Risky Bulletin Newsletter
October 25, 2024
Risky Biz News: US offers reward for suspected Tortoiseshell APT members
Written by

News Editor
This newsletter is brought to you by Okta. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
The US government is offering a $10 million reward for information on four members of an Iranian hacking group named Shahid Hemmat.
The group allegedly "works" for Iran's Islamic Revolutionary Guard Corps Cyber-Electronic Command (IRGC-CEC), an agency inside the Iranian armed forces that specializes in cyber operations.
US officials say the four—Manuchehr Akbari, Amir Hosein Hoseini, Mohammad Hosein Moradi, and Mohammad Reza Rafatinezhad—conducted cyber and intelligence operations that targeted US critical infrastructure.

Two of the four—Akbari and Moradi—have been doxed and linked by LabDookhtegan, a known leaker of Iranian government documents, to an APT group known as Tortoiseshell, Yellow Liderc, Imperial Kitten, TA456, and Crimson Sandstorm.
The same LabDookhtegan claims the four, and others, are employees of a private company named Dadeh Afzar Arman (DAA).
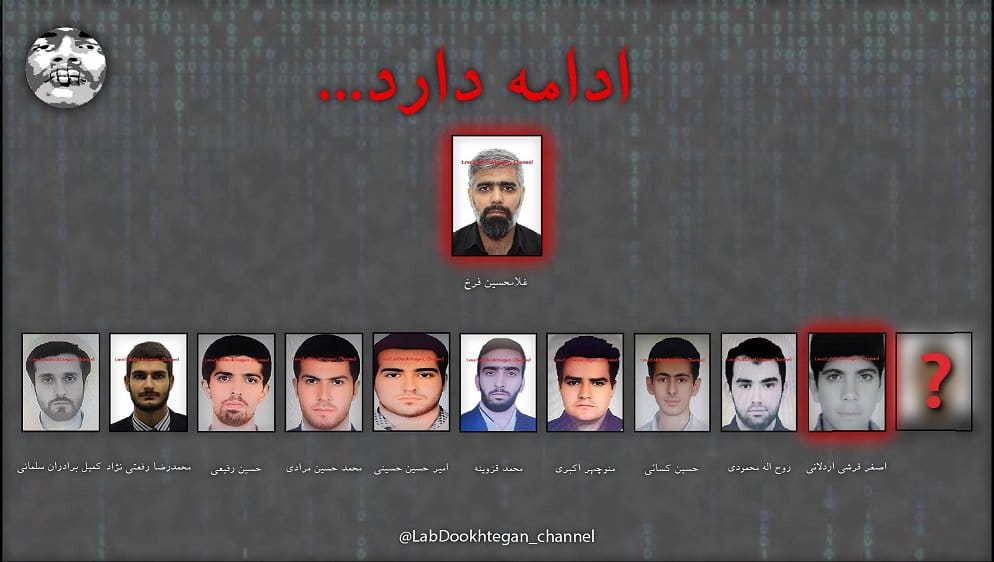
The US Treasury Department sanctioned DAA in April for being one of two IRGC-CEC front companies.
Treasury officials didn't say anything about the company at the time, but they formally linked the other front company they sanctioned to Tortoiseshell APT attacks—so, at this point, it's pretty clear who's behind Tortoiseshell.
In total, the US has now exposed 14 of the IRGC-CEC's hackers.
Besides the four listed on the rewards poster this week, the April sanctions also named four IRGC-CEC hackers. The four were also charged by the Justice Department (the photo below shows only three of them).

In addition, the State Department also named six other IRGC-CEC hackers in August, when it offered a $10 million reward for information on the six, which it claimed were behind the Cyber Av3ngers group and its attacks on US water systems.

Breaches, hacks, and security incidents
Infostealer leaks: Cybercriminals have leaked almost 6.8 billion records via misconfigured command and control servers over the past two months. Most of the data appears to originate from infostealer servers. The leaks were discovered by Bob Diachenko, a security researcher specialized in finding exposed infrastructure.
Polyfill incident: Security firm Silent Push has published a report on the Polyfill supply-chain attack from earlier this year. According to the company, the code added to the Polyfill library was intended to redirect visitors to Chinese gambling sites.
ESET Israel wiper incident: Israeli media claims that an ESET representative in Israel has linked the company's recent wiper incident to the Handala Hack pro-Palestinian (actually Iranian) group.
