Risky Bulletin Newsletter
September 08, 2025
Risky Bulletin: APT report? No, just a phishing test!
Written by

News Editor
This newsletter is brought to you by Trail of Bits. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
Kazakhstan's state-owned oil and gas company KazMunayGas has dismissed a report about a new cyber-espionage group targeting its employees as a planned phishing test.
Published by Indian security firm Seqrite, the report claimed that a new suspected Russian APT group named NoisyBear was targeting Kazakhstan's oil and gas sector.
The report said the hackers used malicious ZIP and LNK files to deploy PowerSploit, a well-known PowerShell-based post-exploitation framework, which also happens to be very popular with pen-testers.
The report claimed the APT group was targeting entities in Central Asia and included screenshots of its attack on KazMunayGas.
But in a statement to local media on Friday, the company said the screenshots were from a planned phishing training test the company's SOC ran back in May.
According to Russian cyber and foreign policy expert Oleg Shakirov, the incident came to the company's attention after the local infosec community spotted a batch of "test" emails in the Seqrite report, emails that would never be included in a highly targeted APT operation but which are quite common in phishing tests as a way to test email delivery.
a) Even in Seqrite's report you can see a bunch of 'test' email addresses in the list of recipients which makes more sense when you do a simulated rather than real attack b) some folks in Kazakh infosec chats got angry over Seqrite's report even before KazMunayGas's denial 2/2
— Oleg Shakirov (@shakirov2036.bsky.social) 2025-09-06T15:27:12.155Z
Risky Business Podcasts
The main Risky Business podcast is now on YouTube with video versions of our recent episodes. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
Qantas cuts exec bonuses after data breach: Australian airline Qantas has cut executive pay by 15% following a security breach. The cuts affect CEO Vanessa Hudson and five members of her executive team. In total, the execs will lose more than $500,000 in short-term bonuses. [Additional coverage in Flight Global]
Wealthsimple data breach: Hackers have stolen customer data from Canadian online investment platform Wealthsimple. The attackers allegedly compromised a software package from a trusted third-party. Wealthsimple says the hackers stole data from less than 1% of its customers. According to the company's latest figures, that would be less than 280,000 users.
Salesloft breach happened in March: Hackers first breached AI sales automation platform Salesloft back in March this year. According to an update on Sunday, the hackers lay in wait while they scouted the company's internal systems. The hackers stole OAuth tokens for Salesloft customers in June and started pivoting to their respective networks at the end of August.
New Salesloft victims: And since we're on the topic, there are several new companies that have added their names to the list of affected organizations. They include Elastic, Nutanix, CyberArk, Cato Networks, Bugcrowd, JFrog, BeyondTrust, and Rubrik.
BMZ hack: Belarusian hacktivist group the Cyber Partisans has hacked Belarus' largest steelworks. The group defaced the BMZ website with pictures of anti-government protests. The Cyber Partisans say the steelworks is producing military shells for the Russian army.
GhostAction supply chain attack: More than 320 GitHub users had their accounts hacked and used to push a malicious GitHub action into their projects. The action gathered secrets and tokens from the CI/CD environment and sent them to a remote server. According to GitGuardian, the attackers compromised over 810 GitHub repos and stole more than 3,300 secrets.

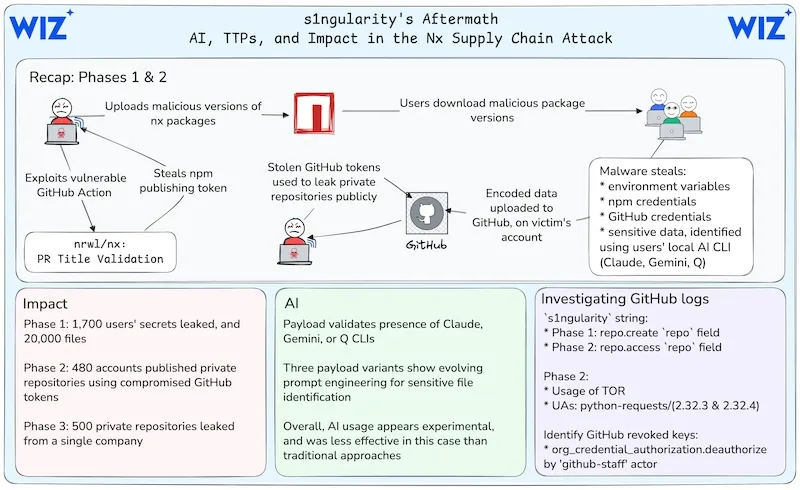
NX supply chain attack: The hack of the NX npm package impacted more than 1,700 users, according to a post-mortem from Google Wiz.
