Risky Bulletin Newsletter
February 05, 2025
Risky Bulletin: Crypto-stealer makes it on the iOS App Store
Written by

News Editor
This newsletter is brought to you by Thinkst, the makers of the much-loved Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
Kaspersky researchers have discovered a new crypto-stealer that has found its way into both the iOS and Android app stores.
Named SparkCat, the trojan takes photos from the phone's gallery and scans them with an OCR module to extract text that may appear in any of the images.
The malware looks for text that resembles mnemonic phrases in different languages, which may indicate the photo might be a screenshot of a cryptocurrency wallet recovery phrase.
Any photos matching mnemonic phrases are uploaded to the attacker's servers.
Kaspersky says the malware's malicious code was disguised inside benign-looking SDKs used for both the Android and iOS apps. The malware's name comes from Spark, the malicious SDK used for Android apps, and bigCat, the SDK used for iOS.
Researchers say they found the Spark SDK in multiple Android apps uploaded to the Play Store that have been downloaded more than 242,000 times—with some of the apps still active.
They only found one malicious iOS app on the Apple App Store. While visibility was limited on iOS, researchers found clues that multiple iOS apps were developed, with some being offline or not containing the malicious code—at least yet.
Kaspersky says the malware was advanced for several reasons, such as the use of the Rust programming language for some of its code, the targeting of both iOS and Android ecosystems, and its encrypted codebase.
The malware also used the Google ML Kit, a machine learning model for mobile developers, to scan images for text. This makes SparkCat the second known malware strain to use the ML Kit to extract crypto-wallet recovery phrases from images after a similar malware family spotted in 2023 by ESET.
Kaspersky says that based on the keyword recognition patterns and OCR modules it loaded, the malware appears to have targeted audiences in Europe and Asia.
Some of the malware's source code also contained comments in Chinese, making researchers believe the attacker was fluent in the language.
Risky Business Podcasts
Risky Business is now on YouTube with video versions of our main podcasts. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
Grubhub security breach: Food delivery service Grubhub says hackers accessed the personal details of customers, diners, and drivers. Hackers stole names, emails, phone numbers, and partial payment card data. They also stole hashed passwords for some legacy systems. Grubhub tracked the breach to a third-party service provider for its support service. The company says it terminated its contract with the third-party provider and rotated passwords for internal systems.
Breach mills: Edu sector news outlet The 74 has published a profile on "breach mills" and "breach coaches," a term used to describe law firms and lawyers that work to keep security breaches secret.
Trump Twitter account hacked: US President Donald Trump's Twitter account was hacked to promote a shitcoin.
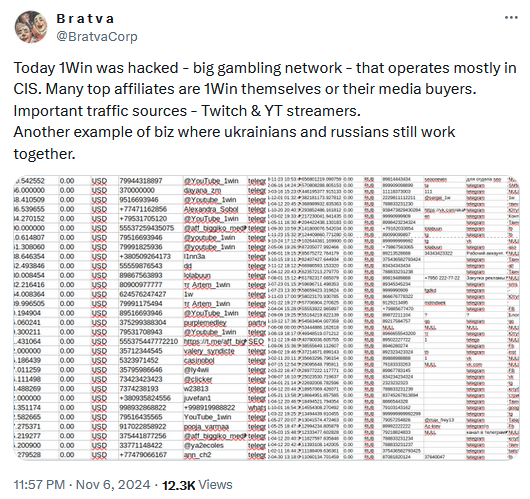
1win data leaks: A huge data trove of 96 million user records from Russian sports betting and gambling company 1win has been leaked online. The data was stolen in a hack in November of last year. The hacker allegedly used a wave of DDoS attacks to distract the company's security team and dump its user database. According to 1win's CEO, the hacker initially demanded a ransom of $1 million but increased the sum to $15 million after several failed negotiations. The 1win data is now available in HIBP.
General tech and privacy
Firefox 135: Mozilla has released Firefox 135. New features and security fixes are included. The biggest feature in this release is the addition of Simplified Chinese, Japanese, and Korean to Firefox's built-in translator. In addition, the credit card autofill feature and the AI chatbot feature are now being gradually rolled out to users.
Government, politics, and policy
Texas bans Chinese apps on government devices: Texas officials banned the use of six Chinese mobile apps on government devices. The ban covers social media networks Lemon8 and Rednote, AI app DeepSeek, and online trading apps Moomoo, Tiger Brokers, and Webull. Texas previously banned TikTok on government devices in 2022.
