Risky Bulletin Newsletter
February 28, 2025
Risky Bulletin: Cellebrite bans bad boy Serbia
Written by

News Editor
This newsletter is brought to you by vulnerability management and analysis platform Nucleus Security. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
Israeli hacking tools maker Cellebrite has banned the Serbian government from using its products, citing misuse of its technology.
The company's decision comes after an Amnesty International report last December accused Serbian law enforcement of using Cellebrite tools to unlock phones and install spyware on the devices of anti-government dissidents and journalists.
Amnesty says this usually happened while victims were being interrogated by police. Their phones were taken away and then returned to them with spyware installed.
The Cellebrite tool allowed Serbian police to unlock devices without the victim's unlock code or password.
"We take seriously all allegations of a customer's potential misuse of our technology in ways that would run counter to both explicit and implied conditions outlined in our end-user agreement. After a review of the allegations brought forth by the December 2024 Amnesty International report, Cellebrite took precise steps to investigate each claim in accordance with our ethics and integrity policies. We found it appropriate to stop the use of our products by the relevant customers at this time."
Cellebrite investigates how all its customers use its tools on a yearly basis. The company says the reviews are to avoid changes in a country's "political structure and commitment to democracy, human rights and privacy."
Serbia has been rocked by massive public protests over the past three years—in 2023, following what observers have described as unfair parliamentary elections, and in 2024 and 2025, following the collapse of a railway station canopy and public shootings.
Many of the protests have demanded the resignation of the country's pro-Kremlin candidate. The government has responded with mass arrests, media censorship, and the surveillance of known dissidents and journalists.
Amnesty praised Cellebrite's response, calling the license withdrawal as a "critical first step."
The organization is also calling for a thorough and impartial investigation of the illicit spying. Knowing how the Serbian government operates—there's no way that will ever happen with the current regime in power.
Risky Business Podcasts
Risky Business is now on YouTube with video versions of our main podcasts. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
Philippine Army breach: A hacking group named the Philippine Exodus Security has leaked data from the country's armed forces on a cybercrime forum. The Philippine Army confirmed the breach. The leaked data allegedly includes highly sensitive details on military personnel who were active and discharged between 2018 and 2024.
Genea breach: The Termite ransomware gang has claimed the hack of Australian IVC clinic Genea.
Southern Water ransomware attack costs: United Kingdom water supplier Southern Water says that a ransomware attack it suffered in February 2024 cost the company £4.5 million. That appears to have also included a $750,000 payment. [Additional coverage in DataBreaches.net]
ALIEN TXTBASE: The Have I Been Pwned service has been "enriched" with ALIEN TXTBASE, a ginormous collection of infostealer logs found in a Telegram channel of the same name. The dump allegedly includes information on over 284 million user accounts.
Infini crypto-heist: A threat actor has drained $50 million worth of assets from DeFi protocol Infini. The attacker compromised private keys to gain admin access and slowly stole the funds on Monday. The sum represents almost all of the platform's funds. According to reports, the private keys appear to belong to a former developer who maintained admin access months after completing their work.
Bybit intrusion originated at Safe{Wallet}: New evidence reveals that North Korean hackers stole $1.5 billion from cryptocurrency exchange Bybit after initially hacking a developer at multisig wallet provider Safe{Wallet}. The hackers injected malicious code in the Safe{Wallet} domain that only targeted Bybit—its smart contracts and multi-sig process. Safe{Wallet} says it has now removed the code. Initial reports claimed that the intrusion point was on Bybit's network. In the meantime, the FBI has also confirmed North Korea's involvement in the hack and linked it to a group it tracks as TraderTraitor.
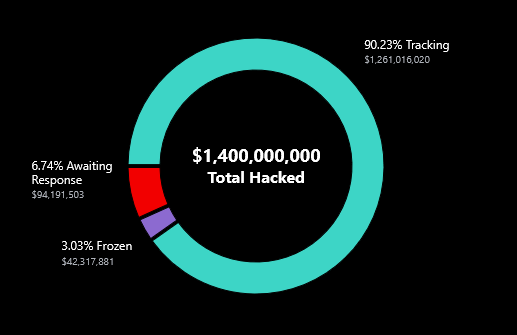
Bybit recovery starts: According to a special website it set up, cryptocurrency exchange Bybit says it has already frozen and is in the process of recovering $42 million worth of ETH from the $1.5 billion stolen by North Korean hackers last week. That's a long way to go!
