Risky Bulletin Newsletter
February 06, 2026
Risky Bulletin: Denmark recruits hackers for offensive cyber operations
Written by

News Editor
This newsletter is brought to you by Dropzone. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
Denmark's military intelligence service has launched a campaign to recruit cybersecurity specialists for offensive cyber operations.
The recruits will work "to compromise the opponents’ networks and obtain information for the benefit of Denmark’s security," the Forsvarets Efterretningstjeneste (Danish Defence Intelligence Service, or DDIS) said in a press release last week.
The new recruits will go through a five-month training course at the agency's hacker academy.
The DDIS says it is only interested in the applicants' skills and there are no special conditions for joining, such as age and education requirements.
Intelligence agencies are always recruiting, but this particular announcement comes at a crucial point, both because of the Greenland pressure point but also because of a general shift towards offensive cyber operations among democratic states.
Countries like Canada, Germany, Finland, France, Japan, the Netherlands, Poland, and Sweden have or are updating their legal frameworks to account for offensive cyber operations.
The states are also creating new agencies for offensive cyber or recruiting more cyber personnel for the new objectives, according to a Binding Hook report from last week.
Most of these expansions are a direct result of Russia's invasion of Ukraine and the role offensive cyber operations have played before and during the conflict. Lawmakers are also getting annoyed with the increasing aggressiveness of cybercrime and influence operations that are constantly targeting their citizens.
Over the past half decade, we have also seen US Cyber Command and the NSA successfully tackle some cybercrime and disinfo farms when they crossed some lines, something that is making other states take notice and embrace as a "defend forward" approach.
While the US has conducted more offensive cyber operations than any other Western democracy, even it is considering an expansion, with the Trump administration pushing Congress to let Cyber Command go on the offensive more often and with fewer rules and restrictions.
The new administration is also terrified of China's massive cyber ecosystem, which is conducting cyber espionage at an industrial scale. Recent backroom discussions have raised the issue of the US also tapping into its huge private contracting ecosystem, just like China, to shore up some of its offensive cyber capabilities. The general idea floated right now is to let contractors handle smaller jobs targeting cybercrime infrastructure while government agencies handle the more sensitive operations.
Risky Business Podcasts
The main Risky Business podcast is now on YouTube with video versions of our recent episodes. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
New Coinbase insider breach: A malicious insider has stolen and sold to hackers the data of around 30 Coinbase users. The new breach was discovered after the Scattered Lapsus Hunters posted a screenshot of a Coinbase support interface on Telegram. Coinbase says the breach took place in December and it has now fired the contractor. This is Coinbase's second insider breach over the past year. [BleepingComputer]
Conduent breach grows larger: A ransomware attack on US government contractor Conduent impacted far more individuals than initially thought, with the total ballooning to the real of tens of millions. [TechCrunch]
PSNI officers get breach compensation: Police officers in Northern Ireland will receive £7,500 in compensation over a 2023 data breach that exposed their data. More than 9,400 cops and police staff had their data leaked online due to a website misconfiguration. A day after the payouts were announced, the police force suffered another breach after a local court published the names of dozens of officers on its website. [Police Federation of Northern Ireland // [Belfast Telegraph]
MilChat hack rumors: There are reports in Russian media claiming that two pro-Kremlin hacktivist groups have breached Ukraine's MilChat, a soldier messenger platform, and Reserve+, the army's recruitment platform. There's nothing on this except Russian media and it's unclear if there was an actual breach or just online yapping.
US used cyber weapons against Iran: The US military allegedly used cyber weapons to disrupt Iran's air missile defense systems. The operation took place last year during US strikes on Iran's nuclear program. The cyberattack allegedly prevented Iran from launching its surface-to-air missiles during the US air strike. CyberCommand called it one of its most sophisticated actions it ever took against Iran. The US is currently amassing forces near Iran and this report can very well be a psyop. [The Record]
Russian hackers targeted Olympics, again: Russian hackers launched cyberattacks targeting the Milano Winter Olympics. Italian officials say they blocked attacks that targeted websites for this year's Olympics, hotels in Cortina d'Ampezzo, and its foreign ministry offices. Russia has been banned from this year's Olympics due to repeated doping infractions and its invasion of Ukraine. Russian hackers previously also targeted the Paris 2024 and Pyeongchang in 2018 Olympic events. [DW]
Harvard and UPenn hacks: Although it was suspected, the ShinyHunters group has now formally claimed credit for the hacks of Harvard University and University of Pennsylvania last year. [TechCrunch]
La Sapienza cyberattack: One of Europe's largest universities has gone offline after a cyberattack this week. The La Sapienza University in Rome called the IT shutdown a precautionary measure. The university serves more than 120,000 students.