Thailand to cut power to scam center regions: The Thai government will cut power to some areas near the Myanmar border as part of a crackdown against online scam compounds. Officials didn't say when they would start cutting power but said they have the ability to do it starting today if they had to. The Thai government has been under international pressure over the last year to crack down on cyber scam centers. Thai police launched an international coordination center last week to fight online cyber scam operations operating across Southeast Asia. [Additional coverage in Reuters]
India expands Aadhaar usage: The Indian government will allow private companies to use its Aadhaar database to authenticate and confirm the identity of Indian nationals on their services. The Aadhaar database was introduced in 2020 and stores the personal information of all Indian citizens, including biometrics data. Until this year, the database was used exclusively to authenticate citizens when accessing government services.
Russia hacked Starmer's email: Russian state hackers breached Sir Keir Starmer's personal email account at the start of 2022. The hack took place shortly after Russia's invasion of Ukraine and when Starmer was the leader of the UK opposition. Starmer abandoned the account at the advice of British intelligence. [Additional coverage in The Telegraph]
Kazakhstan to investigate Russian hack: Kazakh officials will investigate a suspected hack of its Ministry of Foreign Affairs by Russian hackers following a Sekoia report from earlier this month. [Additional coverage in Orda]
Australia sanctions Terrorgram: The Australian government sanctioned white supremacist online network Terrorgram. The group operated via a Telegram channel that encouraged members to carry out murders, physical attacks, and hate crimes. Terrorgram has been linked to a shooting at an LGBTQ bar in Slovakia and the stabbing of five people near a mosque in Turkey. The US arrested two Terrorgram admins last September and sanctioned the group in January. It was also added to the UK's list of terrorist organizations last year.
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Thinkst CTO Marco Slaviero about a concept called Defending off the Land, a way to detect attacks and even deceive and frustrate attackers.
Arrests, cybercrime, and threat intel
Canadian crypto hacker charged: US authorities have charged a 22-year-old Canadian man with hacking two cryptocurrency platforms. Andean Medjedovic allegedly stole $16.5 million from Indexed Finance in October 2021 and another $48.4 million from KyberSwap in November 2023. Medjedovic allegedly exploited vulnerabilities in the smart contracts to modify key parameters and withdraw funds at inflated prices. US officials say the suspect also tried to blackmail the KyberSwap team into getting full control over their platform in return for half of the stolen funds.
Police raid Manila online scam compound: Authorities in the Philippines have arrested 100 Filipinos and a Chinese national following a raid at an online scam compound operating in the country's capital, Manila. The compound occupied two floors in a condominium, and the Chinese national acted as the supervisor. Officials say the suspects used AI-generated conversations and fake profile pictures of attractive women to lure victims into fraudulent cryptocurrency schemes. [Additional coverage in PhilStar and the Rappler]
Card skimmer charged: US authorities have indicted two Romanian men for installing ATM skimmers across Louisiana.
XE Group: The XE Group cybercrime operation has moved from web store e-skimming operations to breaching networks using zero-day vulnerabilities. The group has been around since 2013 and is believed to operate out of Vietnam. According to a joint Intezer and Solis report, the group has used at least two zero-days in supply chain management software VeraCore.
Malicious DeepSeek PyPI packages: Positive Technologies has discovered two malicious Python libraries on the PyPI portal that mimic DeepSeek AI tools and deploy an infostealer to steal data from infected PCs.
Malicious Go module: Security researchers have discovered a malicious Go module for the BoltDB database that contains a hidden backdoor. According to Socket Security, the module is cached in the Go Module Mirror. The mirror is from where Go command-line installers download needed packages. Socket says this attack is among the first documented instances of a malicious package making it on the Go Module Mirror despite manual code reviews.
Malicious Chrome extensions: Security researcher Wladimir Palant has discovered another set of 10 malicious Chrome extensions after finding a first set of 35 last month.
Guide for securing edge devices: Cyber agencies from the Five Eyes, Australia, Canada, New Zealand, the UK, and the US, released guidance on securing network edge devices.
