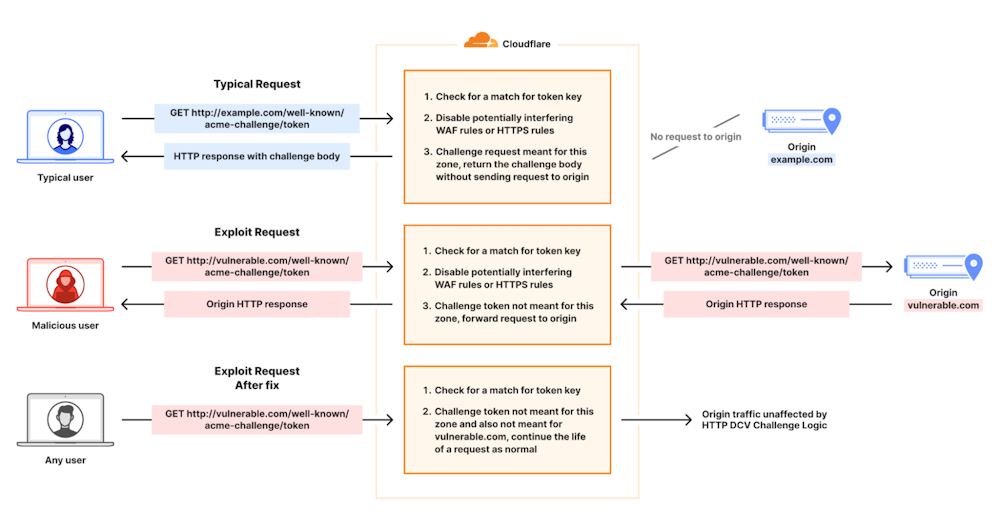
Cloudflare patches ACME bug: Cloudflare has patched a vulnerability in its ACME certificate manager that could have allowed threat actors to bypass security controls and firewalls.
Infosec industry
Threat/trend reports: ANY.RUN, eSentire, Gen Digital, and Netskope have recently published reports and summaries covering various threats and infosec industry trends.
Risky Business podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about what information warfare even is, revisit a 30-year-old paper and examine why Western governments struggle with the concept.
In this edition of Seriously Risky Business, Tom Uren and Amberleigh Jack talk about the Chinese government's reactive approach to tackling scam compounds. It's driven by bad news on domestic media and therefore focuses on the compounds that are targeting Chinese citizens. Rather than eliminating the industry, that may instead be shaping the industry to focus on other countries and particularly Americans.
