Risky Bulletin Newsletter
December 08, 2025
Risky Bulletin: APTs go after the React2Shell vulnerability within hours
Written by

News Editor
This newsletter is brought to you by Mastercard. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
At least two Chinese APT groups are exploiting a recently disclosed vulnerability in the React framework's server components.
Attacks began within hours after the vulnerability, tracked as CVE-2025-55182 and named React2Shell, was disclosed last Wednesday.
The AWS security team has linked the attacks to two groups tracked as Earth Lamia and Jackpot Panda.
"Earth Lamia is a China-nexus cyber threat actor known for exploiting web application vulnerabilities to target organizations across Latin America, the Middle East, and Southeast Asia. The group has historically targeted sectors across financial services, logistics, retail, IT companies, universities, and government organizations."
"Jackpot Panda is a China-nexus cyber threat actor primarily targeting entities in East and Southeast Asia. The activity likely aligns to collection priorities pertaining to domestic security and corruption concerns."
Amazon says the attackers used anonymizing proxies to hide their infrastructure and also deployed exploits for other vulnerabilities.
The attacks used private exploits, but several public proof-of-concepts have since been released, including one from Lachlan Davidson, the security researcher who initially found and reported the bug.
React2Shell details
The vulnerability itself is quite the doozy. It has a severity rating of 10/10. The vulnerability impacts the server components of the React web development framework. React was initially developed by Facebook for its main web app, and later open-sourced.
It was great for developing web apps, and was later expanded with support for developing desktop and mobile apps. Some apps can function all on their own, being self-contained, but some need a server component where they send data for storage or processing, in the case of more interactive apps, such as games, business portals, or mobile apps.
Data sent from a client to the backend server is serialized for easier transport and sent to the server, where the data is deserialized and processed by the app's React server-side backend.
React2Shell impacts this deserialization process. It allows threat actors to send malicious data to a server that when deserialized, corrupts the process and tricks the server into executing malicious commands. In most cases, attackers don't need to authenticate on the React-based server to send the data, and the data is processed without additional checks.
The Reach2Shell impact is huge. According to the 2025 Stack Overflow developer survey, more than half of today's web development uses React in one way or another. According to the Shadowserver Foundation, more than 77,000 servers have React server components exposed on the internet. That number surpasses 293,000 in a separate Censys scan. Palo Alto Networks claims that internal data has identified over 968,000 React and Next.js instances in its internal telemetry alone. Scans searching for vulnerable endpoints are already underway, according to GreyNoise and VulnCheck.
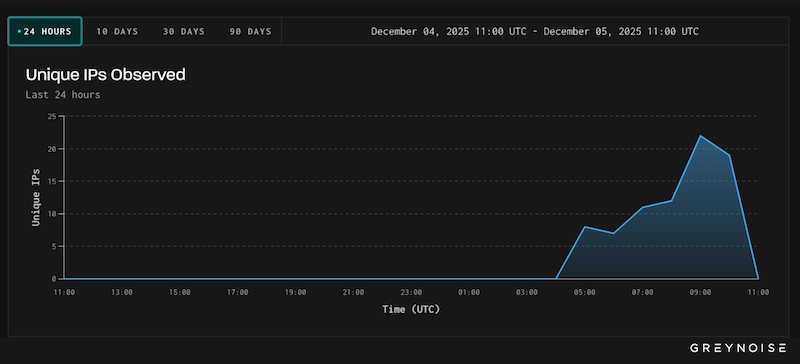
React2Shell exploitation frequency in GreyNoise dec 5-dec 6
— Andrew Morris (@andrewmorr.is) 2025-12-07T16:14:54.712Z
The bug doesn't just impact apps built on the React framework, but also on other frameworks that evolved from it, such as Vercel's super-popular Next.js, a core platform for most of today's Node.js-based CMS systems. In fact, Davidson first found the issue and reported it to Vercel, before the bug was passed down the line to Meta for additional fixes.
Other React-based frameworks impacted include Waku, Parcel.js, and Cloudflare's Redwood.
Fixes have been released last week. CDN providers like AWS, Cloudflare, and Fastly also rolled out their own protections, with Cloudflare's temporary fixes causing a mini-outage of 25 minutes as the platform hurried to mitigate the bug before abuse started.
