Risky Bulletin Newsletter
March 19, 2025
Risky Bulletin: China says Taiwan's military is behind PoisonIvy APT
Written by

News Editor
This newsletter is brought to you by /no-code automation platform Tines. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
China's main intelligence agency said on Monday that a branch of the Taiwanese military is behind an APT group known as PoisonIvy and GreenSpot.
China's Ministry of State Security (MSS) says a cyber warfare center (Network Environment Research and Analysis Center) inside the Taiwan Information, Communications, and Electronic Force Command (ICEFCOM) is behind the APT group's operations.
The MSS accused ICEFCOM of hacking Chinese government agencies, military targets, organizations in China's critical sectors, and private sector companies.
The agency named four individuals linked to PoisonIvy operations, such as the center's head, team leader, and two of its personnel.

This is the second time that the MSS has revealed the names of ICEFCOM operatives and linked them to a public hacking group.
The MSS linked three different ICEFCOM members in September of last year to a hacktivist group named Anonymous64.
This newsletter has ridiculed China's public attribution efforts in the past, and this one also doesn't disappoint.
After the US government called out China for using a sprawling network of private companies to conduct its cyber operations, the MSS decided to do the same—but to Taiwan.
In a propaganda-ladden press release, the MSS claims ICEFCOM also "hired hackers and cybersecurity companies as external support to execute the cyber warfare directives issued by the Democratic Progressive Party (DPP) authorities."
But unlike the US, which provided the exact names of those companies and their employees, the MSS did not do anything of that. Instead, Chinese authorities were more focused on repeatedly denying that Taiwan is an independent state and that Taiwan should submit to China's rule. Expressions like cannon fodder, resistance is futile, and abandon the fantasy of Taiwan independence because it's a dead-end road are included in an official government communique; I kid you not!
The entire press release also has a smell of counter-intel and sabotage. It accuses ICEFCOM leaders of stealing credit from their subordinates, infighting, fabricating results to claim performance rewards, handing "meritorious individuals" for legal action, and wasting government funds on fruitless cyber operations—a claim China has also made about the NSA's operations.
As expected, Taiwanese officials denied the accusations.
Another interesting tidbit about the Monday press release was that the official statement was also accompanied by the release of two reports from Chinese security firms Antiy and QiAnXin. The two reports also formally attributed PoisonIvy/GreenSpot to the Taiwanese government. The two companies previously linked the APT to Taiwan, but this marked the first time they linked it to government operations.
This coordination between the Chinese government and its cybersecurity private sector is slowly becoming a norm after having happened three times already.
All the previous instances took place when China replied to new US indictments of Chinese cyber operators, with the MSS, China's CERT, and several companies publishing coordinated reports on US operations.
Risky Business Podcasts
Risky Business is now on YouTube with video versions of our main podcasts. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
Infosys settles 2023 class-actions: Indian IT services provider Infosys has settled multiple class-action lawsuits related to a 2023 security breach. The company has agreed to pay $17.5 million into a shared fund that will distribute the funds to all affected plaintiffs. The Infosys hack took place in November 2023 and exposed the personal data of over 6.5 million individuals. [Additional coverage in The Times of India]
Cryobank hack: Sperm bank California Cryobank has disclosed a data breach that took place last April.
Wemix crypto-heist: Hackers have stolen $6.2 million worth of crypto-assets from the Wemix blockchain gaming platform at the end of February. Wemix CEO Kim Seok-hwan confirmed the attack weeks after it happened. Kim said in a press conference that he tried to avoid a market panic and crashing the token's value and was not trying to conceal the breach. [Additional coverage in Binance News]
Car dealership supply chain attack: An attacker compromised the websites of over 100 car dealerships to target users with malware. Site visitors were greeted by a ClickFix popup that instructed users to copy-paste and run malicious commands on their computers. According to security researcher Randy McEoin, the malicious code was delivered via a shared video player platform.
General tech and privacy
EU tech companies call for a "Euro stack": A coalition of over 100 European tech companies have asked the EU's top brass to shrink reliance on foreign software and server infrastructure and invest in a "Euro stack." Signatories include the likes of Airbus, OVHCloud, Nextcloud, and Proton. The letter asks EU lawmakers to encourage the investment in and acquisition of European tech through public procurement requirements. [Additional coverage in TechCrunch]
Facebook community notes roll out: Meta rolled out Community Notes for testing on Facebook and Instagram in the US.
