Risky Bulletin Newsletter
December 18, 2024
Risky Bulletin: CISA sent 2,100+ pre-ransomware alerts this year
Written by

News Editor
You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
The US Cybersecurity and Infrastructure Security Agency has sent out 2,131 pre-ransomware activity notifications to US organizations throughout the year.
The notifications were sent via a program named the Pre-Ransomware Notification Initiative (PRNI), which CISA launched in March of 2023.
The program uses tips received from the private sector to detect early ransomware activity and notify potential targets before their data is stolen or encrypted.
In its 2024 Year In Review report, CISA says the PRNI has sent out 3,368 notifications since its inception. Almost two-thirds of these were sent in 2024, as the program appears to have matured and gained the industry's trust.
"These notifications include those sent to hundreds of K-12 school districts; state, local, tribal and territorial government entities; healthcare organizations and hospitals; and other critical infrastructure."
CISA's PRNI program is unique among the world's cybersecurity agencies.
As part of a separate initiative, the agency says it also sent 1,200 notifications to organizations that had systems vulnerable to common ransomware entry vectors. This was down from the 1,700+ notifications sent last year.
But, according to the 2024 report, CISA spent most of its time this year dealing with election-related threats and Secure by Design, a program designed to promote safe programming practices. The program is the agency's way of dealing with an ever-increasing number of software vulnerabilities and the havoc they're creating in US critical sectors when they get exploited.
Risky Business Podcasts
Risky Business is now on YouTube with video versions of our main podcasts. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
Telecom Namibia ransomware attack: A ransomware gang has breached the network of Telecom Namibia, the country's largest telecommunications provider. The incident took place last week, and officials have confirmed the breach. A group named Hunters International took credit for the attack and is now threatening the publish almost half a million of the telco's files. [Additional coverage in The Namibian]
Firm goes into insolvency after ransomware attack: French company Octave filed for insolvency administration following an August ransomware attack. [Additional coverage in Ouest France] [h/t SwitHak]
ConnectOnCall breach: Phreesia says that almost one million users had their data stolen after hackers gained access to ConnectOnCall, a service used by doctors to take after-hour calls.
Texas Tech breach: Texas Tech University has disclosed a data breach that impacted some of its health departments.
Nebraska sues Change Healthcare: Nebraska Attorney General Mike Hilgers has filed a lawsuit against Change Healthcare over the company's February ransomware attack. Officials claim the company failed to protect consumer data prior to the attack. Attorney General Hilgers says the company ran outdated and poorly segmented IT systems, had an inadequate response to the breach, and failed to notify consumers in due time. Hilgers says the incident exposed the personal information of hundreds of thousands of Nebraskans and also caused disruptions to the state's healthcare facilities. Nebraska is the first state to sue Change Healthcare, although the company is dealing with a class-action lawsuit already.
Apple refuses Harris campaign investigation request: Apple has allegedly refused to help the Harris campaign investigate the hack of two staffers' iPhones. According to a Forbes report, the company declined to help obtain a raw image of the phones' operating system to help the campaign investigate the devices. Apple refused to help even if the phones' owners provided their consent. The devices are currently being investigated by security firm iVerify.
General tech and privacy
TikTok EU reports loss: TikTok's EU branch has reported $1 billion in losses as it set aside the exact same sum to deal with potential fines from regulatory investigations. [Additional coverage in RTE]
Meta gets fined twice: US social media company Meta was fined twice this week for two security breaches. The company was fined €251 million in Ireland and AUS$50 million in Australia. The Ireland fine is for a 2018 security breach when a bug in the Facebook "View as" feature exposed the data of over 29 million Facebook users. The fine in Australia is related to the company's failure to detect the Cambridge Analytica scandal.
Government, politics, and policy
Serbia deploys spyware against dissidents and journalists: The Serbian security service has allegedly deployed a novel piece of Android spyware on the phones of anti-government dissidents and local journalists. According to Amnesty International, the spyware was deployed after police gained physical access to the device while the victims were being interrogated. Cops allegedly used Cellebrite hacking tools to unlock the phones and manually install the new NoviSpy spyware. Amnesty and Google believe the Cellebrite tools might have used a zero-day in Qualcomm chips to deploy the spyware. Serbia's BIA security service called the Amnesty report "meaningless allegations" and claimed it operates within the boundaries of Serbian law.