Substack breach: Newsletter platform Substack has exposed customer data in a security breach last October. An intruder collected user emails, phone numbers, and metadata for some Substack users. The company has notified affected users after discovering the hack this week.
"I'm reaching out to let you know about a security incident that resulted in the email address and phone number from your Substack account being shared without your permission. … This sucks. I'm sorry. We will work very hard to make sure it does not happen again." - Chris Best, CEO of Substack
— Steve Herman (@newsguy.bsky.social) 2026-02-05T02:23:25.152Z
General tech and privacy
Microsoft has a new security exec: Microsoft has appointed Hayete Gallot as the company's new Executive Vice President for Security. Gallot replaces Charlie Bell, who is moving to oversee engineering quality. Gallot spent the last two years as President for Customer Experience at Google Cloud. Prior to that she spent 15 years at Microsoft across multiple roles, including security.
Sysmon ships with Windows 11: Sysmon has been added as a built-in Windows utility in this week's release of Windows 11 Insider Preview builds, with the rollout to the main branch expected this spring.
Azure TLS migration: Microsoft has stopped supporting TLS 1.0 and 1.1 for Azure Blob Storage this week. Azure customers have been asked to migrate to at least TLS 1.2.
Adobe Animate EOL: Adobe is putting its Animate app in "maintenance mode," where the product is available, will receive fixes, but no new features going forward.
42% of Android devices don't get security updates: Around 42% of all Android devices are running outdated versions that don't receive security updates. According to Google's latest Android distribution numbers, only 7.5% of devices run the latest Android version, v16. The slow rollout is due to smartphone vendors, who took months to deploy it to their devices. [9to5Google]
Pinterest fires staff for "custom scripts": Pinterest fired two engineers who coded custom scripts to track who was getting fired in the company's layoffs. The scripts scanned which Slack usernames were being deactivated and removed. Pinterest instead claimed the script accessed confidential data. The company announced layoffs of 15% of its staff last week as it was re-focusing on AI features going forward. [BBC]
Internet Archive is getting locked out of the web: News sites are blocking the Internet Archive, aka the Wayback Machine, from indexing their sites to prevent AI companies from scraping their content from its repos. [The Conversation]
WaPo layoffs: The Washington Post is firing almost a third of its staff, including many of its reporters. The layoffs will impact the paper's cyber and tech divisions.
Most of the Washington Post’s tech reporters were laid off today, including me. I have loved my time at the paper, which is where I wanted to work from age 15. I take some consolation in not being among the survivors who will have to work harder with less for fewer readers. On to better things.
— Joseph Menn (@joemenn.bsky.social) 2026-02-04T16:47:55.223Z
Government, politics, and policy
EU tests Matrix for internal comms: The European Commission is testing a new internal communications tool based on the Matrix protocol. There are no official plans to replace Microsoft Teams, but this could change if the test is successful. The EU's Financial Services Commissioner Maria Luis Albuquerque has called this week on the Union to focus on digital sovereignty and move away from US tech. [Euractiv // Reuters]
No killswitch detected in smart meters: Dutch officials say they haven't found any killswitch mechanism in Chinese-made smart meters. An investigation of Kaifa Technologies smart meters did not find anything suspicious. Dutch officials said the Kaifa component only measures electricity use and that grid operators use their own components for data transfer operations. The company's devices are set to be installed in more than four million Dutch homes.
South Korea and Myanmar to collaborate: Police forces in South Korea and Malaysia have signed a memorandum to collaborate and crack down on cyber scam compounds. [Yonhap News]
AI-ISAC close to launch: Speaking at an event, a CISA official says the AI Information Sharing and Analysis Center, or AI-ISAC, is close to an official launch. [CybersecurityDive]
Trump admin abuses administrative subpoenas: The DHS is abusing a process called "administrative subpoenas" to request data from US tech companies on anti-ICE protesters and critics of the Trump administration. These subpoenas can be issued without a judge. They also carry no legal requirement for tech companies to comply. [TechCrunch]
CISA tells agencies to remove old edge devices: CISA has told federal agencies to decommission old and unsupported edge devices within the next 12 months. Agencies will have to inventory their networks and monitor when devices reach End-of-Support. CISA will provide an initial list of devices that have reached their End-of-Support and should be targeted for removal within the next months.