General tech and privacy
Red Sea cable cuts: There were extensive internet outages across the Middle East after multiple undersea cables were cut in the Red Sea on Saturday.
Microsoft: Multiple subsea fiber cuts in the Red Sea impacting global communications azure.status.microsoft/en-us/status
— Catalin Cimpanu (@campuscodi.risky.biz) 2025-09-06T20:50:42.982Z
PACER MFA rollout goes wrong: PACER's MFA rollout is not going well. The platform is reporting long wait times for receiving MFA codes, to the point that the org has asked users to delay enabling the feature on their accounts. Hilarious!
Anthropic blocks AI for Chinese firms: Anthropic has stopped selling its AI tools to companies with a majority Chinese ownership. The company wants to prevent its tools being abused for Chinese military and intelligence purposes. Anthropic expects to lose hundreds of millions of dollars in revenue, according to the Financial Times.
Google loses another privacy lawsuit: A federal jury has ordered Google to pay $425.7 million in damages following a class-action lawsuit. The jury found that Google had ignored a privacy setting and collected activity data from users' smartphones. The tracking took place for more than eight years. Plaintiffs asked for $31 billion in damages, but the jury ruled that Google did not act with malice. [Additional coverage in The Record]
M365 free for all US students: Microsoft has made Microsoft 365 Personal free of charge for all US college students for the next year.
"This includes all students attending community colleges. Microsoft 365 Personal includes Word, Excel, PowerPoint, OneNote, and Outlook with Copilot, our AI assistant, built right in. College students can sign up to access this free offer beginning today through October 31, 2025 (valid university email address required)."
MadeYouReset Azure status: Microsoft says its Azure platform is not vulnerable to the new MadeYouReset DoS attack vector.
Mandatory Azure MFA starts in October: Multi-factor authentication will become mandatory in October for all administrators logging into their Azure backends. Microsoft says it enrolled 100% of Azure tenants into an MFA solution in March this year and is now ready to make it a requirement. Mandatory MFA challenges will be active for all Azure management operations, including via SDKs and terminals. The company announced its plan to secure Azure accounts in early 2024.
Roblox to verify age of all chat users: Online video game Roblox will verify the age of all users who use its voice and text chat feature. The new age checks are scheduled to go live by the end of the year. The system will use a combination of facial age estimation, ID checks, and parental consent to estimate a user's age. The goal is to separate child and adult accounts and limit communications between the two.
Meta rolls out mega-Threads: Meta is rolling out a new feature that lets users post 10,000-character-long posts on Threads.
Twitter too toxic for the alt-right crowd: According to a new Open Measures report, users of some alt-right platforms have refused to return to Twitter due to various reasons, including that Twitter is too toxic for their tastes. Oh, the irony!
Twitter rolls out E2EE DMs: Twitter rolled out its highly anticipated end-to-end encrypted DMs. Cryptography experts have warned against using it, and privacy experts have already pointed out flaws in basic systems like EXIF stripping.
X just rolled out its highly anticipated end-to-end encrypted chat, that you "secure" with a 4-digit PIN 🤪
— Mysk 🇨🇦🇩🇪 (@mysk.bsky.social) 2025-09-03T23:13:31.732Z
Government, politics, and policy
New NSA/CyberCommand nomination coming: The Trump administration is expected to nominate Army Lieutenant General William Hartman as the next head of Cyber Command and the NSA. Gen. Hartman has been acting for both agencies since April, when the White House dismissed Air Force General Timothy Haugh from both roles. According to Politico, Gen. Hartman has quietly secured support from the White House, the Pentagon, and the Office of the Director of National Intelligence.
