Risky Bulletin Newsletter
November 29, 2024
Risky Biz News: Tor Project has "urgent need" for 200 new bridges to avoid Russian censorship
Written by

News Editor
This newsletter is brought to you by Stairwell. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
The Tor Project says it urgently needs at least 200 new bridges by the end of December to ensure Russian users can continue accessing the Tor network.
The project says it specifically needs bridges that run the WebTunnel protocol, which disguises connections to Tor networks as mundane web browsing activity.
WebTunnel bridges are harder to detect and censor compared to normal Tor bridges.
The Tor Project launched WebTunnel bridges in March and is currently running 143 servers. Tor maintainers believe 200 more servers would create enough of a server population to ensure Russian users will have enough servers available to connect to Tor safely.
The Russian government started cracking down on the Tor network in late 2021, months before its invasion of Ukraine.
Since then, it doubled its effort to track down and block Tor entry servers, and has also cracked down on a slew of other technologies that can be used to bypass its IPS-level internet censorship systems.
"If you've ever thought about running a Tor bridge, now is the time," Tor Community Team Lead Gus said in a blog post on Thursday.
Risky Business Podcasts
Risky Business is now on YouTube with video versions of our main podcasts. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
Hoboken ransomware attack: The city of Hoboken, New Jersey, has shut down its government offices after a ransomware attack this week. The incident impacted the Hoboken city hall, local courthouses, and public sanitation. No ransomware gang has taken credit for the attack.
T-Mobile breach: T-Mobile says that a recent attempted hack of its telco infrastructure originated from a connected wireline provider's network. The company says it severed connectivity with the wireline provider as soon as it detected suspicious reconnaissance activity. T-Mobile CSO Jeff Simon says no sensitive customer data was exposed in the attack and that he believes the wireline provider may still be compromised. Simon told Bloomberg he believes the attack was carried out by a Chinese espionage group known as Salt Typhoon. The same group also breached at least three other US telco providers, such as AT&T, Lumen, and Verizon.
Zello breach: Push-to-talk walkie-talkie app Zello has asked customers who created an account before November 2 this year to change their passwords. Companies usually request users to reset passwords in the wake of data breaches or credential-stuffing attacks. So far, Zello has not publicly confirmed any security breach. The company claims it has 140 million registered users. [Additional coverage in Bleeping Computer]
General tech and privacy
FTC opens antitrust Microsoft probe: The US Federal Trade Commission has opened a broad antitrust investigation into Microsoft's business practices. The investigation will cover the company's software licensing practices, cloud computing, cybersecurity, and AI business units. The FTC allegedly received complaints that Microsoft was locking in customers and preventing them from moving to competitors. In September, Google filed an official antitrust complaint against Microsoft's cloud business in the EU. [Additional coverage in the Bussiness Standard]
PQC transition standards: NIST has published official guidance for transitioning from quantum-vulnerable cryptographic algorithms to post-quantum digital signature algorithms and key-establishment schemes.
Government, politics, and policy
India adopts new telecom security rules: The Indian government has passed new cybersecurity rules for the country's telecommunications sector. The rules require telecom operators to report cybersecurity incidents to the country's regulator within six hours of detecting a breach, with a more comprehensive report being owed within 24 hours. The new rules also require telcos to log traffic data and grant authorities access to the data in case of emergencies. Legal experts warn the new regulations may be abused for surveillance and may incur huge costs to telcos. The rules don't specify what type of data telcos should log, for how long, or any type of oversight for accessing the data. [Additional coverage in the India Times]
UK to help allies with incident response: The UK government will provide incident response assistance to allied countries dealing with cyberattacks. Officials announced the new capability at a NATO cyber conference this week. UK Minister for Intergovernmental Relations Pat McFadden says the assistance is aimed specifically at countries dealing with attacks on critical infrastructure. UK officials warned that Russia is preparing cyberattacks on critical infrastructure in Western countries as the Ukrainian war escalates. [Additional coverage in The Record]
Cybercrime law abuse: AccessNow has published a report that looks at how Arab countries have repeatedly abused cybercrime laws to go after government critics and dissidents.
Sponsor section
In this Risky Business News sponsored interview, Tom Uren talks to Mike Wiacek, CEO and founder of Stairwell, about the occasionally dysfunctional relationship between IT and security teams. Mike talks about how security vendors need to reach out to turn IT teams into allies.

