Risky Bulletin Newsletter
February 16, 2026
Risky Bulletin: Cambodia promises to dismantle scam networks by April
Written by

News Editor
This newsletter is brought to you by runZero, the Total Attack Surface & Exposure Management platform. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
Following growing international pressure, the Cambodian government has promised to crack down and dismantle cyber scam networks operating within its borders by April this year.
The government says it raided 190 locations in January alone, and arrested more than 2,500 suspects.
More than 110,000 foreigners who used to work in the scam compounds, by force or voluntary, have also been freed and left the country already, according to the country's Commission for Combating Online Scams (CCOS).
The raids have hit 44 casinos, which are often used to hold the call center workers in spare rooms and under guard. Raids have also hit major hotel chains and newly-built building clusters that researchers have also been tracking for years.
CAMBODIA: #8 Park in Prey Veng was until recently holding out against the current crackdown on online scam compounds in Cambodia. This changed this week, and thousands of people have left over the last few days. Check out our updated profile on the park below. 1/3
— Cyber Scam Monitor (@cyberscammonitor.bsky.social) 2026-02-13T23:25:57.852Z
CAMBODIA: A large contingent of police gathered outside Golden Lion International casino and hotel in Sihanoukville. 1/3
— Cyber Scam Monitor (@cyberscammonitor.bsky.social) 2026-02-14T11:31:49.754Z
While the junta in neighboring Myanmar chose to use dynamite to blow up buildings in its biggest scam compound, the Cambodian government chose to be a bit more pragmatic and turned the Mango Park 2 into a holding center for freed workers until their identities are sorted out and sent home.
Not all of these crackdowns have been as clean as the government makes them look. The sheer size of the cyber scam compound and human trafficking component is giving Cambodian authorities major problems, even if they have assigned a massive task force of 700 people to deal with the problem.
An Associated Press investigation found that many of these workers are often left to fend off on their own. Some are deported by the state, some get help from their embassies or consulates, but just as many find themselves sleeping on the streets, asking locals for help, or even going back to the compound premises just for a place to sleep.
Cambodian officials say the courts have already tried 48 cases related to cyber scam operations and convicted 168 suspects, with more cases on the docks.
The government has also recently put forward a bill that would grant the police the legal powers to intercept and dismantle tech and cyber-enabled crimes. Officials say the new law will streamline the process of cracking down on cyber compounds, which is a new phenomenon that has sprouted across Southeast Asia just over the past half decade, catching many government and law enforcement agencies on the back foot.
The messaging around scam compounds has taken a 180-degree turn compared to last year. From denial and playing down the problem, Cambodia officials seem to have taken the bull by the horns and are tackling the problem as directly and blunt as possible—with arrests, and then more arrests.
Risky Business Podcasts
The main Risky Business podcast is now on YouTube with video versions of our recent episodes. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
Odido hackers came in via phishing: The hackers who breached Dutch ISP Odido hacked the company by phishing one of its customer service representatives. The intruders gained access to their account and then scraped customer data from the company's Salesforce account. The details of more than 6.2 million customers were harvested. [NOS] [h/t R.V.D.]
Conduent under investigation: The Texas OAG has launched an investigation of Conduent's 2025 data breach, calling it "likely the largest breach in US history."
Guernsey healthcare provider told to get its act together: The Guernsey data protection agency has told a local healthcare provider to make changes to its cybersecurity practices. The agency says First Contact Health has failed to take any measures to protect patient data after a May 2024 data breach. [BBC]
Breach at sex toy maker Tenga: Sex toy maker Tenga has notified customers of a data breach. The company says a hacker gained access to one of its employees' inboxes. The hacker used the account to phish other employees. Tenga fears customer data in the employee's inbox was likely harvested. [TechCrunch]
General tech and privacy
Linux kernel gets PQC support: The next major branch of the Linux kernel, v7, will ship with support for ML-DSA (Module-Lattice-Based Digital Signature Algorithm), a quantum-resistant signature algorithm. It is the same algorithm that will also ship with macOS and Windows. The algorithm was previously known as CRYSTALS-Dilithium. It allows the three operating systems to generate digital signatures that are resistant to quantum computers. US NIST selected ML-DSA as an approved post-quantum encryption standard in August 2024. [Phoronix] [h/t Marius A.]