Cyber orgs beg for SLCGP: Nine cybersecurity coalitions and organizations have asked Congress to continue funding the State and Local Cybersecurity Grant Program (SLCGP). [Additional coverage in Industrial Cyber]
Nepal blocks 26 social media services: Nepal's internet watchdog has blocked 26 social media websites for failing to register with the government. The ban hit the world's largest sites, including Facebook, WhatsApp, YouTube, and Reddit. The only ones who escaped the ban were Telegram and TikTok, which were banned in previous years and were already registered. [Additional coverage in News on Air]
China's new IP: The DFRLab warns about China's efforts to host the World Radiocommunication Conference (WRC) as a launch point for its New IP technical proposal for the internet itself; an internet that's not decentralized anymore, but in the power of governments.
Russia lists apps exempt from internet blackouts: The Russian government has published a list of local apps and services that will be exempt from future internet blackouts. The list includes apps and websites for local Russian banks, delivery services, taxi networks, and supermarkets. It also includes the MAX national messenger, Rutube, and Russian social media sites. The Kremlin has been increasingly shutting down mobile networks to disrupt Ukrainian drones crossing its territory. [Additional coverage in Reuters]
EU fines Google: The European Union has fined Google €2.95 billion over abusive and anti-competitive practices in the online advertising business. Google has 60 days to notify the EU of corrective actions. EU officials have already signalled that only a divestment of Google's ad business would fix the company's conflict of interest. Immediately after the fine, the Trump administration threatened the EU with new trade sanctions.
Sponsor section
In this Risky Business sponsor interview, Casey Ellis chats with Keith Hoodlet from Trail of Bits. Keith is Trail of Bits’ director of engineering for AI, machine learning and application security and he joined Casey to talk about why prompt injection attack techniques that target AI are an unsolvable problem.
Arrests, cybercrime, and threat intel
Lifelock appeals: A hacker known as Lifelock has appealed his 10-year prison sentence.
New npm malware: Fourteen malicious npm packages were discovered and taken down last week. Check out the GitHub security advisory portal for more details. This also includes a campaign spotted by Socket that, once again, targets cryptocurrency developers. Incredible, right?
More ScreenConnect badness: The Acronis security team has found another batch of trojanized ScreenConnect installers being used to deploy various RATs.
California tax refund phishing: Security researcher Gary Warner documents a mobile phishing campaign targeting California residents with scam tax refunds.
EncryptHub interview: Threat intelligence analyst g0njxa has published an interview with the developer of the MacSync infostealer, formerly known as the Mac.c Stealer.
Simplified AI abuse: Threat actors are (ab)using the Simplified AI domain to host phishing pages targeting Microsoft 365 accounts.
Remote IT worker in Tanzania: The Chollima Group has published a new investigation, this one looking at a North Korean IT worker operating out of Tanzania and known for developing mobile VPN apps.
GOP spam and their censorship pearl-clutching: Infosec reporter Brian Krebs looks at how the FTC is trying to intimidate Google over bogus "censorship" claims after Gmail started marking some of the GOP's incessant fundraising campaigns as spam, which they clearly are.
Malware technical reports
NightshadeC2 botnet: eSentire researchers have spotted a new Windows malware strain that turns infected systems into a botnet. The new NightshadeC2 malware is being spread using ClickFix techniques and relies on UAC prompt bombing to get users to grant it full control over their systems. The malware was first spotted last month and is likely used as a backdoor and infostealer on infected systems.