Firefox PWA support coming: Mozilla is working on adding support for progressive web apps in Firefox. That's over a decade after Chromium introduced them. [Additional coverage in Windows Report]
Vivaldi 7.2: The Vivaldi browser has released a major update this week that managed to cut its page loading times in half.
AI project failures are increasing: The number of companies that reported the failure of their AI projects increased from 17% to 42% during the past year, according to a new S&P study. [Additional coverage in CybersecurityDive]
Government, politics, and policy
South Korea urges for more cybersecurity from drone makers: South Korea's intelligence agency urged local drone makers to invest in more cybersecurity and secure systems in the face of rising espionage and IP theft attacks on the sector. [Additional coverage in The Korea Post]
French-Canadian threat-sharing agreement: The Canadian and French governments announced a new intelligence and threat-sharing agreement that will also cover cybersecurity.
US House to investigate Chinese hack response: The US House Homeland Security Committee has asked the DHS to provide all documents related to the agency's response to the Volt and Salt Typhoon intrusions. The request seems to be a political stunt focused on investigating "the previous administration."
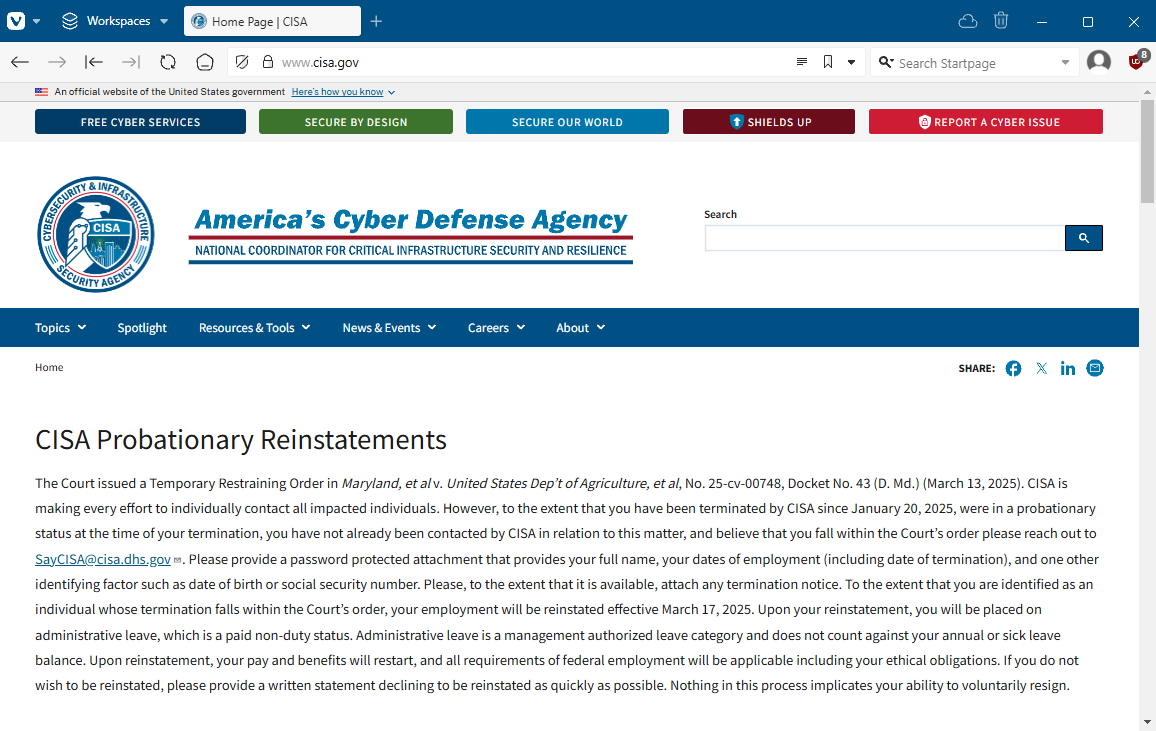
CISA told to reinstate fired workers: A US court has ordered CISA to reinstate fired probationary workers the agency fired since January 20. CISA has emailed workers and is placing them on administrative leave while the case is being heard. Firings have impacted CISA's election security, anti-disinformation, and penetration testing teams. It's still likely that employees will still get fired since they worked in areas the DHS has deprioritized. [Additional coverage in NextGov]
Sponsor section
In this Risky Business News sponsor interview, Tom Uren talks to Matt Muller, field CISO of Tines. He explains how governments are using carrots and sticks to improve the security of enterprise software. Matt discusses CISA's "Secure by Design" pledge and the UK NCSC's effort to quantify "unforgivable bugs."
