Risky Bulletin Newsletter
December 02, 2024
Risky Biz News: Russia arrests WazaWaka
Written by

News Editor
This newsletter is brought to you by Push Security. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
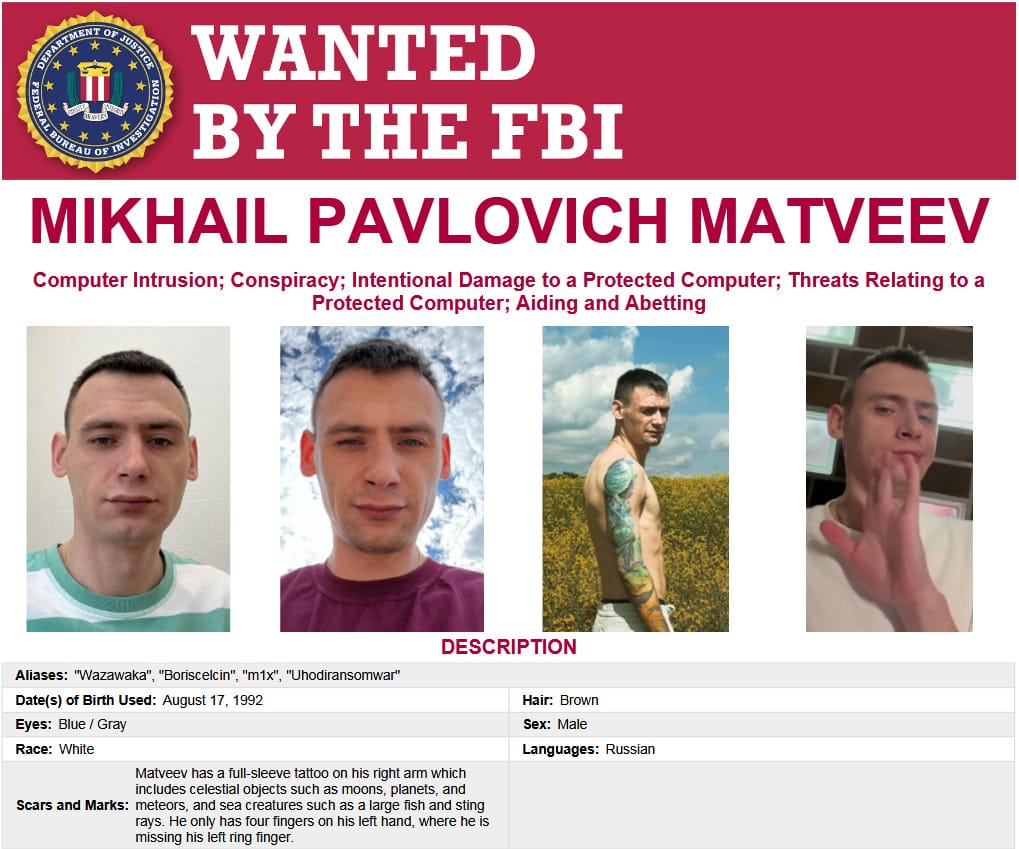
Russian authorities have arrested Mikhail Matveev, a high-profile ransomware affiliate known for his hacker name of WazaWaka.
Matveev's arrest was mentioned in a court case filed in Russia's Kaliningrad exclave, Russian state news agency RIA Novosti [archived] reported on Friday.
He was detained and charged with creating malware. The criminal case specifically mentions that WazaWaka wrote new ransomware in January this year.
Matveev's real-world identity was exposed in a Brian Krebs article in January 2022. He was charged a year later by the US Justice Department for a series of ransomware attacks across the US, including two attacks against police departments.
According to the DOJ indictment, Matveev worked as an affiliate for ransomware gangs such as Babuk, Conti, Darkside, Hive, and LockBit. He gained access to private networks, escalated access, and then deployed ransomware to encrypt files and ransom companies.
Matveev's most notorious incident is the ransomware attack on the Washington DC Metro police department in April 2021. In an attempt to extort the department, he threatened to release files containing police investigations and informants.
The heat and attention he generated from that incident alone was so bad that the entire Babuk Ransomware-as-a-Service operation shut down and released its source code on the dark web days later.
WazaWaka's arrest is the third crackdown on ransomware gangs in Russia. Members of the REvil gang were detained and recently sentenced to prison, while the suspect behind the Medibank ransomware was detained in February and is currently awaiting trial.
