Risky Bulletin Newsletter
April 11, 2025
Risky Bulletin: AI slopsquatting... it's coming!
Written by

News Editor
You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
Security firms, open-source experts, and academics are warning about a new supply chain vector they're calling slopsquatting.
The technique's name is a combination of terms like AI slop and typosquatting.
It revolves around the increasing use of AI coding tools to generate blocks of source code that may sometimes make their way into production systems.
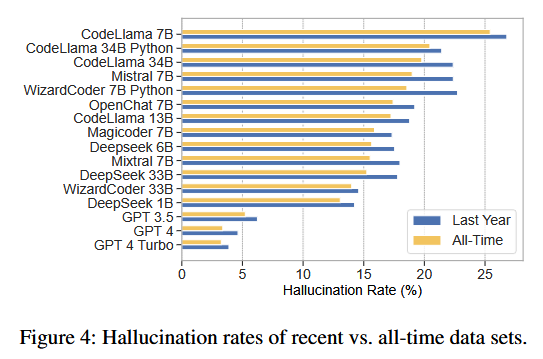
A recent academic paper that analyzed 16 AI coding models found that these tools generate shoddy code that often includes and loads packages and libraries that don't exist.
"Our findings reveal hat that the average percentage of hallucinated packages is at least 5.2% for commercial models and 21.7% for open-source models, including a staggering 205,474 unique examples of hallucinated package names, further underscoring the severity and pervasiveness of this threat."
DevSecOps company Socket Security says that such behavior opens the door to slopsquatting—where threat actors study the LLMs and then register package names hallucinated or likely to be hallucinated in the future.
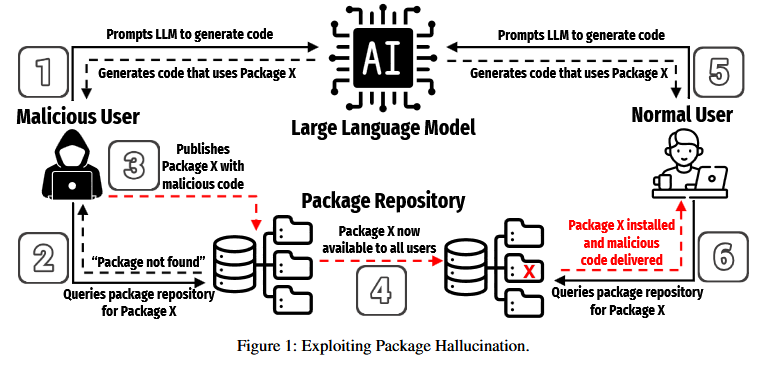
The attack looks farcical and impractical, but so did typosquatting when it was first described years ago. Yet, years later, it is one of the most pervasive and common sources of supply chain issues in the software development industry.
It sounds ridiculous that developers wouldn't spot a typo in the names of packages they install, but reality has shown they don't. Does it actually sound that far off that developers wouldn't spot non-existent packages in huge blocks of code they're using when cutting corners?
The use of AI coding tools is increasing, and the chances that developers may use code blocks generated through these tools are also growing exponentially, along with the chances of a successful slopsquatting attack.
Risky Business Podcasts
Risky Business is now on YouTube with video versions of our main podcasts. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
Moroccan government leaks: Algerian hacker group JabaRoot DZ has leaked data from two Moroccan government agencies—the Ministry of Economic Inclusion and the National Social Security Fund (CNSS). [Additional coverage in Yabiladi]
Dutch government breach: The Dutch government is investigating a data breach of three ministries. The incident is impacting the Ministry of the Interior, the Ministry of Economic Affairs, and the Ministry of Climate and Green Growth. The government has not disclosed the nature of the incident. [Additional coverage in BNR]
NetJets breach: Hackers have breached and stolen customer information from private business jet company NetJets. The hack took place last month after the attacker phished an employee. The company says only a "very small number of owners" were impacted. NetJets is owned by Warren Buffett's Berkshire Hathaway company. [Additional coverage in Bloomberg]
DGO hack: German intelligence is probing a suspected Russian hack of the German Association for East European Studies (DGO). [Additional coverage in DW]
Sensata ransomware attack: Industrial sensor maker Sensata has disclosed a major ransomware attack that has impacted operations, such as "shipping, receiving, manufacturing production, and various other support functions."
