Risky Bulletin Newsletter
November 18, 2024
Risky Biz News: Unpatched zero-day in Palo Alto Networks is in the wild
Written by

News Editor
You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
Details of a zero day vulnerability in Palo Alto Networks software and a design flaw in a Fortinet product were published on Friday—every IT engineer's favorite day for emergency security procedures.
The zero-day impacts Palo Alto Networks firewall appliances, while the design weakness affects Fortinet's Windows VPN client.
The Palo Alto zero-day is believed to be related to an alleged exploit sold on the Exploit hacking forum earlier this month.
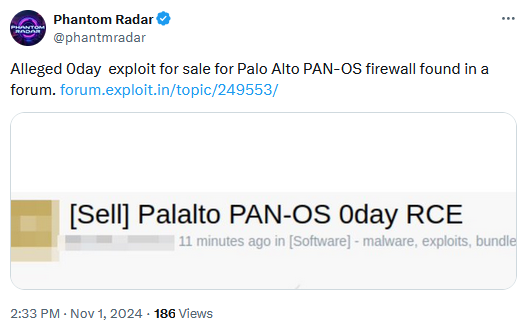
The company issued a security alert about the rumored exploit 10 days ago and has now updated the advisory to confirm live exploitation.
Palo Alto says the zero-day is a pre-auth remote code execution in its firewalls' web management interface. The company has asked customers to restrict access to this web panel only to trusted IP addresses.
The number of Palo Alto firewalls that still have their management interface exposed online varies from 9,000 to 31,000—depending on who's doing the scanning.
Because the exploit is still private, firewall owners may still have a chance to secure their device before it gets exploited. Palo Alto's security team has shared a list of IP addresses that have exploited the zero-day and a hash of a webshell that's installed on compromised devices.
News of a new PAN zero-day comes just days after CISA warned that threat actors were also exploiting two other vulnerabilities in its Expedition firewall configuration migration tool.
Until last week, Palo Alto engineers couldn't prepare a patch due to the limited information about the "supposed" exploit or if it existed. With confirmed attacks, we expect the company to have something out throughout the week.
On the other hand, Fortinet knew about a weakness exploited in the wild in its Windows VPN client—the FortiClient—since July 18, but has yet to release a fix.
Security firm Volexity, which discovered the attacks, says the zero-day (Volexity calls it a zero-day, but looks more like a design weakness to us) was exploited on systems that were previously infected with the DEEPDATA malware.
DEEPDATA used the bug to extract VPN credentials in cleartext from the FortiClient's memory space. The credentials were then sent to a command and control server using another malware known as DEEPPOST.
Volexity linked the malware strains and the FortiClient exploitation to a threat actor it tracks as BrazenBamboo. It described it as a developer of hacking tools used by other threat actors for "domestic surveillance."
Besides DEEPDATA and DEEPPOST, BrazenBamboo also developed LIGHTSPY, an infamous malware framework discovered in 2020 and which saw a resurgence this year with new versions for Android, macOS, and Windows—on top of its original iOS variant.
Neither the PAN two zero-day and the Fortinet bug have CVEs.
Risky Business Podcasts
Risky Business is now on YouTube with video versions of our main podcasts. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
Turkey fines Twitch over breach: Turkey's data protection agency has fined Amazon 2 million lira ($58,000) over a Twitch security breach. Hackers leaked over 125GB of data from Twitch systems in October 2021, including data on registered users and creator payouts. Turkish officials say Amazon failed to report the incident to the agency and that it impacted the data of more than 35,000 Turkish citizens. [Additional coverage in Reuters]
Spain fines Phone House over breach: Spain's data protection agency has fined electronics retail chain store Phone House €6,5 million over a 2021 security breach. The company was the victim of the Babuk ransomware, which leaked the personal details of 13 million customers after Phone House refused to pay a ransom. Spain's data protection agency fined Phone House for failing to anonymize customer data and for storing the information in plaintext. Phone House is the largest telco electronics retail chain in Europe, with over 400 stores and over 2,500 employees.
