Risky Bulletin Newsletter
January 31, 2025
Risky Bulletin: Authorities seize Cracked and Nulled cybercrime forums
Written by

News Editor
This newsletter is brought to you by asset inventory and network visibility company runZero. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
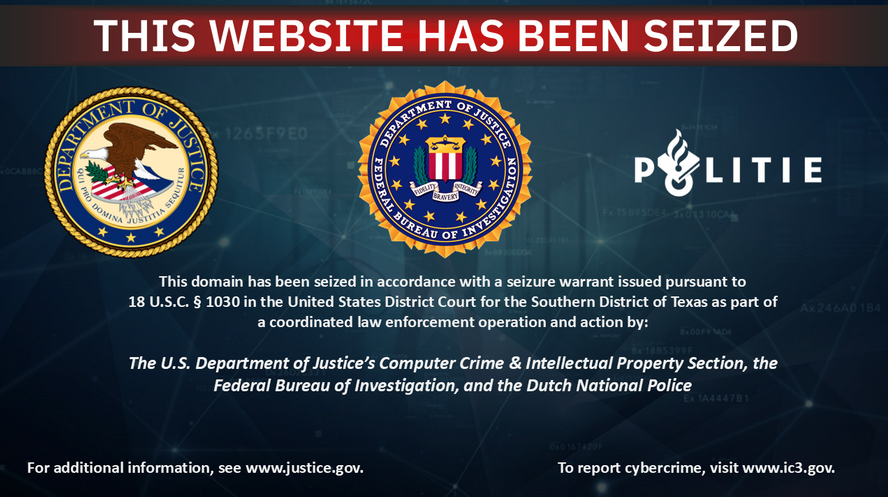
Law enforcement agencies from Europe and the US have seized the domains of Cracked and Nulled, two of today's most popular cybercrime forums.
Authorities have seized 12 domains and made two arrests after searches at seven locations across the EU.
The US Justice Department has identified one of the Nulled admins as Lucas Sohn, 29, an Argentinian national residing in Spain.
Both forums have been around for over a decade. Cracked had over 4.7 million registered users, and Nulled had over 5.3 million users before they were taken offline on Wednesday.
While the forums claimed to be ethical hacking and educational portals, they also served as a marketplace for the exchange of hacking services and malware.
Throughout the years, the forums were used to sell access to DDoS tools and botnets, hacked accounts, stolen databases, and hacked security camera feeds.
Every time the public's attention turned to some of its sections, admins banned the topics, only for a new one to pop up a few months later.
For the past two-three years, both forums became a go-to place to buy "config files" and "combo lists" that could be used to launch brute-force attacks against various online platforms, such as streaming services, cloud platforms, and email servers.
The admin of the Cracked forum confirmed the takedown hours after an FBI banner appeared on the site's front page.

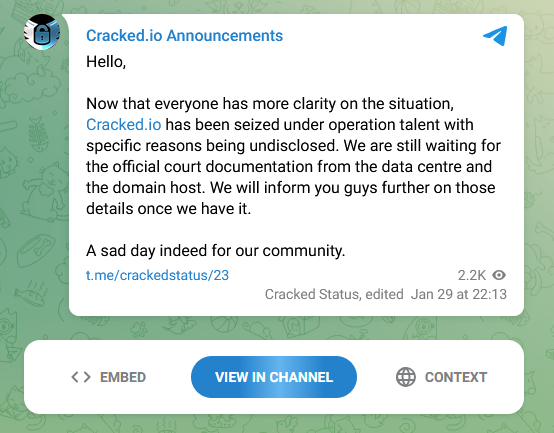
Operation Talent also seized the domains of two other smaller cybercrime services—StarkRDP, a marketplace that sold access to hacked Windows RDP servers, and Sellix, a platform for creating custom online stores that were often used to host online criminal shops.
Europol says both platforms were run by the same suspects.