It's not an exaggeration to say that this bug will haunt the dev ecosystem for ages to come, mainly due to its ease of exploitation, available POCs, and React's popularity. Currently, Next.js is considered the best web technology for producing the best SEO-friendly content. If a technology was ever expected to replace WordPress, it was Next.js. Via Palo Alto Networks:
"Ultimately, this incident underscores the inherent friction between performance and security in modern architecture. While React Server Components optimize data fetching and search engine optimization (SEO) by moving logic closer to the source, they simultaneously move the attack surface closer to organizations’ most sensitive and valuable data."
Risky Business Podcasts
The main Risky Business podcast is now on YouTube with video versions of our recent episodes. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
Coupang sells shares after breach: Several Coupang executives have sold their shares after the company disclosed a major security breach at the end of November. [The Chosun Daily]
Gmarket breach: South Korean authorities are investigating the Gmarket online platform after reports of unauthorized mobile payments. Customers reported losing between $20 and $135 via unauthorized transactions on Gmarket's SmilePay system. The company says it wasn't hacked and that hackers used data stolen from other platforms. Authorities are investigating its claims. [The Korea Times]
Bangkok airport hack: Iranian hacking group Handala has apparently breached the Suvarnabhumi Airport (BKK) in Bangkok, Thailand.
Truenorth cyberattack impacts three Puerto Rico agencies: A cyberattack that hit Puerto Rican IT vendor Truenorth has disrupted activities at three Puerto Rico government agencies—The Department of Education, the Puerto Rico Health Insurance Administration, and the State Insurance Fund Corporation. [InDiario//DysruptionHub]
ASUS ransomware attack: Taiwanese hardware maker ASUS says a recent ransomware attack claimed by the Everest group had actually hit one of its suppliers, a company handling the firmware for its smartphone cameras. ASUS did not name the supplier. [Focus Taiwan]
Freedom Mobile breach: Freedom Mobile, Canada's fourth-largest mobile carrier, disclosed a security breach.
Leroy Merlin breach: French home improvement and gardening retailer Leroy Merlin has notified users of a security breach.
Petco breach: Pet products company Petco disclosed a data breach after it accidentally leaked some data online due to a misconfiguration. [TechCrunch]
Marquis data breach: Fintech company Marquis Software Solutions has disclosed a security breach. The company has over 700 customers, including banks, credit unions, and mortgage lenders. [BleepingComputer]
DreamX nude image leak: Over one million nude images and videos have leaked from a misconfigured database belonging to DreamX, an AI image generator startup behind sites like MagicEdit and DreamPal. [WIRED]
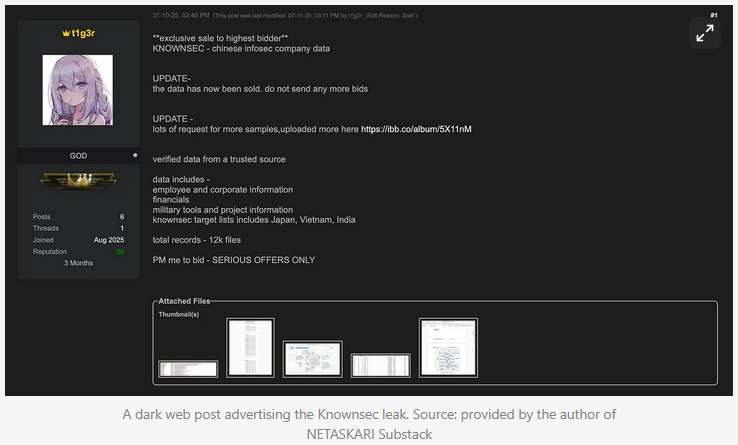
KnownSec leak originates from 2023 breach: A recent leak of internal documents from Chinese security firm KnownSec originates from a 2023 hack. The hacker allegedly exploited three zero-days to breach KnownSec systems. According to Natto Thoughts, the company was unaware of the breach until the files were offered for sale on a hacking forum last month.
General tech and privacy
Micron exits consumer RAM market: American hardware vendor Micron will leave the consumer RAM market and discontinue its Crucial brand. The move comes as the AI boom has led to an explosion in prices for RAM and SSDs as AI companies build data-guzzling data centers and have swallowed almost the entire market output for the next few years.