T-Mobile joins the Salt Typhoon victim list: US wireless carrier T-Mobile has become the fourth victim of a Chinese cyber-espionage group named Salt Typhoon. The breach was part of a large-scale campaign that targeted US telcos and which also compromised AT&T, Lumen, and Verizon. The breaches allowed Chinese hackers to spy on political figures and tap into the US law enforcement wiretapping system. [Coverage in the Wall Street Journal]
Destatis breach: Germany's statistics agency Destatis is investigating a possible breach of its IT network after some of its data was put up for sale by pro-Russian hackers. The agency has taken its IDEV data-sharing system offline while it investigates the incident further. The system is used by private companies, state, and federal governments to share statistical data and reports. [Coverage in Barron's]
Thala crypto-heist: A threat actor has exploited a vulnerability and drained over $25 million worth of crypto assets from the Thala DeFi platform. The company says it immediately identified the attacker and negotiated a return of all funds for a $300,000 bounty payment. Thala says it will return all stolen funds to user accounts once it re-audits its codebase.
General tech and privacy
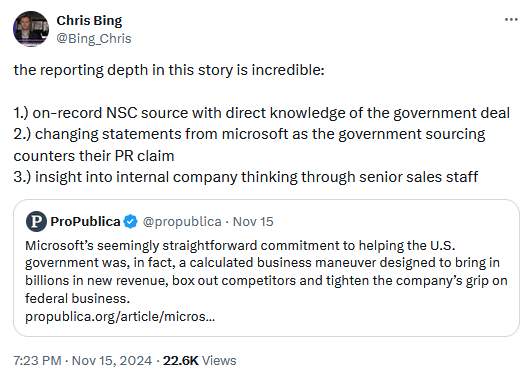
The US' Microsoft dependency: A ProPublica investigation looks at how Microsoft offered the US government free cybersecurity upgrades in 2021 and ensnared the US government IT apparatus into its closed ecosystem, making it harder to switch to other solutions due to high migration costs.
"The White House Offer, as it was known inside Microsoft, would dispatch Microsoft consultants across the federal government to install the company's cybersecurity products — which, as a part of the offer, were provided free of charge for a limited time. But once the consultants installed the upgrades, federal customers would be effectively locked in, because shifting to a competitor after the free trial would be cumbersome and costly, according to former Microsoft employees involved in the effort, most of whom spoke on the condition of anonymity because they feared professional repercussions. At that point, the customer would have little choice but to pay for the higher subscription fees."
Canadian extremism on Telegram: In a recent report, Open Measures looks at Canadian white nationalist groups on Telegram.
Google Shielded Email: Google is working on a new email masking feature for its Gmail service called Shielded Email. The feature will allow users to generate random-looking usernames to use in online forms and hide their real email addresses. Users will be able to delete email masks if they ever start receiving spam through one of them. The feature is not new and both Apple and Mozilla already offer a similar service in iCloud Hide My Email and Firefox Relay. [Coverage in Android Authority]
O2 granny AI wastes scammers' time: British internet service provider O2 says it developed an AI system that mimics an elderly lady to fight off phone fraud. The system detects suspected phone scammers and keeps them on the phone for as long as possible, posing as a gullible victim. O2 says the new Daisy granny AI has successfully kept multiple scammers on the phone for more than 40 minutes at a time.
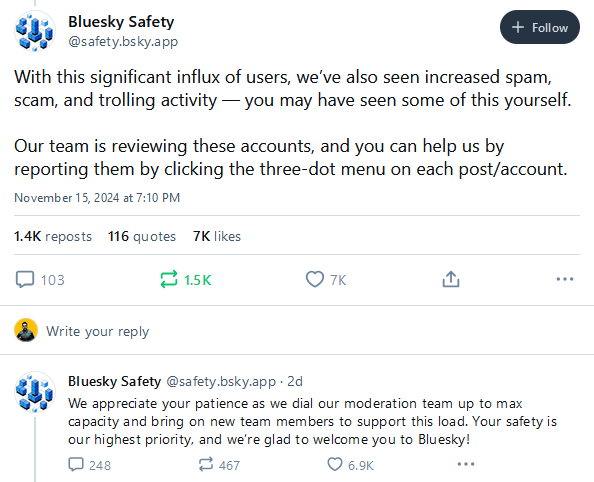
BlueSky trolls and spam: After reaching 18 million users and growing about 1 million new users per day, BlueSky says it's now seeing an influx of spam, scam, and troll accounts. 'twas to be expected!