Risky Business Podcasts
Risky Business is now on YouTube with video versions of our main podcasts. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
Uganda cyber-heist: Hackers have stolen almost $17 million from Uganda's central bank in a brazen hack earlier this month. A hacking group named "Waste" is believed to be behind the attack. Ugandan officials confirmed the incident at the end of last week and said they tracked some of the stolen money to bank accounts in Japan. Over half of the stolen funds have already been recovered. [Additional coverage in Reuters]
DefCamp DDoS attacks: Pro-Kremlin hacktivist group has launched a DDoS attack against the website of Romanian security conference DefCamp as one of its speakers was scheduled to hold a talk on the group's activities.
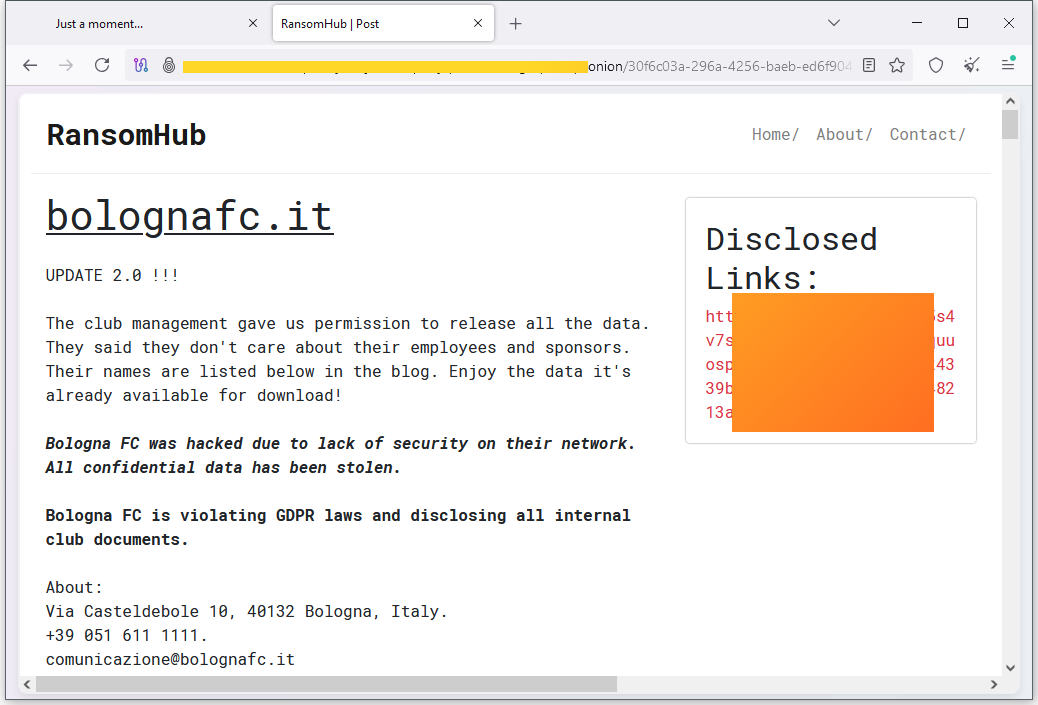
Bologna FC ransomware attack: Italian soccer club Bologna FC has disclosed a security breach after falling victim to a ransomware attack. The club put out a statement last week warning that data from its internal network had been published online. The RansomHub ransomware group published the data after the club refused to pay. The leaked data allegedly includes the personal and medical records of the club's players, staff, and financial records. Bologna FC is currently ranked eighth in Italy's soccer league.
