Risky Bulletin Newsletter
September 22, 2025
Risky Bulletin: Cyberattack disrupts airports across Europe
Written by

News Editor
This newsletter is brought to you by SpecterOps, the experts in Attack Path Management. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
A cyberattack has disrupted flights at multiple airports across Europe and elsewhere over the weekend.
The attack brought down self-service kiosks used by passengers to check in, drop luggage, and print boarding passes for their flights.
While the kiosks are installed in hundreds of airports, the disruption forced an usually large number of travelers to manual check-in counters, creating cascading delays that slowly bogged down the larger airports as time went on.
Hundreds of flights were delayed or canceled at the airports in London, Berlin, Brussels, Dublin, Cork, and other places.
The attack itself ARINC SelfServ vMUSE kiosks operated by Collins Aerospace, a company owned by RTX (previously known as Raytheon). The attack had a broader impact the more vMUSE devices were installed at an airport.
See this Kevin Beaumont thread for some technical details. From the thread, it looks like the attackers affected the vMUSE user database, which is preventing the devices from authenticating and working.
In the meantime, Collins flew technicians to affected airports to restore service for each set of devices.
According to CNBC, the company and affected airports have asked airlines to cancel some of their flights on Sunday and Monday to alleviate check-in traffic and avoid more delays and cancellations.
It's unclear who was behind the attack, and if the attackers are state-backed, hacktivists, or an e-crime group.
Risky Business Podcasts
The main Risky Business podcast is now on YouTube with video versions of our recent episodes. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
KT reports security breach: South Korea's second-largest mobile operator apologized on Friday for a security breach. Korea Telecom, or KT, says attackers have stolen the IMSI and IMEI codes and the phone numbers of its customers. Unknown individuals allegedly used two fake cell towers to collect data on over 5,500 subscribers. Attackers harvested IMSI and IMEI codes and the phone numbers of nearby customers. KT discovered the breach after receiving reports of fraudulent micropayments from affected customers. [Additional coverage in the Korea JoongAng Daily and Korea Times]
NGP crypto-heist: Hackers have stolen $2 million worth of NGP tokens from the New Gold Protocol DeFi platform. [Additional coverage in The Block]
Brain data incident: There was some weird reporting last week that a Chinese tech company named BrainCo, tied to the country's military, secretly collected brain wave data from a focus-training headband worn by some of the world's top athletes. [Additional coverage in Hunterbrook]
General tech and privacy
Samsung rolls ads to its fridges: After putting a giant screen on fridge models, Samsung is now shoving ads on those screens without giving users the option to decline after they paid up to $2,000 for some models.
LinkedIn resumes training AI on EU data: LinkedIn will resume training its AI models on the data of EU, Canadian, and UK users. The company paused the process at the end of last year after pressure from EU privacy watchdogs. The company updated its terms of service last week to include the new behavior. LinkedIn is already training its AI on US user data since last November. [Additional coverage in Bloomberg Law]
Steam drops 32-bit: Valve will drop support for 32-bit platforms in its Steam gaming client starting next year.
"Existing Steam Client installations will continue to function for the near term on Windows 10 32-bit but will no longer receive updates of any kind including security updates."
RubyGems takeover: The Ruby Central team has taken over the RubyGems package repository from its current maintainers and revoked everyone's access. Ruby Central says that going forward, "only engineers employed or contracted by Ruby Central will hold administrative permissions" over RubyGems. [Additional coverage in Seuros, Andre Arko, Pup-e/PDF]
Government, politics, and policy
ICE signs new social media surveillance contract: US Immigration and Customs Enforcement has signed a new $5 million contract with Cobwebs. The company provides tools to track activity on social media and the dark web. ICE also has active contracts with three other known surveillance tech vendors—Clearview AI, Paragon Solutions, and Magnet Forensics. [Additional coverage in Forbes]
Criticality of public-private partnerships: FNN's Jen Sovada looks at the growing importance and criticality of US public-private partnerships after recent cuts to the US cybersecurity budget.
New Pentagon cyber policy chief: The US Senate confirmed Katherine Sutton last week as the next Pentagon cyber policy chief. Sutton replaces Laurie Buckhout, who led the office after it was set up in March last year. The Assistant Secretary of Defense for Cyber Policy is a civilian role that advises the DOD on cyber policy. [Additional coverage in The Record]
DOD cyber talent hiring window: The Pentagon wants to shorten the hiring window for cybersecurity talent to only 25 days. The department currently averages 70 days for a new hire. The DOD says it's short almost 20,000 cyber professionals and has accelerated hiring efforts. A GAO report published last week put the DOD's cyber workforce total at just over 70,000 civilian and military staff. [Additional coverage in CyberScoop]
CISA wants international involvement in CVE program: CISA wants international partners to contribute to the CVE vulnerability management program. Officials didn't clarify what this means. CISA said in a paper two weeks ago that it was looking to expand community partnerships for managing the CVE. The CVE database is run by the MITRE Corporation, and the program almost collapsed in April after CISA funding lapsed. [Additional coverage in NextGov]
China bans NVIDIA chips: The Chinese government has told local companies to stop buying NVIDIA chips. According to the Financial Times, companies were told to stop tests and cancel future orders. The move is part of Beijing's efforts to boost the local semiconductor sector and cut US dependence. Chinese officials accused the US last month of trying to sneak backdoors inside NVIDIA chips.