Georgia absentee voter website DDoS attack: Officials from the US state of Georgia say they've repelled a DDoS attack that targeted the state's absentee voter website. The incident took place last week, and officials have yet to identify the attackers. Officials say the website is now up and running normally. [Additional coverage in CBS]
Cosmos DPRK incident: The creator of the Cosmos blockchain has admitted that the company inadvertently hired a North Korean IT worker. The company says the FBI notified the project about the North Korean worker, but the individual who received the notification did not report the incident to his managers. Cosmos says code contributed by the North Korean worker contained at least one major vulnerability. The company is now performing a security audit to review the code for other issues. [Additional coverage in Rekt News]
ZachXBT profile: WIRED has published a profile on ZachXBT, an individual who has helped companies track and recover billions worth of crypto-assets stolen in hacks over the past years.
General tech and privacy
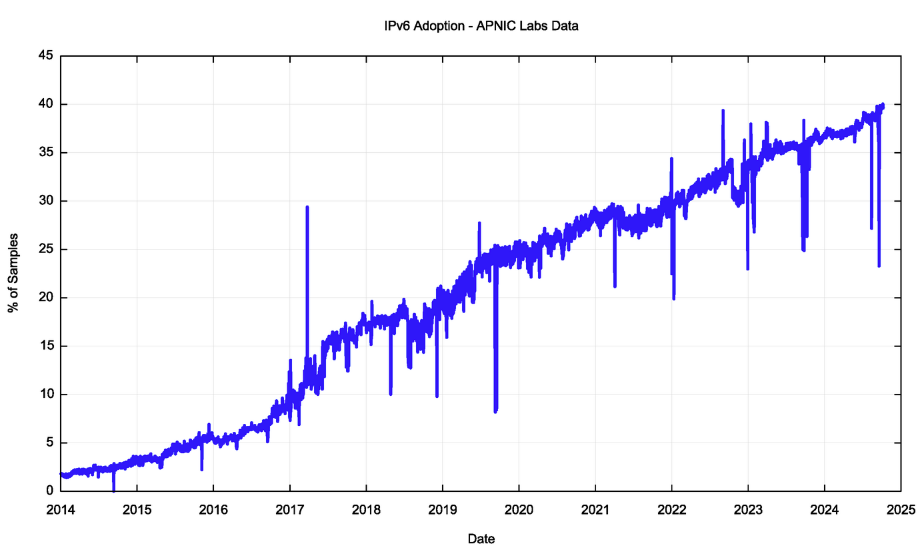
IPv6 adoption: APNIC says that 25 years after IPv6 was released, adoption has slowly crawled to a 40% adoption rate. This must be the most painful and slowest standard transition ever at this point. The article is a good read because it argues that IPv6 may not be as critical as we thought.
LocateX profile: Brian Krebs and 404 Media have published a profile on LocateX, a platform that allows customers to track individual mobile users by their Mobile Advertising ID. It's quite a long and convoluted story, mainly because the online advertising business is a giant mesh of data resellers. Good luck to the US government enforcing a ban on sensitive data sales against this mess of shell companies.
Telcos sue to block click-to-cancel rule: A US telco industry group has sued the FTC to block its new click-to-cancel rule. Before you ask, yes, the lawsuit was filed in the 5th US Circuit Court of Appeals, the home of every big corp-loving judge. [Additional coverage in Reuters]
Pinterest complaint: European privacy group noyb has filed a complaint against Pinterest over the company's failure to ask for user consent before tracking them. Seems like a slam dunk fine!
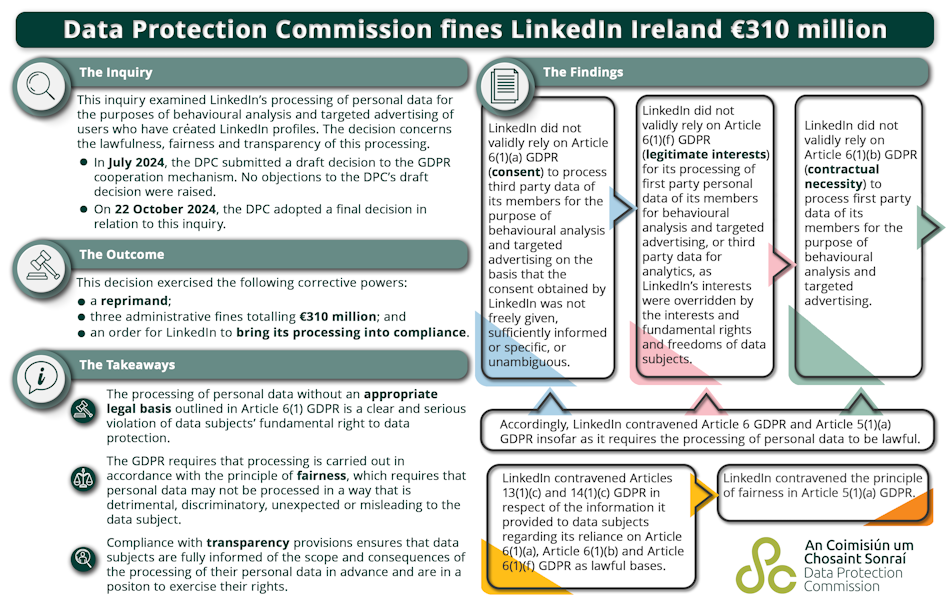
Ireland fines LinkedIn over targeted ads: The Irish data protection agency has fined LinkedIn €310 million for breaking the EU GDPR and abusing user data for targeted advertising. The agency has ordered LinkedIn to bring its business practices into compliance or face another fine. The fine is for a 2018 complaint made in France by digital rights non-profit La Quadrature Du Net. In a statement, LinkedIn claimed innocence but promised to become compliant by the agency's deadline.