Government, politics, and policy
Senator asks Valve to crack down on extremist content: A US senator has asked gaming platform Steam to crack down on extremist and hateful content on its platform. Sen. Mark R. Warner (D-VA) cited a recent report from the Anti-Defamation League that found over 1.5 million users and over 73,000 groups sharing at least one potentially extremist or hateful symbol, text, or keyword. According to The Verge, this marks the third time over the past three years that Congress has inquired Steam about its moderation practices. The platform has been one of the slowest to address hateful conduct, having added moderation tools on its forum only in 2018.
FTC reports 50% robocalls drop: The US Federal Trade Commission says the number of unwanted telemarketing calls has gone down by more than half since 2021. The agency says 2024 is the third year in a row when it has registered a decline in robocalls across the US. The FTC credits the decline to new rules banning unwanted calls and its crackdown on illegal telemarketing services.
Easterly to leave CISA: CISA Director Jen Easterly will depart her role on January 20, next year, on the day Donald Trump is inaugurated as the next US president. Easterly has already notified staff via email and at an all-hands staff meeting, according to a NextGov report. Several of her staff will also depart the agency on the same day. Easterly has served as CISA's head since July 2021.
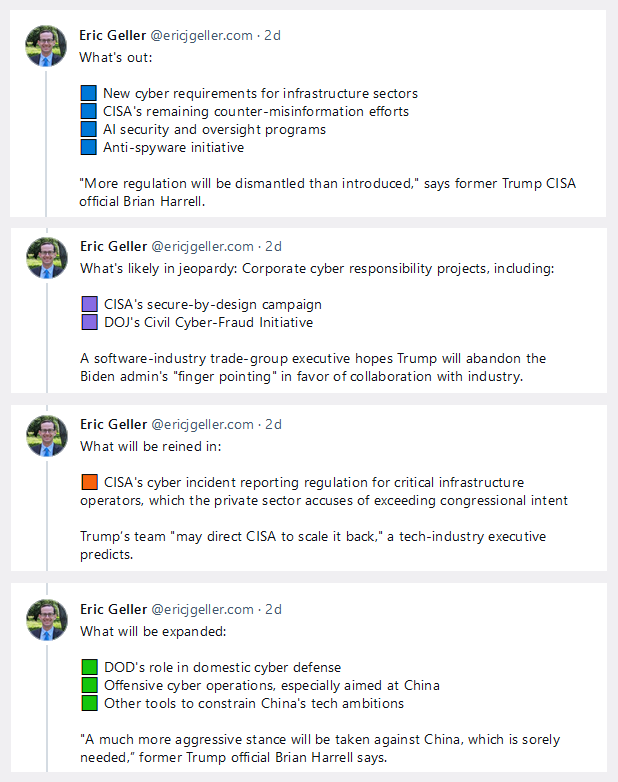
Predictions for Trump's cyber stance: WIRED interviewed Brian Harrell, former CISA assistant director during the first Trump presidency, about the upcoming administration's future cyber positions. Harrell sees more aggressive actions against China's hacking operations, a rollback of the White House's anti-spyware efforts, and an elimination of CISA's counter-misinformation efforts. [Plus more, see article or image below]
Risky Business Podcasts
In this podcast, Tom Uren and Patrick Gray talk about what to expect from President Trump's second term. Trump is an activist president who believes in using state power, so intelligence agencies will be pushed to conduct more audacious or even outrageous covert operations.
Arrests, cybercrime, and threat intel
Bitfinex hacker sentenced: US authorities have sentenced Ilya Lichtenstein to five years in prison for hacking cryptocurrency exchange Bitfinex. Officials say Lichtenstein stole almost 120,000 Bitcoin from the company's wallets in August 2016. He laundered the stolen funds with the help of his wife, Heather Morgan, until they were both detained in February 2022. Both pleaded guilty to their crimes. Besides his prison sentence, Lichtenstein will also serve three years of supervised release. Morgan is scheduled to be sentenced this week. The funds were worth $70 million at the time of the hack but are now valued at more than $10.5 billion.