General tech and privacy
Bing removes caching feature: Something that we missed from last year was that Microsoft removed the search results caching feature from Bing, a move similar to what Google also did earlier in the year. [Additional coverage in SearchEngineLand]
Ad blockers remain functional in Firefox: Mozilla will continue to support the old Manifest V2 browser extension API in Firefox. The API allows ad-blocker extensions to continue working properly and block ads. A newer API called Manifest V3, proposed by Google several years ago, has severely limited the ability for ad blockers to remove ads from web pages. Mozilla's statement comes a week after Google started disabling extensions built on the old API inside Chrome, including the older and better ad blockers.
New RIS jamming tech: A team of academics has developed a new type of jamming technology named Reconfigurable Intelligent Surfaces (RIS). The new RIS technology allows attackers fine-grained spatial control over the area they can jam signals in. Academics say the new technology will lower the bar for the precise delivery of jamming signals. For example, a RIS jamming attack can be confined to a select few devices while other nearby systems remain unaffected, even if the distance between them is in the range of millimeters. [Additional coverage in techXplore]
"We demonstrate complete denial-of-service of a Wi-Fi device while a second device located at a distance as close as 5 mm remains unaffected, sustaining wireless communication at a data rate of 25 Mbit/s. Lastly, we conclude by proposing potential countermeasures to thwart RIS-based spatial domain wireless jamming attacks."
Government, politics, and policy
Belgium investigates Chinese hack: Chinese state-sponsored hackers have allegedly breached the email server of Belgium's intelligence service VSSE. The hack took place in early 2023 and exploited a zero-day in email security product Barracuda. According to local media, the hackers stole VSSE emails from 2021 to 2023. The stolen content represented 10% of all the agency's emails. [Additional coverage in Le Sour/English coverage in Politico EU]
RNC hides Chinese hack: Chinese state-sponsored hackers breached the email system of the Republican National Committee in July of last year. The intrusion took place a month after Iranian hackers also gained access to the Trump campaign's emails. According to the Wall Street Journal, the RNC did not notify the FBI about the intrusion.
Russia looking at internet age checks: Russia's Commissioner for Human Rights has urged the government to adopt age verification mandates for the RuNet to prevent children from accessing 18+ content. [Additional coverage in Klops]
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Aaron Attarzadeh, Enterprise Security Engineer at Nucleus. Aaron goes into new concepts for the vulnerability management scene, such as asset correlation and asset linking.
Arrests, cybercrime, and threat intel
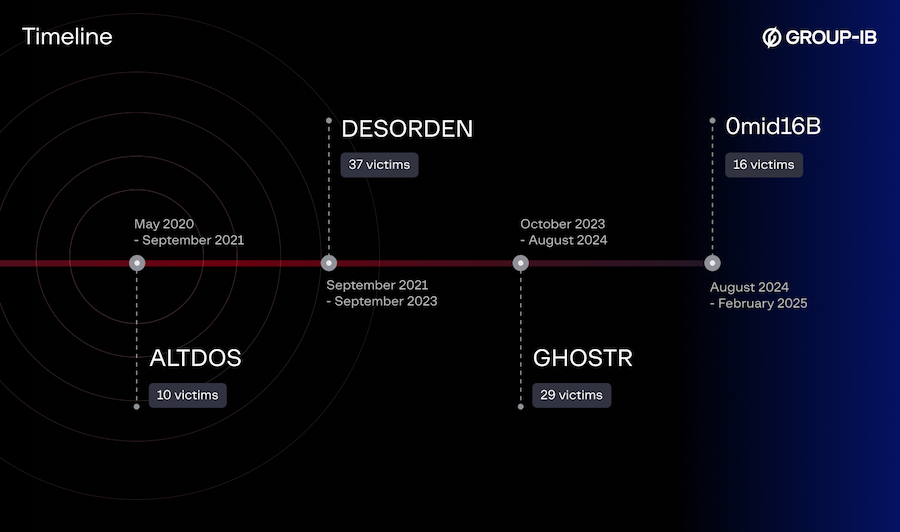
Desorden hacker arrested in Thailand: Thai police detained a hacker who breached and sold the data of over 70 companies. The 39-year-old suspect used multiple names over the past five years, such as AltDos, Desorden, GhostR, and 0mid16B. Most of his victims are companies from Southeast Asia. The hacker was identified as a Singaporean citizen. [Additional coverage in DataBreaches.net]