WhatsApp to encrypt contact lists: The WhatsApp messaging app has added a new feature to encrypt a user's contact list. The new feature uses Meta's Identity Proof Linked Storage (IPLS) protocol to store a user's contact list inside an encrypted storage system only accessible through the WhatsApp application. The system prevents third-party apps from reading contacts but still allows Meta to sync address books between devices.
iOS nude reporting feature: Apple has added a new feature to iMessage that will allow children to report nude images and videos they receive via the app. The reports will go to Apple, which will then decide if it needs to contact law enforcement. The new feature is currently being tested in Australia with iOS beta releases. [Additional coverage in The Guardian]
Linux removes Russian maintainers: The Linux kernel project has removed 11 Russian developers from the project's list of official maintainers. The project has not provided an explanation for the removal besides a vague statement that the developers did not meet "compliance requirements." The 11 developers were maintainers of various Linux kernel drivers. [Additional coverage in Phoronix]
Huawei launches HarmonyOS NEXT: Chinese phone maker Huawei has launched HarmonyOS NEXT, the OS' first version not based on Android.
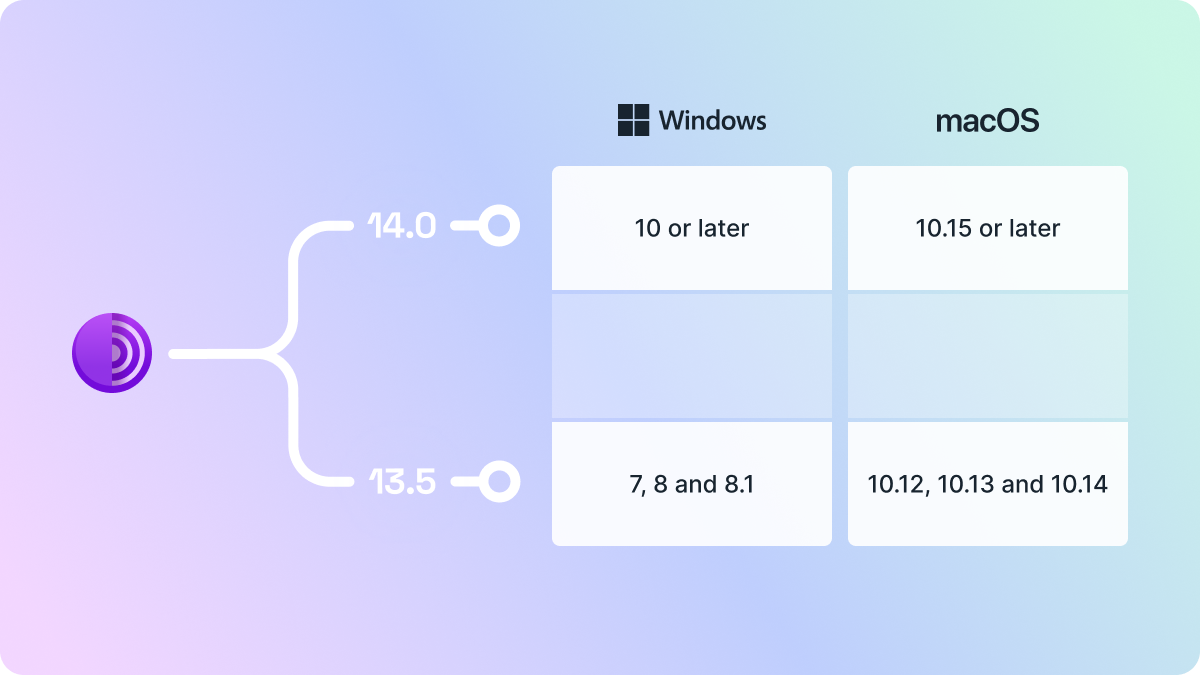
Tor Browser 14: The Tor Project has released v14 of its Tor Browser. With this edition, Tor devs have dropped support for Windows 7 and older macOS versions.