Telecoms block Salt Typhoon docs: AT&T and Verizon are blocking the release of sensitive reports about their Salt Typhoon hacks. The two companies have invoked attorney-client privilege to block Google Mandiant from sharing the reports with Congress. Senator Maria Cantwell has asked the Senate Committee on Commerce, Science and Transportation to hold a new meeting and force the companies to share the reports. The office of Committee Chairman Ted Cruz says it is not interested in holding a new meeting on the hacks. [CyberScoop]
Cruz's office doesn't seem interested in holding the hearing that Cantwell requested. A Cruz spokesperson says the committee "discussed Salt Typhoon and other cybercommunications threats" at a December hearing on telecom security.
— Eric Geller (@ericjgeller.com) 2026-02-03T20:12:32.783Z
Sponsor section
In this Risky Business sponsor interview, Casey Ellis chats to Edward Wu, founder of Dropzone AI about a recent Vanderbilt University report that reveals that foreign adversaries’ resources are growing. Edward says AI capabilities are critical to the future of cyber defence, because the west can’t hire itself out of the shortfall.
Arrests, cybercrime, and threat intel
Fake prince scam netted $2.5m: A Romanian businesswoman lost $2.5 million to scammers posing as Dubai's Crown Prince. The victim thought she had been recruited for a humanitarian investment by the UAE royal house. Authorities from the UK and Romania traced the fake Dubai prince to a Nigerian scammer. [OCCRP]
Scam network impersonates law firms: Security firm Sygnia has discovered a network of 150+ websites impersonating real law firms and targeting users looking for legal advice and representation. The sites are hosted on infrastructure that previously hosted many other scams.
Incognito Market admin sentenced to 30: A US court has sentenced a Taiwanese national to 30 years in prison for running the Incognito dark web marketplace. The site was used to trade more than $105 million in illegal drugs, as well as other illicit services. Rui-Siang Lin was arrested in May 2024 at the JFK Airport in New York. He was detained two months after he shut down the site and ran away with his users' money.
EnCase abuse: Huntress has spotted threat actors abusing a legitimate Guidance Software (EnCase) forensic driver to disable EDRs in the wild.
SCR abuse: There's a new malware campaign spreading RMM tools using malicious Windows screensaver files (.scr).
Dead#Vax campaign: Securonix looks at a stealthy malware campaign that uses an uncommon chain of VHD files, script-based execution, self-parsing batch logic, and fileless PowerShell injections to drop RAT.
CrashFix campaign: Microsoft has published a report on CrashFix, the new ClickFix social engineering tactic that mimics browser crashes to trick users into running malicious PowerShell commands that later install an infostealer on their systems.
NGINX attacks: DataDog has identified a threat actor using the React2Shell vulnerability to take over NGINX web servers. The attackers install tools to hijack and redirect their traffic to their own domains.