Risky Business Podcasts
Risky Business is now on YouTube with video versions of our main podcasts. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
DeepSeek leak: Chinese AI company DeepSeek has exposed an internal database containing sensitive data on the internet. The database included millions of records, such as user queries, secret keys, and app logs. DeepSeek secured the database after a report from cloud security firm Wiz.
Smiths Group hack: London-based engineering giant Smiths Group has disclosed a security breach after a threat actor gained access to its internal systems.
SAWS cyberattack: A cyberattack has taken down the website of the South African Weather Service (SAWS), leaving local government services and businesses without weather forecasts for almost a week.
MGM breach settlement: A judge has approved a preliminary settlement in a class-action lawsuit filed against MGM for the company's July 2019 data breach and a September 2023 ransomware attack. The total settlement is $45 million, with a tiered payout system. Plaintiffs in the first tier will receive $75, while those in tier two and three will receive $50 and $20 payments, respectively. [Additional coverage in The Record]
DogWifTool supply chain attack: A threat actor has stolen over $10 million worth of crypto tokens after a supply chain attack against the crypto dev community. The attack targeted DogWifTool, an app used by crypto developers to launch and promote memecoins on the Solana blockchain. The hack took place after attackers allegedly compromised the app's GitHub account and released malicious versions containing a remote access trojan. Attackers are believed to have used the RAT to steal private keys and empty out dev wallets. [Additional coverage in Cybernews]
General tech and privacy
US states fail at privacy: A report released by the Electronic Privacy Information Center (EPIC) and US PIRG Education Fund has found that none of the 19 US states that have privacy laws received a maximum A privacy assessment rating. In fact, eight received Fs as the laws failed to properly protect user data from tech corporate abuses.
DOJ sues to block HPE's Juniper acquisition: The US government has sued to block HPE's proposed $14 billion acquisition of rival wireless networking technology provider Juniper Networks.
Google Sync deprecation: Google will deprecate the Chrome Sync feature for browsers that are older than four years.
PyPI now supports project archival: Developers of Python packages can now archive projects on the PyPI portal as a way to let users know no new updates will be provided.
Death of OCSP: ModSecurity founder and Let's Encrypt board member Ivan Ristic has published an overview on the creation and then slow death of the Online Certificate Status Protocol (OCSP).
NordWhisper protocol: NordVPN has developed a new protocol the company claims can bypass VPN-blocking technologies. Named NordWhisper, the protocol is a new type of web tunneling technology that mimics regular web traffic. The protocol is similar in design to the Tor Project's new WebTunnel anti-censorship technology, which works in a similar fashion.
Verified badge for Play VPN apps: Google will add a special "verified" badge on the official Play Store to VPN apps known to respect user privacy. So far, three VPN apps have already earned the badge. Google says that any VPN app can apply and go through an audit to receive the verified badge.
Government, politics, and policy
UK NAO warns of impending cyberattacks: The UK National Audit Office says the risk of a major cyberattack against UK government networks is "severe and advancing quickly." The agency cited the rising number of legacy systems and vacant cybersecurity positions among government forces. NOA says one in three cybersecurity government roles were vacant or filled by temporary staff.
US internet censorship: A proposed US bill would grant American copyright owners (to be read as the US film industry) the power to block foreign piracy websites in the US. The blocking orders would apply to both ISPs and DNS resolvers. Blocks imposed on global DNS providers will most likely take effect in other countries as well. [Additional coverage in TorrentFreak]
Russian internet censorship: In the meantime, since its invasion of Ukraine, Russia's internet censorship has expanded to include a whopping 417,000 websites. [Additional coverage in the Moscow Times]
Thailand wants to punish third parties for online scams: The Thai government is working on a law that will hold third-party entities responsible for online scams. If companies fail to implement sensible security measures, the bill will require banks, telecom operators, and social media platforms to co-pay victims of online scams. The current bill is part of a government crackdown against the online scam industry that is both operating from and targeting Thailand. [Additional coverage in Nation Thailand]
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with runZero founder and CEO HD Moore about the company's latest capability, a feature called Inside-Out Attack Surface Management that takes internal fingerprints and scans the internet to discover possible exposures.