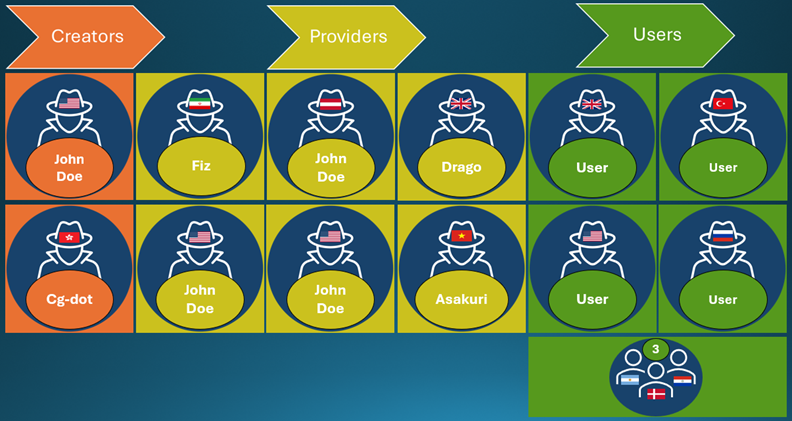
Microsoft sues Storm-2139: Microsoft has filed a lawsuit against four individuals who are part of a cybercrime group that bypassed guardrails in its GenAI services to generate celebrity and sexually explicit deepfakes. The four used customer credentials scraped from public sources to access Microsoft services. They modified customer systems and then re-sold access to the GenAI capabilities to their own customers via underground forums. The four suspects are based in Iran, the UK, China, and Vietnam and are part of a group that Microsoft tracks as Storm-2139.
Kiberphant0m pleads guilty: The US Army soldier who recently hacked AT&T has pleaded guilty. His guilty plea includes loads of tasty details, such as his online search history for epic stuff like:
- can hacking be treason?
- where can I defect the US government military which country will not hand me over
- US military personnel defecting to Russia
- Embassy of Russia – Washington, D.C.
Gotbit founder extradited: The US has extradited a Russian national from Portugal for his role in a scheme to manipulate cryptocurrency markets. Officials charged last year Aleksei Andriunin and two executives at his company Gotbit. Gotbit allegedly provided market manipulation services to create fake trading volumes for cryptocurrency companies and boost the value of their crypto assets. The FBI created and ran its own crypto token last year to catch Gotbit and several other "market-maker" companies.
Starlink is a favorite in scam compounds: The operators of cyber scam centers in Myanmar are now using Starlink to get online. Starlink equipment was seen on top of at least eight scam compounds since June of last year. The move to Starlink comes after Thai authorities seized shipments of internet equipment and cut fiber optic cables in the area. [Additional coverage in WIRED]
ScreamedJungle: A threat actor named ScreamedJungle has compromised and injected malicious JavaScript code in over 100 Magento online stores to create... browser fingerprints for users visiting the site. Huh? I'm so confused about this.
PyPI package abused for music piracy: Socket Security has discovered a malicious PyPI package that created a botnet to pirate songs from music streaming service Deezer. The package was named automslc and was downloaded over 100,000 since its release in 2019. It posed as a music automation and metadata retrieval tool but used built-in credentials to bypass the Deezer API and force the download of complete audio files.
Malicious extensions found on the VSCode Marketplace: Microsoft has removed two VSCode theme extensions from the VSCode Marketplace for containing malicious code. The two extensions are named "Material Theme – Free" and "Material Theme Icons – Free" and were coded by the same developer. The two were downloaded four million and five million times, respectively. Microsoft says the malicious code was found by a member of the VSCode community but did not elaborate on its nature. Its staff is now reviewing the developer's other extensions. The developer claims the malicious code was shipped via compromised dependency.
WhatsApp hijacking campaign: Sandworm "Signal device linking" tactics come to WhatsApp. Security researcher Vlad Pasca has documented a campaign targeting Romanian users with a "vote in a contest" lure that social-engineers them into linking their WhatsApp account to an attacker's device.