GenNomis leak: A South Korean AI nudify and face-swapping service has left a database exposed on the internet without a password. The database contained over 93,000 images generated through the service. According to the researcher who found it, the database allegedly belonged to a company named GenNomis by AI-NOMIS and contained pornographic images, including of "very young people."
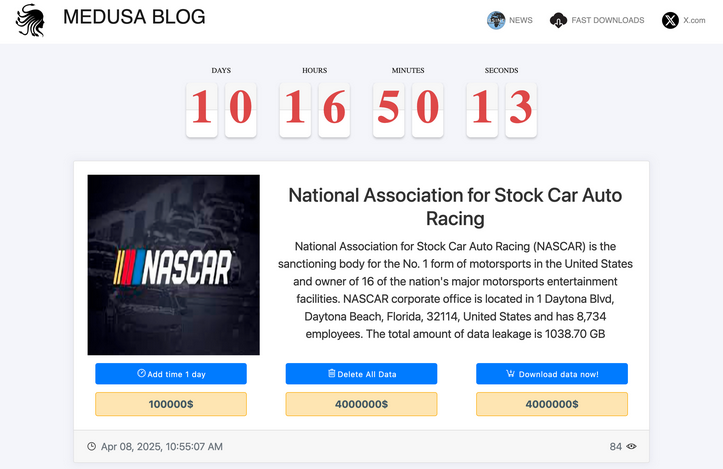
NASCAR cyber incident claim: The Medusa ransomware gang claims to have hacked NASCAR. The organization has not confirmed anything yet.
General tech and privacy
OpenSSH removes DSA: OpenSSH 10 has removed support for the DSA signature algorithm almost 10 years after it started the deprecation process.
Firefox CSP protections: The Firefox security team has published a blog post on the browser's UI CSP hardening efforts.
Google Unified Security: Google has launched Unified Security, a new AI-powered platform that unifies all its cybersecurity offerings under one umbrella. This includes security operations, cloud security, threat intelligence, secure enterprise browsing, and Mandiant expertise.
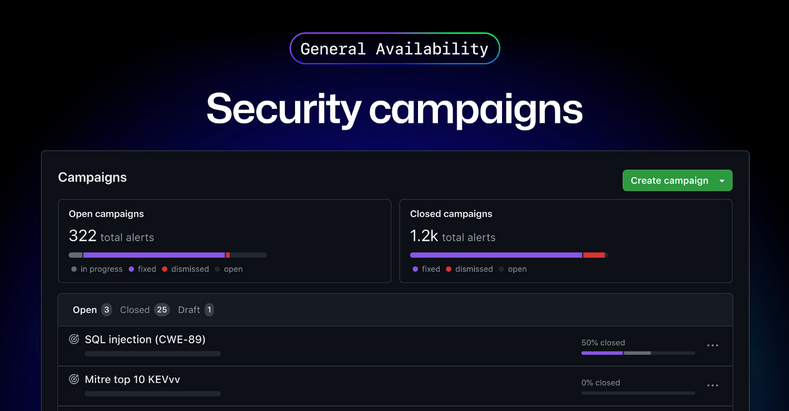
GitHub Security Campaigns: GitHub has released a new security feature named Security Campaigns that can allow organizations to fix security alerts at scale across projects.
Government, politics, and policy
Trump orders probe of Chris Krebs: US President Donald Trump has revoked security clearance and ordered an investigation of former CISA Director Chris Krebs. Trump accused Krebs of censorship over CISA's anti-misinformation work and for countering the president's claims that the 2020 election was stolen. He also suspended security clearances for the staff of cybersecurity firm SentinelOne, Krebs' current employer. The company said that only 10 employees are impacted.
Trump signed a memo going after Chris Krebs. Krebs in 2020 pushed back against Trump’s claims that the election had been fraudulent and was adamant that the nation’s elections were not compromised. He did a wonderful job. The president, he’s evil.
