Risky Bulletin Newsletter
November 08, 2024
Risky Biz News: Russia blocks Cloudflare ECH connections
Written by

News Editor
This newsletter is brought to you by vulnerability management and analysis platform Nucleus Security. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
Russia's internet watchdog agency, the Roskomnadzor, has blocked traffic to Cloudflare-hosted websites that use the new Encrypted Client Hello (ECH) technology.
Users in Russia and abroad started reporting issues with accessing a large number of websites on Wednesday, November 6.
Roskomnadzor, through its Center for Monitoring and Control of Public Communications Networks department, says it took the decision after Cloudflare enabled ECH by default for customer accounts in October.
The agency said ECH was being used by Russian citizens to bypass its censorship measures and access restricted resources.
Formerly known as Encrypted Server Name Indication (ESNI), ECH is a new option in the TLS 1.3 standard that allows website operators to hide a piece of metadata that in previous versions of TLS was leaking the possible location of an HTTPS connection.
Security software vendors and oppressive regimes have used the Server Name Indication (SNI) field for years to filter and block encrypted HTTPS traffic going to "unwanted" websites and locations.
Since Russia's invasion of Ukraine, the Roskomnadzor has slowly been building a national internet censorship system to prevent citizens from accessing sites where news on the war are presented in an "unfiltered" and "uncontrolled" manner.
It has blocked hundreds of thousands of website URLs, VPN services, and multiple VPN protocols and technologies.
With Cloudflare turning ECH on by default, the move neutered a large chunk of Roskomnadzor's website censorship system.
In mid-2020, the Chinese government also blocked ESNI (as known back then, now known as ECH) shortly after the launch of TLS 1.3 and after the technology was used to bypass the Great Firewall's super-strict internet censorship.
The new ECH block in Russia has also been made worse by the fact that only Cloudflare paid accounts can disable the new technology. Many website operators on free accounts couldn't turn ECH off and keep services alive for Russian audiences.
Breaches, hacks, and security incidents
Serco cyberattack: A cyberattack has disrupted tracking devices and panic alarms installed on prison vans operated by Serco across the UK. The downtime was caused by a ransomware attack last week that hit Microlise, a UK-based company that provides transport tech solutions. DHL's UK division was also impacted and lost access to its package tracking tool. [Additional coverage in the Financial Times]
Replit discloses security incident: AI coding platform Replit has emailed customers to disclose a security breach. The company says that a misconfiguration in its service allowed its employees to access plaintext passwords for a small number of its customers. Replit says it has not discovered any instances where the passwords were abused to access customer accounts. The company claims to have over 30 million users.
Singtel hack: Chinese state-sponsored hackers have breached Singapore's largest telecommunications provider Singtel, in June this year. The attack is believed to be the work of a group known as Volt Typhoon. Officials believe the Singtel hack was a test run before hackers moved on to target US telcos. [Additional coverage in Bloomberg]
Washington courts hack: A cyberattack has taken down court IT systems across the US state of Washington. The outage is impacting court systems across several counties and major cities, delaying fine payments and scheduled hearings. The incident took place over the weekend and is believed to be yet another ransomware attack. Officials say they took down systems as a precaution and are now restoring affected systems. [Additional coverage in The Record]
DataBreach.com: PCMag has a profile on DataBreach.com, a site that advertises itself as a HIBP alternative.
General tech and privacy
PHP hardening efforts: Julien Voisin takes a look over some of the new security hardening efforts coming to PHP in upcoming releases. Some of them include better random names for file uploads, safe-unlink's comeback, allocation isolation, and more.
Mozilla layoffs: The Mozilla Foundation has laid off 30% of its staff. The layoffs impacted the organization's advocacy and global programs. This is the second layoff at Mozilla this year. It previously laid off dozens of employees from its Firefox browser division. The organization previously announced a re-focus on AI and ad-related technologies. [Additional coverage in TechCrunch]
Government, politics, and policy
Canada kinda bans TikTok: The Canadian government has ordered TikTok to shut down its Canadian operations following a national security review. The company operates two offices in Toronto and Vancouver. Officials have not blocked the app, and Canadians are still free to access it. The government has urged Canadians to understand they are using an app controlled by an adversary nation that may collect and abuse their data. [Additional coverage in the CBC]
Germany drafts security research law: The German government has drafted legislation to protect security researchers who discover and report vulnerabilities. The proposed law would eliminate the risk of criminal liability from cybersecurity research as long as bugs are responsibly disclosed to vendors. The law will also introduce harsh prison sentences from three months to five years for researchers who abuse the process of vulnerability research for criminal acts. These include incidents when researchers cause substantial financial damage during their research, extortions, or acts that damage critical infrastructure.