Fake CAPTCHA campaigns: Infoblox and Netskope have both published reports on the wave of fake CAPTCHA malicious campaigns delivering the Lumma Stealer infostealer.
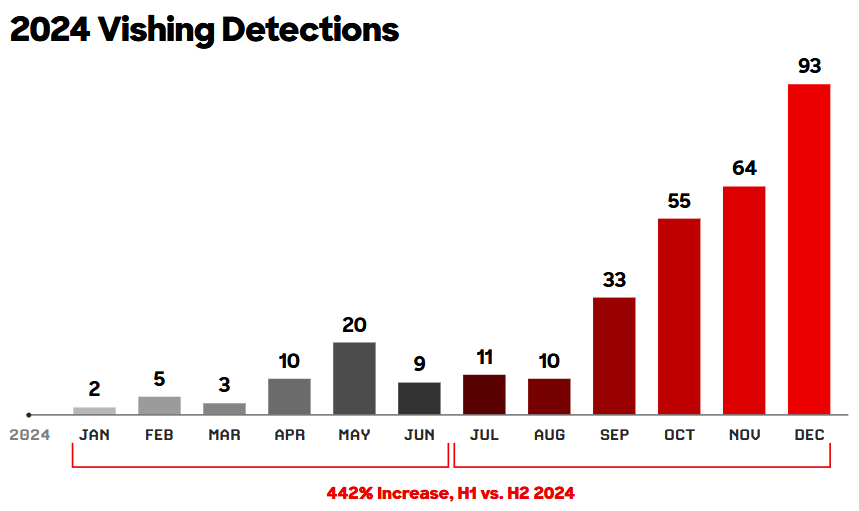
Vishing activity exploded in 2024: Voice phishing (vishing) attacks saw explosive growth and grew by 442% last year, according to CrowdStrike's yearly threat report. The technique saw increased adoption over the last four months of 2024. It is widely used to deploy backdoors or remote access tools on enterprise networks. These tools are then used to enable or deploy ransomware. It is now widely used by e-crime groups across China and Russia, such as Chatty Spider, Plump Spider, and Curly Spider.
Malware technical reports
RustDoor and Koi Stealer: PAN Unit 42 has seen the RustDoor and Koi Stealer malware in campaigns linked to North Korean hackers to target macOS users in the cryptocurrency space.
Vo1d botnet: QiAnXin has spotted a new variant of the Vo1d IoT botnet. The new variant is now running on over 1.6 million devices, most of which are smart TVs. QiAnXin says traffic to the botnet's infrastructure is so massive that ten of its command and control servers have entered the Tranco Top one million most popular websites on the internet. The Vo1d botnet was discovered last year by Russian security firm Dr.Web on over 1.3 million devices.
Sponsor section
Nucleus Security's COO Scott Kuffer shows Patrick Gray their vulnerability management platform. It ingests scan outputs from a number of vulnerability identification tools, normalizes that information and then allows vulnerability management teams to do things like assign responsibility for certain types of bugs to the correct people.
APTs, cyber-espionage, and info-ops
Lotus Blossom (Billbug, Thrip, Spring Dragon): Cisco Talos has discovered new cyber espionage activity from the Lotus Blossom APT that delivers the Sagerunex backdoor.
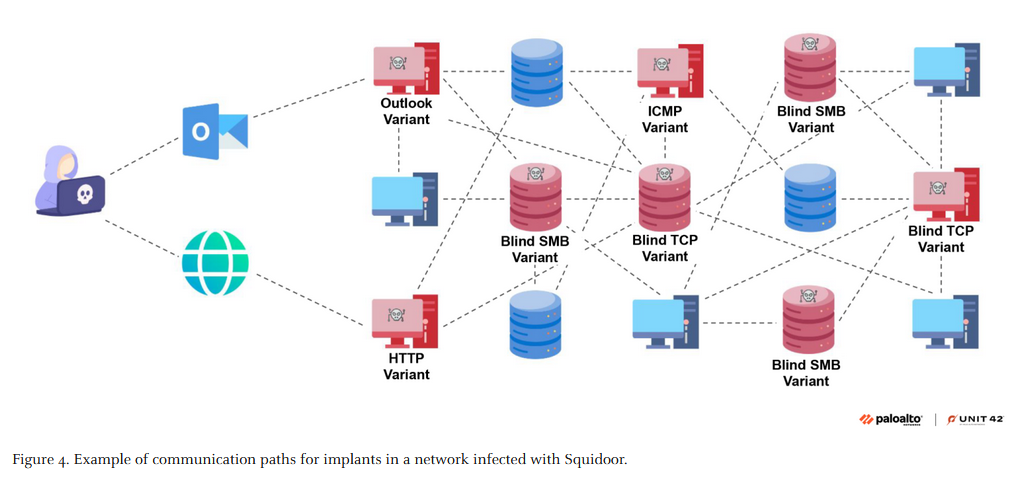
CL-STA-0049 and Squidoor: PAN Unit 42 has published a report on a Chinese APT group it tracks as CL-STA-0049 and its main malware, a backdoor named Squidoor. This is what the Elastic security team calls REF7707 and FINALDRAFT.