— Gen Michael Hayden (@genmhayden.bsky.social) 2025-04-09T23:21:39.130Z
US disbands DOJ crypto crime team: The US Department of Justice is disbanding its National Cryptocurrency Enforcement Team. The team was established in 2022 and focused on the illicit use of cryptocurrencies. Its most important case targeted Binance and its founder, resulting in a $4.3 billion settlement. The DOJ told the team to close all ongoing cases and told its staff to focus future crypto investigations on the crypto use among terrorist groups and drug cartels only. [Additional coverage in CNBC]
Wyden blocks CISA nominee: US Senator Ron Wyden has placed a hold on the nomination of Sean Plankey for CISA director. Senator Wyden plans to block the nomination until CISA releases a 2022 report on the security of US telcos. Wyden says the report is unclassified, but CISA has repeatedly refused to release it over the years. He believes the report exposes major security lapses in the networks of US telcos, some of which might have been exploited by Chinese hackers last year.
NSO hires new lobby team: Israeli spyware maker NSO Group has hired a new lobby team to petition the White House and have its sanctions lifted. According to WIRED, the new team has ties to the Republican party and the Trump administration. The NSO previously sunk $1.8 million into a pre-election lobbying effort that targeted Texas lawmakers ahead of last year's US elections. The Biden administration added NSO to the US Commerce Department entity list in 2022. The sanctions prevent any US company and government agency from working with the Israeli company.
CIS to cover MS-ISAC's cut funding: The Center for Internet Security non-profit will provide temporary funding for the Multi-State Information Sharing & Analysis Center, also known as MS-ISAC. CIS has been running MS-ISAC since it was established in 2004 using DHS funding, which the US government cut in February. MS-ISAC has over 18,000 members. Its main role is to share information on emerging cyber threats and vulnerabilities with small and underfunded local governments. It's unclear for how much time CIS will be able to foot the bill for MS-ISAC's operations. [Additional coverage in StateScoop]
UK government breach survey: A survey commissioned by the UK government has found that the number of breaches in 2024 has declined compared to previous years.
"This decline is primarily attributed to fewer micro and small businesses reporting phishing attacks. Prevalence of cyber breaches and attacks remains high among medium and large businesses. For charities, the prevalence has remained stable since 2024, with an estimated 61,000 charities experiencing cyber breaches and attacks over the last 12 months."
Russia warns against foreign encryption: Roskomnadzor, Russia's internet watchdog, has warned companies that use VPN protocols to avoid using "foreign" encryption protocols to protect their traffic. Companies that need to do so were told to contact the agency to have their VPN IPs added to a whitelist. [Additional coverage in Interfax]
Risky Business podcasts
Tom Uren and Patrick Gray discuss Trump's recent firing of General Timothy Haugh, the head of NSA and Cyber Command. Tom dives into the implications and thinks why this is not good news for the agencies.
Arrests, cybercrime, and threat intel
Europol detains "Superstar" members: European law enforcement has detained five suspects linked to the Superstar pay-per-install cybercrime service. The service allowed other cybercrime groups to install their own malware on systems that were previously infected with the Smokeloader malware. Europol says it discovered the service and its operators after it analyzed data seized from the Smokeloader botnet in May of last year.
NSO's WhatsApp hacking scope finally revealed: NSO Group deployed a WhatsApp exploit against 1,223 user accounts as part of its 2019 hacking spree, according to new documents unsealed in Meta's lawsuit against the Israeli spyware vendor. A third of all victims were located in Mexico, followed by victims in India and Bahrain. NSO customers deployed the WhatsApp exploit in 51 different countries, including many Western states, such as the UK, the US, Spain, and the Netherlands. The court documents also reveal that NSO cut off 10 government customers from its platform after reports of abuse and improper use. [Additional coverage in TechCrunch]
More npm malware (sigh): ReversingLabs has identified another npm package that patches local software to hijack cryptocurrency transfers.
Smishing Triad's new phishing kit: SilentPush has published a profile of Chinese cybercrime group Smishing Triad. The group is massive, with operations across 121 countries. The report also looks at the group's new phishing kit, named Lighthouse, which was designed specifically for banking-related smishing ops.
Atlas Lion profile: Security firm Expel looks at a Moroccan cybercrime group named Atlas Lion that targets organizations issuing gift cards.
Toll road smishing: Cisco Talos has published a threat report on the rising trend of SMS toll road payment phishing scams that are currently hitting the US. It's hitting other places, too, but the US and UK seem to be the main focus of most campaigns these days.