WD sells all HDD inventory: Western Digital has recently announced that it sold all of the year's hard-drive inventory to AI companies. In other words, prepare for huge SSD price surges. [Wccftech]
Bitwarden Cupid Vault: Password manager Bitwarden has released Cupid Vault, a feature to let users safely share passwords with loved ones.
Ring cancels Flock integration: Amazon's Ring and Flock have both canceled their integration after major backlash of both companies working with US law enforcement, and especially ICE.
Apple account locks in Russia: There is a growing number of users reports from Russia that Apple is blocking access to accounts and requiring local users to verify their account using a photo of their passport. [iPhones.ru]
EU tells TikTok to change addictive features: The European Commission has told TikTok to change some of its features to avoid a fine for addictive design. TikTok was told to disable infinite scrolling, change its recommendation system, and add screen time breaks. Facebook and Instagram are also under investigation in the EU for using addictive design features. TikTok can defend its practices and challenge the results of the Commission's investigation. [Politico Europe]
OpenAI prepares to go into the gutter: OpenAI has fired a female executive for discrimination against a fellow male employee. Coincidentally, the same executive also raised complaints about OpenAI's plans to add an erotica and adult mode to ChatGPT. [WSJ // Gizmodo] [h/t Kevin Beaumont]
Meta to add facial recognition to its smart glasses: Meta plans to add a facial recognition feature to its smart glasses. In an internal memo, Meta said political tumult in the US will distract critics from the controversial feature's release. Meta smart glasses are already under heavy public criticism for being used to secretly record women. The company sold seven million glasses last year. [NYT]
At least one Meta employee thinks it's a good time to add facial recognition technology to glasses because we're too distracted by fascism to effectively protest www.nytimes.com/2026/02/13/t...
— Casey Newton (@caseynewton.bsky.social) 2026-02-13T15:41:16.012Z
Government, politics, and policy
DHS, CISA funding lapses: CISA is operating with diminished capabilities this week after Congress has allowed funding to lapse for the Department of Homeland Security. The US cybersecurity agency has furloughed most of its staff except those on essential duties. It is unclear when the partial government shutdown will end as the two parties fight over ICE's immigration enforcement funding. [Axios // NextGov]
CISA prepares to shut down more cyber programs: CISA will shut down more cyber programs this year as the agency refocuses on OT security. The agency notified staff of the upcoming changes at a town-hall meeting last week. The changes will impact the agency's Cybersecurity Division, also known as the CSD. [CybersecurityDive]
CISA urges OpenEoX adoption: CISA has urged the public and private sector to adopt the OpenEoX standard. Created last year, OpenEoX provides a simple way for devices to broadcast their End-of-Life (EOL) and End-of-Support (EOS) information. Companies like Cisco, Dell, IBM, Microsoft, Oracle, and Red Hat have already implemented the technology in their products. CISA is now urging more vendors to adopt it and urging companies to use OpenEoX data for inventory management.
Democrats angry over lifting of Intellexa sanctions: Five US Democratic senators have asked the Trump administration to explain why it lifted sanctions on three Intellexa executives. The senators claim the government didn't show up to a meeting on the spyware maker's sanctions evasion tactics in early December last year. Instead, the government lifted sanctions on the executives three weeks later without any public explanation. The letter was sent last week to Treasury Secretary Scott Bessent and Secretary of State Marco Rubio. [Bloomberg]
Full letter: www.banking.senate.gov/imo/media/do...
— Vas Panagiotopoulos (@vaspanagiotopoulos.com) 2026-02-14T19:36:12.110Z
Pegasus probe stalls in Israel: The members of a Justice Ministry committee that was investigating abuses committed by Israeli police using the Pegasus spyware have resigned after the police force refused to cooperate and obstructed their work. [Haaretz]
IMSI-catcher behind Sanchez hack: Moroccan intelligence services allegedly infected the smartphone of Spanish PM Pedro Sanchez using an IMSI-catcher. The hack took place in May 2021 when Sanchez visited the city of Ceuta, a Spanish exclave on the Moroccan coast. The attackers then deployed the Pegasus spyware using a zero-click exploit. Details of the hack have been revealed for the first time five years after the hack by sources in the Spanish intelligence community. [The Objective]
Palantir sues Republik over failed Swiss contract: American surveillance giant Palantir has filed a lawsuit against Swiss magazine Republik over two articles that exposed vulnerabilities in its products. The articles triggered a government investigation. The government eventually dropped the Palantir contract on the grounds of national security, citing that sensitive data would not be safe from US government snooping.