New Meta antitrust probe: The EU is investigating Meta for blocking rival AI companies from providing their services to WhatsApp users. [CNBC]
EU fines Twitter: The EU fined Twitter €120 million for breaching transparency obligations under the EU Digital Services Act (DSA). Twitter failed to provide access to its data to researchers and disclose its advertising data. Twitter also profited from the paid verification feature, which was abused for fraud and scams. [Politico Europe]
The blue checks thing is about consumer deception. X changed the rules in a way that allowed impersonation and scams to flourish. Kind of like if Kellogg's said it was checking your cereal to remove any bugs or glass shards, and then stopped actually checking but kept that representation. 2/
— Daphne Keller (@daphnek.bsky.social) 2025-12-05T15:03:56.303Z
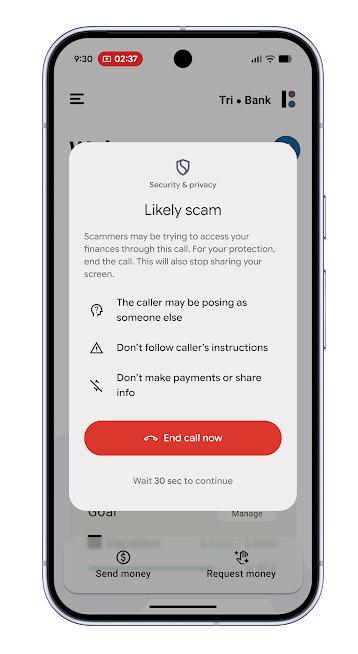
Android expands in-call scam protection: Google will expand a pilot program for a security feature that detects scam attempts during a live call. The pilot program is now live in the UK after it was tested in Brazil and India earlier this year.
Government, politics, and policy
India abandons mandatory cyber app requirement: Smartphone makers will not be required to preinstall a government cybersecurity app on all devices sold in India. Officials mandated the Sanchar Saathi app on all new smartphones in a decision last week. The app was developed by the Department of Telecommunications to allow citizens to report SMS and WhatsApp fraud. The government changed its mind two days after the announcement following extensive public criticism of veiled surveillance.
Taiwan bans RedNote: The Taiwanese government has banned the use of Chinese social media network RedNote. Officials cited the proliferation of scams on the app's online store. The ban will apply for at least one year. [BBC]
Portugal modifies cybercrime law: Portuguese authorities have modified the country's cybercrime laws to add protections for security researchers. [BleepingComputer]
Russia blocks Snapchat, FaceTime, and Roblox: Russia's internet watchdog has blocked access to Snapchat, Apple's FaceTime, and the Roblox game. Roskomnadzor claimed the first two apps were used for terrorist activities, while Roblox was used to spread LGBTQ propaganda. [Meduza]
NCSC Proactive Notifications Service: The UK's cybersecurity agency has launched a service to notify British organizations of vulnerabilities in their networks. The new NCSC Proactive Notifications Service uses Netcraft to scan the British internet and detect outdated and exposed systems. The agency then notified system owners via email.
US halts plan to sanction MSS over telco hacks: The Trump administration has halted plans to impose sanctions on China's spy agency over recent US telco hacks. According to the Financial Times, the administration has instructed staff to prioritize trade deals and not anger Chinese counterparts. A Chinese cyber-espionage group named Salt Typhoon has hacked more than a dozen US telcos to spy on top US officials. The sanctions were supposed to target China's Ministry of State Security and cyber contractors involved in Salt Typhoon hacks.
Plankey nomination stalls again: Sean Plankey nomination for CISA Director has stalled again. The nomination was excluded from a Senate vote after a challenge from Sen. Rick Scott of Florida. It is one of the multiple procedural challenges Plankey has faced since being nominated in March. Sources told CyberScoop that Plankey's nomination may be over and a new candidate may be put forward next year. [GovInfoSecurity]
Trump ends Cybersecurity Retention Incentive Program: The Trump administration has ended a CISA cyber retention program. The Cybersecurity Retention Incentive Program provided extra pay to cybersecurity experts to remain in government jobs. The program covered nearly half of CISA employees. A government audit found the program had enrolled and paid employees working in non-cyber roles. [Bloomberg]
CISA warns employees: CISA has warned employees not to talk to the press anymore. [NextGov]
US Coast Guard mandates cybersecurity training: The US Coast Guard has mandated cybersecurity training for any personnel with access to IT and OT systems. This includes systems running on ships, Coast Guard facilities, or in US territorial waters. Staff will have to complete training by January 12, next year. [Industrial Cyber]
US to deny visas for content moderators and disinfo experts: The US will reject H-1B work visas for individuals who previously worked as content moderators. Individuals who worked on activities such as misinformation, disinformation, and fact-checking will also have visas denied. The new rule entered into effect last week through a State Department cable sent to all embassies and diplomatic missions. The State Department described the individuals as involved in "censorship." [Reuters]
NSA cuts 2k staff: The US National Security Agency has cut its staff by around 2,000 employees. The cuts include employees who were terminated, voluntarily left, or took deferred resignation offers. The Trump administration pressured the NSA to cut some of its staff in meetings earlier this year. [NextGov]
The figure marks a historic staffing reduction for the spy agency, one of the largest in the U.S. intelligence enterprise, and reflects monthslong pressures from the second Trump admin clean out alleged bloat and politicization in its spy offices. www.nextgov.com/people/2025/...