General tech and privacy
Zoom willing to settle SEC privacy probe: Video conferencing app Zoom has submitted a proposal of $18 million to settle a probe from the US Securities and Exchange Commission into the company's privacy practices. In documents [PDF] filed last week, the company says it's still waiting for the SEC's answer and is unclear if the matter would be resolved. The SEC started a formal investigation of Zoom in 2020 during the height of the COVID-19 pandemic, when the company's product rose to fame. The investigation is covering Zoom's privacy policies and the company's misleading practices about call encryption. [Additional coverage in Mashable]
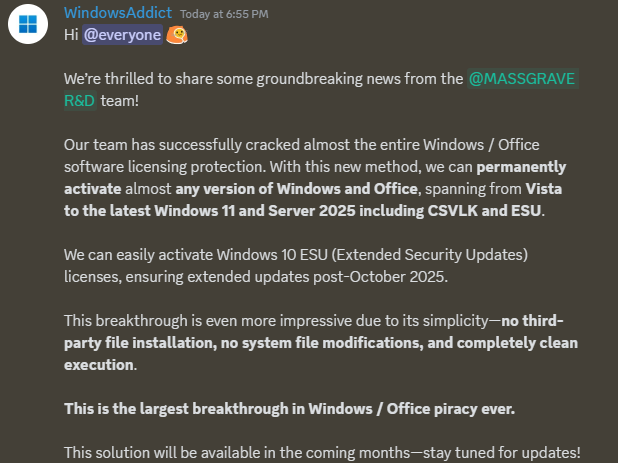
Windows piracy: A team of software hackers claims to have cracked "almost the entire Windows and Office software licensing protection" scheme. The MAS group claims their bypass can work natively without the need of third-party software. The group has tested the technique to activate licenses for Microsoft Office, Windows 7, Windows 8, all Windows Server editions, and licenses for Microsoft's Extended Security Updates (ESU) program. If confirmed, the technique is bound to trigger a new boon for Windows piracy. [Additional coverage in GHacks]
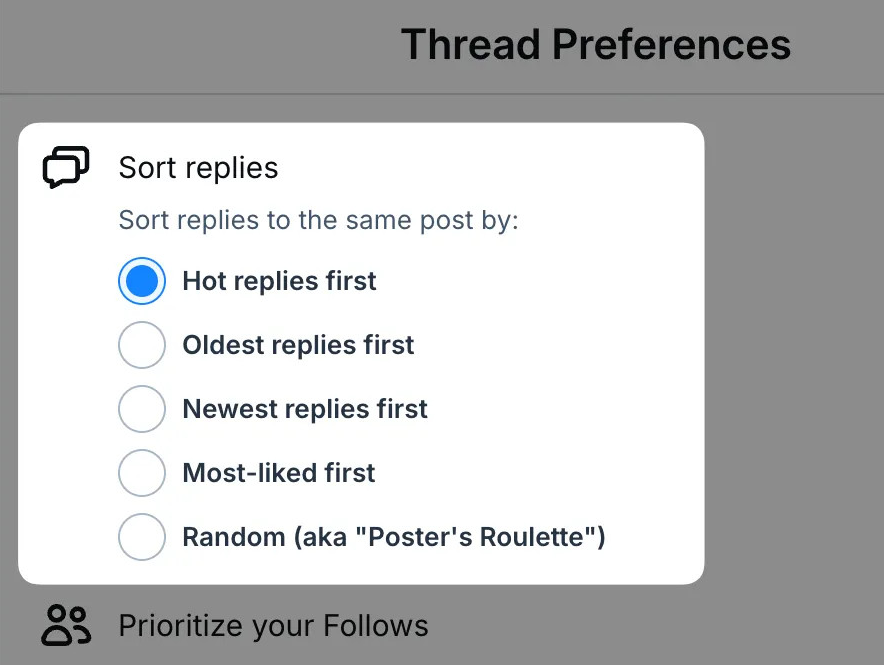
BlueSky update: BlueSky now lists user replies by default based on "hotness"—or by the amount of likes replies get.
Government, politics, and policy
Online scam compounds in Myanmar: The Global China Pulse has published an analysis of the role cyber scam compounds—together with other factors—play in Myanmar's economy and internal political struggles.
"The Covid-19 pandemic and the construction of a 2,000-kilometre wall along the China–Myanmar border (Strangio 2020) significantly disrupted traditional illicit economies that were sustaining EAOs (ethnic armed organisations). In response, these groups adapted by venturing further into the digital realm, specifically the online scam industry, which is less reliant on physical economies. While online scam operators were already becoming established in the region, these disruptions catalysed a rapid growth, and this industry has evolved into what Franceschini et al. (2023) have termed 'compound capitalism': a new form of predatory capitalism characterised by labour segregation, forceful data extraction, and exploitation of workers' desperation."
ECHR rules against Hungary in spying scandal: The European Court of Human Rights (ECHR) has ruled that the Hungarian government violated a reporter's rights in a November 2016 wiretapping scandal. Blikk reporter Klaudia Csikos sued the government after police wiretapped her to unmask a source who shared details about a high-profile murder case. Conversations from the wiretaps were later used to fire her source. The court says the government broke the reporter's right to privacy and freedom of expression but also failed to investigate her complaint of illegal spying.
CISA debuts new cybersecurity training platform: CISA launched last month a new cybersecurity training platform named CISA Learning. [Additional coverage in FNN]
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Jacques Louw, co-founder and chief product officer at Push Security, on the company's new stolen credentials detection feature, how AitM phishing can be spotted in the browser, and how Push deals with customers needing help with MFA.