Government, politics, and policy
TLP in the government: The White House has encouraged government agencies to adopt the Traffic Light Protocol (TLP) when sharing sensitive cybersecurity data and reports, such as those from security researchers.
New software dev guide: CISA and its international partners have published a new guide to help software vendors establish secure software deployment processes.
Russia to limit the collection of personal data: After spending years telling everyone how the EU is bad and a failed organization, Russia's internet watchdog is slowly reaching the conclusion that it needs to limit the collection of personal data to protect the privacy of its citizens. The EU GDPR says "hi!" hypocrites! [Additional coverage in the RBC]
Telegram's role in the Moldovan vote-buying scandal: More details are coming forward on how Telegram bots were being used by the pro-Russian side in the recent Moldovan election to sign up users for Russian bank accounts and receive money for their votes. Moldovan authorities estimate that Russia has channeled $39 million in September and October alone for the vote-buying scheme. Moldovan officials estimate that roughly 300,000 locals signed up and sold their votes. To Telegram's credit, the platform took down the bots at the request of Moldovan authorities a week before the election. [Additional coverage in Reuters]
UK Data Use and Access Bill: The UK government has introduced the Data Use and Access Bill, a new attempt to revamp the country's privacy laws.
Ukraine considers military cyber branch: The Ukrainian government is considering adding a separate cyber branch to its military forces. The proposal came directly from the country's General Staff of the Armed Forces. Officials cited the success of an informal group of cybersecurity experts known as the IT Army of Ukraine and their role in offensive operations. If approved, Ukraine would join the ranks of China and Indonesia, which recently also created separate cyber branches inside their armed forces. Germany is also considering a similar measure. [Additional coverage in the Kyiv Independent]
Sponsor section
In this Risky Business News sponsored interview, Tom Uren talks to Brett Winterford, Okta's APAC Chief Security Officer. Brett has mined Okta's data and finds strong evidence that organizations invest in phishing-resistant authentication methods once they know they've been targeted by groups that excel at social engineering (such as Scattered Spider). Brett discussed this research at Okta's conference, Oktane, which was held in Las Vegas from 15 to 17 October 2024.

Cybercrime and threat intel
Telegram data traders arrested: Dutch authorities have detained four suspects for buying and selling stolen data. The suspects ran Telegram channels that bought and sold hacked data. Dutch police seized devices and left messages in the Telegram channels warning that trading hacked data is illegal and traders will be prosecuted.
Email security is hard: Red Sift says that nearly 75% of US Senate campaign websites do not support DMARC.
Webflow abuse: Netskope has seen a tenfold increase in phishing campaigns abusing the Webflow website builder to host phishing pages. The vast majority of campaigns mimicked popular crypto wallet solutions, such as Coinbase, MetaMask, and Trezor. Some campaigns also targeted popular webmail platforms and Microsoft 365 accounts. The campaigns have targeted more than 120 organizations worldwide, with the majority located in North America and Asia.
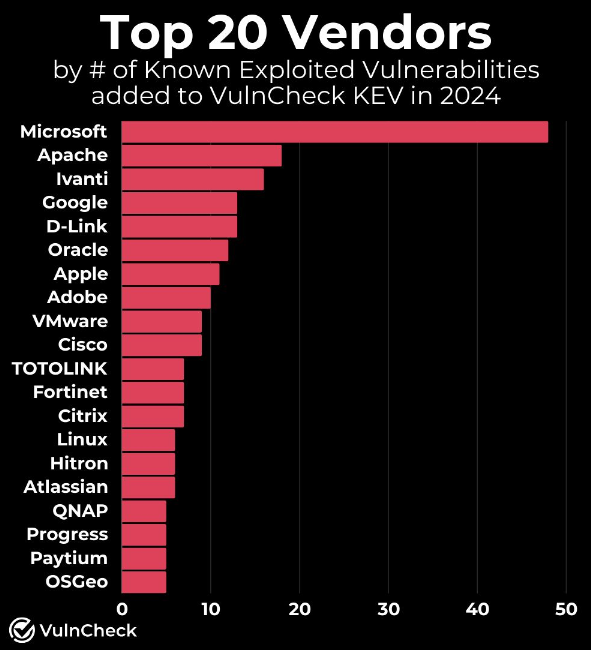
Top exploited vendors in 2024: Congratulations to Microsoft for being the top exploited vendor this year, based on CISA KEV entries. [via VulnCheck]
Malware technical reports
WarmCookie: Cisco Talos has published a report on WarmCookie (aka BadSpace), a new backdoor first spotted back in April that is currently being distributed via malspam and malvertising campaigns. The malware appears to be used to sell access to infected systems to other threat actors—with at least one of them being a state-sponsored espionage campaign.