Arrests, cybercrime, and threat intel
OKX suspends service abused for money laundering: Cryptocurrency exchange OKX suspended its DEX aggregator after North Korean hackers abused it to launder proceeds from the Bybit $1.5 billion hack. OKX took the step after it was approached by European financial regulators. The company also launched a system to track the Bybit hackers' latest addresses and block them in real-time.
Compromised logins rampant on Cloudflare: Internet infrastructure company Cloudflare says that 41% of successful logins across websites protected by Cloudflare for a period of three months last year involved the use of compromised passwords.
Cobalt Strike gets a sleep mode: Fortra has released a new version of Cobalt Strike with support for putting its Beacon implant in sleep mode to avoid detection.
New ClearFake variant: Sekoia has discovered a new variant of the ClearFake (ClearFix) attack that leverages blockchains to store some of its payloads.
VHD abuse: Forcepoint looks at how VenomRAT and other malware strains are abusing virtual hard disks (VHDs) to host and distribute payloads.
Italy DDoS attacks: Netscout says Italy has seen an increase in DDoS attacks recently, with many of them coming from pro-Kremlin "hacktivist" groups.
Malware technical reports
StilachiRAT: Microsoft has discovered a new malware strain named StilachiRAT that was used in attacks targeting cryptocurrency users.
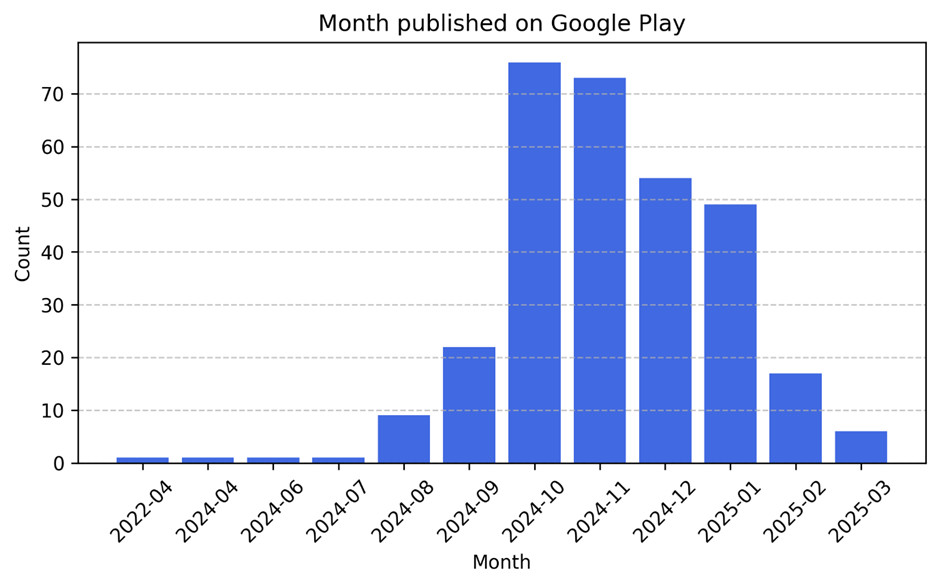
Google Play ad campaign: Bitdefender researchers have uncovered a cluster of over 330 malicious apps on the official Google Play Store. The apps abused a novel technique to hide their icons even on recent versions of Android, start without interaction, and show unwanted ads. Some of the apps also launched phishing attacks that collect credentials and banking details via a popup. The apps have been downloaded by over 60 million users since April 2022, when the oldest was uploaded to the store.
Sponsor section
In this product demo, CEO Eoin Hinchy shows how Tines' Workbench can integrate an LLM into security workflows to gather, analyze, and act on data from both inside and outside your company. This demo includes grabbing IOCs from an external webpage, comparing them to your companies' own incidents, and taking actions like resetting passwords.