Arrests, cybercrime, and threat intel
Operation HeartBlocker: Dutch and US authorities have seized domains and servers associated with the HeartSender phishing group. Also known as the Manipulaters Team and Saim Raza, the group sold access to phishing kits, antibot technologies, and stolen data. The group operates out of Pakistan. No arrests or charges have been announced.
Spyware arrests in Turkiye: Turkish law enforcement has detained five suspects on charges of spying on local attorneys. Officials say the group developed a software program named Adalet (Turkish for "justice") they advertised to local attorneys. The group allegedly used the software to spy on customers and steal data from their networks. [Additional coverage in the Daily Sabah]
Hacker Abdilo pleads guilty: David Kee Crees, an Australian hacker also known as Abdilo and DR32, has pleaded guilty two days ahead of his trial in the US. [Additional coverage in DataBreaches.net]
China seeking 36 scam gangs: In a visit to Thailand, Chinese officials said they are seeking help in apprehending 35 major scam gangs that operate out of the country. [Additional coverage in the Bangkok Post]
Jakarta romance scam arrests: Indonesian police have detained 20 suspects believed to be part of an online romance scam operation. The group used dating apps to approach victims and then lure them to invest in cryptocurrency through malicious apps that stole their funds. The group was active on sites like OkCupid, Bumble, and Tinder and targeted victims in Southeast Asia. [Additional coverage in the Jakarta Post]
A1project RaaS: A threat actor is selling A1project, a failed RaaS platform.
TAG-124: Recorded Future has published a profile on TAG-124, a name the company has given to a threat actor running a traffic distribution system (TDS) used by multiple malware operations. Other names for this group also include LandUpdate808, 404TDS, KongTuke, and Chaya_002.
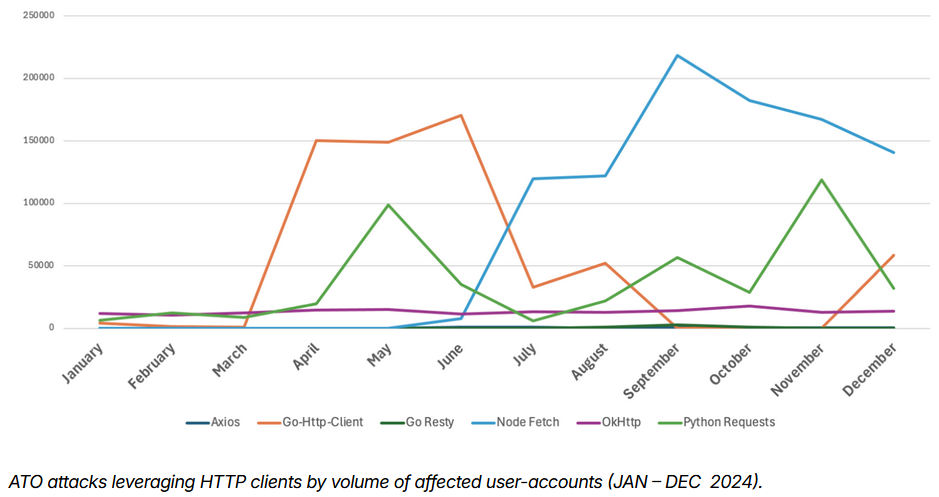
HTTP clients abuse: Proofpoint researchers look at HTTP client tools and how they're abused for account takeover attacks.
French spoofing scene: French security firm Intrinsec has published a report on the voice spoofing services advertised to French-speaking cybercriminals.
AI Chrome extensions: Incogni has published a privacy review of 238 AI-powered Chrome browser extensions currently available on the Chrome Web Store.
Google Play Store abuse: Google says it banned over 158,000 developer accounts last year that tried to publish malicious apps on the official Android app store. In total, Google says it blocked over 2.36 million apps from being published on the store and another 1.3 million from getting excessive permissions on users' devices. It also found another 13 million malicious apps hosted outside the Play Store. The company says that now, over 91% of all Play Store apps use the latest security protections introduced in Android 13, released in 2022.