Malware technical reports
SmokeLoader abuses 7-Zip zero-day: Trend Micro says Russian hackers have abused a zero-day in the 7-Zip file archiving utility as part of cyber-espionage and cybercrime operations. The zero-day (CVE-2025-0411) leveraged the double-archiving trick to decompress malicious files without the Mark-of-the-Web security protection. Trend Micro linked the attacks to the SmokeLoader cybercrime group and espionage operations targeting the Ukrainian government. The earliest malicious samples date back to September of last year. The 7-Zip patched the bug at the end of November.
ValleyRAT: Morphisec researchers look at ValleyRAT, a remote access trojan developed and used by China-based threat group SilverFox.
FleshStealer: CyFirma has published a report on FleshStealer, a new .NET infostealer that was put up for sale in underground cybercrime circles earlier this year.
macOS infostealers: Palo Alto Networks has published an overview of the macOS infostealer scene.

Sponsor section
In this Soap Box edition of the podcast, Patrick Gray chats with Thinkst Canary founder Haroon Meer about his "decade of deception."
APTs, cyber-espionage, and info-ops
GRU Unit 54777: Lab52 looks at GRU Unit 54777, responsible for some of the GRU's social media influence operations.
FlexibleFerret: SentinelOne researchers have published a technical deep-dive into FlexibleFerret, a macOS backdoor used by North Korean state-sponsored hackers.
DaggerFly's ELF/Sshdinjector: Fortinet published an analysis of ELF/Sshdinjector, a Linux malware strain that injects into the SSH daemon that has been used in previous DaggerFly APT campaigns.
GreenSpot: A Hunt.io report looks at a phishing campaign from the GreenSpot APT targeting 163.com email inboxes.
Vulnerabilities, security research, and bug bounty
OPA Gatekeeper bypass: Aqua security researchers have found multiple policy bypasses in OPA Gatekeeper, a utility for managing Kubernetes clusters.
AMD Zen vulnerability: The Google security team has found a security flaw in some of AMD's Zen CPUs. The vulnerability (CVE-2024-56161) allows threat actors with admin rights on a system to load malicious CPU firmware patches. The attack can bypass AMD Secure Encrypted Virtualization protections and allow malicious customers to compromise cloud infrastructure. Vulnerable AMD processors include Zen 1 through Zen 4. AMD released security updates on Monday.
Netgear security updates: Netgear has released security updates for an authentication bypass and unauth RCE in its WiFi routers.
Android Security Bulletin: Google has released the Android security updates for February 2025. This month, the company has patched a zero-day exploited in attacks in the wild. Tracked as CVE-2024-53104, the vulnerability is an elevation of privilege attack in Android's UVC kernel component, typically used for connecting external USB devices. GrapheneOS developers believe the zero-day is "likely one of the USB bugs exploited by forensic data extraction tools."
KEV update: CISA has updated its KEV database with two vulnerabilities that are currently exploited in the wild. This includes two 2018 bugs in Paessler PRTG network monitors, a 2024 bug in Apache OFBiz, and another 2024 bug in the Microsoft .NET Framework.
Sysinternals vulnerabilities: Software engineer Raik Schneider has discovered DLL hijacking bugs in several of Microsoft's Sysinternal tools. The issues remain unpatched, even after a 90-day disclosure window.
Supply chain attack via S3 buckets: watchTowr Labs researchers have discovered and registered ~150 AWS S3 buckets that were previously owned by now-abandoned commercial and open-source projects. Researchers say the buckets still received traffic, including from government and military domains and Fortune 500 companies. The traffic suggests the buckets stored software updates, server configuration, and various files that could be replaced and abused to hijack remote networks.
Infosec industry
Threat/trend reports: Contrast Security, KRCERT, PAN, Picus Security, Qrator, and VulnCheck have published reports and summaries covering various infosec trends and industry threats.
New tool—uscope: Security researcher Jim Calabro has released uscope, a native code graphical debugger and introspection toolchain for Linux.
BSides Belfast videos: Talks from the BSides Belfast 2024 security conference, which took place in September, are available on YouTube.
BSides London videos: Talks from the BSides London 2024 security conference, which took place in December, are available on YouTube.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about the evolution of Russian cyber operations during its invasion of Ukraine.
In this podcast, Tom Uren and Adam Boileau talk about the continued importance of hack and leak operations. They didn't really affect the recent US presidential election, but they are still a powerful tool for vested interests to influence public policy.