Arrests, cybercrime, and threat intel
Police arrest tech CEO for building DDoS function: South Korean police have arrested a tech company's CEO and four employees for adding a DDoS feature to the firmware of its satellite broadcasting receiver. The company allegedly added the feature at the request of one of its customers. The customer claimed they were facing DDoS attacks by one of their competitors and requested the DDoS feature to fight back. The unnamed South Korean company allegedly shipped the feature to more than 240,000 units sold since January 2019.
India's SIM crackdown: The Indian government has blocked over 670,000 SIM cards and 130,000 IMEI codes linked to cybercrime activity. The SIM cards and IMEI codes were used in recent FedEx scams and calls impersonating government and police officers. Officials believe the calls and scams originated from outside its borders. [Additional coverage in the India Times]
New npm malware: Four-hundred-fourteen malicious npm packages were discovered and taken down last week. Check out the GitHub security advisory portal for more details.
Corrupted file abuse: Threat actors are using corrupted files to sneak malware past email security, sandboxes, and spam filters. Although broken and corrupted, user applications open the malicious files through built-in recovery mechanisms. Security firm ANY.RUN says the technique has been used in the wild since at least August this year.
PAN zero-day attacks: Webscout has found additional C&C servers involved in attacks exploiting the two recent Palo Alto Networks zero-days (CVE-2024-0012 and CVE-2024-9474).
Russia's IP exposure: SANS ISC researcher Jan Kopriva has an interesting piece on how many Russian IP addresses are disappearing from internet scans—a sign Russia is amping its internet censorship efforts.
DW marketplace OpSec: Evan Boehs looks at the various OpSec practices used by the administrators of past dark web marketplaces.
Malicious ads across Egypt: Group-IB researchers look at a wave of malicious ads pushing Egyptian users towards scammy apps that steal their money and personal data.
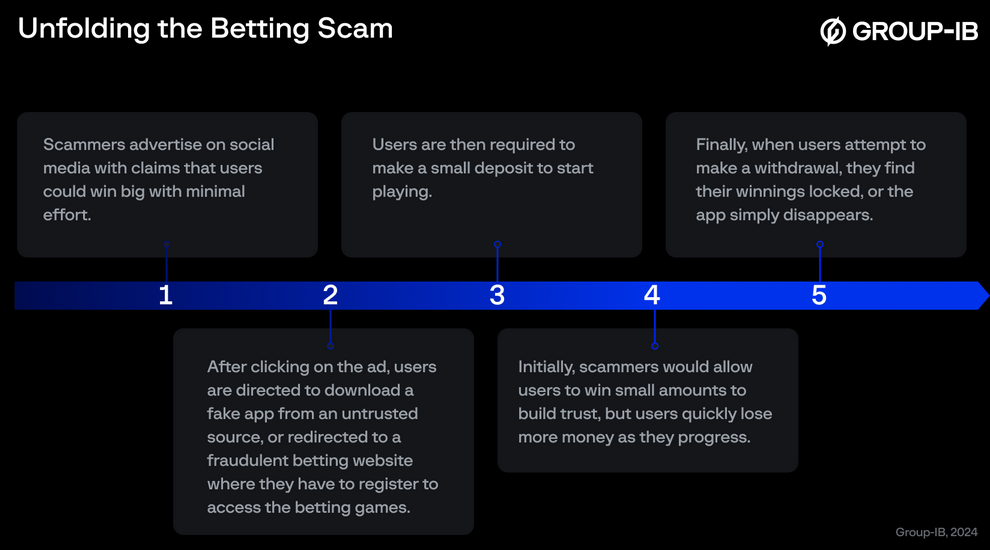
Malware technical reports
Cobalt Strike: A security researcher named Rasta Mouse has published an analysis of Cobalt Strike's UDRL, SleepMask, and BeaconGate features.
Interlock ransomware: Fortinet has published a report on Interlock, the first ransomware to have a FreeBSD version besides its Windows encrypter.
PixPirate: IBM's Trusteer security division looks at new campaigns spreading the PixPirate Android RAT across India. The company previously identified the malware earlier this year in January, targeting Brazilian banks. The malware is being distributed via WhatsApp.
Magento skimmer: Sucuri researchers have published a breakdown of a new e-skimmer found on Magento stores.
"This sophisticated skimmer targets Magento checkout pages to steal sensitive payment data, either by injecting fake forms or extracting live input fields. Its dynamic approach and encryption mechanisms make it challenging to detect."