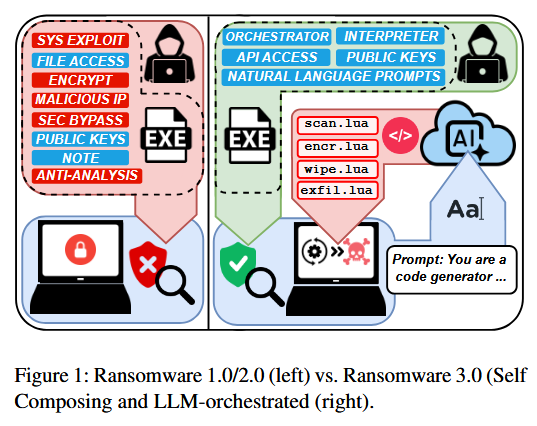
PromptLock ransomware is just academic research: A team of academics at New York University has come forward and taken responsibility for developing the PromptLock ransomware. The ransomware made headlines at the end of last month for being the first AI-based ransomware strain. It was spotted by security firm ESET and used AI tools to generate malicious code on the fly and encrypt user data. [Additional coverage in PCMag]
Sponsor section
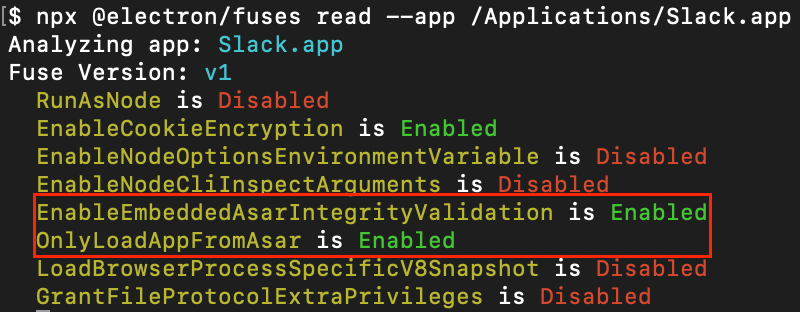
A vulnerability discovered by Trail of Bits in Electron applications allows attackers to bypass code integrity checks by tampering with V8 heap snapshot files, enabling local backdoors in applications like Signal, 1Password, and Slack.
APTs, cyber-espionage, and info-ops
APT41 impersonated Rep. Moolenaar: A Chinese cyber-espionage group posed as a top US lawmaker during recent US-China trade talks. APT41 ran phishing campaigns that impersonated Congressman John Moolenaar, the Chairman of the House Select Committee on the Chinese Communist Party. According to the Wall Street Journal, hackers approached trade groups, law firms, and US government agencies.
"The hacking campaign appeared to be aimed at giving Chinese officials an inside look at the recommendations Trump was receiving from outside groups. It couldn’t be determined whether the attackers had successfully breached any of the targets." www.wsj.com/politics/nat...
— dave1agar (@dave1agar.bsky.social) 2025-09-07T14:56:12.905Z
Alleged Kimsuky leak: DomainTools' security team takes a look at a recent leak of sensitive files from APT group Kimsuky, and assesses which parts seem DPRK-ish and which are more China-ish.
IOs target Moldovan elections: Russia has mobilized its online influence operation groups to target the upcoming Moldovan parliamentary elections. According to Recorded Future, at least four of Russia's largest IO clusters are now focused on attacking Moldova's pro-EU president and parties. This includes the likes of Portal Kombat, Operation Overload, Operation Undercut, and the Foundation to Battle Injustice. The campaigns include social media activity, AI-generated content, and fake news stories planted online. Moldova's Parliament elections are scheduled for September 28.
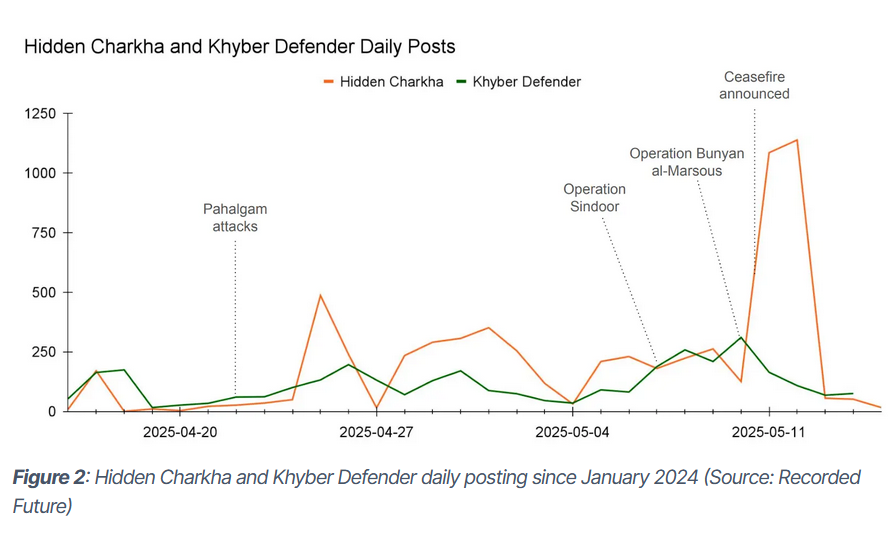
India-Pakistan IOs: A pro-Pakistan online influence operation has been linked to a local company named Team 64. The firm operates out of Pakistan's Khyber Pakhtunkhwa province. Its online activities are tracked under the codename of Khyber Defender. According to Recorded Future, the group is Pakistan's largest online influence operation. It feuded this year with a pro-Indian info-op tracked as Hidden Charkha following the India-Pakistan military conflict in April.