US moves to ban China Telecom: The US Commerce Department has issued a preliminary ruling that China Telecom's American division is a threat to national security. The preliminary ruling is one of the steps before banning the company from operating in the US. China Telecom was given 30 days to respond. The move for a ban comes as the US government is dealing with a widespread hack of its telco networks by Chinese hackers. [Additional coverage in Reuters]
EU starts formal TikTok investigation: The European Commission has opened an investigation against TikTok on election-related risks under the EU's new Digital Services Act. EU officials say the Chinese company failed to detect a foreign interference campaign that targeted Romania's presidential election last month. Romania's Supreme Court ruled the campaign tainted and tilted public opinion for one candidate and annulled the election—the first time this has happened in the EU block's history. The investigation will focus on TikTok's recommendation algorithm and its handling of political ads. As the EU was announcing its investigation, TikTok was rife with another anti-EU disinformation campaign claiming that EU chief Ursula von der Leyen was the one who ordered Romania to cancel its election.
TikTok asks USC to stop US ban: In its last and desperate move, TikTok has now asked the US Supreme Court to stop an impending law next year that would force the company to divest from its Chinese investors or face a national ban. [Additional coverage in CBS]
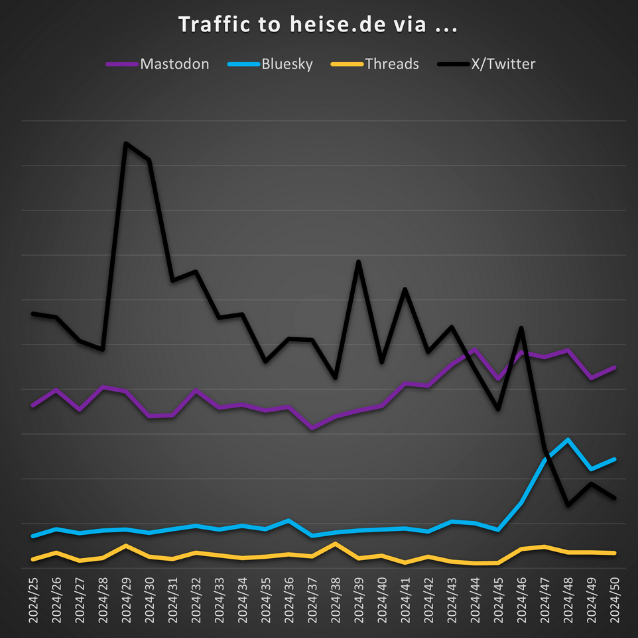
Twitter's failing traffic: More and more online news outlets are reporting that both BlueSky and Mastodon are now a primary source of web traffic to their articles, compared to Twitter or Threads, both of which punish users who post links—which, honestly, is plainly a ridiculous foot-gun practice.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about the evolution of Russian cyber operations during its invasion of Ukraine.
Arrests, cybercrime, and threat intel
Crypto scammers arrested in Nigeria: Nigerian authorities arrested a whopping 792 suspects last week following a raid on a seven-story building housing a cyber scam compound in Lagos. 148 Chinese and 40 Filipinos were also among the detained suspects. Officials say the suspects were low-level pawns in a larger online scam ring. They initiated romantic chats with victims and then handed off the conversation to someone overseas to execute the actual scam.
Everest negotiator sentence: A French court has sentenced cybersecurity professional Florent Curtet to a two-year suspended prison sentence for acting as a negotiator for the Everest ransomware gang in a 2021 attack against a French company. Curtet was also fined €13,000 and banned from working in cybersecurity roles for five years. The court's decision is well below the five-year prison sentence prosecutors had asked for earlier this year.
Hive member OSINT mistake: According to ZDNet France, the Hive ransomware gang member detained last year in Paris was betrayed by his passion for running. He allegedly pre-announced he was coming to Paris for a marathon and French police had time to prepare.
Carder sentenced: A US judge has sentenced a hacker named Vitalii Antonenko, who used SQL injection attacks to steal and sell credit card data from online sites to 69 months in prison.