Australia prepares social media age limit: The Australian government is preparing legislation that would introduce an age limit of 16 years for social media accounts. The bill would hold online platforms accountable for enforcing the ban. The government plans to table the bill in Parliament next week. Officials said they are introducing the bill because of the harm social media is doing to Australian children.
Romania scraps solar panel security audit: The Romanian government has scrapped a controversial measure from an upcoming bill on solar panels that would have mandated that all panel owners conduct a cybersecurity audit of their devices every year. [Additional coverage in HotNews]
Sponsor Section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Adam Dudley, Senior Director for Strategic Initiatives & Alliances at Nucleus Security, on how the company works with partners and customers to constantly improve its service. Adam also touches on how executives are now inquiring about vulnerability management more than low-level practitioners.

Arrests, cybercrime, and threat intel
Judische profile: Security firm Intel471 has published a profile on Alexander "Connor" Moucka, a hacker known as Judische, who was recently arrested for the Snowflake hacks.
Zebleer interview: TechCrunch has published an interview with Zebleer, the cheat maker who exploited a bug in Call of Duty's anti-cheat engine to get thousands of players and high-profile creators banned.
Linear eMerge exposure: There are currently more than 2,700 Linear eMerge E3 smart door and access control platforms exposed on the internet that are vulnerable to hacking. Around 95% are located in the US. The devices are vulnerable to a command injection issue (CVE-2024-9441) that was disclosed at the end of September. The issue was disclosed through the SSD Disclosure platform after the vendor failed to patch the bug. Proof-of-concept exploit is also available online.
NCSC malvertising guide: The UK's cybersecurity agency has published a guide to help businesses deal with malvertising attacks.
FBI sees increase in illegal emergency data requests: The FBI says it's seeing an uptick in posts on criminal forums about the sale of compromised law enforcement credentials. Threat actors use the compromised accounts to file emergency data requests at tech companies and obtain sensitive data about high-value targets. The information is later used for social engineering or SIM-swapping attacks. The FBI has urged companies that deal with law enforcement requests to review and adjust security protocols. [FBI PIN alert/PDF]
Malware technical reports
Interlock ransomware: Cisco Talos has published a technical analysis of the new Interlock ransomware.
Mozi returns as Androxgh0st: Indian security firm CloudSek has linked the new Androxgh0st malware to the old Mozi botnet. Androxgh0st was first spotted this year attacking web servers and Laravel-based applications. The botnet was the subject of a CISA alert, which warned against its increasing attacks on cloud infrastructure. CloudSek says it is now seeing Androxgh0st deploy Mozi-like payloads against IoT devices. Mozi was a large IoT botnet that operated between 2019 and 2021 when Chinese authorities detained some of its administrators.
Silent skimmer: Palo Alto Networks looks at a new version of the Silent skimmer. The malware was first spotted last year and is exclusively deployed on the infrastructure of companies that host or create payment infrastructure and gateways.
SteelFox: Kaspersky has published a report on SteelFox, a new malware spread online via forum posts, torrent trackers, and blogs, imitating popular software like Foxit PDF Editor and AutoCAD.
SpyNote: CyFirma looks at the ancient SpyNote Android remote access trojan and some of its "newest" versions.
Rhadamantys: Check Point has published an analysis of v0.7 of the Rhadamanthys infostealer.
Wish Stealer: CyFirma has found Wish Stealer, a new Node-based infostealer targeting Windows systems that can steal sensitive data from Discord, browsers, and cryptocurrency wallets.
AsyncRAT: ANY.RUN has published a report on "two distinct methods used to infect systems with AsyncRAT via open directories."
GuLoader: Cado Security looks at new versions and campaigns spreading the GuLoader. These ones targeted European industrial and engineering companies.
Gootloader: Sophos has published a report on a Gootloader version distributed via cat-themed SERP-poisoned results and websites.
Void Arachne: Trend Micro has spotted a new Chinese cybercrime group named Void Arachne that targets Chinese-speaking users. The group uses SEO poisoning tactics, social media, and instant messaging platforms to distribute a Windows backdoor. Void Arachne's main lures are software that can evade the Great Firewall and online censorship. Seems to be the same thing spotted by Fortinet too.