APTs, cyber-espionage, and info-ops
UAC-0200: Suspected Russian threat actor UAC-0200 is targeting Ukraine's military-industrial complex with phishing lures related to UAVs and electronic warfare.
MirrorFace: ESET says Chinese APT group MirrorFace hacked "a Central European diplomatic institute in relation to Expo 2025, which will be held in Osaka, Japan."
11 APTs abuse Windows zero-day: Multiple cyber-espionage groups have abused a Windows zero-day vulnerability for the past eight years. The zero-day is a bug that allows attackers to add command-line arguments inside LNK shortcut files that are invisible to a user. At least 11 APT groups from North Korea, Iran, Russia, and China have used the zero-day to hide malicious instructions in LNK files sent to targets. Trend Micro says it discovered almost 1,000 malicious LNK files abusing the technique. Microsoft has declined to patch the issue following a Trend Micro report last September.
Disinformation domains: DomainTools' security team has published an overview of the domain registrars used by Russian disinformation actors.

Vulnerabilities, security research, and bug bounty
Tomcat bug exploited in the wild: Attackers are exploiting a recently patched remote code execution bug (CVE-2025-24813) in Apache Tomcat servers. The attacks are abusing a public proof-of-concept published on a Chinese forum last week. The Apache project released patches at the start of the month.
DRAY:BREAK bugs exploited: A Mirai botnet is now exploiting a set of security flaws known as DRAY:BREAK that impact DrayTek Vigor routers.
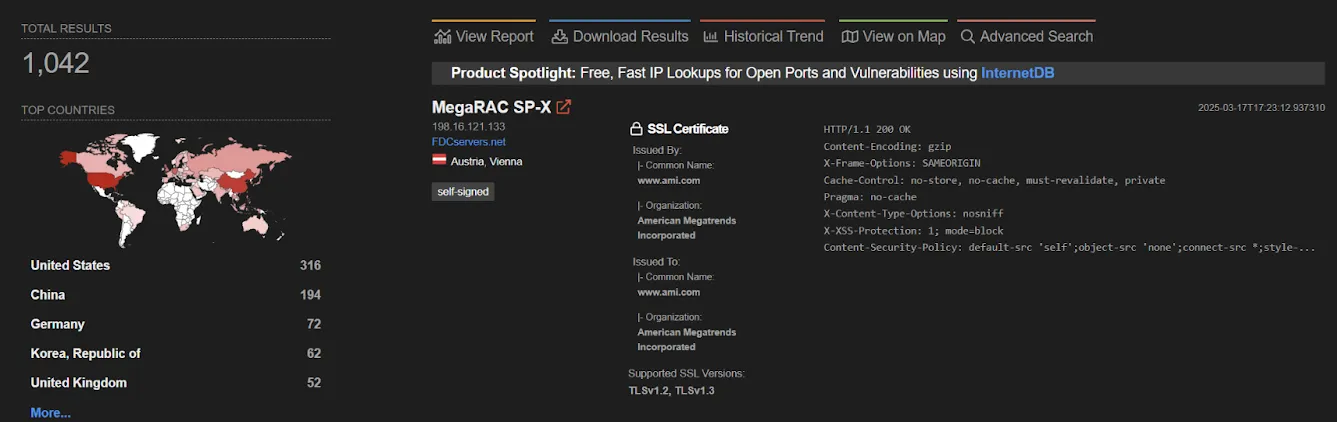
MegaRAC vulnerabilities: Firmware security company Eclypsium has discovered a remotely exploitable vulnerability in AMI MegaRAC baseboard management controllers (BMCs). The vulnerability allows attackers to bypass authentication through the Redfish Host Interface and access the BMC's remote management capabilities. Eclypsium says attackers could abuse this flaw to tamper with firmware, disable security protections, and even brick devices. The vulnerability (CVE-2024-54085) received a 10/10 severity score. Over 1,000 devices with MegaRAC interfaces are currently exposed on the internet. Affected vendors include ASUS, ASRockRack, and HPE.
Kentico vulns: watchTowr researchers have identified three vulnerabilities in the Kentico Xperience CMS that can be used to hijack vulnerable sites. They include two auth bypasses and a post-auth RCE. Patches are out, but no CVEs.