AkiraBot spam service: SentinelOne has discovered an underground cybercrime service that abuses OpenAI tools to bypass CAPTCHAs and post spam inside open web forms. Named AkiraBot, the service has posted spam on over 80,000 websites since its launch in September. Its primary use is for posting SEO spam via comment fields.
Malware technical reports
Tycoon 2FA: Trustwave has published a report looking at the new evasion techniques used by the Tycoon 2FA PhaaS in recent operations.
ViperSoftX: AhnSec researchers look at a malspam campaign distributing the ViperSoftX to Arabic-speaking users.
SpyNote: DomainTools' security team has discovered new domains involved in distributing the SpyNote RAT for Android.
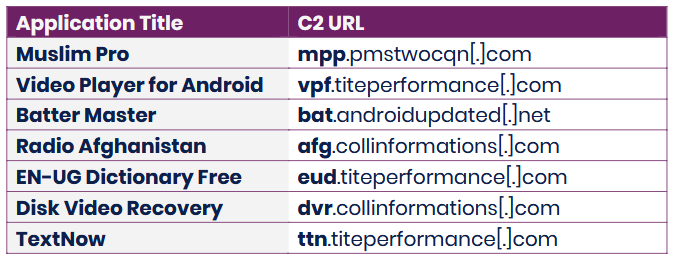
BADBAZAAR and MOONSHINE: Cybersecurity agencies from Germany and the Five Eyes alliance have released joint technical reports on BADBAZAAR and MOONSHINE, two pieces of Android spyware used by Chinese state-sponsored hackers against Uyghur, Tibetan and Taiwanese communities.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq look at the idea of 'false scarcities' in cyber security. Are bugs and talent rare? Or is our thinking blinkered?
APTs, cyber-espionage, and info-ops
Sapphire Werewolf: BI.ZONE has published a new report on the Sapphire Werewolf and its use of the Amethyst stealer in new operations. These campaigns started back in June last year.
GOFFEE APT: Kaspersky has spotted new campaigns from a suspected Chinese APT named GOFFEE, which the company first saw targeting Russia back in 2022.
SideCopy: Seqrite Labs has published new TTPs used by Pakistan APT group SideCopy in December 2024 campaigns.
"The group has expanded its scope of targeting beyond Indian government, defence, maritime sectors, and university students to now include entities under railway, oil & gas, and external affairs ministries. One notable shift in recent campaigns is the transition from using HTML Application (HTA) files to adopting Microsoft Installer (MSI) packages as a primary staging mechanism."
APT-Q-12 (DarkHotel): QiAnXin has spotted the APT-Q-12 group deploy a one-click vulnerability in the Tencent Foxmail service to steal inbox content from their targets.
DPRK hackers on npm, again: You've probably heard this before, but North Korean hackers are uploading malware to npm. Just like most previous cases, the packages target crypto-related tools and contain malware dedicated to stealing crypto-related files and passwords.
Shuckworm (Gamaredon): Russian APT Shuckworm has hacked a military mission of a Western country sent to Ukraine. The source of the infection was an infected removable drive.
Russian anti-EU disinfo in Bulgaria: A giant disinformation wave has hit Bulgaria this month and almost created a mass panic, claiming that the EU would confiscate private savings if owners didn't spend the funds in the next six months. The campaign was linked to pro-Russian and Eurosceptic accounts and local political figures. [Additional coverage in Novinite]
Yemeni/Houthi influence campaign: Israeli security firm ClearSky has discovered a Yemeni/Houthi influence campaign operating in Israel and the Gulf states. The campaign has been active since 2019 and only switched to targeting Israeli audiences last year. ClearSky says the network mainly posts about gossip but could be easily converted to sharing fear-inducing messages or malicious content.
Vulnerabilities, security research, and bug bounty
Gladinet CentreStack exploitation: Threat actors are exploiting a zero-day vulnerability to take over Gladinet CentreStack secure file-sharing servers. Attackers are using a hardcoded cryptographic key to carry out deserialization attacks and run malicious code on vulnerable systems. Gladinet released a patch last week after initial attacks last month. Customers who can't install the patch are advised to change the hardcoded key. [More in the Gladinet advisory/PDF]
AWS EC2 exploitation: Hackers are using SSRF vulnerabilities to target AWS EC2 servers to find and steal server metadata. The goal of the attacks is to find IAM credentials in the metadata and take over a larger chunk of the victim's infrastructure. F5 Networks says most of the attacks took place over the course of ten days last month.