Arrests, cybercrime, and threat intel
FBI investigates Exxon Mobil consultant: The FBI is investigating an Exxon Mobil consultant for their role in a hack-and-leak operation. According to Reuters, the consultant allegedly hired hackers to target hundreds of Exxon critics. The consultant allegedly shared stolen data with Exxon before it was leaked online. Exxon used the leaked data to counter climate change litigation by portraying itself as a target of political vendettas. The hacking targeted Greenpeace, the Union of Concerned Scientists, the Rockefeller Family Fund, and former Democratic presidential candidate and billionaire environmentalist Tom Steyer.
Appeals court overturns Tornado Cash sanctions: A US court of appeals has overturned the US Treasury Department's sanctions on cryptocurrency mixing service Tornado Cash. The court ruled that the US Treasury overstepped its authority when it sanctioned the service in September 2022. The court sided with six cryptocurrency users who claimed the Treasury can only sanction property and not software. The Tornado Cash service has been linked to massive crypto money laundering operations, ranging from drug cartels to state-sponsored hacking groups. [Additional coverage in Axios]
Money launderers charged: The US government has unsealed an indictment against nine suspects who laundered millions of dollars from internet fraud and BEC schemes. Officials say the group has laundered more than $20 million since it began operating in November 2016. The suspects are still at large and face up to 20 years in prison if caught and found guilty.
IPTV service takedown: European law enforcement agencies have taken down a sports pirate streaming platform. Officials have detained 11 suspects and seized over 100 domains. The unnamed service allegedly broadcasted pirate streams from over 2,500 channels, had over 22 million registered users, and was making around €250 million per month.
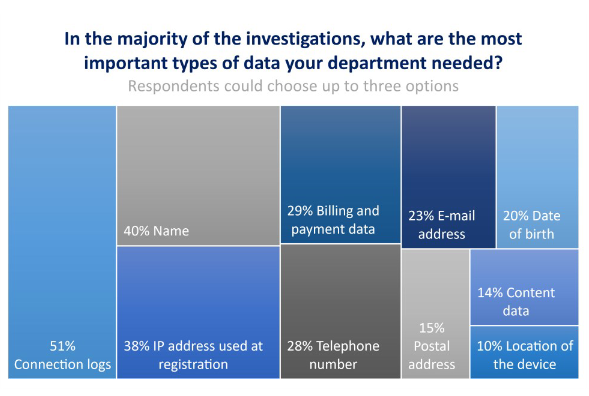
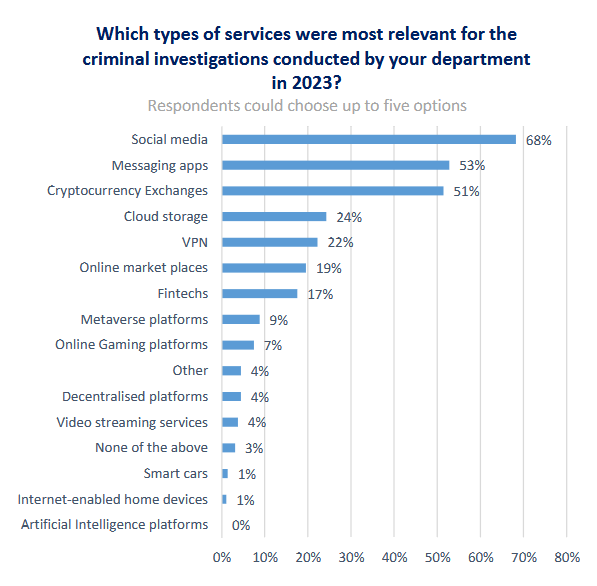
What law enforcement looks for: Europol says that connection logs and IP addresses are the most useful information that agents seek during law enforcement investigations. Data points like names and billing information are also useful, but connection details are what officials say have provided more value over the past year. In its yearly electronic evidence report, Europol says that social media, messaging apps, and crypto exchanges have proven by far to contain the most relevant information for its investigations.