EU yearns for offensive cyber: The EU's top tech chief has admitted for the first time that the bloc needs to build its own offensive cyber capabilities. European Commission Executive Vice President Henna Virkkunen says the tide is turning among member states on the topic. Countries like Germany, Latvia, Estonia, and Denmark are now on board with the idea of hacking back. Previously, the EU has stayed away from offensive cyber not to trigger escalation from countries like China and Russia. Virkkunen said EU countries should stop being naive about enemies shutting down critical infrastructure. [Politico Europe // Heise]
Don't hold your breadth
— Catalin Cimpanu (@campuscodi.risky.biz) 2026-02-11T11:42:52.382Z
Sponsor section
In this sponsored interview Casey Ellis chats to Todd Beardsley, VP of Security at RunZero about Kevology, the company’s analysis of CISA’s KEV list. Kevology lets you easily identify and fix vulnerabilities from the list that are urgent and relevant to you.
Arrests, cybercrime, and threat intel
Dutch police arrest extortionist: Dutch authorities have arrested a 40-year-old man for extorting the local police force. The suspect wanted to share footage with authorities but was given a download link instead of an upload one. He downloaded police files and then requested money to delete them.
New SMS blasters spotted in Malaysia: Malaysian authorities have disrupted two SMS blaster operations. The first was active near a casino resort in the country's capital while the second operated in a border town near Singapore. Both operations used fake cell towers installed in the back of cars to capture smartphone signals and send out spam impersonating official services. [CommsRisk]
Malicious Chrome extension: Socket Security has discovered a malicious Chrome extension posing as a Facebook helper tool that steals Facebook and Meta Business Manager TOTP seeds and one time security codes. The extension also exports CSV contacts and steals and Business Manager analytics data and uploads everything to a remote Telegram channel. Similarly, Koi Security also discovered a Chrome extension posing as a VK customization tool that hijacked user accounts. More than 500,000 users downloaded this extension.
Kurd Hacker Forum: A new forum has popped up on the dark web that is modeled after the old BreachForums but focuses on leaks from Iran, Syria, and Turkey. [DataBreaches.net]
Bashe RaaS interview: Threat intelligence analyst Marco A. De Felice has published an interview with the operator of the Bashe Ransomware-as-a-Service platform. The RaaS was previously known as APT73.
More scam letters: Using physical letters to deliver scams to cryptocurrency users is still going strong. The technique was first seen last year, has continued through the winter, and new letters were spotted last week.
Qishing overview: Palo Alto Networks has published a top-down overview of the QR code phishing ecosystem and the most popular tricks current campaigns employ, such as the recent use of in-app deep links to trigger malicious behavior on the device.
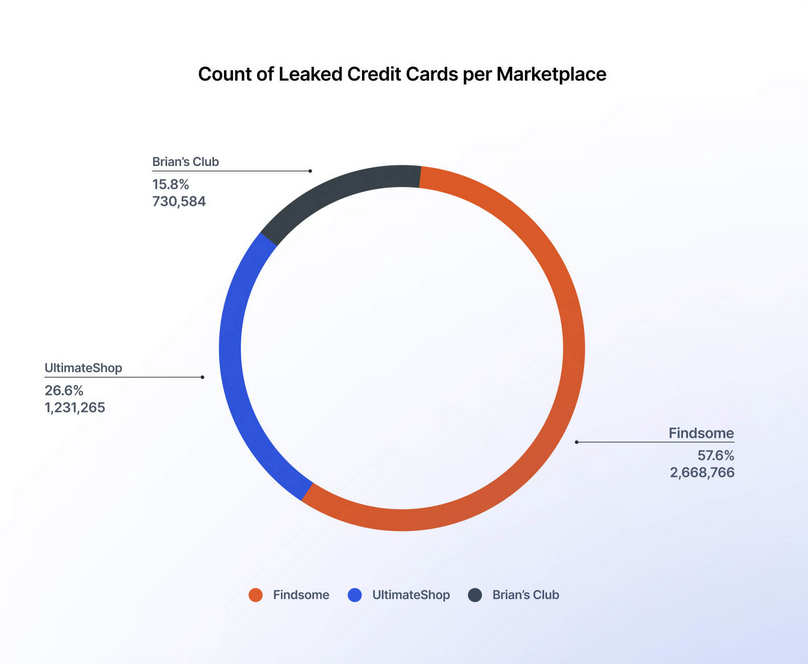
Carding ecosystem, 2026: Following law enforcement crackdown against carding forums in recent years, Rapid7 looks at the major players left on the carding ecosystem this year—Brian's Club, Findsome, and UltimateShop.