— David DiMolfetta (@ddimolfetta.bsky.social) 2025-12-02T16:51:58.786Z
Sponsor section
In this Risky Business News sponsor interview, Mike Lashlee, CSO of Mastercard talks to Tom Uren about why the company got into threat intelligence.
Mike talks about bringing together payments insights with threat intel to get strong signals about fraud or crime, the benefits of international collaboration and when it makes sense for your CSO to also be the CISO.
Arrests, cybercrime, and threat intel
US charges two twins for destroying govt DBs: The US Department of Justice indicted two twin brothers for deleting almost 100 government databases. Muneeb and Sohaib Akhter, both 34, stole data and deleted databases minutes after they were fired from their contractor roles. The incident impacted multiple government agencies, such as the IRS and the DHS. The brothers allegedly asked an AI tool on how to clear system logs of their actions.
Japan arrests two Chinese hackers: Tokyo police have arrested two Chinese nationals on hacking and financial fraud charges. The two allegedly broke into securities accounts and made unauthorized trades to manipulate the stock market. The suspects were linked to hacks of securities accounts across ten Japanese prefectures. Almost 3,600 victims filed complaints with authorities over the past year. Authorities believe the accounts were compromised through phishing. [Piyolog]
Japan issues arrest warrant for teen hacker: Japanese police have issued an arrest warrant for a teen who used AI tools for cyberattacks. An Osaka 17-year-old boy was charged for allegedly hacking Kaikatsu Frontier, the operator of a chain of internet cafes and fitness gyms. The teen supposedly used ChatGPT to hack the company and steal the data of almost 7.3 million customers. [NHK]
Russian scientist sentenced to prison for DDoS attacks: Russian authorities sentenced a Moscow man to 21 years in prison for launching DDoS attacks on the Russian postal service. The attacks took place in August 2022, after Russia's invasion of Ukraine. Artyom Khoroshilov allegedly worked with the IT Army of Ukraine, a hacktivist group working under Ukraine's military intelligence service. Prior to his arrest, he worked as a mathematician for the Moscow Institute of General Physics. He was also accused of treason for donations to Ukraine's military, taking pictures of Russian rail lines, and planning to create explosive devices. [TASS]
Angler EK and Ransom Cartel plead guilty: A Belarussian and Ukrainian dual-national plead guilty for his role in two long-running cybercrime operations. Maksim Silnikau was a core member of the Angler exploit kit malvertising operation and founded and ran the Ransom Cartel ransomware service. He was arrested in a resort town in Spain in 2023 and extradited to the US last year. [Court document PDF//via CourtHouseNews]
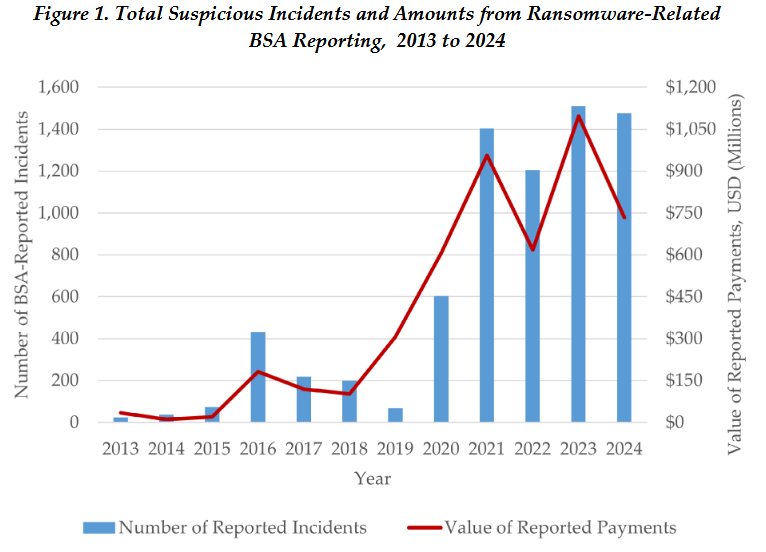
Ransomware payments go down: Ransomware incidents and payments dropped in 2024 after law enforcement disrupted two high-profile ransomware groups. According to FinCEN, US banks and financial institutions paid $734 million to ransomware gangs. This is down from $1.1 billion in 2023.