Germany cyberattack costs: The German economy lost an estimate €300 billion due to cyberattacks last year. Almost half of the attacks that could be traced back were traced to China and Russia. [Additional coverage in Reuters]
EU to exclude US tech firms from new financial system: The EU is moving to exclude US tech companies from the Union's new financial data-sharing system. Under a German proposal, companies like Amazon, Apple, Google, and Meta will be barred from accessing the shared data. Only banks will be allowed access to the data. According to the Financial Times, US tech firms are "facing almost certain defeat" in their lobby efforts. The ban is part of the EU's new push for digital sovereignty.
Sponsor section
In this Risky Business sponsor interview, Catalin Cimpanu talks with Jared Atkinson, CTO at SpecterOps. They discuss how SpecterOps is using classifying identities under two categories, identities at rest and identities in transit, what they are, and how they should be treated differently.
Arrests, cybercrime, and threat intel
Canada seizes TradeOgre: Canadian authorities have seized cryptocurrency platform TradeOgre. Authorities received a tip about the platform from Europol in 2024. TradeOgre allegedly failed to register with authorities and identify its users, enabling money laundering and other crimes. Officials say they seized $40 million and plan to investigate the collected transaction data. This is the first time that Canadian authorities dismantled a cryptocurrency exchange platform.
Scattered Spider teen turns himself in: A member of the Scattered Spider hacking group has turned himself in to Las Vegas police. The suspect, identified as a teenage boy, was allegedly involved in the 2023 hacks of several Las Vegas casinos and hotels. He faces six felony charges. The teen surrendered to police a day before the US charged a UK national for his central role in the group's attacks.
King Bob profile: Bloomberg has published a profile on Noah "King Bob" Urban, a member of the Scattered Spider hacking group that was recently sentenced to 10 years in prison.
Moldova raids Russian disinfo farm: Moldovan authorities have raided a media company for spreading Russian propaganda and disinformation. Authorities say the organization was illegally financed by the outlawed party of Ilan Sor. Sor is a Moldovan pro-Russian oligarch who fled the country after being sentenced to 15 years in prison for bank fraud. He has been financing pro-Kremlin parties and propaganda in the country for the past half-decade.
New npm malware: Three hundred malicious npm packages were discovered and taken down last week. Check out the GitHub security advisory portal for more details.
FBI website spoofing alert: The FBI says threat actors are spoofing its crime-reporting website in campaigns designed to collect personal and financial data.
Malware technical reports
DeerStealer: CyFirma has spotted yet another infostealer advertised and sold via Telegram. This one's named DeerStealer.
Akira ransomware: ZenSek has published a technical analysis of the Akira ransomware, with data from 30 incident response cases.
KawaLocker ransomware: AhnLab has spotted a new ransomware strain named KawaLocker, or KAWA4096. See similar reports on the same strain from Huntress and Trustwave.
"One intriguing point from correlation analysis is the visual similarity between Kawa4096's leak site and that of the Akira ransomware group. Akira is known for its retro-style Tor site, reminiscent of 1980s green-screen consoles, featuring a command-line interface. While this resemblance could imply a direct connection or rebranding effort, it may also be a case of design imitation."
Sponsor section
Justin Kohler, VP of Product at SpecterOps, shows how BloodHound Enterprise can be used to find and fix Active Directory (mis)configurations that could let attackers easily own your entire enterprise.
APTs, cyber-espionage, and info-ops
Turla and Gamaredon work together for the first time: Two Russian cyber-espionage groups have been spotted working together for the first time. Both groups operate under the Russian FSB intelligence service, but under different regional centers. Gamaredon operates from Crimea, while Turla from Moscow. ESET has seen one group's malware drop or restart the other group's payloads. Researchers believe Gamaredon is now working as an initial access provider for more complex Turla operations.
APT-C-00: Qihoo 360 has published a report on a recent APT-C-00 phishing campaign that drops Havoc payloads. The group is also known as APT32 and OceanLotus.
APT27 profile: DeXpose has published a profile on APT27, a Chinese cyber-espionage group also known as Iron Tiger and Emmisary Panda.