"At the same time, carding marketplaces are increasingly focused on selling richer data sets that include personal and contact information (“Fullz”), not just card details. This shift enables a wider range of fraud, including account takeover, wallet abuse, phishing, and identity-based scams, which are less dependent on the underlying payment technology. Rather than disappearing, carding-as-a-service is evolving into a broader identity-driven ecosystem, where marketplaces supply raw data, and buyers use automation and AI to decide how and where to exploit it."
Malware technical reports
BADIIS: The BadIIS malware botnet has infected more than 1,800 Windows IIS servers. The malware deploys malicious IIS modules to perform SEO poisoning or to redirect users to gambling and casino sites. The botnet has been active since last year. According to the Elastic security team, recent versions of the malware now deploy the D-Shield firewall on hacked servers to prevent other botnets from infecting it.
StealC: LevelBlue looks at a recent ClickFix campaign spreading the StealC infostealer.
Sponsor section
In this product demo Patrick Gray hosts Ali Cheikh while he shows off how you can use runZero to scan for and manage vulnerabilities in your environment.
APTs, cyber-espionage, and info-ops
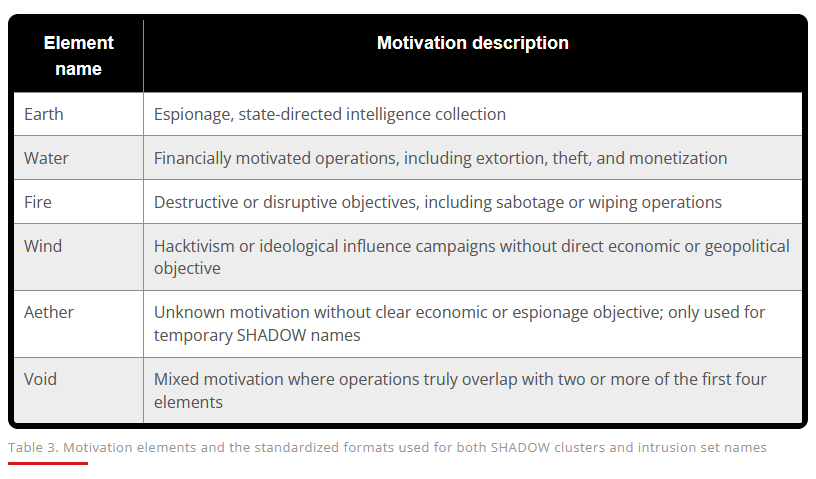
Trend Micro introduces new APT naming scheme: Cybersecurity firm Trend Micro has introduced a new cyber attribution framework and naming scheme for threat actors. The company will use the format of ELEMENT-MONSTERNAME for established and known groups and SHADOW-ELEMENT-NUMBER for temporary clusters. Earth used for the ELEMENT means the group is cyber-espionage focused, Water is for financially motivated groups, Wind is for hacktivism, Fire for destructive attacks, and Aether for unknown motivations.
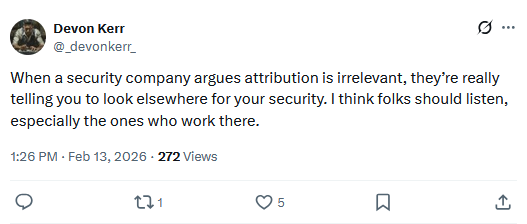
Palo Alto avoids Chinese APT attribution on purpose: Cybersecurity firm Palo Alto Networks has intentionally avoided attributing a recent global cyber-espionage campaign to the Chinese government. The company's research teams linked the attacks to Chinese state-backed hackers but were overruled by executives. Sources told Reuters that the company feared retaliation from the Chinese government. Beijing told Chinese companies at the start of the year to stop using cybersecurity products from a dozen of Western companies. Palo Alto Networks was on a secret blacklist sent to Chinese companies, alongside CrowdStrike, SentinelOne, Mandiant, Wiz, and others.
"Asked to comment on the allegedly softened language, Palo Alto issued a statement to Reuters that said in part: 'Attribution is irrelevant.'"