"The threat actor behind the CL-STA-0049 cluster of activity has attacked high-value targets in South America and Southeast Asia. The primary objective appears to be gaining a foothold and obtaining sensitive information from their targets. We assess with moderate-high confidence that this threat actor is of Chinese origin."
Vulnerabilities, security research, and bug bounty
NAKIVO vulnerabilities: watchTowr Labs has discovered a vulnerability in Nakivo backup software that allows unauthenticated attackers to remotely retrieve files from the application. Tracked as CVE-2024-48248, the vulnerability can be used to retrieve the backup server's password or the backup files themselves. watchTowr says the vendor patched the bug even if it never replied to its disclosure.
Cisco security updates: Cisco has released three security advisories for various products.
Mattermost security updates: Open-source collaboration platform Mattermost has released security updates to patch three security flaws.
Google calls for a memory-safety standard: Google says that with the rise of several memory-safe languages and technologies, there is now a need for a common standard to address and prevent memory safety vulnerabilities.
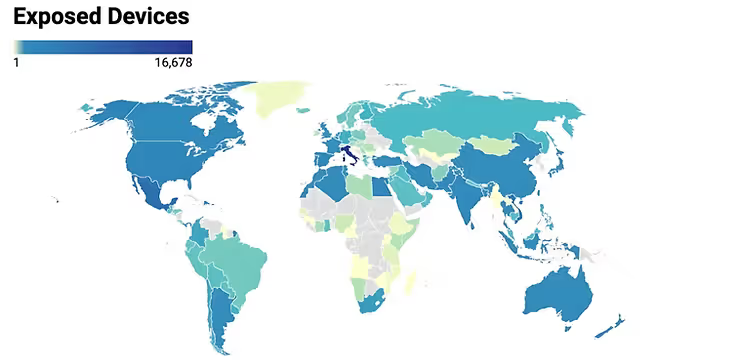
Huge AMS exposure: Security firm Modat has found over 49,000 devices related to building access systems exposed on the internet.
Infosec industry
NCC sell-off: NCC Group has sold off Fox Crypto, a division of Fox-IT that specializes in high-assurance cryptographic products.
New tool—Twilio Security Scanner: Security firm Relay Hawk has open-sourced Twilio Security Scanner, a security scanning tool for Twilio accounts.
New tool—Kubernetes Spoofilizer: Positron Security has released Kubernetes Spoofilizer, a tool to perform Kubernetes Golden Tickets attacks.
New tool—AWeSomeUserFinder: Pen tester Joe Helle has released AWeSomeUserFinder, an AWS IAM username enumerator and password spraying tool.
New tool—FindGPPPasswords: Security researcher Rémi Gascou has released FindGPPPasswords, a "cross-platforms tool to find and decrypt Group Policy Preferences passwords from the SYSVOL share using low-privileged domain accounts."
Threat/trend reports: Anvil Logic, Bluesight, CrowdStrike, GreyNoise, Kaspersky, NCC Group, Quorum Cyber, Radware, StormWall, and Veracode have published reports and summaries covering various infosec trends and industry threats.
Risky Business Podcasts
Tom Uren and Patrick Gray talk about the White House apparently considering kicking Canada out of the Five Eyes intelligence alliance to apply pressure on the country. It's a terrible idea and even thinking about it undermines the strength of the alliance.
In this edition of Between Two Nerds, Tom Uren and The Grugq examine the fundamental principles of network exploitation as described in Matthew Monte's "Network Attacks and Exploitation: A Framework" book.