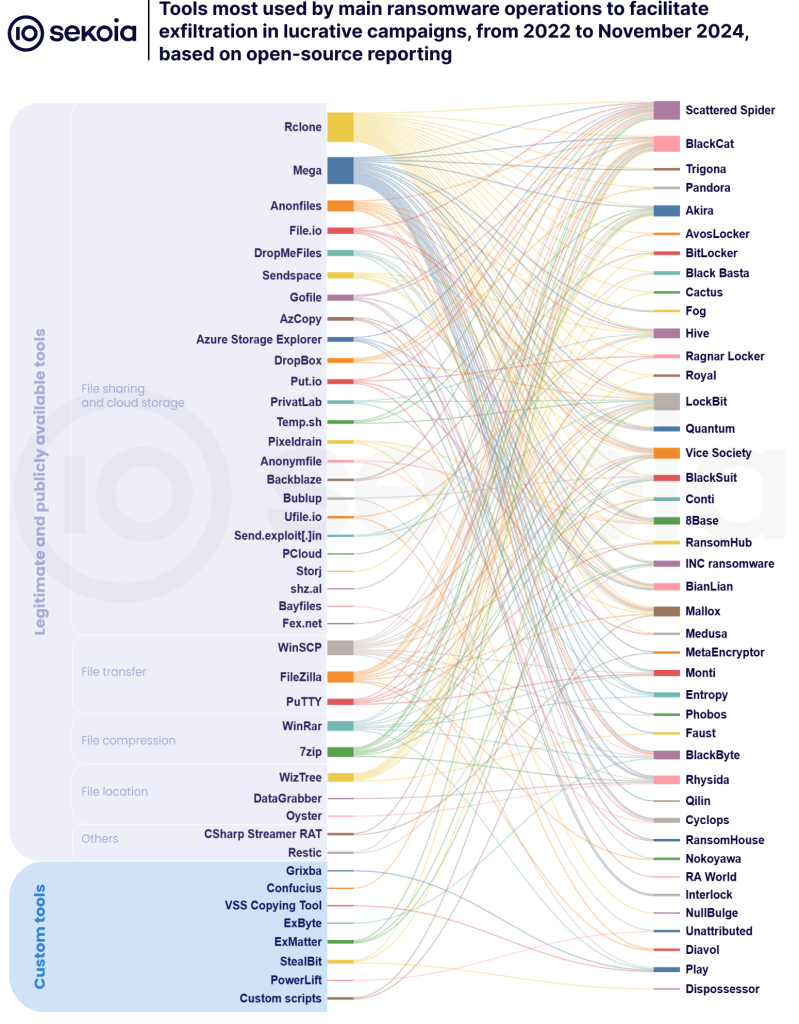
Ransomware exfil techniques: Sekoia has published research on how ransomware gangs exfiltrate data from compromised environments.
Kiberphant0m: Brian Krebs has published a profile on Kiberphant0m, the third hacker involved in the Snowflake hacks and extortions earlier this year. Two suspects—Alexander Moucka (Canada) and John Erin Binns (American living in Turkey)—have already been charged. Krebs believes the third suspect may be a member of the US military.
CryptoLove: TRAC Labs has a profile of CryptoLove, a traffic distribution (traffer) gang that often redirects users to infostealer-infected apps.
npm malware: Checkmarx looks at yet another malicious JS library uploaded on npm, this one targeting users looking for the React Native official documentation.
New scareware tactics: According to security researcher Lukas Stefanko, a new type of Android scareware uses fullscreen images that resemble cracked or malfunctioning screens to trick users into calling tech support numbers or downloading malware on their devices.
Malware technical reports
Helldown ransomware: CyFirma has published a report on Helldown, a new ransomware gang exploiting a Zyxel zero-day for initial access.
CleverSoar: Rapid7 has published a technical analysis of CleverSoar, a new malware loader targeting Chinese and Vietnamese-speaking users.
PSLoramyra: ANY.RUN has taken a look at PSLoramyra, a new PowerShell-based malware loader.