Malware technical reports
NOVA Stealer: BI.ZONE has spotted a new infostealer named NOVA being sold in underground cybercrime circles under a MaaS model.
FleshStealer: Flashpoint researchers have spotted FleshStealer, a new infostealer that was put up for sale in underground cybercrime circles earlier this year.
Lumma Stealer: Trend Micro looks at a campaign spreading the Lumma Stealer using GitHub repos.
Tria Stealer: Kaspersky researchers have spotted a new malicious campaign targeting Malaysia and Brunei with a new Android infostealer named Tria. The campaign uses WhatsApp spam to spread. Its main purpose appears to be to hijack personal accounts and then request money from a victim's acquaintances. Kaspersky says the threat actor behind Tria appears to be an Indonesian speaker.
"Our investigation suggests that this campaign is likely operated by an Indonesian-speaking threat actor, as we found artifacts written in the Indonesian language, namely several unique strings embedded in the malware and the naming pattern of the Telegram bots that are used for hosting C2 servers."
SparkRAT: Hunt.io shares some tips for detecting SparkRAT servers in the wild. SparkRAT is an open-source cross-platform RAT that has been recently adopted by cybercrime and APT operators.
Coyote banking trojan: Fortinet's security team looks at a new sample of the Coyote banking trojan, recently seeing a resurgence across Brazil.
Lynx RaaS: Group-IB has published a report on Lynx, a ransomware RaaS platform that started operations in July of last year. According to Palo Alto Networks, the Lynx ransomware is a rebrand of the older INC ransomware group, an opinion Group-IB also shares.
"Notably, in-depth analysis revealed a significant code overlap with INC ransomware (over 90% of the Linux ESXi variant functions match when compared via BinDiff). This strongly indicates that Lynx may have purchased or adapted the INC ransomware source code, enabling them to build upon existing malware capabilities."
Sponsor section
Senior Sales Engineer Ali Cheikh demonstrates runZero to Risky Business host Patrick Gray. runZero is a cyber asset management tool that combines active scanning, passive discovery, and API integrations to discover IT, OT, and IoT assets (both managed and unmanaged) across your network, including cloud, mobile, and remote environments.
APTs, cyber-espionage, and info-ops
APTs abuse Google's Gemini: Over 20 Chinese and over 10 Iranian APT and IO groups abused Google's Gemini AI assistant for their campaigns. The groups used Gemini for target reconnaissance, task automation, and content translation, but some groups also attempted to write malware, such as a Chrome infostealer. They also used Gemini for content generation, like disinformation and phishing emails. Russian and North Korean groups also abused Gemini, but to a lesser degree than their Chinese and Iranian counterparts.
Operation Phantom Circuit: Security Scorecard has published a report on Operation Phantom Circuit, another DPRK hacking campaign targeting cryptocurrency devs with malicious software.
Lazarus: On the same note, there's also a Socket Security report on a Lazarus campaign targeting devs with malicious npm packages.
Chinese IO calls for overthrow of Spanish government: A Chinese social media influence operation has used recent floods in the city of Valencia to urge Spanish citizens to overthrow their government. Research group Graphika says this is the first time it saw the Spamouflage group call for the overthrow of a foreign government. The campaign took place over the past three months and is also the first campaign that ran on BlueSky, besides classic places such as Facebook, TikTok, Twitter, and YouTube. The campaign posed as members of a famous Spanish non-profit named Safeguard Defenders. Graphika believes Spamouflage posed as the organization in an effort to discredit its reputation. The non-profit was one of the first organizations to expose China's illegal overseas police stations.
Earth Minotaur attribution: Reporters from Intelligence Online have found links between a Chinese APT group named Earth Minotaur and a private Chinese IT company. The report is paywalled and very expensive so I don't have the company's name. The group is responsible for spying on China's Uyghur and Tibetan minorities. [Later edit: The company has been identified as Sichuan Dianke Network Security Technology]
CL-STA-0048: PAN Unit42 has discovered a new APT group targeting telcos across South Asia.