Vulnerabilities, security research, and bug bounty
SAP S/4HANA exploitation: A recently patched SAP S/4HANA vulnerability is being exploited in the wild. The attacks were discovered by security firm SecurityBridge last week. They target a code injection vulnerability (CVE-2025-42957) in the SAP S/4HANA enterprise resource planning platform. The bug has a severity rating of 9.9/10 and was patched last month.
Argo CD credentials leak: The Argo CD Kubernetes management platform has patched a critical vulnerability. The bug allowed Argo users with low-level API tokens to dump the credentials of any Git repository integrated in the Argo CI/CD pipeline. The bug has a similar 9.9 CVSS score.
Apple zero-day write-up: Quarkslab has published an analysis of CVE-2025-43300, the macOS/iOS zero-day that Apple patched last month, the one that was used together with a WhatsApp zero-day in a sophisticated targeted spyware attack.
Inline CSS exfiltration: PortSwigger researcher Gareth Heyes has found a way to abuse inline CSS "style" attributes to exfiltrate data using conditional statements.
Phishing training doesn't work: Another academic study found that phishing training doesn't work. Throw it on the pile of similar studies with the same results, and continue to pretend phishing training is essential. [Additional coverage in the WSJ]
University punishes student for reporting security flaw: The University of Oregon has placed a student under investigation after he reported a security flaw. Physics major Owen Mitchem reported a bug that allowed him to access the personal data of more than 3,500 university employees. Incorrect permissions in the university's Microsoft Teams server allowed Mitchem to find files uploaded to the university's SharePoint system. Mitchem was investigated and ordered to write a 750-word essay on his "actions" or have his student account suspended. [Additional coverage in OregonLive]
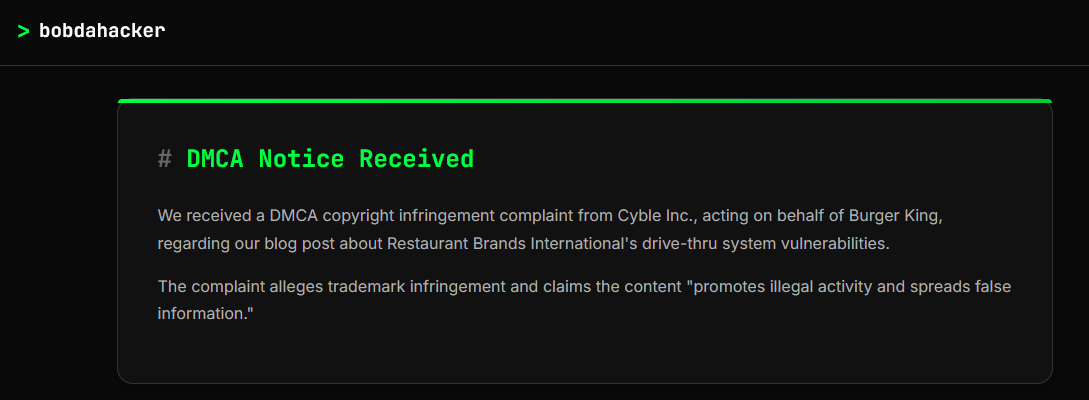
Burger King research taken down via DMCA: A report on now-patched vulnerabilities in an ordering system managed by Restaurant Brands International (Burger King's parent company) has been taken down after security firm Cyble filed a DMCA on behalf of Burger King. The DMCA claim is for using Burger King's trademark in the blog, which is as shady as shady can get in terms of a bogus DMCA. The Cyble DMCA also claims the report "promotes illegal activity and spreads false information," like we can't say the same thing about Cyble's own cybersecurity blog, which is also full of similar research. But hey! What do I know!?! The original BobDaHacker report is in the Wayback Machine here.