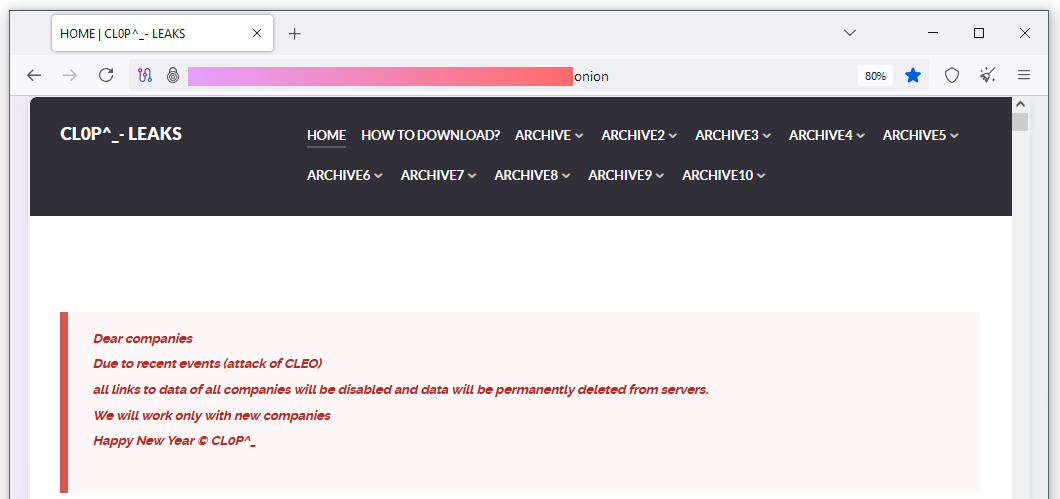
Clop takes credit over Cleo attacks: The Clop ransomware gang has taken credit for the attacks against Cleo file-transfer servers. Initial reports claimed another ransomware operation named Termite was behind the attacks with a Cleo zero-day. Clop announced on its leak site on Monday it was deleting older victim data in order to make space to host the new stolen data, which it plans to use to extort hacked companies. [Additional coverage in BleepingComputer]
FLUX#CONSOLE: Securonix looks at the phishing campaigns of a group it tracks as FLUX#CONSOLE, which is currently targeting Pakistani businesses.
ClickFix campaign: Guardio Labs looks at a campaign that relies on malicious ads to bring users to malicious sites where they're asked to copy-paste malicious code on their PC that installs the Lumma Stealer.
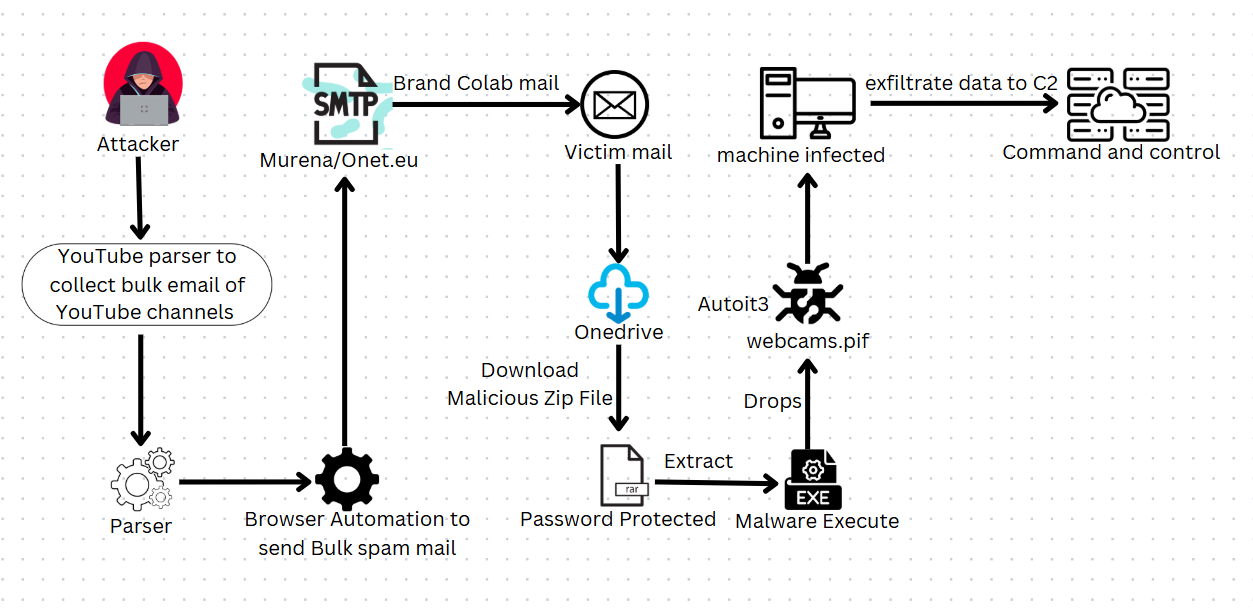
Phishers target YouTube content creators: A threat actor is targeting popular YouTube channel owners with fake brand collaborations and sponsorships to infect them with malware. The goal of the campaign is to hijack their YouTube channels and even steal personal profits. The campaign has been taking place since July and has targeted over 200,000 content creators so far.