"The campaign primarily aimed to obtain the personal information of government employees and steal sensitive data from targeted organizations. These objectives bear the hallmarks of a nation-state advanced persistent threat (APT) espionage operation."
NGC4020: Rostelecom's security team has published a report on a new APT the company tracks as NGC4020. The company says the group abuses vulnerabilities to enter networks to disable security software and deploy its malware. The report covers an intrusion where a mistake in a scheduled task stopped the attack.
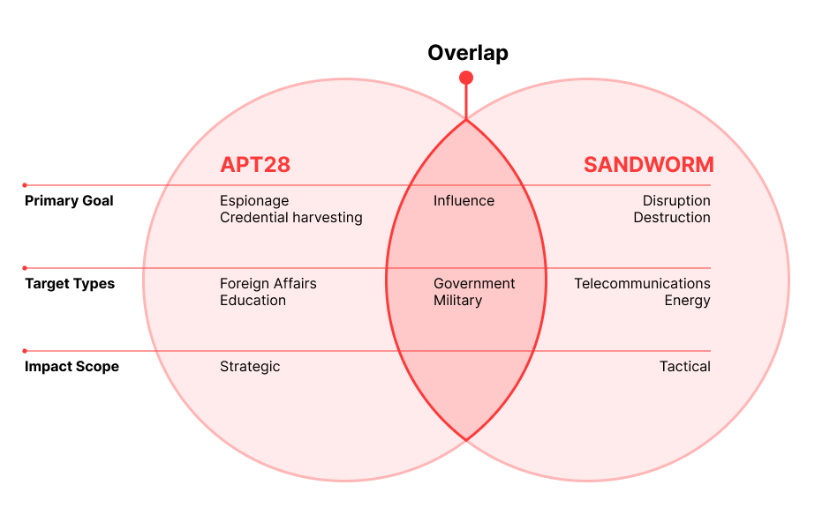
APT28: Maverits has released a report on APT28, a Russian state-sponsored cyber espionage group linked to the GRU Military Unit 26165. The report covers the group's operations since the start of the war in Ukraine, including its new partnerships with non-state entities, such as cybercrime operators.
Vulnerabilities, security research, and bug bounty
Unnamed API vulnerability: In a heavily anonymized report, Salt Security says it helped secure a "world-class travel company" after they discovered an account takeover of a third-party service provider account that could have allowed access to the travel company's data.
Zyxel exploitation: A Mirai botnet is behind a wave of attacks targeting Zyxel CPE routers. The attacks are leveraging a vulnerability (CVE-2024-40891) that was discovered last July but has yet to be patched by the vendor. The vulnerability can be used to execute arbitrary commands on affected devices, leading to complete system compromise. GreyNoise says attacks started around 10 days ago.
Unpatched Voyager bug: Sonarsource researchers have found an arbitrary file write vulnerability in Voyager, a popular open-source PHP package designed for the management of Laravel apps. The issue has not been fixed, per the researchers.
SonicWall security update: SonicWall has patched an LPE in its NetExtender VPN appliance.
KEV data is now on GitHub: CISA has formally brought its KEV database to GitHub, allowing easier access to the data without having to scrape the official website every few hours. [h/t Socket Security]
Browser Syncjacking attack: SquareX researchers have discovered a new attack against Chrome browsers that can allow threat actors to hijack their profile data and browser using a malicious extension. The attack is named Browser Syncjacking and heavily relies on social engineering tricks.
Infosec industry
Acquisition news #1: American vulnerability management platform Tenable plans to acquire Israeli cybersecurity company Vulcan Cyber for $147 million in cash.
Acquisition news #2: UK threat intel company Searchlight Cyber has acquired Australian attack surface management firm Assetnote.
New tool—SprayShark: Security researcher Helvio Junior has published SprayShark, a tool to password-spray Google Workspace (formerly G-Suite) accounts.