New DDoS record: Cloudflare has mitigated a new record DDoS attack of 29.7 Tbps. It also mitigated an attack of 14.1 Bpps DDoS attack, the largest of its kind. The attacks originated from a DDoS-for-hire botnet known as Aisuru. The botnet has infected up to four million devices across the globe and is regularly used to attack the gaming and hosting sectors.
IPCola profile: Synthient has published a profile on IPCola, a new proxy network offering more than 1.6 million unique IPs for sale. The network's operator appears to operate out of China.
New GlobalProtect attacks: GreyNoise has spotted a new wave of attacks against Palo Alto Networks GlobalProtect VPN portals. This new spike originated from 7,000 IPs.
Virtual kidnapping scams: The FBI says scammers are demanding ransoms in fake kidnapping schemes. The threat actors trick victims by taking a photo of a family member from social media and altering it to use as a proof-of-life image when demanding ransoms.
Water Saci adopts AI: The Water Saci e-crime group is using AI tools to automate WhatsApp phishing attacks and payload delivery. The group is primarily active in Brazil.
"Evidence suggests that attackers may have used AI tools like LLMs to convert their malware propagation scripts from PowerShell to Python; this would explain their capabilities for batch messaging, improved error handling, and enhanced console output."
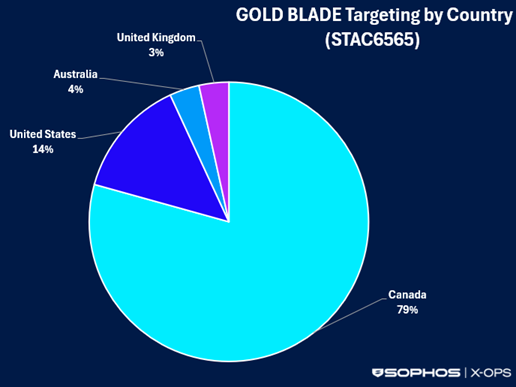
Gold Blade refocuses on Canada: Sophos says that an e-crime named Gold Blade has been running ransomware attacks against Canadian organizations. The group has been active since 2018, is made up of Russian-speaking members, is also known as RedCurl, RedWolf, and Earth Kapre, and operates the QWCrypt ransomware strain.
Operation DupeHike: Seqrite looks at a campaign targeting Russian companies in the HR and payroll management sectors.
Storm-0900 campaigns: Microsoft has detected a new mass phishing campaign originating from Storm-0900. The lures lead users to ClickFix pages and the final payload was the XWorm trojan.
Malicious Rust&Go packages: Socket Security has discovered two+one malicious Rust libraries on the Crates repository. It also found two malicious Go packages as well.
Toddler cybercrime: According to Sky News, children as small as seven years have been referred to the UK police's cybercrime intervention program.
Come on, Cloudflare: New research from SicuraNext has found that Cloudflare helps protect and hide the infrastructure of two-thirds of today's phishing sites.