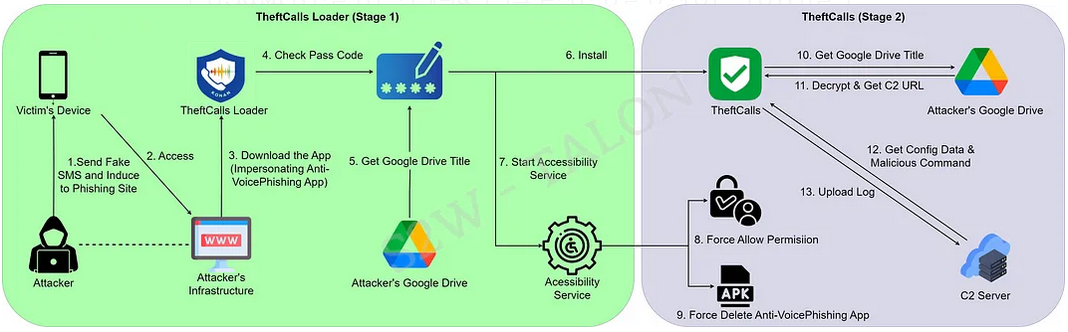
TheftCalls: South Korean security firm S2W has published an analysis of TheftCalls, an Android malware strain operated by the TheftCrow gang. The group calls victims by phone, posing as official institutions, and tricks them into installing the malware. The malware itself is a basic loader that is used to deploy other malicious tools.
Sponsor Section
Nucleus Security's COO Scott Kuffer shows Patrick Gray their vulnerability management platform. It ingests scan outputs from a number of vulnerability identification tools, normalizes that information, and then allows vulnerability management teams to do things like assigning responsibility for certain types of bugs to the correct people.
APTs, cyber-espionage, and info-ops
MirrorFace expands to Europe: In its Q3 APT report, ESET says it has seen Chinese APT group MirrorFace add EU organizations to its target list, which, historically, has included mainly Japan. The report also covers how several Chinese APT groups are now deploying SoftEther VPN servers on compromised hosts.
BlueNoroff: SentinelOne has published an analysis of a campaign from DPRK APT BlueNoroff that targeted crypto-related companies with the RustBucket malware.
Vulnerabilities, security research, and bug bounty
Cisco URWB bug: Cisco has patched a critical vulnerability that can allow threat actors to run commands with root privileges on Ultra-Reliable Wireless Backhaul (URWB) access points. Tracked as CVE-2024-20418, the vulnerability impacts the AP's web-based management interface. URWB access points are typically used in manufacturing, ports, and mines, where they need to face harsher conditions. The issue has a severity score of 10 and is one of 15 bugs Cisco patched this week.
UltiMaker RCE: Checkmarx researcher Ori Ron has discovered a remote code execution vulnerability in the UltiMaker Cura 3D printer. Tracked as CVE-2024-8374, the vulnerability can be exploited via the 3MF format reader.
Synology security updates: NAS and backup solutions provider Synology has released four security updates this week.
KEV update: CISA has updated its KEV database with four vulnerabilities that are currently exploited in the wild.
- CVE-2024-43093 - Android Framework Privilege Escalation Vulnerability
- CVE-2024-51567 - CyberPanel Incorrect Default Permissions Vulnerability
- CVE-2019-16278 - Nostromo nhttpd Directory Traversal Vulnerability
- CVE-2024-5910 - Palo Alto Expedition Missing Authentication Vulnerability
Infosec industry
Acquisition news: CrowdStrike has agreed to acquire Israel-based cloud security firm Adaptive Shield for around $300 million.
Acquisition news: Malwarebytes has acquired AzireVPN to improve its own VPN service offering.
New tool—CAPICHE: Cloud security firm Permiso has released CAPICHE (Cloud API Conversion Helper Express), an open-source tool designed to simplify each step of cloud API detection translation pipeline, enabling any defender to instantly create numerous styles of detection rules from groupings of APIs.
New tool—DetentionDodger: The same Permiso also released DetentionDodger, a tool that finds identities with leaked credentials and the impact they have on a target.
ATT&CK v16: MITRE has released v16 of the ATT&CK framework.
Threat/trend reports: ANSSI, Dogesec, ESET, FACCT, HackerOne, NBIP, and Positive Technologies have recently published reports and summaries covering various infosec trends and industry threats.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq discuss what the Russian state gains and loses from hosting a ransomware ecosystem.
In this podcast, Tom Uren and Patrick Gray talk about the Snowflake hack after the person allegedly responsible was arrested in Canada. Telegram is involved at all sorts of levels and Tom wonders if this crime would have occurred if Telegram didn't exist.
Risky Business is now on YouTube with video versions of our main podcasts. Below is our latest weekly show with Pat and Adam at the helm!