Helix mixer admin sentenced: A US judge has sentenced an Ohio man to three years in prison for operating a dark web-based cryptocurrency mixer. Officials say Larry Dean Harmon was the administrator of Helix, a service that laundered over $310 million in crypto-assets linked to dark web drug markets. Harmon ran Helix between 2014 and 2017 and was arrested in 2020. Harmon's brother is already serving a prison sentence of four years and three months for hiding some of Helix mixer funds in his personal accounts.
ANOM distributor sentenced: US authorities have sentenced an Australian man to 63 months in prison for participating in a scheme to distribute ANOM encrypted devices to criminal syndicates. Osemah Elhassen of Sydney, Australia, was one of 17 suspects detained in 2021 in connection to the ANOM encrypted phone service. According to officials, Elhassen worked as the company's distributor in Colombia, where he was arrested and later extradited to the US.
Jetflicks programmer convicted: A US jury has convicted a Cuban national of helping run one of the biggest illegal streaming services in the US. Yoany Vaillant worked as a programmer for Jetflicks, a website that hosted TV shows pirated from Netflix, Disney+, and other streaming services. He is the eighth and final suspect charged in 2019 for running the site. Vaillant and five others are scheduled to be sentenced in February next year.
Three SIM-swappers arrested: US authorities have charged three Indiana residents for a SIM-swapping scheme. Officials say the group performed SIM swaps for themselves but also in exchange for money for other individuals. The trio allegedly hijacked accounts, stole funds from their victims, and also demanded ransoms to restore access to stolen profiles. The three suspects were arrested last week.
FinCEN warns of deepfake scams: The US Department of the Treasury's Financial Crimes Enforcement Network (FinCEN) has warned financial institutions to be prepared for more deepfake scams due to the rise of GenAI tools.
Fake government job boards: DomainTools' security team has put out a report with a number of fake government job portals it found in countries such as the US, Pakistan, India, Taiwan, and the Middle East.
Rescator interview: Brian Krebs has published an interview with Mikhail Shefel, the Russian hacker Rescator, known for the Target and Home Depot hacks.
New npm malware: Eighty malicious npm packages were discovered and taken down last week. Check out the GitHub security advisory portal for more details.
Botnet exploits GeoVision zero-day: A botnet operator is using a zero-day vulnerability to take over GeoServer cameras and video servers. The attacks were spotted last week by Taiwan CERT and are exploiting an unauthenticated command injection (CVE-2024-11120) in the devices' firmware. The devices have reached end-of-life, and no patch is available. According to the Shadowserver Foundation, there are around 17,000 vulnerable systems currently connected to the internet.
NSO had three WhatsApp exploits: Israeli spyware company NSO Group has continued to develop and use WhatsApp exploits even after Meta sued the company in a US court. New unsealed court documents reveal that NSO developed three exploits named Eden, Heaven, and Hummingbird, with the last being used in the wild months after Meta's 2020 lawsuit. In addition, court documents also reveal that NSO employees were the ones deploying the exploits against a customer's desired target. This contradicts previous NSO statements that the company didn't know how customers were using its hacking tools. [Additional coverage in TechCrunch]
New Termite ransomware group: There's a new ransomware gang on the scene—named Termite, and operating a dark web leak site as well. [h/t Dieter V. H.]

Malware technical reports
Thanos ransomware: The Thanos RaaS is still active, apparently, and has hit an unnamed police department in the UAE, per SonicWall, which has a technical report on the malware.
BabbleLoader: Intezer researchers have published a report on BabbleLoader, "an extremely evasive loader, packed with defensive mechanisms, that is designed to bypass antivirus and sandbox environments to deliver stealers into memory."
Glove Stealer: Gen Digital has published a report on Glove Stealer, the latest in a long line of new infostealers this year. The malware is written in .NET, can bypasses Chrome's new App-Bound Encryption scheme, and can steal data from browsers, crypto wallets, and 2FA authenticator apps.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about how ungoverned spaces on Telegram result in increasingly toxic and antisocial communities.
APTs, cyber-espionage, and info-ops
CL-STA-0237: Palo Alto Networks has found evidence that a cluster of North Korean IT workers who sought employment at Western companies was also involved in a malware distribution campaign. The IT workers set up website clones for the FreeConference and MiroTalk video conference apps. The websites were hosted on the servers of a US-based company they used to work in the past. The group, which PAN tracks as CL-STA-0237, sent phishing emails and attempted to lure recipients into installing the fake video conferencing software. Palo Alto Networks says the app installers were embedded with BeaverTail, a malware typically associated with North Korean APT operations. The company says the workers appeared to operate out of the city of Vientiane, Laos.