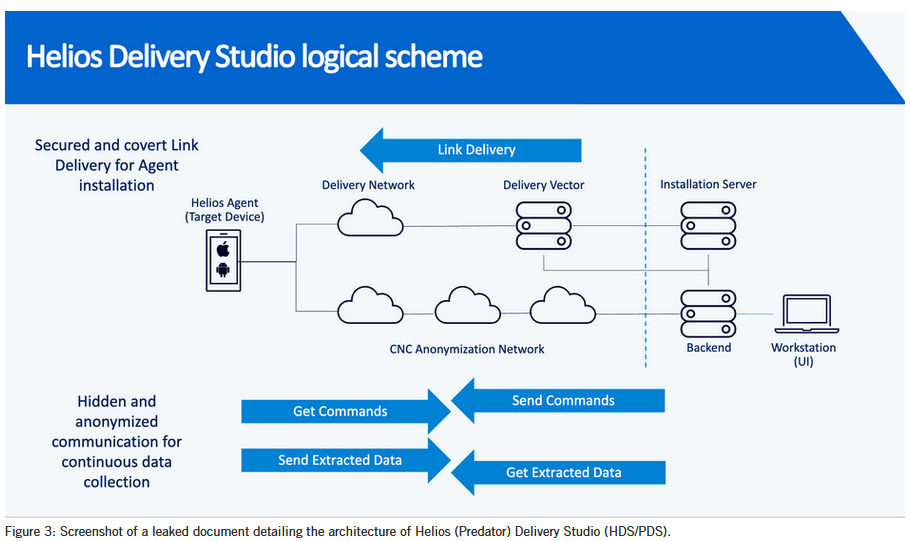
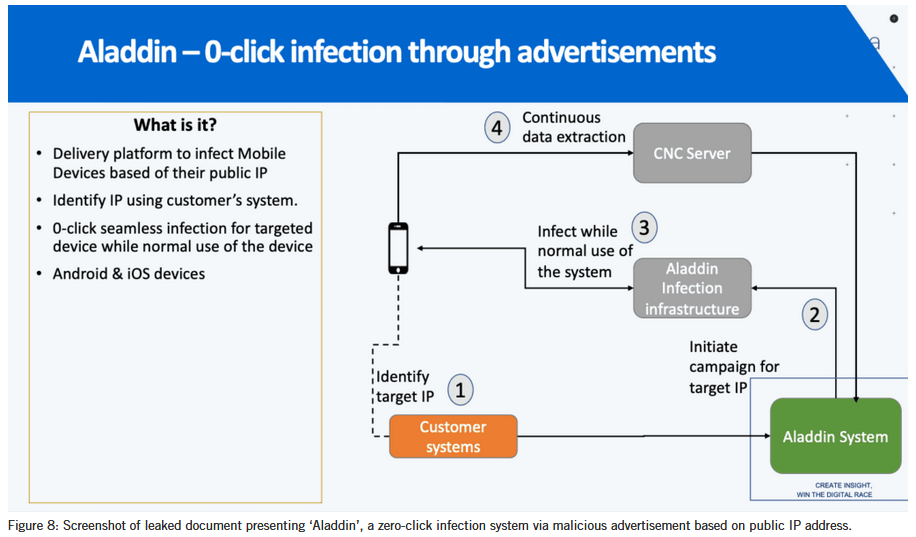
Intellexa is still active despite sanctions: Spyware vendor Intellexa remained active and continued selling its product despite US sanctions. Leaked internal files claim the company has recently sold its product to the Pakistani government. The leak includes training manuals, marketing brochures, and business documents. The latter claim that Intellexa has full access to customer systems and their collected data. The files also exposed a new Intellexa product named Aladdin that delivered payloads via online ads. [Google // Amnesty International // Recorded Future // Inside Story // Haaretz // WAV Research Collective]
Malware technical reports
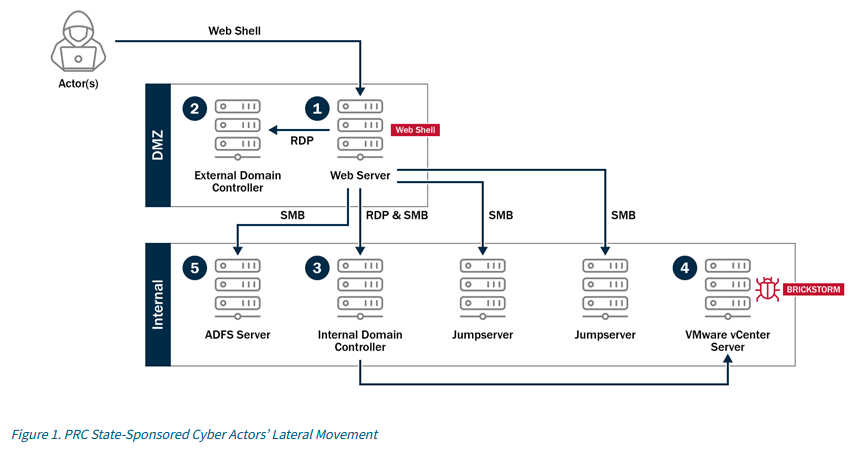
BRICKSTORM: CISA, the NSA, and Canadian authorities have published a malware report on BRICKSTORM, a Windows backdoor used in attacks by a Chinese cyber-espionage group. The backdoor is usually deployed on Windows environments after the group breaches networks via their networking devices. There's also a report from the Walmart security team on this, as well as CrowdStrike, which tracks the group behind the attacks as Warp Panda.