XML-crypto signature bypasses: Security researcher Alexander Tan has discovered two vulnerabilities in the XML-crypto JavaScript library. The vulnerabilities can be used to bypass authentication systems where the library is used to verify signed XML documents. The WorkOS project has confirmed the bugs can be used to bypass its SAML authentication and impersonate any account. Other SAML implementations that use the library may also be impacted.
Wazuh RCE: A remote code execution bug (CVE-2025-24016) has been found in the Wazuh open-source SIEM.
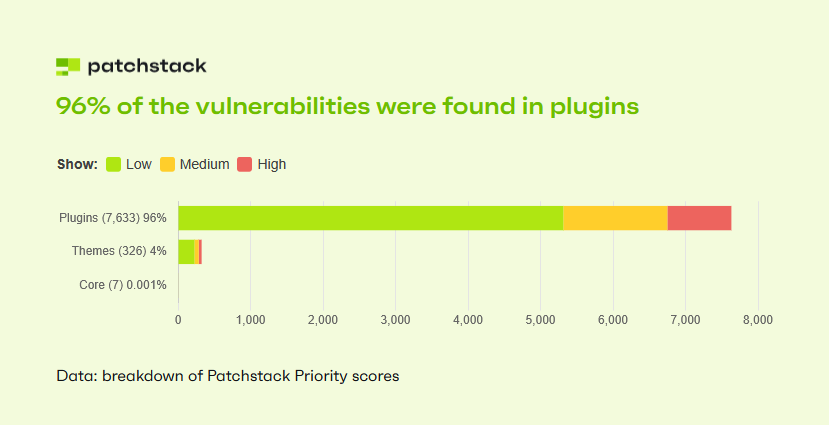
WordPress vulnerabilities are getting easier to exploit: Forty-three percent of all WordPress vulnerabilities discovered last year required no authentication to exploit, according to Patchstack's year-in-review report. The vast majority of WordPress vulnerabilities impacted plugins, continuing a trend seen in previous years. Only a handful of vulnerabilities were exploited, but the time-to-exploit was shorter than in previous years. Over half a million WordPress sites were hacked, with the vast majority hosting SEO spam.
Infosec industry
Threat/trend reports: Bedrock Security, BSI, Cato Networks, Flashpoint, Gartner, Patchstack, and Red Canary have recently published reports and summaries covering various infosec trends and industry threats.
Google buys Wiz: Google has acquired cloud security startup Wiz for $32 billion in cash, pending regulatory review. The company will join Google's Cloud division but will continue to support its current services for all major cloud platforms. Google also tried to buy Wiz last year for $23 billion before the deal collapsed. This is the largest cybersecurity-related acquisition to date.
AWS: “Here are eleven overlapping security services you have to configure juuuuust right.” Google Cloud: “Yeah, we just went ahead and bought Wiz.” GCP continues to crush the user security experience.
— Corey Quinn (@quinnypig.com) 2025-03-18T17:13:58.295Z
New tool—TruffleShow: Security researcher Ali Oguzhan Yildiz has released TruffleShow, a web viewer for TruffleHog JSON output. The code is also available on GitHub.
New tool—CHECKM8: A security researcher named 3itch has released CHECKM8, an exploit to bypass Intel TXT hash integrity checks.
New tool—Evilginx Pro: There's now a commercial version of the Evilginx phishing toolkit.
New tool—Xenon: The Mythic red team framework now has a Windows implant/agent named Xenon.
Tool update—OSV-Scanner: Google has released v2 of its OSV-Scanner. The original was released in late 2022 and used the OSV database to find known vulnerabilities affecting a project's dependencies.
Tool update—ANY.RUN: The ANY.RUN interactive sandbox now supports Android apps.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about how offensive cyber operations could do so much more than just "deny, disrupt, degrade, and destroy." Grugq thinks this thinking is rooted in US military culture, and he wonders why cyber operations are always so mean.
Tom Uren and Patrick Gray discuss how X is actively engaging in political interference outside the US. The risks mirror those of TikTok. American legislators moved against TikTok because it could potentially be a powerful tool for the Chinese government to interfere with American political discourse. X is a realized threat, not a potential one, so we expect that foreign governments will start to consider a ban.