Lazarus ops: eSentire has published part two of an incident report on a Lazarus attack on a crypto developer who got infected with the group's malware from a GitHub repository. Part one is here.
DarkHotel: Russian security firm Positive Technologies has published a report on a cluster of activity targeting Asian countries that appears to mingle resources from DarkHotel, APT-C-60, and APT-Q-12 (Pseudo Hunter).
Emennet Pasargad targets Israeli athletes: France's counter-espionage agency DGSI says that an Iranian cyber group named Emennet Pasargad targeted Israeli athletes during the Paris Olympic Games. According to French news site Mediapart, the operation included phishing, mobile malware, data leaks, and even death threats. The group is primarily known for interfering in the US 2020 presidential election when it hacked voter websites and posed as right wing group Proud Boys to send threatening emails to Democrat voters.
Vulnerabilities, security research, and bug bounty
PostgreSQL bug write-up: RedRays researchers have published a technical breakdown of a recent PostgreSQL vulnerability (CVE-2024-10979) disclosed last week by Varonis.
Firefox zero-day write-up: French security researcher Dimitri Fourny has published a technical analysis of CVE-2024-9680, a recent Firefox zero-day that was patched at the start of October.
Firefox bug write-ups: Ricerca Security has published a technical write-up looking at two Firefox bugs patched in June (CVE-2024-5690) and October (CVE-2024-9398) this year. The report describes them as zero-days, but they were not exploited in the wild.
Gogs RCE: A security researcher has published details and proof-of-concept code for a vulnerability in the Gogs version control system after the project failed to release a patch. Tracked as CVE-2024-44625, the vulnerability allows threat actors to run malicious code on Gogs version control servers. While the vulnerability does not have a patch, the only upside is that attackers need access to an account on the Gogs system to run the exploit. Security researcher Fysac has urged Gogs admins to disable user registration and enforce MFA to prevent attacks.
"I advise anyone running Gogs to close off access to the public and untrusted users, disable user registration, set strong passwords and enable 2FA for existing accounts, and migrate to Gitea, which is an actively maintained fork of Gogs not affected by this vulnerability."
Major WP plugin auth bypass: Security researchers have discovered a major vulnerability in a WordPress security plugin installed on more than 4 million websites. The bug is an authentication bypass in Really Simple Security and allows attackers to access any account on a WordPress site. The bug is also scriptable and can be used for automated attacks at scale. Wordfence researchers described the bug as "one of the more serious vulnerabilities" they have reported in the company's 12-year history.
Scoold vulnerability: XBOW says its AI system has found an authentication bypass (CVE-2024-50334) in the Scoold open-source Q&A platform.
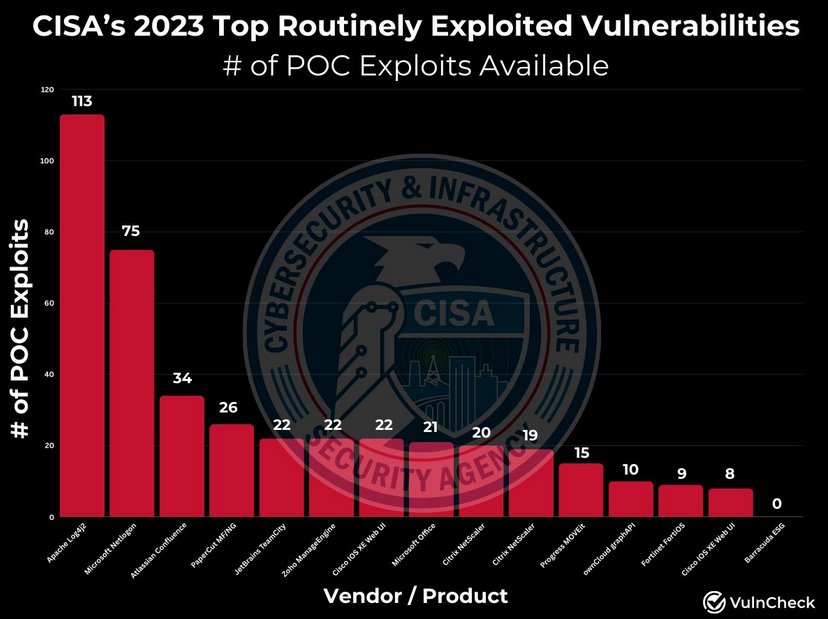
POC availability for most exploited vulns: VulnCheck's Patrick Garrity looks at the number of publicly available POCs for the CISA Top 15 most frequently exploited vulnerabilities of 2023. Only one vulnerability was exploited at scale last year that did not have a public PoC.