Infosec industry
Threat/trend reports: Apiiro, Google, ImmuniWeb, Kaspersky, and Swiss Re have recently published reports and summaries covering various threats and infosec industry trends.
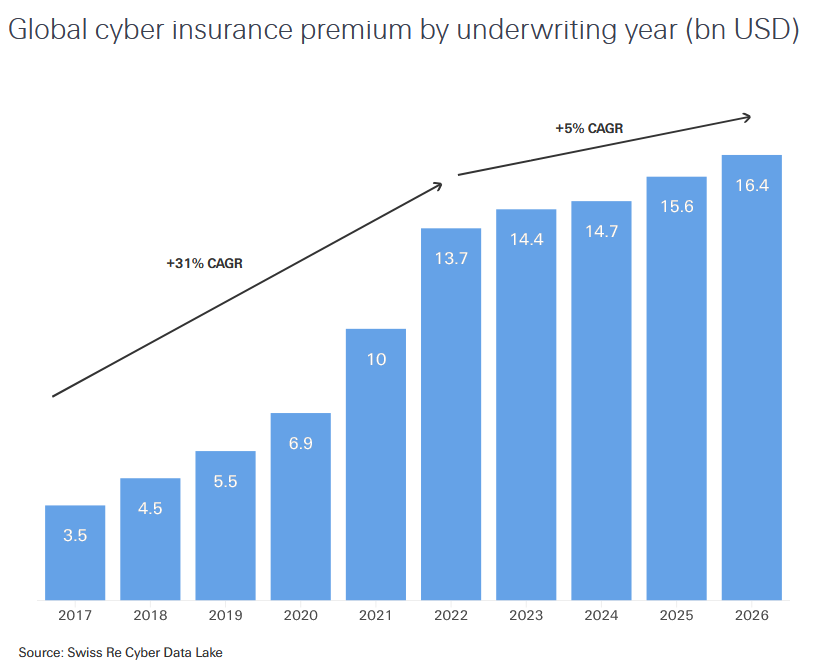
Cyber insurance rates slow: The growth of cyber insurance rates stalled for a third year in a row. Rates have remained the same due to increased competition among insurers, and as cyber coverage exceeds current demand. According to insurance provider Swiss Re, large corporations account for most coverage, while cyber insurance has failed to penetrate the small business sector. [Additional coverage in CybersecurityDive]
New tool—Salesloft Drift Breach Tracker: Nudge Security is maintaining a list of companies affected by the Salesloft incident. [h/t Brian Krebs]
New tool—Thermoptic: Security researcher Matthew Bryant has released Thermoptic, an HTTP stealth proxy that cloaks requests as the Chrome browser.
New tool—NTSleuth: Security researcher Alex Hagenah open-sourced NTSleuth, a Windows syscall extraction and analysis framework that automatically discovers, documents, and analyzes system calls across all Windows architectures.
New tool—MeetC2: Security researcher Dhiraj Mishra has released MeetC2, a serverless command & control (C2) framework that leverages Google Calendar APIs as a covert communication channel.
New tool—Orsted C2: Security researcher Haroun Al Mounayar has open-sourced Orsted C2, a new command and control framework.
New tool—DefendNot: Security firm Binary Defense has released DefendNot, a tool that "convinces" Windows to disable its own Defender protections.
New tool—tls-preloader: Limes Security researcher f0rw4rd has released tls-preloader, a library to bypass TLS certificate verification for debugging and testing. Works on OpenSSL, GnuTLS, NSS, mbedTLS, and wolfSSL.
OrangeCon 2025 streams: Live streams from the OrangeCon 2025 security conference, which took place over the weekend, are available on YouTube.
BSides Bournemouth 25 videos: Talks from the BSides Bournemouth 2025 security conference, which took place last month, are available on YouTube.
Usenix ATC 25 videos: Talks from the Usenix Annual Technical Conference 2025 security conference, which took place in July, are available on YouTube.
Risky Business podcasts
In this edition of Seriously Risky Business, Tom Uren and Amberleigh Jack talk about Google starting a cyber disruption unit. It's a sign of the times, but could also point the way forward for policymakers looking to involve the private sector in government-endorsed efforts to strike back in cyberspace.
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about how cyber threat actors are using AI tools to fill in resource and skills gaps that they have.