Malware technical reports
HiatusRAT: The operators of the HiatusRAT botnet are targeting old vulnerabilities in security cameras and DVR systems. The new campaign started in March and specifically targeted networks in Five Eyes countries. The FBI says the campaign targeted D-Link, Dahua, Xiongmai, and Hikvision devices. The HiatusRAT botnet was discovered in July 2022 and is believed to be part of Chinese reconnaissance operations against Western networks. [More in the FBI advisory PDF]
I2PRAT: G DATA researchers have published a report on I2PRAT, a new remote access trojan that uses the I2P anonymization technology for C2 comms.
CoinLurker: Morphisec has found a new infostealer being distributed in the wild. Named CoinLurker, it is written in Go and distributed via fake update prompts and other web-based methods like ClickFix, ClearFake, FakeCAPTCHAs, or whatever you call those things.
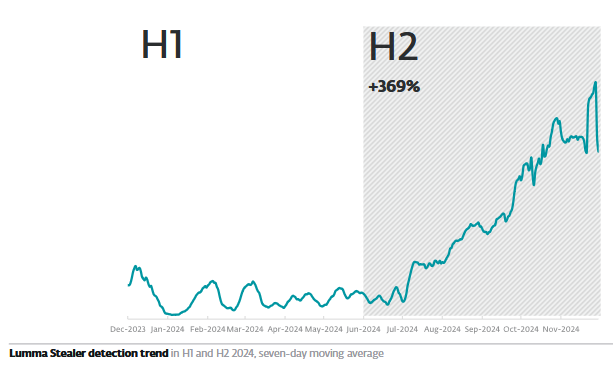
LummaStealer: Cybereason looks at LummaStealer, one of this year's most active infostealer operations.
Bizfum Stealer: CyFirma has released a report on Bizfum Stealer, a new infostealer available via GitHub for eDuCaTiOnAl purposes.
Xloader: Sublime Security has published an analysis of a recent Xloader distribution campaign that leverages SharePoint files as lures.
RiseLoader: Security firm Zscaler has spotted a new malware family named RiseLoader being distributed in the wild since October. Researchers believe the malware was developed by the same individual behind the RisePro infostealer. They base their attribution on the fact that RiseLoader uses the same C2 protocol as RisePro and that the RisePro author shut down the infostealer in June this year—most likely to focus on the newer project.
SocGholish: Malwarebytes looks at a malvertising campaign redirecting users to SocGholish pages.
Mamont banker: Kaspersky has discovered a new Android banking trojan named Mamont. It was first spotted in October and appears to have been used in campaigns targeting Russian-speaking users.
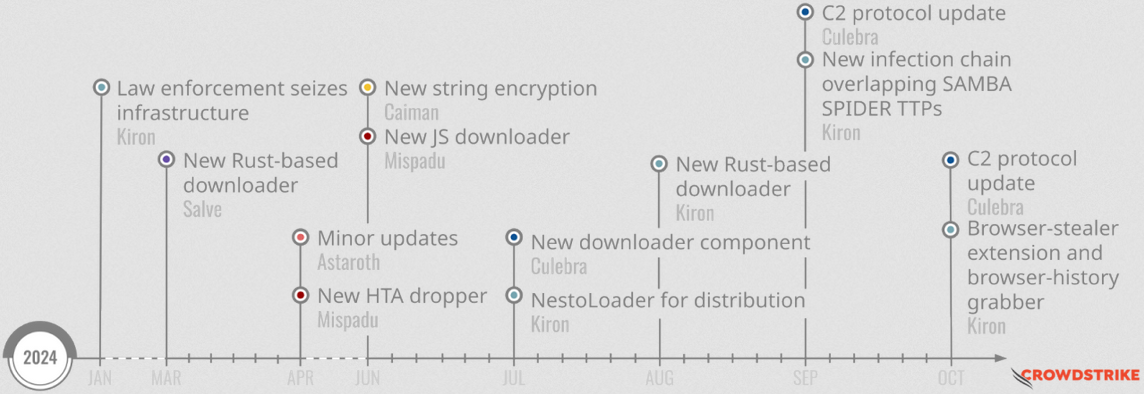
LATAM malware: CrowdStrike has published a look back at how LATAM-specific malware evolved throughout the past year.
Risky Business Podcasts
In this podcast, Tom Uren and Adam Boileau talk about the continued importance of hack and leak operations. They didn't really affect the recent US presidential election, but they are still a powerful tool for vested interests to influence public policy.
APTs, cyber-espionage, and info-ops
UAC-0099: The UAC-0099 cyber-espionage group is back with new attacks on Ukrainian government orgs, this time dropping the LONEPAGE backdoor.