New Symbiote and BPFdoor versions: Fortinet researchers have spotted new versions of the Symbiote and BPFdoor backdoors.
Shanya packer: Sophos looks at Shanya, a new packer-as-a-service advertised on underground hacking circles. The service has been seen used by some ransomware crews on their EDR killer tools.
TangleCrypt packer: WithSecure also seems to look at the same Shanya packer, but they call it TangleCrypt.
SeedSnatcher: CyFirma researchers have found a new Android infostealer named SeedSnatcher, designed around stealing data from crypto wallet apps.
"The threat actor operates as a coordinated team, assigning unique agent identifiers to track infections and manage tasks. Chinese language usage in the operator interface indicates a China-based or Chinese-speaking origin. The malware features device profiling, data exfiltration, command execution, and targeted phishing of cryptocurrency wallets, reflecting a mature, scalable, and financially motivated operation."
FvncBot: A new Android banking trojan named FvncBot has been seen in campaigns targeting Polish users at the end of last month.
New ClayRat attacks: Zimperium has spotted new campaigns spreading the ClayRat Android spyware.
ValleyRAT: Trend Micro has spotted new campaigns spreading ValleyRAT, a remote access trojan developed and used by China-based threat group SilverFox.
CastleRAT: Cisco's Splunk team looks at recent campaigns spreading CastleRAT.
Beima botnet: A student from Bangladesh is behind a new botnet targeting WordPress and cPanel servers. Websites are infected with the Beima PHP web shell and then rented to other threat actors for up to $200. According to Cyderes, most of the operation's customers are Chinese threat actors spreading scams.
Matanbuchus v3: Five years later, the Matanbuchus malware downloader has now reached v3.0, according to Zscaler.
Sponsor section
In this sponsored Soap Box edition of the Risky Business podcast, host Patrick Gray chats with Mastercard's Executive Vice President and Head of Security Solutions, Johan Gerber, about how the card brand thinks about cybersecurity and why it's aggressively investing in the space.
APTs, cyber-espionage, and info-ops
Possible APT group behind gambling network: Security firm Malanta believes a giant network of fraudulent gambling sites targeting Indonesian users might be the work of a state-sponsored APT group, likely with Chinese ties. [ArsTechnica]
Chinese think tank goes after Western researchers: A Chinese think tank has published a hit piece on seven cybersecurity and policy experts specializing in Chinese cyber operations. [Guancha//Internet Archive]
Nimbus Manticore: DeepInstinct looks at new malware from the Nimbus Manticore APT, also known as UNC1549, Smoke Sandstorm, and Subtle Snail.
New US reward for Iranian hackers: The US State Department is offering a $10 million reward for an Iranian couple linked to Iran's cyber operations. Fatemeh Sedighian Kashi and Mohammad Bagher Shirinkar allegedly work for a contractor for Iran's Islamic Revolutionary Guard Corps Cyber-Electronic Command (IRGC-CEC). The two have been linked to hacking operations targeting the US 2020 presidential election as the Emennet Pasargad hacktivist group.

APT-C-53 (Gamaredon): Qihoo 360 has published a report on Gamaredon's abuse of a WinRAR vulnerability (CVE-2025-8088) for its operations. The group, also tracked as Primitive Bear, also abused another WinRAR vulnerability, tracked as CVE-2025-6218.
Calisto's French campaign: Russian cyber-espionage group Calisto has targeted French NGO Reporters Without Borders (RSF).
"Calisto spear-phishing campaigns often involve the impersonation of trusted contacts, sending email either forgetting the attachment, or sending a dysfunctional yet benign PDF file, in order to trigger a response for the victim asking for a resend. We assess this technique is likely to increase the credibility of the exchange."
UTA0355: Russian cyber-espionage group UTA0355 has used European security events as lures for phishing operations. The campaign uses a "live support" feature that guides targets through the attack, such as logging into their accounts and sharing URLs for OAuth phishing workflows.
A study in the evolution of SVR cyberespionage tradecraft
— Mark Kelly (@mkyo.bsky.social) 2025-12-06T19:07:52.221Z
Vulnerabilities, security research, and bug bounty
Important security updates: Akamai, Apache Tika, Duc, Kubernetes, nopCommerce, PickleScan, React Server.