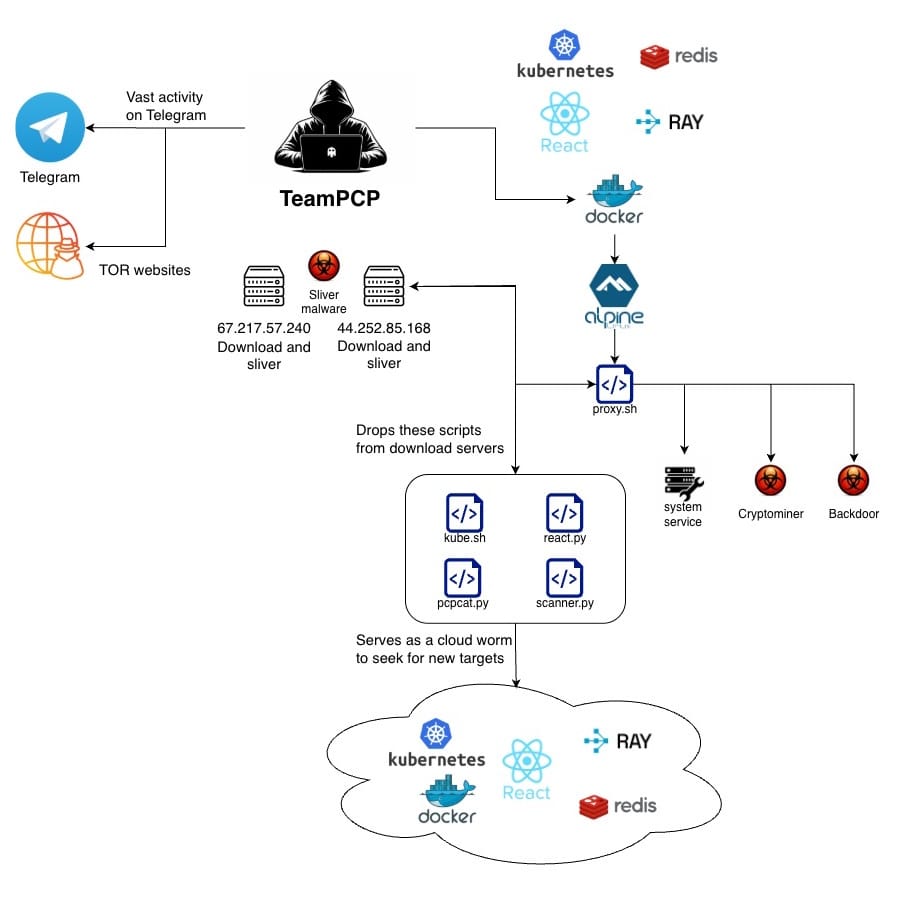
TeamPCP targets the clouds: A newly observed cybercrime group launched a massive hacking campaign targeting cloud environments. Starting with November of last year, TeamPCP (PCPcat, ShellForce, PersyPCP, DeadCatx3) compromised cloud environments to steal data for future extortions and deploy cryptominers. The attacks targeted misconfigured cloud technologies like Docker, Kubernetes, Ray dashboards, and Redis databases. Some of the stolen data is now being ransomed via public Telegram groups.
New ShadowSyndicate infrastructure: Group-IB researchers have uncovered new infrastructure linked to ShadowSyndicate, a threat actor specialized in compromising servers and then renting them to cybercrime groups for their operations.
Stan Ghouls profile: Kaspersky has published a profile on Stan Ghouls, a cybercrime group also known as Bloody Wolf. The group is behind campaigns with the NetSupport RAT that have targeted Russian and other CIS countries.
Rublevka Team makes $10m: A Russian cybercrime group has made over $10 million over the past two years by stealing cryptocurrency via social media scams. The Rublevka Team uses social media posts and ads to lure victims to fake crypto promotion sites. It then uses a custom crypto-drainer kit to empty the accounts of users who connect their crypto-wallets.
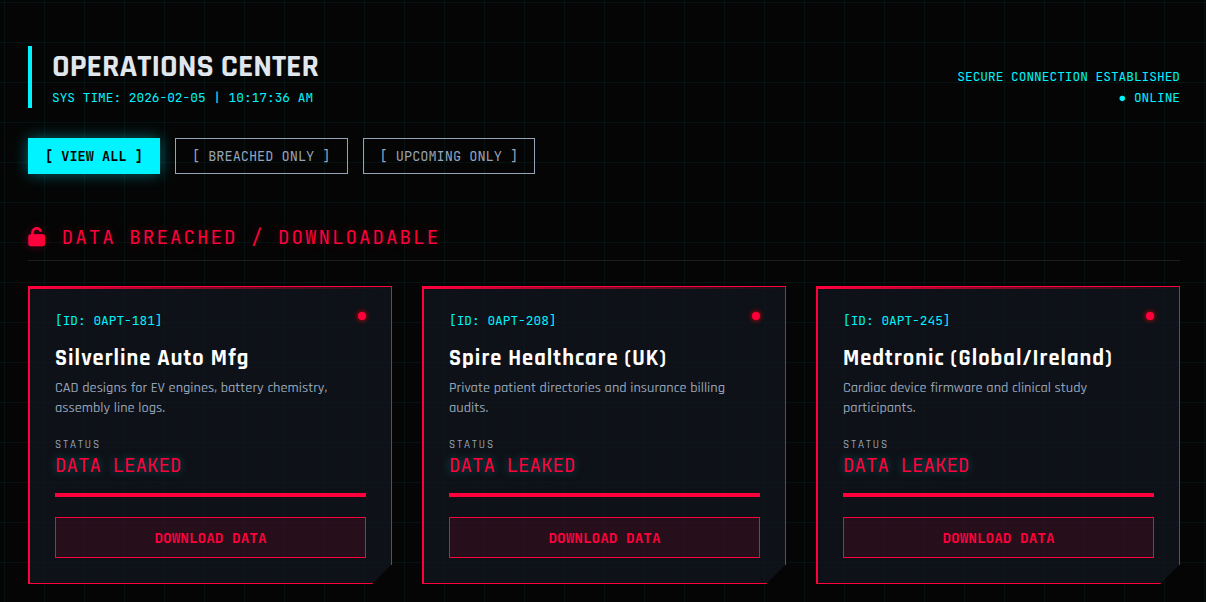
New 0apt group is a fraud: A new data extortion group (maybe ransomware?) has popped up on the dark web last week, with a leak site containing the names of almost 100 victims. The group goes by 0APT. According to DataBreach, the names of some of the victim companies appear to be randomly generated. Others are real, but it's unclear if they have been actually hacked.