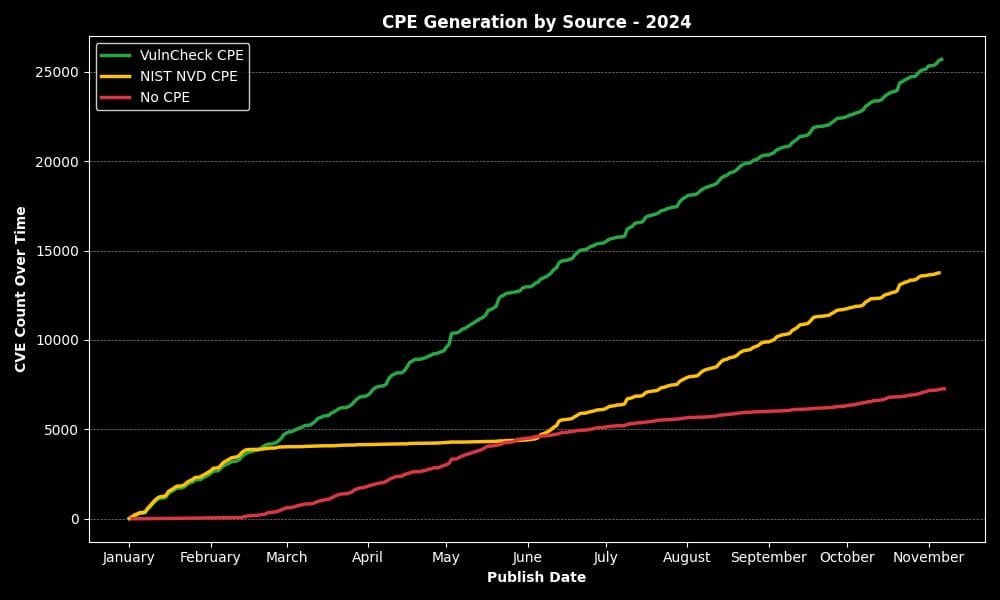
NIST backlog analysis: VulnCheck looks at NIST's slow efforts to address its CVE backlog. According to its data, NIST is slowly getting back to enriching CVEs, but it still has a long way to go.
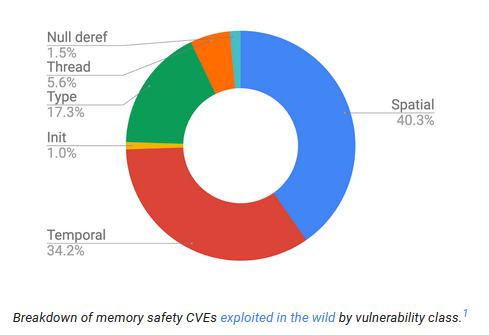
Google hardens its C++ code: Google has rolled out security improvements to its C++ code to protect against spatial memory vulnerabilities. These are vulnerabilities such as buffer overflow and out-of-bounds access. The company says it's now using a hardened version of the libc++ library in its production environments. The code is now live in Search, Gmail, Drive, YouTube, and Maps after it was initially tested in Chrome in 2022. Google says the hardened library only had a 0.3% impact on performance.
Infosec industry
Threat/trend reports: AuditBoard, NordPass, Thinkst, and Wordfence have recently published reports and summaries covering various infosec trends and industry threats.
Decipher shuts down: Cisco Duo has shut down its Decipher infosec news blog.
IRISSCON 2024 videos: Talks from the IRISSCON 2024 security conference, which took place earlier this month, are available on YouTube.
Swiss Cyber Storm 2024 videos: Talks from the Swiss Cyber Storm 2024 security conference, which took place in late October, are available on YouTube.