ChainedShark: A new APT group is targeting China's academic and scientific research sector. The new ChainedShark group has been active since May 2024 and its main focus has been the collection of intelligence on Chinese diplomacy and marine technology. Past victims include universities and research institutions specializing in international relations. Chinese security firm NSFOCUS says the group possesses advanced technical sophistication, strong social engineering capabilities, and advanced knowledge of the Chinese language.
APT28's Operation MacroMaze: Lab52 looks at an APT28 campaign that was active since late September 2025 through January 2026 and which still uses Word macros111!!!!! YOLO!
Russian TV broadcasts its own disinfo: While Russian TV isn't the most accurate form of media, it passed a "milestone" last week when it broadcast a fake news headline from Russia's own info-ops group Matryoshka, passing made-up headlines from fake Le Parisien and Libération websites as real world events. You know what they say, right? Don't get high on your own supply. [The Insider]
SVR takes over Wagner's info-ops: The late Yevgeny Prigozhin's influence operations have now been taken over by Russia's foreign intelligence service, the SVR. Former Wagner-affiliated companies and operatives have been regrouped under a new company called StratConsult. According to a new leak of documents, the company runs influence operations in more than 30 countries, with 22 of them being in Africa. [All Eyes on Wagner // Forbidden Stories // iStories // The Continent // The Dossier Center]
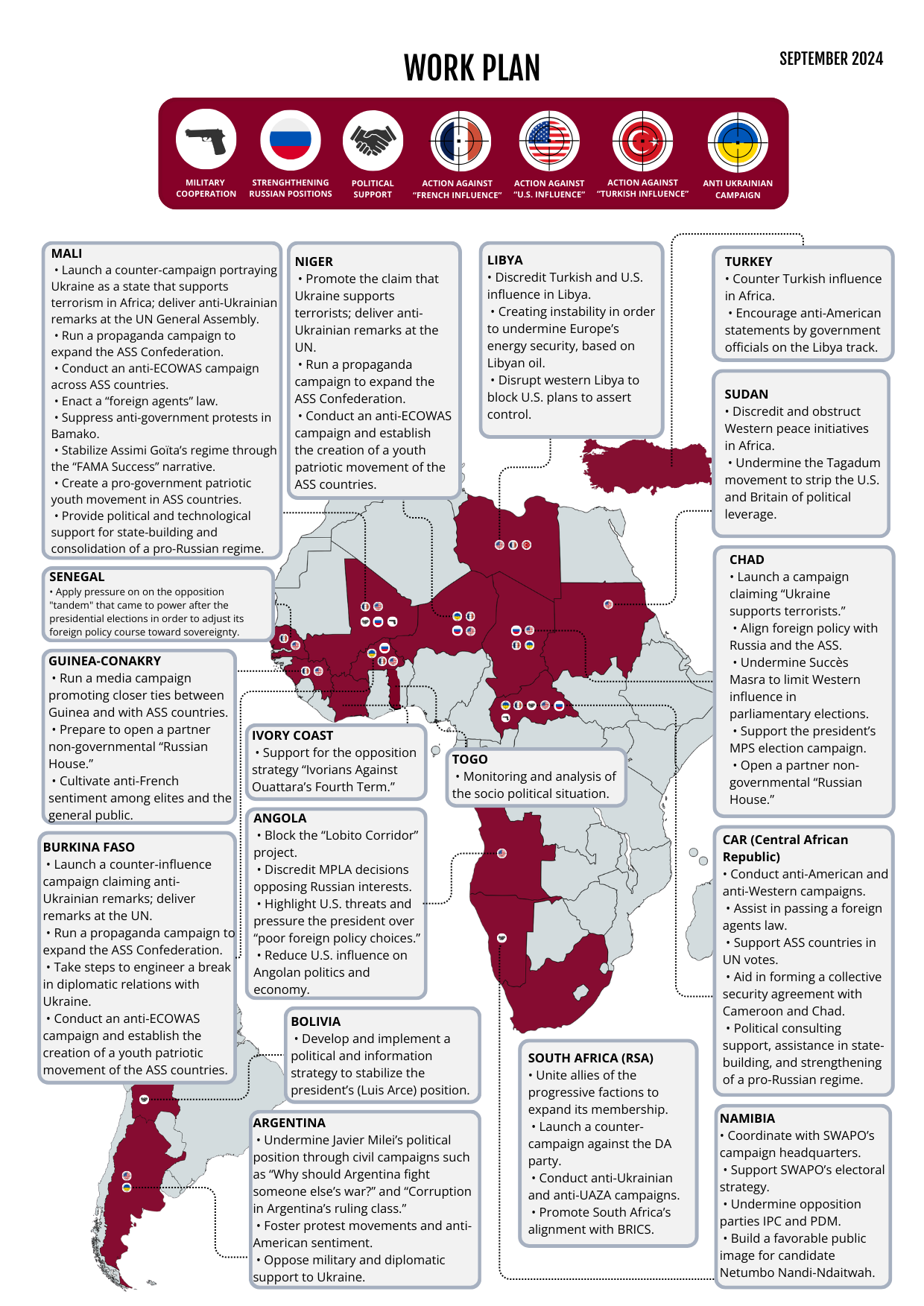
This also explains why Russian propaganda & the SVR have been busy accusing France of plotting coups in African countries lately. Classic attempt to deflect the attention as their extensive disinfo & destabilization ops in Africa and Latin America were about to be exposed. ⬇️
— Roman A. (@romanad.bsky.social) 2026-02-14T12:40:35.754Z
Vulnerabilities, security research, and bug bounty
BeyondTrust exploitation: Threat actors are exploiting a recent vulnerability in BeyondTrust remote access solutions. Security firms Arctic Wolf, Defused, GreyNoise, and watchTowr have spotted attacks less than 24 hours after proof-of-concept code was published online. Tracked as CVE-2026-1731, the vulnerability is a remote code execution bug in Remote Support and Privileged Remote Access products. The bug has a 9.9/10 severity. It was one of eleven bugs CISA added to its KEV database last week.