Sponsor Section
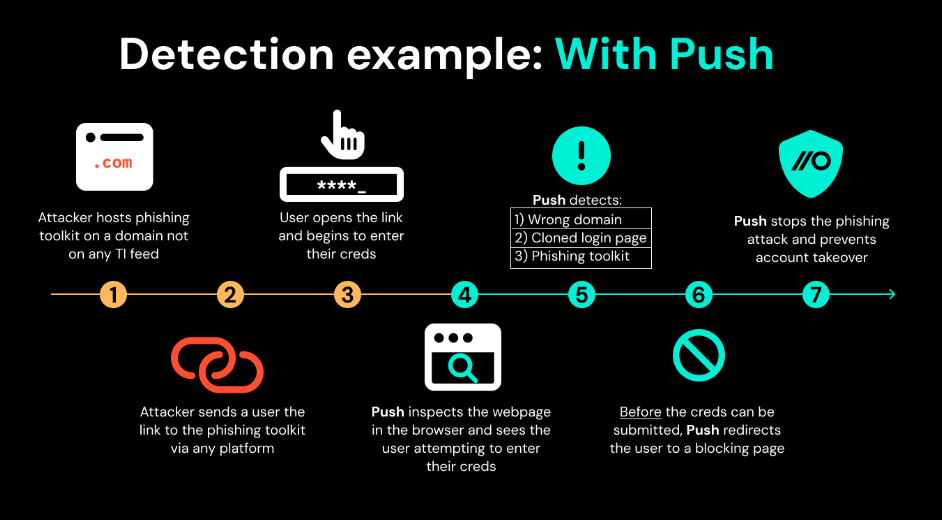
How Push detects and blocks phishing attempts in the browser – explained in less than two minutes.
APTs, cyber-espionage, and info-ops
TaxOff: A new cyber-espionage group named TaxOff is targeting Russian government agencies using time-sensitive legal and financial emails. The final payload is a new C++17 backdoor named Trinper.
APT-C-48: Qihoo's security team has published a report on resume-themed spear-phishing campaigns carried out by APT-C-48, also known as CNC.
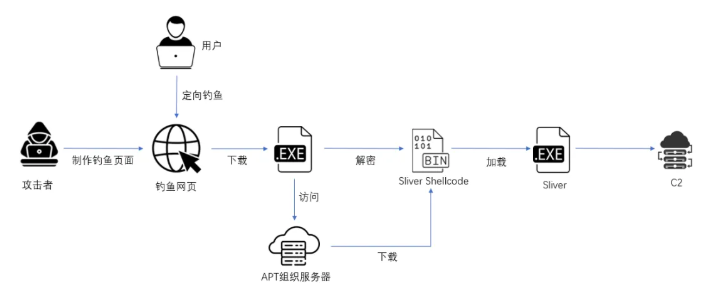
APT-C-01: The same company also looked at a recent APT-C-01 (Poison Ivy) campaign delivering the Sliver RAT via drive-by downloads.
Vulnerabilities, security research, and bug bounty
Windows Server 2012 zero-day: ACROS security researchers have discovered a new vulnerability that can allow threat actors to bypass the Mark of the Web (MotW) security check on Windows Server 2012 operating systems. Researchers say they reported the issue to Microsoft but the bug is currently still unpatched. The bug impacts all Windows Server 20212 versions released over the past two years. ACROS has released its own micro-patch for the bug until Microsoft releases a fix through its Extended Security Updates program. Windows Server 2012 reached end-of-support in October last year.
LLM Flowbreaking: Knostic researchers have published details on two race condition-type attacks on LLMs.
"We are disclosing two attacks of the LLM Flowbreaking class: (1) 'Second Thoughts,' and (2) 'Stop and Roll,' both resulting in information disclosure. More importantly, the research team managed to bypass policy, with a widely used successful LLM potentially providing explicit instructions to a girl on the topic of self-harm."
Infosec industry
New tool—ShadowHound: A group of security researchers have released ShadowHound, a "set of PowerShell scripts for Active Directory enumeration without the need for introducing known-malicious binaries like SharpHound."
New tool—Eclipse: Security researcher Kurosh Dabbagh has released Eclipse, a proof-of-concept exploit to launch DLL sideloading attacks via Microsoft's Activation Context data structures.
New tool—NoDelete: Security researcher Charles Lomboni has released NoDelete, a tool that assists in malware analysis by locking a folder where malware drops files before deleting them.
DefCamp CJ 2024 videos: Talks from the DefCamp Cluj-Napoca 2024 security conference, which took place in May, are available on YouTube.
Threat/trend reports: ENISA, Fortinet, Kaspersky, and Wordfence have recently published reports and summaries covering various infosec trends and industry threats.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about different views on attribution and why it still matters for sophisticated state-backed groups.
In this podcast, Tom Uren and Patrick Gray talk about the Australian Government's extraordinary legislation that will retrospectively ensure that warrants used for the An0m crime-phone sting operation are valid.