HookBot: Netcraft looks at the HookBot Android banking trojan and its complex overlay credentials phishing system.
DarkComet RAT: ANY.RUN's Mostafa ElSheimy has published a technical analysis of the DarkCommet remote access trojan.
Embargo ransomware: ESET has published a report on Embargo, a new ransomware group that was first spotted in June. The report covers the group's Rust-based ransomware, its new MDeployer loader, and the MS4Killer EDR-silencing toolkit.
Qilin ransomware: Halycon researchers published a report on the Qilin RaaS, also known as the Agenda ransomware. The report covers the ransomware's new encryption algorithms and defense evasion tactics.
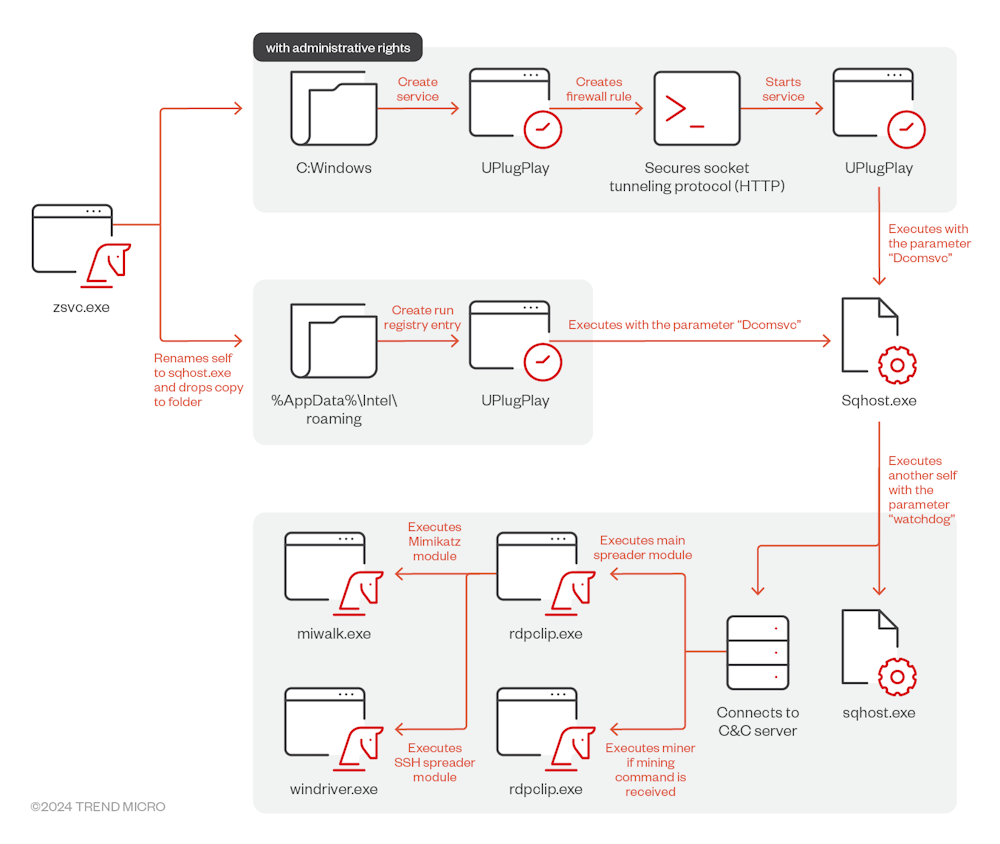
Prometei: Trend Micro has published an analysis of Prometei, a crypto-mining botnet that's been around since as far back as 2016. A recent version released in 2022 also integrated credentials-theft capabilities. By early 2023, the botnet seemed to have infected over 10,000 systems across the globe.
Sponsor Section
In this sponsored product demo, Okta's Harish Chakravarthy and Brett Winterford walk through four new features Okta introduced in the wake of the emergence of modern attacker techniques targeting identity providers. These features will help you to prevent or limit the damage to your environment if an attacker manages to compromise a session token.
APTs, cyber-espionage, and info-ops
Lazarus npm attack: eSentire researchers look at a malicious npm package they linked to the Lazarus group that tried to infect victims with the BeaverTrail backdoor. The package targeted crypto-developers.
Tenacious Pungsan: On the same note, DataDog seems to have looked at the same campaign, which they have linked to a group it tracks as Tenacious Pungsan.