Malware technical reports
Black Basta adopts BYOVD: According to a new Broadcom report, the Black Basta ransomware group is now using Bring Your Own Vulnerable Driver (BYOVD) tactics in attacks, installing vulnerable drivers, exploiting them to elevate privileges, and then using the access to kill security tools.
Marco Stealer: Zscaler looks at Marco Stealer, an infostealer first spotted in June of last year. It is one of the hundreds of new infostealers that launched last year.
RenEngine Loader: The Cyderes team has uncovered a new malware strain, the RenEngine Loader. The malware is currently being used together with the HijackLoader to deploy various infostealers on infected systems.
SystemBC reaches 10K: The SystemBC malware botnet has now infected more than 10,000 Windows systems, according to a new report from Silent Push, which built a custom tracker to follow the botnet's operations.
RondoDox: Logpoint researchers look at the evolution of RondoDox, a major IoT botnet that has evolved from mass-spraying exploits for run-of-the-mill smart devices to incorporating fresh vulnerabilities for enterprise applications. The botnet now also supports more CPU architectures.
Sponsor section
In this sponsored product demo, Dropzone founder and CEO Edward Wu walks Risky Business podcast host Patrick Gray through the company's AI SOC analyst.
APTs, cyber-espionage, and info-ops
APT28 targets Europe's military: Russia's military hackers are targeting European military and government agencies. A cyber unit tracked as APT28 is using a recently patched Microsoft Office zero-day (CVE-2026-21509) in a campaign that focuses on maritime and transport organizations. Attacks have been spotted targeting Poland, Slovenia, Turkey, Greece, the UAE, and Ukraine. [Trellix // similar reports from CERT-UA, Synaptic Systems, and Zscaler]
Matryoshka jumps on the Epstein train: Russian disinformation group Matryoshka is using the recently released Epstein files to spin up fake claims and attack France and Ukraine officials. [The Insider]
Iran internet outage impacts APT group activity: An Iranian cyber-espionage group went silent for 16 days during Iran's recent internet outage. According to SafeBreach, during the outage, the Prince of Persia (Infy) group didn't exfiltrate any new files or register new domains. The group resumed activity a day before the blackout was lifted for the rest of the population.
Transparent Tribe: Acronis says the suspected Pakistani APT Transparent Tribe has recently expanded operations to target India's startup ecosystem.
"The use of Crimson RAT to deliver via startup-themed lures and container-based files reflects a continued reliance on proven tooling adapted for new victim profiles. Reuse of malware, infrastructure and tradecraft across earlier campaigns strongly reinforces attribution and demonstrates that emerging technology sectors are now core intelligence targets, along with the previous sectors."
APT‑Q‑27 (GoldenEyeDog): CyStack looks at a mid-January campaign of APT-Q-27 that targeted Southeast Asian financial institutions.
TGR-STA-1030: A new state-sponsored APT group has compromised organizations across 37 countries. Victims over the past year include law enforcement agencies, government ministries, diplomatic entities, and critical infrastructure operators. Its operations routinely align with international or regional events. The group operates out of Asia and has recently expanded reconnaissance operations to target 155 countries. Palo Alto Networks tracks the group as TGR-STA-1030.