20yo Munge bug: Security researchers have discovered a vulnerability in Munge, an authentication system used for supercomputers and high-performance computing clusters. The vulnerability can leak the Munge secret key and allow attackers to forge their own Munge tokens and access a cluster's resources. According to French security firm Lexfo, the bug has existed in Munge's code for 20 years.
Dava pharmacy chain bugs: The Dava pharmacy chain in India has secured an exposed API that allowed full access to its backend systems. Security researcher Eaton Zveare says the API could have allowed attackers to create super admin accounts and access any of the company's data. This included customer details, orders, and the ability to edit prices and medicinal details. The attacker could have also created 100% discount coupons or remove prescription requirements from dangerous drugs.
Promptware: A team of academics argues to call cyberattacks carried out against LLMs via prompt injection attacks as "promptware." The report likens the increasing complexity of multi-step prompt injection attacks to classic malware operations. It also warns that promptware could become a serious threat vector in the years to come if AI agents catch on and are here to stay—which they likely will (eventually).
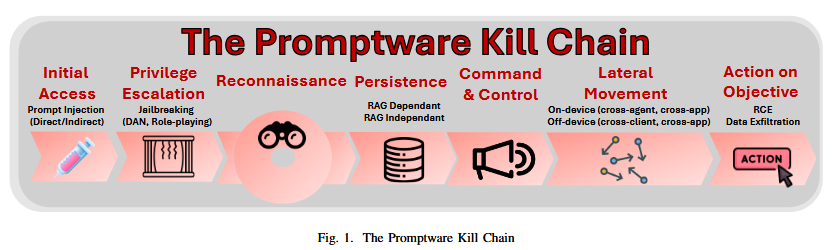
Infosec industry
Threat/trend reports: Backblaze, CyFirma, DCSO, IT-ISAC, and Quorum Cyber have recently published reports and summaries covering various threats and infosec industry trends.
Acquisition news: Email security giant Proofpoint has acquired Acuvity, an enterprise AI security startup.
New tool—Cyber Threat Intelligence Framework: The EU's CERT has released the Cyber Threat Intelligence Framework, the tools and procedures the agency uses for reporting and alerting EU agencies about cyber threats.
New tool—Brutus: Security firm Praetorian has open-sourced Brutus, a zero-dependency credential testing tool written in Go.
New tool—ElephantPoint: Security firm LRQA has released ElephantPoint, a tool to search and exfil data from SharePoint servers.
Risky Business podcasts
In this edition of Seriously Risky Business, Tom Uren and Amberleigh Jack talk about Microsoft CEO Satya Nadella's messaging around personnel changes at the top of its security organisation. These signal a focus on selling security products rather than on making secure products.
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about why the world is destined to be perpetually insecure.