Lazarus: ThreatBook has also published a report on a Lazarus campaign. This one used malicious Python libraries to target crypto developers. Honestly, if you work in the crypto space, you must know by now at least three Lazarus hackers by their birth name, or your project most likely suck.
Lazarus Chrome zero-day attack: North Korean hackers have used a fake tank game to deploy a Chrome zero-day against individuals in the cryptocurrency space. The attack took place in May this year and targeted a crypto-expert based in Russia. Kaspersky researchers linked the attack to a North Korean group known as Lazarus. The group is known to target members of the crypto space to steal credentials and orchestrate hacks against their employers. The zero-day (CVE-2024-4947) was patched in May, days after the Kaspersky report.
Suspected MuddyWater campaign in Armenia: A security researcher going by k3yp0d has published an analysis of a spear-phishing campaign targeting Armenia. The campaign is believed to be the work of an Iranian APT group named MuddyWater.
Georgia raids home of Atlantic Council disinfo researchers: Authorities from the country of Georgia have raided the homes of two Atlantic Council disinformation researchers. The raids took place a day after the two researchers published an article about Russia's efforts to influence the Georgian elections this weekend. Authorities searched the homes of Eto Buziashvili and Sopo Gelava and seized devices from them and their family members. Georgia is currently run by a pro-Kremlin party named the Georgia Dream. [Additional coverage in The Record]
Amazon seizes APT29 domains: Amazon has seized domains that mimicked the AWS cloud service and were being used by a Russian espionage group to target Ukrainian organizations. The company linked the domains to APT29, a cyber unit inside Russia's SVR Foreign Intelligence Service. The attacks were initially detected by Ukraine CERT. The agency says they targeted Ukrainian state authorities and its military-industrial base with a phishing campaign that used "zero trust" as a lure to deploy malware on their systems. Ukraine CERT tracked the attacks under a threat actor name UAC-0215.
UAC-0218: The same CERT-UA has also published a report on UAC-0218, a group behind another spear-phishing campaign targeting Ukrainian users with fake bills.
TA866 (Asylum Ambuscade): Cisco Talos looks at TA866, a suspected Russian financially-motivated threat actor that appears to have turned to espionage after Russia's invasion of Ukraine. The group is also known as Asylum Ambuscade and was previously seen targeting organizations that deal with Ukrainian refugees.
Dougan profile: The Washington Post has published a profile on John Mark Dougan, a former US Marines and Florida sheriff who fled to Russia while being under investigation in the US and is now working with the Russian military intelligence service on disinfo and influence campaigns targeting the Harris-Walz campaign. According to documents, he's allegedly working for/with GRU Unit 29155 and has become one of Russia's most prolific propagandists.
BRICS info-ops: Meduza reporters claim to have received a media guideline intended for Russian state news agencies and online propagandists. The document instructs state news agencies and disinfo farms to push "anti-dollar BRICS payment system and push US election conspiracy theories" while covering the current BRICS forum taking place in Kazan, Russia. Some of the talking points include:
- Vladimir Putin is the "informal leader of the global majority."
- The elites in Western countries are "panicking."
- The West as a whole is "racked with anxiety."
Pre- and post-election info-ops: The US government warns that Russia and Iran might use disinformation campaigns to stoke violence in the US during and after Election Day. Officials warn that Russia and Iran will focus on calling into question the election process as a way to attack democracy as a valid political system. Opposed to Russia and Iran, Microsoft says that China has only focused on attacking candidates with an anti-Chinese agenda. Microsoft says that current Iran disinformation efforts are calling on Americans to boycott candidates that support Israel, and Russia is focused on attacking the Harris camp with deepfake videos.