Earth Koshchei (APT29): Trend Micro has published a report on a recent Earth Koshchei (APT29) campaign that abused RDP config files to trick victims into connecting to rogue RDP servers.
TA397 (Bitter): Proofpoint has published a report on recent TA397 (Bitter) APT campaigns targeting Turkey's defense sector. The final payloads were the WmRAT and MiyaRAT malware families.
"The usage of RAR archives is a staple tactic of TA397 payload delivery. Throughout the first half of 2024, Proofpoint has observed TA397 utilizing Microsoft Compiled Help Files (CHM) files within RAR archives as a means of creating scheduled tasks on target machines."
Vulnerabilities, security research, and bug bounty
KEV update: CISA has updated its KEV database (twice) with two vulnerabilities that are currently exploited in the wild. This includes a ColdFusion bug from March and a Windows one from June.
Unsafe Unpacking Research: Doyensec has published research on the various attacks that are exploiting unsafe ways of unpacking data across six different programming languages.
DirtyDAG vulnerabilities: PAN Unit42 researchers have found vulnerabilities in the Azure Data Factory Apache Airflow integration that can allow threat actors to create shadow admin accounts. The vulnerabilities are exploited via directed acyclic graph (DAG) files or using compromised service principals.
"Exploiting these flaws could allow attackers to gain persistent access as shadow administrators over the entire Airflow Azure Kubernetes Service (AKS) cluster. This could enable malicious activities like data exfiltration, malware deployment or covert operations within the cluster. Once inside, attackers can also manipulate Azure's internal Geneva service, which is responsible for managing critical logs and metrics. This could allow attackers to potentially tamper with log data or access other sensitive Azure resources."
Azure Key Vault EoP: DataDog researchers have discovered a vulnerability in the Azure Key Vault service that allows any user to elevate privileges and access everyone's secure material. This includes API keys, passwords, Azure Storage shared access signatures (SAS), and authentication certificates. Microsoft did not patch the issue but has updated documentation to add a new warning about access policy risks.
GStreamer vulnerabilities: GitHub security researcher Antonio Morales has found 29 vulnerabilities in GStreamer, the GNOME media framework, with most of them affecting the libraries handling MKV and MP4 media formats.
BeyondTrust vuln: Identity and PAM provider BeyondTrust has patched a command injection vulnerability in its Privileged Remote Access (PRA) and Remote Support (RS) products. The bug has a severity rating of 9.8 out of 10, so expect to be easy to exploit. [h/t @cR0w]
Link Trap attack: Trend Micro looks at a new type of prompt injection attack against GenAI systems named the Link Trap.
New Struts exploitation: SANS ISC has detected the first exploitation attempts against a recently disclosed Apache Struts file upload vulnerability tracked as CVE-2024-53677.
Infosec industry
US company buys Israeli spyware vendor: US private investment company AE Industrial Partners has agreed to acquire Israeli spyware company Paragon Solutions. AE will pay $900 million, with half paid in cash this year and the other half paid in the future based on profitability milestones. The company is known for developing a mobile spyware tool named Graphite. [Additional coverage in Globes]
BlackBerry sells off Cylance: BlackBerry has sold off its Cylance security division to fellow cybersecurity firm Arctic Wolf for $160 million in cash. BlackBerry will receive half the sum at closing and the other a year after. The company acquired Cylance in 2018 for a whopping $1.4 billion at a time when it was trying to pivot from smartphones to cybersecurity.
Interpol pig butchering request: Interpol has called on the general public to stop using the term "pig butchering" to refer to online scams and their victims. The agency says the term is stigmatizing, dehumanizes, and shames victims. The term comes from scammers who refer to victims as "pigs" who need to be 'fattened up' through fake romance or friendships before 'butchering' them by convincing them to invest in fake cryptocurrency or other investment schemes. Interpol has suggested the public use "romance baiting" as an alternative.
New tool—Sickle: Security researcher Milton Valencia has released Sickle, a payload development framework.
New tool—MarkItDown: Microsoft has open-sourced MarkItDown, a tool for converting various files to Markdown format.
Tool update—RansomLordNG: RansomLord, the tool that intercepts and stops ransomware execution, has received a major update called RansomLordNG, which can now intercept 54 ransomware strains/groups.
OBTS 2024: Talks from the Objective by the Sea 2024 security conference, which took place last October, are available on YouTube.
Threat/trend reports: Au10tix, Cloudflare, ESET, the Geneva Association, OpenSSF, and Rapid7 have recently published reports and summaries covering various infosec trends and industry threats.