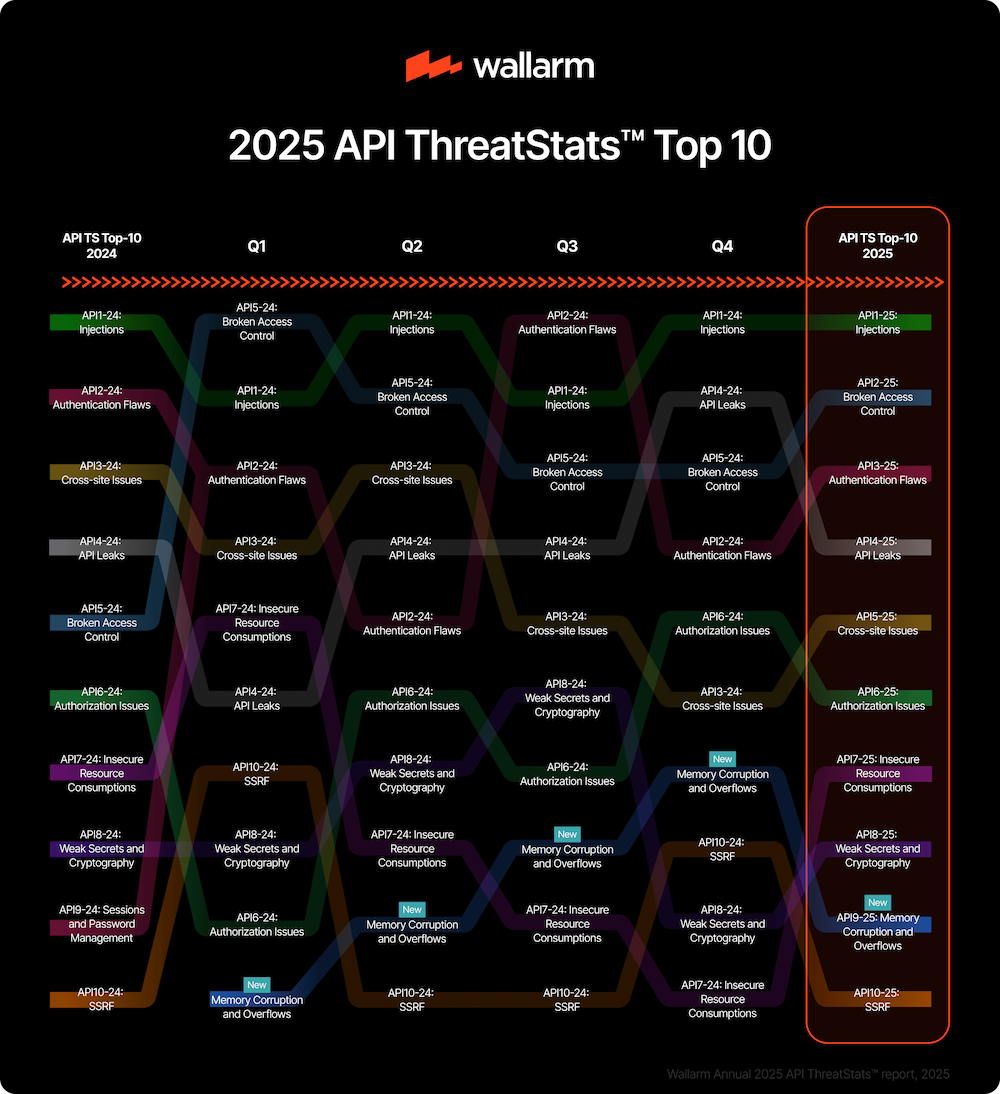
Threat/trend reports: Cisco Talos, Dr.Web, EPIC, Google, Illumio, ITRC, Splunk, and Wallarm have published reports and summaries covering various infosec trends and industry threats.
Risky Business Podcasts
In this podcast, Tom Uren and Adam Boileau talk about the continued importance of hack and leak operations. They didn't really affect the recent US presidential election, but they are still a powerful tool for vested interests to influence public policy.
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about the evolution of Russian cyber operations during its invasion of Ukraine.