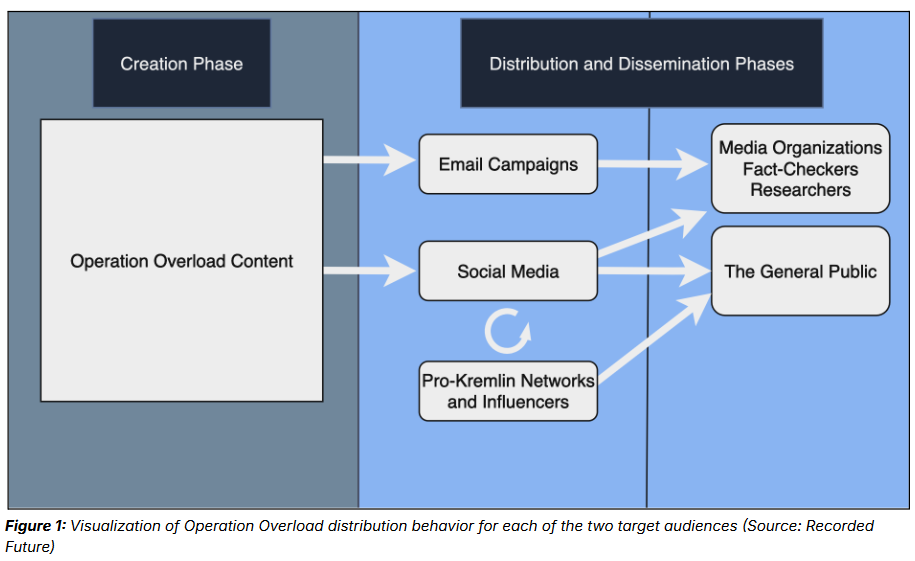
Operation Overload: And speaking of Russian disinfo groups meddling in the US election, Recorded Future has published a report on Operation Overload (aka Matryoshka, Storm-1679). The group impersonates Western news media outlets and uses AI to generate large quantities of low-quality propaganda. Recorded Future believes the group is trying to overwhelm fact-checkers and journalists with garbage content in the hopes some narratives slip into mainstream media coverage unchecked. Recorded Future says that prior to targeting the US election, the same group targeted the French elections and the Paris Olympics.
Vulnerabilities, security research, and bug bounty
Another Fortinet zero-day: Network equipment vendor Fortinet says that threat actors are exploiting a new zero-day in FortiManager, a server system that allows companies to manage their FortiGate firewalls from a central location. Fortinet has confirmed the zero-day after reports of active attacks leaked on Reddit last week. Tracked as CVE-2024-47575, the zero-day allowed attackers to mimic FortiGate firewalls and run malicious commands on the FortiManager server. According to security researcher Kevin Beaumont, a state-sponsored group is behind the zero-day. The exploits allegedly targeted some managed service providers, from where the attackers pivoted to all the MSP's customers. Google's Mandiant division says the zero-day has been exploited in the wild since June by a group the company tracks as UNC5820. According to Censys, there are currently over 4,000 FortiManager admin portals exposed online, with about 30% of those in the US. As ArsTechnica points out, Fortinet has a history of silently patching critical vulnerabilities and disclosing them only after they're widely exploited.
SharePoint exploitation: CISA says that threat actors have now weaponized and are exploiting a recent vulnerability in the Microsoft SharePoint server. Tracked as CVE-2024-38094, the vulnerability allows for remote code execution and was patched in July. Security researcher Nguyen Jang published proof-of-concept code for the bug a week after the patch.
Unpatched Vesta bug: FortBridge researchers have found a vulnerability in the password reset process for Vesta, a popular web hosting panel. The bug can be used to take over admin accounts. The vendor did not respond to researchers when they reported the bug.
More AWS CDK: Aqua Security has discovered more vulnerabilities in the AWS Cloud Development Kit (CDK). The new bugs are a continuation of the company's Bucket Monopoly research from August. The new bug allows an attacker to gain administrative access to a target AWS account.
Xerox printers RCE: The vulnerability (CVE-2024-6333) allows an attacker with credentials for the printer's web panel to fully compromise the device and gain root privilege over the printer. Affected models include the likes of Xerox EC80xx, AltaLink, VersaLink, and WorkCentre. The company released security updates [PDF] for affected models last week.
Cisco zero-day and security updates: Cisco has released 36 security updates for its products, including a patch for an actively exploited zero-day in ASA and FTD firewalls. Tracked as CVE-2024-20481, the zero-day has been used to crash Cisco firewalls using a large number of VPN authentication requests. Cisco says the zero-day was being used as part of password spray attacks. The company's security updates also patched three issues marked as critical, such as a remote command injection in the ASA SSH client, hardcoded credentials in Firepower firewalls, and a command injection in the Cisco firewall management center. All three issues were discovered internally and are not under active exploitation.
Deceptive Delight: PAN's Unit42 has published details on Deceptive Delight, a new technique for jailbreaking large language models (LLMs).
"We tested this simple yet effective method in 8,000 cases across eight models. We found that it achieves an average attack success rate of 65% within just three interaction turns with the target model."