Jenkins security update: Jenkins has released a security update to remove an incident of SSH host key reuse.
Juniper security updates: Juniper has released security updates for dozens of vulnerabilities across multiple products.
Shopware SQLi: Older versions of the Shopware platform will need to install a security plugin to protect themselves against a new SQL injection vulnerability (CVE-2025-27892) patched in recent versions.
SuperNote tablet 0-click RCE: PRIZM Labs has discovered a zero-click remote code execution vulnerability (CVE-2025-32409) in Ratta SuperNote A6 X2 Nomad e-ink tablets that can allow remote attackers to backdoor its firmware.
NVIDIA incomplete patch: Trend Micro says that an NVIDIA September 2024 security update for the NVIDIA Container Toolkit was incomplete and still leaves servers exposed to container escapes.
Langflow vulnerability: Horizon3 has found a code injection vulnerability in Langflow, a popular tool used for building agentic AI workflows.
Tracked as CVE-2025-3248, the vulnerability can allow unauthenticated, remote attackers to compromise Langflow servers.
NTLM relay attack overview: SpecterOps has published an overview of modern-day NTLM relay attacks and their limitations.
RemoteMonologue: The IBM X-Force Red red team has published details about RemoteMonologue, a Windows credential harvesting technique that enables remote user compromise by leveraging the Interactive User RunAs key and coercing NTLM authentications via DCOM. A PoC is available on GitHub.
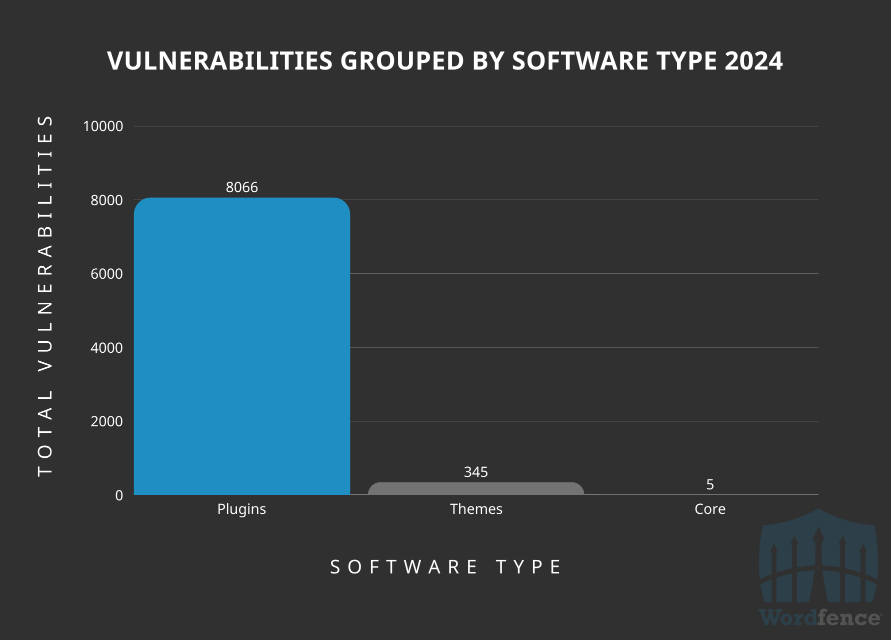
A quarter of WP vulnerabilities remain unpatched: Security researchers disclosed over 8,000 WordPress vulnerabilities last year, but over a quarter have not received a security patch. According to the Wordfence yearly WordPress security report, over 96% of all these bugs impact plugins, which are now the number one threat for WordPress site owners. Only 5 of the 8,000 issues disclosed last year impacted the WordPress core, which shows how much the CMS has advanced in terms of security hardening.
Infosec industry
New tool—YES3 Scanner: Fog Security has released YES3 Scanner, a tool to scan AWS accounts for potential S3 security issues.
Threat/trend reports: Forescout, ReliaQuest, Vodafone UK, UK DSIT, WilmerHale, and Wordfence have recently published reports and summaries covering various infosec trends and industry threats.