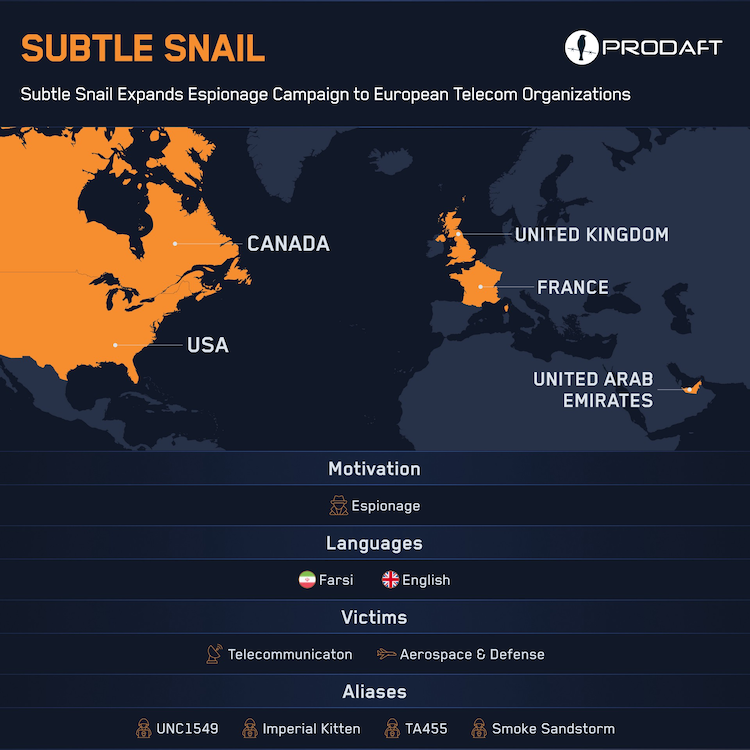
Subtle Snail (UNC1549): An Iranian cyber-espionage group is using fake LinkedIn jobs to target employees of EU telcos and defense organizations. According to security firm Prodaft, one of the group's most recent campaigns has infected 34 devices across 11 organizations. Prodaft linked the attacks to a group it tracks as Subtle Snail. The group has been active since at least June 2022 and is believed to be a smaller cluster inside the larger Charming Kitten operation.
Vulnerabilities, security research, and bug bounty
L1TF Reloaded attack: Google has published more details on how the recently disclosed L1TF Reloaded attack works and impacts its services. The company says it awarded the researchers $151,515 for reporting the bug.
Fortra critical bug: Fortra released a security update last week to patch a critical vulnerability in its GoAnywhere file transfer application. Tracked as CVE-2025-10035, the vulnerability allows threat actors with a forged license to execute deserialization attacks and run malicious commands on remote systems. According to VulnCheck, the vulnerability is nearly identical to another GoAnywhere bug exploited by ransomware and extortion gangs in 2023. Fortra has urged customers to take their admin console off the internet and patch. The vulnerability has a CVSSv3 rating of 10.
Chaotic Deputy vulnerabilities: Four vulnerabilities in the Chaos-Mesh Kubernetes engineering toolkit can be exploited to allow in-cluster attackers to run malicious code on any pod in the cluster. The vulnerabilities, discovered by JFrog, are named Chaotic Deputy.
Chypnosis attack: A team of academics from Europe has developed a new undervoltage attack against FPGAs. The attack, named Chypnosis, was tested on AMD, Microchip, and Open-Titan devices.
Infosec industry
Threat/trend reports: Gartner, Guardz, Kaspersky, Lenovo [PDF], Netwrix [PDF], and Privacy Journal have recently published reports and summaries covering various threats and infosec industry trends.
New tool—Microsoft Vulnerable Driver Block Lists: Security researcher Mehmet Ergene has published the Microsoft Vulnerable Driver Block Lists after Microsoft stopped publishing the list in a browsable web page.
New tool—MFTool: Security researcher Kurosh Dabbagh Escalante has released MFTool, a tool to parse MFTs and NTFS.
New tool—BadPie: Security researcher DTM has released BadPie, a proof-of-concept transparent proxy PyPI mirror to serve malicious updates.
New tool—EDR-Freeze: Red teamer Two Seven One Three has released EDR-Freeze, a tool that exploits the software vulnerability of WerFaultSecure to suspend the processes of EDRs and antimalware services without needing to use the BYOVD technique.
ComfyCon and PancakesCon 2025 streams: Live streams from the ComfyCon and PancakesCon 2025 security conferences, which took place over the weekend, are available on YouTube.
Black Hat Asia 2025 videos: Videos from the Black Hat Asia 2025 security conference, which took place in April, are available on YouTube.
Risky Business podcasts
In this edition of Seriously Risky Business, Tom Uren and Amberleigh Jack talk about why it is good news that US investment in spyware vendors has skyrocketed. They also discuss the in-principle agreement for TikTok to remain in the US. It's a win-win: a win for China and a win for TikTok, but not so much a win for US national security.
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about the limits of a state's cyber power.