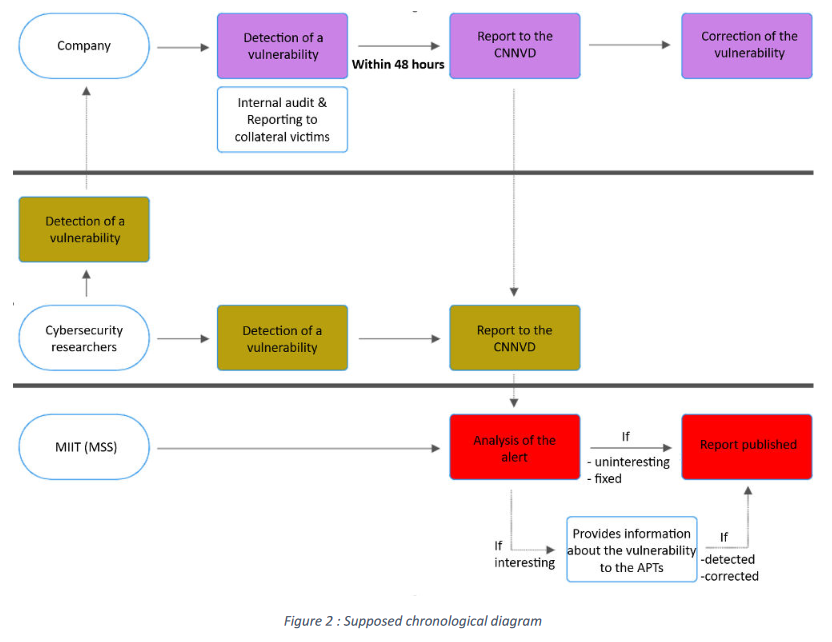
China's handling of vulnerabilities: French security firm Intrinsec has published a report on how the Chinese government is using the local bug hunter community and the vulnerabilities they find as a national strategic resource, forcing all disclosures and bug reports to go through state-controlled agencies. There's nothing new in the report, but it's a good overview of what we know so far at this point in time.
Infosec industry
CVE program 25th anniversary: MITRE's CVE program is now 25 years old.
"From the initial 321 CVE Records in 1999, to over 240,000 in October 2024, CVE serves as a cornerstone for effective vulnerability management worldwide across national vulnerability databases, cybersecurity tool vendors, incident response operations, researchers, and policymakers."
New tool—EDR Telemetry: Security researcher Kostas Tsialemis has released EDR Telemetry, a project that tracks EDR telemetry capabilities across OS platforms. The project is intended to reveal EDR coverage gaps for network defenders (and vendors, too).
New tool—SkyScalpel: Cloud security firm Permiso has open-sourced SkyScalpel, a framework for JSON policy parsing, obfuscation, deobfuscation, and detection in cloud environments.
"We hope SkyScalpel helps many organizations to extend their red team evasion capabilities and to more thoroughly test current detection capabilities for policy obfuscation or any JSON-document-based evasion technique."
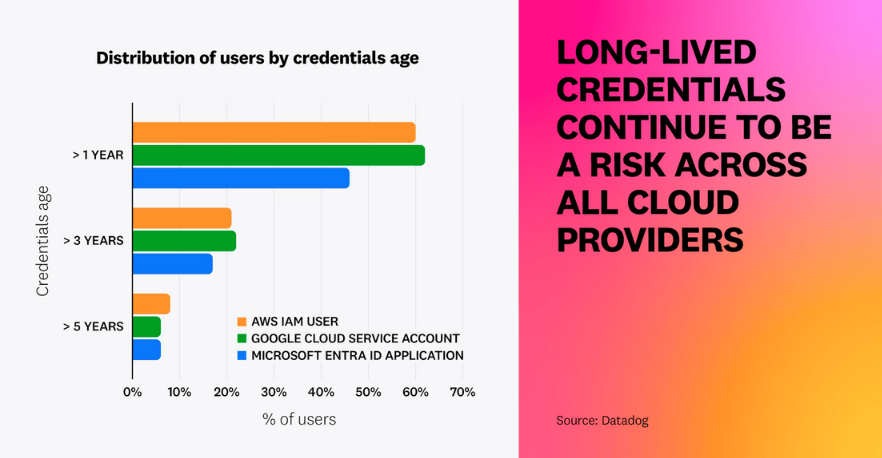
Threat/trend reports: Cisco Talos, Cloudflare, DataDog, Grip Security, Vanta, and Wallarm have recently published reports and summaries covering various infosec trends and industry threats.

Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about a new attempt to measure cyber power, the International Institute for Strategic Studies Cyber Power Matrix.
In this podcast, Tom Uren and Patrick Gray talk about the evolving relationship between Russian intelligence services and the country’' cybercriminals. The GRU's sabotage unit, for example, has been recruiting crooks to build a destructive cyber capability. Tom suspects that GRU thugs are not so good at hands-on-keyboard operations but excellent at coercing weedy cybercriminals to hack for the state.
Risky Business is now on YouTube with video versions of our main podcasts. Below is our latest weekly show with Pat and Adam at the helm!