Amaranth-Dragon: Check Point looks at Amaranth-Dragon, a group closely connected to APT41 campaigns. It's unclear, but from the report this seems to be the TGR-STA-1030 group listed above.
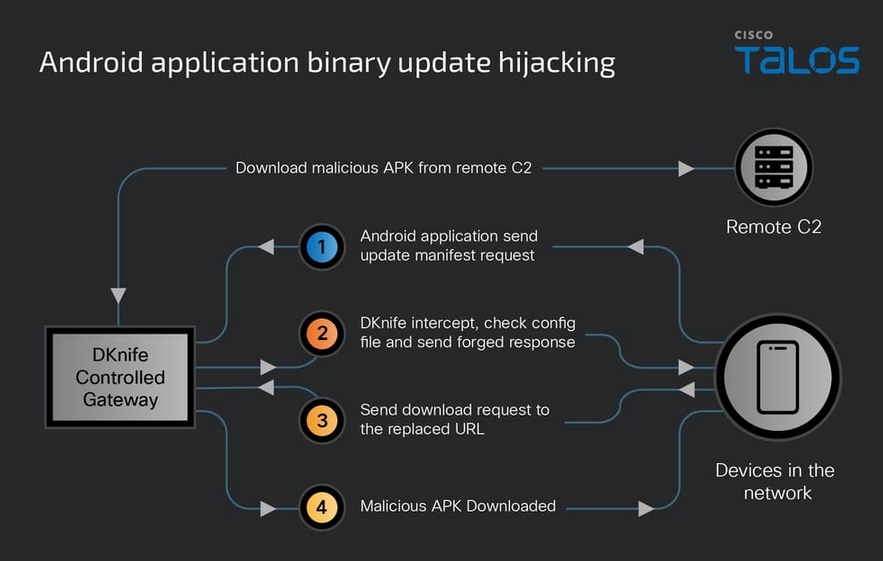
DKnife framework: Chinese state-sponsored hackers are using a special tool named DKnife for adversary-in-the-middle (AitM) attacks. The toolkit is meant to be installed on routers and network edge devices. It performs deep-packet inspection and manipulates traffic to deliver malware to specific targets. Cisco says the tool has been used in the wild since 2019 and command-and-control infrastructure was active as recently as last month.
Vulnerabilities, security research, and bug bounty
Zyxel RCE: Security researcher Alessandro "RainPwn" Sgreccia has discovered an RCE vulnerability in the Dynamic DNS feature of Zyxel routers.
Cisco security updates: Cisco has released five security advisories for its firewall products.
Detecting backdoored LLMs: Microsoft has released new research on how to check the integrity of AI agents and detect backdoored LLMs at scale.
CVE changes date format: The CVE program will update the date format for older vulnerabilities this month. The new yyyy-MM-ddTHH:mm:ss.sssZ format was introduced in February last year, but older entries use a different system.
Infosec industry
Threat/trend reports: Cloudflare, Cybereason, International AI Safety, Malwarebytes, and runZero have recently published reports and summaries covering various threats and infosec industry trends.
Acquisition news #1: Cybersecurity and enterprise backup solution Varonis will acquire AI Trust, Risk, and Security Management (AI TRiSM) startup AllTrue for $125 million.
Acquisition news #2: Cybersecurity firm Semperis is acquiring cloud IdP startup MightyID.
New tool—KEV Collider: Security firm runZero has launched KEV Collider, a tool that enhances the CISA KEV catalog with additional metadata.
New tool—Dropkit: Security firm Trail of Bits has open-sourced Dropkit, a command-line tool for managing DigitalOcean droplets with automated setup, SSH configuration, and lifecycle management.
JSAC videos: Talks from Japan CERT's JSAC 2025 security conference, which took place last January, are available on YouTube. This year's edition videos have not yet been uploaded.
leHACK videos: Talks from the leHACK 2025 security conference, which took place last June, are available on YouTube.
Risky Business podcasts
In this edition of Seriously Risky Business, Tom Uren and Amberleigh Jack talk about Google's cyber disruption unit taking aim at the IPIDEA residential proxy network. The network was a cybercrime enabler that was used by hundreds of threat actors for crime and espionage.
In this edition of Between Two Nerds, Tom Uren and The Grugq discuss the recent Russian attack on Polish electricity infrastructure.