Microsoft silently patches LNK zero-day: Microsoft has silently patched a zero-day in the Windows LNK file format. Tracked as CVE-2025-9491, the vulnerability had been exploited in the wild by 22 hacking groups since last year. The patches had been rolling out in small batches since June. Microsoft initially declined to patch the issue after it was notified of the attacks.
Apple cuts macOS bug bounty payouts: While it has been increasing rewards for iOS remote code execution and zero-click attacks, Apple also reduced the payout ranges for multiple macOS vulnerability types, such as TCC bypasses and sandbox escapes. [Csaba Fitzl on LinkedIn]
Array Networks exploitation: Hackers are abusing a command injection vulnerability in the Array Networks AG series VPN devices to install web shells. According to Japan CERT, attacks have taken place since August. The vulnerability was patched in May, but a CVE identifier was never assigned.
Chrome WebXR vuln write-up: Aisle Security has published a write-up on CVE-2025-12443, a memory corruption in Google Chrome's WebXR AR and VR component.
Unpatched bugs in the Convercent whistleblowing platform: The EQS Group has not released fixes for several vulnerabilities reported in its Convercent whistleblowing platform.
"These issues include missing critical HTTP security headers, insecure and duplicated session cookies, inconsistent SameSite attributes, incomplete clickjacking protection, and an unauthenticated API endpoint that leaks internal customer legal entities."
New SVG clickjacking technique: Security researcher Lyra Rebane has discovered a new SVG clickjacking technique that abuses the SVG filters feature to create programmable fake overlays on top of legitimate content.
PromptPwnd attack: Aikido Security has discovered a new class of prompt injection attacks. Named PromptPwnd, the attacks impact CI/CD pipelines when developers use AI agents.
IDEsaster attack: Similarly, security researcher Ari Marzouk has also detailed IDEsaster, a new class of prompt injection vulnerabilities that impacts AI-based IDEs and their coding assistants. Over 10 IDEs are affected, from Windsurf to Claude Code and Gemini CLI.
AI fake hacking research: Anthropic claims its Claude Opus model found exploits in blockchain smart contracts that would have allowed the theft of $4.6 million worth of assets.
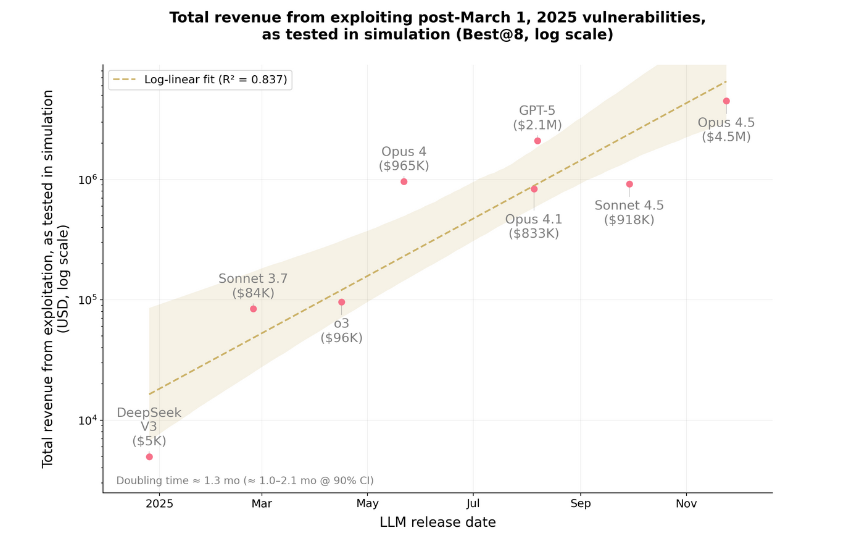
Infosec industry
Threat/trend reports: AhnLab, CyFirma, FinCEN, Incogni, Kaspersky, Sophos, and WanAware have recently published reports and summaries covering various threats and infosec industry trends.
Acquisition news: Cloud software service provider ServiceNow has acquired Veza, an AI-based identity security platform.
New tool—pipetap: Orange's SensePost has released pipetap, a tool to proxy and capture Windows Named Pipes traffic.
Risky Business podcasts
In this edition of Seriously Risky Business, Tom Uren and Patrick Gray discuss a new report proposing a framework for deciding when cyber operations raise red flags. It suggests seven red flags and could help clarify thinking about how to respond to different operations.
In this edition of Between Two Nerds, Tom Uren and The Grugq wonder whether it is possible to deter states from cyber espionage with doxxing and other disruption measures.