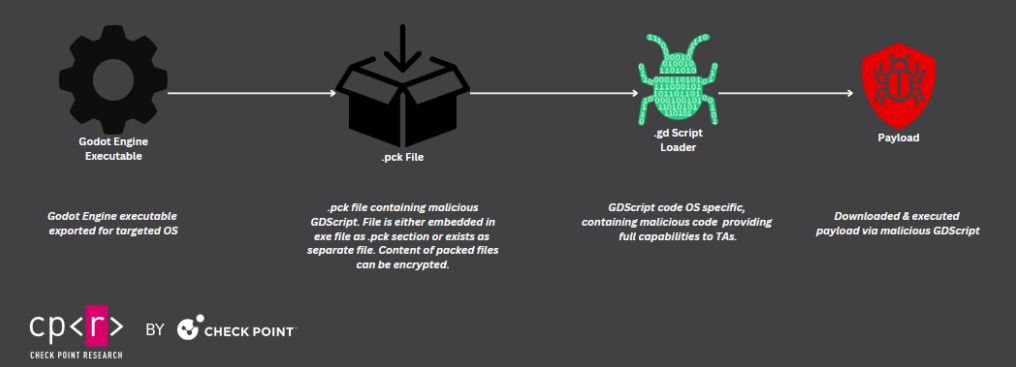
GodLoader: A new malware strain named GodLoader has infected at least 17,000 systems, according to security firm Check Point. The malware is unique because it uses the Godot game engine to generate payloads with cross-platform capabilities. The GodLoader gang uses these payloads to infect devices and then deploy additional malware on the compromised hosts. For now, most of the infected systems appear to be Windows devices.
Bootkitty: ESET researchers have spotted what appears to be the first UEFI bootkit that targets Linux operating systems. The bootkit is named Bootkitty and was specifically designed to work on Ubuntu distributions. ESET says it has no telemetry to suggest the tool was used in the wild, and based on current evidence, the bootkit appears to be just a proof-of-concept.
Sponsor Section
Stairwell gives you the confidence to know if, when, and where malware has ever been on your systems. We take a data search approach to security: collecting, storing, and continuously reassessing every executable file and indicator of compromise — across all time, at planet scale.

APTs, cyber-espionage, and info-ops
APT36's ElizaRAT: Reco has published its own analysis of APT36's ElizaRAT, initially covered by Check Point.
USB attacks: In its Q3 APT report, Kaspersky looks at UTetris and P2, two malware frameworks designed to spread via USB drives and linked to espionage activity across Southeast Asia.
Vulnerabilities, security research, and bug bounty
EpileptiCar phenomenon: New academic research has found that the flashing lights of emergency vehicles can disorient automated driving systems and lead to car crashes. The behavior has been named EpileptiCar and impacts both commercial and open-source Advanced Driver-Assistance Systems (ADAS). The EpileptiCar effect is amplified at night, by the distance to emergency vehicles, and by the self-driving car's camera settings and capabilities.
Unpatched Windows LPE: The SSD Disclosure team has published details about an unpatched Windows local privilege escalation vulnerability. SSD says the vulnerability was used during the TyphoonPWN 2024 hacking contest earlier this year. The company published details after Microsoft claimed the bug was a duplicate and had already been patched. Researchers say their tests showed the exploit still works on Windows 11 systems.
Spring vulnerability: Source Incite researchers have published a write-up covering a still-unpatched vulnerability in the Spring Java framework that can be abused for remote code execution.
Kemp command injection: ERNW has published a write-up on a command injection bug (CVE-2024-7591) they reported and helped patch in the Kemp LoadMaster earlier this month. The bug has a 10/10 severity score and is likely to get exploited.
Microsoft Partner exploitation: A threat actor has exploited a vulnerability in the official Microsoft Partner portal. Microsoft has disclosed the attack this week after it rolled out a patch. The patch was part of a larger set of security updates for Microsoft cloud services. Additional details about the attack remain unknown. [Additional coverage in SecurityWeek]
Jenkins security updates: The Jenkins project has published security updates for its core code and two of its plugins.
Infosec industry
CrowdStrike Q3 results: CrowdStrike reported a loss in Q3 due to its July IT outage but the company still recorded revenue growth and saw its stocks up 42% from the start of the year. [Additional coverage in Investopedia]
New tool—Censeye: Censys has released Censeye, a tool to identify hosts with characteristics similar to a given target.
New tool—Phishing Prevention Framework: FS-ISAC has published a phishing prevention framework for financial organizations.
New tool—Redact: Even if Twitter took down its API, there's still one tool named Redact that can wipe your account if needed.
Threat/trend reports: Kaspersky, the NCC Group, Netskope, and ReliaQuest have recently published reports and summaries covering various infosec trends and industry threats.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about different views on attribution and why it still matters for sophisticated state-backed groups.
In this podcast, Tom Uren and Patrick Gray talk about the Australian Government's extraordinary legislation that will retrospectively ensure that warrants used for the An0m crime-phone sting operation are valid.

